跨网访问企业使用实战
一、openvpn概述
一)VPN
VPN 英文全称(Virtual Private Network),中文译为:虚拟私人网络,又称为虚拟专用网络,用于在不安全的线路上安全的传输数据。VPN:属于远程访问技术,简单地说就是利用公用网络架设专用网络。
二)openvpn
OpenVPN:一个实现VPN的开源软件,OpenVPN 是一个健壮的、高度灵活的 VPN 守护进程。它支持 SSL/TLS 安全、Ethernet bridging、经由代理的 TCP 或 UDP 隧道和 NAT。另外,它也支持动态 IP 地址以及DHCP,可伸缩性足以支持数百或数千用户的使用场景,同时可移植至大多数主流操作系统平台上。
一般使用UDP隧道
官网:https://openvpn.net
GitHub地址:https://github.com/OpenVPN/openvpn
二、openvpn搭建
一)使用一键安装脚本安装openvpn server
1、下载安装脚本
cd ${dest_dir}
wget https://raw.githubusercontent.com/ssoe/openvpn-installer/master/openvpn-installer.sh --no-check-certificate -O openvpn-installer.sh
chmod +x openvpn-installer.sh
2、执行安装脚本安装openvpn-server
# sh /usr/local/src/openvpn-install.sh
Welcome to the OpenVPN installer!
The git repository is available at: https://github.com/angristan/openvpn-install
I need to ask you a few questions before starting the setup.
You can leave the default options and just press enter if you are ok with them.
I need to know the IPv4 address of the network interface you want OpenVPN listening to.
Unless your server is behind NAT, it should be your public IPv4 address.
IP address: 172.30.11.112 ## 或自动获取到主机的内网IP
It seems this server is behind NAT. What is its public IPv4 address or hostname?
We need it for the clients to connect to the server.
Public IPv4 address or hostname: 123.51.16.14 ## 根据实际环境需求,配置公网域名或IP
Checking for IPv6 connectivity...
Your host does not appear to have IPv6 connectivity.
Do you want to enable IPv6 support (NAT)? [y/n]: n ## 默认值是n
What port do you want OpenVPN to listen to?
1) Default: 1194
2) Custom
3) Random [49152-65535]
Port choice [1-3]: 1 ##默认值是1,使用默认端口1194
What protocol do you want OpenVPN to use?
UDP is faster. Unless it is not available, you shouldn't use TCP.
1) UDP
2) TCP
Protocol [1-2]: 1 ##默认值是1,使用UDP协议(因为它更快)
What DNS resolvers do you want to use with the VPN?
1) Current system resolvers (from /etc/resolv.conf)
2) Self-hosted DNS Resolver (Unbound)
3) Cloudflare (Anycast: worldwide)
4) Quad9 (Anycast: worldwide)
5) Quad9 uncensored (Anycast: worldwide)
6) FDN (France)
7) DNS.WATCH (Germany)
8) OpenDNS (Anycast: worldwide)
9) Google (Anycast: worldwide)
10) Yandex Basic (Russia)
11) AdGuard DNS (Russia)
DNS [1-10]: 3 ## 默认值是3
Do you want to use compression? It is not recommended since the VORACLE attack make use of it.
Enable compression? [y/n]: n
Do you want to customize encryption settings?
Unless you know what you're doing, you should stick with the default parameters provided by the script.
Note that whatever you choose, all the choices presented in the script are safe. (Unlike OpenVPN's defaults)
See https://github.com/angristan/openvpn-install#security-and-encryption to learn more.
Customize encryption settings? [y/n]: n ## 默认值是n
Okay, that was all I needed. We are ready to setup your OpenVPN server now.
You will be able to generate a client at the end of the installation.
Press any key to continue... ## 按任何键,继续
Loaded plugins: fastestmirror, product-id, search-disabled-repos, subscription-manager
This system is not registered with an entitlement server. You can use subscription-manager to register.
Loading mirror speeds from cached hostfile
Package epel-release-7-14.noarch already installed and latest version
Nothing to do
Loaded plugins: fastestmirror, product-id, search-disabled-repos, subscription-manager
This system is not registered with an entitlement server. You can use subscription-manager to register.
Loading mirror speeds from cached hostfile
Package iptables-1.4.21-35.el7.x86_64 already installed and latest version
Package 1:openssl-1.0.2k-25.el7_9.x86_64 already installed and latest version
Package wget-1.14-18.el7_6.1.x86_64 already installed and latest version
Package ca-certificates-2021.2.50-72.el7_9.noarch already installed and latest version
Package curl-7.29.0-59.el7_9.1.x86_64 already installed and latest version
Resolving Dependencies
--> Running transaction check
---> Package openvpn.x86_64 0:2.4.12-1.el7 will be installed
--> Finished Dependency Resolution
Dependencies Resolved
============================================================================================================================================================
Package Arch Version Repository Size
============================================================================================================================================================
Installing:
openvpn x86_64 2.4.12-1.el7 epel 529 k
Transaction Summary
============================================================================================================================================================
Install 1 Package
Total download size: 529 k
Installed size: 1.2 M
Downloading packages:
openvpn-2.4.12-1.el7.x86_64.rpm | 529 kB 00:00:00
Running transaction check
Running transaction test
Transaction test succeeded
Running transaction
Installing : openvpn-2.4.12-1.el7.x86_64 1/1
Verifying : openvpn-2.4.12-1.el7.x86_64 1/1
Installed:
openvpn.x86_64 0:2.4.12-1.el7
Complete!
--2022-05-06 16:55:45-- https://github.com/OpenVPN/easy-rsa/releases/download/v3.0.6/EasyRSA-unix-v3.0.6.tgz
Resolving github.com (github.com)... 20.205.243.166
Connecting to github.com (github.com)|20.205.243.166|:443... connected.
HTTP request sent, awaiting response... 302 Found
Location: https://objects.githubusercontent.com/github-production-release-asset-2e65be/4519663/8d46db80-266e-11e9-85e3-7de4dbee40d9?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAIWNJYAX4CSVEH53A%2F20220506%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20220506T085545Z&X-Amz-Expires=300&X-Amz-Signature=7121e2318226058c0386328e6abce3b34dec6a52407a1e3a8e872c39ca257703&X-Amz-SignedHeaders=host&actor_id=0&key_id=0&repo_id=4519663&response-content-disposition=attachment%3B%20filename%3DEasyRSA-unix-v3.0.6.tgz&response-content-type=application%2Foctet-stream [following]
--2022-05-06 16:55:45-- https://objects.githubusercontent.com/github-production-release-asset-2e65be/4519663/8d46db80-266e-11e9-85e3-7de4dbee40d9?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAIWNJYAX4CSVEH53A%2F20220506%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20220506T085545Z&X-Amz-Expires=300&X-Amz-Signature=7121e2318226058c0386328e6abce3b34dec6a52407a1e3a8e872c39ca257703&X-Amz-SignedHeaders=host&actor_id=0&key_id=0&repo_id=4519663&response-content-disposition=attachment%3B%20filename%3DEasyRSA-unix-v3.0.6.tgz&response-content-type=application%2Foctet-stream
Resolving objects.githubusercontent.com (objects.githubusercontent.com)... 185.199.109.133, 185.199.111.133, 185.199.108.133, ...
Connecting to objects.githubusercontent.com (objects.githubusercontent.com)|185.199.109.133|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 40840 (40K) [application/octet-stream]
Saving to: ‘/root/EasyRSA-unix-v3.0.6.tgz’
100%[==================================================================================================================>] 40,840 --.-K/s in 0.08s
2022-05-06 16:55:46 (495 KB/s) - ‘/root/EasyRSA-unix-v3.0.6.tgz’ saved [40840/40840]
Note: using Easy-RSA configuration from: ./vars
init-pki complete; you may now create a CA or requests.
Your newly created PKI dir is: /etc/openvpn/easy-rsa/pki
read EC key
writing EC key
Note: using Easy-RSA configuration from: ./vars
Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017
Generating a 256 bit EC private key
writing new private key to '/etc/openvpn/easy-rsa/pki/private/server_PfE4qk04rDEQ63Il.key.JY8UNhcN2r'
-----
Using configuration from /etc/openvpn/easy-rsa/pki/safessl-easyrsa.cnf
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
commonName :ASN.1 12:'server_PfE4qk04rDEQ63Il'
Certificate is to be certified until Apr 20 08:55:46 2025 GMT (1080 days)
Write out database with 1 new entries
Data Base Updated
Note: using Easy-RSA configuration from: ./vars
Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017
Using configuration from /etc/openvpn/easy-rsa/pki/safessl-easyrsa.cnf
An updated CRL has been created.
CRL file: /etc/openvpn/easy-rsa/pki/crl.pem
* Applying /usr/lib/sysctl.d/00-system.conf ...
net.bridge.bridge-nf-call-ip6tables = 0
net.bridge.bridge-nf-call-iptables = 0
net.bridge.bridge-nf-call-arptables = 0
* Applying /usr/lib/sysctl.d/10-default-yama-scope.conf ...
kernel.yama.ptrace_scope = 0
* Applying /etc/sysctl.d/20-openvpn.conf ...
net.ipv4.ip_forward = 1
* Applying /usr/lib/sysctl.d/50-default.conf ...
kernel.sysrq = 16
kernel.core_uses_pid = 1
kernel.kptr_restrict = 1
net.ipv4.conf.default.rp_filter = 1
net.ipv4.conf.all.rp_filter = 1
net.ipv4.conf.default.accept_source_route = 0
net.ipv4.conf.all.accept_source_route = 0
net.ipv4.conf.default.promote_secondaries = 1
net.ipv4.conf.all.promote_secondaries = 1
fs.protected_hardlinks = 1
fs.protected_symlinks = 1
* Applying /usr/lib/sysctl.d/99-docker.conf ...
fs.may_detach_mounts = 1
* Applying /etc/sysctl.d/99-sysctl.conf ...
vm.swappiness = 0
kernel.sysrq = 1
net.ipv4.neigh.default.gc_stale_time = 120
net.ipv4.conf.all.rp_filter = 0
net.ipv4.conf.default.rp_filter = 0
net.ipv4.conf.default.arp_announce = 2
net.ipv4.conf.lo.arp_announce = 2
net.ipv4.conf.all.arp_announce = 2
net.ipv4.tcp_max_tw_buckets = 5000
net.ipv4.tcp_syncookies = 1
net.ipv4.tcp_max_syn_backlog = 1024
net.ipv4.tcp_synack_retries = 2
net.ipv4.tcp_slow_start_after_idle = 0
* Applying /etc/sysctl.conf ...
vm.swappiness = 0
kernel.sysrq = 1
net.ipv4.neigh.default.gc_stale_time = 120
net.ipv4.conf.all.rp_filter = 0
net.ipv4.conf.default.rp_filter = 0
net.ipv4.conf.default.arp_announce = 2
net.ipv4.conf.lo.arp_announce = 2
net.ipv4.conf.all.arp_announce = 2
net.ipv4.tcp_max_tw_buckets = 5000
net.ipv4.tcp_syncookies = 1
net.ipv4.tcp_max_syn_backlog = 1024
net.ipv4.tcp_synack_retries = 2
net.ipv4.tcp_slow_start_after_idle = 0
Created symlink from /etc/systemd/system/multi-user.target.wants/openvpn@server.service to /etc/systemd/system/openvpn@.service. ## 服务启动配置的文件的路径
mkdir: cannot create directory ‘/etc/iptables’: File exists
Created symlink from /etc/systemd/system/multi-user.target.wants/iptables-openvpn.service to /etc/systemd/system/iptables-openvpn.service.
Tell me a name for the client.
Use one word only, no special characters.
Client name: test ##创建测试用户
Do you want to protect the configuration file with a password?
(e.g. encrypt the private key with a password)
1) Add a passwordless client
2) Use a password for the client
Select an option [1-2]: 1 ## 默认是1(不添加密码),client是否使用密码
Note: using Easy-RSA configuration from: ./vars
Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017
Generating a 256 bit EC private key
writing new private key to '/etc/openvpn/easy-rsa/pki/private/test.key.M6i3seLOrb'
-----
Using configuration from /etc/openvpn/easy-rsa/pki/safessl-easyrsa.cnf
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
commonName :ASN.1 12:'test'
Certificate is to be certified until Apr 20 08:55:55 2025 GMT (1080 days)
Write out database with 1 new entries
Data Base Updated
Client bv added, the configuration file is available at /root/test.ovpn. ## 创建的客户端配置文件,默认存到操作脚本用户的家目录下
Download the .ovpn file and import it in your OpenVPN client.
查看服务启动状态(安装完,默认就启动了服务)
# systemctl status openvpn@server.service
● openvpn@server.service - OpenVPN Robust And Highly Flexible Tunneling Application On server
Loaded: loaded (/etc/systemd/system/openvpn@.service; enabled; vendor preset: disabled)
Active: active (running) since Fri 2022-05-06 17:23:22 CST; 1min 9s ago
Main PID: 1847 (openvpn)
Status: "Initialization Sequence Completed"
CGroup: /system.slice/system-openvpn.slice/openvpn@server.service
└─1847 /usr/sbin/openvpn --cd /etc/openvpn/ --config server.conf
May 06 17:23:22 grafana-prometheus openvpn[1847]: Fri May 6 17:23:22 2022 Socket Buffers: R=[212992->212992] S=[212992->212992]
May 06 17:23:22 grafana-prometheus openvpn[1847]: Fri May 6 17:23:22 2022 UDPv4 link local (bound): [AF_INET][undef]:1194
May 06 17:23:22 grafana-prometheus openvpn[1847]: Fri May 6 17:23:22 2022 UDPv4 link remote: [AF_UNSPEC]
May 06 17:23:22 grafana-prometheus openvpn[1847]: Fri May 6 17:23:22 2022 GID set to nobody
May 06 17:23:22 grafana-prometheus openvpn[1847]: Fri May 6 17:23:22 2022 UID set to nobody
May 06 17:23:22 grafana-prometheus openvpn[1847]: Fri May 6 17:23:22 2022 MULTI: multi_init called, r=256 v=256
May 06 17:23:22 grafana-prometheus openvpn[1847]: Fri May 6 17:23:22 2022 IFCONFIG POOL: base=10.8.0.2 size=252, ipv6=0
May 06 17:23:22 grafana-prometheus openvpn[1847]: Fri May 6 17:23:22 2022 IFCONFIG POOL LIST
May 06 17:23:22 grafana-prometheus openvpn[1847]: Fri May 6 17:23:22 2022 Initialization Sequence Completed
May 06 17:23:22 grafana-prometheus systemd[1]: Started OpenVPN Robust And Highly Flexible Tunneling Application On server.
二)修改server的配置文件
安装完,默认的配置文件如下
# cat /etc/openvpn/server.conf
port 1194
proto udp
dev tun
user nobody
group nobody
persist-key
persist-tun
keepalive 10 120
topology subnet
server 10.8.0.0 255.255.255.0
ifconfig-pool-persist ipp.txt
push "dhcp-option DNS 1.0.0.1"
push "dhcp-option DNS 1.1.1.1"
push "redirect-gateway def1 bypass-dhcp"
dh none
ecdh-curve prime256v1
tls-crypt tls-crypt.key 0
crl-verify crl.pem
ca ca.crt
cert server_6lcnPQ8KabByDsh5.crt
key server_6lcnPQ8KabByDsh5.key
auth SHA256
cipher AES-128-GCM
ncp-ciphers AES-128-GCM
tls-server
tls-version-min 1.2
tls-cipher TLS-ECDHE-ECDSA-WITH-AES-128-GCM-SHA256
status /var/log/openvpn/status.log
verb 3
变更后的配置文件
port 1194
proto udp
dev tun
user nobody
group nobody
persist-key
persist-tun
keepalive 10 120
topology subnet
server 10.8.0.0 255.255.255.0
ifconfig-pool-persist ipp.txt
## 根据实际添加和变更dns服务
push "dhcp-option DNS 114.114.114.114"
### 添加路由配置
push "route 172.31.0.0 255.255.0.0"
push "route 5.78.10.16 255.255.255.255"
## 可以连接客户端的数量
max-clients 100
dh none ecdh-curve prime256v1 tls-crypt tls-crypt.key 0 crl-verify crl.pem ca ca.crt cert server_3ofszxuJxpaOuGC7.crt key server_3ofszxuJxpaOuGC7.key auth SHA256 cipher AES-128-GCM ncp-ciphers AES-128-GCM tls-server tls-version-min 1.2 tls-cipher TLS-ECDHE-ECDSA-WITH-AES-128-GCM-SHA256 status /var/log/openvpn/status.log verb 3
三)扩展一:openvpn集成openldap
https://ld246.com/article/1589975805640
四)扩展二:openvpn使用私网IP,使用nginx(或LB)公网IP做代理
nginx使用stream模块代理openvpn的udp端口1194
注意:
- 安装时,使用代理的公网IP,server启动的端口(协议根据实际需要调整)
- stream模块代理udp时,格式:listen 端口号
stream {
upstream openvpn_udp {
server 172.30.96.38:1194;
}
server {
listen 1194 udp;
proxy_pass openvpn_udp;
}
}
启动nginx,验证代理
# ss -lutnp|grep 1194
udp UNCONN 0 0 *:1194 *:* users:(("nginx",pid=29090,fd=6),("nginx",pid=11448,fd=6),("nginx",pid=11447,fd=6),("nginx",pid=11446,fd=6),("nginx",pid=11445,fd=6),("nginx",pid=11444,fd=6),("nginx",pid=11443,fd=6),("nginx",pid=11442,fd=6),("nginx",pid=11441,fd=6))
三、openvpn使用
一)server端
1、添加用户
# sh /usr/local/src/openvpn-install.sh
Welcome to OpenVPN-install!
The git repository is available at: https://github.com/angristan/openvpn-install
It looks like OpenVPN is already installed.
What do you want to do?
1) Add a new user
2) Revoke existing user
3) Remove OpenVPN
4) Exit
Select an option [1-4]: 1
Tell me a name for the client.
Use one word only, no special characters.
Client name: sky
Do you want to protect the configuration file with a password?
(e.g. encrypt the private key with a password)
1) Add a passwordless client
2) Use a password for the client
Select an option [1-2]: 1
Note: using Easy-RSA configuration from: ./vars
Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017
Generating a 256 bit EC private key
writing new private key to '/etc/openvpn/easy-rsa/pki/private/sky.key.ypmRXUH8aK'
-----
Using configuration from /etc/openvpn/easy-rsa/pki/safessl-easyrsa.cnf
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
commonName :ASN.1 12:'sky'
Certificate is to be certified until Apr 20 09:43:32 2025 GMT (1080 days)
Write out database with 1 new entries
Data Base Updated
Client sky added, the configuration file is available at /root/sky.ovpn.
Download the .ovpn file and import it in your OpenVPN client.
2、删除用户
# sh /usr/local/src/openvpn-install.sh
Welcome to OpenVPN-install!
The git repository is available at: https://github.com/angristan/openvpn-install
It looks like OpenVPN is already installed.
What do you want to do?
1) Add a new user
2) Revoke existing user
3) Remove OpenVPN
4) Exit
Select an option [1-4]: 2
Select the existing client certificate you want to revoke
1) test
Select one client [1]: 1 ## 填入你需要删除用户前面的ID
Using configuration from /etc/openvpn/easy-rsa/pki/safessl-easyrsa.cnf
Revoking Certificate 6DD427C9806B13EFE0F872A6C76DCD1D.
Data Base Updated
Note: using Easy-RSA configuration from: ./vars
Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017
Using configuration from /etc/openvpn/easy-rsa/pki/safessl-easyrsa.cnf
An updated CRL has been created.
CRL file: /etc/openvpn/easy-rsa/pki/crl.pem
Certificate for client test revoked.
3、卸载openvpn-server
# sh /usr/local/src/openvpn-install.sh Welcome to OpenVPN-install! The git repository is available at: https://github.com/angristan/openvpn-install It looks like OpenVPN is already installed. What do you want to do? 1) Add a new user 2) Revoke existing user 3) Remove OpenVPN 4) Exit Select an option [1-4]: 3 Do you really want to remove OpenVPN? [y/n]: y Removed symlink /etc/systemd/system/multi-user.target.wants/openvpn@server.service. Removed symlink /etc/systemd/system/multi-user.target.wants/iptables-openvpn.service. Loaded plugins: fastestmirror, product-id, search-disabled-repos, subscription-manager This system is not registered with an entitlement server. You can use subscription-manager to register. Resolving Dependencies --> Running transaction check ---> Package openvpn.x86_64 0:2.4.12-1.el7 will be erased --> Finished Dependency Resolution Dependencies Resolved ============================================================================================================================================================ Package Arch Version Repository Size ============================================================================================================================================================ Removing: openvpn x86_64 2.4.12-1.el7 @epel 1.2 M Transaction Summary ============================================================================================================================================================ Remove 1 Package Installed size: 1.2 M Downloading packages: Running transaction check Running transaction test Transaction test succeeded Running transaction Erasing : openvpn-2.4.12-1.el7.x86_64 1/1 Verifying : openvpn-2.4.12-1.el7.x86_64 1/1 base/7/x86_64 | 3.6 kB 00:00:00 epel/x86_64 | 4.7 kB 00:00:00 epel/x86_64/updateinfo | 1.0 MB 00:00:00 epel/x86_64/primary_db | 7.0 MB 00:00:00 extras/7/x86_64 | 2.9 kB 00:00:00 updates/7/x86_64 | 2.9 kB 00:00:00 Removed: openvpn.x86_64 0:2.4.12-1.el7 Complete!
二)客户端
下载地址如下,若安装完,不知道具体如何配置,可以找我
1、Windows客户端
https://www.download.io/openvpn-gui-download-windows.html
2、 Mac客户端
https://mac.filehorse.com/download-openvpn/
3、安卓手机客户端
https://openvpn-connect.en.softonic.com/android
4、苹果手机客户端
https://openvpn-connect.en.softonic.com/iphone
5、Linux客户端(以centos操作系统为例)
yum install epel-release -y
yum install openvpn
## 将客户端配置文件放在下面的目录下
cd /etc/openvpn/client
## 后台启动openvpn-client服务
openvpn --config openvpn-client-xxx.ovpn --daemon
四、openvpn监控(openvpn_exporter+Prometheus+grafana)
一)部署openvpn_exporter
openvpn_exporter地址:https://github.com/kumina/openvpn_exporter
github上没有二进制文件,需要自己编译
yum install go -y
#从GitHub上下载源码,编译成二进制文件
tar -xf v0.3.0.tar.gz
cd openvpn_exporter-0.3.0/
go build -o openvpn_exporter main.go
mkdir /usr/local/openvpn_exporter/
mv openvpn_exporter /usr/local/openvpn_exporter/
openvpn_exporter是读取openvpn的状态文件来读取指标的,所以要配置openvpn状态文件的位置。在openvpn 的配置文件 /etc/openvpn/server/server.conf 如下指令是配置状态文件的。
启动openvpn_exporter测试(最好使用进程管理工具管理服务 或 配置系统服务)
./openvpn_exporter -openvpn.status_paths /var/log/openvpn/status.log &
创建systemd服务文件:
[Unit]
Description=Prometheus OpenVPN Node Exporter
Wants=network-online.target
After=network-online.target
[Service]
Type=simple
ExecStart=/usr/local/openvpn_exporter/openvpn_exporter -openvpn.status_paths /var/log/openvpn/status.log
Restart=on-failure
KillMode=process
RestartSec=10
[Install]
WantedBy=multi-user.target
启动服务并配置成开机自启动
systemctl start openvpn_exporter.service && systemctl status openvpn_exporter.service
二)Prometheus中添加服务监控
在Prometheus的配置文件添加下面内容,然后重启服务
- job_name: 'openvpn-server'
scrape_interval: 30s
static_configs:
- targets: ['172.30.96.28:9176'] #根据实际情况作出调整
relabel_configs:
- source_labels: ['__address__']
regex: (.*):(.*)
target_label: pod
action: replace
replacement: $1
验证监控项(浏览访问或curl)
curl http://172.30.96.28:9176/metrics
补充:若缺少openvpn的监控项,变更server的启动命令如下
/usr/sbin/openvpn --cd /etc/openvpn/ --config server.conf
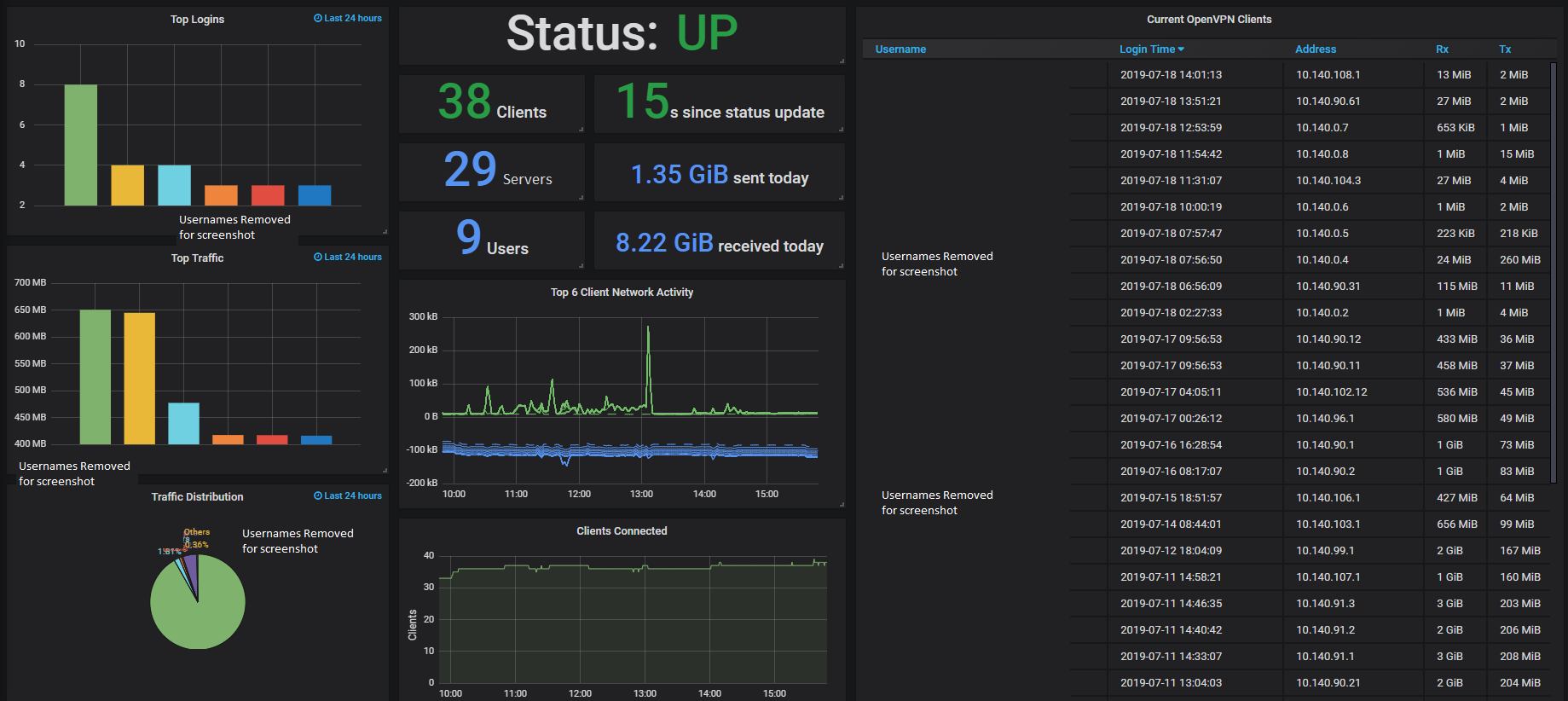
三)导入dashboard到grafana
https://grafana.com/grafana/dashboards/10562
配置完毕后,效果如下图