Wireshark ARP 抓包实践
网上讲 Address Resolution Protocol(地址解析协议)的文章挺多的,我这里就是用Wireshark软件抓包看下,重在实践:
首先贴下 ARP rfc 826地址
下面是ARP协议以太帧格式:
Packet format:
--------------
To communicate mappings from <protocol, address> pairs to 48.bit
Ethernet addresses, a packet format that embodies the Address
Resolution protocol is needed. The format of the packet follows.
Ethernet transmission layer (not necessarily accessible to ## 以太帧头 固定 14个字节 (用户不可访问)
the user):
48.bit: Ethernet address of destination # 6个字节(目的以太网地址)
48.bit: Ethernet address of sender # 6个字节(源以太网地址)
16.bit: Protocol type = ether_type$ADDRESS_RESOLUTION # 2个字节
Ethernet packet data: ## 以太帧数据 总共 28 字节(ip packet,ip包大小为 [46, 1500]个字节)
16.bit: (ar$hrd) Hardware address space (e.g., Ethernet, # 2个字节(硬件类型,以太网为 0001)
Packet Radio Net.)
16.bit: (ar$pro) Protocol address space. For Ethernet # 2个字节(协议类型,ipv4为 0800)
hardware, this is from the set of type
fields ether_typ$<protocol>.
8.bit: (ar$hln) byte length of each hardware address # 1个字节(硬件类型长度,以太网地址长度为 06)
8.bit: (ar$pln) byte length of each protocol address # 1个字节(协议类型长度,ipv4地址为 04)
16.bit: (ar$op) opcode (ares_op$REQUEST | ares_op$REPLY) # 2个字节(1:arp请求,2:arp响应)
nbytes: (ar$sha) Hardware address of sender of this # n的位数由 `ar$hln`(对应下图硬件mac地址大小,值为06,就是6个字节) 字段决定
packet, n from the ar$hln field.
mbytes: (ar$spa) Protocol address of sender of this # n的位数由 `ar$pln`(对应下图协议ipv4地址大小,值为04,就是4个字节) 字段决定
packet, m from the ar$pln field.
nbytes: (ar$tha) Hardware address of target of this # 6个字节
packet (if known).
mbytes: (ar$tpa) Protocol address of target. # 4个字节
Crc 循环冗余校验 ## 总共4个字节(用户不可访问)
下图为ARP报文格式
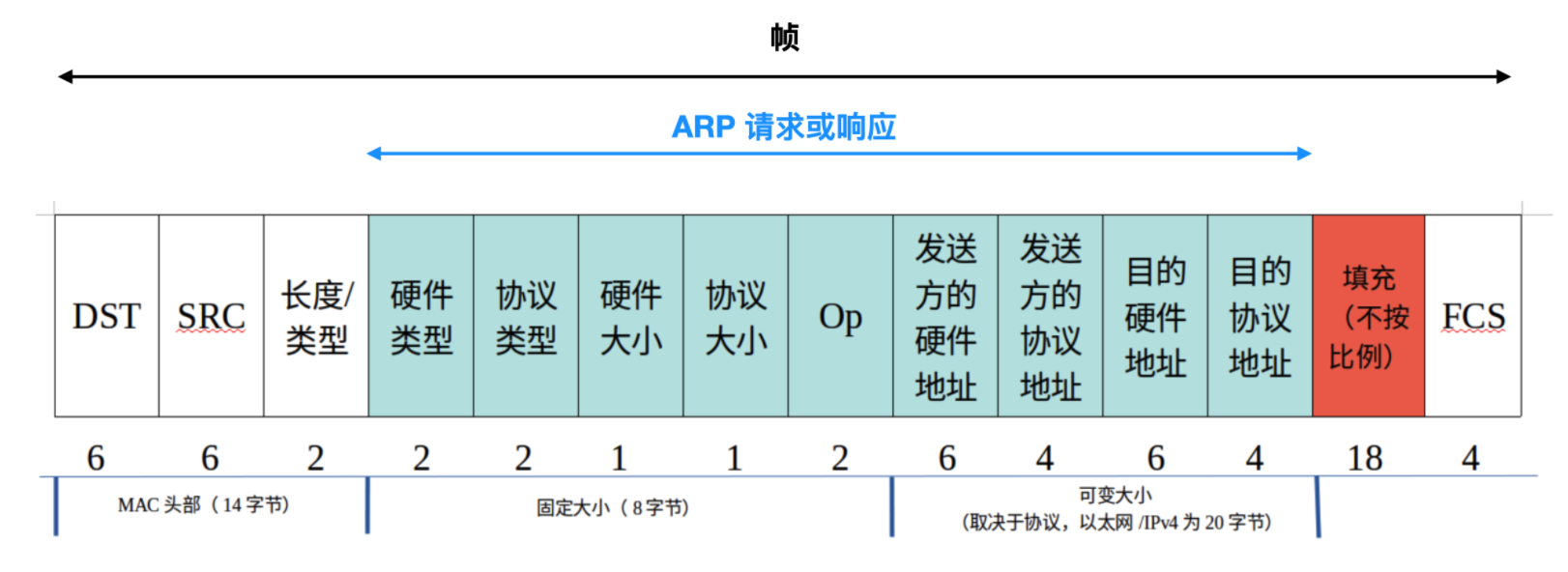
图片来源: 一文详解 ARP 协议
下图为以太帧报文格式
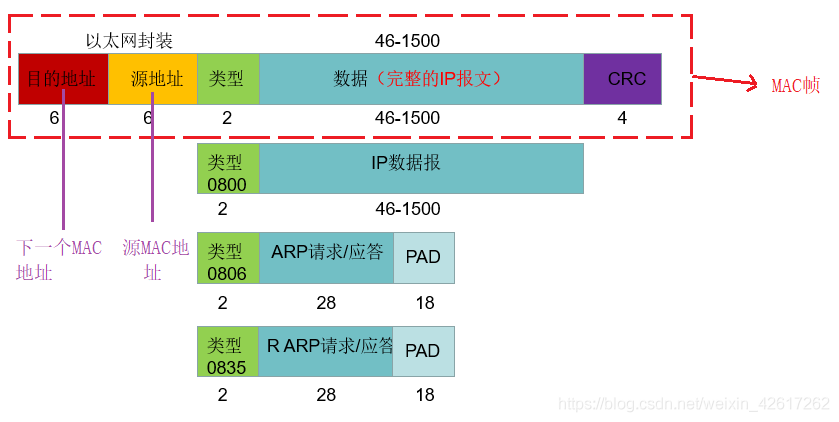
图片来源: 数据链路层---以太网/MAC帧/ARP协议详解
Wireshark安装和使用请自行百度吧,网上一大堆:
打开Wareshark后,按照Protocol(不同的协议颜色是不一样的,这一点给Wareshark点个赞,我电脑是windows,ARP颜色为橘色吧)进行排序筛选,
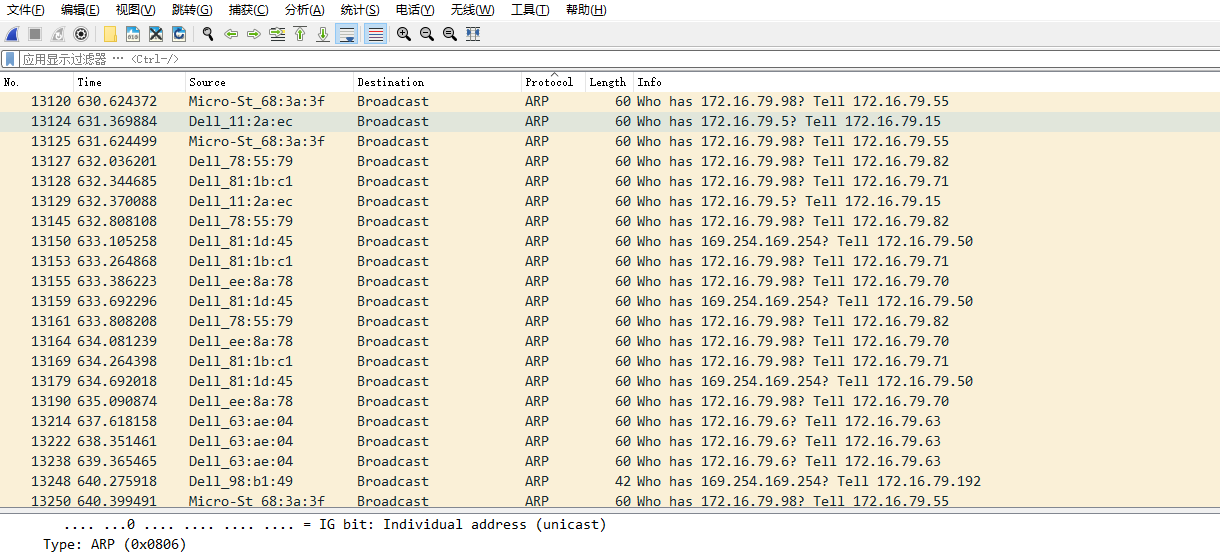
找到ARP后
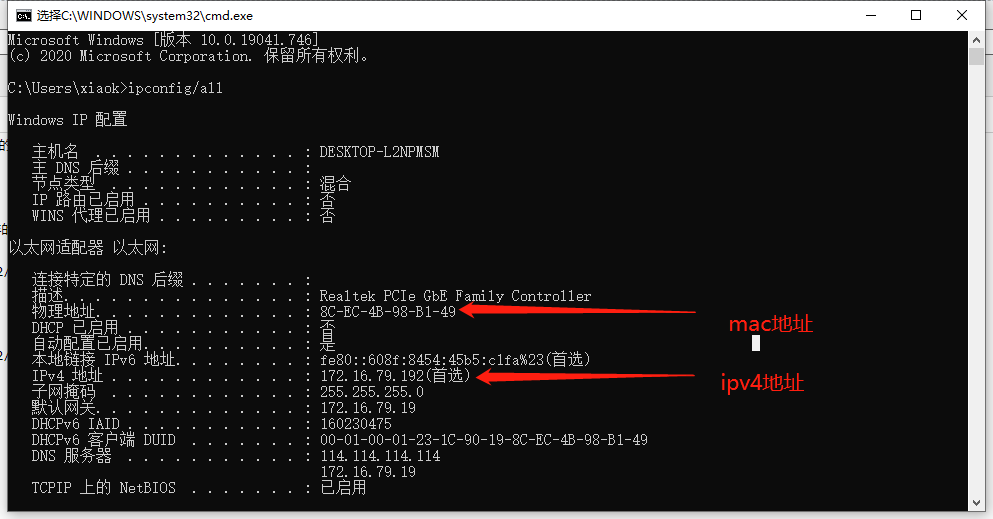
在cmd输入 ipconfig/all 查看本机ipv4地址和mac地址:
mac地址: 8C-EC-4B-98-B1-49
ipv4地址: 172.16.79.192
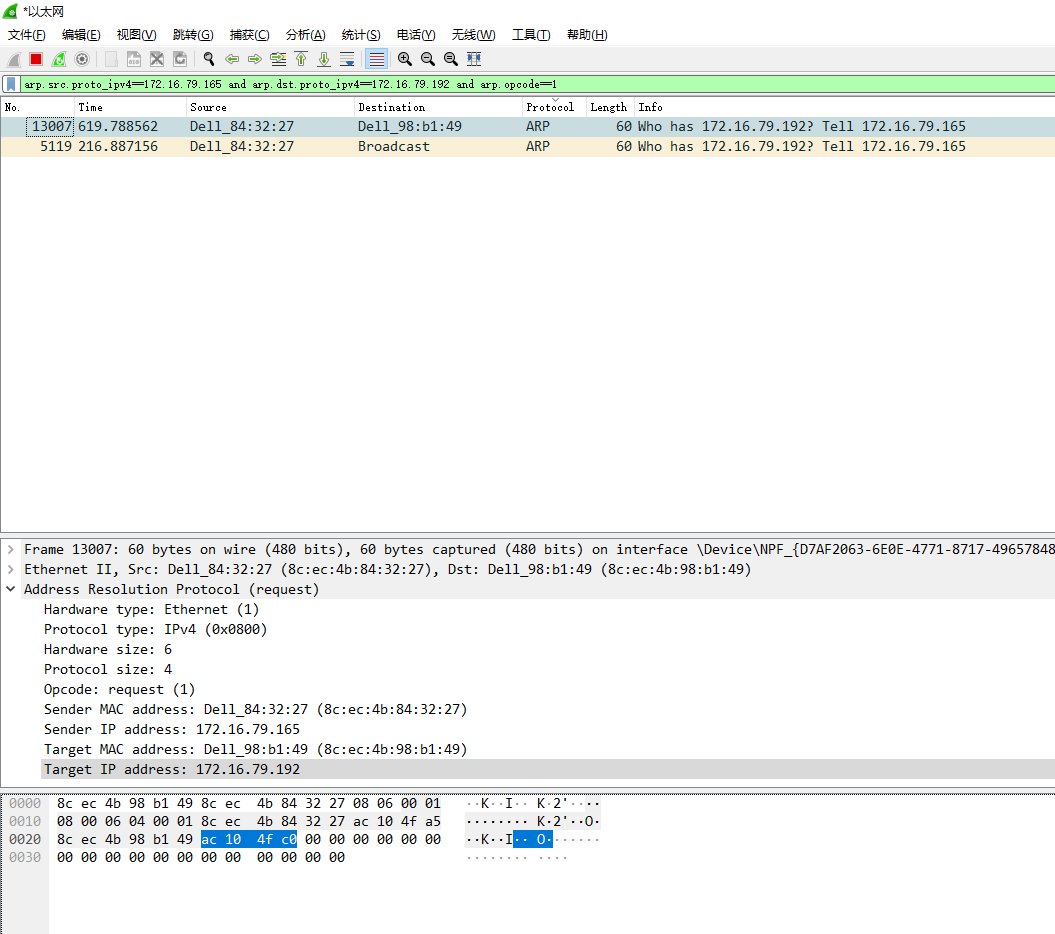
在过滤条件里输入 arp.src.proto_ipv4==172.16.79.165 and arp.dst.proto_ipv4==172.16.79.192 and arp.opcode==1 表示165机器访问192(本机)mac地址的请求包
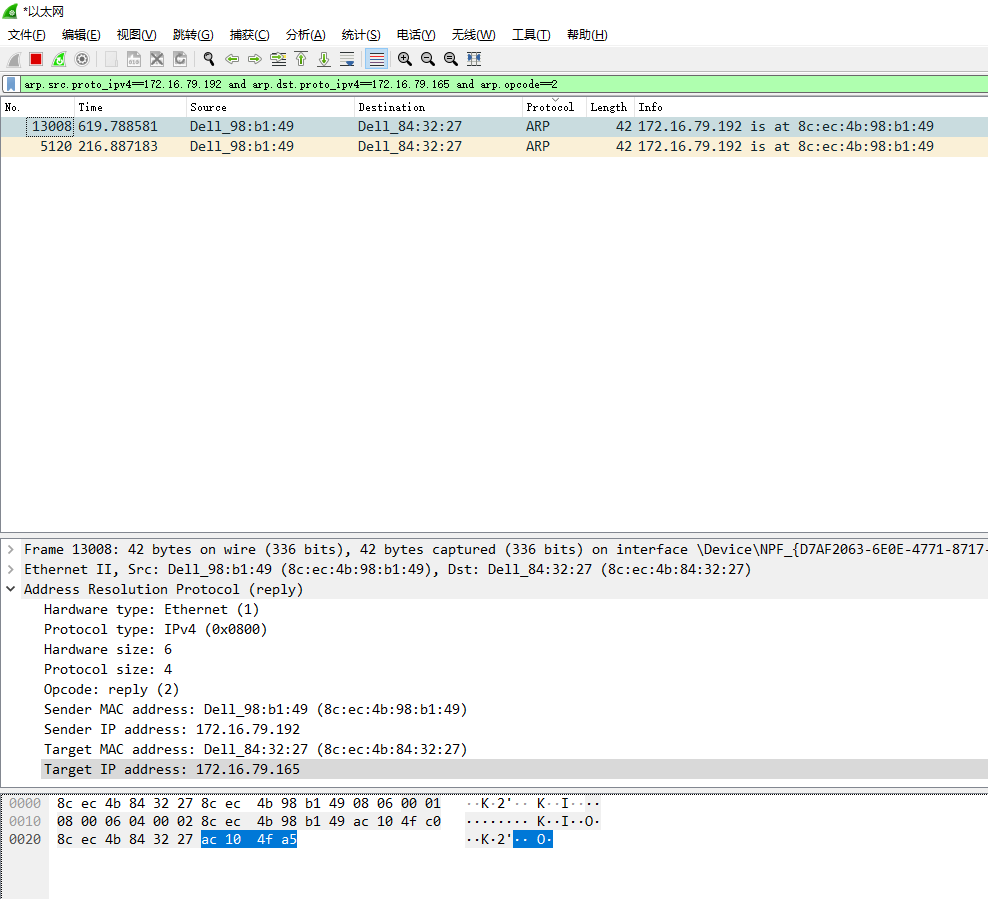
在过滤条件里输入 arp.src.proto_ipv4==172.16.79.192 and arp.dst.proto_ipv4==172.16.79.165 and arp.opcode==2 表示192(本机)响应165机器mac地址的响应包
我们知道ip包最小是 46个字节,加上以太帧固定头14个字节 + CRC校验4个字节,ip包里边还剩应该为46 + 18 = 64字节,也就是说一个ARP报文以太帧应该是64个字节,而我们通过ARP的请求(60个字节被捕获)和响应(42个字节被捕获),这对不上啊?到底是那里出了问题???
一通搜索后发现,解释如下
`No, all ARP packets on Ethernet are 64 bytes, not 42. Wireshark tells you only 42 bytes are sent, but it is lying. The reason for this is because the padding to 60 bytes + 4 byte CRC is done by the Ethernet hardware as the ARP packet is being transmitted. Windows submits only 42 bytes to the NDIS driver, so that's all Wireshark gets to see.
You can observe that all ARP packets are 64 bytes by running Wireshark on two PCs that are connected to the same network. The node that sends the ARP query or response will show 42 bytes sent in Wireshark. The node that receives the ARP packet will show 60 bytes received (4 byte CRC is also something Wireshark cannot normally observe). If you attach an oscilloscope to the Ethernet cable, you will observe a waveform lasting 576 bit times (57.6us). 576 bit times comes about because the frame will consist of 7 bytes of preamble, 1 start of frame delimiter byte, 42 ARP protocol bytes, 18 padding bytes, and 4 CRC bytes for a total of 72 bytes of 576 bits.`
答案来源: Frame with no padding
文中答案就是说:
所有的ARP包都是64个字节,而不是42个。
请求包:60 + 4(CRC)ARP包在通过以太网硬件传输时补充到64个字节的
响应包:windows值只提交42个字节到NDIS(网络驱动程序接口规范)驱动,会填补 18(IP packet包凑够46个字节,我们上边分析暂时总共占用28个字节) + 4(CRC),wireshark只能看到42个
参考资料



