系统调用(四):SSDT
查看SSDT和SSDTShadow
kd> dd KeServiceDescriptorTable
80553fa0 80502b8c 00000000 0000011c 80503000 Ntoskrl.exe
80553fb0 00000000 00000000 00000000 00000000
80553fc0 00000000 00000000 00000000 00000000
80553fd0 00000000 00000000 00000000 00000000
kd> dd KeServiceDescriptorTableShadow
80553f60 80502b8c 00000000 0000011c 80503000 Ntoskrl.exe
80553f70 bf999b80 00000000 0000029b bf99a890 Win32k.sys
80553f80 00000000 00000000 00000000 00000000
80553f90 00000000 00000000 00000000 00000000
第一个DWORD指向函数地址表
kd> dds 80502b8c
ReadVirtual: 80502b8c not properly sign extended
80502b8c 8059a948 nt!NtAcceptConnectPort
80502b90 805e7db6 nt!NtAccessCheck
80502b94 805eb5fc nt!NtAccessCheckAndAuditAlarm
80502b98 805e7de8 nt!NtAccessCheckByType
80502b9c 805eb636 nt!NtAccessCheckByTypeAndAuditAlarm
80502ba0 805e7e1e nt!NtAccessCheckByTypeResultList
第三个DWORD为函数数量
第四个DWORD指向函数参数表
kd> db 80503000
ReadVirtual: 80503000 not properly sign extended
80503000 18 20 2c 2c 40 2c 40 44-0c 08 18 18 08 04 04 0c . ,,@,@D........
80503010 10 18 08 08 0c 04 08 08-04 04 0c 08 0c 04 04 20 ...............
80503020 08 10 0c 14 0c 2c 10 0c-0c 1c 20 10 38 10 14 20 .....,.... .8..
80503030 24 24 1c 14 10 20 10 34-14 08 0c 08 04 04 04 04 $$... .4........
80503040 0c 08 28 04 1c 18 08 18-0c 18 08 18 0c 08 0c 04 ..(.............
80503050 10 00 0c 10 28 08 08 10-1c 04 08 0c 04 10 08 00 ....(...........
80503060 08 04 08 0c 28 08 04 10-04 04 0c 0c 28 04 24 28 ....(.......(.$(
80503070 30 0c 0c 0c 18 0c 0c 0c-0c 30 10 0c 10 0c 0c 0c 0........0......
实验:在函数表尾部加一函数调用
测试代码
#include "stdafx.h"
#include <windows.h>
void __declspec(naked) MyIntWriteProcessMemory(HANDLE hProcess,
LPVOID lpBaseAddress,
LPCVOID lpBuffer,
SIZE_T nSize,
SIZE_T *lpNumberOfBytesWritten){
__asm{
mov eax,0x11c
lea edx,[esp+4]
int 0x2e
ret
}
}
int main(int argc, char* argv[])
{
DWORD X=0xabcd;
DWORD addr=0;
DWORD dwProcessId = 0;
DWORD check=0;
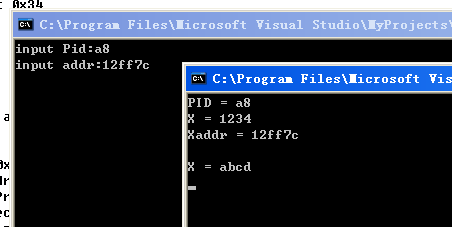
printf("input Pid:");
scanf("%x",&dwProcessId);
printf("input addr:");
scanf("%x",&addr);
HANDLE hProcess = OpenProcess(PROCESS_ALL_ACCESS,FALSE,dwProcessId);
MyIntWriteProcessMemory(hProcess,(char*)addr,(char*)&X,(SIZE_T)4,(SIZE_T*)NULL);
return 0;
}
#include "stdafx.h"
#include <windows.h>
int main(int argc, char* argv[])
{
DWORD X=0x1234;
DWORD PID=GetCurrentProcessId();
printf("PID = %x\n",PID);
printf("X = %x\n",X);
printf("Xaddr = %x\n",&X);
getchar();
printf("X = %x\n",X);
getchar();
return 0;
}
kd> ed 80502ffc 805aa81c
WriteVirtual: 80502ffc not properly sign extended
kd> dds 80502b8c+115*4
ReadVirtual: 80502fe0 not properly sign extended
80502fe0 805aa81c nt!NtWriteVirtualMemory
80502fe4 8050322c nt!NtYieldExecution
80502fe8 8060f632 nt!NtCreateKeyedEvent
80502fec 8060f71c nt!NtOpenKeyedEvent
80502ff0 8060f7ce nt!NtReleaseKeyedEvent
80502ff4 8060fa5a nt!NtWaitForKeyedEvent
80502ff8 805c2798 nt!NtQueryPortInformationProcess
80502ffc 805aa81c nt!NtWriteVirtualMemory
kd> eb 8050311c 14
kd> ed 80553fa8 11d


 浙公网安备 33010602011771号
浙公网安备 33010602011771号